- Table of Contents
-
- 03-Layer 2 Configuration Guide
- 00-Preface
- 01-Ethernet Interface Configuration
- 02-Loopback and Null Interface Configuration
- 03-VLAN Configuration
- 04-MAC Address Table Configuration
- 05-Ethernet Link Aggregation Configuration
- 06-Spanning Tree Configuration
- 07-Layer 2 Forwarding Configuration
- 08-PPPoE Configuration
- 09-FPGA Fast Forwarding Configuration
- 10-QinQ Termination Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 04-MAC Address Table Configuration | 85.11 KB |
Configuring the MAC address table
How a MAC address entry is created
Configuring static, dynamic, and destination blackhole MAC address entries
Adding or modifying a static or dynamic MAC address entry in system view
Adding or modifying a static or dynamic MAC address entry in interface view
Configuring a destination blackhole MAC address entry
Disabling MAC address learning
Disabling global MAC address learning
Disabling MAC address learning on interfaces
Setting the aging timer for dynamic MAC address entries
Setting the MAC learning limit on interfaces
Displaying and maintaining MAC address tables
MAC address table configuration example
Configuring the MAC address table
This document covers only the configuration of unicast MAC address entries, including static, dynamic, and destination blackhole MAC address entries.
The MAC address table configuration tasks can be performed in any order.
Overview
To reduce single-destination packet flooding in a switched LAN, an Ethernet device uses a MAC address table for forwarding frames. This table describes from which interface a MAC address (or host) can be reached. When forwarding a single-destination frame, the device first looks up the destination MAC address of the frame in the MAC address table for a match. If the device finds an entry, it forwards the frame out of the outgoing interface in the entry. If the device does not find an entry, it floods the frame out of all but the incoming interface.
To view MAC address table information, use the display mac-address command, as follows:
<Sysname> display mac-address
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)
000f-e201-0101 1 Learned GigabitEthernet1/0/1 AGING
--- 1 mac address(es) found ---
How a MAC address entry is created
The device automatically learns entries in the MAC address table, or you can add them manually.
MAC address learning
The device can automatically populate its MAC address table by learning the source MAC addresses of incoming frames on each interface.
When a frame arrives at an interface, Port A, for example, the device performs the following operations:
1. Verifies the source MAC address (for example, MAC-SOURCE) of the frame.
2. Looks up the source MAC address in the MAC address table.
3. Updates an entry if it finds one. If the device does not find an entry, it adds an entry for MAC-SOURCE and Port A.
The device performs this learning process each time it receives a frame from an unknown source MAC address, until the MAC address table is fully populated.
After learning a source MAC address, when the device receives a frame destined for MAC-SOURCE, the device finds the MAC-SOURCE entry in the MAC address table and forwards the frame out of Port A.
Manually configuring MAC address entries
With dynamic MAC address learning, a device does not distinguish between illegitimate and legitimate frames. For example, when a hacker sends frames with a forged source MAC address to an interface different from the one with which the real MAC address is associated, the device creates an entry for the forged MAC address, and forwards frames destined for the legal user to the hacker instead.
To improve interface security, you can bind specific user devices to the interface by manually adding MAC address entries to the MAC address table of the device.
Types of MAC address entries
A MAC address table can contain the following types of entries:
· Static entries—Manually added and never age out.
· Dynamic entries—Manually added or dynamically learned, and might age out.
· Destination blackhole entries—Manually configured and never age out. They are configured for filtering out frames with specific destination MAC addresses. For example, to block all packets destined for a specific user for security concerns, you can configure the MAC address of this user as a destination blackhole MAC address entry.
A static or destination blackhole MAC address entry can overwrite a dynamic MAC address entry, but not vice versa.
Configuring static, dynamic, and destination blackhole MAC address entries
To prevent MAC address spoofing attacks and improve interface security, manually add MAC address entries to bind interfaces with MAC addresses. You can also configure destination blackhole MAC address entries to filter out packets with certain destination MAC addresses.
The MAC address table can contain only Layer 2 Ethernet interfaces and Layer 2 aggregate interfaces.
Adding or modifying a static or dynamic MAC address entry in system view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Add or modify a dynamic or static MAC address entry. |
mac-address { dynamic | static } mac-address interface interface-type interface-number vlan vlan-id |
By default, no MAC address entry is configured. Make sure you have created the VLAN and assigned the interface to the VLAN. |
Adding or modifying a static or dynamic MAC address entry in interface view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Add or modify a static or dynamic MAC address entry. |
mac-address { dynamic | static } mac-address vlan vlan-id |
By default, no MAC address entry is configured. Make sure you have created the VLAN and assigned the interface to the VLAN. |
Configuring a destination blackhole MAC address entry
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Add or modify a destination blackhole MAC address entry. |
mac-address blackhole mac-address vlan vlan-id |
By default, no MAC address entry is configured. Make sure you have created the VLAN. |
Disabling MAC address learning
Sometimes, you might need to disable MAC address learning to prevent the MAC address table from being saturated, for example, when your device is being attacked by a large volume of packets with different source MAC addresses.
You can disable MAC address learning globally or on an interface.
Disabling global MAC address learning
Disabling global MAC address learning disables the learning function on all interfaces.
To disable global MAC address learning:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable global MAC address learning. |
mac-address mac-learning disable |
By default, global MAC address learning is enabled. |
Disabling MAC address learning on interfaces
You can disable MAC address learning on a single interface, or on all interfaces in a port group.
To disable MAC address learning on an interface or a port group:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable global MAC address learning. |
undo mac-address mac-learning disable |
Optional. By default, global MAC address learning is enabled. |
|
3. Enter interface view or port group view. |
· Enter Layer 2 Ethernet or aggregate interface
view: · Enter port group view: |
Use either command. Settings in interface view take effect only on the current interface. Settings in port group view take effect on all member interfaces in the port group. For more information about port groups, see "Configuring Ethernet interfaces." |
|
4. Disable MAC address learning. |
mac-address mac-learning disable |
By default, MAC address learning is enabled on each interface. |
Setting the aging timer for dynamic MAC address entries
The MAC address table uses an aging timer for dynamic MAC address entries for security and efficient use of table space. If a dynamic MAC address entry has failed to update before the aging timer expires, the device deletes that entry. This aging mechanism makes sure the MAC address table can promptly update to accommodate the latest network changes.
Set the aging timer appropriately. Too long an aging interval might cause the MAC address table to retain outdated entries, exhaust the MAC address table resources, and fail to update its entries to accommodate the latest network changes. Too short an interval might result in removal of valid entries, causing unnecessary floods, which could affect device performance.
To set the aging timer for dynamic MAC address entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the aging timer for dynamic MAC address entries. |
mac-address timer { aging seconds | no-aging } |
Optional. By default, the aging timer is 300 seconds. The no-aging keyword disables the aging timer. |
You can reduce floods on a stable network by disabling the aging timer to prevent dynamic entries from unnecessarily aging out. By reducing floods, you improve not only network performance, but also security, because you reduce the chances that a data packet will reach unintended destinations.
Setting the MAC learning limit on interfaces
As the MAC address table grows, the forwarding performance of your device might degrade. To prevent the MAC address table from getting so large that the forwarding performance degrades, you can limit the number of MAC addresses that an interface can learn.
To set the MAC learning limit on a Layer 2 Ethernet interface, Layer 2 aggregate interface, or all interfaces in a port group:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view or port group view. |
· Enter Layer 2 Ethernet or aggregate interface
view: · Enter port group view: |
Settings in interface view take effect only on the specific interface. Settings in port group view take effect on all member interfaces in the port group. |
|
3. Set the MAC learning limit on the interface or port group, and configure whether or not frames with unknown source MAC addresses can be forwarded when the MAC learning limit is reached. |
mac-address max-mac-count { count | disable-forwarding } |
The default MAC learning limit varies with devices. By default, frames with unknown source MAC addresses are forwarded when the MAC learning limit is reached. |
Displaying and maintaining MAC address tables
|
Task |
Command |
Remarks |
|
Display MAC address table information. |
display mac-address [ mac-address [ vlan vlan-id ] | [ [ dynamic | static ] [ interface interface-type interface-number ] | blackhole ] [ vlan vlan-id ] [ count ] ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the aging timer for dynamic MAC address entries. |
display mac-address aging-time [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the system or interface MAC address learning state. |
display mac-address mac-learning [ interface-type interface-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display MAC address statistics. |
display mac-address statistics [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
MAC address table configuration example
ACs have either 10 GE or GE interfaces. Table 1 identifies the Ethernet interfaces on different types of ACs.
If the AC is an AC module installed on a switch, make sure the internal Ethernet interface that connects the switch to the AC module has correct settings, including in particular VLAN settings.
Table 1 AC Ethernet interfaces
|
Hardware |
AC Ethernet interfaces |
|
AC modules (installed in a switch) |
|
|
LSQM1WCMD0 LSRM1WCM3A1 LSUM3WCMD0 LSUM1WCME0 |
The internal Ethernet interface that connects the AC module to the switch. |
|
Wireless switches |
|
|
WX3024E WX3010E |
The internal Ethernet interface that connects the AC engine to the switching engine. |
|
ACs |
|
|
WX6103 |
The internal Ethernet interface that connects the main control board to the switching board. |
|
WX5002V2 WX5004 WX3510E WX3540E WX5510E |
Any Ethernet interfaces on the AC. |
|
WX2540E WAC360 WAC361 |
Any LAN or WAN interfaces on the AC. |
|
WX5540E |
The internal Ethernet interface that connects the AC engine to the switching engine. |
Network requirements
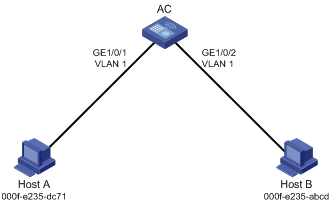
As shown in Figure 1:
· Host A at MAC address 000f-e235-dc71 is connected to GigabitEthernet 1/0/1 of the AC and belongs to VLAN 1.
· Host B at MAC address 000f-e235-abcd, which behaved suspiciously on the network, also belongs to VLAN 1.
Configure the MAC address table as follows:
· To prevent MAC address spoofing, add a static entry for Host A in the MAC address table of the AC.
· To drop all frames destined for Host B, add a blackhole MAC address entry for Host B
· Set the aging timer to 500 seconds for dynamic MAC address entries.
Configuration procedure
# Add a static MAC address entry.
<AC> system-view
[AC] mac-address static 000f-e235-dc71 interface gigabitethernet 1/0/1 vlan 1
# Add a destination blackhole MAC address entry.
[AC] mac-address blackhole 000f-e235-abcd vlan 1
# Set the aging timer to 500 seconds for dynamic MAC address entries.
[AC] mac-address timer aging 500
# Display MAC address entries on GigabitEthernet 1/0/1.
[AC] display mac-address interface gigabitethernet 1/0/1
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)
000f-e235-dc71 1 Config static GigabitEthernet 1/0/1 NOAGED
--- 1 mac address(es) found ---
# Display information about the destination blackhole MAC address table.
[AC] display mac-address blackhole
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)
000f-e235-abcd 1 Blackhole N/A NOAGED
--- 1 mac address(es) found ---
# Display the aging time of dynamic MAC address entries.
[AC] display mac-address aging-time
Mac address aging time: 500s
