- Table of Contents
-
- 11-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-Portal configuration
- 03-User profile configuration
- 04-Password control configuration
- 05-Keychain configuration
- 06-Public key management
- 07-PKI configuration
- 08-IPsec configuration
- 09-Group domain VPN configuration
- 10-SSH configuration
- 11-SSL configuration
- 12-SSL VPN configuration
- 13-ASPF configuration
- 14-APR configuration
- 15-Session management
- 16-Connection limit configuration
- 17-Object group configuration
- 18-Object policy configuration
- 19-Attack detection and prevention configuration
- 20-ARP attack protection configuration
- 21-ND attack defense configuration
- 22-uRPF configuration
- 23-Crypto engine configuration
- 24-FIPS configuration
- 25-SMA configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 25-SMA configuration | 99.00 KB |
Configuring SMA
Overview
State Machine Based Anti-Spoofing (SMA) prevents IPv6 spoofing attacks between autonomous systems (ASs) by verifying source IPv6 addresses.
SMA components
Figure 1 SMA network diagram
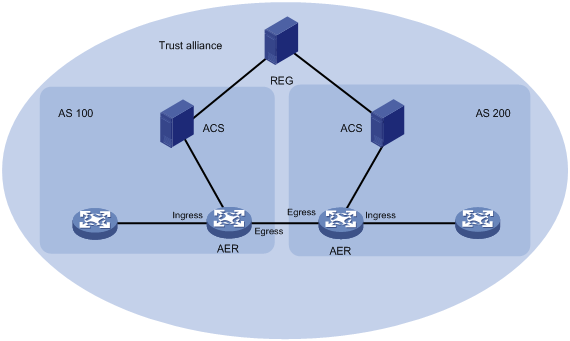
· Trust alliance—A group of ASs that trust each other. ASs in an alliance are member ASs that share the same alliance ID.
· AS pair—An ordered pair of source and destination ASs. An AS pair uses one state machine to generate and update tags. Tags are added to packets by the source AS edge router (AER) and verified by the destination AER to ensure source address validity.
· REG—The registration center (REG) of a trust alliance collects and distributes AS register information to inform an AS of other member ASs in the alliance.
· ACS—An AS controller server (ACS) performs the following tasks over SSL links:
? Registers at the REG to become a member AS of one or multiple trust alliances.
? Exchanges IPv6 prefix and state machine information with ACSs of other member ASs.
? Sends the following information to AERs of the local AS:
- IPv6 prefixes of the local AS and other member ASs.
- Tags generated by the state machines of the local AS and other member ASs.
· AER—An AER adds and verifies tags for packets within an AS pair based on the received IPv6 prefixes and tags. An AER has the following types of SMA interfaces:
? Ingress interface—Connected to an SMA-disabled router in the local AS.
? Egress interface—Connected to an AER in another member AS.
The device can operate only as an AER.
SMA processes for packets
SMA provides inter-AS IPv6 source address validation. It enforces source address validity on AERs. An AER validates source IPv6 addresses of packets between the local AS and other ASs in the same trust alliance.
For outgoing packets from the local AS to other ASs
1. When the ingress interface receives a packet, it checks the source IPv6 prefix of the packet to identify the source AS.
? If the source AS is not the local AS, the AER discards the packet.
? If the source AS is the local AS, the AER forwards the packet to its egress interface.
2. When the egress interface receives a packet, it checks the source IPv6 prefix of the packet to identify the source AS.
? If the source AS is not the local AS, the AER forwards the packet.
? If the source AS is the local AS, the AER verifies the destination IPv6 prefix of the packet to identify the destination AS.
- If the destination AS is not a member AS, the AER directly forwards the packet.
- If the destination AS is a member AS, the AER adds a tag to the packet and then forwards the packet.
For incoming packets from other ASs to the local AS
1. When the egress interface receives a packet, it examines the following information:
? Whether the packet has an SMA tag.
? The source and destination ASs (AS pair) of the packet.
? Whether the AS pair has an SMA tag.
2. The AER processes the packet based on the principles in Table 1.
Table 1 Packet processing principles
|
Situations |
AER operations |
|
The AS pair does not have an SMA tag. |
Removes the packet's SMA tag (if any) and forwards the packet. |
|
The AS pair has an SMA tag but the packet does not. |
Discards the packet. |
|
The AS pair and the packet has the same SMA tag. |
Removes the packet's SMA tag and forwards the packet. |
|
The AS pair and the packet has different SMA tags. |
Discards the packet. |
SMA configuration procedure
Before you configure SMA on each AER, synchronize clocks for all devices in the alliance, including the REG, ACSs, and AERs. On an AER, use the clock datetime command to configure the system time. For more information about the clock datetime command, see Fundamentals Command Reference.
To configure SMA:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SMA. |
sma-anti-spoof ipv6 enable |
By default, SMA is disabled. |
|
3. Configure an SSL link between the AER and the ACS. |
sma-anti-spoof ipv6 server ipv6-address ssl-client-policy policy-name |
By default, the SSL link is not configured between the AER and the ACS. For information about configuring an SSL client policy, see "Configuring SSL." |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Configure SMA interface type. |
sma-anti-spoof ipv6 port-type { ingress | egress } |
By default, no SMA interface is configured. |
Displaying and maintaining SMA
Execute display commands in any view.
|
Task |
Command |
|
Display IPv6 prefix information for all ASs. |
display sma-anti-spoof ipv6 address-prefix |
|
Display SMA tag information for all AS pairs. |
display sma-anti-spoof ipv6 packet-tag |
SMA configuration example
Network requirements
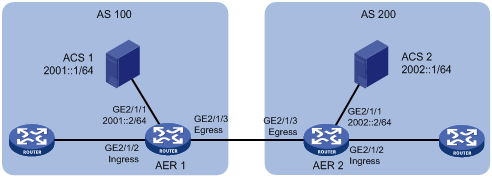
As shown in Figure 2, AER 1 and AER 2 use SMA to prevent IPv6 source address spoofing.
Configuration procedure
1. Synchronize clocks for all devices in the alliance. (Details not shown.)
2. Configure ACS 1 and ACS 2. (Details not shown.)
3. Configure AER 1.
# Configure an IPv6 address for AER 1. (Details not shown.)
# Create SSL client policy sma on AER 1.
<AER1> system-view
[AER1] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AER1-ssl-client-policy-sma] undo server-verify enable
[AER1-ssl-client-policy-sma] quit
# Enable SMA on AER 1 and configure an SSL link between AER 1 and ACS 1.
[AER1] sma-anti-spoof ipv6 enable
[AER1] sma-anti-spoof ipv6 server 2001::1 ssl-client-policy sma
# Configure SMA interfaces for AER 1.
[AER1] interface gigabitethernet 2/1/2
[AER1-GigabitEthernet2/1/2] sma-anti-spoof ipv6 port-type ingress
[AER1-GigabitEthernet2/1/2] quit
[AER1] interface gigabitethernet 2/1/3
[AER1-GigabitEthernet2/1/3] sma-anti-spoof ipv6 port-type egress
[AER1-GigabitEthernet2/1/3] quit
4. Configure AER 2.
# Configure an IPv6 address for AER 2. (Details not shown.)
# Create SSL client policy sma on AER 2.
<AER2> system-view
[AER2] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AER2-ssl-client-policy-sma] undo server-verify enable
[AER2-ssl-client-policy-sma] quit
# Enable SMA on AER 2 and configure an SSL link between AER 2 and ACS 2.
[AER2] sma-anti-spoof ipv6 enable
[AER2] sma-anti-spoof ipv6 server 2002::1 ssl-client-policy sma
# Configure SMA interfaces for AER 2.
[AER2] interface gigabitethernet 2/1/2
[AER2-GigabitEthernet2/1/2] sma-anti-spoof ipv6 port-type ingress
[AER2-GigabitEthernet2/1/2] quit
[AER2] interface gigabitethernet 2/1/3
[AER2-GigabitEthernet2/1/3] sma-anti-spoof ipv6 port-type egress
[AER2-GigabitEthernet2/1/3] quit
Verifying the configuration
# Verify that the AER can obtain IPv6 prefixes and SMA tags from the ACS.
[AER1] display sma-anti-spoof ipv6 address-prefix
Alliance number: 0 AS number: 200
IPv6 prefix Effecting time
FF::/16 May 5 07:00:11 2014(i)
Alliance number: 0 AS number: 200
IPv6 prefix Effecting time
EE::/16 May 5 07:00:11 2014(i)
[AER1] display sma-anti-spoof ipv6 packet-tag
Alliance number: 0
Source AS number: 100 Destination AS number: 200
State machine ID: 100 Tag: 0xAB12
Effecting time: May 5 07:00:11 2014(i) Transition interval: 3600s

