- Table of Contents
-
- 11-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-Portal configuration
- 03-User profile configuration
- 04-Password control configuration
- 05-Keychain configuration
- 06-Public key management
- 07-PKI configuration
- 08-IPsec configuration
- 09-Group domain VPN configuration
- 10-SSH configuration
- 11-SSL configuration
- 12-SSL VPN configuration
- 13-ASPF configuration
- 14-APR configuration
- 15-Session management
- 16-Connection limit configuration
- 17-Object group configuration
- 18-Object policy configuration
- 19-Attack detection and prevention configuration
- 20-ARP attack protection configuration
- 21-ND attack defense configuration
- 22-uRPF configuration
- 23-Crypto engine configuration
- 24-FIPS configuration
- 25-SMA configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 16-Connection limit configuration | 96.09 KB |
Connection limit configuration task list
Creating a connection limit policy
Configuring the connection limit policy
Applying the connection limit policy
Displaying and maintaining connection limits
Connection limit configuration example
Troubleshooting connection limits
ACLs in the connection limit rules with overlapping segments
Configuring connection limits
Overview
The connection limit feature enables the device to monitor and limit the number of established connections.
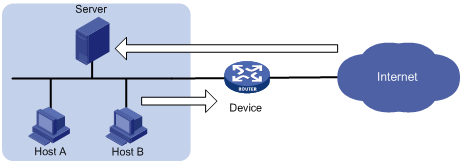
As shown in Figure 1, configure the connection limit feature to resolve the following problems:
· If Host B initiates a large number of connections in a short period of time, it might exhaust system resources and cause Host A to be unable to access the Internet.
· If the internal server receives a large number of connection requests in a short period of time, the server cannot process other requests.
Connection limit configuration task list
|
Tasks at a glance |
|
(Required.) Creating a connection limit policy |
|
(Required.) Configuring the connection limit policy |
|
(Required.) Applying the connection limit policy |
Creating a connection limit policy
A connection limit policy contains a set of connection limit rules, each of which defines a range of connections and the criteria for limiting the connections.
To create a connection limit policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a connection limit policy and enter its view. |
connection-limit { ipv6-policy | policy } policy-id |
By default, no connection limit policies exist. |
Configuring the connection limit policy
To use a connection limit policy, you need to add limit rules to the policy. Each rule defines a range of connections and the criteria for limiting the connections. Connections in the range will be limited based on the criteria. The criteria include upper/lower connection limit and connection establishment rate limit. When the number of matching connections reaches the upper limit, the device does not accept new connections until the number of connections drops below the lower limit. The device will send logs when the number of connections exceeds the upper limit and when the number of connections drops below the lower limit. If the matching connections are limited based on the establishment rate, the number of connections established per second cannot exceed the rate limit. The connections that do not match any connection limit rules are not limited.
In each connection limit rule, an ACL is used to define the connection range. In addition, the rule also uses the following filtering methods to further limit the connections:
· per-destination—Limits user connections by destination IP address.
· per-service—Limits user connections by service (transport layer protocol and service port).
· per-source—Limits user connections by source IP address.
· per-ds-lite-b4—Limits user connections by the B4 device on a DS-Lite tunnel. For information about DS-Lite tunnels, see Layer 3—IP Services Configuration Guide.
You can select more than one filtering method, and the selected methods take effect at the same time. For example, if you specify both per-destination and per-service, the user connections using the same service and destined to the same IP address are limited. If you do not specify any filtering methods in a limit rule, all user connections in the range are limited.
When a connection limit policy is applied, connections on the device match all limit rules in the policy in ascending order of rule IDs. As a best practice, specify a smaller range and more filtering methods in a rule with a smaller ID.
The connections are limited on a per-device basis.
To configure the connection limit policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter connection limit policy view. |
connection-limit { ipv6-policy | policy } policy-id |
N/A |
|
3. Configure a connection limit rule. |
· In IPv4 connection limit policy view: ¡ limit limit-id acl { acl-number | name acl-name } [ per-destination | per-service | per-source ] * { amount max-amount min-amount | rate rate } * [ description text ] ¡ limit limit-id acl ipv6 { acl-number | name acl-name } per-ds-lite-b4 { amount max-amount min-amount | rate rate } * [ description text ] · In IPv6 connection limit policy view: |
By default, no connection limit rules exist. |
|
4. (Optional.) Configure a description for the connection limit policy. |
By default, the connection limit policy does not have a description. |
Applying the connection limit policy
To make a connection limit policy take effect, apply it globally or to an interface. The connection limit policy applied to an interface takes effect only on the specified connections on the interface. The connection limit policy applied globally takes effect on all the specified connections on the device.
Different connection limit policies can be applied to individual interfaces as well as globally on the device. In this case, the device matches connections against these policies in the order of the policy on the inbound interface, the global policy, and the policy on the outbound interface. It cannot accept new connections as long as the number of connections reaches the smallest upper connection limit defined by these policies.
A connection limit policy takes effect only on new connections. It does not take effect on existing connections.
On an IRF fabric where session synchronization is enabled, connection limit policies applied to a subordinate device do not take effect on sessions switched from the master device.
On a DS-Lite tunnel network, if the AFTR device uses the Endpoint-Independent Mapping-based NAT configuration, you must limit connections from external IPv4 networks to access the internal IPv4 network. To implement B4 device-based connection limits, perform the following tasks:
· Add a rule that has the per-ds-lite-b4 to a connection limit policy.
· Apply the policy globally or on the DS-Lite tunnel interface.
To apply a connection limit policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Apply a connection limit policy. |
· Apply a connection limit policy
globally: · Apply a connection limit policy to an interface: a. interface interface-type interface-number b. connection-limit apply { ipv6-policy | policy } policy-id |
By default, no connection limit is applied. Only one IPv4 connection limit policy and one IPv6 connection limit policy can be applied globally or to an interface. A new IPv4 or IPv6 connection limit policy overwrites the old policy. |
Displaying and maintaining connection limits
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the connection limit policy information. |
display connection-limit { ipv6-policy | policy } { all | policy-id } |
|
Display the connection limit statistics globally or on an interface (in standalone mode). |
display connection-limit statistics { global | interface interface-type interface-number } [ slot slot-number ] |
|
Display the connection limit statistics globally or on an interface (in IRF mode). |
display connection-limit statistics { global | interface interface-type interface-number } [ chassis chassis-number slot slot-number ] |
|
Display statistics about IPv6 connections matching connection limit rules globally or on an interface (in standalone mode). |
display connection-limit { ipv6-stat-nodes | stat-nodes } { global | interface interface-type interface-number } [ slot slot-number ] [ destination destination-ip | service-port port-number | source source-ip ] * [ count ] |
|
Display statistics about IPv6 connections matching connection limit rules globally or on an interface (in IRF mode). |
display connection-limit { ipv6-stat-nodes | stat-nodes } { global | interface interface-type interface-number } [ chassis chassis-number slot slot-number ] [ destination destination-ip | service-port port-number | source source-ip ] * [ count ] |
|
Clear the connection limit statistics globally or on an interface. |
reset connection-limit statistics { global | interface interface-type interface-number } |
Connection limit configuration example
Network requirements
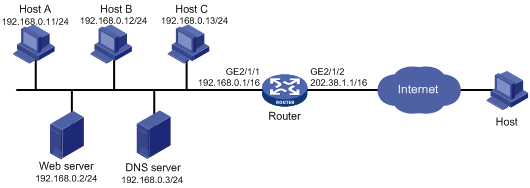
As shown in Figure 2, a company has five public IP addresses: 202.38.1.1/24 to 202.38.1.5/24. The internal network address is 192.168.0.0/16. Configure NAT so that the internal users can access the Internet and external users can access the internal servers. Configure connection limits to meet the following requirements:
· All hosts on segment 192.168.0.0/24 can establish a maximum of 100000 connections to the external network.
· Each host on segment 192.168.0.0/24 can establish a maximum of 100 connections to the external network.
· A maximum of 10000 query requests from DNS clients to the DNS server are allowed at the same time.
· A maximum of 10000 connection requests from Web clients to the Web server are allowed at the same time.
Configuration procedure
The following example only describes how to configure connection limits. For information about NAT configuration and internal server configuration, see Layer 3—IP Services Configuration Guide.
# Create ACL 3000 to permit packets from all hosts on the internal network.
<Router> system-view
[Router] acl advanced 3000
[Router-acl-ipv4-adv-3000] rule permit ip source 192.168.0.0 0.0.0.255
[Router-acl-ipv4-adv-3000] quit
# Create ACL 3001 to permit packets to the Web server and the DNS server.
[Router] acl advanced 3001
[Router-acl-ipv4-adv-3001] rule permit ip destination 192.168.0.2 0
[Router-acl-ipv4-adv-3001] rule permit ip destination 192.168.0.3 0
[Router-acl-ipv4-adv-3001] quit
# Create connection limit policy 1.
[Router] connection-limit policy 1
# Configure connection limit rule 1 to permit a maximum of 100000 connections from all the hosts that match ACL 3000. When the number of connections exceeds 100000, new connections cannot be established until the number drops below 95000.
[Router-connection-limit-policy-1] limit 1 acl 3000 amount 100000 95000
# Configure connection limit rule 2 to permit a maximum of 10000 connections to the servers that match ACL 3001. When the number of connections exceeds 10000, new connections cannot be established until the number drops below 9800.
[Router-connection-limit-policy-1] limit 2 acl 3001 per-destination amount 10000 9800
[Router-connection-limit-policy-1] quit
# Create connection limit policy 2.
[Router] connection-limit policy 2
# Configure connection limit rule 1 to permit a maximum of 100 connections from each host matching ACL 3000. When the number of connections exceeds 100, new connections cannot be established until the number drops below 90.
[Router-connection-limit-policy-2] limit 1 acl 3000 per-source amount 100 90
[Router-connection-limit-policy-2] quit
# Apply connection limit policy 1 globally.
[Router] connection-limit apply global policy 1
# Apply connection limit policy 2 to inbound interface GigabitEthernet 2/1/1.
[Router] interface gigabitethernet 2/1/1
[Router-GigabitEthernet2/1/1] connection-limit apply policy 2
[Router-GigabitEthernet2/1/1] quit
Verifying the configuration
# Display information about the connection limit policy.
[Router] display connection-limit policy 1
IPv4 connection limit policy 1 has been applied 1 times, and has 2 limit rules.
Limit rule list:
Policy Rule StatType HiThres LoThres rate ACL
------------------------------------------------------------
1 1 -- 100000 95000 0 3000
2 Dst 10000 9800 0 3001
Applied list:
Global
[Router] display connection-limit policy 2
IPv4 connection limit policy 2 has been applied 1 times, and has 1 limit rules.
Limit rule list:
Policy Rule StatType HiThres LoThres rate ACL
------------------------------------------------------------
2 1 Src 100 90 0 3000
Applied list:
GigabitEthernet2/1/1
Troubleshooting connection limits
ACLs in the connection limit rules with overlapping segments
Symptom
A connection limit policy has two rules. Rule 1 sets the upper limit to 10 for the connections from each host on segment 192.168.0.0/24. Rule 2 sets the upper limit to 100 for the connections from 192.168.0.100/24.
<Router> system-view
[Router] acl basic 2001
[Router-acl-ipv4-basic-2001] rule permit source 192.168.0.0 0.0.0.255
[Router-acl-ipv4-basic-2001] quit
[Router] acl basic 2002
[Router-acl-ipv4-basic-2002] rule permit source 192.168.0.100 0
[Router-acl-ipv4-basic-2002] quit
[Router] connection-limit policy 1
[Router-connection-limit-policy-1] limit 1 acl 2001 per-destination amount 10 5
[Router-connection-limit-policy-1] limit 2 acl 2002 per-destination amount 100 10
As a result, the host at 192.168.0.100 can only initiate a maximum of 10 connections to the external network.
Solution
To resolve the problem:
1. Rearrange the two connection limit rules by exchanging their rule IDs.
2. If the problem persists, contact H3C Support.

