- Table of Contents
-
- H3C S5500-SI Series Ethernet Switches Operation Manual(V1.01)
- 00-1Cover
- 00-2Overview
- 01-Login Configuration
- 02-VLAN Configuration
- 03-IP Addressing and IP Performance Configuration
- 04-QinQ-BPDU TUNNEL Configuration
- 05-Port Correlation Configuration
- 06-Link Aggregation Configuration
- 07-MAC Address Table Management Configuration
- 08-Port Security Configuration
- 09-MSTP Configuration
- 10-IPv6 Configuration
- 11-IP Routing Overview Configuration
- 12-IPv4 Routing Configuration
- 13-IPv6 Routing Configuration
- 14-Multicast Configuration
- 15-802.1x-HABP-MAC Authentication Configuration
- 16-AAA-RADIUS-HWTACACS Configuration
- 17-ARP Configuration
- 18-DHCP Configuration
- 19-ACL Configuration
- 20-QoS Configuration
- 21-Port Mirroring Configuration
- 22-UDP Helper Configuration
- 23-Cluster Management Configuration
- 24-SNMP-RMON Configuration
- 25-NTP Configuration
- 26-DNS Configuration
- 27-File System Management Configuration
- 28-Information Center Configuration
- 29-System Maintaining and Debugging Configuration
- 30-NQA Configuration
- 31-SSH Configuration
- 32-Track Configuration
- 33-PoE Configuration
- 34-SSL-HTTPS Configuration
- 35-PKI Configuration
- 36-Stack Management Configuration
- 37-Appendix
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 31-SSH Configuration | 741 KB |
1.1.2 Asymmetric Key Algorithm
1.2 Configuring the Device as an SSH Server
1.2.1 SSH Server Configuration Task List
1.2.3 Configuring the User Interfaces for SSH Clients
1.2.4 Configuring RSA and DSA Keys
1.2.5 Configuring a Client Public Key
1.2.7 Setting the SSH Management Parameters
1.3 Configuring the Device as an SSH Client
1.3.1 SSH Client Configuration Task List
1.3.2 Specifying a Source IP address/Interface for the SSH client
1.3.3 Configuring Whether First-time Authentication is Supported
1.3.4 Establishing a Connection Between the SSH Client and the Server
1.4 Displaying and Maintaining SSH
1.5 SSH Server Configuration Examples
1.5.1 When Using Password Authentication
1.5.2 When Using Publickey Authentication
1.6 SSH Client Configuration Examples
1.6.1 When Using Password Authentication
1.6.2 When Using Publickey Authentication
2.2 Configuring an SFTP Server
2.2.1 Configuration Prerequisites
2.2.2 Enabling the SFTP Server
2.2.3 Configuring the SFTP Connection Idle Timeout Period
2.3 Configuring an SFTP Client
2.3.1 Specifying a Source IP Address or Interface for the SFTP Client
2.3.2 Establishing a Connection to the SFTP Server
2.3.3 Working with the SFTP Directories
2.3.5 Displaying Help Information
2.3.6 Terminating the Connection to the Remote SFTP Server
2.4 SFTP Configuration Example
Chapter 1 SSH Configuration
When configuring SSH, go to these sections for information you are interested in:
l Configuring the Device as an SSH Server
l Configuring the Device as an SSH Client
l Displaying and Maintaining SSH
l SSH Server Configuration Examples
l SSH Client Configuration Examples
1.1 SSH2.0 Overview
Secure Shell (SSH) offers an approach to securely logging into a remote device. By encryption and strong authentication, it protects devices against attacks such as IP spoofing and plain text password interception.
The device can not only work as an SSH server to support connections with SSH clients, but also work as an SSH client to allow users to establish SSH connections with a remote device acting as the SSH server.
& Note:
Currently, when acting as an SSH server, the device supports two SSH versions: SSH2 and SSH1. When acting as an SSH client, the device supports SSH2 only.
1.1.1 Algorithm and Key
Algorithm is a set of transformation rules for encryption and decryption. Information without being encrypted is known as plain text, while information that is encrypted is known as cipher text. Encryption and decryption are performed using a string of characters called a key, which controls the transformation between plain text and cipher text, for example, changing the plain text into cipher text or cipher text into plain text.

Figure 1-1 Encryption and decryption
Key-based algorithm is usually classified into symmetric key algorithm and asymmetric key algorithm.
1.1.2 Asymmetric Key Algorithm
Asymmetric key algorithm means that a key pair exists at both ends. The key pair consists of a private key and a public key. The public key is effective for both ends, while the private key is effective only for the local end.
Asymmetric key algorithm encrypts data using the public key and decrypts the data using the private key, thus ensuring data security.
You can also use the asymmetric key algorithm for digital signature. For example, user 1 adds his signature to the data using the private key, and then sends the data to user 2. User 2 verifies the signature using the public key of user 1. If the signature is correct, this means that the data originates from user 1.
Revest-Shamir-Adleman Algorithm (RSA) and Digital Signature Algorithm (DSA) are both asymmetric key algorithms. RSA can be used for data encryption and signature, whereas DSA is used for signatures only.
& Note:
Currently, SSH2 supports both RSA and DSA.
1.1.3 SSH Operating Process
The session establishment between an SSH client and the SSH server involves the following five stages:
Table 1-1 Stages in establishing a session between the SSH client and the server
|
Stages |
Description |
|
SSH1 and SSH2 are supported. The two parties negotiate a version to use. |
|
|
SSH supports multiple algorithms. The two parties negotiate an algorithm for communication. |
|
|
The SSH server authenticates the client in response to the client’s authentication request. |
|
|
This client sends a session request to the server. |
|
|
The client and the server start to communicate with each other. |
I. Version negotiation
l The server opens port 22 to listen to connection requests from clients.
l The client sends a TCP connection request to the server. After the TCP connection is established, the server sends the first packet to the client, which includes a version identification string in the format of “SSH-<primary protocol version number>.<secondary protocol version number>-<software version number>”. The primary and secondary protocol version numbers constitute the protocol version number, while the software version number is used for debugging.
l The client receives and resolves the packet. If the protocol version of the server is lower but supportable, the client uses the protocol version of the server; otherwise, the client uses its own protocol version.
l The client sends to the server a packet that contains the number of the protocol version it decides to use. The server compares the version carried in the packet with that of its own to determine whether it can cooperate with the client.
l If the negotiation is successful, the server and the client proceed with key and algorithm negotiation; otherwise, the server breaks the TCP connection.
& Note:
All the packets involved in the above steps are transferred in plain text.
II. Key and algorithm negotiation
l The server and the client send key algorithm negotiation packets to each other, which include the supported public key algorithm list, encryption algorithm list, MAC algorithm list, and compression algorithm list.
l Based on the received algorithm negotiation packets, the server and the client figure out the algorithms to be used.
l The server and the client use the DH key exchange algorithm and parameters such as the host key pair to generate the session key and session ID.
Through the above steps, the server and the client get the same session key, which is to be used to encrypt and decrypt data exchanged between the server and the client later. The server and the client use session ID in the authentication stage.
![]() Caution:
Caution:
Before the negotiation, the server must have already generated the RSA and DSA key pairs, which are mainly used for generating the session key.
III. Authentication
l The client sends to the server an authentication request, which includes the username, authentication method and information related to the authentication method (the password in the case of password authentication).
l The server authenticates the client. If the authentication fails, the server informs the client by sending a message, which includes a list of available methods for re-authentication.
l The client selects a method from the list to initiate another authentication.
l The above process repeats until the authentication succeeds or the authentication times timeout and the session is torn down.
SSH provides two authentication methods: password authentication and publickey authentication.
In password authentication:
l The client encrypts the username and password, encapsulates them into a password authentication request, and sends the request to the server.
l Upon receiving the request, the server decrypts the username and password, compares them against those it maintains, and then informs the client of the authentication result.
In publickey authentication:
l The server authenticates clients using digital signatures. Currently, the device supports two publickey algorithms to implement digital signatures: RSA and DSA. The client sends to the server a public authentication request containing its user name, public key and algorithm. The server validates the public key. If the public key is invalid, the authentication fails; otherwise, the server generates a digital signature to authenticate the client, and then sends back a message to inform the success or failure of the authentication.
& Note:
Besides password authentication and publickey authentication, SSH provides another two authentication methods:
l password-publickey: Performs both password authentication and publickey authentication of the client. A client running SSH1 client only needs to pass either type of the two, while a client running SSH2 client must pass both of them to login.
l any: Performs either password authentication or publickey authentication. The client tries publickey authentication first.
IV. Session request
After passing authentication, the client sends a session request to the server, while the server listens to and processes the request from the client. If the client passes authentication, the server sends back to the client an SSH_SMSG_SUCCESS packet and goes on to the interactive session stage with the client. Otherwise, the server sends back to the client an SSH_SMSG_FAILURE packet, indicating that the processing fails or it cannot resolve the request.
V. Interactive session
In this stage, the server and the client exchanges data in this way:
l The client encrypts and sends the command to be executed to the server.
l The server decrypts and executes the command, and then encrypts and sends the result to the client.
l The client decrypts and displays the result on the terminal.
l During interactive session, the client can send the commands to be performed by pasting the text, which must be within 2000 bytes. It is recommended that the text pasted be commands in the same view; otherwise, the server may not be able to perform the commands.
l If the text exceeds 2000 bytes, you can upload the configuration file to the server and use the configuration file to restart the server so that the server executes the commands.
1.2 Configuring the Device as an SSH Server
1.2.1 SSH Server Configuration Task List
Complete the following tasks to configure an SSH server:
|
Task |
Remarks |
|
|
Required |
||
|
Required |
||
|
Required |
||
|
Optional |
||
|
Optional |
||
|
Required for publickey authentication users and optional for password authentication users |
||
|
Optional |
||
|
Optional |
||
& Note:
As a client uses either RSA or DSA algorithm for authentication and different clients may support different algorithms, the server needs to generate both RSA and DSA key pairs for successful authentication.
1.2.2 Enabling SSH Server
Follow these steps to enable SSH server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the SSH server function |
ssh server enable |
Required Disabled by default |
1.2.3 Configuring the User Interfaces for SSH Clients
An SSH client accesses the device through a VTY user interface. Therefore, you need to configure the user interfaces for SSH clients to allow SSH login. Note that the configuration takes effect at the next login.
Follow these steps to configure the protocols for the current user interface to support:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter user interface view of one or more user interfaces |
user-interface vty number [ ending-number ] |
Required |
|
Set the login authentication method to scheme |
authentication-mode scheme [ command-authorization ] |
Required By default, the authentication mode is password. |
|
Specify the protocols for the user interfaces to support |
protocol inbound { all | ssh | telnet } |
Optional All protocols are supported by default. |
![]() Caution:
Caution:
l For detailed information about the authentication-mode and protocol inbound commands, refer to Login Commands.
l If you configure a user interface to support SSH, be sure to configure the corresponding authentication method with the authentication-mode scheme command.
l For a user interface configured to support SSH, you cannot configure the authentication-mode password command and the authentication-mode none command.
1.2.4 Configuring RSA and DSA Keys
I. Creating RSA or DSA key pairs
For successful SSH login, you must create the RSA or DSA key pairs first.
Follow these steps to create an RSA or DSA key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create the local RSA key pair |
public-key local create rsa |
Required Use either command. By default, there is neither RSA key pair nor DSA key pair. |
|
Create the local DSA key pair |
public-key local create dsa |
![]() Caution:
Caution:
l Configuration of the rsa local-key-pair create and public-key local create dsa command can survive a reboot. You only need to configure it once.
l The length of an RSA server/host key is in the range 512 to 2048 bits. With SSH2, however, some clients require that the keys generated by the server must not be less than 768 bits.
l The length of a DSA host key is in the range 512 to 2048 bits. With SSH2, nevertheless, some clients require that the keys generated by the server must not be less than 768 bits.
II. Exporting RSA or DSA key pairs
You can display or export the local RSA or DSA host key for setting the host key on the remote end.
Follow these steps to display or export an RSA or DSA host key:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Display the local RSA host key on the screen in a specified format, or export it to a specified file |
public-key local export rsa { openssh | ssh1 | ssh2 } [ filename ] |
Required Use either command. |
|
Display the local DSA host key on the screen in a specified format, or export it to a specified file |
public-key local export dsa { openssh | ssh2 } [ filename ] |
III. Destroying RSA or DSA key pairs
Follow these steps to destroy an RSA or DSA key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Destroy the local RSA key pair |
public-key local destroy rsa |
Required Use either command. |
|
Destroy the local DSA key pair |
public-key local destroy dsa |
1.2.5 Configuring a Client Public Key
& Note:
This configuration task is only necessary for SSH users using publickey authentication.
For an SSH user that uses publickey authentication to login, the server must be configured with the client RSA or DSA host public key in advance, and the corresponding private key for the client must be specified on the client.
You can manually configure or import the publickey public key from a public key file. In the former case, you can manually copy the client’s public key configuration to the server. In the latter case, the system automatically converts the public key to a string coded using the PKCS standard. Before importing the public key, you must upload the public key file (in binary) to the server through FTP or TFTP.
![]() Caution:
Caution:
l When the device functions as the SSH server, you cannot use Secure CRT 4.07 to upload the client public key to the server.
l You can configure at most 20 client pubic keys on an SSH server.
I. Configuring a client public key manually
Follow these steps to configure the client public key manually:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
System-view |
— |
|
Enter public key view |
public-key peer keyname |
— |
|
Enter public key code view |
public-key-code begin |
— |
|
Configure a client public key |
Enter the content of the public key |
Required The content must be a hexadecimal string that is generated randomly by the SSH-supported client software and coded compliant to PKCS. Spaces and carriage returns are allowed between characters. |
|
Return from public key code view to public key view |
public-key-code end |
— When you exit public key code view, the system automatically saves the public key. |
|
Return from public key view to system view |
peer-public-key end |
— |
II. Importing a client public key from a public key file
Follow these steps to import a public key from a public key file:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Import the public key from a public key file |
public-key peer keyname import sshkey filename |
Required |
1.2.6 Configuring an SSH User
This configuration allows you to create an SSH user and specify the service type and authentication method.
Follow these steps to configure an SSH user:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Create an SSH user, and specify the service type and authentication method |
For stelnet users |
ssh user username service-type stelnet authentication-type { password | { any | password-publickey | publickey } assign publickey keyname } |
Required Use either command. |
|
For all users or sftp users |
ssh user username service-type { all | sftp } authentication-type { password | { any | password-publickey | publickey } assign publickey keyname work-directory directory-name } |
||
![]() Caution:
Caution:
l After passing AAA authentication, an AAA user without SSH user account still can log on to the server using password authentication and Stelnet or SFTP service.
l An SSH server supports up to 1024 SSH users.
l The service type of an SSH user can be Stelnet or SFTP. stelnet, or the secure Telnet protocol, refers to the traditional SSH service. For information about stelnet, refer to SSH2.0 Overview. sftp represents the secure FTP protocol. For information about sftp, refer to SFTP Overview.
l For successful login through SFTP, you must set the user service type to sftp or all.
l You can set the service type of an SSH user to stelnet or all if the user does not need SFTP service.
l As SSH1 does not support service type sftp, if the client uses SSH1 to log in to the server, you must set the service type to stelnet or all on the server. Otherwise, the client will fail to log in successfully.
l The working folder of an SFTP user is subject to the user authentication method. For a user using only password authentication, the working folder is the AAA authorized one. For a user using only publickey authentication or using both the publickey and password authentication methods, the working folder is the one set by using the ssh user command.
l The configured authentication method takes effect when the user logs in next time.
& Note:
For users using publickey authentication:
l You must configure on the device the corresponding username and public keys.
l After login, the commands available for a user are determined by the user privilege level, which is configured with the user privilege level command on the user interface. By default, the command privilege level is 0.
For users using password authentication:
l You can configure the accounting information either on the device or on the remote authentication server (such as RADIUS authentication server).
l After login, the commands available to a user are determined by AAA authorization.
1.2.7 Setting the SSH Management Parameters
SSH management includes:
l Enabling the SSH server to be compatible with SSH1
l Setting the server key pair update interval, applicable to users using SSH1 client.
l Setting the SSH user authentication timeout period
l Setting the maximum number of SSH authentication attempts
Setting the above parameters can help avoid malicious guess at and cracking of the keys and usernames, securing your SSH connections.
Follow these steps to set the SSH management parameters:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the SSH server to work with SSH1.x clients |
ssh server compatible-ssh1x enable |
Optional By default, the SSH server can work with SSH1.x clients. |
|
Set the RSA server key pair update interval |
ssh server rekey-interval hours |
Optional 0 by default, that is, the RSA server key pair is not updated. |
|
Set the SSH user authentication timeout period |
ssh server authentication-timeout time-out-value |
Optional 60 seconds by default |
|
Set the maximum number of SSH authentication attempts |
ssh server authentication-retries times |
Optional 3 by default |
& Note:
Authentication will fail if the number of authentication attempts (including both publickey and password authentication) exceeds that specified in the ssh server authentication-retries command.
1.3 Configuring the Device as an SSH Client
1.3.1 SSH Client Configuration Task List
Complete the following tasks to configure an SSH client:
|
Task |
Remarks |
|
Optional |
|
|
Optional |
|
|
Establishing a Connection Between the SSH Client and the Server |
Required |
1.3.2 Specifying a Source IP address/Interface for the SSH client
This configuration task allows you to specify a source IP address or interface for the client to access the SSH server, improving service manageability.
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Specify a source IP address or interface for the SSH client |
Specify a source IPv4 address or interface for the SSH client |
ssh client source { ip ip-address | interface interface-type interface-number } |
Required By default, the address of the interface decided by the routing is used to access the SSH server |
|
Specify a source IPv6 address or interface for the SSH client |
ssh client ipv6 source { ipv6 ipv6-address | interface interface-type interface-number } |
||
1.3.3 Configuring Whether First-time Authentication is Supported
When the device connects to the SSH server as an SSH client, you can configure whether the device supports first-time authentication.
l With first-time authentication, when an SSH client not configured with the server host public key accesses the server for the first time, the user can continue accessing the server, and save the host public key on the client for use in subsequent authentications.
l Without first-time authentication, a client not configured with the server host public key will be denied of access to the server. To access the server, a user must configure in advance the server host public key locally and specify the public key name for authentication.
I. Enable the device to support first-time authentication
Follow these steps to enable the device to support first-time authentication:
|
To do... |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the device to support first-time authentication |
ssh client first-time enable |
Optional By default, first-time authentication is supported on a client. |
II. Disable first-time authentication
For successful authentication of an SSH client not supporting first-time authentication, the server host public key must be configured on the client and the public key name must be specified.
Follow these steps to disable first-time authentication:
|
To do... |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Disable first-time authentication support |
undo ssh client first-time |
Optional By default, first-time authentication is supported on a client. |
|
Configure the server public key |
Refer to 1.2.5 Configuring a Client Public Key |
Required The method of configuring server public key on the client is similar to that of configuring client public key on the server. |
|
Specify the host public key name of the server |
ssh client authentication server server assign publickey keyname |
Required |
1.3.4 Establishing a Connection Between the SSH Client and the Server
Follow these steps to establish the connection between the SSH client and the server:
|
To do... |
Use the command… |
Remarks |
|
|
Establish a connection between the SSH client and the server, and specify the preferred key exchange algorithm, encryption algorithms, and HMAC algorithms for them |
Establish a connection between the SSH client and the IPv4 server, and specify the preferred key exchange algorithm, encryption algorithms, and HMAC algorithms for them |
ssh2 server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Use either command in user view. |
|
Establish a connection between the SSH client and the IPv6 server, and specify the preferred key exchange algorithm, encryption algorithms, and HMAC algorithms for them |
ssh2 ipv6 server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
||
1.4 Displaying and Maintaining SSH
|
To do… |
Use the command… |
Remarks |
|
Display information about the public keys of the local key pair |
display public-key local { dsa | rsa } public |
Available in any view |
|
Display information about the public keys |
display public-key peer [ brief | name publickey-name ] |
Available in any view |
|
Display the source IP address or interface currently set for the SFTP client |
display sftp client source |
Available in any view |
|
Display the source IP address or interface currently set for the SSH client |
display ssh client source |
Available in any view |
|
Display the status information or session information of an SSH server |
display ssh server { status | session } |
Available in any view |
|
Display the mappings between host public keys and SSH servers saved on a client |
display ssh server-info |
Available in any view |
|
Display information about a specified or all SSH users on the SSH server |
display ssh user-information [ username ] |
Available in any view |
1.5 SSH Server Configuration Examples
1.5.1 When Using Password Authentication
I. Network requirements
l As shown in Figure 1-2, a local SSH connection is established between the host (SSH client) and the switch (SSH server) for secure data exchange.
l Password authentication is required.
II. Network diagram

Figure 1-2 Network diagram for SSH server configuration (using password authentication)
III. Configuration procedure
Configure the SSH server
# Generate RSA and DSA key pairs and enable the SSH server.
<Switch> system-view
[Switch] public-key local create rsa
[Switch] public-key local create dsa
[Switch] ssh server enable
# Configure an IP address for VLAN interface 1. This address will serve as the destination for the SSH client in connecting the server.
[Switch] interface vlan-interface 1
[Switch-Vlan-interface1] ip address 192.168.1.40 255.255.255.0
[Switch-Vlan-interface1] quit
# Set the authentication mode for the user interface to AAA.
[Switch] user-interface vty 0 4
[Switch-ui-vty0-4] authentication-mode scheme
# Enable the user interface to support SSH.
[Switch-ui-vty0-4] protocol inbound ssh
[Switch-ui-vty0-4] quit
# Create local user client001, and set the user command privilege level to 3
[Switch] local-user client001
[Switch-luser-client001] password simple aabbcc
[Switch-luser-client001] service-type ssh level 3
[Switch-luser-client001] quit
# Specify the service type for user client001 as Stelnet, and the authentication method as password.
[Switch] ssh user client001 service-type stelnet authentication-type password
Configure the SSH client
& Note:
There are a variety of SSH client software, such as PuTTY, OpenSSH, and so on. The following is an example of configuring SSH client using PuTT v0.58.
# Establish a connection with the SSH server
Launch PuTTY.exe to enter the following interface. In the Host Name (or IP address) text box, enter the IP address of the server (192.168.1.40).
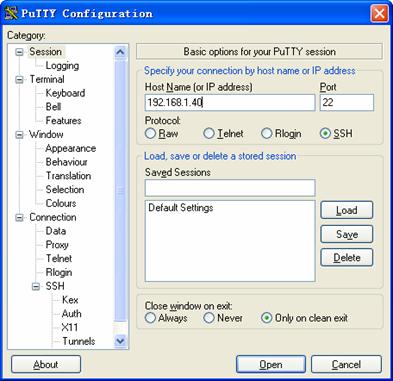
Figure 1-3 SSH client configuration interface
From the window shown in Figure 1-3, click Open. The following SSH client interface appears. If the connection is normal, you will be prompted to enter the username (client001) and password (aabbcc)
1.5.2 When Using Publickey Authentication
I. Network requirements
l As shown in Figure 1-4, a local SSH connection is established between the host (SSH client) and the switch (SSH server) for secure data exchange.
l Publickey authentication is used, the algorithm is RSA.
II. Network diagram

Figure 1-4 Network diagram of SSH server configuration (using publickey authentication)
III. Configuration procedure
1) Configure the SSH server
# Generate RSA and DSA key pairs and enable SSH server.
<Switch> system-view
[Switch] public-key local create rsa
[Switch] public-key local create dsa
[Switch] ssh server enable
# Configure an IP address for VLAN interface 1. This address will serve as the destination for the SSH client in connecting the server.
[Switch] interface vlan-interface 1
[Switch-Vlan-interface1] ip address 192.168.1.40 255.255.255.0
[Switch-Vlan-interface1] quit
# Set the authentication mode for the user interface to AAA.
[Switch] user-interface vty 0 4
[Switch-ui-vty0-4] authentication-mode scheme
# Enable the user interface to support SSH.
[Switch-ui-vty0-4] protocol inbound ssh
# Set the user command privilege level to 3.
[Switch-ui-vty0-4] user privilege level 3
[Switch-ui-vty0-4] quit
& Note:
Before performing the following tasks, you must generate an RSA public key pair (using the client software) on the client, save the key pair in a file named key.pub, and then upload the file to the SSH server through FTP or TFTP. For details, refer to Configuring the SSH Client.
# Import the client’s public key from file “key.pub”.
[Switch] public-key peer Switch001 import sshkey key.pub
# Specify the authentication type for user “client002” as publickey, and assign the public key “Switch001” for the user.
[Switch] ssh user client002 service-type stelnet authentication-type publickey assign publickey Switch001
2) Configure the SSH client
# Generate an RSA key pair
Run PuTTYGen.exe, choose SSH2-(RSA) and click Generate.
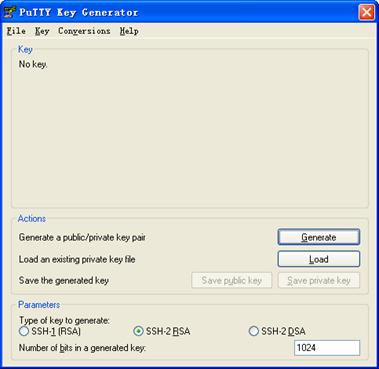
Figure 1-5 Generate a client key pair (1)
While generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar shown in Figure 1-6. Otherwise, the process bar stops moving and the key pair generating process is stopped.
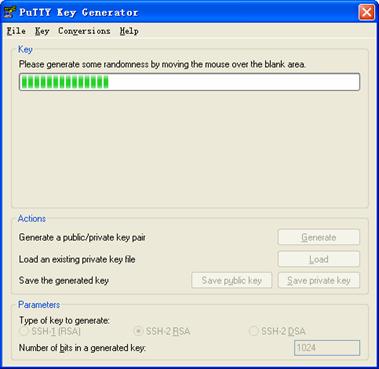
Figure 1-6 Generate a client key pair (2)
After the key pair is generated, click Save public key to save the key in a file by entering a file name (“key.pub” in this case).
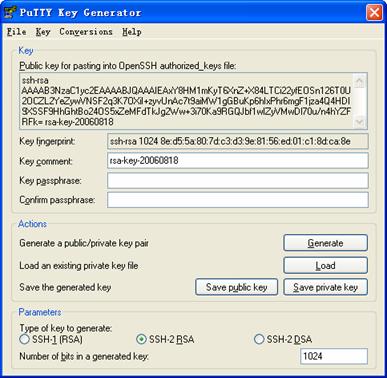
Figure 1-7 Generate a client key pair (3)
Likewise, to save the private key, click Save private key. A warning window pops up to prompt you whether to save the private key without any protection. Click Yes and enter the name of the file for saving the key (“private” in this case).
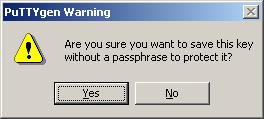
Figure 1-8 Generate a client key pair (4)
& Note:
After generating a key pair on a client, you need to transmit the saved public key file to the server through FTP or TFTP and have the configuration on the server done before continuing configuration of the client.
# Specify the private key file and establish a connection with the SSH server
Launch PuTTY.exe to enter the following interface. In the Host Name (or IP address) text box, enter the IP address of the server (192.168.1.40).
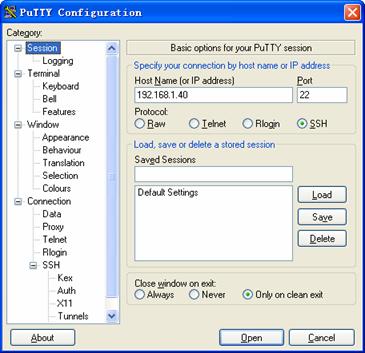
Figure 1-9 SSH client configuration interface (1)
Select Connection/SSH/Auth. The following window appears. Click Browse… to bring up the file selection window, navigate to the private key file and click OK.
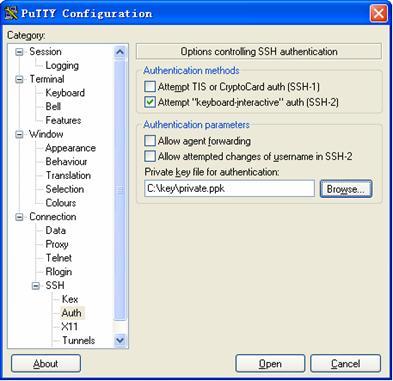
Figure 1-10 SSH client configuration interface (2)
From the window shown in Figure 1-10, click Open. The following SSH client interface appears. If the connection is normal, you will be prompted to enter the username (client002) to enter the configuration interface..
1.6 SSH Client Configuration Examples
1.6.1 When Using Password Authentication
I. Network requirements
l As shown in Figure 1-11, Switch A (the SSH client) needs to log on to Switch B (the SSH server) through the SSH protocol.
l The username of the SSH client is client001 and the password is aabbcc. Password authentication is required.
II. Network diagram

Figure 1-11 Network diagram for SSH client configuration (using password authentication)
III. Configuration procedure
1) Configure the SSH server
# Create an RSA and DSA key pair and enable the SSH server.
<SwitchB> system-view
[SwitchB] public-key local create rsa
[SwitchB] public-key local create dsa
[SwitchB] ssh server enable
# Create an IP address for VLAN interface 1, which the SSH client will use as the destination for SSH connection.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] ip address 10.165.87.136 255.255.255.0
[SwitchB-Vlan-interface1] quit
# Set the authentication mode for the user interface to AAA.
[SwitchB] user-interface vty 0 4
[SwitchB-ui-vty0-4] authentication-mode scheme
# Enable the user interface to support SSH.
[SwitchB-ui-vty0-4] protocol inbound ssh
[SwitchB-ui-vty0-4] quit
# Create local user client001.
[SwitchB] local-user client001
[SwitchB-luser-client001] password simple aabbcc
[SwitchB-luser-client001] service-type ssh level 3
[SwitchB-luser-client001] quit
# Specify the service type for user “client001” as Stelnet, and the authentication method as password.
[SwitchB] ssh user client001 service-type stelnet authentication-type password
2) Configure the SSH client
# Configure an IP address for VLAN interface 1.
<SwitchA> system-view
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] ip address 10.165.87.137 255.255.255.0
[SwitchA-Vlan-interface1] quit
# Disable first-time authentication.
[SwitchA] undo ssh client first-time
# Configure the host public key of the SSH server.
[SwitchA] public-key peer key1
[SwitchA-pkey-public-key] public-key-code begin
[SwitchA-pkey-key-code]308201B73082012C06072A8648CE3804013082011F0281810
0D757262C4584C44C211F18BD96E5F0
[SwitchA-pkey-key-code]61C4F0A423F7FE6B6B85B34CEF72CE14A0D3A5222FE08CECE
65BE6C265854889DC1EDBD13EC8B274
[SwitchA-pkey-key-code]DA9F75BA26CCB987723602787E922BA84421F22C3C89CB9B0
6FD60FE01941DDD77FE6B12893DA76E
[SwitchA-pkey-key-code]EBC1D128D97F0678D7722B5341C8506F358214B16A2FAC4B3
68950387811C7DA33021500C773218C
[SwitchA-pkey-key-code]737EC8EE993B4F2DED30F48EDACE915F0281810082269009E
14EC474BAF2932E69D3B1F18517AD95
[SwitchA-pkey-key-code]94184CCDFCEAE96EC4D5EF93133E84B47093C52B20CD35D02
492B3959EC6499625BC4FA5082E22C5
[SwitchA-pkey-key-code]B374E16DD00132CE71B020217091AC717B612391C76C1FB2E
88317C1BD8171D41ECB83E210C03CC9
[SwitchA-pkey-key-code]B32E810561C21621C73D6DAAC028F4B1585DA7F42519718CC
9B09EEF0381840002818000AF995917
[SwitchA-pkey-key-code]E1E570A3F6B1C2411948B3B4FFA256699B3BF871221CC9C5D
F257523777D033BEE77FC378145F2AD
[SwitchA-pkey-key-code]D716D7DB9FCABB4ADBF6FB4FDB0CA25C761B308EF53009F71
01F7C62621216D5A572C379A32AC290
[SwitchA-pkey-key-code]E55B394A217DA38B65B77F0185C8DB8095522D1EF044B465E
8716261214A5A3B493E866991113B2D
[SwitchA-pkey-key-code]485348
[SwitchA-pkey-key-code] public-key-code end
[SwitchA-pkey-public-key] peer-public-key end
# Specify the host public key for the SSH server (10.165.87.136) as “key1”.
[SwitchA] ssh client authentication server 10.165.87.136 assign publickey key1
[SwitchA] quit
# Establish an SSH connection to server 10.165.87.136.
<SwitchA> ssh2 10.165.87.136
Username: client001
Trying 10.165.87.136
Press CTRL+K to abort
Connected to 10.165.87.136...
Enter password:
**************************************************************************
* Copyright (c) 2004-2007 Hangzhou H3C Tech. Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
**************************************************************************
<SwitchB>
1.6.2 When Using Publickey Authentication
I. Network requirements
l As shown in Figure 1-12, Switch A (the SSH client) needs to log on to Switch B (the SSH server) through SSH protocol.
l Publickey authentication is used; the algorithm is DSA.
II. Network diagram

Figure 1-12 Network diagram of SSH client configuration (using publickey authentication)
III. Configuration procedure
1) Configure the SSH server
# Generate RSA and DSA key pairs and enable SSH server.
<SwitchB> system-view
[SwitchB] public-key local create rsa
[SwitchB] public-key local create dsa
[SwitchB] ssh server enable
# Configure an IP address for VLAN interface 1, which the SSH client will use as the destination for SSH connection.
[SwitchB] interface vlan-interface 1
[SwitchB-Vlan-interface1] ip address 10.165.87.136 255.255.255.0
[SwitchB-Vlan-interface1] quit
# Set the authentication mode for the user interface to AAA.
[SwitchB] user-interface vty 0 4
[SwitchB-ui-vty0-4] authentication-mode scheme
# Enable the user interface to support SSH.
[SwitchB-ui-vty0-4] protocol inbound ssh
# Set the user command privilege level to 3.
[SwitchB-ui-vty0-4] user privilege level 3
[SwitchB-ui-vty0-4] quit
& Note:
Before performing the following tasks, you must generate a DSA public key pair (using the client software) on the client, save the key pair in a file named key.pub, and then upload the file to the SSH server through FTP or TFTP. For details, refer to Configuring the SSH Client.
# Import the remote public key pair from the file “key.pub”.
[SwitchB] public-key peer Switch001 import sshkey key.pub
# Specify the authentication type for user “client002” as publickey, and assign the public key “Switch001” for the user.
[SwitchB] ssh user client002 service-type stelnet authentication-type publickey assign publickey Switch001
2) Configure the SSH client
# Configure an IP address for Vlan interface 1.
<SwitchA> system-view
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] ip address 10.165.87.137 255.255.255.0
[SwitchA-Vlan-interface1] quit
# Generate a DSA key pair.
[SwitchA] public-key local create dsa
# Export the DSA key pair to the file key.pub.
[SwitchA] public-key local export dsa ssh2 key.pub
[SwitchA] quit
& Note:
After generating a key pair on a client, you need to transmit the saved public key file to the server through FTP or TFTP and have the configuration on the server done before continuing configuration of the client.
# Establish an SSH connection to the server (10.165.87.136).
<SwitchA> ssh2 10.165.87.136
Username: client002
Trying 10.165.87.136 ...
Press CTRL+K to abort
Connected to 10.165.87.136 ...
The Server is not authenticated. Continue? [Y/N]:y
Do you want to save the server public key? [Y/N]:n
**************************************************************************
* Copyright (c) 2004-2007 Hangzhou H3C Tech. Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
**************************************************************************
<SwitchB>
Chapter 2 SFTP Service
When configuring SFTP, go to these sections for information you are interested in:
2.1 SFTP Overview
The secure file transfer protocol (SFTP) is a new feature in SSH 2.0.
SFTP uses the SSH connection to provide secure data transfer. The device can serve as the SFTP server, allowing a remote user to login to the SFTP server for secure file management and transfer. The device can also server as an SFTP client, enabling a user to login from the device to a remote device for secure file transfer.
2.2 Configuring an SFTP Server
2.2.1 Configuration Prerequisites
l You have configured the SSH server. For the detailed configuration procedure, refer to Configuring the Device as an SSH Server.
l You have used the ssh user service-type command to set the service type of SSH users to sftp or all. For configuration procedure, refer to Configuring an SSH User.
2.2.2 Enabling the SFTP Server
This configuration task is to enable the SFTP service so that a client can login to the SFTP server through SFTP.
Follow these steps to enable the SFTP server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the SFTP server |
sftp server enable |
Required Disabled by default |
& Note:
When the device functions as the SFTP server, only one client can access the SFTP server at a time. If the SFTP client uses WinSCP, a file on the server cannot be modified directly; it can only be downloaded to a local place, modified, and then uploaded to the server.
2.2.3 Configuring the SFTP Connection Idle Timeout Period
Once the idle period of an SFTP connection exceeds the specified threshold, the system automatically tears the connection down, so that a user cannot occupy a connection for nothing.
Follow these steps to configure the SFTP connection idle timeout period:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the SFTP connection idle timeout period |
sftp server idle-timeout time-out-value |
Required 10 minutes by default |
2.3 Configuring an SFTP Client
2.3.1 Specifying a Source IP Address or Interface for the SFTP Client
You can configure a client to use only a specified source IP address or interface to access the SFTP server, thus enhancing the service manageability.
Follow these steps to specify a source IP address or interface for the SFTP client:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Specify a source IP address or interface for the SFTP client |
Specify a source IPv4 address or interface for the SFTP client |
sftp client source { ip ip-address | interface interface-type interface-number } |
Required Use either command. By default, an SFTP client uses the interface address specified by the route of the device to access the SFTP server. |
|
Specify a source IPv6 address or interface for the SFTP client |
sftp client ipv6 source { ipv6 ipv6-address | interface interface-type interface-number } |
||
2.3.2 Establishing a Connection to the SFTP Server
This configuration task is to enable the SFTP client to establish a connection with the remote SFTP server and enter SFTP client view.
Follow these steps to enable the SFTP client:
|
To do… |
Use the command… |
Remarks |
|
|
Establish a connection to the remote SFTP server and enter SFTP client view |
Establish a connection to the remote IPv4 SFTP server and enter SFTP client view |
sftp server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Use either command in user view. |
|
Establish a connection to the remote IPv6 SFTP server and enter SFTP client view |
sftp ipv6 server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
||
2.3.3 Working with the SFTP Directories
SFTP directory operations include:
l Changing or displaying the current working directory
l Displaying files under a specified directory or the directory information
l Changing the name of a specified directory on the server
l Creating or deleting a directory
Follow these steps to work with the SFTP directories:
|
To do… |
Use the command… |
Remarks |
|
Establish a connection to the remote SFTP server and enter SFTP client view |
sftp [ ipv6 ] server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Execute the command in user view. |
|
Change the working directory of the remote SFTP server |
cd [ remote-path ] |
Optional |
|
Return to the upper-level directory |
cdup |
Optional |
|
Display the current working directory of the remote SFTP server |
pwd |
Optional |
|
Display files under a specified directory |
dir [ -a | -l ] [ remote-path ] |
Optional The dir command functions as the ls command. |
|
ls [ -a | -l ] [ remote-path ] |
||
|
Change the name of a specified directory on the SFTP server |
rename oldname newname |
Optional |
|
Create a new directory on the remote SFTP server |
mkdir remote-path |
Optional |
|
Delete a directory from the SFTP server |
rmdir remote-path&<1-10> |
Optional |
2.3.4 Working with SFTP Files
l Changing the name of a file
l Downloading a file
l Uploading a file
l Displaying a list of the files
l Deleting a file
Follow these steps to work with SFTP files:
|
To do… |
Use the command… |
Remarks |
|
Establish a connection to the remote SFTP server and enter SFTP client view |
sftp [ ipv6 ] server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Execute the command in user view. |
|
Change the name of a specified file on the SFTP server |
rename old-name new-name |
Optional |
|
Download a file from the remote server and save it locally |
get remote-file [ local-file ] |
Optional |
|
Upload a local file to the remote SFTP server |
put local-file [ remote-file ] |
Optional |
|
Display the files under a specified directory |
dir [ -a | -l ] [ remote-path ] |
Optional The dir command functions as the ls command. |
|
ls [ -a | -l ] [ remote-path ] |
||
|
Delete a file from the SFTP server |
delete remote-file&<1-10> |
Optional The delete command functions as the remove command. |
|
remove remote-file&<1-10> |
2.3.5 Displaying Help Information
This configuration task is to display a list of all commands or the help information of an SFTP client command, such as the command format and parameters.
Follow these steps to display a list of all commands or the help information of an SFTP client command:
|
To do… |
Use the command… |
Remarks |
|
Establish a connection to the remote SFTP server and enter SFTP client view |
sftp [ ipv6 ] server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Execute the command in user view. |
|
Display a list of all commands or the help information of an SFTP client command |
help [ all | command-name ] |
Required |
2.3.6 Terminating the Connection to the Remote SFTP Server
Follow these steps to terminate the connection to the remote SFTP server:
|
To do… |
Use the command… |
Remarks |
|
Establish a connection to the remote SFTP server and enter SFTP client view |
sftp [ ipv6 ] server [ port-number ] [ identity-key { dsa | rsa } | prefer-ctos-cipher { aes128 | des } | prefer-ctos-hmac { md5 | md5-96 | sha1 | sha1-96 } | prefer-kex { dh-group-exchange | dh-group1 | dh-group14 } | prefer-stoc-cipher { aes128 | des } | prefer-stoc-hmac { md5 | md5-96 | sha1 | sha1-96 } ] * |
Required Execute the command in user view. |
|
Terminate the connection to the remote SFTP server and return to user view |
bye |
Required. These three commands function in the same way. |
|
exit |
||
|
quit |
2.4 SFTP Configuration Example
I. Network requirements
As shown in Figure 2-1, an SSH connection is established between Switch A and Switch B. Switch A, an SFTP client, uses the username client001 and password aabbcc to login to Switch B for file management and file transfer.
II. Network diagram

Figure 2-1 Network diagram for SFTP configuration
III. Configuration procedure
1) Configure the SFTP server (Switch B)
# Generate RSA and DSA key pairs and enable the SSH server.
<SwitchB> system-view
[SwitchB] public-key local create rsa
[SwitchB] public-key local create dsa
[SwitchB] ssh server enable
# Configure an IP address for VLAN interface 1, which the SSH client uses as the destination for SSH connection.
[SwitchB] interface Vlan-interface 1
[SwitchB-Vlan-interface1] ip address 192.168.0.1 255.255.255.0
[SwitchB-Vlan-interface1] quit
# Set the authentication method on the user interface to AAA.
[SwitchB] user-interface vty 0 4
[SwitchB-ui-vty0-4] authentication-mode scheme
# Set the protocol that a remote user uses to login as SSH.
[SwitchB-ui-vty0-4] protocol inbound ssh
[SwitchB-ui-vty0-4] quit
# Create local user client001.
[SwitchB] local-user client001
[SwitchB-luser-client001] password simple aabbcc
[SwitchB-luser-client001] service-type ssh
[SwitchB-luser-client001] quit
# Set the SSH authentication method to password, service type to SFTP.
[SwitchB] ssh user client001 service-type sftp authentication-type password
& Note:
If you set the SSH authentication method to publickey, you need to configure the host public key of SwitchA. For the specific configuration, refer to When Using Publickey Authentication.
# Enable the SFTP server.
[SwitchB] sftp server enable
2) Configure the SFTP client (Switch A)
# Configure an IP address for VLAN interface 1.
<SwitchA> system-view
[SwitchA] interface vlan-interface 1
[SwitchA-Vlan-interface1] ip address 192.168.0.2 255.255.255.0
[SwitchA-Vlan-interface1] quit
[SwitchA] quit
# Establish a connection to the remote SFTP server and enter SFTP client view.
<SwitchA> sftp 192.168.0.1
Input Username: client001
Trying 192.168.0.1 ...
Press CTRL+K to abort
Connected to 192.168.0.1 ...
The Server is not authenticated. Continue? [Y/N]:y
Do you want to save the server public key? [Y/N]:y
Enter password:
sftp-client>
# Display files under the current directory of the server, delete the file named “z”, and check if the file is deleted successfully.
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
-rwxrwxrwx 1 noone nogroup 0 Sep 01 08:00 z
sftp-client> delete z
The following files will be deleted:
/z
Are you sure to delete it? [Y/N]:y
This operation may take a long time.Please wait...
File successfully Removed
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
# Add a directory named “new1” and check if it is created successfully.
sftp-client> mkdir new1
New directory created
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:30 new1
# Rename directory “new1” to “new2” and check if the directory is renamed successfully.
sftp-client> rename new1 new2
File successfully renamed
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
-rwxrwxrwx 1 noone nogroup 225 Sep 01 06:55 pub
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2
# Download the file “pubkey2” from the server and change the name to “public”.
sftp-client> get pubkey2 public
Remote file:/pubkey2 ---> Local file: public
Downloading file successfully ended
# Upload the local file “pu” to the server, save it as “puk”, and check if the file is uploaded successfully.
sftp-client> put pu puk
Local file:pu ---> Remote file: /puk
Uploading file successfully ended
sftp-client> dir
-rwxrwxrwx 1 noone nogroup 1759 Aug 23 06:52 config.cfg
-rwxrwxrwx 1 noone nogroup 225 Aug 24 08:01 pubkey2
-rwxrwxrwx 1 noone nogroup 283 Aug 24 07:39 pubkey1
drwxrwxrwx 1 noone nogroup 0 Sep 01 06:22 new
drwxrwxrwx 1 noone nogroup 0 Sep 02 06:33 new2
-rwxrwxrwx 1 noone nogroup 283 Sep 02 06:35 pub
-rwxrwxrwx 1 noone nogroup 283 Sep 02 06:36 puk
sftp-client>
# Terminate the connection to the remote SFTP server.
sftp-client> quit
Bye
Connection closed.
<SwitchA>
