- Table of Contents
-
- 17-Network Management and Monitoring Configuration Guide
- 00-Preface
- 01-Information center configuration
- 02-Flow log configuration
- 03-Fast log output configuration
- 04-NetStream configuration
- 05-Cloud connection configuration
- 06-Mirroring configuration
- 07-Packet capture configuration
- 08-NQA configuration
- 09-Track configuration
- 10-BFD configuration
- 11-Monitor Link configuration
- 12-Smart Link configuration
- 13-Interface backup configuration
- 14-Interface collaboration configuration
- 15-System maintenance and debugging configuration
- 16-NTP configuration
- 17-EAA configuration
- 18-Process monitoring and maintenance configuration
- 19-NETCONF configuration
- 20-CWMP configuration
- 21-SNMP configuration
- 22-RMON configuration
- 23-Event MIB configuration
- 24-Process placement configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-Flow log configuration | 255.96 KB |
Contents
Specifying a flow log export destination
Restrictions and guidelines for flow log export destination configuration
Specifying a log host as the flow log export destination
Specifying the information center as the flow log export destination
Configuring the flow log version
Specifying a source IP address for flow log packets
Configuring the timestamp of flow log entries
Enabling load balancing for flow log entries
Configuring flow log host groups
Prerequisites for log host group configuration
Configuring an IPv4 flow log host group
Configuring an IPv6 flow log host group
Display and maintenance commands for flow log
NAT flow log configuration examples
Example: Configuring NAT flow log export
Example: Configuring session flow log export
Example: Configuring NAT flow log export to a flow log host group
AFT IPv6 to IPv4 flow log fields
AFT IPv4 to IPv6 flow log fields
Configuring flow log
About flow log
Flow log records session information based on flows.
A flow log entry might contain the following information about a flow:
· Network access quintuple information (source IP address, destination IP address, source port, destination port, and protocol number).
· Statistics about sent and received packets.
· Flow-based link selection information.
Flow log export
You can export flow log entries in the following methods:
· Export flow log entries to log hosts. Flow log entries are sent as binary characters in UDP. One UDP packet can contain multiple log entries.
· Export flow log entries to the information center. Flow log entries are converted to syslog entries in ASCII format, with the informational severity level. The information center specifies the output destinations for the log entries. For more information about the information center, see "Configuring the information center."
Log entries in ASCII format are human readable. However, the log data volume is higher in ASCII format than in binary format. It's recommended to export flow log entries in binary format to log hosts if the log data volume is large.
Flow log packet
The flow log data (including the log header and log body) is carried in the body of a UDP packet. The log header contains the common fields and the log body contains the service-specific log information. The log body of a flow log packet can contain one or multiple log entries of the same type.
Figure 1 Flow log packet
Flow log supports multiple service modules. The log body fields vary with the log type or log version. For more information about flow log fields, see "Appendix A Flow log fields."
Flow log tasks at a glance
To configure flow log, perform the following tasks:
2. Specifying a flow log export destination
Choose one of the following tasks:
¡ Specifying a log host as the flow log export destination
¡ Specifying the information center as the flow log export destination
3. (Optional.) Configuring the flow log version
4. (Optional.) Specifying a source IP address for flow log packets
5. (Optional.) Configuring the timestamp of flow log entries
6. (Optional.) Enabling load balancing for flow log entries
7. (Optional.) Configuring flow log host groups
Enabling flow log
Before you configure the flow log feature, complete the following tasks to enable flow log output for modules:
· Enable NAT flow log output by using the nat log enable command. For more information about the NAT logging commands, see NAT Command Reference.
· Enable AFT flow log output by using the aft log enable command. For more information, see AFT commands in Layer 3—IP Services Command Reference.
· Enable load balancing NAT flow log output by using the loadbalance log enable nat command. For more information, see load balancing commands in Load Balancing Command Reference.
Specifying a flow log export destination
Restrictions and guidelines for flow log export destination configuration
You can export flow log entries to a log host or to the information center, but not both. If you configure both methods, the system exports flow log entries to the information center.
flow log entries exported to the information center has the informational severity level.
Specifying a log host as the flow log export destination
1. Enter system view.
system-view
2. Specify a log host as the destination for flow log export.
userlog flow export [ vpn-instance vpn-instance-name ] host { hostname | ipv4-address | ipv6 ipv6-address } port udp-port
By default, no log hosts are specified.
You can specify multiple log hosts.
Specifying the information center as the flow log export destination
1. Enter system view.
system-view
2. Specify the information center as the destination for flow log export.
userlog flow syslog
By default, flow log entries are not exported to the information center.
|
CAUTION: The device might generate a lot of session logs in a short time. If the session logs are exported to the information center for processing, the information center might consume too much performance, affecting normal operations of the device. |
Configuring the flow log version
Restrictions and guidelines
Make sure the specified flow log version is supported on the log host.
If you configure the flow log version multiple times, the most recent configuration takes effect.
Procedure
1. Enter system view.
system-view
2. Configure the flow log version.
userlog flow export version version-number
The default flow log version is 1.0.
Specifying a source IP address for flow log packets
About this task
By default, the source IP address for flow log packets is the IP address of their outgoing interface. For the log hosts to filter log entries by log sender, specify a source IP address for all flow log packets.
Restrictions and guidelines
As a best practice, use a Loopback interface's address as the source IP address for flow log packets. A Loopback interface is always up. The setting avoids export failure on interfaces that might go down.
Procedure
1. Enter system view.
system-view
2. Specify a source IP address for flow log packets.
userlog flow export source-ip { ipv4-address | ipv6 ipv6-address }
By default, the source IP address for flow log packets is the IP address of their outgoing interface.
Configuring the timestamp of flow log entries
About this task
The device uses either the local time or the UTC time in the timestamp of flow logs.
· UTC time—Standard Greenwich Mean Time (GMT).
· Local time—Standard GMT plus or minus the time zone offset.
The time zone offset can be configured by using the clock timezone command. For more information, see device management in Fundamentals Command Reference.
Procedure
1. Enter system view.
system-view
2. Configure the device to use the local time in the flow log timestamp.
userlog flow export timestamp localtime
By default, the UTC time is used in the flow log timestamp.
Enabling load balancing for flow log entries
About this task
By default, the device sends a copy of each flow log entry to all configured log hosts. When one log host fails, other log hosts still have complete flow log entries.
In load balancing mode, flow log entries are distributed among log hosts based on the source IP addresses (before NAT) that are recorded in the entries. The flow log entries generated for the same source IP address are sent to the same log host.
Restrictions and guidelines
In load balancing mode, flow log entries are load balanced among all configured log hosts, regardless of whether the log hosts are reachable. If a log host is unreachable, the flow log entries sent to it will be lost.
Procedure
1. Enter system view.
system-view
2. Enable load balancing for flow log entries.
userlog flow export load-balancing
By default, load balancing is disabled.
Configuring flow log host groups
About flow log host group
By default, the device sends a copy of each flow log entry to all available log hosts. To filter logs and reduce the log sending and processing workload of the device, configure the flow log host group feature.
The flow log host group feature allows you to classify flow log hosts into groups and specify an ACL for each group. A flow log matches a log host group if it matches the group's ACL, and it is sent only to the log hosts in the matching group.
If a flow log matches multiple log host groups, the device sends the log to the group that comes first in alphabetical order of the matching group names.
If a flow log does not match any log host groups, the device ignores the log host group configuration and sends the log to all configured log hosts.
If load balancing is enabled, flow logs sent to a log host group will be load-shared among the log hosts in the group. flow logs generated for the same source IP address are sent to the same log host.
Prerequisites for log host group configuration
Before you configure flow log host groups, complete the following tasks:
· Configure the ACLs to be used by the flow log host groups.
· Use the userlog flow export host command to configure the log hosts to be assigned to the flow log host groups.
Configuring an IPv4 flow log host group
1. Enter system view.
system-view
2. Create an IPv4 flow log host group and enter its view.
userlog host-group host-group-name acl { name acl-name | number acl-number }
By default, no IPv4 flow log host groups exist.
3. Assign an IPv4 log host to the flow log host group.
userlog host-group [ vpn-instance vpn-instance-name ] host flow { hostname | ipv4-address }
By default, an IPv4 flow log host group does not contain any log hosts.
Configuring an IPv6 flow log host group
1. Enter system view.
system-view
2. Create an IPv6 flow log host group and enter its view.
userlog host-group ipv6 host-group-name acl { name acl-name | number acl-number }
By default, no IPv6 flow log host groups exist.
3. Assign an IPv6 log host to the flow log host group.
userlog host-group [ vpn-instance vpn-instance-name ] host flow ipv6 { hostname | ipv6-address }
By default, an IPv6 flow log host group does not contain any log hosts.
Display and maintenance commands for flow log
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display flow log configuration and statistics. |
display userlog export |
|
Display flow log host group information. |
display userlog host-group [ ipv6 ] [ host-group-name ] |
|
Clear flow log statistics. |
reset userlog flow export |
NAT flow log configuration examples
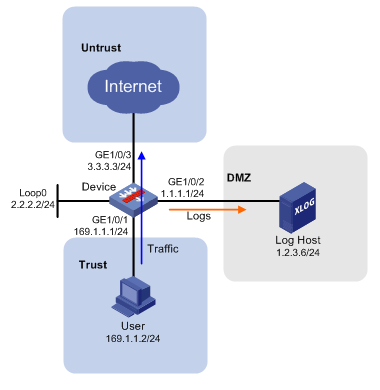
Example: Configuring NAT flow log export
Network configuration
As shown in Figure 2, configure flow log on the device to send flow log entries generated for the user to the log host.
Procedure
1. Assign IP addresses to interfaces.
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface loopback 0
[Device-LoopBack0] ip address 2.2.2.2 255.255.255.0
[Device-LoopBack0] quit
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 169.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hops in the routes are 1.1.1.2 and 3.3.3.1, respectively.
[Device] ip route-static 1.2.3.0 24 1.1.1.2
[Device] ip route-static 0.0.0.0 0 3.3.3.1
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/2
[Device-security-zone-DMZ] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/3
[Device-security-zone-Untrust] quit
4. Configure a security policy:
# Configure a rule named loglocalout to allow the device to send log packets to the log host.
[Device] security-policy ip
[Device-security-policy-ip] rule name loglocalout
[Device-security-policy-ip-1-loglocalout] source-zone local
[Device-security-policy-ip-1-loglocalout] destination-zone dmz
[Device-security-policy-ip-1-loglocalout] source-ip-host 2.2.2.2
[Device-security-policy-ip-1-loglocalout] destination-ip-host 1.2.3.6
[Device-security-policy-ip-1-loglocalout] action pass
[Device-security-policy-ip-1-loglocalout] quit
# Configure a rule named trust-untrust to all the user to access the Internet.
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-3-trust-untrust] source-zone trust
[Device-security-policy-ip-3-trust-untrust] destination-zone untrust
[Device-security-policy-ip-3-trust-untrust] source-ip-subnet 169.1.1.0 24
[Device-security-policy-ip-3-trust-untrust] action pass
[Device-security-policy-ip-3-trust-untrust] quit
[Device-security-policy-ip] quit
5. Configure flow log settings:
# Enable NAT logging for session establishment events, session removal events, and active flows. Set the flow log version to 3.0.
[Device] nat log enable
[Device] nat log flow-begin
[Device] nat log flow-end
[Device] nat log flow-active 10
[Device] userlog flow export version 3
# Specify the log host at 1.2.3.6 as the destination for flow log export, set the UDP port number to 2000, and specify 2.2.2.2 as the source IP address for flow log packets.
[Device] userlog flow export host 1.2.3.6 port 2000
[Device] userlog flow export source-ip 2.2.2.2
Verifying the configuration
# Display the flow log configuration and statistics.
[Device] display userlog export
Flow:
Export flow log as UDP Packet.
Version: 3.0
Source ipv4 address: 2.2.2.2
Log load balance function: Disabled
Local time stamp: Disabled
Number of log hosts: 1
Log host 1:
Host/Port: 1.2.3.6/2000
Total logs/UDP packets exported: 112/87
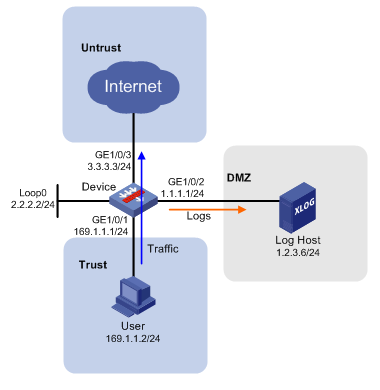
Example: Configuring session flow log export
Network configuration
As shown in Figure 3, configure flow log on the device to send session flow log entries generated for the user to the log host.
Procedure
1. Assign IP addresses to interfaces.
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface loopback 0
[Device-LoopBack0] ip address 2.2.2.2 255.255.255.0
[Device-LoopBack0] quit
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 169.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hops in the routes are 1.1.1.2 and 3.3.3.1, respectively.
[Device] ip route-static 1.2.3.0 24 1.1.1.2
[Device] ip route-static 0.0.0.0 0 3.3.3.1
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/2
[Device-security-zone-DMZ] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/3
[Device-security-zone-Untrust] quit
4. Configure a security policy.
# Configure a rule named loglocalout to allow the device to send log packets to the log host.
[Device] security-policy ip
[Device-security-policy-ip] rule name loglocalout
[Device-security-policy-ip-1-loglocalout] source-zone local
[Device-security-policy-ip-1-loglocalout] destination-zone dmz
[Device-security-policy-ip-1-loglocalout] source-ip-host 2.2.2.2
[Device-security-policy-ip-1-loglocalout] destination-ip-host 1.2.3.6
[Device-security-policy-ip-1-loglocalout] action pass
[Device-security-policy-ip-1-loglocalout] quit
# Configure a rule named trust-untrust to allow the user to access the Internet.
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-3-trust-untrust] source-zone trust
[Device-security-policy-ip-3-trust-untrust] destination-zone untrust
[Device-security-policy-ip-3-trust-untrust] source-ip-subnet 169.1.1.0 24
[Device-security-policy-ip-3-trust-untrust] action pass
[Device-security-policy-ip-3-trust-untrust] quit
[Device-security-policy-ip] quit
5. Configure flow log settings:
# Enable NAT logging for session establishment events and session removal events. Set the flow log version to 3.0.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] session log enable ipv4 inbound
[Device] session log flow-begin
[Device] session log flow-end
[Device] userlog flow export version 3
# Specify the log host at 1.2.3.6 as the destination for flow log export, set the UDP port number to 2000, and specify 2.2.2.2 as the source IP address for flow log packets.
[Device] userlog flow export host 1.2.3.6 port 2000
[Device] userlog flow export source-ip 2.2.2.2
Verifying the configuration
# Display the flow log configuration and statistics.
[Device] display userlog export
Flow:
Export flow log as UDP Packet.
Version: 3.0
Source ipv4 address: 2.2.2.2
Log load balance function: Disabled
Local time stamp: Disabled
Number of log hosts: 1
Log host 1:
Host/Port: 1.2.3.6/2000
Total logs/UDP packets exported: 112/87
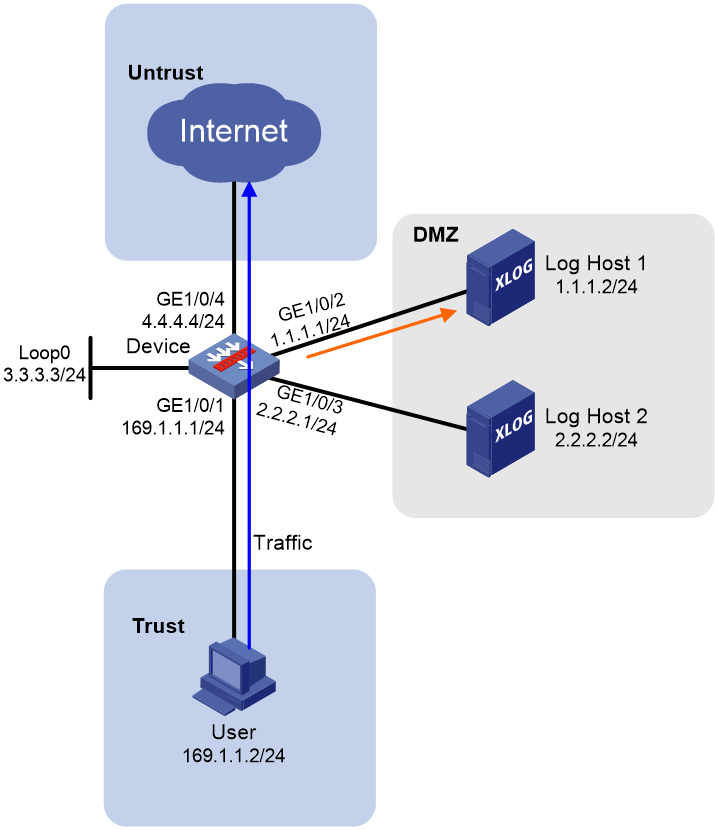
Example: Configuring NAT flow log export to a flow log host group
Network configuration
As shown in Figure 4, configure a flow log host group on the device to send flow log entries generated for the user only to Log Host 1.
Procedure
1. Assign IP addresses to interfaces.
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface loopback 0
[Device-LoopBack0] ip address 3.3.3.3 255.255.255.0
[Device-LoopBack0] quit
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet 1/0/1] ip address 169.1.1.1 255.255.255.0
[Device-GigabitEthernet 1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route, and the next hop in the routes is 4.4.4.1.
[Device] ip route-static 0.0.0.0 0 4.4.4.1
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/2
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/4
[Device-security-zone-Untrust] quit
4. Configure a security policy.
# Configure a rule named loglocalout for the device to send log packets to the log hosts.
[Device] security-policy ip
[Device-security-policy-ip] rule name loglocalout
[Device-security-policy-ip-1-loglocalout] source-zone local
[Device-security-policy-ip-1-loglocalout] destination-zone dmz
[Device-security-policy-ip-1-loglocalout] source-ip-host 3.3.3.3
[Device-security-policy-ip-1-loglocalout] destination-ip-host 1.1.1.2
[Device-security-policy-ip-1-loglocalout] destination-ip-host 2.2.2.2
[Device-security-policy-ip-1-loglocalout] action pass
[Device-security-policy-ip-1-loglocalout] quit
# Configure a rule named trust-untrust for the user to access the Internet.
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-3-trust-untrust] source-zone trust
[Device-security-policy-ip-3-trust-untrust] destination-zone untrust
[Device-security-policy-ip-3-trust-untrust] source-ip-subnet 169.1.1.0 24
[Device-security-policy-ip-3-trust-untrust] action pass
[Device-security-policy-ip-3-trust-untrust] quit
[Device-security-policy-ip] quit
5. Configure flow log settings.
# Enable NAT logging for session establishment events, session removal events, and active flows.
[Device] nat log enable
[Device] nat log flow-begin
[Device] nat log flow-end
[Device] nat log flow-active 10
# Specify the log hosts as the destinations for flow log export, set the UDP port number to 2000. Specify 3.3.3.3 as the source IP address for flow log packets.
[Device] userlog flow export host 1.1.1.2 port 2000
[Device] userlog flow export host 2.2.2.2 port 2000
[Device] userlog flow export source-ip 3.3.3.3
# Create ACL 2000 to match packets sent by the user.
[Device] acl basic 2000
[Device-acl-ipv4-basic-2000] rule permit source 169.1.1.2 0.0.0.0
[Device-acl-ipv4-basic-2000] quit
# Create an IPv4 flow log host group named test and specify ACL 2000 for it. Assign Log Host 1 to flow log host group test.
[Device] userlog host-group test acl number 2000
[Device-userlog-host-group-test] userlog host-group host flow 1.1.1.2
[Device-userlog-host-group-test] quit
Verifying the configuration
# Display information about flow log host group test.
[Device] display userlog host-group test
Userlog host-group test:
ACL number: 2000
Flow log host numbers: 1
Log host 1:
Host/port: 1.1.1.2/2000
# After the user comes online, display flow log export statistics.
[Device] display userlog export
Flow:
Export flow log as UDP Packet.
Version: 1.0
Source ipv4 address: 3.3.3.3
Log load balance function: Disabled
Local time stamp: Disabled
Number of log hosts: 2
Log host 1:
Host/Port: 1.1.1.2/2000
Total logs/UDP packets exported: 13/13
Log host 2:
Host/Port: 2.2.2.2/2000
Total logs/UDP packets exported: 0/0
Appendix
Appendix A Flow log fields
The fields described in this section are those in the original log data sent to the log host. The log format might differ from the actual log format displayed on the log host. The displayed log format depends on the log analysis tool.
Log header fields
Table 1 shows the log header fields, and the corresponding length and description.
Table 1 Fields in a log header
|
Field |
Length (Bytes) |
Description |
|
Version |
1 |
Version number of the log packet: · 1—Version 1.0. · 3—Version 3.0. · 5—Version 5.0. |
|
LogType |
1 |
Log type: · 4—NAT flow log. · 5—NAT66 flow log. · 7—AFT IPv6 to IPv4 log. · 8—AFT IPv4 to IPv6 log. · 11—LB NAT64 flow log. · 12—LB NAT46 flow log. · 13—LB NAT44 flow log. · 14—LB NAT66 flow log. · 15—RIR flow log. |
|
Count |
2 |
Number of flows recorded in the current packet. The value range is 1 to 100. |
|
Second |
4 |
Number of seconds from 1970-01-01 00:00:00 to the time when the packet was generated. |
|
FlowSequence |
4 |
Sequence number of the log packet, which equals to the count of log packets of all log types and versions. |
|
Chassis |
2 |
Number of chassis sent the log packet. |
|
Slot |
1 |
Number of slot sent the log packet. |
|
Cpu |
1 |
Number of CPU sent the log packet. |
NAT flow log fields
NAT flow log has three versions: 1.0, 3.0, and 5.0. Table 2, Table 3, and Table 4 show the fields available in the versions.
Table 2 NAT flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
SrcIP |
4 |
Source IP address before NAT. |
|
DestIP |
4 |
Destination IP address before NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 if the Operator field is 6. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
Reserved |
2 |
Reserved for future use. |
Table 3 NAT flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol number. |
|
Operator |
1 |
Reasons why a NAT flow log was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
TosIPv4 |
1 |
ToS field of the IPv4 packet. |
|
SourceIP |
4 |
Source IP address before NAT. |
|
SrcNatIP |
4 |
Source IP address after NAT. |
|
DestIP |
4 |
Destination IP address before NAT. |
|
DestNatIP |
4 |
Destination IP address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
1 |
ID of the source VPN instance. |
|
OutVPNID |
1 |
ID of the destination VPN instance. |
|
vSystemID |
2 |
vSystem ID. |
|
AppID |
4 |
Application protocol ID. |
|
Reserved3 |
4 |
Reserved field. |
Table 4 NAT flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a flow log was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
TosIPv4 |
1 |
ToS field of the IPv4 packet. |
|
SourceIP |
4 |
Source IP address before NAT. |
|
SrcNatIP |
4 |
Source IP address after NAT. |
|
DestIP |
4 |
Destination IP address before NAT. |
|
DestNatIP |
4 |
Destination IP address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. |
|
EndTime |
4 |
End time of the flow, in seconds. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
AppID |
4 |
Application protocol ID. |
|
UserName |
56 |
Username. |
|
vSystemID |
2 |
vSystem ID. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field |
|
Reserved3 |
4 |
Reserved field |
NAT66 flow log fields
NAT66 flow log has three versions: 1.0, 3.0, and 5.0. Table 5, Table 6, and Table 7 show the fields available in the versions.
Table 5 NAT66 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 if the Operator field is 6. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
Reserved |
2 |
Reserved for future use. |
Table 6 NAT66 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol number. |
|
Operator |
1 |
Reasons why a NAT flow log was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
Traffic class |
1 |
Traffic Class field of the IPv6 packet. |
|
SourceIP |
16 |
Source IPv6 address before NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
AppID |
4 |
Application protocol ID. |
Table 7 NAT66 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a flow log was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
Traffic class |
1 |
Traffic Class field of the IPv6 packet. |
|
SourceIP |
16 |
Source IPv6 address before NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
AppID |
4 |
Application protocol ID. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field |
|
Reserved3 |
4 |
Reserved field |
AFT IPv6 to IPv4 flow log fields
AFT IPv6 to IPv4 flow log has three versions: 1.0, 3.0, and 5.0. Table 8, Table 9, and Table 10 show the fields available in the versions.
Table 8 AFT IPv6 to IPv4 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
Traffic class |
1 |
Traffic Class field of the IPv6 packet. |
|
SourceIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved |
4 |
Reserved field. |
Table 9 AFT IPv6 to IPv4 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
Traffic class |
1 |
Traffic Class field of the IPv6 packet. |
|
SourceIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved |
4 |
Reserved field. |
Table 10 AFT IPv6 to IPv4 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
Traffic class |
1 |
Traffic Class field of the IPv6 packet. |
|
SourceIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |
AFT IPv4 to IPv6 flow log fields
AFT IPv4 to IPv6 flow log has three versions: 1.0, 3.0, and 5.0. Table 11, Table 12, and Table 13 show the fields available in the versions.
Table 11 AFT IPv4 to IPv6 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
TosIPv4 |
1 |
ToS field of the IPv4 packet. |
|
SourceIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved |
4 |
Reserved field. |
Table 12 AFT IPv4 to IPv6 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
TosIPv4 |
1 |
ToS field of the IPv4 packet. |
|
SourceIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved |
4 |
Reserved field. |
Table 13 AFT IPv4 to IPv6 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
Protocol |
1 |
Protocol type carried by IP. |
|
Operator |
1 |
Reasons why a NAT flow log entry was generated: · 0—Reserved. · 1—Flow was ended normally. · 2—Flow was aged out because of aging timer expiration. · 3—Flow was aged out because of configuration change or manual deletion. · 4—Flow was aged out because of insufficient resources. · 5—Reserved. · 6—Regular connectivity check record for the active flow. · 7—Flow was deleted because a new flow was created when the flow table was full. · 8—Flow was created. · FE—Other reasons. · 10-FE-1—Reserved for future use. |
|
IPVersion |
1 |
IP packet version. |
|
TosIPv4 |
1 |
ToS field of the IPv4 packet. |
|
SourceIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
StartTime |
4 |
Start time of the flow, in seconds. The value is counted from 1970/1/1 0:0. |
|
EndTime |
4 |
End time of the flow, in seconds. The value is counted from 1970/1/1 0:0. This field is 0 when the Operator field is 6. |
|
InTotalPkg |
4 |
Number of packets received for the session. |
|
InTotalByte |
4 |
Number of bytes received for the session. |
|
OutTotalPkg |
4 |
Number of packets sent for the session. |
|
OutTotalByte |
4 |
Number of bytes sent for the session. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |
LB NAT64 flow log fields
LB NAT64 flow log has three versions: 1.0, 3.0, and 5.0. Table 14, Table 15, and Table 16 show the fields available in the versions.
Table 14 LB NAT64 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 15 LB NAT64 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 16 LB NAT64 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |
LB NAT46 flow log fields
LB NAT46 flow log has three versions: 1.0, 3.0, and 5.0. Table 17, Table 18, and Table 19 show the fields available in the versions.
Table 17 LB NAT46 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 18 LB NAT46 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 19 LB NAT46 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |
LB NAT44 flow log fields
LB NAT44 flow log has three versions: 1.0, 3.0, and 5.0. Table 20, Table 21, and Table 22 show the fields available in the versions.
Table 20 LB NAT44 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 21 LB NAT44 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 22 LB NAT44 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
4 |
Source IPv4 address before NAT. |
|
SrcNatIP |
4 |
Source IPv4 address after NAT. |
|
DestIP |
4 |
Destination IPv4 address before NAT. |
|
DestNatIP |
4 |
Destination IPv4 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |
LB NAT66 flow log fields
LB NAT66 flow log has three versions: 1.0, 3.0, and 5.0. Table 23, Table 24, and Table 25 show the fields available in the versions.
Table 23 LB NAT66 flow log 1.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 24 LB NAT66 flow log 3.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
Reserved2 |
4 |
Reserved field. |
Table 25 LB NAT66 flow log 5.0 fields
|
Field |
Length (Bytes) |
Description |
|
LBVersion |
1 |
Version number for the LB log. |
|
Protocol |
1 |
Protocol type carried by IP. |
|
IPVersion |
1 |
IP packet version. |
|
Reserved1 |
1 |
Reserved field. |
|
SrcIP |
16 |
Source IPv6 address before NAT. |
|
SrcNatIP |
16 |
Source IPv6 address after NAT. |
|
DestIP |
16 |
Destination IPv6 address before NAT. |
|
DestNatIP |
16 |
Destination IPv6 address after NAT. |
|
SrcPort |
2 |
Source TCP/UDP port number before NAT. |
|
SrcNatPort |
2 |
Source TCP/UDP port number after NAT. |
|
DestPort |
2 |
Destination TCP/UDP port number before NAT. |
|
DestNatPort |
2 |
Destination TCP/UDP port number after NAT. |
|
InVPNID |
2 |
ID of the source VPN instance. |
|
OutVPNID |
2 |
ID of the destination VPN instance. |
|
ContextID |
4 |
ID of the context for the session. |
|
UserName |
56 |
Username. |
|
Reserved1 |
4 |
Reserved field. |
|
Reserved2 |
4 |
Reserved field. |
|
Reserved3 |
4 |
Reserved field. |