- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-Proxy policy configuration
- 10-WAF configuration
- 11-IP reputation configuration
- 12-APT defense configuration
- 13-Domain reputation configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-File filtering configuration | 99.20 KB |
Contents
File filtering tasks at a glance
Configuring a file filtering policy
Setting the action for packets with files carrying false extensions
Applying a file filtering policy to a DPI application profile
Activating file filtering policy and rule settings
Applying a DPI application profile to a security policy rule
File filtering configuration examples
Example: Using a file filtering policy in a security policy
Configuring file filtering
About file filtering
The file filtering feature filters files based on file extensions. You can configure file filtering to perform actions on files based on the file extensions.
File filtering supports filtering packets of the following protocols:
· HTTP.
· FTP.
· SMTP.
· IMAP.
· NFS.
· POP3.
· RTMP.
· SMB.
Basic concepts
File type match pattern
A file type match pattern identifies a type of files by file extension.
File type group
A file type group can contain a maximum of 32 file type match patterns. A file matches a file type group if it matches a pattern in the group.
File filtering rule
A file filtering rule contains a set of filtering criteria for matching files, including file type group, traffic direction, and application layer protocol. You can specify the actions to take on packets matching a file filtering rule. Supported actions include drop, permit, and logging. A file must match all the filtering criteria for the actions specified for the rule to apply.
File filtering mechanism
File filtering takes effect after you apply a file filtering policy to a DPI application profile and use the DPI application profile in a security policy rule.
Upon receiving a packet of a protocol that file filtering supports, the device performs the following operations:
1. Compares the packet with the security policy rules.
If the packet matches a rule that is associated with a file filtering policy (through a DPI application profile), the device submits the packet to the DPI engine for file filtering processing.
For more information about security policies, see Security Configuration Guide.
2. Extracts and records the file extension in the packet.
3. Identifies the real file extension and compares it with the recorded file extension:
¡ If the two file extensions match or if the real file extension cannot be identified, the device proceeds to step 4.
¡ If the two file extensions do not match, the device checks the action specified for packets with files carrying false extensions.
- If the Drop action is specified, the device drops the packet directly.
- If the Permit action is specified, the device proceeds to step 4 to perform file filtering inspection based on the real file extension.
4. Determines the actions to take on the packet by comparing the packet attributes (file extension, application layer application, and traffic direction) with the file filtering rules in the file filtering policy:
¡ If the packet does not match any file filtering rules in the policy, the device permits the packet to pass.
¡ If the packet matches only one rule, the device takes the actions specified for the rule.
¡ If the packet matches multiple rules, the device determines the actions as follows:
- If the matching rules have both the permit and drop actions, the device takes the drop action.
- The logging action is taken if it is specified for any of the matching rules.
File filtering tasks at a glance
To configure data filtering, perform the following tasks:
1. Configuring a file type group
2. Configuring a file filtering policy
3. Setting the action for packets with files carrying false extensions
4. Applying a file filtering policy to a DPI application profile
5. (Optional.) Activating file filtering policy and rule settings
6. Applying a DPI application profile to a security policy rule
Configuring a file type group
About this task
A file type group is a group of file type match patterns. A file type match pattern is a text or regular expression string that matches files by file extension.
A file matches a file type group if it matches a pattern in the group.
Procedure
1. Enter system view.
system-view
2. Create a file type group and enter its view.
file-filter policy policy-name
3. (Optional.) Configure a description for the file type group.
description string
By default, a file type group does not have a description.
4. Configure a file type match pattern.
pattern pattern-name text pattern-string
By default, a file type group does not contain any file type match patterns.
Configuring a file filtering policy
About this task
A file filtering policy can contain a maximum of 32 file filtering rules. Each rule defines a set of filtering criteria and the actions for matching packets. The filtering criteria include:
· One file type group.
· One or more application layer protocols.
· Traffic direction.
Restrictions and guidelines
File filtering rules applied to the NFS protocol take effect only on NFSv3 traffic.
File filtering rules applied to the SMB protocol take effect only on SMBv1 and SMBv2 traffic.
The logging keyword enables the file filtering module to log packet matching events and send log messages to the information center.
With the information center, you can set log message filtering and output rules, including output destinations.
The information center can output file filtering logs to any destinations except the console and the monitor terminal. If you configure the console or monitor terminal as an output destination, the output destination setting will not take effect.
To view file filtering logs stored on the device, use the display logbuffer command. Make sure you do not disable log output to the log buffer, which is enabled by default.
For more information about configuring the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Create a file filtering policy and enter its view.
file-filter policy policy-name
3. (Optional.) Configure a description for the file filtering policy.
description string
By default, a file filtering policy does not have a description.
4. Create a file filtering rule and enter its view.
rule rule-name
5. Specify a file type group for the file filtering rule.
filetype-group group-name
By default, a file filtering rule does not contain any file type group.
6. Specify the application layer protocols to which the file filtering rule applies.
application { all | type { ftp | http | imap | nfs | pop3 | rtmp | smb | smtp } * }
By default, no applicable application layer protocols are specified for a file filtering rule.
7. Specify the traffic directions to which the file filtering rule applies.
direction { both | download | upload }
By default, a file filtering rule applies to upload traffic.
8. Specify the actions to take on matching packets.
action { drop | permit } [ logging ]
The default action of a file filtering rule is drop.
Setting the action for packets with files carrying false extensions
About this task
A packet might contain files that carry false extensions. For example, a file that carries the .exe file extension might actually be a .txt file.
Use this command to specify the action for packets with files carrying false extensions. To perform file filtering inspection based on the real file extension, set the action to permit. To discard such packets directly, set the action to drop.
Procedure
1. Enter system view.
system-view
2. Set the action for packets with files carrying false extensions.
file-filter false-extension action { drop | permit }
The default action is permit, which enables the device to determine the packet processing action based on the real file extension.
Applying a file filtering policy to a DPI application profile
About this task
A file filtering policy must be applied to a DPI application profile to take effect.
A DPI application profile can use only one file filtering policy. If you apply different file filtering policies to the same DPI application profile, only the most recent configuration takes effect.
Procedure
1. Enter system view.
system-view
2. Enter DPI application profile view.
app-profile profile-name
For more information about this command, see DPI engine commands in DPI Command Reference.
3. Apply a file filtering policy to the DPI application profile.
file-filter apply policy policy-name
By default, no file filtering policy is applied to the DPI application profile.
Activating file filtering policy and rule settings
About this task
By default, the system will detect whether another configuration change (such as creation, modification, or deletion) occurs within a 20-second interval after a change to the file filtering policy and rule settings:
· If no configuration change occurs within the interval, the system performs an activation operation at the end of the next 20-second interval to make the configuration take effect.
· If a configuration change occurs within the interval, the system continues to periodically detect whether configuration changes occur within next 20-second intervals.
To activate the policy and rule configurations immediately, you can execute the inspect activate command.
Procedure
1. Enter system view.
system-view
2. Activate file filtering policy and rule settings.
inspect activate
By default, file filtering policy and rule settings will be activated automatically.
|
CAUTION: This command can cause temporary outage for DPI services. Services based on the DPI services might also be interrupted. For example, security policies cannot control application access. |
Applying a DPI application profile to a security policy rule
1. Enter system view.
system-view
2. Enter security policy view.
security-policy { ip | ipv6 }
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Set the rule action to pass.
action pass
The default rule action is drop.
5. Use a DPI application profile in the rule.
profile app-profile-name
By default, no DPI application profile is used in a security policy rule.
File filtering configuration examples
Example: Using a file filtering policy in a security policy
Network configuration
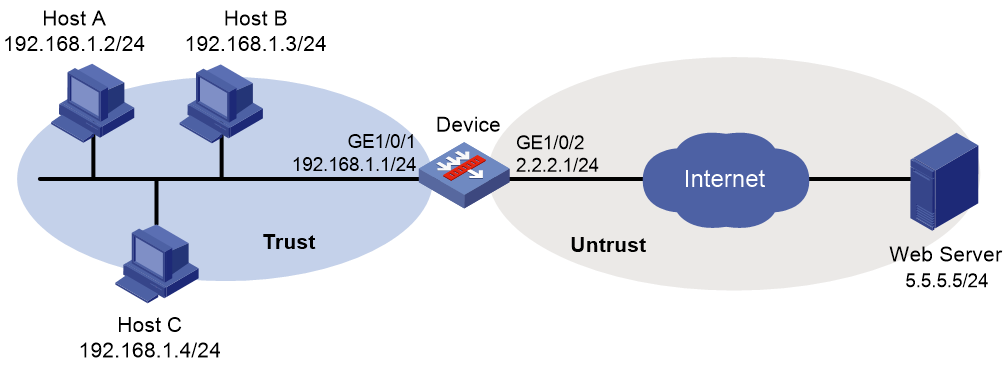
As shown in Figure 1, the device connects to the LAN and Internet through security zones Trust and Untrust, respectively.
Configure file filtering on the device so the device performs the following operations:
· Blocks files with the pptx or dotx extension.
· Logs the blocked files.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route to reach the Web server, and the next hop in the route is 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Configure file filtering:
a. Create a file type group named fg1 and create two file type match patterns to match files with the pptx and dotx extensions, respectively.
[Device] file-filter filetype-group fg1
[Device-file-filter-fgroup-fg1] pattern 1 text pptx
[Device-file-filter-fgroup-fg1] pattern 2 text dotx
[Device-file-filter-fgroup-fg1] quit
b. Create a file filtering rule named r1 and configure it to drop and log both upload and download HTTP packets that match file type group fg1.
[Device] file-filter policy p1
[Device-file-filter-policy-p1] rule r1
[Device-file-filter-policy-p1-rule-r1] filetype-group fg1
[Device-file-filter-policy-p1-rule-r1] application type http
[Device-file-filter-policy-p1-rule-r1] direction both
[Device-file-filter-policy-p1-rule-r1] action drop logging
[Device-file-filter-policy-p1-rule-r1] quit
5. Configure a DPI application profile and activate the file filtering policy and rule settings:
# Create a DPI application profile named sec and apply file filtering policy p1 to the DPI application profile.
[Device] app-profile sec
[Device-app-profile-sec] file-filter apply policy p1
[Device-app-profile-sec] quit
# Activate the file filtering policy and rule settings.
[Device] inspect activate
6. Configure a security policy:
# Create a security policy rule named trust-untrust. Configure the rule to apply DPI application profile sec to packets from security zone Trust to security zone Untrust with source subnet address 192.168.1.0/24.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] profile sec
[Device-security-policy-ip-10-trust-untrust] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
Verifying the configuration
# Verify that the device blocks and logs files that meet the specified criteria. (Details not shown.)