- Table of Contents
-
- 04-Policies
- 01-Security policy
- 02-Security policy redundancy analysis
- 03-Security policy hit analysis
- 04-Security policy optimization
- 05-Policy-based NAT
- 06-Interface NAT
- 07-AFT
- 08-QoS
- 09-Bandwidth management
- 10-Application audit
- 11-Application proxy
- 12-IP reputation
- 13-Domain reputation
- 14-Blacklist
- 15-Connection limit
- 16-Server connection detection
- 17-Access rate limit
- 18-DLP
- 19-Server load balancing
- 20-Outbound link load balancing
- 21-Inbound link load balancing
- 22-Transparent DNS proxy
- 23-NetShare control
- 24-Zero trust policy
- 25-Trusted application proxies
- 26-Trusted API proxies
- 27-NAT66
- 28-uRPF
- 29-Load balancing common configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 21-Inbound link load balancing | 153.19 KB |
This help contains the following topics:
· Configure inbound link load balancing
¡ Configure health monitoring (optional)
¡ Configure proximity (optional)
¡ Configure ISP information (optional)
¡ Configure a region (optional)
¡ Configure a forward DNS zone (optional)
¡ Configure a reverse DNS zone (optional)
Introduction
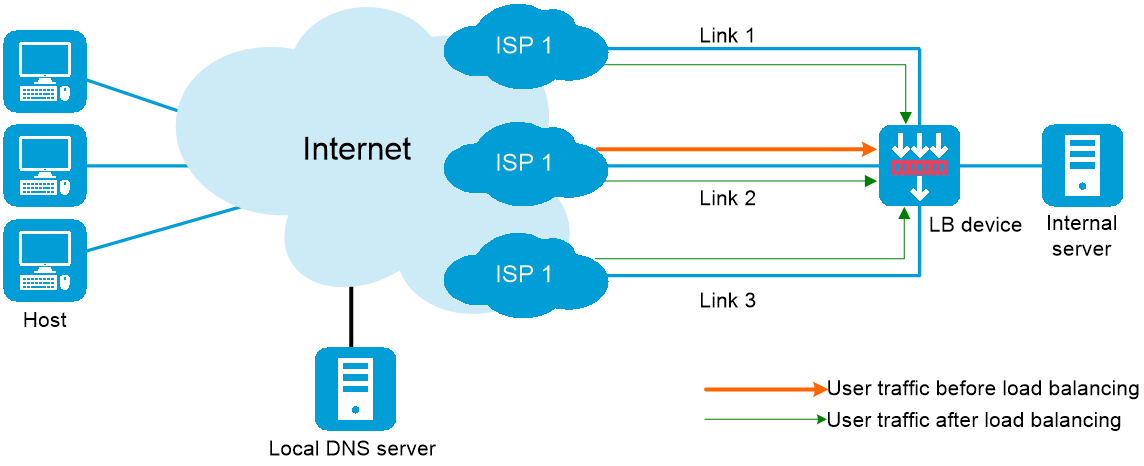
How it works
Inbound link load balancing load balances traffic among the links from the external network to the internal network. This feature provides link redundancy and increased link efficiency.
Workflow on the device
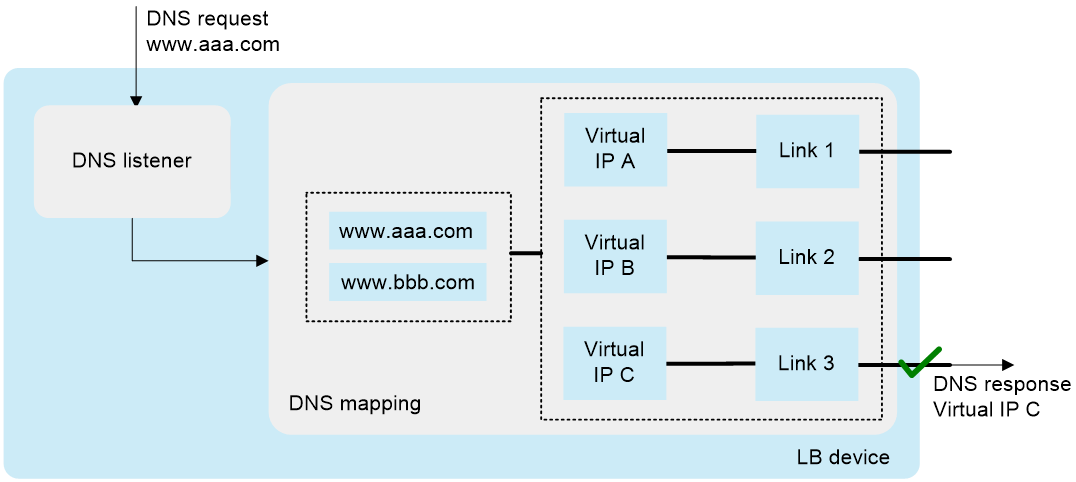
Figure 2 Workflow
When the device receives a DNS request with the destination IP address matching the DNS listener IP address, it queries the virtual IP addresses associated with the domain name in DNS mappings. Then, the device selects a virtual IP address for the best link according to the configured scheduling algorithm. The device sends the virtual IP address to the client in the outgoing DNS response. The client uses the virtual IP address as the destination IP address to access the internal server.
Restrictions and guidelines
To ensure correct operation of inbound link load balancing when server load balancing is also enabled, do not specify the virtual server's IP address as the DNS listener's IP address.
Configure inbound link load balancing
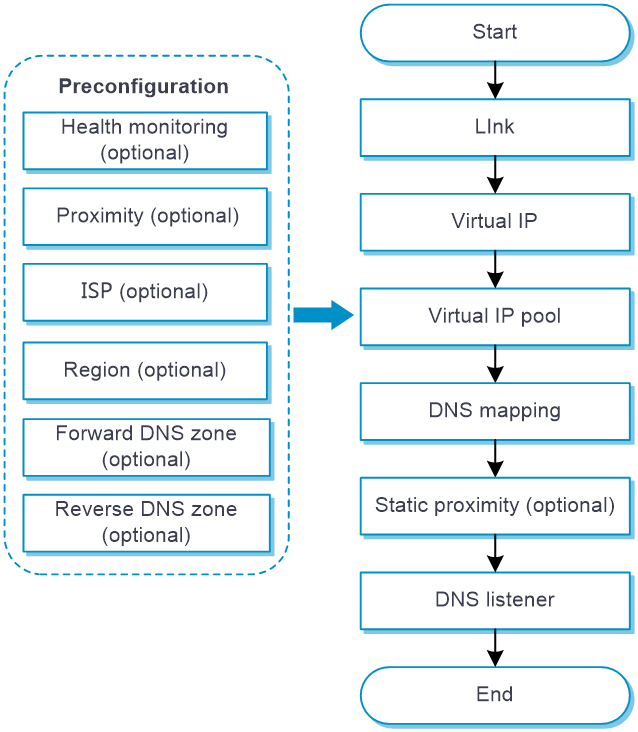
Figure 3 shows the configuration procedure for inbound link load balancing.
Figure 3 Inbound link load balancing configuration procedure
Configure health monitoring (optional)
The health monitoring configuration can be used by a link or link group.
For detailed steps required to configure health monitoring, see the online help for health monitoring.
Configure proximity (optional)
For detailed steps required to configure proximity, see the online help for Objects > Load Balancing.
Configure ISP information (optional)
For detailed steps required to configure ISP information, see the online help for Objects > Load Balancing.
Configure a region (optional)
For detailed steps required to configure regions, see the online help for Objects > Load Balancing.
Configure a forward DNS zone (optional)
During DNS resolution, an LB device looks up the resource records configured in a forward DNS zone for the host name corresponding to the target domain name. DNS resource records are used by an LB device to resolve DNS requests and have the following types:
· Canonical name (CNAME)—Maps multiple aliases to one host name (server). For example, an enterprise intranet has a server with host name host.aaa.com. The server provides both Web service and mail service. You can configure two aliases (www.aaa.com and mail.aaa.com) in a CNAME resource record for this server. When a user requests Web service, the user accesses www.aaa.com. When a user requests mail service, the user accesses mail.aaa.com. Actually, the user accesses host.aaa.com in both cases.
· Mail exchanger (MX)—Specifies the mail server for a forward DNS zone.
· Name server (NS)—Specifies the authoritative DNS server for a forward DNS zone.
· Start of authority (SOA)—Specifies authoritative information about a forward DNS zone, including the primary DNS server and administrator mailbox.
Procedure
1. Select Policies > Link Load Balancing > Inbound Link Load Balancing > Forward DNS Zone.
2. Click Create on the Forward DNS Zone page.
3. Create a forward DNS zone.
Table 1 Forward DNS zone configuration items
|
Item |
Description |
|
Zone name |
Specifies a domain name for the forward DNS zone, a case-insensitive string of 1 to 253 characters. Each dot-separated part in the domain name can contain a maximum of 63 characters. The domain name can contain letters, digits, hyphens (-), underscores (_), and dots (.). |
|
TTL |
Specify the TTL for all resource records in the forward DNS zone. |
|
Resource record list |
1. Click Create to add a resource record. ¡ Type—Select a resource type: MX, NS, or CNAME. ¡ Subname—Specify a subname for the forward DNS zone, a case-insensitive, dot-separated string of 1 to 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. This parameter appears only if you have selected MX or NS from the Type list. ¡ Mail server host name—Specify the host name of the mail server, a case-insensitive, dot-separated string that contains a maximum 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. This parameter appears only if you have selected MX from the Type list. ¡ Priority—Specify the preference for the resource record, in the range of 0 to 65535. The smaller the value, the higher the priority. This parameter appears only if you have selected MX from the Type list. ¡ Authoritative name server host name—Specify the host name of the authoritative DNS server, a case-insensitive, dot-separated string that contains a maximum of 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. The smaller the value, the higher the priority. This parameter appears only if you have selected NS from the Type list. ¡ Alias—Specify an alias for a host name, a case-insensitive, dot-separated string that contains a maximum of 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. ¡ Canonical name—Specify the host name, a case-insensitive, dot-separated string that contains a maximum 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. This parameter appears only if you have selected CNAME from the Type list. ¡ TTL—Specify the TTL for the current resource record. 2. Click Create. The new resource record appears in the resource record list. |
|
SOA configuration-Primary name server host name |
Specify the host name for the primary DNS server, a case-insensitive and dot-separated string of up to 254 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. The host name of the primary DNS server can be a relative domain name (does not end with a dot) or an absolute domain name (ends with a dot). For an absolute domain name, the host name is not automatically expanded and cannot exceed 254 characters. For a relative domain name, the current domain name is automatically appended to the host name. The host name plus the appended domain name cannot exceed 254 characters. |
|
SOA configuration-Administrator email address |
Specify the email address of the administrator. The email address of the administrator can be a relative domain name (does not end with a dot) or an absolute domain name (ends with a dot). For an absolute domain name, the email address is not automatically expanded and cannot exceed 254 characters. For a relative domain name, the current domain name is automatically appended to the email address. The email address plus the appended domain name cannot exceed 254 characters. |
|
SOA configuration-Serial number |
Configure the serial number for a forward DNS zone. The serial number indicates the configuration order of a forward DNS zone. A newly configured forward DNS zone has a greater serial number than an old forward DNS zone. The secondary DNS server periodically queries the serial numbers of forward DNS zones on the primary DNS server and compares them with local serial numbers. |
|
SOA configuration-Refresh interval |
Specify the refresh interval. The secondary DNS server obtains SOA resource records from the primary DNS server at the refresh interval. After obtaining SOA resource records, the secondary DNS server compares them with the local SOA resource records. |
|
SOA configuration-Retry interval |
Specify the retry interval, which is the amount of time that the secondary DNS server waits after it fails to copy a forward DNS zone. |
|
SOA configuration-Expiration time |
Specify the expiration time for SOA resource records. The expiration time for SOA resource records is the amount of time that the secondary DNS server can work after it loses contact with the primary DNS server. |
|
SOA configuration-Minimum TTL |
Specify the minimum TTL, which is the amount of time that resource records on the primary DNS server are cached on the secondary DNS server. |
4. Click OK. The forward DNS zone appears on the Forward DNS Zone page.
Configure a reverse DNS zone (optional)
The LB device performs reverse DNS resolution according to the reverse DNS zone configuration. Reverse DNS resolution searches for a domain name according to an IP address. The pointer record (PTR) resource records configured in a reverse DNS zone record mappings between domain names and IP addresses.
Reverse DNS resolution is used to address spam attacks by verifying the validity of the email sender. When a mail server receives an email from an external user, it sends a reverse DNS resolution request to the LB device. The LB device resolves the source IP address of the sender into a domain name according to PTR resource records and sends the domain name to the mail server. The mail server compares the received domain name with the actual domain name of the sender. If the two domain names match, the mail server accepts the email. If not, the mail server considers the email as a spam email and discards it.
Procedure
1. Select Policies > Link Load Balancing > Inbound Link Load Balancing > Reverse DNS Zone.
2. Click Create on the Reverse DNS Zone page.
3. Create a reverse DNS zone.
Table 2 Reverse DNS zone configuration items
|
Item |
Description |
|
Type |
Specify a zone type: IPv4 or IPv6. |
|
IPv4 address |
Specify an IPv4 address for the reverse DNS zone. This parameter appears only if you have selected IPv4 from the Type list. |
|
IPv6 address |
Specify an IPv6 address for the reverse DNS zone. This parameter appears only if you have selected IPv6 from the Type list. |
|
Mask |
Specify the mask length for the reverse DNS zone. This parameter appears only if you have selected IPv4 from the Type list. |
|
Prefix |
Specify the prefix length for the reverse DNS zone. This parameter appears only if you have selected IPv6 from the Type list. |
|
PTR resource record list |
3. Click Create to add a PTR resource record. ¡ IPv4 address—Specify an IPv4 address. The IPv4 address specified in a PTR resource record must be within the IPv4 address range of the reverse DNS zone. This parameter appears only if you have selected IPv4 from the Type list. ¡ IPv6 address—Specify an IPv6 address. The IPv6 address specified in a PTR resource record must be within the IPv6 address range of the reverse DNS zone. This parameter appears only if you have selected IPv6 from the Type list. ¡ Domain name—Specify a domain name, a case-insensitive, dot-separated string that contains a maximum of 253 characters. The string can contain letters, digits, hyphens (-), underscores (_), and dots (.). Each dot-separated part can have a maximum of 63 characters. ¡ TTL—Specify the TTL for the resource record. 4. Click OK. The new PTR resource record appears in the PTR resource record list. |
4. Click OK. The reverse DNS zone appears on the Reverse DNS Zone page.
Configure a link
For detailed steps required to configure links, see the online help for Objects > Load Balancing.
Configure a DNS mapping
By configuring a DNS mapping, you can associate a domain name with virtual IP addresses/virtual servers. The LB device can obtain the virtual IP addresses/virtual servers associated with the domain name in a DNS request and select one virtual IP address/virtual server according to the configured scheduling algorithm.
Procedure
1. Select Policies > Link Load Balancing > Inbound Link Load Balancing > DNS Mapping.
2. Click Create on the DNS Mapping page.
3. Create a DNS mapping.
Table 3 DNS mapping configuration items
|
Item |
Description |
|
DNS mapping name |
Enter a name for the DNS mapping, case insensitive. |
|
Domain name list |
1. Enter a domain name, a case-insensitive string of 1 to 253 characters. Each dot-separated label in the domain name can contain a maximum of 63 characters. The domain name can contain letters, digits, hyphens (-), underscores (_), dots (.), and wildcards (asterisks and question marks). Dots cannot be used as the start and end characters. When you use wildcards (asterisks and question marks) in a domain name, follow these guidelines: ¡ The wildcards can substitute any characters except for dots (.). ¡ An asterisk (*) can substitute a character string. ¡ A question mark (?) can substitute a single character. 2. Click Add. The added domain name appears in the domain name list. |
|
Virtual IP/Virtual server list |
1. Click Create to add a virtual IP address or virtual server. ¡ Virtual server—Specify a virtual server. You can select an existing virtual server or create a virtual server. ¡ Virtual IP address—Configure a virtual IP address. In a scenario where server load balancing is not required, configure only a virtual IP address instead of both a virtual IP address and a virtual server. ¡ Link—Specify a link to associate with the virtual server or virtual IP address. You can select an existing link or create a link. ¡ Weight—Specify the weight for the virtual server or virtual IP address. For the weighted round robin and weighted least connections algorithms, a greater value means a higher priority to be referenced. 2. Click OK. The new virtual server or virtual IP address appears in the virtual server/virtual IP list. |
|
Preferred predictor |
Specify the preferred predictor for virtual IP addresses/virtual servers. The preferred predictor has the highest priority. If no virtual IP address/virtual server can be selected by using the preferred predictor, the alternative predictor is used to select a virtual IP address/virtual server. If no virtual IP address/virtual server can be selected by using the alternative predictor, the backup predictor is used to select a virtual IP address/virtual server. You can specify one of the following predictors as the preferred predictor: · Weight round robin—Assigns DNS requests to virtual IP addresses/virtual servers based on the weights of virtual IP addresses/virtual servers. A higher weight indicates more DNS requests will be assigned. · Random—Randomly assigns DNS requests to virtual IP addresses/virtual servers. · Weighted least connections—Always assigns DNS requests to the virtual IP addresses/virtual server with the fewest number of weighted active connections (the number of active connections divided by weight). · Static proximity—Assigns DNS requests to virtual IP addresses/virtual servers based on static proximity entries. · Dynamic proximity—Assigns DNS requests to virtual IP addresses/virtual servers based on dynamic proximity entries. · Hash source IP address—Hashes the source IP address of DNS requests and distributes DNS requests to different virtual IP addresses/virtual servers according to the hash values. · Hash source IP address and port number—Hashes the source IP address and port number of DNS requests and distributes DNS requests to different virtual IP addresses/virtual servers according to the hash values. · Hash destination IP address—Hashes the destination IP address of DNS requests and distributes DNS requests to different virtual IP addresses/virtual servers according to the hash values. · Bandwidth—Distributes DNS requests to virtual IP addresses/virtual servers according to the weights and remaining bandwidth of them. · Max bandwidth—Distributes DNS requests always to an idle virtual IP address/virtual server that has the largest remaining bandwidth. By default, the weighted round robin algorithm is used. |
|
Alternative predictor |
Specify the alternative predictor. The supported predictors are the same as those supported by the preferred predictor. |
|
Backup predictor |
Specify the backup predictor. The supported predictors are the same as those supported by the preferred predictor. |
|
Link protection |
Enable or disable link protection. This feature enables the device to select a virtual IP address based on the bandwidth ratio of the associated link. If the bandwidth ratio of a link is exceeded, the virtual IP address is not selected. You can set the bandwidth ratio of a link on the Links page. |
|
TTL |
Specify the TTL value in the range of 0 to 4294967295 seconds. This time is the amount of time that DNS records are cached for DNS responses. For the DNS client to get the updated DNS record when the virtual IP configuration changes, set a smaller TTL value, for example, 60 seconds. For stable, fast domain name resolution when the network is stable, set a larger TTL value, for example, 86400 seconds. |
|
DNS mapping |
Enable or disable DNS mapping. |
4. Click OK. The new DNS mapping appears on the DNS Mapping page.
Configure static proximity
A static proximity policy associates the region where the local DNS server resides with the IP address range of a virtual IP. When the static proximity algorithm is specified in a DNS mapping, you must configure a static proximity policy.
Procedure
1. Select Policies > Link Load Balancing > Inbound Link Load Balancing > Static Proximity.
2. Click Create on the Static Proximity page.
3. Create a static proximity policy.
Table 4 Static proximity policy configuration items
|
Item |
Description |
|
Region name |
Select an existing region or create a region. |
|
Address range |
Specify an IPv4 address range in the form of IPv4 address/Mask length or an IPv6 address range in the form of IPv6 address/Prefix length. The mask length is in the range of 0 to 32. If the mask length is 32, the most significant eight bits must be smaller than 224 and cannot be 0 or 127. The prefix length is in the range of 0 to 128. |
|
Priority |
Specify a priority value. When a DNS request matches multiple static proximity policies, the static proximity policy with the greatest priority value is selected. |
4. Click OK. The new static proximity policy appears on the Static Proximity page.
Configure a DNS listener
A DNS listener listens DNS requests on the LB device. If the destination address of a DNS request matches the address being listened, inbound link load balancing is performed. The LB device searches for the address-to-domain name mapping, and obtains the virtual IP address corresponding to the domain name. The LB device sends the virtual IP address to the user in a DNS response before the user can establish a connection to the server.
Procedure
1. Select Policies > Link Load Balancing > Inbound Link Load Balancing > DNS Listener.
2. Click Create on the DNS Listener page.
3. Create a DNS listener.
Table 5 DNS listener configuration items
|
Item |
Description |
|
DNS listener name |
Enter a name for the DNS listener, case insensitive. |
|
IPv4 address |
Specify an IPv4 for the DNS listener. The IPv4 address cannot be a loopback address, multicast address, broadcast address, or an address in the format of 0.X.X.X. |
|
IPv6 address |
Specify an IPv6 for the DNS listener. The IPv6 address cannot be a loopback address, multicast address, link-local address, or all-zero address. |
|
Port number |
Specify a port number for the DNS listener. |
|
VRF |
Select an existing VPN instance or create a VPN instance. A created VPN instance can be viewed from Network > VRF. |
|
DNS listening |
Enable or disable DNS listening. |
|
Processing for nonexistent domain |
Specify a processing method for DNS mapping search failure. · Do not respond · Respond with a DNS reject · Respond through a DNS proxy |
4. Click OK. The new DNS listener appears on the DNS Listener page.