- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-WAF configuration
- 10-Proxy policy configuration
- 11-IP reputation configuration
- 12-Domain reputation configuration
- 13-APT defense configuration
- 14-DLP configuration
- 15-Content moderation configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-DLP configuration | 185.68 KB |
Sensitive information detection
Restrictions: Hardware compatibility with DLP
Display and maintenance commands for DLP
Configuring DLP
About DLP
Data loss prevention (DLP) is used to detect sensitive information in files transferred by the device and notify users of sensitive information leakage by logs or emails. This feature facilitates users to harden data security.
DLP mechanisms
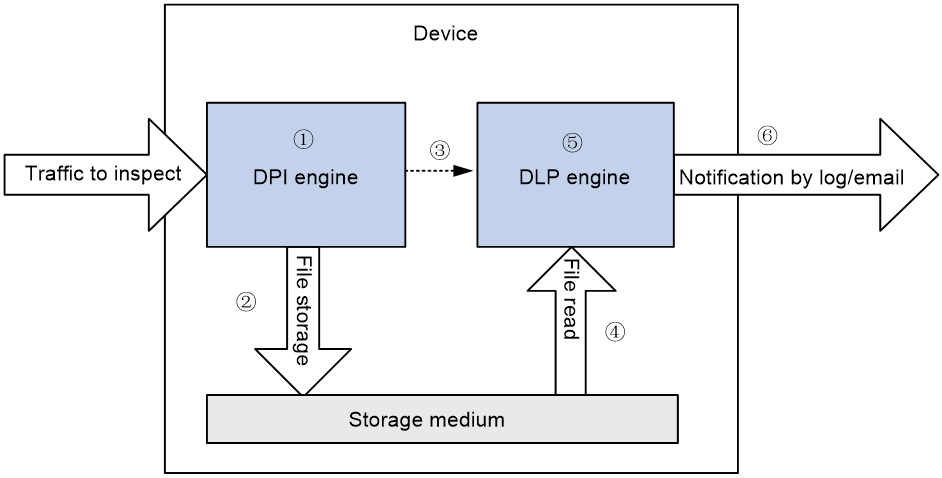
As shown in Figure 1, the device uses the DPI engine and DLP engine to perform DLP flow monitoring. The DPI engine performs file extraction and the DLP engine performs sensitive information detection. For more information about the DPI engine, see "Configuring DPI engine."
DLP uses the following workflow:
1. The DPI engine extracts files from the traffic to inspect.
2. The DPI engine stores the files to the storage medium of the device.
3. The DPI engine notifies the DLP engine to scan the files.
4. The DLP engine scans and reads the files from the storage medium.
5. The DLP engine detects sensitive information in the files.
6. The DLP engine sends a notification by log or email based on the detection result.
File extraction
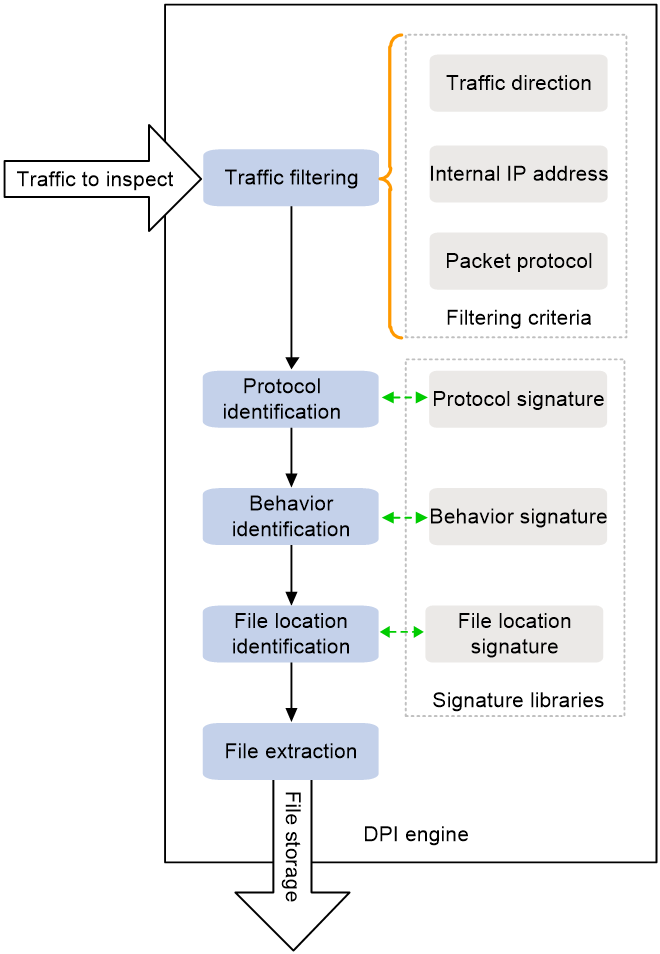
As shown in Figure 2, the DPI engine identifies the application layer information and extracts files in packets as follows:
1. Filters traffic by using the following filtering criteria:
¡ Traffic direction—Matches the packet transmission direction. Options include external-to-internal, internal-to-external, and bidirectional.
¡ Internal IP address—Matches the destination IP address of packets transferred in the external-to-internal direction and matches the source IP address of packets transferred in the internal-to-external direction.
¡ Packet protocol—Matches the application layer protocol of packets.
2. Identifies the application layer protocol of the matching packets, FTP or SMTP, for example.
3. Identifies the behavior of the matching packets, for example, uploading a file or sending an email.
4. Searches the signature libraries to identify the start and end locations of the files to be extracted in the packets.
5. Extracts the files from the packets, saves the extracted files locally on the device, and assigns a unique URL to each file for the DLP engine to access.
Figure 2 DPI engine operation process
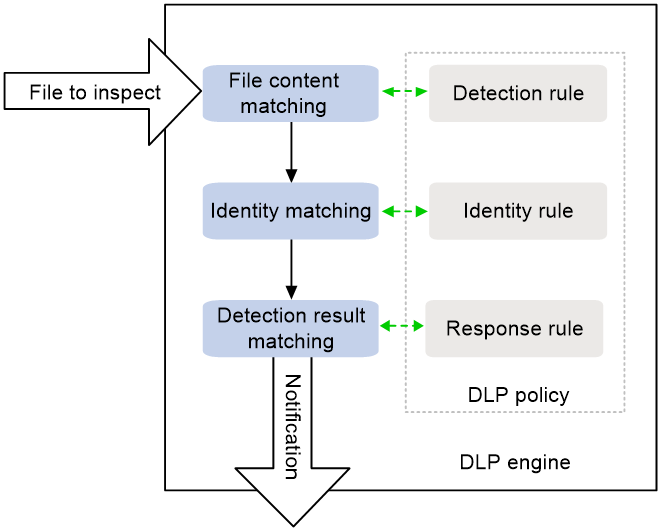
Sensitive information detection
If the extracted file is a compressed file, the DLP engine will decompress the file and perform sensitive information detection on the extracted file as follows:
1. Uses the detection rule to match the file content.
2. Uses the identity rule to match the identity of the sender or recipient.
3. Uses the response rule to match the detection result.
4. Sends a notification.
Figure 3 DLP engine operation process
Detection rule
A detection rule includes the following items:
· Regular expression—Used to identify sensitive file signatures.
· Keyword—A string used to identify sensitive file signatures.
· Fingerprint file—Sensitive file hash code.
· File name—Sensitive file name.
· File size—Sensitive file size.
· File type—Sensitive file type.
· Protocol—File transfer protocol.
A file matches a detection rule only when its content matches all items in that detection rule. You must set a severity level for each detection rule. If a file matches a detection rule of the specified severity level, the system generates an event of that severity level accordingly.
Identity rule
An identity rule includes the following items:
· IP address—IP address of the file sender or file recipient.
· Email address—Email address of the file sender or file recipient.
· User—User name of the file recipient.
The file sender or recipient matches an identity rule only when its identity information matches all items in that identity rule. You must set a severity level for each identity rule. If a file matches an identity rule of the specified severity level, the system generates an event of that severity level accordingly.
Response rule
A response rule includes the following items:
· Severity level—DLP event severity level.
· Protocol—Protocol for the file in which sensitive information is detected.
A DLP event matches a response rule only when the event matches all items in that response rule. If a matching response rule is found, the DLP engine will send a notification by log, email, or others according to the response rule.
Restrictions: Hardware compatibility with DLP
|
Hardware platform |
Module type |
DLP compatibility |
|
M9006 M9010 M9014 |
Blade IV firewall module |
Yes |
|
Blade V firewall module |
No |
|
|
NAT module |
No |
|
|
M9010-GM |
Encryption module |
Yes |
|
M9016-V |
Blade V firewall module |
No |
|
M9008-S M9012-S |
Blade IV firewall module |
Yes |
|
Intrusion prevention service (IPS) module |
Yes |
|
|
Video network gateway module |
Yes |
|
|
M9008-S-6GW |
IPv6 module |
Yes |
|
M9008-S-V |
Blade IV firewall module |
Yes |
|
M9000-AI-E4 M9000-AI-E8 M9000-AI-E16 |
Blade V firewall module |
Yes |
|
M9000-X06 M9000-X10 |
Blade VI firewall module |
Yes |
Configuring DLP
About this task
DLP flow monitoring requires the cooperation of the DPI engine and DLP engine. The DPI engine extracts files and the DLP engine performs sensitive information detection on the files.
Procedure
1. Enter system view.
system-view
2. Enable the TCP segment reassembly feature.
inspect tcp-reassemble enable
By default, the TCP segment reassembly feature is disabled.
For more information about this command, see DPI engine in DPI Command Reference.
3. Disable stream fixed length inspection.
inspect stream-fixed-length disable
By default, the stream fixed length inspection feature is enabled.
For more information about this command, see DPI engine in DPI Command Reference.
4. Activate policy and rule settings for DPI service modules.
inspect activate
By default, the creation, modification, and deletion of DPI service policies and rules do not take effect.
For more information about this command, see DPI engine in DPI Command Reference.
5. Monitor files transferred in the specified direction.
dlp flow-monitor file-transfer { all | incoming | outgoing }
By default, DLP does not monitor files of any direction.
6. Configure internal IP addresses for DLP flow monitoring:
a. Enter a DLP internal address view.
dlp flow-monitor local-address { ip | ipv6 }
b. Specify an IP address object group for DLP flow monitoring.
object-group object-group-name
By default, no IP address object groups are specified for DLP flow monitoring.
7. (Optional.) Configure DLP flow monitoring for specific protocols:
a. Enter DLP protocol configuration view.
dlp flow-monitor protocol
b. Disable DLP flow monitoring for specific protocols.
disable protocol { all | type protocol-name }
By default, DLP flow monitoring is enabled for all DLP-supported protocols.
8. Configure a DLP policy.
A DLP policy includes detection rules, identity rules, and response rules. You can configure the DLP policy from the Web interface. For more information, see DLP online help.
9. Enable DLP.
undo dlp bypass
By default, DLP is enabled.
Display and maintenance commands for DLP
Execute display commands in any view.
|
Task |
Command |
|
Display IPv4 address object group configuration for DLP flow monitoring. |
display dlp flow-monitor local-address ip config |
|
Display IPv6 address object group configuration for DLP flow monitoring. |
display dlp flow-monitor local-address ipv6 config |
|
Display DLP flow monitoring status for all protocols supported by DLP. |
display dlp flow-monitor protocol config |
DLP configuration examples
Example: Configuring DLP
Network configuration
As shown in Figure 4, the device is deployed at the edge of the internal network in a company to detect and notify internal sensitive file leakage events. Configure the device to log the following security events:
· Sensitive file abc.zip is leaked.
· An internal user sends an email to sensitive email box [email protected] in the external network.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
3. Configure a security policy rule named trust-untrust to permit traffic from the hosts in security zone Trust to the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-1-trust-untrust] source-zone trust
[Device-security-policy-ip-1-trust-untrust] destination-zone untrust
[Device-security-policy-ip-1-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-1-trust-untrust] action pass
[Device-security-policy-ip-1-trust-untrust] quit
[Device-security-policy-ip] quit
4. Configure DPI:
# Enable the TCP segment reassembly feature.
[Device] inspect tcp-reassemble enable
# Disable stream fixed length inspection.
[Device] inspect stream-fixed-length disable
# Activate policy and rule settings for DPI service modules.
[Device] inspect activate
5. Configure DLP flow monitoring:
# Monitor traffic transferred from the internal network to the external network.
[Device] dlp flow-monitor file-transfer outgoing
# Configure IP address object group obj1 and specify internal IP addresses in the object group.
[Device] object-group ip address obj1
[Device-obj-grp-ip-obj1] network subnet 192.168.1.0 24
[Device-obj-grp-ip-obj1] quit
# Specify the IP address object group for DLP flow monitoring.
[Device] dlp flow-monitor local-address ip
[Device-dlp-flow-monitor-local-addr-ip] object-group obj1
[Device-dlp-flow-monitor-local-addr-ip] quit
# Enable DLP.
[Device] undo dlp bypass
6. Configure a DLP policy:
a. Log in to the Web interface of the device.
b. Select Policies > DLP > DLP Policies.
c. Click Create.
d. In the dialog box that opens, configure parameters for the DLP policy:
- Enter a policy name.
- Select a scan mode.
- Select Start policy.
Figure 5 Creating a DLP policy
e. On the Detection Rules tab of the Create DLP Policy dialog box, click Create in the Add Rule area.
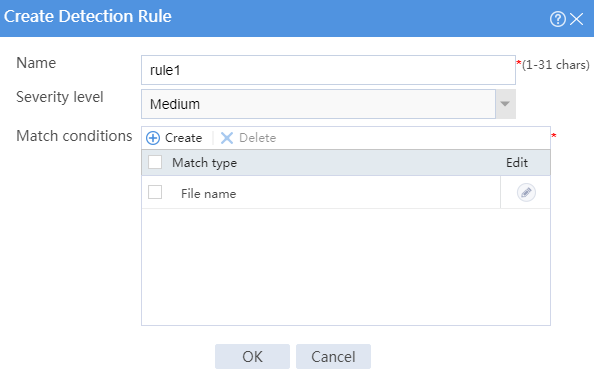
f. Configure parameters for the detection rule:
- Enter a rule name.
- Select a severity level.
- Configure the match conditions as matching the file named abc.zip.
Figure 6 Creating a detection rule
Figure 7 Creating a match condition
g. Click OK. Then, click the Identity Rules tab on the Create DLP Policy dialog box and click Create in the Add Rule area.
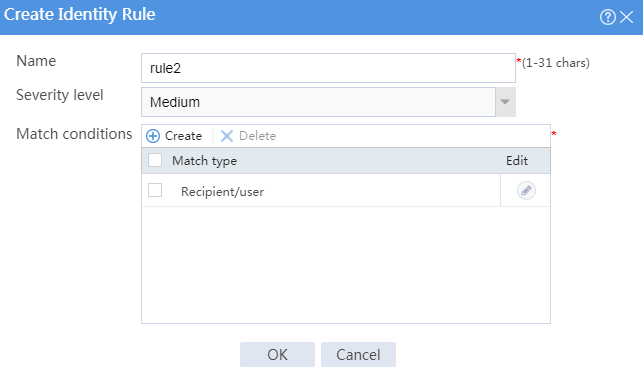
h. Configure parameters for the identity rule:
- Enter a rule name.
- Select a severity level.
- Configure the match conditions as matching the recipient at [email protected].
Figure 8 Creating an identity rule
Figure 9 Creating a match condition
i. Click OK. Then, click the Response Rules tab on the Create DLP Policy dialog box and create a response rule.
j. Configure parameters for the response rule:
- Enter a rule name.
- Configure the match conditions as matching security events with the medium severity level.
- Configure the action as sending logs.
Figure 10 Creating a response rule
k. Click OK. The response rule is created.
l. Click OK. The DLP policy is created.
Verifying the configuration
# Verify that the device can generate log messages when it detects that file abc.zip has been leaked or an internal user has sent an email to email box [email protected]. (Details not shown.)