- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-WAF configuration
- 10-Proxy policy configuration
- 11-IP reputation configuration
- 12-Domain reputation configuration
- 13-APT defense configuration
- 14-DLP configuration
- 15-Content moderation configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 10-Proxy policy configuration | 223.86 KB |
Contents
Restrictions: Hardware compatibility with the proxy policy
Restrictions and guidelines: Proxy policy configuration
Proxy policy configuration procedure summary
Proxy policy tasks at a glance
Prerequisites for proxy policy configuration
Configuring attributes in the proxy policy
Setting the default action for the proxy policy
Configuring the traffic filtering criteria for a proxy policy rule
Setting the action for a proxy policy rule
Configuring SSL decryption certificates
Importing an SSL decryption certificate
Channing the credibility of an SSL decryption certificate
Deleting an SSL decryption certificate
Configuring internal server certificates
Importing an internal server certificate
Deleting an internal server certificate
Configuring the SSL proxy whitelist
Adding a hostname to the user-defined SSL hostname whitelist
Disabling hostnames on the predefined SSL hostname whitelist
Activating SSL hostname whitelist settings
Display and maintenance commands for the proxy policy
Proxy policy configuration examples
Example: Configuring the proxy policy
Configuring the proxy policy
About the proxy policy
The proxy policy enables the device to proxy TCP or SSL connections between clients and servers and implement deep packet inspection and audit on the traffic for high security.
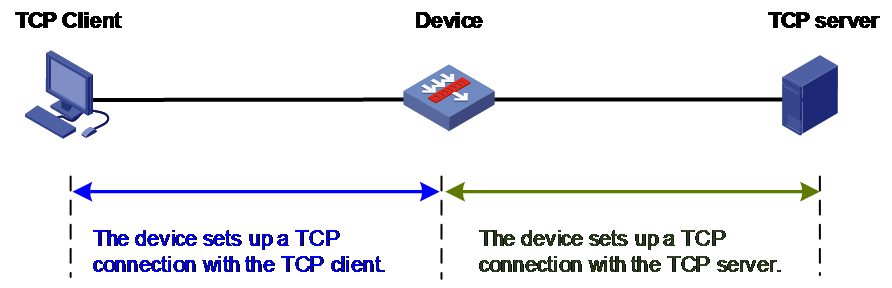
TCP proxy
As shown in Figure 1, the device implements TCP proxy for traffic between the TCP client and server. After receiving traffic from the TCP client to the server, the device becomes a TCP proxy. It proxies the server to establish a connection with the client and proxies the client to establish a connection with the server, respectively. The client and server exchange data through the two TCP connections. This mechanism provides TCP-layer isolation between the TCP client and server and helps effectively block unauthorized access attempts and malicious attacks.
SSL proxy
About this task
SSL proxy enables the device to decrypt SSL traffic and perform deep packet inspection on the traffic.
As shown in Figure 2, the device implements SSL decryption on HTTPS traffic from the HTTPS client to the HTTPS server. After receiving HTTP traffic from the HTTPS client to the server, the device becomes an SSL proxy. It proxies the server to complete the SSL handshake and establish an SSL connection with the client and proxies the client to establish an SSL connection with the server. When the HTTPS client and server exchange data, the device performs the following operations:
1. Decrypts the HTTPS traffic.
2. Performs deep packet inspection and audit on the traffic according to the DPI service configuration.
For more information about DPI services, see DPI Configuration Guide.
3. Re-encrypts the traffic and send it to the server or client.
Application scenarios
The SSL decryption can be used in the following scenarios:
· Protecting internal clients—The device is deployed at the exit of the network where the internal clients are. When the internal clients access an external server, the device acts as a proxy server to decrypt the packets and perform deep packet inspection on the decrypted packets. It protects the internal clients from being attacked by external malicious websites. In this scenario, the device requires imported SSL decryption certificates to establish SSL connections with the clients. For more information about the SSL decryption certificate, see "SSL decryption certificate."
· Protecting internal servers—The device is deployed at the entrance of the network where the internal servers are. When the external clients access an internal server, the device acts as a proxy server to decrypt the packets and perform deep packet inspection on the decrypted packets. It protects the internal servers from being attacked by external malicious traffic. In this scenario, the device requires imported internal server certificates to establish SSL connections with the clients. For more information about the internal server certificate, see "Internal server certificate."
For more information about DPI, see "DPI overview."
Basic concepts
SSL decryption certificate
The device supports a maximum of one trusted SSL decryption certificate and one untrusted SSL decryption certificate, both of which are CA certificates that must be manually imported to the device.
· Trusted SSL decryption certificate—SSL decryption certificate that is trusted by clients. The device uses the trusted SSL decryption certificate to sign proxy server certificates for servers whose certificates are verified as legitimate. The trusted SSL decryption certificate must be installed on the client browser so the client can trust the proxy server certificates signed by it.
· Untrusted SSL decryption certificate—SSL decryption certificate that clients do not trust. The device uses the untrusted SSL decryption certificate to sign proxy server certificates for servers whose certificates are verified as illegitimate.
Proxy server certificate
In the scenario of protecting internal clients, the device acts as an SSL proxy server to check whether an external server is trusted. After the identity verification, the device issues a new server certificate (that is a proxy server certificate) to the clients for SSL negotiation according to the received server certificate. Through the proxy server certificate, the internal clients can obtain the device identity and know whether the external server is trusted.
When the device proxies the SSL server to establish a connection with the client, it need to send a certificate to the client to identify itself. Instead of sending the certificate of the real server, the device uses the SSL decryption certificate to issue a new certificate (proxy server certificate) based on the real server certificate.
After receiving the certificate of the real server, the device verifies the legitimacy of the certificate on behalf of the SSL client.
· If the server certificate is legitimate, the device uses the trusted SSL decrypted certificate to issue the proxy server certificate. The client considers the proxy server certificate as legitimate because it trusts the SSL decryption certificate used to issue the certificate.
· If the server certificate is illegitimate, the device uses the untrusted SSL decryption certificate to issue the proxy server certificate. The client considers the proxy server certificate as illegitimate because it does not trust the SSL decryption certificate used to issue the certificate. A security alarm will be generated to indicate that the certificate is illegitimate and users must clear the alarm to continue the access.
Internal server certificate
The internal server certificates are required in the scenario of protecting internal servers. With an internal server certificate imported, the device will decrypt the certificate and generate a CER file and a key file.
· CER file—Used to identify the server. The device will calculate the MD5 value of the CER file and use the MD5 value as the unique identifier of the file. During the SSL proxy process, the device first calculates the MD5 value of the received server certificate and then compares the calculated MD5 value with the MD5 value of the imported internal server certificate. If they are the same, the certificate is trusted. If they are different, the certificate is untrusted.
· Key file—Used to encrypt and decrypt the packets in the subsequent SSL proxy process.
SSL proxy whitelist
The device does not proxy SSL connections destined for a server if the IP address or domain name of the server is on the SSL proxy whitelist.
The device supports the following types of SSL proxy whitelist lists:
· Predefined—The device provides a predefined SSL hostname whitelist and a predefined SSL IP address whitelist.
· User-defined—The device supports a user-defined SSL hostname list. You can disable SSL proxy for SSL connections destined for a server by adding the server hostname to the whitelist.
Mechanism for protecting internal clients
The SSL proxy function is implemented based on the TCP proxy function. When the device detects SSL traffic that needs SSL proxy, it first acts as the TCP proxy to set up TCP connections, and then implements SSL proxy.
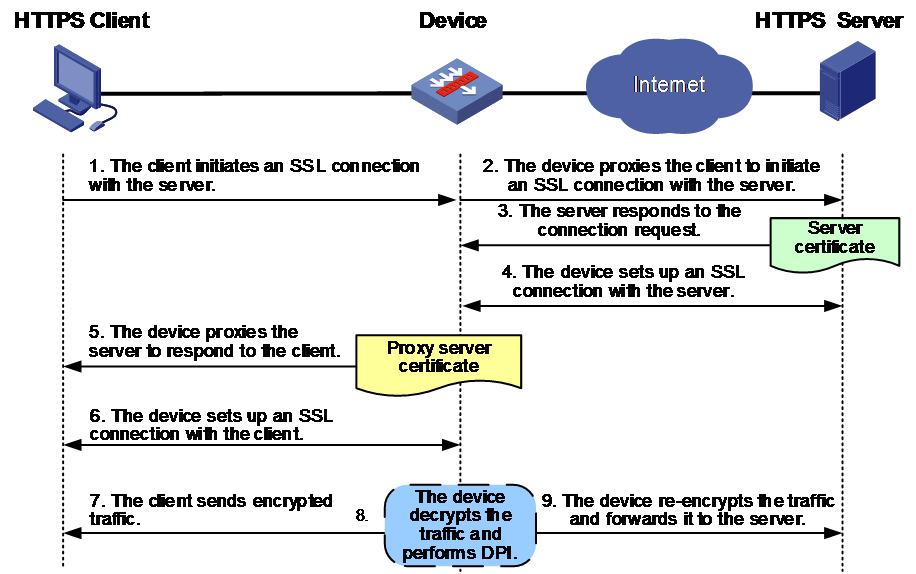
Figure 3 shows how the device acts as an SSL proxy to protect the internal client when it accesses the external server.
Figure 3 SSL proxy mechanism for protecting the internal client
1. The client sends a request to initiate an SSL connection with the server.
2. The device receives the request from the client and proxies the client to send a new SSL connection request to the server.
3. The server responds to the request and sends the server certificate to the device.
4. The device verifies the legitimacy of the server certificate, completes the SSL handshake with the server on behalf of the SSL client, and sets up an SSL connection.
5. The device acts as the SSL proxy server to respond to the client connection request and send a proxy server certificate to the client. The proxy server certificate is issued by using the SSL decryption certificate based on the content of the real server certificate.
6. The client verifies the proxy server certificate, completes the SSL handshake with the device, and sets up an SSL connection.
7. The client and server transmit encrypted SSL traffic with the device, respectively.
8. The device decrypts the SSL traffic from the client or server and performs deep packet inspection and audit on the traffic.
9. The device re-encrypts the traffic and sends it to the server.
Mechanism for protecting internal servers
The SSL proxy function is implemented based on the TCP proxy function. When the device detects SSL traffic that needs SSL proxy, it first acts as the TCP proxy to set up TCP connections, and then implements SSL proxy.
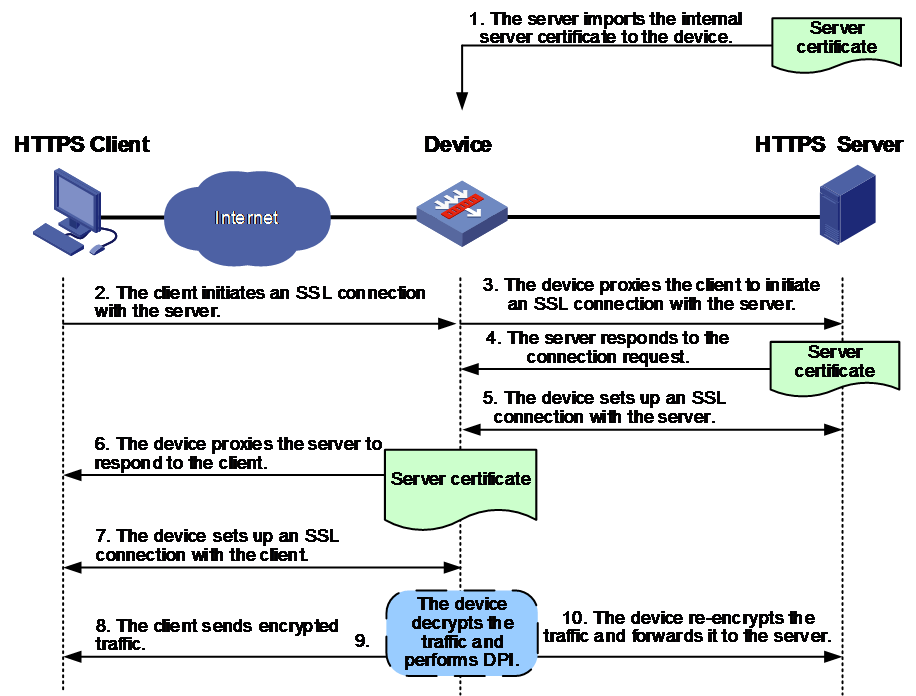
Figure 3 shows how the device acts as an SSL proxy to protect the internal server when it is accessed by the external client.
Figure 4 SSL proxy mechanism for protecting the internal server
1. The administrator obtains the certificate of the internal server to be protected and imports the internal server certificate to the device.
2. The device receives the SSL connection request from the client.
3. The device proxies the client to send a new SSL connection request to the server.
4. The server responds to the request and sends the server certificate to the device.
5. The device verifies the legitimacy of the server certificate, completes the SSL handshake with the server on behalf of the SSL client, and sets up an SSL connection.
6. The device acts as the SSL proxy server to respond to the client connection request and send the imported internal server certificate to the client.
7. The client verifies the internal server certificate, completes the SSL handshake with the device, and sets up an SSL connection.
8. The client and server transmit encrypted SSL traffic with the device, respectively.
9. The device decrypts the SSL traffic from the client or server and performs deep packet inspection and audit on the traffic.
10. The device re-encrypts the traffic and sends it to the server.
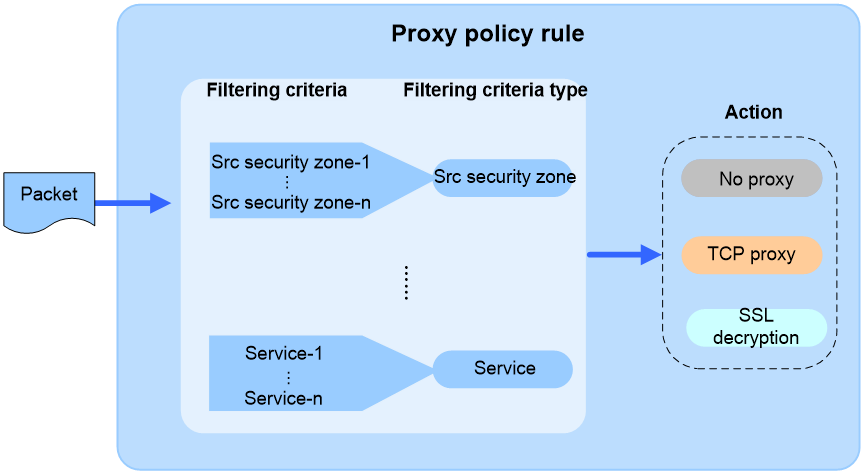
Proxy policy rules
The device supports only one proxy policy.
The proxy policy contains a set of user-defined proxy policy rules. Each rule defines a set of traffic filtering criteria and an action (TCP proxy, SSL decryption, or no-proxy) for traffic matching the rule.
Naming and numbering of proxy policy rules
Each proxy policy rule is identified by a unique rule name and ID. The rule name is required but the rule ID is optional when you create a rule. If you do not specify a rule ID, the system automatically assigns an ID to the rule.
Traffic filtering criteria in a proxy policy rule
You can configure the following types of criteria to filter the traffic to which a proxy policy rule applies:
· Source security zone.
· Destination security zone.
· Source IP address.
· Destinations IP address.
· User.
· User group.
· Service.
You can configure multiple criteria for each filtering criteria type. A packet matches a filtering criteria type if it matches a filtering criterion of the type. For example, you can configure multiple source security zone filtering criteria in a proxy policy rule. A packet passes the source security zone filtering if it matches any of the configured source security zone filtering criteria.
Proxy policy rule match order
By default, proxy policy rules are matched in the order they were created. A rule created earlier has a higher priority. You can change the rule match order by rearranging proxy policy rules. The match process stops once a matching rule is found.
The more refined the traffic filtering criteria are, the smaller the application range of the proxy policy rule. Configure the proxy policy rules in ascending order of their application ranges as a best practice.
Proxy policy rule actions
The device supports the following actions for traffic matching a proxy policy rule:
· TCP-proxy—The device acts as a TCP proxy and provides TCP-layer isolation between the TCP client and TCP server.
· SSL-decryption—The device acts as an SSL proxy to decrypt the SSL traffic between the SSL client and server and to implement deep packet inspection on the decrypted traffic.
The SSL decryption supports the following protection services:
¡ Internal client protection.
¡ Internal server protection.
· No-proxy—The device directly transmits the traffic without TCP or SSL proxy.
Matching process
As shown in Figure 5, a packet is compared against the proxy policy rules as follows:
1. The device compares the packet against the proxy policy rule with the highest priority.
The proxy policy rule can contain multiple filtering criteria types and each filtering criteria type can contain multiple filtering criteria. The packet matches a filtering criteria type if it matches any filtering criterion of the type.
2. The device determines that the packet matches the proxy policy rule if the packet matches each of following filtering criteria types in the rule:
¡ Source security zone.
¡ Destination security zone.
¡ Source IP address.
¡ Destinations IP address.
¡ Service.
¡ Either the user or user group filtering criteria type.
3. If the packet does not match the highest priority rule, the device continues the match process. The match process stops until a matching rule is found, and the action associated with the matching rule is applied.
4. If the packet does not match any rules in the proxy policy, the device applies the default action specified in the proxy policy to the packet.
Restrictions: Hardware compatibility with the proxy policy
|
Hardware platform |
Module type |
Proxy policy compatibility |
|
M9006 M9010 M9014 |
Blade 4 firewall module |
Yes |
|
Blade 5 firewall module |
No |
|
|
NAT module |
No |
|
|
M9010-GM |
Encryption module |
Yes |
|
M9016-V |
Blade 5 firewall module |
No |
|
M9008-S M9012-S |
Blade 4 firewall module |
Yes |
|
Intrusion prevention service (IPS) module |
Yes |
|
|
Video network gateway module |
Yes |
|
|
M9008-S-6GW |
IPv6 module |
Yes |
|
M9008-S-V |
Blade 4 firewall module |
Yes |
|
M9000-AI-E4 M9000-AI-E8 M9000-AI-E16 |
Blade 5 firewall module |
Yes |
|
M9000-X06 M9000-X10 |
Blade 6 firewall module |
Yes |
Restrictions and guidelines: Proxy policy configuration
· The TCP proxy and SSL proxy functions impact the device forwarding performance. When you configure proxy policy rules, refine the traffic filtering criteria to restrict application of the rules only to traffic that requires TCP or SSL proxy.
· Proxy policy rules are matched in descending order of their priorities. In the scenario that requires both TCP proxy and SSL decryption, make sure the proxy policy rule with the SSL decryption action has a higher priority than the rule with the TCP proxy action. This ensures that SSL traffic that requires SSL decryption can match the SSL decryption rule first.
· In the security policy to which the proxy policy is applied, make sure communications between the source security zones and the Local security zone are permitted. For more information about security zones, see security zone configuration in Security Configuration Guide.
· After the SSL proxy function is enabled, the packet capture action of the intrusion prevention system will be invalid. For more information about IPS, see "Configuring IPS."
· Select a protection service of the SSL decryption as required and import the corresponding certificates to the device for SSL connection establishment with the clients.
Proxy policy configuration procedure summary
Figure 6 shows how to configure the proxy policy.
Figure 6 Proxy policy configuration procedure
Proxy policy tasks at a glance
To configure the proxy policy:
1. Configuring attributes in the proxy policy
a. Setting the default action for the proxy policy
b. Creating a proxy policy rule
c. Configuring the traffic filtering criteria for a proxy policy rule
d. Setting the action for a proxy policy rule
2. (Optional.) Managing proxy policy rules
a. Changing the rule match order
b. Disabling a proxy policy rule
3. Configuring SSL decryption certificates
The SSL decryption certifications are required in the scenario of protecting internal clients.
a. Importing an SSL decryption certificate
b. (Optional.) Channing the credibility of an SSL decryption certificate
c. (Optional.) Deleting an SSL decryption certificate
4. Configuring internal server certificates
The internal server certificates are required in the scenario of protecting internal servers.
a. Importing an internal server certificate
b. (Optional.) Deleting an internal server certificate
5. (Optional.) Configuring the SSL proxy whitelist
a. Adding a hostname to the user-defined SSL hostname whitelist
b. Disabling hostnames on the predefined SSL hostname whitelist
c. Activating SSL hostname whitelist settings
Prerequisites for proxy policy configuration
Before you configure the proxy policy, complete the following tasks:
· Configure IP address object groups and service object groups. For more information, see object group configuration in Security Configuration Guide.
· Configure user and user groups. For more information, see user identification configuration in Security Configuration Guide.
· Configure security zones. For more information, see security zone configuration in Security Configuration Guide.
· Configure security policies. For more information, see security policy configuration in Security Configuration Guide.
· Configure DPI services. For more information, see DPI Configuration Guide.
Configuring attributes in the proxy policy
Setting the default action for the proxy policy
About this task
If a packet does not match any rules in the proxy policy or if the proxy policy does not contain any rules, the device applies the default action to the packet.
Procedure
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Set the default action for the proxy policy.
default action { no-proxy | ssl-decrypt | tcp-proxy }
By default, the device transmits packets that do not match any proxy policy rules directly without TCP or SSL proxy.
4. Specify an SSL decryption protection mode for the proxy policy.
default ssl-decrypt protect-mode { client | server }
By default, the SSL decryption protection mode of the proxy policy is client.
Creating a proxy policy rule
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Create a proxy policy rule and enter its view.
rule { rule-id | [ rule-id ] name rule-name }
Configuring the traffic filtering criteria for a proxy policy rule
Restrictions and guidelines
A proxy policy rule that does not contain any filtering criteria matches all packets.
A filtering criterion is ignored during packet matching if it is associated with a nonexistent or empty object group.
Procedure
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Enter the view of a proxy policy rule.
rule { rule-id | [ rule-id ] name rule-name }
4. Configure the traffic filtering criteria as needed:
¡ Configure a source security zone filtering criterion.
source-zone source-zone-name
By default, a proxy policy rule does not contain any source security zone filtering criterion.
¡ Configure a destination security zone filtering criterion.
destination-zone destination-zone-name
By default, a proxy policy rule does not contain any destination security zone filtering criterion.
¡ Configure a source IP address filtering criterion.
source-ip object-group object-group-name
By default, a proxy policy rule does not contain any source IP address filtering criterion.
¡ Configure a destination IP address filtering criterion.
destination-ip object-group object-group-name
By default, a proxy policy rule does not contain any destination IP address filtering criterion.
¡ Configure a service filtering criterion.
service object-group { object-group-name | any }
By default, a proxy policy rule does not contain any service filtering criterion.
¡ Configure a user filtering criterion.
user username [ domain domain-name ]
By default, a proxy policy rule does not contain any user filtering criterion.
¡ Configure a user group filtering criterion.
user-group user-group-name [ domain domain-name ]
By default, a proxy policy rule does not contain any user group filtering criterion.
Setting the action for a proxy policy rule
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Enter the view of a proxy policy rule.
rule { rule-id | [ rule-id ] name rule-name }
4. Set the action for traffic matching the proxy policy rule.
action { no-proxy | ssl-decrypt | tcp-proxy }
By default, the device transmits packets that match a proxy policy rule directly without TCP or SSL proxy.
5. Specify an SSL decryption protection mode for the proxy policy rule.
ssl-decrypt protect-mode { client | server }
By default, the SSL decryption protection mode of a proxy policy rule is client.
Configure this command only when the SSL decryption action is used as the default action for the proxy policy.
Managing proxy policy rules
Changing the rule match order
About this task
By default, proxy policy rules are matched in the order they were created. A rule created earlier has a higher priority. You can change the rule match order by rearranging proxy policy rules. The match process stops once a matching rule is found.
Procedure
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Move a proxy policy rule.
move rule rule-id before insert-rule-id
Disabling a proxy policy rule
1. Enter system view.
system-view
2. Enter proxy policy view.
app-proxy-policy
3. Enter the view of a proxy policy rule.
rule { rule-id | [ rule-id ] name rule-name }
4. Disable the proxy policy rule.
disable
By default, a proxy policy rule is enabled.
Configuring SSL decryption certificates
Importing an SSL decryption certificate
About this task
The SSL decryption certifications are required in the scenario of protecting internal clients.
Restrictions and guidelines
The device supports a maximum of one trusted SSL decryption certificate and one untrusted SSL decryption certificate. Both of them must be manually imported to the device.
If you import multiple trusted or multiple untrusted SSL decryption certificates to the device, the most recent configuration takes effect.
You must install the trusted SSL decryption certificate on the client browser so the client can trust proxy server certificates issued by using the trusted SSL decryption certificate.
After an SSL decryption certificate is imported, its file extension will be changed to .cer.
Procedure
1. Enter system view.
system-view
2. Import a CA certificate as a trusted or untrusted SSL decryption certificate to the device.
app-proxy ssl-decrypt-certificate import { trusted | untrusted } { pem | p12 } filename filename
Channing the credibility of an SSL decryption certificate
Restrictions and guidelines
The device supports only one trusted SSL decryption certificate and one untrusted SSL decryption certificate. A newly imported trusted or untrusted SSL decryption certificate will overwrite the existing one.
After an SSL decryption certificate is imported, its file extension will be changed to .cer. Append the .cer file extension when you specify the file containing the certificate whose credibility you want to change.
Procedure
1. Enter system view.
system-view
2. Change the credibility of an SSL decryption certificate.
app-proxy ssl-decrypt-certificate modify { trusted | untrusted } filename filename
Deleting an SSL decryption certificate
Restrictions and guidelines
The device, acting as an SSL proxy, requires the correct SSL decryption certificate to issue proxy server certificates to send to clients for server authentication. If the required SSL decryption certificate is not available, the device cannot set up a connection with the client and the SSL traffic will be transmitted directly without SSL decryption.
After an SSL decryption certificate is imported, its file extension will be changed to .cer, which must be appended to the file name when you delete the certificate.
Procedure
1. Enter system view.
system-view
2. Delete an SSL decryption certificate.
app-proxy ssl-decrypt-certificate delete filename filename
Configuring internal server certificates
Importing an internal server certificate
About this task
The internal server certifications are required in the scenario of protecting internal servers.
Restrictions and guidelines
Each internal server certificate stored in the device has a MD5 value. If the MD5 value of an internal server certificate to be imported is the same as that stored in the device, the new certificate will overwrite the old certificate.
Procedure
1. Enter system view.
system-view
2. Import an internal server certificate.
app-proxy internal-server-certificate import { p12 | pem } filename filename
Deleting an internal server certificate
About this task
When an internal server certificate expires or an internal server does not need to be protected, you can execute this command to delete the imported internal server certificate.
You can execute the display app-proxy imported internal-server-certificate command to view the MD5 values of the internal server certificates.
Procedure
1. Enter system view.
system-view
2. Delete an internal server certificate.
app-proxy internal-server-certificate delete md5 md5-value
Configuring the SSL proxy whitelist
Adding a hostname to the user-defined SSL hostname whitelist
About this task
In the scenario that requires SSL client authentication or in-depth server certificate inspection, SSL proxy will cause the device (as an SSL proxy) unable to pass SSL client or server verification. By adding the server's hostname to the SSL hostname whitelist, you can disable SSL proxy for connections destined for the server so the SSL traffic is transmitted directly without SSL decryption.
Procedure
1. Enter system view.
system-view
2. Add the hostname of a server to the user-defined SSL hostname whitelist.
app-proxy ssl whitelist user-defined-hostname host-name
By default, the user-defined SSL hostname whitelist does not contain any hostnames.
Disabling hostnames on the predefined SSL hostname whitelist
1. Enter system view.
system-view
2. Disable hostnames on the predefined SSL hostname whitelist.
undo app-proxy ssl whitelist predefined-hostname { chrome-hsts [ hostname ] | hostname } enable
By default, the entire predefined SSL hostname whitelist is enabled.
Activating SSL hostname whitelist settings
About this task
You must manually activate the SSL hostname whitelist settings for the following configurations to take effect:
· Adding or removing hostnames to or from the user-defined SSL hostname whitelist.
· Enabling or disabling hostnames on the predefined SSL hostname whitelist.
Procedure
1. Enter system view.
system-view
2. Activate SSL hostname whitelist configuration.
app-proxy ssl whitelist activate
Display and maintenance commands for the proxy policy
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display proxy policy information. |
display app-proxy-policy |
|
Display information about imported internal server certificates. |
display app-proxy imported internal-server-certificate |
|
Display SSL decryption certificate information. |
display app-proxy ssl-decrypt-certificate |
|
Display the SSL server certificates received by the device as the SSL proxy client. |
In standalone mode: display app-proxy server-certificate [ slot slot-number ] In IRF mode: display app-proxy server-certificate [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display the predefined or user-defined SSL hostname whitelist. |
display app-proxy ssl whitelist hostname { user-defined | predefined } |
|
Display IP addresses on the SSL IP address whitelist. |
In standalone mode: display app-proxy ssl whitelist { ipv4 | ipv6 } { all [ slot slot-number ] | ip-address } In IRF mode: display app-proxy ssl whitelist { ipv4 | ipv6 } { all [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] | ip-address } |
|
Clear information about the SSL server certificates received by the device as the SSL proxy client. |
reset app-proxy server-certificate |
|
Clear the SSL IP address whitelist. |
reset app-proxy ssl whitelist ip |
Proxy policy configuration examples
Example: Configuring the proxy policy
Network configuration
As shown in Figure 7, the device connects the LAN and the Internet. The LAN resides in security zone Trust and the Internet resides in security zone Untrust.
Configure the device to decrypt the HTTPS traffic and perform deep packet inspection on the traffic.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Create an IP address object group named obj1 and configure an IP address object with subnet 192.168.1.0/24.
[Device] object-group ip address obj1
[Device-obj-grp-ip-obj1] network subnet 192.168.1.0 24
[Device-obj-grp-ip-obj1] quit
5. Import CA certificate trust.pem as a trusted SSL decryption certificate and CA certificate untrust.pem as an untrusted SSL decryption certificate to the device.
[Device] app-proxy ssl-decrypt-certificate import trust pem filename trust.pem
[Device] app-proxy ssl-decrypt-certificate import untrust pem filename untrust.pem
6. Install CA certificate trust.pem on all internal hosts and set the CA certificate trust.pem as a trusted SSL decryption certificate. (Details not shown.)
7. Create proxy policy rule https to match HTTPS traffic from internal hosts destined for the Web server and set the action for traffic matching rule https to SSL decryption.
[Device] app-proxy-policy
[Device-app-proxy-policy] rule 1 name https
[Device-app-proxy-policy-rule-1-https] source-zone trust
[Device-app-proxy-policy-rule-1-https] destination-zone untrust
[Device-app-proxy-policy-rule-1-https] source-ip object-group obj1
[Device-app-proxy-policy-rule-1-https] service object-group https
[Device-app-proxy-policy-rule-1-https] action ssl-decrypt
[Device-app-proxy-policy-rule-1-https] quit
8. Configure URL filtering:
# Create user-defined URL category https, set its severity level to 1001, and create URL filtering rule 1 to match HTTPS packets that contain host name www. baidu.com in the URL.
[Device] url-filter category https severity 1001
[Device-url-filter-category-https] rule host text www.baidu.com
[Device-url-filter-category-https] quit
# Create a URL filtering policy named p1. Specify action drop for URL category https, enable logging for the matching packets.
[Device] url-filter policy p1
[Device-url-filter-policy-p1] category https action reset logging
[Device-url-filter-policy-p1] quit
9. Apply URL filtering policy p1 to a DPI application profile and activate the URL filtering policy settings:
# Create a DPI application profile named sec, and apply URL filtering policy p1 to the DPI application profile.
[Device] app-profile sec
[Device-app-profile-sec] url-filter apply policy p1
[Device-app-profile-sec] quit
# Activate the URL filtering policy and rule settings.
[Device] inspect activate
10. Configure a security policy:
# Create a security policy rule named trust-untrust to permit the packets from security zone Trust to security zone Untrust and to perform URL filtering on the packets.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] profile sec
[Device-security-policy-ip-10-trust-untrust] quit
# Create a security policy rule named untrust-trust to permit the packets from security zone Untrust to security zone Trust.
[Device] security-policy ip
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-11-untrust-trust] source-zone untrust
[Device-security-policy-ip-11-untrust-trust] destination-zone trust
[Device-security-policy-ip-11-untrust-trust] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-11-untrust-trust] action pass
[Device-security-policy-ip-11-untrust-trust] profile sec
[Device-security-policy-ip-11-untrust-trust] quit
# Create two security policy rules named proxyserverlocalin and proxyserverlocalout to permit the traffic between the Trust and Local security zones. Thus, the device can proxy the traffic from internal hosts destined for the Web server.
[Device-security-policy-ip] rule name proxyserverlocalin
[Device-security-policy-ip-12-proxyserverlocalin] source-zone trust
[Device-security-policy-ip-12-proxyserverlocalin] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-12-proxyserverlocalin] destination-zone local
[Device-security-policy-ip-12-proxyserverlocalin] action pass
[Device-security-policy-ip-12-proxyserverlocalin] quit
[Device-security-policy-ip] rule name proxyserverlocalout
[Device-security-policy-ip-13-proxyserverlocalout] source-zone local
[Device-security-policy-ip-13-proxyserverlocalout] destination-zone trust
[Device-security-policy-ip-13-proxyserverlocalout] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-13-proxyserverlocalout] action pass
[Device-security-policy-ip-13-proxyserverlocalout] quit
# Create two security policy rules named proxyclientlocalin and proxyclientlocalout to permit the traffic between the Untrust and Local security zones. Thus, the device can proxy the traffic from the Web server destined for internal hosts.
[Device-security-policy-ip] rule name proxyclientlocalin
[Device-security-policy-ip-14-proxyclientlocalin] source-zone untrust
[Device-security-policy-ip-14-proxyclientlocalin] destination-zone local
[Device-security-policy-ip-14-proxyclientlocalin] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-14-proxyclientlocalin] action pass
[Device-security-policy-ip-14-proxyclientlocalin] quit
[Device-security-policy-ip] rule name proxyclientlocalout
[Device-security-policy-ip-15-proxyclientlocalout] source-zone local
[Device-security-policy-ip-15-proxyclientlocalout] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-15-proxyclientlocalout] destination-zone untrust
[Device-security-policy-ip-15-proxyclientlocalout] action pass
[Device-security-policy-ip-15-proxyclientlocalout] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
Verifying the configuration
Verify that the device can deny HTTPS requests to www.baidu.com and generate logs. You can also execute the display app-proxy server-certificate command to view the following information:
· SSL server certificates received by the device as the SSL proxy client.
· Number of times connections to the server had been proxied.
· Most recent time the device proxied a connection to the server.
· First time the device proxied a connection to the server.