- Table of Contents
-
- 04-DPI Configuration Guide
- 00-Preface
- 01-DPI overview
- 02-DPI engine configuration
- 03-IPS configuration
- 04-URL filtering configuration
- 05-Data filtering configuration
- 06-File filtering configuration
- 07-Anti-virus configuration
- 08-Data analysis center configuration
- 09-WAF configuration
- 10-Proxy policy configuration
- 11-IP reputation configuration
- 12-Domain reputation configuration
- 13-APT defense configuration
- 14-DLP configuration
- 15-Content moderation configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-Domain reputation configuration | 104.54 KB |
Contents
Restrictions: Hardware compatibility with domain reputation
Restrictions: Licensing requirements for domain reputation
Domain reputation tasks at a glance
Enabling domain reputation globally
Specifying actions for an attack category
Specifying an exception domain name
Managing the domain reputation signature library
Scheduling automatic domain reputation signature library update
Triggering an immediate domain name signature update
Performing an domain name signature manual update
Rolling back the domain reputation signature library
Enabling the top hit ranking feature
Display and maintenance commands for domain reputation
Domain reputation configuration examples
Example: Configuring domain reputation
Configuring domain reputation
About domain reputation
The domain reputation feature uses domain names on the domain reputation signature library to filter network traffic. By matching the domain name in a DNS request packet with domain names in the signature library, the device enabled with the domain reputation feature can control network access behaviors of the users.
The signature library contains domain names with poor reputation, which are vulnerable to DDoS attacks, command injection attacks, Trojan virus download attacks, and port scan attacks. The signature library also contains the attack category and other attribute information for the domain name.
Domain reputation workflow
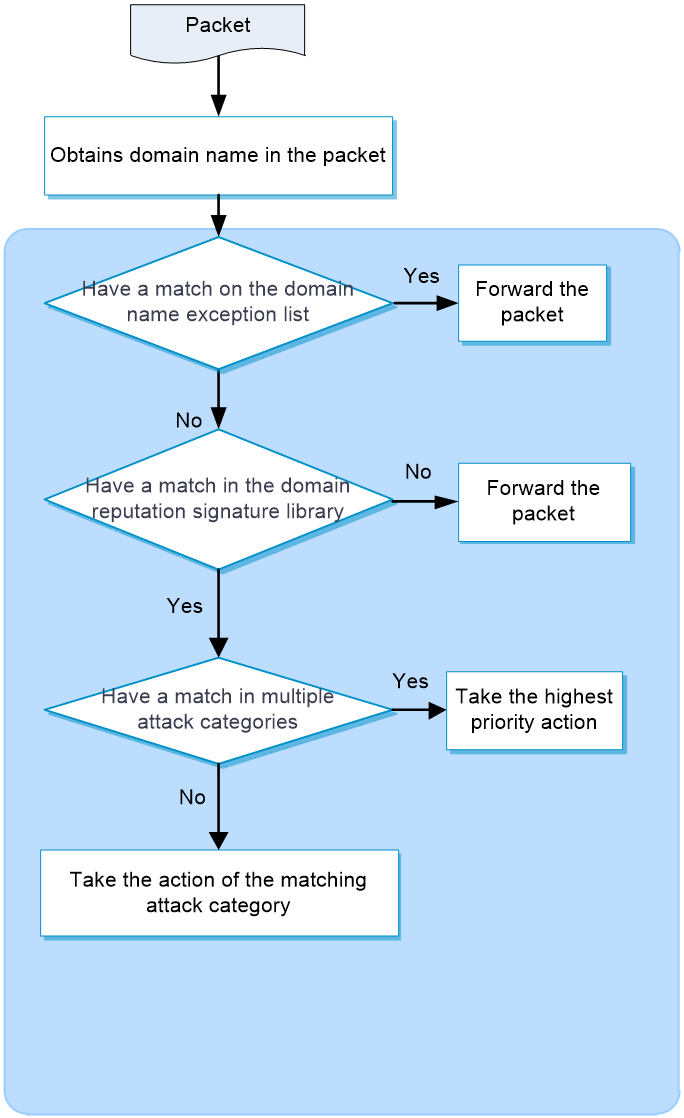
Figure 1 describes the domain reputation workflow.
Figure 1 domain reputation workflow
After receiving a packet, the device performs the following operations:
1. Determines whether the domain name of the packet matches an exception domain name.
¡ If a match is found, the device forwards the packet.
¡ If no match exists, the device proceeds to the next step.
2. Determines whether the domain name of the packet matches a domain name on the domain reputation signature library.
¡ If the domain name belongs to only one attack category, the device takes the actions in this attack category.
¡ If the domain name belongs to multiple attack categories, the device takes an action that has higher priority among all actions in those attack categories.
The device supports the following actions:
- Permit—Allows packets to pass through.
- Drop—Drops packets.
- Logging—Generates domain reputation logs for the matching domain name.
Restrictions: Hardware compatibility with domain reputation
|
Hardware platform |
Module type |
Domain reputation compatibility |
|
M9006 M9010 M9014 |
Blade IV firewall module |
Yes |
|
Blade V firewall module |
No |
|
|
NAT module |
No |
|
|
M9010-GM |
Encryption module |
Yes |
|
M9016-V |
Blade V firewall module |
No |
|
M9008-S M9012-S |
Blade IV firewall module |
Yes |
|
Intrusion prevention service (IPS) module |
Yes |
|
|
Video network gateway module |
Yes |
|
|
M9008-S-6GW |
IPv6 module |
Yes |
|
M9008-S-V |
Blade IV firewall module |
Yes |
|
M9000-AI-E4 M9000-AI-E8 M9000-AI-E16 |
Blade V firewall module |
Yes |
|
M9000-X06 M9000-X10 |
Blade VI firewall module |
Yes |
Restrictions: Licensing requirements for domain reputation
The domain reputation feature requires a license to run on the device. If the license expires, you can still use the domain reputation feature but you can no longer upgrade the domain reputation signature library on the device. For more information about licenses, see license management in Fundamentals Configuration Guide.
Domain reputation tasks at a glance
To configure domain reputation, perform the following tasks:
1. Enabling domain reputation globally
2. Specifying actions for an attack category
3. (Optional.) Specifying actions for an attack category
4. Managing the domain reputation signature library
5. (Optional.) Enabling the top hit ranking feature
Enabling domain reputation globally
About this task
This feature identifies packets based on the domain name on the reputation signature library and processes the matching packets based on the attack category of the domain name.
Procedure
1. Enter system view.
system-view
2. Enter domain reputation view.
domain-reputation
3. Enable domain reputation globally.
global enable
By default, domain reputation is disabled globally.
Specifying actions for an attack category
About this task
On the domain reputation list, a domain name can belong to multiple attack categories. Each attack category has its own actions.
If a domain name belongs to only one attack category, the device takes the actions in this attack category. If a domain name belongs to multiple attack categories, the device takes an action that has higher priority among all actions in those attack categories. The drop action has higher priority than the permit action.
If logging is enabled for one of attack categories to which a domain name belongs, the device generates a log when the domain name is matched.
The device supports fast output of domain reputation logs. For more information about fast log output, see fast log output configuration in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter domain reputation view.
domain-reputation
3. Specify actions for an attack category.
attack-category attack-id { action { deny | permit } | logging { disable | enable } } *
By default, no actions are configured for an attack category and the device allows the matching packets to pass through and generates logs for the matching events.
Specifying an exception domain name
About this task
If you trust some domain names and do not want the device to perform domain reputation inspection on them, you can configure those domain names as exceptions.
The device forwards a DNS packet if the domain name of the packet is an exception domain name.
Procedure
1. Enter system view.
system-view
2. Enter domain reputation view.
domain-reputation
3. Specify an exception domain name.
exception domain domain-name
By default, no exception domain name is specified.
Managing the domain reputation signature library
Restrictions and guidelines
· Do not delete the /dpi/ folder in the root directory of the storage medium.
· Do not perform update or rollback of the domain reputation signature library when the device's free memory is below the normal state threshold. For more information about device memory thresholds, see device management in Fundamentals Configuration Guide.
· For successful automatic and immediate signature library update, make sure the device can resolve the domain name of the company's website into an IP address through DNS. For more information about DNS, see DNS configuration in Layer 3—IP Services Configuration Guide.
· Update only one signature library at a time. Do not perform signature library update until the existing signature library update is completed.
Scheduling automatic domain reputation signature library update
About this task
You can schedule automatic domain reputation signature library update if the device can access the signature database services on the official website to update its local signature library according to the update schedule.
Procedure
1. Enter system view.
system-view
2. Enable automatic update of the domain reputation signature library and enter automatic domain reputation signature library update configuration view.
domain-reputation signature auto-update
By default, automatic update of the domain reputation signature library is disabled.
3. Schedule the update time.
update schedule { daily | weekly { fri | mon | sat | sun | thu | tue | wed } } start-time time tingle minutes
By default, the device starts updating the domain reputation signature library at a random time between 01:00:00 and 03:00:00 every day.
Triggering an immediate domain name signature update
About this task
Anytime you find a release of new signature library version on the official website, you can trigger the device to immediately update the local signature library.
After you execute this command, the device immediately starts the automatic update process of the domain reputation signature library no matter whether or not automatic signature library update is enabled. The device automatically backs up the current signature library before overwriting it.
Procedure
1. Enter system view.
system-view
2. Trigger an immediate domain reputation signature library update.
domain-reputation signature auto-update-now
Performing an domain name signature manual update
About this task
If the device cannot access the signature database services on the official website, use one of the following methods to manually update the domain reputation signature library on the device:
· Local update—Updates the domain reputation signature library by using a locally stored domain reputation signature library file. To use this method, first obtain the signature library file from the official website and import it to the device.
(In standalone mode.) Store the update file on the active MPU for successful signature library update.
(In IRF mode.) Store the update file on the global active MPU for successful signature library update.
· FTP/TFTP update—Updates the domain reputation signature library by using the file stored on an FTP or TFTP server.
Procedure
1. Enter system view.
system-view
2. Manually update the domain reputation signature library on the device.
domain-reputation signature update file-path
Rolling back the domain reputation signature library
About this task
If a domain reputation signature library update causes exceptions or a high false alarm rate, you can roll back the domain reputation signature library.
Before performing a domain reputation signature library rollback, the device backs up the current domain reputation signature library as the previous version. For example, the previous library version is V1 and the current library version is V2. If you perform a rollback to the previous version, library version V1 becomes the current version and library version V2 becomes the previous version. If you perform a rollback to the previous version again, the library rolls back to library version V2.
Procedure
1. Enter system view.
system-view
2. Roll back the domain reputation signature library to the previous version.
domain-reputation signature rollback last
Enabling the top hit ranking feature
About this task
This feature enables the device to collect hit statistics for domain names on the domain reputation signature library and rank them. After you disable this feature, the device clears hit statistics for domain reputation.
Procedure
1. Enter system view.
system-view
2. Enter domain reputation view.
domain-reputation
3. Enabling the top hit ranking feature.
top-hit-statistics enable
By default, the top hit ranking feature is disabled.
Display and maintenance commands for domain reputation
Execute display commands in any view.
|
Task |
Command |
|
Display information about attack categories for domain reputation. |
display domain-reputation attack-category |
|
Display exception domain names. |
display domain-reputation exception |
|
Display information about domain reputation signature library |
display domain-reputation signature library |
|
Display statistics for domain names with the highest hits on the domain reputation list. |
In standalone mode: display domain-reputation top-hit-statistics [ top-number ] [ slot slot-id [ cpu cpu-nunmber ] ] In IRF mode: display domain-reputation top-hit-statistics [ top-number ] [chassis chassis-number slot slot-id [ cpu cpu-nunmber ] ] |
|
Display domain reputation information about a domain name. |
display domain-reputation domain domain-name |
Domain reputation configuration examples
Example: Configuring domain reputation
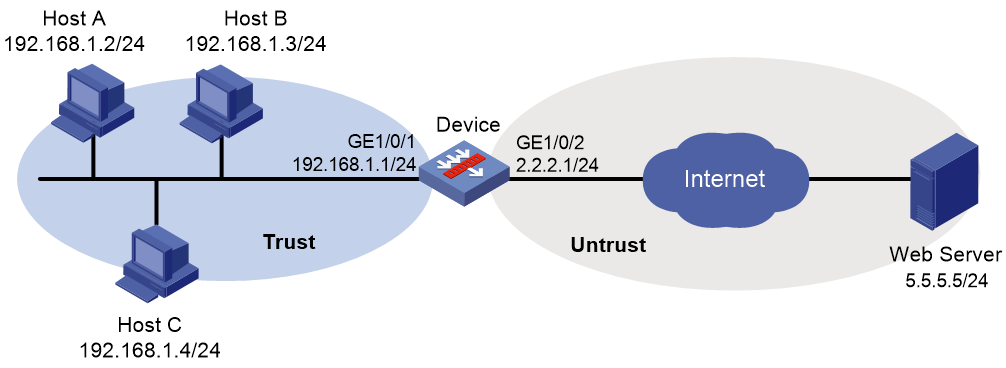
Network configuration
As shown in Figure 2, the device connects to the LAN and Internet through security zones Trust and Untrust, respectively. Configure domain reputation on the device to control the illegal domain name requests of various departments.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures a static route to reach the Web server, and the next hop in the route is 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Configure a security policy:
# Enter IPv4 security policy view. Create a rule named trust-untrust to allow the internal users to access the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
5. Configure domain reputation:
# Enable domain reputation.
[Device] domain-reputation
[Device-domain-reputation] global enable
# Enable the top hit ranking feature.
[Device-domain-reputation] top-hit-statistics enable
# Specify actions deny and logging for attack category 1.
[Device-domain-reputation] attack-category 1 action deny logging enable
Verifying the configuration
# Verify that the device drops packets that match attack category 1 and generates logs for domain names that are matched. You can view the top hit ranks for IP addresses on the domain reputation list on the Web interface. (Details not shown.)