- Table of Contents
-
- 09-Network Management Configuration Guide
- 00-Preface
- 01-System Maintenance and Debugging Configuration
- 02-NQA Configuration
- 03-NTP Configuration
- 04-IPC Configuration
- 05-SNMP Configuration
- 06-RMON Configuration
- 07-Mirroring Configuration
- 08-Information Center Configuration
- 09-sFlow Configuration
- 10-Flow Log Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-SNMP Configuration | 174.99 KB |
MIB and view-based MIB access control
Configuring SNMP basic parameters
Configuring SNMPv3 basic parameters
Configuring SNMPv1 or SNMPv2c basic parameters
Configuring the SNMP agent to send traps to a host
Setting the sampling interval and statistics interval for certain MIB nodes
Configuring the SNMP proxy agent for an SNMP agent
Displaying and maintaining SNMP
SNMPv1/SNMPv2c configuration example
SNMP logging configuration example
SNMP proxy agent configuration example
Displaying and maintaining MIB style
Configuring SNMP
This chapter provides an overview of the Simple Network Management Protocol (SNMP) and guides you through the configuration procedure.
Overview
SNMP is an Internet standard protocol widely used for a management station to access and operate the devices on a network, regardless of their vendors, physical characteristics, and interconnect technologies.
SNMP enables network administrators to read and set the variables on managed devices for state monitoring, troubleshooting, statistics collection, and other management purposes.
SNMP framework
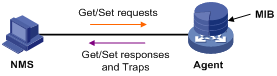
The SNMP framework comprises the following elements:
· SNMP manager—Works on an NMS to monitor and manage the SNMP-capable devices in the network.
· SNMP agent—Works on a managed device to receive and handle requests from the NMS, and sends traps to the NMS when some events, such as an interface state change, occur.
· Management Information Base (MIB)—Specifies the variables (for example, interface status and CPU usage) maintained by the SNMP agent for the SNMP manager to read and set.
Figure 1 Relationship between an NMS, agent and MIB
MIB and view-based MIB access control
A MIB stores variables called "nodes" or "objects" in a tree hierarchy and identifies each node with a unique OID. An OID is a string of numbers that describes the path from the root node to a leaf node. For example, object B in Figure 2 is uniquely identified by the OID {1.2.1.1}.
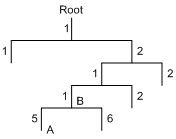
A MIB view represents a set of MIB objects (or MIB object hierarchies) with certain access privileges and is identified by a view name. The MIB objects included in the MIB view are accessible, and those excluded from the MIB view are inaccessible.
A MIB view can have multiple view records each identified by a view-name oid-tree pair.
You control access to the MIB by assigning MIB views to SNMP groups or communities.
SNMP operations
SNMP provides the following basic operations:
· Get—The NMS retrieves SNMP object nodes in an agent MIB.
· Set—The NMS modifies the value of an object node in an agent MIB.
· Notifications—Includes traps and informs. An SNMP agent sends traps or informs to report events to the NMS. The difference between these two types of notifications is that informs require acknowledgement but traps do not. The device supports only traps.
SNMP protocol versions
H3C supports SNMPv1, SNMPv2c, and SNMPv3. An NMS and an SNMP agent must use the same SNMP version to communicate with each other.
· SNMPv1—Uses community names for authentication. To access an SNMP agent, an NMS must use the same community name as the one that is set on the SNMP agent. If the community name used by the NMS is different from that set on the agent, the NMS cannot establish an SNMP session to access the agent or receive traps from the agent.
· SNMPv2c—Uses community names for authentication. SNMPv2c is compatible with SNMPv1 but supports more operation modes, data types, and error codes.
· SNMPv3—Uses a user-based security model (USM) to secure SNMP communication. You can configure authentication and privacy mechanisms to authenticate and encrypt SNMP packets for integrity, authenticity, and confidentiality.
SNMP configuration task list
|
Task |
Remarks |
|
Required. |
|
|
Optional. |
|
|
Optional. |
|
|
Setting the sampling interval and statistics interval for certain MIB nodes |
Optional. |
|
Optional. |
Configuring SNMP basic parameters
SNMPv3 differs from SNMPv1 and SNMPv2c in many ways. Their configuration procedures are described in separate sections.
Configuring SNMPv3 basic parameters
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the SNMP agent. |
snmp-agent |
Optional. By default, the SNMP agent is disabled. You can also enable the SNMP agent by using any command that begins with snmp-agent except for the snmp-agent calculate-password command. |
|
3. Configure system information for the SNMP agent. |
snmp-agent sys-info { contact sys-contact | location sys-location | version { all | { v1 | v2c | v3 }* } } |
Optional. The defaults are as follows: · Contact—New H3C Technologies Co., Ltd.. · Location—Hangzhou China. · Version—SNMPv3. |
|
4. Configure the local engine ID. |
snmp-agent local-engineid engineid |
Optional. The default local engine ID is the company ID plus the device ID. After you change the local engine ID, the existing SNMPv3 users become invalid, and you must re-create the SNMPv3 users. |
|
5. Create or update a MIB view. |
snmp-agent mib-view { excluded | included } view-name oid-tree [ mask mask-value ] |
Optional. By default, the MIB view ViewDefault is predefined and its OID is 1. Each view-name oid-tree pair represents a view record. If you specify the same record with different MIB subtree masks multiple times, the last configuration takes effect. Except for the four subtrees in the default MIB view, you can create up to 16 unique MIB view records. |
|
6. Configure an SNMPv3 group. |
snmp-agent group v3 group-name [ authentication | privacy ] [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
By default, no SNMP group exists. |
|
7. Convert a plaintext key to a ciphertext (encrypted) key. |
snmp-agent calculate-password plain-password mode { 3desmd5 | 3dessha | md5 | sha } { local-engineid | specified-engineid engineid } |
Optional. The 3des and md5 keywords are supported only in non-FIPS mode. Only the sha keyword is supported in FIPS mode. |
|
8. Add a user to the SNMPv3 group. |
snmp-agent usm-user v3 user-name group-name [ [ cipher ] authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
The md5, des56, and 3des keywords are supported only in non-FIPS mode. |
|
9. Configure the maximum SNMP packet size (in bytes) that the SNMP agent can handle. |
snmp-agent packet max-size byte-count |
Optional. By default, the maximum SNMP packet size that the SNMP agent can handle is 2000 bytes. |
Configuring SNMPv1 or SNMPv2c basic parameters
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the SNMP agent. |
snmp-agent |
Optional. By default, the SNMP agent is disabled. You can also enable the SNMP agent service by using any command that begins with snmp-agent except for the snmp-agent calculate-password command. |
|
3. Configure system information for the SNMP agent. |
snmp-agent sys-info { contact sys-contact | location sys-location | version { all |{ v1 | v2c | v3 }* } } |
The defaults are as follows: · Contact—New H3C Technologies Co., Ltd.. · Location—Hangzhou China. · Version—SNMPv3. |
|
4. Configure the local engine ID. |
snmp-agent local-engineid engineid |
Optional. The default local engine ID is the company ID plus the device ID. |
|
5. Create or update a MIB view. |
snmp-agent mib-view { excluded | included } view-name oid-tree [ mask mask-value ] |
Optional. By default, the MIB view ViewDefault is predefined and its OID is 1. Each view-name oid-tree pair represents a view record. If you specify the same record with different MIB subtree masks multiple times, the last configuration takes effect. Except for the four subtrees in the default MIB view, you can create up to 16 unique MIB view records. |
|
6. Configure the SNMP access right. |
· (Approach 1.) Create an SNMP community: · (Approach 2.) Create an SNMP group, and add a user to the SNMP group: a. snmp-agent group { v1 | v2c } group-name [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * b. snmp-agent usm-user { v1 | v2c } user-name group-name [ acl acl-number | acl ipv6 ipv6-acl-number ] * |
Use either approach. By default, no SNMP group exists. In approach 2, the username is equivalent to the community name in approach 1, and must be the same as the community name configured on the NMS. |
|
7. Configure the maximum SNMP packet size (in bytes) that the SNMP agent can handle. |
snmp-agent packet max-size byte-count |
Optional. By default, the maximum SNMP packet size that the SNMP agent can handle is 2000 bytes. |
Configuring SNMP logging
If the device is operating correctly, disable SNMP logging to prevent a large amount of SNMP logs from decreasing device performance.
The SNMP logging function logs Get requests, Set requests, and Set responses, but does not log Get responses.
· Get operation—The agent logs the IP address of the NMS, name of the accessed node, and node OID.
· Set operation—The agent logs the NMS IP address, name of accessed node, node OID, variable value, and error code and index for the Set operation.
The SNMP module sends these logs to the information center as informational messages. You can configure the information center to output these messages to certain destinations (for example, the console and the log buffer). The total output size for the node field (MIB node name) and the value field (value of the MIB node) in each log entry is 1024 bytes. If this limit is exceeded, the information center truncates the data in the fields. For more information about the information center, see "Configuring the information center."
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP logging. |
snmp-agent log { all | get-operation | set-operation } |
By default, SNMP logging is disabled. |
Configuring SNMP traps
The SNMP agent sends traps to inform the NMS of important events, such as a reboot.
Traps are divided into generic traps and vendor-specific traps. Available generic traps include authentication, coldstart, linkdown, linkup and warmstart. All other traps are vendor-defined.
SNMP traps generated by a module are sent to the information center. You can configure the information center to enable or disable outputting the traps from a module by severity and set output destinations. For more information about the information center, see "Configuring the information center."
Enabling SNMP traps
Enable SNMP traps only if necessary. SNMP traps are memory-intensive and might affect device performance.
To generate linkUp or linkDown traps when the link state of an interface changes, enable the linkUp or linkDown trap function both globally by using the snmp-agent trap enable [ standard [ linkdown | linkup ] * ] command and on the interface by using the enable snmp trap updown command.
After you enable a trap function for a module, whether the module generates traps also depends on the configuration of the module. For more information, see the configuration guide for each module.
To enable traps:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable traps globally. |
snmp-agent trap enable [ arp rate-limit | configuration | default-route | flash | standard [ authentication | coldstart | linkdown | linkup | warmstart ]* | system | vrrp [ authfailure | newmaster ] | wlan ] |
By default, the trap function of all modules is enabled. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable link state traps. |
enable snmp trap updown |
By default, the link state traps are enabled. |
Configuring the SNMP agent to send traps to a host
The SNMP module buffers the traps received from a module in a trap queue. You can set the size of the queue, the duration that the queue holds a trap, and trap target (destination) hosts, typically the NMS.
To successfully send traps, you must also perform the following tasks:
· Complete the basic SNMP settings and verify that they are the same as those on the NMS. If SNMPv1 or SNMPv2c is used, you must configure a community name. If SNMPv3 is used, you must configure an SNMPv3 user and MIB view.
· Make sure the device and the NMS can reach each other.
To configure the SNMP agent to send traps to a host:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a target host. |
snmp-agent target-host trap address udp-domain { ip-address | ipv6 ipv6-address } [ udp-port port-number ] params securityname security-string [ v1 | v2c | v3 [ authentication | privacy ] ] |
To send traps to a host, you must perform this step to specify its IP address. |
|
3. Configure the source address for traps. |
snmp-agent trap source interface-type interface-number |
Optional. By default, SNMP chooses the IP address of an interface to be the source IP address of traps. |
|
4. Extend the standard linkUp/linkDown traps. |
snmp-agent trap if-mib link extended |
Optional. By default, standard linkUp/linkDown traps are used. Extended linkUp/linkDown traps add interface description and interface type to standard linkUp/linkDown traps. If the NMS does not support extended SNMP messages, use standard linkUp/linkDown traps. |
|
5. Configure the trap queue size. |
snmp-agent trap queue-size size |
Optional. The default trap queue size is 1000. When the trap queue is full, the oldest traps are automatically deleted for new traps. |
|
6. Configure the trap holding time. |
snmp-agent trap life seconds |
Optional. The default setting is 120 seconds. A trap is deleted when its holding time expires. |
|
7. Configure the maximum number of traps that the SNMP agent can send for an alarm condition. |
trap-send times timevalue |
Optional. The default is 0, which indicates that no limit is set on the number of traps that can be sent for an alarm condition. |
Setting the sampling interval and statistics interval for certain MIB nodes
By default, the system does not calculate statistics for certain MIB nodes, including 3cDot11AvgRxSignalStrength, h3cDot11HighestRxSignalStrength, h3cDot11LowestRxSignalStrength, h3cEntityExtCpuAvgUsage, and h3cEntityExtMemAvgUsage. To periodically calculate statistics for these MIB nodes, you need to set a sampling interval and a statistics interval.
The system polls data at sampling intervals, and uses the collected data to calculate the values of the MIB nodes for each statistics interval. For example, set the statistics interval to 5 seconds and the sampling interval to 2 seconds. Then, the system collects CPU usage data twice for each statistics interval, and set the MIB node h3cEntityExtCpuAvgUsage to the average of the two sampling values.
To set the sampling interval and statistics interval for calculating statistics for the MIB nodes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the sampling interval. |
sample-interval sample-interval |
By default, the sampling interval is 0, and the system does not sample data for calculating statistics for the MIB nodes. |
|
3. Set the statistics interval. |
statistics-interval statistics-interval |
By default, the statistics interval is 0, and the system does not calculate statistics for the MIB nodes. |
To make sure the system performs at least one data poll for each statistics interval, set the statistics interval equal to or greater than the sampling interval.
Configuring the SNMP proxy agent for an SNMP agent
|
|
NOTE: Support for this feature depends on the device model. For more information about the feature matrixes, see About the H3C Access Controllers Configuration Guides. |
The SNMP proxy agent function is designed for access controllers installed with a SecBlade IAG card. The function enables the access controller to communicate with the SNMP NMS on behalf of the SecBlade IAG card and transparently forwards SNMP messages to the SecBlade IAG card. From the perspective of the SNMP NMS, the access controller and the SecBlade IAG card appear as if they were one managed node.
An access controller can work as the SNMP proxy agent for only one device.
To use this function, you must set up a tunnel between the SNMP proxy agent and the SNMP agent by using the Inter AC Tunneling Protocol mobility group feature. For more information about the IACTP mobility group, see WLAN Configuration Guide.
To configure the SNMP proxy agent for an SNMP agent:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the SNMP proxy agent for an SNMP agent. |
snmp-agent proxy { ip ipv4-address | ipv6 ipv6-address } |
By default, the SNMP proxy agent function is disabled. |
Displaying and maintaining SNMP
|
Command |
Remarks |
|
|
Display SNMP agent system information, including the contact, physical location, and SNMP version. |
display snmp-agent sys-info [ contact | location | version ]* [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display SNMP agent statistics. |
display snmp-agent statistics [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the local engine ID. |
display snmp-agent local-engineid [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display SNMP group information. |
display snmp-agent group [ group-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display basic information about the trap queue. |
display snmp-agent trap queue [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the modules that can send traps and their trap status (enable or disable). |
display snmp-agent trap-list [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display SNMPv3 user information. |
display snmp-agent usm-user [ engineid engineid | username user-name | group group-name ] * [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display SNMPv1 or SNMPv2c community information. |
display snmp-agent community [ read | write ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display MIB view information. |
display snmp-agent mib-view [ exclude | include | viewname view-name ] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
SNMP configuration examples
SNMPv1/SNMPv2c configuration example
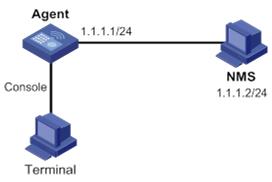
Network requirements
As shown in Figure 3, the NMS (1.1.1.2/24) uses SNMPv1 or SNMPv2c to manage the AC (1.1.1.1/24), and the AC automatically sends traps to report events to the NMS.

Configuration procedure
1. Configure the AC:
# Configure the IP address of the AC as 1.1.1.1/24, and make sure the AC and the NMS can reach each other. (Details not shown.)
# Specify SNMPv1 and SNMPv2c, and create a read-only community public and a read and write community private.
<AC> system-view
[AC] snmp-agent sys-info version v1 v2c
[AC] snmp-agent community read public
[AC] snmp-agent community write private
# Configure contact and physical location information for the AC.
[AC] snmp-agent sys-info contact Mr.Wang-Tel:3306
[AC] snmp-agent sys-info location telephone-closet,3rd-floor
# Enable SNMP traps, set the NMS at IP address 1.1.1.2/24 as an SNMP trap destination, and use public as the community name. (To make sure the NMS can receive traps, specify the same SNMP version in the snmp-agent target-host command as on the NMS.)
[AC] snmp-agent trap enable
[AC] snmp-agent target-host trap address udp-domain 1.1.1.2 udp-port 5000 params securityname public v1
2. Configure the SNMP NMS:
# Configure the SNMP version for the NMS as v1 or v2c, create the read-only community public, and create the read and write community private. For more information about configuring the NMS, see the NMS manual.
|
|
NOTE: The SNMP settings on the AC and the NMS must match. |
3. Verify the configuration:
# Try to get the count of sent traps from the AC. The attempt succeeds.
Send request to 1.1.1.1/161 ...
Protocol version: SNMPv1
Operation: Get
Request binding:
1: 1.3.6.1.2.1.11.29.0
Response binding:
1: Oid=snmpOutTraps.0 Syntax=CNTR32 Value=18
Get finished
# Use a wrong community name to get the value of a MIB node from the AC. You can see an authentication failure trap on the NMS.
1.1.1.1/2934 V1 Trap = authenticationFailure
SNMP Version = V1
Community = public
Command = Trap
Enterprise = 1.3.6.1.4.1.43.1.16.4.3.50
GenericID = 4
SpecificID = 0
Time Stamp = 8:35:25.68
SNMPv3 configuration example
Network requirements
As shown in Figure 4, the NMS (1.1.1.2/24) uses SNMPv3 to monitor and manage the interface status of the agent (1.1.1.1/24), and the agent automatically sends traps to report events to the NMS.
The NMS and the agent perform authentication when they set up an SNMP session. The authentication algorithm is MD5, and the authentication key is authkey. The NMS and the agent also encrypt the SNMP packets between them by using the DES algorithm and the privacy key prikey.

Configuration procedure
1. Configure the agent:
# Configure the IP address of the agent and make sure the agent and the NMS can reach each other. (Details not shown.)
# Assign the NMS read and write access to the objects under the SNMP node (OID 1.3.6.1.2.1.11), and deny its access to any other MIB object.
<AC> system-view
[AC] undo snmp-agent mib-view ViewDefault
[AC] snmp-agent mib-view included test snmp
[AC] snmp-agent group v3 managev3group read-view test write-view test
# Set the username to managev3user, authentication algorithm to MD5, authentication key to authkey, encryption algorithm to DES56, and privacy key to prikey.
[AC] snmp-agent usm-user v3 managev3user managev3group authentication-mode md5 authkey privacy-mode des56 prikey
# Configure contact person and physical location information for the agent.
[AC] snmp-agent sys-info contact Mr.Wang-Tel:3306
[AC] snmp-agent sys-info location telephone-closet,3rd-floor
# Enable traps, specify the NMS at 1.1.1.2 as a trap destination, and set the username to managev3user for the traps.
[AC] snmp-agent trap enable
[AC] snmp-agent target-host trap address udp-domain 1.1.1.2 params securityname managev3user v3 privacy
2. Configure the SNMP NMS:
¡ Specify the SNMP version for the NMS as v3.
¡ Create two SNMP users: managev3user and public.
¡ Enable both authentication and privacy functions.
¡ Use MD5 for authentication and DES for encryption.
¡ Set the authentication key to authkey and the privacy key to prikey.
¡ Set the timeout time and maximum number of retries.
For information about configuring the NMS, see the NMS manual.
|
|
NOTE: The SNMP settings on the agent and the NMS must match. |
3. Verify the configuration:
# Try to get the count of sent traps from the agent. The get attempt succeeds.
Send request to 1.1.1.1/161 ...
Protocol version: SNMPv3
Operation: Get
Request binding:
1: 1.3.6.1.2.1.11.29.0
Response binding:
1: Oid=snmpOutTraps.0 Syntax=CNTR32 Value=18
Get finished
# Try to get the device name from the agent. The get attempt fails because the NMS has no access right to the node.
Send request to 1.1.1.1/161 ...
Protocol version: SNMPv3
Operation: Get
Request binding:
1: 1.3.6.1.2.1.1.5.0
Response binding:
1: Oid=sysName.0 Syntax=noSuchObject Value=NULL
Get finished
# Execute the shutdown or undo shutdown command on an idle interface on the agent. You can see the interface state change traps on the NMS:
1.1.1.1/3374 V3 Trap = linkdown
SNMP Version = V3
Community = managev3user
Command = Trap
1.1.1.1/3374 V3 Trap = linkup
SNMP Version = V3
Community = managev3user
Command = Trap
SNMP logging configuration example
Network requirements
Configure the SNMP agent (1.1.1.1/24) in Figure 5 to log the SNMP operations performed by the NMS.
Configuration procedure
This example assumes that you have configured all required SNMP settings for the NMS and the agent (see "SNMPv1/SNMPv2c configuration example" or "SNMPv3 configuration example").
# Enable displaying log messages on the configuration terminal. (This function is enabled by default. Skip this step if you are using the default.)
<AC> terminal monitor
<AC> terminal logging
# Enable the information center to output system information with severity level equal to or higher than informational to the console port.
<AC> system-view
[AC] info-center source snmp channel console log level informational
# Enable logging GET and SET operations.
[AC] snmp-agent log all
# Verify the configuration:
Use the NMS to get a MIB variable from the agent. The following is a sample log message displayed on the configuration terminal:
%Nov 23 16:10:09:482 2011 Agent SNMP/6/SNMP_GET: -seqNO=27-srcIP=1.1.1.2-op=GET-node=sysUpTime(1.3.6.1.2.1.1.3.0)-value=-node=ifHCOutOctets(1.3.6.1.2.1.31.1.1.1.10.1)-value=; The agent received a message.
Use the NMS to set a MIB variable on the agent. The following is a sample log message displayed on the configuration terminal:
%Nov 23 16:16:42:581 2011 Agent SNMP/6/SNMP_SET: -seqNO=37-srcIP=1.1.1.2-op=SET-errorIndex=0-errorStatus=noError-node=sysLocation(1.3.6.1.2.1.1.6.0)-value=beijing; The agent received a message.
Table 1 SNMP log message field description
|
Field |
Description |
|
Nov 23 16:10:09:482 2011 |
Time when the SNMP log was generated. |
|
seqNO |
Serial number automatically assigned to the SNMP log, starting from 0. |
|
srcIP |
IP address of the NMS. |
|
op |
SNMP operation type (GET or SET). |
|
node |
MIB node name and OID of the node instance. |
|
errorIndex |
Error index, with 0 meaning no error. |
|
errorStatus |
Error status, with noError meaning no error. |
|
value |
Value set by the SET operation. This field is null for a GET operation. If the value is a character string that has invisible characters or characters beyond the ASCII range 0 to 127, the string is displayed in hexadecimal format (for example, value = <81-43>[hex]). |
The information center can output system event messages to several destinations, including the terminal and the log buffer. In this example, SNMP log messages are output to the terminal. To configure other message destinations, see "Configuring the information center."
SNMP proxy agent configuration example
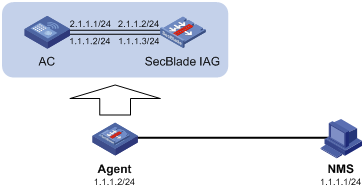
Network requirements
· As shown in Figure 6, configure the SNMP proxy agent function on the AC installed with an H3C SecBlade IAG card.
· The AC communicates with the SNMP NMS on behalf of the SecBlade IAG card. The NMS manages both the AC and the H3C SecBlade IAG card.
· The IP address of NMS is 1.1.1.1/24.
· The AC has two subinterfaces (1.1.1.2/24 and 2.1.1.1/24) connected to two subinterfaces (1.1.1.3/24 and 2.1.1.2/24) on the H3C SecBlade IAG card.
Configuration procedure
This configuration example assumes that you have configured all required SNMP settings for the NMS and the agent (see "SNMPv1/SNMPv2c configuration example" and "SNMPv3 configuration example").
For information about the IACTP mobility group, see WLAN Configuration Guide.
1. Configure the SNMP NMS:
# Assign the NMS the IP address 1.1.1.1/24 and make sure active routes are available between the NMS and the subinterface (1.1.1.2/24) on the agent. (Details not shown.)
2. Configure the agent (the AC):
# Assign one subinterface on the agent the IP address 1.1.1.2/24. Make sure active routes are available between this subinterface and the subinterface (1.1.1.3/24) on the NMS, and between this subinterface and the subinterface (1.1.1.3/24) on H3C SecBlade IAG card. Assign the other subinterface on the agent the IP address 2.1.1.1/24. Make sure active routes are available between this subinterface and the subinterface (2.1.1.2/24) on H3C SecBlade IAG card. (Details not shown.)
# Configure the mobility group abc.
<AC> system-view
[AC] wlan mobility-group abc
[AC-wlan-mg-abc] member ip 2.1.1.2
[AC-wlan-mg-abc] source ip 2.1.1.1
[AC-wlan-mg-abc] mobility-group enable
[AC-wlan-mg-abc] quit
# Configure the AC as the SNMP proxy agent for the SecBlade IAG card at 2.1.1.2.
[AC] snmp-agent proxy ip 2.1.1.2
3. Configure the H3C SecBlade IAG card:
# Assign the two subinterfaces on the SecBlade IAG card the IP addresses 1.1.1.3/24 and 2.1.1.2/24. Make sure active routes are available between each subinterface on the SecBlade IAG card and the agent. (Details not shown.)
# Configure the mobility group abc.
<IAG> system-view
[IAG] wlan mobility-group abc
[IAG-wlan-mg-abc] member ip 2.1.1.1
[IAG-wlan-mg-abc] source ip 2.1.1.2
[IAG-wlan-mg-abc] mobility-group enable
[IAG-wlan-mg-abc] quit
4. Verify the configuration:
You can log in to the AC from the NMS to perform SNMP operations on both the AC and the H3C SecBlade IAG card.
Configuring MIB style
MIBs include public MIBs and private MIBs. A private MIB is attached to a sub-node under the enterprises MIB node (1.3.6.1.4.1). The H3C private MIB has two styles: the H3C compatible MIB style and the H3C new MIB style:
· In the H3C compatible MIB style, the device public MIB is under the H3C's enterprise ID 25506, and the private MIB is under the enterprise ID 2011.
· In the H3C new MIB style, both the device public MIB and the private MIB are under the H3C's enterprise ID 25506.
These two styles of MIBs implement the same management function. Your device comes with a MIB loaded but the MIB style depends on the device model. You can change the MIB style as needed, but must make sure the device is using the same MIB style as the NMS.
Setting the MIB style
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the MIB style. |
mib-style [ compatible | new ] |
By default, H3C new MIB style is used. |
After changing the MIB style, reboot the device to validate the change.
Displaying and maintaining MIB style
|
Task |
Command |
Remarks |
|
Display the MIB style. |
display mib-style [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
