- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI configuration
- 02-RBAC configuration
- 03-Login management configuration
- 04-FTP and TFTP configuration
- 05-File system management configuration
- 06-Configuration file management configuration
- 07-Software upgrade configuration
- 08-ISSU configuration
- 09-Emergency shell configuration
- 10-Automatic configuration
- 11-Device management configuration
- 12-Security zone configuration
- 13-Tcl configuration
- 14-Python configuration
- 15-Management with BootWare
- 16-License management
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-Security zone configuration | 89.87 KB |
Security zone-based security management
Security zone configuration task list
Adding members to a security zone
Specifying the default action for packets between interfaces in the same security zone
Security zone configuration example
Configuring security zones
Overview
You can configure security zones to implement security zone-based security management.
Basic concepts
The security zone feature includes the following basic concepts:
· Security zone—A security zone is a collection of interfaces that have the same security requirements.
· System-defined security zones—The device provides the following system-defined security zones: Local, Trust, DMZ, Management, Untrust, library, and office. These security zones are created automatically by the system when one of following events occurs:
¡ The first command for creating a security zone is executed.
¡ The first command for creating a zone pair is executed.
System-defined security zones cannot be deleted.
· DMZ—A demilitarized zone is a network that is separate from the internal network and the external network both logically and physically. Typically, a DMZ contains devices for the public to access, such as the FTP servers.
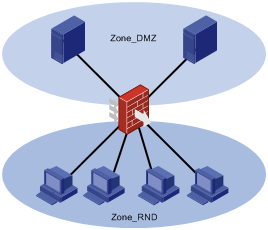
Security zone-based security management
For example, your enterprise has four network segments for the R&D department and two network segments for the servers. You can perform the following tasks to control traffic between the security zones:
· Create two security zones: Zone_RND and Zone_DMZ.
· Assign the four firewall interfaces that are connected to the R&D department to Zone_RND.
· Assign the two firewall interfaces that are connected to the servers to Zone_DMZ.
· Deploy security policies between the two security zones, including ACLs, ASPF policies, and object policies.
If the network topology changes, you only need to change interface assignments. You do not need to modify the security policies. For more information about packet filtering policies, see ACL and QoS Configuration Guide. For more information about ASPF and object policies, see Security Configuration Guide.
The following table describes how the device handles packets when security zone-based security management is configured:
|
Packets |
Action |
|
Packets between an interface that is in a security zone and an interface that is not in any security zone |
Discard. |
|
Packets between two interfaces that are in the same security zone |
Discard by default. |
|
Packets between two interfaces that belong to different security zones |
Forward or discard, depending on the matching object policy. If the object policy does not exist or does not take effect, the packets are discarded. For more information, see "Creating a zone pair." |
|
Packets between two interfaces that are not in any security zone |
Forward. |
|
Packets originated from or destined for the device itself |
Forward or discard, depending on the matching object policy. By default, these packets are discarded. |
Application scenarios
As a best practice, use security zone-based security management when the firewall is connected to multiple network segments or the network topology might change.
The traditional security management technology is based on interfaces. To filter packets, you must apply security policies on the inbound and outbound interfaces of a firewall. When the firewall is connected to multiple network segments, deploying security policies is time consuming and complicated. If the network topology changes, you might have to reconfigure security policies.
Security zone configuration task list
|
(Required.) Creating a security zone |
|
(Required.) Adding members to a security zone |
|
(Optional.) Creating a zone pair |
|
(Optional.) Specifying the default action for packets between interfaces in the same security zone |
Configuring a security zone
Creating a security zone
A security zone created on the default MDC belongs to the default MDC. To create a security zone for a non-default MDC, you must create the MDC and enter the MDC's system view.
To create a security zone:
|
Command |
Remarks |
|
|
1. Enter system view. |
N/A |
|
|
This command is required only if you want to create a security zone for a non-default MDC. |
||
|
3. (Optional.) Enter the system view of the MDC. |
This command is required only if you want to create a security zone for a non-default MDC. |
|
|
4. Create a security zone and enter security zone view. |
security-zone name zone-name |
By default, no security zone exists. |
Adding members to a security zone
A security zone can include member types listed in Table 1.
Table 1 Security zone members and objects that the members identify
|
Security zone member |
Objects that each member identifies |
|
Layer 3 interface: · Layer 3 Ethernet interface · Layer 3 logical interface, such as a Layer 3 subinterface |
All packets received or sent on the interface |
|
Layer 2 interface-VLAN combination |
All packets received or sent on the interface that carry the specified VLAN tag |
If a security zone has multiple types of members, a packet is matched in the following order: service chain, subnet, interface, and VLAN. The match operation stops when the first matching member is found.
To add members to a security zone:
|
Command |
Remarks |
|
|
1. Enter system view. |
N/A |
|
|
2. (Optional.) Log in to the MDC. |
This command is required only if you want to create a security zone for a non-default MDC. |
|
|
3. (Optional.) Enter the system view of the MDC. |
This command is required only if you want to create a security zone for a non-default MDC. |
|
|
4. Enter security zone view. |
N/A |
|
|
5. Add members to the security zone. |
· Add a Layer 3 Ethernet interface: · Add Layer 2 interface-VLAN combinations: |
By default, a security zone does not have any members. You can perform this step multiple times to add multiple members. |
Creating a zone pair
A zone pair has a source security zone and a destination security zone. The device examines received first data packets and uses zone pairs to identify data flows.
You can use the zone-pair security source any destination any command to define the any-to-any zone pair. This zone pair matches all packets from one security zone to another security zone.
After you apply security policies to zone pairs, the device processes data flows based on security policies.
· If a packet matches a zone pair between specific security zones, the device processes the packet by using the security policies applied to the zone pair.
· If a packet does not match any zone pair between specific security zones, the device identifies whether the packet is between the Management and Local zones.
¡ If the packet is between the Management and Local zones, the device discards the packet.
¡ If the packet is not between the Management and Local zones, the device searches for the any-to-any zone pair.
- If the zone pair exists, the device processes the packet by using the security policies applied to the zone pair.
- If the zone pair does not exist, the device discards the packet.
If you apply an object policy and a packet filtering policy to a zone pair, the object policy takes precedence.
To create a zone pair:
|
Command |
Remarks |
|
|
1. Enter system view. |
N/A |
|
|
2. (Optional.) Log in to the MDC. |
This command is required only if you want to create a security zone for a non-default MDC. |
|
|
3. (Optional.) Enter the system view of the MDC. |
This command is required only if you want to create a security zone for a non-default MDC. |
|
|
4. Create a zone pair and enter zone pair view. |
zone-pair security source { source-zone-name | any } destination { destination-zone-name | any } |
By default, no zone pair exists |
Specifying the default action for packets between interfaces in the same security zone
By default, packets exchanged between interfaces in the same security zone are dropped if no zone pair is configured from a security zone to the security zone itself. You can use this feature to change the processing policy for the packets.
To specify the default action for packets exchanged between interfaces in the same security zone:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. (Optional.) Log in to the MDC. |
switchto mdc mdc-name |
This command is required only if you want to create a security zone for a non-default MDC. |
|
3. (Optional.) Enter the system view of the MDC. |
system-view |
This command is required only if you want to create a security zone for a non-default MDC. |
|
4. Specify the default action for packets exchanged between interfaces in the same security zone. |
· Set the default action to permit: · Set the default action to deny: |
By default, the default action is deny for packets exchanged between interfaces in the same security zone. |
Displaying security zones
Execute display commands in any view.
|
Command |
|
|
Display security zone information. |
|
|
Display zone pair information. |
Security zone configuration example
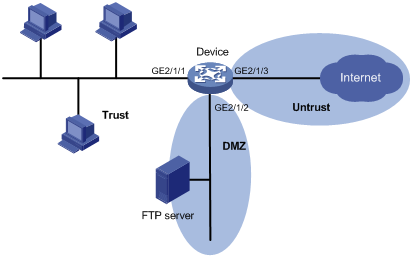
Network requirements
As shown in Figure 2, a firewall (Device) connects the corporate network to the Internet. The corporate network needs to provide FTP services for external users.
To ensure corporate network security, configure the firewall as follows:
· Assign the interfaces used to connect the internal network, the servers, and the Internet to security zones Trust, DMZ, and Untrust, respectively.
· Configure zone pairs and apply object policies to control access as follows:
¡ Allow internal users to access the FTP server and the Internet.
¡ Allow external users to access the FTP server.
¡ Allow the FTP server to access the Internet.
¡ Deny external users and the FTP server access to the internal network.
Configuration procedure
# Add interface GigabitEthernet 2/1/1 to security zone Trust.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 2/1/1
[Device-security-zone-Trust] quit
# Add interface GigabitEthernet 2/1/2 to security zone DMZ.
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 2/1/2
[Device-security-zone-DMZ] quit
# Add interface GigabitEthernet 2/1/3 to security zone Untrust.
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 2/1/3
[Device-security-zone-Untrust] quit
# Configure ACL 3500 to permit IP traffic.
[Device] acl advanced 3500
[Device-acl-ipv4-3500] rule permit ip
[Device-acl-ipv4-3500] quit
# Configure ASPF policy 1 to detect FTP traffic. To detect other types of traffic, use the detect command to add the protocols.
[Device] aspf policy 1
[Device-aspf-policy-1] detect ftp
[Device-aspf-policy-1] quit
# Create a zone pair with the source security zone Trust and destination security zone Untrust.
[Device] zone-pair security source trust destination untrust
# Apply ASPF policy 1 and ACL 3500 to the zone pair.
[Device-zone-pair-security-Trust-Untrust] aspf apply policy 1
[Device-zone-pair-security-Trust-Untrust] packet-filter 3500
[Device-zone-pair-security-Trust-Untrust] quit
# Create a zone pair with the source security zone Trust and destination security zone DMZ.
[Device] zone-pair security source trust destination dmz
# Apply ASPF policy 1 and ACL 3500 to the zone pair.
[Device-zone-pair-security-Trust-DMZ] aspf apply policy 1
[Device-zone-pair-security-Trust-DMZ] packet-filter 3500
[Device-zone-pair-security-Trust-DMZ] quit
Verifying the configuration
# Verify that internal hosts can access resources on the Internet and the FTP resources in the DMZ zone. (Details not shown.)
# Verify that access requests initiated from the Internet or the DMZ zone are denied. (Details not shown.)