- Table of Contents
-
- 16-Security Configuration Guide
- 00-Preface
- 01-ACL configuration
- 02-Packet filter configuration
- 03-Time range configuration
- 04-User profile configuration
- 05-Password control configuration
- 06-Keychain configuration
- 07-Public key management
- 08-PKI configuration
- 09-IPsec configuration
- 10-IKE configuration
- 11-IKEv2 configuration
- 12-SSH configuration
- 13-SSL configuration
- 14-SSL VPN configuration
- 15-Session management
- 16-Connection limit configuration
- 17-Attack detection and prevention configuration
- 18-IP-based attack prevention configuration
- 19-IP source guard configuration
- 20-ARP attack protection configuration
- 21-ND attack defense configuration
- 22-Protocol packet rate limit configuration
- 23-Security policy configuration
- 24-Object group configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 23-Security policy configuration | 274.30 KB |
Contents
Restrictions and guidelines: Security policy configuration
Prerequisites for security policies
Security policy tasks at a glance
Configuring IPv4 security policy rules
Configuring the action of the default security policy rule
Creating a security policy rule
Configuring filtering criteria for a security policy rule
Specifying the action for a security policy rule
Enabling a security policy rule
Specifying a time range for a security policy rule
Applying a DPI application profile to a security policy rule
Setting the session aging time for a security policy rule
Associating a security policy rule with a track entry
Enabling logging for matched packets
Enabling statistics collection for matched packets
Configuring IPv6 security policy rules
Configuring the action of the default security policy rule
Creating a security policy rule
Configuring filtering criteria for a security policy rule
Specifying the action for a security policy rule
Enabling a security policy rule
Specifying a time range for a security policy rule
Applying a DPI application profile to a security policy rule
Setting the session aging time for a security policy rule
Associating a security policy rule with a track entry
Enabling logging for matched packets
Enabling statistics collection for matched packets
Activating rule matching acceleration
Configuring security policy rule groups
Creating a security policy rule group
Specifying a security policy rule group for a security policy rule
Moving a security policy rule group
Renaming a security policy rule group
Verifying and maintaining security policies
Clearing object policy statistics
Displaying the object policy configuration and statistics
Configuring security policies
About security policies
A security policy defines a set of rules for forwarding control and Deep Packet Inspection (DPI). It matches packets against the rules and takes the action stated in the rules on the matched packets.
Security policy rules
A security policy contains one or multiple rules. Each security policy rule is a permit or deny, or DPI statement for identifying traffic based on criteria.
Rule numbering
Each rule is uniquely identified by a name and an ID. When you create a rule, the rule name must be manually configured, and the rule ID can be manually configured or automatically assigned by the system.
Rule match criteria
The rule match criteria include the following types: source IP address and source MAC address, destination IP address, user and user group, application and application group, and service.
Rule and session management
When a security policy is configured, the device generates session entries for permitted packets to record packet information.
You can set session aging times for protocol states, application layer protocols, or rules. The aging time configured for a rule takes precedence over the aging time configured for a protocol state or an application layer protocol. For more information about session management, see "Managing sessions."
Security policy mechanism
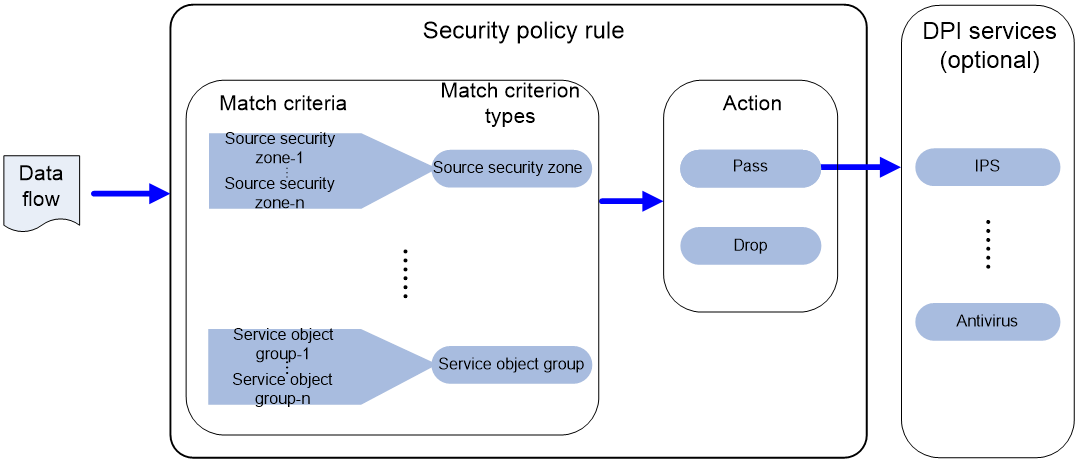
As shown in Figure 1, a security policy operates as follows:
1. After receiving a packet, the device matches the packet against the configured security policy rules.
A security policy rule includes various match criterion types. A packet is considered matched if it matches all the criterion types in the rule. Each criterion type includes one or more criteria, and a packet matches a criterion type if it matches any criterion of the type. Source MAC address criteria and source IP address criteria belong to the same criterion type.
¡ If no match is found, the device discards the packet.
¡ If a match is found and the rule action is drop, the device discards the packet.
¡ If a match is found and the rule action is pass, the device goes to the next step.
2. If a DPI application profile is configured for the matched rule, the device uses the specified profile to perform DPI on the packet. If no DPI application profile is specified, the device allows the packet to pass.
Figure 1 Security policy mechanism
Rule matching acceleration
This feature accelerates security policy rule matching to enhance connection establishment and packet forwarding performance, especially for a device using multiple rules to match packets from multiple users.
Security policy rule grouping
Security policy rule grouping allows users to enable, disable, delete, and move security policy rules in batches. A security policy rule in a security policy rule group takes effect only when both the rule and the group are enabled.
Restrictions and guidelines: Security policy configuration
When you configure security policies, follow these restrictions and guidelines:
· Packet filtering, if configured, is performed only on packets that do not match any security policy rule. As a best practice, make sure security policies have stricter filtering criteria than packet filtering, so the unmatched packets can still be filtered by packet filtering.
· Follow the depth-first order during rule creation to create rules with stricter match criteria first because the system matches packets against rules in the order the rules were created.
· Security policy rules specified with an IP address object group that uses a user or user group cannot match packets. To filter packets by user or user group, configure security policy rules specified with user or user group criteria.
Prerequisites for security policies
Before you configure security policies, perform the following tasks:
· Configure a time range. See "Configuring time ranges."
· Configure IP address object groups and service object groups. See "Configuring object groups."
· Configure applications and application groups. See APR in DPI Configuration Guide.
· Configure user and user groups. See "Configuring user identification."
· Configure DPI. See DPI Configuration Guide.
Security policy tasks at a glance
To configure security policies, perform the following tasks:
1. Configuring IPv4 security policy rules
a. Configuring the action of the default security policy rule
b. Creating a security policy rule
c. Configuring filtering criteria for a security policy rule
d. Specifying the action for a security policy rule
e. Enabling a security policy rule
f. (Optional.) Specifying a time range for a security policy rule
g. (Optional.) Applying a DPI application profile to a security policy rule
h. (Optional.) Setting the session aging time for a security policy rule
i. (Optional.) Associating a security policy rule with a track entry
j. (Optional.) Enabling logging for matched packets
k. (Optional.) Enabling statistics collection for matched packets
2. Configuring IPv6 security policy rules
a. Configuring the action of the default security policy rule
b. Creating a security policy rule
c. Configuring filtering criteria for a security policy rule
d. Specifying the action for a security policy rule
e. Enabling a security policy rule
f. (Optional.) Specifying a time range for a security policy rule
g. (Optional.) Applying a DPI application profile to a security policy rule
h. (Optional.) Setting the session aging time for a security policy rule
i. (Optional.) Associating a security policy rule with a track entry
j. (Optional.) Enabling logging for matched packets
k. (Optional.) Enabling statistics collection for matched packets
3. (Optional.) Manage security policies
a. Changing the rule match order
b. Activating rule matching acceleration
4. (Optional.) Configuring security policy rule groups
a. Creating a security policy rule group
b. Specifying a security policy rule group for a security policy rule
c. Moving a security policy rule group
d. Renaming a security policy rule group
Configuring IPv4 security policy rules
Configuring the action of the default security policy rule
About this task
When a packet does not match any security policy rules, the action for the default rule is taken on the packet.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Configure the action of the default security policy rule.
default rule action { drop | pass }
By default, the action for the default security policy rule is drop.
4. Enable statistics collection for the default security policy rule.
default rule counting enable
By default, the device does not collect statistics about packets matching the default security policy rule.
5. Enable logging for the default security policy rule.
default rule logging enable
By default, logging is disabled for packets matching the default security policy rule.
Creating a security policy rule
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. (Optional.) Configure a description for the policy.
description text
By default, a security policy does not have a description.
4. Create a security policy rule.
rule { rule-id | [ rule-id ] name rule-name }
5. (Optional.) Configure a description for the rule.
description text
By default, a security policy rule does not have a description.
Configuring filtering criteria for a security policy rule
Restrictions and guidelines
A rule matches all packets if no criteria are specified for the rule.
If a specified object group has no objects, the rule cannot match any packets.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Configure source filtering criteria:
¡ Specify a source IPv4 address object group as a filtering criterion.
source-ip object-group-name
By default, no source IPv4 address object group is specified as a filtering criterion.
¡ Specify a source MAC address object group as a filtering criterion.
source-mac object-group-name
By default, no source MAC address object group is specified as a filtering criterion.
5. Configure destination filtering criteria:
¡ Specify a destination IPv4 address object group as a filtering criterion.
destination-ip object-group-name
By default, no destination IPv4 address object group is specified as a filtering criterion.
6. Specify a service object group as a filtering criterion.
service { object-group-name | any }
By default, no service object group is specified as a filtering criterion.
7. Configure application filtering criteria:
¡ Specify an application as a filtering criterion.
application application-name
By default, no application is specified as a filtering criterion.
For the application filtering criteria to be identified, you must permit the dependent applications to pass through.
¡ Specify an application group as a filtering criterion.
app-group app-group-name
By default, no application group is specified as a filtering criterion.
8. Configure user filtering criterion:
¡ Specify a user as a filtering criterion.
user username [ domain domain-name ]
By default, no user is specified as a filtering criterion.
¡ Specify a user group as a filtering criterion.
user-group user-group-name [ domain domain-name ]
By default, no user group is specified as a filtering criterion.
Specifying the action for a security policy rule
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify the action for the security policy rule.
action { drop | pass }
By default, the action for a security policy rule is drop.
Enabling a security policy rule
About this task
Use this feature to enable a security policy rule. Rules that are not enabled cannot be used to match and control packets.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable the security policy rule.
undo disable
By default, security policy rules are disabled.
Specifying a time range for a security policy rule
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify a time range during which the security policy rule is in effect.
time-range time-range-name
By default, a security policy rule is in effect at any time.
Applying a DPI application profile to a security policy rule
About this task
This feature enables the device to perform DPI on packets matching the specified rule. For more information about DPI, see DPI Configuration Guide.
Restrictions and guidelines
This feature takes effect only when the rule action is pass.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify the rule action as pass.
action pass
By default, the action for a security policy rule is drop.
5. Apply a DPI application profile to the rule.
profile app-profile-name
By default, no DPI application profile is applied to a rule.
Setting the session aging time for a security policy rule
About this task
Perform this task to specify the aging time for stable sessions and persistent sessions. The configuration takes effect only on sessions established afterwards.
The configured aging time for persistent sessions is effective only on TCP sessions in ESTABLISHED state.
The priorities of the session aging times configured by using the session persistent aging-time, session aging-time, and session persistent acl commands are in descending order.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Set the session aging time.
session aging-time time-value
By default, the session aging time is not configured.
5. Set the aging time for persistent sessions.
session persistent aging-time time-value
By default, the aging time for persistent sessions is not configured.
Associating a security policy rule with a track entry
About this task
Perform this task to enable the collaboration between the track module and a security policy rule. The collaboration operates as follows:
· If a rule is associated with the Negative state of a track entry, the device:
¡ Sets the rule state to Active if the track entry is in Negative state.
¡ Sets the rule state to Inactive if the track entry is in Positive state.
· If a rule is associated with the Positive state of a track entry, the device:
¡ Sets the rule state to Active if the track entry is in Positive state.
¡ Sets the rule state to Inactive if the track entry is in Negative state.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Associate the rule with a track entry.
track { negative | positive } track-entry-number
By default, no track entry is associated with a rule.
Enabling logging for matched packets
About this task
This feature enables the device to log matching packets and send the log to the information center for processing. The log destinations and output rules are determined by the information center settings. For more information about the information center, see System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable logging for matched packets.
logging enable
By default, logging for matched packets is disabled.
5. (Optional.) Enable real-time sending for security policy log messages.
security-policy log real-time-sending enable
By default, real-time sending is disabled for security policy log messages.
Enabling statistics collection for matched packets
About this task
Perform this task to enable the device to collect statistics about matched packets. The collected statistics can be viewed by executing the display security-policy statistics command.
Restrictions and guidelines
When inter-VLAN bridge forwarding is configured, this feature collects statistics only about packets discarded by security policies and DPI. Statistics about permitted packets are not collected. For more information about inter-VLAN bridge forwarding, see Layer 2 forwarding in Network Connectivity Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable statistics collection for matched packets.
counting enable
By default, the device does not collect statistics about matched packets.
Configuring IPv6 security policy rules
Configuring the action of the default security policy rule
About this task
When a packet does not match any security policy rules, the action for the default rule is taken on the packet.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Configure the action of the default security policy rule.
default rule action { drop | pass }
By default, the action for the default security policy rule is drop.
4. Enable statistics collection for the default security policy rule.
default rule counting enable
By default, the device does not collect statistics about packets matching the default security policy rule.
5. Enable logging for the default security policy rule.
default rule logging enable
By default, logging is disabled for packets matching the default security policy rule.
Creating a security policy rule
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. (Optional.) Configure a description for the policy.
description text
By default, a security policy does not have a description.
4. Create a security policy rule.
rule { rule-id | [ rule-id ] name rule-name }
5. (Optional.) Configure a description for the rule.
description text
By default, a security policy rule does not have a description.
Configuring filtering criteria for a security policy rule
Restrictions and guidelines
A rule matches all packets if no criteria are specified for the rule.
If a specified object group has no objects, the rule cannot match any packets.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Configure source filtering criteria:
¡ Specify a source IPv6 address object group as a filtering criterion.
source-ip object-group-name
By default, no source IPv6 address object group is specified as a filtering criterion.
5. Configure destination filtering criteria:
¡ Specify a destination IPv6 address object group as a filtering criterion.
destination-ip object-group-name
By default, no destination IPv6 address object group is specified as a filtering criterion.
6. Specify a service object group as a filtering criterion.
service { object-group-name | any }
By default, no service object group is specified as a filtering criterion.
7. Configure application filtering criteria:
¡ Specify an application as a filtering criterion.
application application-name
By default, no application is specified as a filtering criterion.
For the application filtering criteria to be identified, you must permit the dependent applications to pass through.
¡ Specify an application group as a filtering criterion.
app-group app-group-name
By default, no application group is specified as a filtering criterion.
8. Configure user filtering criterion:
¡ Specify a user as a filtering criterion.
user username [ domain domain-name ]
By default, no user is specified as a filtering criterion.
¡ Specify a user group as a filtering criterion.
user-group user-group-name [ domain domain-name ]
By default, no user group is specified as a filtering criterion.
Specifying the action for a security policy rule
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify the action for the security policy rule.
action { drop | pass }
By default, the action for a security policy rule is drop.
Enabling a security policy rule
About this task
Use this feature to enable a security policy rule. Rules that are not enabled cannot be used to match and control packets.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ip
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable the security policy rule.
undo disable
By default, security policy rules are disabled.
Specifying a time range for a security policy rule
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify a time range during which the security policy rule is in effect.
time-range time-range-name
By default, a security policy rule is in effect at any time.
Applying a DPI application profile to a security policy rule
About this task
This feature enables the device to perform DPI on packets matching the specified rule. For more information about DPI, see DPI Configuration Guide.
Restrictions and guidelines
This feature takes effect only when the rule action is pass.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify the rule action as pass.
action pass
By default, the action for a security policy rule is drop.
5. Apply a DPI application profile to the rule.
profile app-profile-name
By default, no DPI application profile is applied to a rule.
Setting the session aging time for a security policy rule
About this task
Perform this task to specify the aging time for stable sessions and persistent sessions. The configuration takes effect only on sessions established afterwards.
The configured aging time for persistent sessions is effective only on TCP sessions in ESTABLISHED state.
The priorities of the session aging times configured by using the session persistent aging-time, session aging-time, and session persistent acl commands are in descending order.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Set the session aging time.
session aging-time time-value
By default, the session aging time is not configured.
5. Set the aging time for persistent sessions.
session persistent aging-time time-value
By default, the aging time for persistent sessions is not configured.
Associating a security policy rule with a track entry
About this task
Perform this task to enable the collaboration between the track module and a security policy rule. The collaboration operates as follows:
· If a rule is associated with the Negative state of a track entry, the device:
¡ Sets the rule state to Active if the track entry is in Negative state.
¡ Sets the rule state to Inactive if the track entry is in Positive state.
· If a rule is associated with the Positive state of a track entry, the device:
¡ Sets the rule state to Active if the track entry is in Positive state.
¡ Sets the rule state to Inactive if the track entry is in Negative state.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Associate the rule with a track entry.
track { negative | positive } track-entry-number
By default, no track entry is associated with a rule.
Enabling logging for matched packets
About this task
This feature enables the device to log matching packets and send the log to the information center for processing. The log destinations and output rules are determined by the information center settings. For more information about the information center, see System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable logging for matched packets.
logging enable
By default, logging for matched packets is disabled.
5. (Optional.) Enable real-time sending for log messages.
security-policy log real-time-sending enable
By default, real-time sending is disabled for log messages.
Enabling statistics collection for matched packets
About this task
Perform this task to enable the device to collect statistics about matched packets. The collected statistics can be viewed by executing the display security-policy statistics command.
Restrictions and guidelines
When inter-VLAN bridge forwarding is configured, this feature collects statistics only about packets discarded by security policies and DPI. Statistics about permitted packets are not collected. For more information about inter-VLAN bridge forwarding, see Layer 2 forwarding in Network Connectivity Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IPv6 security policy view.
security-policy ipv6
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Enable statistics collection for matched packets.
counting enable
By default, the device does not collect statistics about matched packets.
Changing the rule match order
About this task
The device matches packets against security policy rules in the order the rules were created. You can change the rule match order by changing the position of a security policy rule in the rule list.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Move a security policy rule.
¡ Move a security policy rule by rule ID.
move rule rule-id before insert-rule-id
¡ Move a security policy rule by rule name.
move rule name rule-name1 { { after | before } name rule-name2 | bottom | down | top | up }
Activating rule matching acceleration
About this task
Rule matching acceleration does not take effect on newly added, modified, and moved rules unless the feature is activated for the rules. By default, the system automatically activates rule matching acceleration for such rules at specific intervals. The interval is 2 seconds if 100 or fewer rules exist and 20 seconds if over 100 rules exist.
To activate rule matching acceleration immediately after a rule change, you can perform this task.
Restrictions and guidelines
If no rule change is detected, the system does not perform an activation operation.
Insufficient memory can cause rule matching acceleration failures. Unaccelerated rules do not take effect, and rules that have been accelerated are not affected.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Activate rule matching acceleration.
accelerate enhanced enable
Configuring security policy rule groups
Creating a security policy rule group
About this task
Perform this task to create a security policy rule group and add security policy rules to the group.
Restrictions and guidelines
To add a list of security policy rules, make sure the end rule is listed behind the start rule and the specified rules do not belong to any other security policy rule group.
A security policy rule group can contain only IPv4 rules or IPv6 rules.
Procedure
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Create a security policy rule group and add security policy rules to the group.
group name group-name [ from rule-name1 to rule-name2 ] [ description description-text ] [ disable | enable ]
Specifying a security policy rule group for a security policy rule
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Enter security policy rule view.
rule { rule-id | [ rule-id ] name rule-name }
4. Specify a security policy rule group for the security policy rule.
parent-group group-name
Moving a security policy rule group
About this task
Perform this task to move a security policy rule group to change the match order of security policy rules.
Restrictions and guidelines
If you specify a target security policy rule that belongs to a security policy rule group, follow these restrictions and guidelines:
· If the target rule is neither the start nor end rule of the group, you cannot move a security policy rule group to the place before or after the rule.
· If the target rule is the start rule of the group, you can only move a security policy rule group to the place before the rule.
· If the target rule is the end rule of the group, you can only move a security policy rule group to the place after the rule.
You can move a security policy rule group before or after a security policy rule or group of the same type (IPv4 or IPv6).
Procedure
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Move a security policy rule group.
group move group-name1 { after | before } { group group-name2 | rule rule-name }
Renaming a security policy rule group
1. Enter system view.
system-view
2. Enter IPv4 or IPv6 security policy view.
security-policy { ip | ipv6 }
3. Rename a security policy rule group.
group rename old-name new-name
Verifying and maintaining security policies
Clearing object policy statistics
To clear object policy statistics, execute the following command in user view:
reset security-policy statistics [ ip | ipv6 ] [ rule rule-name ]
Displaying the object policy configuration and statistics
Perform display tasks in any view.
· Display security policy configuration.
display security-policy { ip | ipv6 }
· Display security policy statistics.
display security-policy statistics { ip | ipv6 } [ rule rule-name ]