- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Flowspec configuration | 139.25 KB |
Contents
Prerequisites for Flowspec configuration
Creating and activating a Flowspec rule
Applying a Flowspec rule to the public network
Applying a Flowspec rule to a VPN instance
Enabling BGP to distribute Flowspec rules
About BGP Flowspec rule distribution
Restrictions and guidelines for enabling BGP to distribute Flowspec rules
Enabling BGP to distribute public network IPv4 Flowspec rules
Enabling BGP to distribute private network Flowspec rules
Enabling BGP to distribute VPNv4 Flowspec rules
Configuring BGP Flowspec route reflection
Display and maintenance commands for Flowspec
Flowspec configuration examples
Configuring Flowspec
About Flowspec
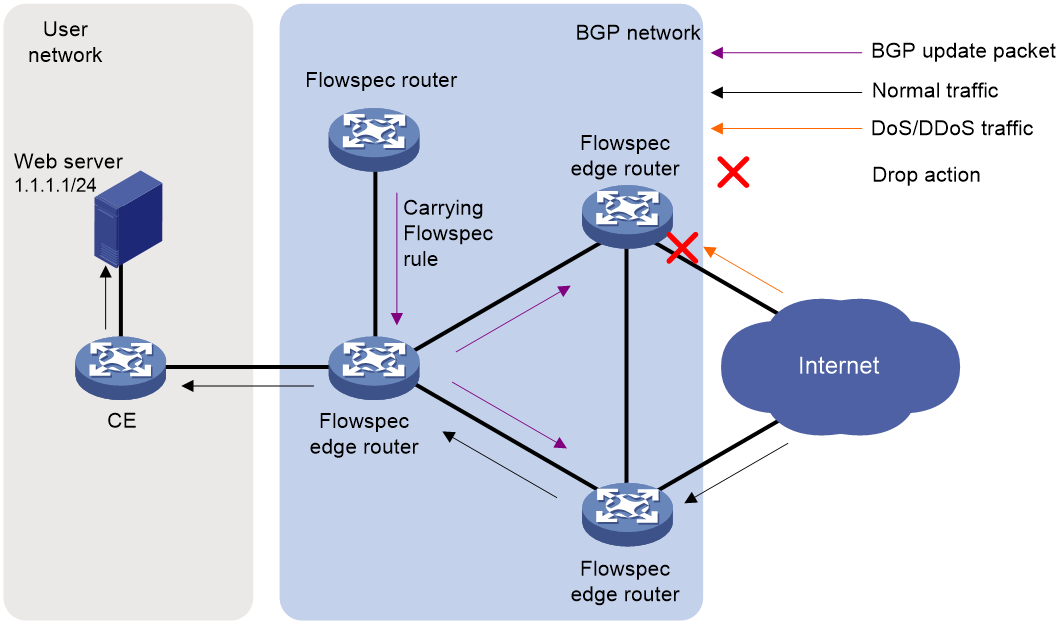
The flow specification (Flowspec) feature allows you to filter and manage illegal traffic in BGP networks, therefore mitigating the effects of DoS and DDoS attacks. Flowspec classifies attack traffic and takes action on classified traffic, such as drop, redirect, or rate limit.
Flowspec device roles
The following Flowspec device roles are involved in a Flowspec network:
· Flowspec router—A BGP router in a BGP network, also called a Flowspec controller. A Flowspec router distributes Flowspec rules (match criteria and actions) to Flowspec edge routers through BGP updates.
· Flowspec edge router—A BGP router in a BGP network, also called a Flowspec client. A Flowspec edge router receives Flowspec rules from a Flowspec router and applies the match criteria and actions to its forwarding plane.
When configuring Flowspec, select one BGP router as the Flowspec router and all other BGP routers as Flowspec edge routers.
Protocols and standards
RFC 5575: Dissemination of Flow Specification Rules
RFC 7674: Clarification of the Flowspec Redirect Extended Community
How Flowspec works
To support Flowspec, MP-BGP defines the Flowspec IPv4 address family and the Flowspec VPNv4 address family and introduces Flowspec Network Layer Reachability Information (NLRI), called Flowspec routes. Flowspec can distribute Flowspec rules (match criteria and actions) to the public network and VPN instances through the Flowspec IPv4 address family and the Flowspec VPNv4 address family.
As shown in Figure 1, the Flowspec router distributes Flowspec rules to Flowspec edge routers. After receiving Flowspec rules, a Flowspec edge router applies the criteria and actions to its forwarding plane. A Flowspec router can also distribute Flowspec rules to other ASs. This enables you to filter and control attack traffic on the device closest to the attack source.
Flowspec tasks at a glance
To configure Flowspec, perform the following tasks:
1. Creating and activating a Flowspec rule
Perform this task only on the Flowspec router.
¡ Applying a Flowspec rule to the public network
¡ Applying a Flowspec rule to a VPN instance
Perform this task only on the Flowspec router.
3. Enabling BGP to distribute Flowspec rules
¡ Enabling BGP to distribute public network IPv4 Flowspec rules
¡ Enabling BGP to distribute private network Flowspec rules
¡ Enabling BGP to distribute VPNv4 Flowspec rules
Perform this task on both the Flowspec router and Flowspec edge routers.
4. (Optional.) Configuring BGP Flowspec route reflection
Perform this task only on the Flowspec router.
Prerequisites for Flowspec configuration
Before you configure Flowspec, you must configure basic BGP functions on the Flowspec router and Flowspec edge routers. For information about configuring basic BGP functions, see Layer 3—IP Routing Configuration Guide.
Creating and activating a Flowspec rule
1. Enter system view.
system-view
2. Create a Flowspec rule and enter Flowspec rule view.
flow-route flowroute-name
3. Configure a match criterion.
if-match match-criteria
By default, no match criterion is configured.
4. Apply an action.
apply action
5. (Optional.) Display the match criteria and actions that are not committed.
check flow-route-configuration
6. Commit match criteria and actions.
commit
By default, match criteria and actions are not committed.
Applying a Flowspec rule
Applying a Flowspec rule to the public network
1. Enter system view.
system-view
2. Enter Flowspec view.
flowspec
3. Create a Flowspec IPv4 address family for the public network and enter its view.
address-family ipv4
4. Apply a Flowspec rule to the public network.
flow-route flowroute-name
By default, no Flowspec rule is applied to the public network.
Applying a Flowspec rule to a VPN instance
1. Enter system view.
system-view
2. Configure a VPN instance.
a. Create a VPN instance and enter VPN instance view.
ip vpn-instance vpn-instance-name
b. Configure an RD for the VPN instance.
route-distinguisher route-distinguisher
By default, no RD is configured for a VPN instance.
c. Configure route targets for the VPN instance.
vpn-target { vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ] }
By default, no route targets are configured.
For more information about the ip vpn-instance, route-distinguisher, and vpn-target commands, see MPLS L3VPN commands in MPLS Command Reference.
3. Enter the IPv4 Flowspec address family view of the VPN instance.
address-family ipv4 flowspec
4. Configure route targets for the IPv4 Flowspec address family.
vpn-target vpn-target&<1-8> [ both | export-extcommunity | import-extcommunity ]
By default, no route targets are configured for the IPv4 Flowspec address family.
The route targets configured must be the same as the route targets configured previously for the VPN instance.
5. Execute the quit command twice to return to system view.
6. Enter Flowspec view.
flowspec
7. Create a Flowspec IPv4 address family and associate the address family with the VPN instance.
address-family ipv4 vpn-instance vpn-instance-name
8. Apply a Flowspec rule to the Flowspec IPv4 VPN instance address family.
flow-route flowroute-name
By default, no Flowspec rule is applied to a Flowspec IPv4 VPN instance address family.
Enabling BGP to distribute Flowspec rules
About BGP Flowspec rule distribution
By default, the device validates received Flowspec rules and their redirection next hops (if present).
A Flowspec rule is valid if the following conditions exist:
· The Flowspec rule contains a destination address match criterion.
· The device that receives the rule has routes with the destination address for matching as their destination address.
For the device to take the action on matching traffic without validation, disable validation of Flowspec rules.
A redirection next hop is valid if the following conditions exist:
· A route exists on the device with the redirection next hop as the route's next hop.
· The next hop IP address and the device are in the same AS.
For the device to take the action of redirecting traffic to a next hop without validation, disable validation of the redirection next hops.
The BGP Flowspec rule distribution feature not only distributes Flowspec rules in BGP routes to Flowspec edge routers but also makes those Flowspec rules take effect on the Flowspec router itself.
Restrictions and guidelines for enabling BGP to distribute Flowspec rules
For more information about the bgp and peer enable commands, see Layer 3—IP Routing Command Reference.
Enabling BGP to distribute public network IPv4 Flowspec rules
1. Enter system view.
system-view
2. Execute the following commands in sequence to enter BGP IPv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
address-family ipv4 flowspec
3. Enable BGP Flowspec peers to exchange routing information.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP Flowspec peers cannot exchange routing information.
4. (Optional.) Disable validation of Flowspec rules from BGP Flowspec peers.
peer { group-name | ip-address [ mask-length ] } validation-disable
By default, Flowspec rules from BGP Flowspec peers are validated.
5. (Optional.) Disable validation of the redirection next hops in Flowspec rules from BGP Flowspec peers.
peer { group-name | ip-address [ mask-length ] } validation-redirect-disable
By default, the redirection next hops in Flowspec rules from BGP Flowspec peers are validated.
6. (Optional.) Configure the device to not change the next hop of routes advertised to EBGP peers.
peer { group-name | ip-address [ mask-length ] } next-hop-invariable
By default, the device uses its own IP address as the next hop of routes advertised to EBGP peers.
Enabling BGP to distribute private network Flowspec rules
1. Enter system view.
system-view
2. Execute the following commands in sequence to enter BGP-VPN IPv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
ip vpn-instance vpn-instance-name
address-family ipv4 flowspec
3. Enable BGP Flowspec peers to exchange routing information.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP Flowspec peers cannot exchange routing information.
4. (Optional.) Disable validation of Flowspec rules from BGP Flowspec peers.
peer { group-name | ip-address [ mask-length ] } validation-disable
By default, Flowspec rules from BGP Flowspec peers are validated.
5. (Optional.) Disable validation of the redirection next hops in Flowspec rules from BGP Flowspec peers.
peer { group-name | ip-address [ mask-length ] } validation-redirect-disable
6. (Optional.) Configure the device to not change the next hop of routes advertised to EBGP peers.
peer { group-name | ip-address [ mask-length ] } next-hop-invariable
By default, the device uses its own IP address as the next hop of routes advertised to EBGP peers.
Enabling BGP to distribute VPNv4 Flowspec rules
1. Enter system view.
system-view
2. Execute the following commands in sequence to enter BGP VPNv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
address-family vpnv4 flowspec
3. Enable BGP Flowspec peers to exchange routing information.
peer { group-name | ipv4-address [ mask-length ] } enable
By default, BGP Flowspec peers cannot exchange routing information.
4. (Optional.) Configure the device to not change the next hop of routes advertised to EBGP peers.
peer { group-name | ip-address [ mask-length ] } next-hop-invariable
By default, the device uses its own IP address as the next hop of routes advertised to EBGP peers.
Configuring BGP Flowspec route reflection
About Flowspec route reflection
Route reflection reduces the number of IBGP connections in an AS. In an AS, you can configure a BGP route reflector and its clients. The route reflector and its clients automatically form a cluster identified by the router ID of the route reflector. The route reflector forwards route updates among its clients, which do not need to establish connections with one another.
Procedure
1. Enter system view.
system-view
2. Enter one of the following views:
¡ Execute the following commands in sequence to enter BGP IPv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
address-family ipv4 flowspec
¡ Execute the following commands in sequence to enter BGP-VPN IPv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
ip vpn-instance vpn-instance-name
address-family ipv4 flowspec
¡ Execute the following commands in sequence to enter BGP VPNv4 Flowspec address family view:
bgp as-number [ instance instance-name ]
address-family vpnv4 flowspec
3. Configure the router as a route reflector and specify a peer or peer group as its client.
peer { group-name | ipv4-address [ mask-length ] } reflect-client
By default, no route reflector or client is configured.
4. (Optional.) Disable route target filtering for received BGP VPNv4 Flowspec routes.
undo policy vpn-target
By default, route target filtering is enabled for received VPNv4 routes. The VPNv4 routes whose export route target attribute matches the local import route target attribute are added to the routing table.
This command is available only in BGP VPNv4 Flowspec address family view.
5. (Optional.) Enable route reflection between clients.
reflect between-clients
By default, route reflection between clients is enabled.
6. (Optional.) Configure the cluster ID of the route reflector.
reflector cluster-id { cluster-id | ipv4-address }
By default, a route reflector uses its own router ID as the cluster ID.
Display and maintenance commands for Flowspec
For more information about the commands not covered in this feature, see Layer 3—IP Routing Command Reference.
Execute the display commands in any view and the reset and refresh commands in user view.
|
Task |
Command |
|
Display BGP Flowspec peer information. |
display bgp [ instance instance-name ] peer ipv4 flowspec [ vpn-instance vpn-instance-name ] [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ] |
|
Display BGP Flowspec peer group information. |
display bgp [ instance instance-name ] group ipv4 flowspec [ vpn-instance vpn-instance-name ] [ group-name group-name ] |
|
Display BGP VPNv4 Flowspec peer information. |
display bgp [ instance instance-name ] peer vpnv4 flowspec [ ipv4-address mask-length | { ipv4-address | group-name group-name } log-info | [ ipv4-address ] verbose ] |
|
Display BGP IPv4 Flowspec routing information. |
display bgp [ instance instance-name ] routing-table ipv4 flowspec [ vpn-instance vpn-instance-name ] [ flowspec-prefix [ advertise-info ] | statistics ] display bgp [ instance instance-name ] routing-table ipv4 flowspec [ vpn-instance vpn-instance-name ] peer ipv4-address { advertised-routes | received-routes } [ flowspec-prefix | statistics ] |
|
Display BGP VPNv4 Flowspec routing information. |
display bgp [ instance instance-name ] routing-table vpnv4 flowspec [ peer ipv4-address { advertised-routes | received-routes } [ flowspec-prefix | statistics ] | [ route-distinguisher route-distinguisher ] [ flowspec-prefix [ advertise-info ] ] | statistics ] |
|
Display BGP IPv4 Flowspec update group information. |
display bgp [ instance instance-name ] update-group ipv4 flowspec [ ipv4-address ] |
|
Display BGP VPNv4 Flowspec update group information. |
display bgp [ instance instance-name ] update-group vpnv4 flowspec [ ipv4-address ] |
|
Display Flowspec rule information. |
In standalone mode: display flow-route { all | flow-route-id | ip [ vpn-instance vpn-instance-name ] } In IRF mode: display flow-route { all | flow-route-id | ip [ vpn-instance vpn-instance-name ] } [ slot slot-number ] |
|
Reset all BGP sessions. |
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } ipv4 flowspec [ vpn-instance vpn-instance-name ] |
|
Reset BGP sessions for a VPNv4 address family. |
refresh bgp [ instance instance-name ] { ipv4-address [ mask-length ] | all | external | group group-name | internal } { export | import } vpnv4 flowspec [ vpn-instance vpn-instance-name ] |
|
Reset BGP sessions for a BGP IPv4 Flowspec address family. |
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | group group-name | internal } ipv4 flowspec [ vpn-instance vpn-instance-name ] |
|
Reset BGP sessions for a BGP VPNv4 Flowspec address family. |
reset bgp [ instance instance-name ] { as-number | ipv4-address [ mask-length ] | all | external | internal | group group-name } vpnv4 flowspec [ vpn-instance vpn-instance-name ] |
|
Clear Flowspec rule statistics. |
reset flow-route statistics { all | flow-route-id | ip [ vpn-instance vpn-instance-name ] } |
Flowspec configuration examples
Example: Configuring Flowspec
Network configuration
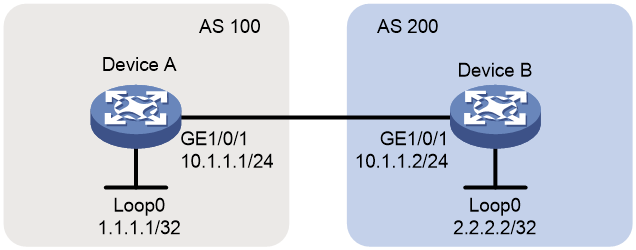
As shown in Figure 2, all routers run BGP. Device A is a Flowspec router, and Device B is a Flowspec edge router.
Configure Flowspec to limit the rate of incoming packets with destination IP address 1.1.1.0/24 and port 10 on Device B.
Procedure
1. Assign IP addresses to interfaces. (Details not shown.)
2. Configure Device A:
# Configure a BGP connection.
<DeviceA> system-view
[DeviceA] bgp 100
[DeviceA-bgp-default] peer 10.1.1.2 as-number 200
[DeviceA-bgp-default] address-family ipv4 flowspec
[DeviceA-bgp-default-flowspec-ipv4] peer 10.1.1.2 enable
[DeviceA-bgp-default-flowspec-ipv4] peer 10.1.1.2 validation-disable
[DeviceA-bgp-flowspec-ipv4] quit
[DeviceA-bgp-default] quit
# Configure a Flowspec rule.
[DeviceA] flow-route route1
[DeviceA-flow-route-route1] if-match destination-ip 1.1.1.0 24
[DeviceA-flow-route-route1] if-match destination-port 10
[DeviceA-flow-route-route1] apply traffic-rate 20
[DeviceA-flow-route-route1] check flow-route-configuration
Traffic filtering rules:
Destination ip : 1.1.1.0 255.255.255.0
Destination port : 10
Traffic filtering actions:
Traffic rate : 20(kbps)
[DeviceA-flow-route-route1] commit
[DeviceA-flow-route-route1] quit
# Apply the Flowspec rule to the public network.
[DeviceA] flowspec
[DeviceA-flowspec] address-family ipv4
[DeviceA-flowspec-ipv4] flow-route route1
[DeviceA-flowspec-ipv4] quit
3. Configure Device B:
# Configure a BGP connection.
<DeviceB> system-view
[DeviceB] bgp 200
[DeviceB-bgp-default] peer 10.1.1.1 as-number 100
[DeviceB-bgp-default] address-family ipv4 flowspec
[DeviceB-bgp-default-flowspec-ipv4] peer 10.1.1.1 enable
[DeviceB-bgp-default-flowspec-ipv4] peer 10.1.1.1 validation-disable
[DeviceB-bgp-default-flowspec-ipv4] quit
[DeviceB-bgp-default] quit
Verifying the configuration
# On Device A, display BGP IPv4 Flowspec peer information.
[DeviceA] display bgp peer ipv4 flowspec
BGP local router ID: 192.168.150.1
Local AS number: 100
Total number of peers: 1 Peers in established state: 1
* - Dynamically created peer
Peer AS MsgRcvd MsgSent OutQ PrefRcv Up/Down State
10.1.1.2 200 10 12 0 0 00:06:40 Established
# On Device B, display BGP IPv4 Flowspec peer information.
[DeviceB] display bgp peer ipv4 flowspec
BGP local router ID: 192.168.150.2
Local AS number: 200
Total number of peers: 1 Peers in established state: 1
* - Dynamically created peer
Peer AS MsgRcvd MsgSent OutQ PrefRcv Up/Down State
10.1.1.1 100 10 12 0 0 00:06:40 Established
# On Device B, display BGP IPv4 Flowspec routing information.
[DeviceB] display bgp routing-table ipv4 flowspec
Total number of routes: 1
BGP local router ID is 192.168.150.2
Status codes: * - valid, > - best, d - dampened, h - history
s - suppressed, S - stale, i - internal, e - external
a - additional-path
Origin: i - IGP, e - EGP, ? - incomplete
Network NextHop MED LocPrf PrefVal Path/Ogn
* >e DEST:1.1.1.0/24/40
0.0.0.0 100 0 ?
# On Device B, display information about all Flowspec rules.
<DeviceB> display flow-route ipv4 all
Total number of flow-routes: 1
Flow-Route (ID 0x0)
BGP instance : default
Traffic filtering rules:
Destination IP : 1.1.1.0 255.255.255.0
Destination port : 10
Traffic filtering actions:
Traffic rate : 20(kbps)