- Table of Contents
-
- 05-Layer 3—IP Routing Configuration Guide
- 00-Preface
- 01-Basic IP routing configuration
- 02-Static routing configuration
- 03-RIP configuration
- 04-OSPF configuration
- 05-IS-IS configuration
- 06-BGP configuration
- 07-Policy-based routing configuration
- 08-IPv6 static routing configuration
- 09-RIPng configuration
- 10-OSPFv3 configuration
- 11-IPv6 policy-based routing configuration
- 12-Routing policy configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Policy-based routing configuration | 179.60 KB |
Contents
Restrictions and guidelines: PBR configuration
Setting match criteria for a node
Configuring actions for a node
Specifying a policy for local PBR
Specifying a policy for interface PBR
Specifying a policy for outbound PBR on a VXLAN tunnel interface
Display and maintenance commands for PBR
Example: Configuring packet type-based local PBR
Example: Configuring packet type-based interface PBR
Example: Configuring VXLAN ID-based outbound PBR
Configuring PBR
About PBR
Policy-based routing (PBR) uses user-defined policies to route packets. A policy can specify parameters for packets that match specific criteria such as ACLs or that have specific VXLAN IDs. The parameters include the next hop, output interface, default next hop, and default output interface.
Packet forwarding process
When the device receives a packet, the device searches the PBR policy for a matching node to forward that packet.
· If a matching node is found and its match mode is permit, the device performs the following operations:
a. Uses the next hops or output interfaces specified on the node to forward the packet.
b. Searches the routing table for a route (except the default route) to forward the packet if one of the following conditions exists:
- No next hops or output interfaces are specified on the node.
- Forwarding failed based on the next hops or output interfaces.
c. Uses the default next hops or default output interfaces specified on the node to forward the packet if one of the following conditions exists:
- No matching route was found in the routing table.
- The routing table-based forwarding failed.
d. Uses the default route to forward the packet if one of the following conditions exists:
- No default next hops or default output interfaces are specified on the node.
- The forwarding failed based on the default next hops or default output interfaces.
· The device performs routing table lookup to forward the packet in either of the following conditions:
¡ No matching node is found.
¡ A matching node is found, but its match mode is deny.
PBR types
PBR includes the following types:
· Local PBR—Guides the forwarding of locally generated packets, such as ICMP packets generated by using the ping command.
· Interface PBR—Guides the forwarding of packets received on an interface.
· Outbound PBR on a VXLAN tunnel interface—Guides the forwarding of outgoing packets when equal-cost routes exist.
Policy
A policy includes match criteria and actions to be taken on the matching packets. A policy can have one or multiple nodes as follows:
· Each node is identified by a node number. A smaller node number has a higher priority.
· A node contains if-match and apply clauses. An if-match clause specifies a match criterion, and an apply clause specifies an action.
· A node has a match mode of permit or deny.
A policy compares packets with nodes in priority order. If a packet matches the criteria on a node, it is processed by the action on the node. If the packet does not match any criteria on the node, it goes to the next node for a match. If the packet does not match the criteria on any node, the device performs a routing table lookup.
Relationship between if-match clauses
On a node, you can specify multiple types of if-match clauses but only one if-match clause for each type.
To match a node, a packet must match all types of the if-match clauses for the node.
Relationship between apply clauses
You can specify multiple apply clauses for a node, but some of them might not be executed. For more information about relationship between apply clauses, see "Configuring actions for a node."
Relationship between the match mode and clauses on the node
|
Does a packet match all the if-match clauses on the node? |
Match mode |
|
|
Permit |
Deny |
|
|
Yes. |
· If the node contains apply clauses, PBR executes the apply clauses on the node. ¡ If PBR-based forwarding succeeds, PBR does not compare the packet with the next node. ¡ If PBR-based forwarding fails, PBR does not compare the packet with the next node. · If the node does not contain apply clauses, the device performs a routing table lookup for the packet. |
The device performs a routing table lookup for the packet. |
|
No. |
PBR compares the packet with the next node. |
PBR compares the packet with the next node. |
|
|
NOTE: A node that has no if-match clauses matches any packet. |
PBR and Track
PBR can work with the Track feature to dynamically adapt the availability status of an apply clause to the link status of a tracked object. The tracked object can be a next hop, output interface, default next hop, or default output interface.
· When the track entry associated with an object changes to Negative, the apply clause is invalid.
· When the track entry changes to Positive or NotReady, the apply clause is valid.
For more information about Track and PBR collaboration, see High Availability Configuration Guide.
Restrictions and guidelines: PBR configuration
If a packet destined for the local device matches a PBR policy, PBR will execute the apply clauses in the policy, including the clause for forwarding. When you configure a PBR policy, be careful to avoid this situation.
PBR tasks at a glance
To configure PBR, perform the following tasks:
Enable VXLAN mode for PBR on VTEPs to direct packets to VXLAN tunnels.
About this task
Restrictions and guidelines
Procedure
ip policy-based-route vxlan-mode enable
By default, VXLAN-mode PBR is disabled.
b. Setting match criteria for a node
c. Configuring actions for a node
4. Specifying a policy for PBR
Choose the following tasks as needed:
¡ Specifying a policy for local PBR
¡ Specifying a policy for interface PBR
¡ Specifying a policy for outbound PBR on a VXLAN tunnel interface
Enabling VXLAN-mode PBR
About this task
VXLAN-mode PBR enables you to guide packets from a site-facing interface on a VXLAN VTEP to a VXLAN tunnel by using a PBR policy. If VXLAN-mode PBR is not enabled, the PBR policy on a site-facing interface cannot guide packets to a VXLAN tunnel.
Restrictions and guidelines
Enable VXLAN-mode PBR before you apply a PBR policy to a site-facing interface. This task requires PBR to update forwarding entries, which is time-consuming and might cause inadequate table entry resources.
Procedure
1. Enter system view.
system-view
2. Enable VXLAN-mode PBR.
ip policy-based-route vxlan-mode enable
By default, VXLAN-mode PBR is disabled.
Configuring a policy
Creating a node
1. Enter system view.
system-view
2. Create a node for a policy, and enter its view.
policy-based-route policy-name [ deny | permit ] node node-number
3. (Optional.) Configure a description for the policy node.
description text
By default, no description is configured for a policy node.
Setting match criteria for a node
Restrictions and guidelines
On a transport network device, you can configure PBR on the Layer 3 interface to guide the forwarding of packets based on VXLAN IDs. On a VTEP, you can configure PBR on the tunnel interface to guide the forwarding of packets based on VXLAN IDs.
Procedure
1. Enter system view.
system-view
2. Enter policy node view.
policy-based-route policy-name [ deny | permit ] node node-number
3. Set match criteria.
¡ Set an ACL match criterion.
if-match acl { acl-number | name acl-name }
By default, no ACL match criterion is set.
The ACL match criterion cannot match Layer 2 information.
When using the ACL to match packets, PBR ignores the action (permit or deny) and time range settings in the ACL.
¡ Set a VXLAN match criterion.
if-match vxlan-id vxlan-id
By default, no VXLAN match criterion is set.
Configuring actions for a node
About this task
The apply clauses allow you to specify the actions to be taken on matching packets on a node.
The following apply clauses determine the packet forwarding paths in a descending order:
· apply access-vpn vpn-instance
· apply next-hop
· apply output-interface
· apply default-next-hop
· apply default-output-interface
PBR supports the apply clauses in Table 1.
Table 1 Apply clauses supported in PBR
|
Clause |
Meaning |
Remarks |
|
apply precedence |
Sets an IP precedence. |
This clause is always executed. |
|
apply access-vpn vpn-instance |
Sets VPN instances. |
If a packet matches a forwarding entry of a specified VPN instance, it is forwarded in the VPN instance. |
|
apply next-hop and apply output-interface |
Sets next hops and sets output interfaces. |
If both clauses are configured, only the apply next-hop clause is executed. |
|
apply default-next-hop and apply default-output-interface |
Sets default next hops and sets default output interfaces. |
If both clauses are configured, only the apply default-next-hop clause is executed. The clauses take effect only in the following cases: · No next hops or output interfaces are set or the next hops and output interfaces are invalid. · The packet does not match any route in the routing table. |
|
apply fail-action-drop next-hop |
Sets the action that drops matching packets when all next hops become invalid. |
If no next hops are specified on the policy node, this clause drops all packets that match the policy node. This clause is typically used in scenarios that require strict routing paths. |
Restrictions and guidelines
For outbound PBR on a VXLAN tunnel interface, you can specify only one next hop and the next hop must be directly connected.
If you specify a next hop or default next hop, PBR periodically performs a lookup in the FIB table to determine its availability. Temporary service interruption might occur if PBR does not update the route immediately after its availability status changes.
Configuring actions to modify packet fields
1. Enter system view.
system-view
2. Enter policy node view.
policy-based-route policy-name [ deny | permit ] node node-number
3. Set an IP precedence.
apply precedence { type | value }
By default, no IP precedence is specified.
Configuring actions to direct packet forwarding
1. Enter system view.
system-view
2. Enter policy node view.
policy-based-route policy-name [ deny | permit ] node node-number
3. Configure actions.
¡ Set VPN instances.
apply access-vpn vpn-instance vpn-instance-name
By default, no VPN instances are specified.
After configuring this command for a policy node, you can configure only an ACL match criterion to match the input interface, source IP address, and destination IP address of packets.
If you apply the PBR policy configured with this command to a Layer 3 Ethernet interface or Layer 3 aggregate interface, the PBR policy also applies to all the associated subinterfaces. If you apply the PBR policy configured with this command to a Layer 3 Ethernet subinterface or Layer 3 aggregate subinterface, the PBR policy also applies to its primary interface and other associated subinterfaces.
¡ Set next hops.
apply next-hop [ vpn-instance vpn-instance-name ] { ip-address [ direct ] [ track track-entry-number ] }&<1-2>
By default, no next hops are specified.
On a node, you can specify a maximum of two next hops for backup in one command line or by executing this command multiple times.
If multiple next hops on the same subnet are specified for backup, the device first uses the subnet route for the next hops to forward packets when the primary next hop fails. If the subnet route is not available, the device selects a backup next hop.
¡ Set output interfaces.
apply output-interface interface-type interface-number [ track track-entry-number ]
By default, no output interfaces are specified.
¡ Set default next hops.
apply default-next-hop [ vpn-instance vpn-instance-name ] { ip-address [ direct ] [ track track-entry-number ] }&<1-2>
By default, no default next hops are specified.
On a node, you can specify a maximum of two default next hops for backup in one command line or by executing this command multiple times.
¡ Set default output interfaces.
apply default-output-interface interface-type interface-number [ track track-entry-number ]
By default, no default output interfaces are specified.
¡ Set the action that drops matching packets when all next hops specified on the policy node are invalid.
apply fail-action-drop next-hop
By default, the drop action is not configured. The matching packets are forwarded based on the typical packet forwarding process as described in "Packet forwarding process."
This command does not apply to software-forwarded packets.
Specifying a policy for PBR
|
IMPORTANT: An S12500X-AF H card operating in normal mode (set the by the hardware-resource vxlan command) supports only local PBR and interface-based PBR. It does not support outbound PBR on a VXLAN tunnel interface. An S12500X-AF H card operating in MAC address mode supports local PBR, interface-based PBR, and outbound PBR on a VXLAN tunnel interface. |
Specifying a policy for local PBR
About this task
Perform this task to specify a policy for local PBR to guide the forwarding of locally generated packets.
Restrictions and guidelines
You can specify only one policy for local PBR and must make sure the specified policy already exists. Before you apply a new policy, you must first remove the current policy.
Local PBR might affect local services such as ping and Telnet. When you use local PBR, make sure you fully understand its impact on local services of the device.
Procedure
1. Enter system view.
system-view
2. Specify a policy for local PBR.
ip local policy-based-route policy-name
By default, local PBR is not enabled.
Specifying a policy for interface PBR
About this task
Perform this task to apply a policy to an interface to guide the forwarding of packets received on the interface.
To apply a policy to multiple VLAN interfaces at the same time, you can use the ip policy-based-route apply command. Using this command simplifies configuration and saves device resources.
Restrictions and guidelines
You can apply only one policy to an interface and must make sure the specified policy already exists. Before you can apply a new interface PBR policy to an interface, you must first remove the current policy from the interface.
You can apply a policy to multiple interfaces.
In a VXLAN IP gateway or EVPN gateway deployment, when you apply a policy to an interface on a border gateway, follow these restrictions and guidelines:
· If the interface is a Layer 3 Ethernet interface, the policy is also applied to its subinterfaces. For more information about VXLAN IP gateway deployment, see VXLAN Configuration Guide.
· If the interface is a Layer 3 aggregate interface, the policy is also applied to its subinterfaces. For more information about EVPN gateway deployment, see EVPN Configuration Guide.
When you use interface PBR in conjunction with VXLAN-mode PBR to guide packets on a site-facing interface to a VXLAN tunnel, enable VXLAN-mode PBR before you apply the PBR policy. For more information about VXLAN-mode PBR, see "Enabling VXLAN-mode PBR."
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify a policy for interface PBR.
ip policy-based-route policy-name [ share-mode ]
By default, no interface policy is applied to an interface.
4. (Optional.) Specify a policy for a list of VLAN interfaces:
a. Return to system view.
quit
b. Specify a policy for a list of VLAN interfaces.
ip policy-based-route policy-name apply vlan-interface interface-list
By default, no policy is applied to the specified VLAN interfaces.
Use this command only when you want to specify a policy for multiple VLAN interfaces.
Specifying a policy for outbound PBR on a VXLAN tunnel interface
About this task
In a VXLAN network, equal-cost routes might exist between two endpoints of a VXLAN tunnel. The device cannot route VXLAN packets to the exact next hop. To choose the desired next hop for outgoing VXLAN packets, use outbound PBR on the VXLAN tunnel interface.
Restrictions and guidelines
You can specify only one policy to a VXLAN tunnel interface and must make sure the specified policy already exists. Before you can apply a new policy to an interface, you must first remove the current policy from the interface.
Procedure
1. Enter system view.
system-view
2. Create a VXLAN tunnel interface and enter tunnel interface view.
interface tunnel tunnel-number mode vxlan
The endpoints of a tunnel must use the same tunnel mode to correctly transmit packets.
3. Specify a policy for outbound PBR.
ip policy-based-route policy-name egress
By default, no policy is specified for outbound PBR on a VXLAN tunnel interface.
Display and maintenance commands for PBR
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display PBR policy information. |
display ip policy-based-route [ policy policy-name ] |
|
Display the PBR configuration and statistics for a VLAN interface. |
In standalone mode: display ip policy-based-route apply vlan-interface interface-number [ slot slot-number ] In IRF mode: display ip policy-based-route apply vlan-interface interface-number [ chassis chassis-number slot slot-number ] |
|
Display outbound PBR configuration and statistics for an interface. |
In standalone mode: display ip policy-based-route egress interface interface-type interface-number [ slot slot-number ] In IRF mode: display ip policy-based-route egress interface interface-type interface-number [ chassis chassis-number slot slot-number ] |
|
Display interface PBR configuration and statistics. |
In standalone mode: display ip policy-based-route interface interface-type interface-number [ slot slot-number ] In IRF mode: display ip policy-based-route interface interface-type interface-number [ chassis chassis-number slot slot-number ] |
|
Display local PBR configuration and statistics. |
In standalone mode: display ip policy-based-route local [ slot slot-number ] In IRF mode: display ip policy-based-route local [ chassis chassis-number slot slot-number ] |
|
Display PBR configuration. |
display ip policy-based-route setup |
|
Clear PBR statistics. |
reset ip policy-based-route statistics [ policy policy-name ] |
PBR configuration examples
Example: Configuring packet type-based local PBR
Network configuration
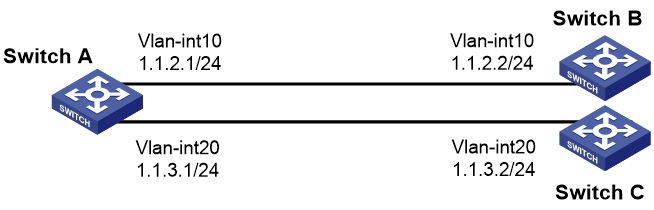
As shown in Figure 1, Switch B and Switch C do not have a route to reach each other.
Configure PBR on Switch A to forward all TCP packets to the next hop 1.1.2.2 (Switch B).
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
1. Configure Switch A:
# Create VLAN 10 and VLAN 20.
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] vlan 20
[SwitchA-vlan20] quit
# Configure the IP addresses of VLAN-interface 10 and VLAN-interface 20.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 1.1.2.1 24
[SwitchA-Vlan-interface10] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.3.1 24
[SwitchA-Vlan-interface20] quit
# Configure ACL 3101 to match TCP packets.
[SwitchA] acl advanced 3101
[SwitchA-acl-ipv4-adv-3101] rule permit tcp
[SwitchA-acl-ipv4-adv-3101] quit
# Configure Node 5 for the policy aaa to forward TCP packets to next hop 1.1.2.2.
[SwitchA] policy-based-route aaa permit node 5
[SwitchA-pbr-aaa-5] if-match acl 3101
[SwitchA-pbr-aaa-5] apply next-hop 1.1.2.2
[SwitchA-pbr-aaa-5] quit
# Configure local PBR by applying the policy aaa to Switch A.
[SwitchA] ip local policy-based-route aaa
2. Configure Switch B:
# Create VLAN 10.
<SwitchB> system-view
[SwitchB] vlan 10
[SwitchB-vlan10] quit
# Configure the IP address of VLAN-interface 10.
[SwitchB] interface vlan-interface 10
[SwitchB-Vlan-interface10] ip address 1.1.2.2 24
3. Configure Switch C:
# Create VLAN 20.
<SwitchC> system-view
[SwitchC] vlan 20
[SwitchC-vlan20] quit
# Configure the IP address of VLAN-interface 20.
[SwitchC] interface vlan-interface 20
[SwitchC-Vlan-interface20] ip address 1.1.3.2 24
Verifying the configuration
1. Perform telnet operations to verify that local PBR on Switch A operates as configured to forward the matching TCP packets to the next hop 1.1.2.2 (Switch B), as follows:
# Verify that you can telnet to Switch B from Switch A successfully. (Details not shown.)
# Verify that you cannot telnet to Switch C from Switch A. (Details not shown.)
2. Verify that Switch A forwards packets other than TCP packets through VLAN-interface 20. For example, verify that you can ping Switch C from Switch A. (Details not shown.)
Example: Configuring packet type-based interface PBR
Network configuration
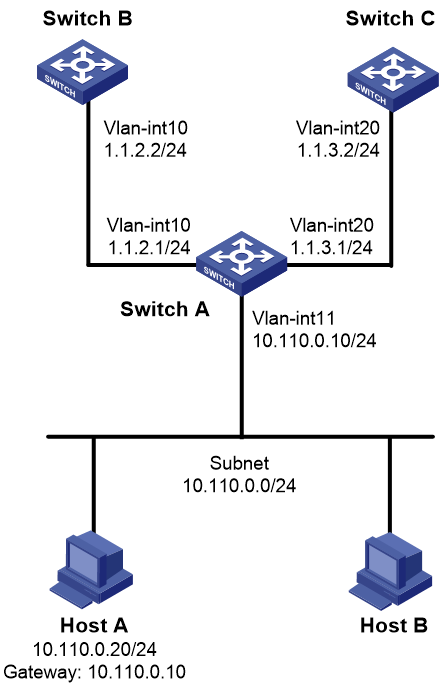
As shown in Figure 2, Switch B and Switch C do not have a route to reach each other.
Configure PBR on Switch A to forward all TCP packets received on VLAN-interface 11 to the next hop 1.1.2.2 (Switch B).
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
1. Make sure Switch B and Switch C can reach Host A. (Details not shown.)
2. Configure Switch A:
# Create VLAN 10 and VLAN 20.
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] vlan 20
[SwitchA-vlan20] quit
# Configure the IP addresses of VLAN-interface 10 and VLAN-interface 20.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 1.1.2.1 24
[SwitchA-Vlan-interface10] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.3.1 24
[SwitchA-Vlan-interface20] quit
# Configure ACL 3101 to match TCP packets.
[SwitchA] acl advanced 3101
[SwitchA-acl-ipv4-adv-3101] rule permit tcp
[SwitchA-acl-ipv4-adv-3101] quit
# Configure Node 5 for the policy aaa to forward TCP packets to next hop 1.1.2.2.
[SwitchA] policy-based-route aaa permit node 5
[SwitchA-pbr-aaa-5] if-match acl 3101
[SwitchA-pbr-aaa-5] apply next-hop 1.1.2.2
[SwitchA-pbr-aaa-5] quit
# Configure interface PBR by applying the policy aaa to VLAN-interface 11.
[SwitchA] interface vlan-interface 11
[SwitchA-Vlan-interface11] ip address 10.110.0.10 24
[SwitchA-Vlan-interface11] ip policy-based-route aaa
[SwitchA-Vlan-interface11] quit
Verifying the configuration
1. Perform telnet operations to verify that interface PBR on Switch A operates as configured to forward the matching TCP packets to the next hop 1.1.2.2 (Switch B), as follows:
# Verify that you can telnet to Switch B from Host A successfully. (Details not shown.)
# Verify that you cannot telnet to Switch C from Host A. (Details not shown.)
2. Verify that Switch A forwards packets other than TCP packets through VLAN-interface 20. For example, verify that you can ping Switch C from Host A. (Details not shown.)
Example: Configuring VXLAN ID-based outbound PBR
Network configuration
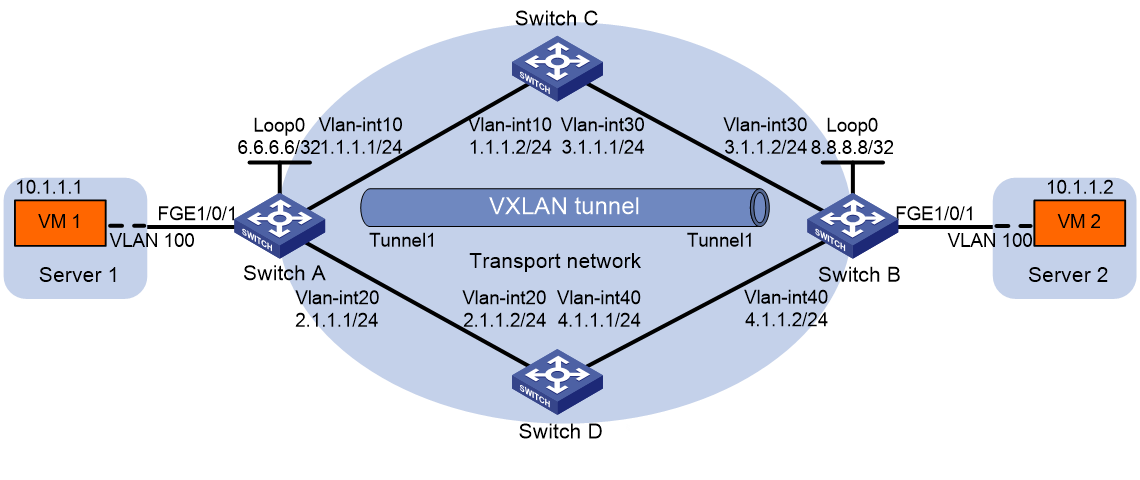
As shown in Figure 3, Switch C and Switch D are Layer 3 switches in the transport network. VXLAN 10 is configured on Switch A and Switch B (the VTEPs) to provide Layer 2 connectivity for VM 1 and VM 2 across the network sites.
· A VXLAN tunnel between the VTEPs is manually established.
· The tunnel is assigned to the VXLAN.
· Remote MAC address learning is enabled.
· The VTEPs flood VXLAN traffic in unicast mode (head-end replication).
Traffic from VM 1 to VM 2 enters the VXLAN tunnel through one of the equal-cost routes between the VXLAN endpoints. The route points to the next hop at 2.1.1.2.
Configure PBR for Tunnel 1 on Switch A to forward the outgoing traffic through the route with the next hop at 1.1.1.2.
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
1. Configure IP addresses and unicast routing settings:
# Assign IP address to interfaces, as shown in Figure 3. (Details not shown.)
# Configure OSPF on all switches in the transport network. (Details not shown.)
2. Configure Switch A:
# Enable L2VPN.
<SwitchA> system-view
[SwitchA] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchA] undo vxlan ip-forwarding
# Create VSI vpna and VXLAN 10.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# Assign an IP address to Loopback 0. The IP address will be used as the source IP address of the VXLAN tunnel.
[SwitchA] interface loopback 0
[SwitchA-Loopback0] ip address 6.6.6.6 255.255.255.255
[SwitchA-Loopback0] quit
# Create a VXLAN tunnel to Switch B. The tunnel interface is Tunnel 1. The tunnel destination is Loopback 0 at 8.8.8.8 on Switch B.
[SwitchA] interface tunnel 1 mode vxlan
[SwitchA-Tunnel1] source 6.6.6.6
[SwitchA-Tunnel1] destination 8.8.8.8
[SwitchA-Tunnel1] quit
# Assign Tunnel 1 to VXLAN 10.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] tunnel 1
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# Create Ethernet service instance 1000 on FortyGigE 1/0/1 to match frames from VLAN 10.
[SwitchA] interface fortygige 1/0/1
[SwitchA-FortyGigE1/0/1] service-instance 1000
[SwitchA-FortyGigE1/0/1-srv1000] encapsulation s-vid 10
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchA-FortyGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchA-FortyGigE1/0/1-srv1000] quit
[SwitchA-FortyGigE1/0/1] quit
# Configure node 5 in policy aaa to forward packets that match VXLAN ID 10 to 1.1.1.2.
[SwitchA] policy-based-route aaa permit node 5
[SwitchA-pbr-aaa-5] if-match vxlan 10
[SwitchA-pbr-aaa-5] apply next-hop 1.1.1.2
[SwitchA-pbr-aaa-5] quit
# Apply the policy to Tunnel 1 to guide the forwarding of outgoing packets.
[SwitchA] interface tunnel 1
[SwitchA-Tunnel1] ip policy-based-route aaa egress
[SwitchA-Tunnel1] quit
3. Configure Switch B:
# Enable L2VPN.
<SwitchB> system-view
[SwitchB] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchB] undo vxlan ip-forwarding
# Create VSI vpna and VXLAN 10.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# Assign an IP address to Loopback 0. The IP address will be used as the source IP address of the VXLAN tunnel.
[SwitchB] interface loopback 0
[SwitchB-Loopback0] ip address 8.8.8.8 255.255.255.255
[SwitchB-Loopback0] quit
# Create a VXLAN tunnel to Switch A. The tunnel interface is Tunnel 1. The tunnel destination is Loopback 0 at 6.6.6.6 on Switch A.
[SwitchB] interface tunnel 1 mode vxlan
[SwitchB-Tunnel1] source 8.8.8.8
[SwitchB-Tunnel1] destination 6.6.6.6
[SwitchB-Tunnel1] quit
# Assign Tunnel 1 to VXLAN 10.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] tunnel 1
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# Create Ethernet service instance 1000 on FortyGigE 1/0/1 to match frames from VLAN 10.
[SwitchB] interface fortygige 1/0/1
[SwitchB-FortyGigE1/0/1] service-instance 1000
[SwitchB-FortyGigE1/0/1-srv1000] encapsulation s-vid 10
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchB-FortyGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchB-FortyGigE1/0/1-srv1000] quit
[SwitchB-FortyGigE1/0/1] quit