- Table of Contents
-
- 17-Network Management and Monitoring Configuration Guide
- 00-Preface
- 01-System maintenance and debugging configuration
- 02-NQA configuration
- 03-NTP configuration
- 04-EAA configuration
- 05-Process monitoring and maintenance configuration
- 06-NETCONF configuration
- 07-Information center configuration
- 08-SNMP configuration
- 09-NetStream configuration
- 10-RMON configuration
- 11-Flow log configuration
- 12-Event MIB configuration
- 13-Packet capture configuration
- 14-Fast log output configuration
- 15-Mirroring configuration
- 16-GOLD configuration
- 17-BFD configuration
- 18-Track configuration
- 19-Interface collaboration configuration
- 20-Process placement configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 13-Packet capture configuration | 66.30 KB |
Restrictions and guidelines: Packet capture configuration
Packet capture tasks at a glance
Configuring packet capture settings
Display and maintenance commands for packet capture
Packet capture configuration examples
Example: Configuring packet capture (in standalone mode)
Configuring packet capture
About packet capture
The packet capture feature captures incoming and outgoing packets, generates packet capture records, and saves the records to a .cap file. The file can reside on the device or a remote file server. You can use a packet analyzer such as Wireshark to view the file for traffic analysis.
The minimum packet capture unit is a packet. The packet capture process is as follows:
1. The device captures a specific number of bytes from a packet and generates a packet capture record, ignoring the remaining part of the packet (if any).
2. The device saves the packet capture record in memory.
3. When the maximum number of packet capture records for a file is reached, the device saves the records to a file and clears the records in memory.
Restrictions and guidelines: Packet capture configuration
Start packet capture only when necessary. Packet capture affects device performance.
Only one packet capture process can run on the device.
You can configure packet capture parameters only when packet capture is not started.
If packet capture saves .cap files on the device, back up the .cap files on the device as required after you finish packet capture. Starting packet capture again deletes the existing .cap files.
Packet capture is not supported for non-default contexts that use their own respective interfaces. You can start packet capture only on the default context to capture packets of the default context and non-default contexts that share interfaces. For more information about contexts, see context configuration in Virtual Technologies Configuration Guide.
To capture packets of a context, you must configure flow mirroring to mirror the packets to the main security engine of the security engine group to which the context belongs. For more information about flow mirroring, see flow mirroring configuration in Network Management and Monitoring Configuration Guide. For more information about security engine groups, see context configuration in Virtual Technologies Configuration Guide.
You can identify the packets to be captured only by specifying an ACL. You cannot identify the packets to be captured by specifying an interface.
Packet capture tasks at a glance
To configure packet capture, perform the following tasks:
1. Configuring packet capture settings
Configuring packet capture settings
1. Enter system view.
system-view
2. Set the maximum packet size for a packet capture record.
packet-capture max-bytes bytes
By default, the maximum packet size is 1600 bytes for a packet capture record.
To capture all bytes of packets, make sure the maximum packet size for a packet capture record is equal to or greater than the interface MTU.
3. Set the maximum number of packet capture records for a file.
packet-capture max-file-packets number
By default, the maximum number of packet capture records is 100 for a file.
4. Specify the storage directory for the .cap files.
packet-capture storage { local [ limit limit-space ] | remote serverpath [ vpn-instance vpn-instance-name ] [ user username [ password { cipher | simple } string ] ] }
The default storage directory is the pcap directory of the default file system on the active MPU. (In standalone mode.)
The default storage directory is the pcap directory of the default file system on the global active MPU. (In IRF mode.)
Starting packet capture
1. Enter system view.
system-view
2. Start packet capture.
packet-capture start acl { acl-number | ipv6 acl-number }
By default, the system does not capture packets.
Stopping packet capture
About this task
Saving packet capture records to a file takes time. The packet-capture stop command without the immediately keyword saves all packet capture records to a file before stopping packet capture. If you do not want to use the packet capture records in memory, execute the packet-capture stop immediately command.
Procedure
1. Enter system view.
system-view
2. Stop packet capture.
packet-capture stop [ immediately ]
Display and maintenance commands for packet capture
Execute display commands in any view.
|
Command |
|
|
Display packet capture settings and status information. |
display packet-capture status |
Packet capture configuration examples
Example: Configuring packet capture (in standalone mode)
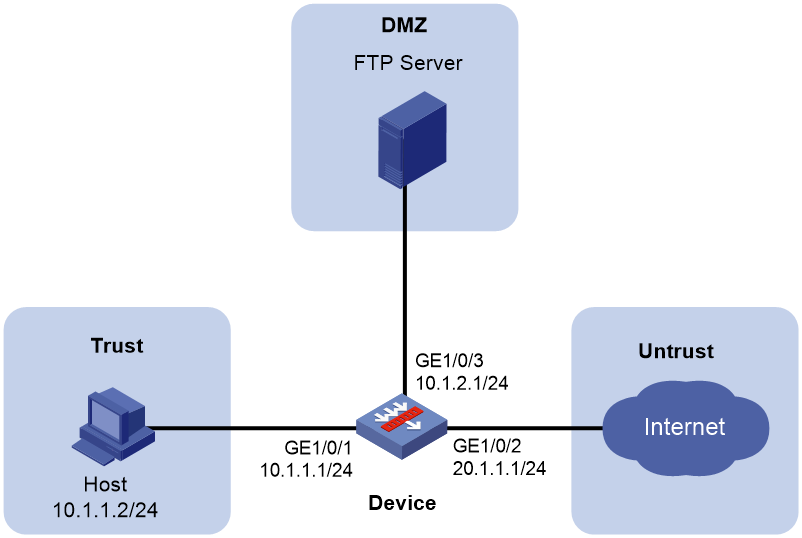
Network configuration
As shown in Figure 1, capture packets between 10.1.1.0/24 and 20.1.1.0/24 on GigabitEthernet 1/0/1. Set the maximum packet size for a packet capture record to 3000 bytes. Use a remote file server to save the .cap files.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 10.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
3. Configure a security policy:
# Configure a rule named capturelocalout to allow the device to transfer captured packets to the FTP server. In this example, the FTP server address is 10.1.2.2/24.
[Device] security-policy ip
[Device-security-policy-ip] rule name capturelocalout
[Device-security-policy-ip-1-capturelocalout] source-zone local
[Device-security-policy-ip-1-capturelocalout] destination-zone dmz
[Device-security-policy-ip-1-capturelocalout] destination-ip-host 10.1.2.2
[Device-security-policy-ip-1-capturelocalout] action pass
[Device-security-policy-ip-1-capturelocalout] quit
[Device-security-policy-ip] quit
4. Configure flow mirroring:
# Configure IPv4 advanced ACL 3001 to identify packets between 10.1.1.0/24 and 20.1.1.0/24.
<Device> system-view
[Device] acl advanced 3001
[Device-acl-ipv4-adv-3001] rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 20.1.1.0 0.0.0.255
[Device-acl-ipv4-adv-3001] rule 1 permit ip source 20.1.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[Device-acl-ipv4-adv-3001] quit
# Configure traffic class abc to use ACL 3001 to match packets.
[Device] traffic classifier abc
[Device-classifier-abc] if-match acl 3001
[Device-classifier-abc] quit
# Configure traffic behavior abc to mirror traffic to the main security engine of the security engine group to which the context belongs. In this example, the interface on the main security engine is Blade 4/0/1.
[Device] traffic behavior abc
[Device-behavior-abc] mirror-to interface blade 4/0/1
[Device-behavior-abc] quit
# Configure QoS policy abc to associate traffic class abc with traffic behavior abc.
[Device] qos policy abc
[Device-qospolicy-abc] classifier abc behavior abc
[Device-qospolicy-abc] quit
# Apply QoS policy abc to both directions of interface GigabitEthernet 1/0/1 in enhanced mode.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] qos apply policy abc inbound enhancement
[Device-GigabitEthernet1/0/1] qos apply policy abc outbound enhancement
[Device-GigabitEthernet1/0/1] quit
5. Configure packet capture:
# Set the storage directory for the .cap files. Specify the username and password for accessing the FTP server.
[Device] packet-capture storage remote ftp://ftp.remote.com/pcap/ user zhangsan password packet-capture storage remote ftp:
# Set the maximum packet size for a packet capture record.
[Device] packet-capture max-bytes 3000
# Start packet capture to capture packets identified by ACL 3001.
[Device] packet-capture start acl 3001
Verifying the configuration
# Display packet capture settings and status information.
[Device] display packet-capture status
Capture status: Started
Filter: ACL 3001
# Use a packet analyzer to display captured packets. (Details not shown.)