- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 18-WAF | 57.93 KB |
This help contains the following topics:
Introduction
The web application firewall (WAF) feature enables devices to monitor HTTP and HTTPS traffic to and from web applications for malicious activity and to proactively take prevention actions.
WAF profiles
WAF is implemented based on WAF profiles. A WAF profile contains a set of WAF signatures to match packets and the actions for the matching packets.
WAF signatures
The device compares packets with WAF signatures to detect, classify, and prevent network attacks.
Each WAF signature contains multiple attributes, including attack category, action, protected target, severity level, and direction. You can set criteria to filter WAF signatures that a WAF profile uses based on the signature attributes.
Signature exceptions
WAF signatures have default signature actions and enabling status.
To change the enabling status or action for a WAF signature in a WAF profile, set the WAF signature as a signature exception in the WAF profile. The action specified for the signature exception takes precedence over the global signature action.
WAF actions
When the device detects a packet matching a WAF signature, it takes the global action for the signature on the packet.
The device supports the following WAF actions:
· Blacklist—Drops matching packets and adds the sources of the packets to the IP blacklist. If the IP blacklist feature is enabled, packets from the blacklisted sources will be blocked for the blacklist period. If the IP blacklist feature is not enabled, packets from the blacklisted sources are not blocked.
For more information about the IP blacklist feature, see attack defense online help.
To configure the blacklist period for the blacklist action, go to Objects > APPSecurity > Security Actions > Block.
· Drop—Drops matching packets.
· Permit—Permits matching packets to pass.
· Reset—Closes the TCP or UDP connections for matching packets by sending TCP reset messages or ICMP port unreachable messages.
· Redirect—Redirects matching packets to a webpage.
· Default—Uses the default signature action.
· Capture—Captures matching packets.
· Logging—Logs matching packets.
WAF mechanism
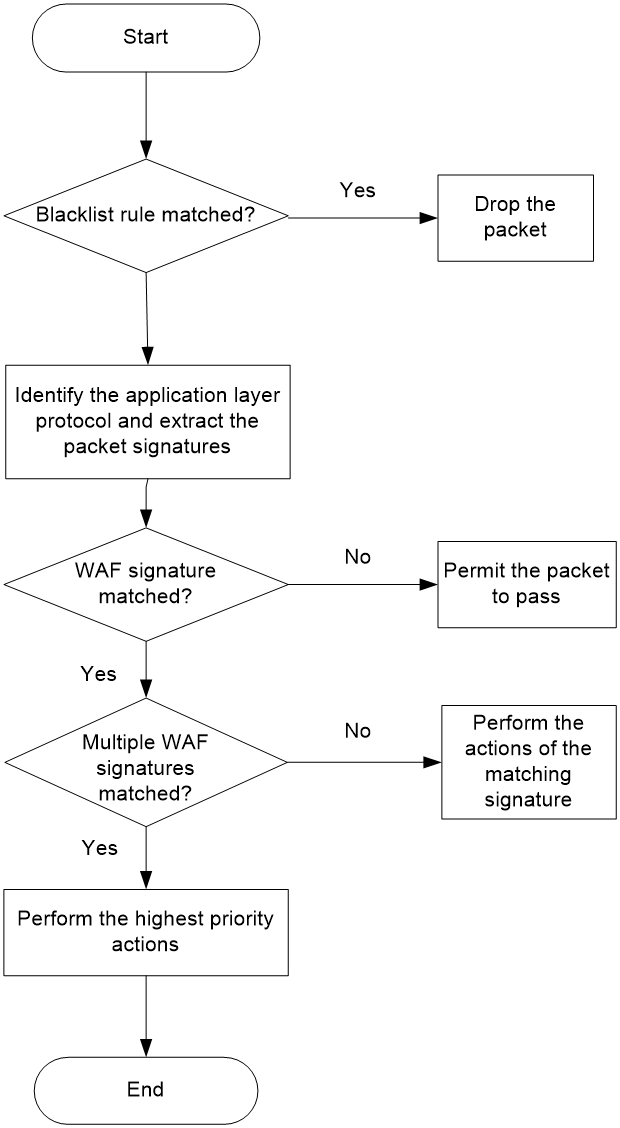
As shown in Figure 1, upon receiving a packet, the device performs the following operations:
1. The device compares the packet with the IP blacklist rules.
¡ If a matching rule is found, the device drops the packet.
¡ If no matching rule is found, the device goes to step 2.
2. The device compares the packet with the security policies.
If the packet matches a security policy that is associated with a WAF profile, the device identifies the packet application layer protocol and extracts the packet signatures.
3. The device determines the actions for the packet by comparing the extracted packet signatures with the WAF signatures in the WAF profile:
¡ If the packet does not match any WAF signatures, the device permits the packet to pass.
¡ If the packet matches only one WAF signature, the device takes the signature actions.
¡ If the packet matches multiple WAF signatures, the device uses the following rules to select the actions:
- If the matching WAF signatures have two or more actions, including redirect, drop, permit, and reset, the device takes the action of the highest priority. The actions in descending order of priority are reset, redirect, drop, and permit.
- The device will execute the blacklist, capture, and logging actions if they are in the matching WAF signatures.
Restrictions and guidelines
· The WAF module requires a license to run on the device. If the license expires, you can still use the WAF functions but you can no longer upgrade the WAF signature library on the device. For more information about licenses, see license online help.
· Changes to WAF profiles and WAF signatures must be activated to take effect. By default, the system automatically activates the changes 40 seconds after the changes are made. You can also click Submit to activate the changes immediately.
Configure WAF
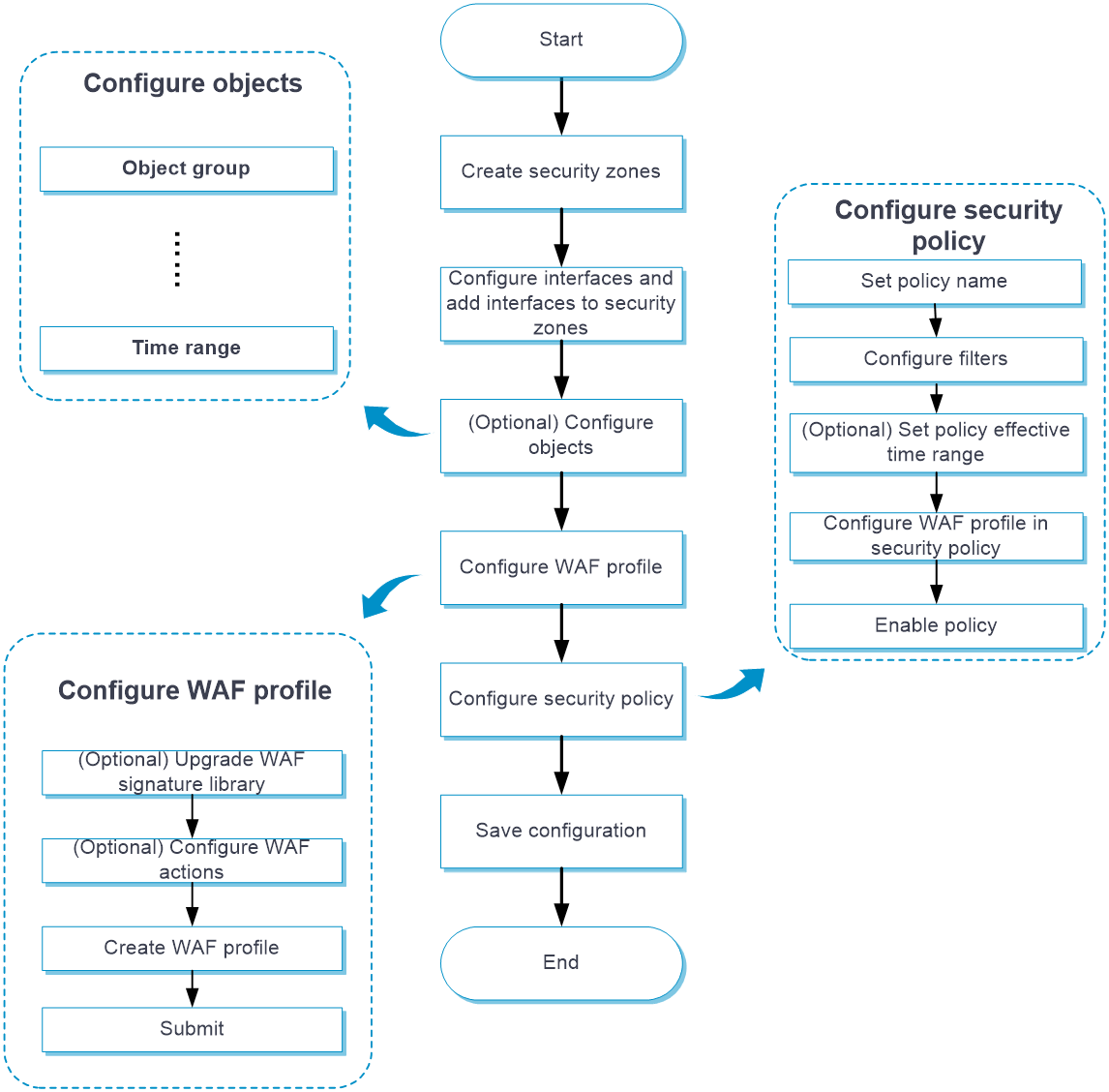
Configure WAF as shown in Figure 2.
Figure 2 WAF configuration procedure
Configure a WAF profile
The device provides a predefined WAF profile named default. The default WAF profile uses all enabled WAF signatures on the device and cannot be modified or deleted.
You can also create WAF profiles on the device as needed..
You can configure global action for a WAF profile or change the action for individual WAF signatures in the profile.
The system selects the actions for packets matching a WAF signature in the following order:
1. Actions configured for the WAF signature as a signature exception in the WAF profile.
2. Global action configured for the WAF profile.
3. Default action of the WAF signature.
Procedure
1. Click the Objects tab.
2. In the navigation pane, select APPSecurity > WAF > Profiles.
The WAF Profiles page opens.
3. Click Create.
The Create WAF Profile page opens.
4. Create a WAF profile.
Table 1 WAF profile configuration items
5. Click OK.
The WAF profile is displayed on the WAF Profiles page.
6. Use the WAF profile in a security policy. For more information about security policies, see security policy online help.
7. To have the WAF profile configuration take effect immediately, click Submit.
A newly added WAF profile must be activated to take effect. By default, the system automatically activates a WAF profile 40 seconds after the profile is created.