- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Data filtering | 145.42 KB |
This help contains the following topics:
¡ Restrictions and guidelines: Regular expression-based keyword match pattern configuration
¡ Restrictions and guidelines: Data filtering profile configuration
¡ Configure a data filtering profile
Introduction
Data filtering filters packets based on application layer information. You can use data filtering to effectively prevent leakage of internal information, distribution of illegal information, and unauthorized access to the Internet.
Data filtering supports filtering packets of the following protocols:
· HTTP.
· FTP.
· SMTP.
· IMAP.
· NFS.
· POP3.
· RTMP.
· SMB.
Basic concepts
Keyword
The device provides a list of predefined keywords and allows you to create user-defined keywords in a keyword group.
· Predefined keyword—Includes Phone, Bank card, Credit card, and ID card. These keywords can be used to identify packets that contain phone numbers, bank card numbers, credit card numbers, and ID card numbers.
· User-defined keyword—A text- or regular expression-based string to identify patterns in the application layer data of packets.
Keyword group
A keyword group is a group of up to 32 keywords. A packet matches a keyword group if it matches a keyword in the group. You can enable or disable predefined keywords and create new keywords in a keyword group.
Data filtering rule
A data filtering rule contains a set of packet filtering criteria and the actions for matching packets. The packet filtering criteria include keyword group, direction (Upload, Download, or Both), and applications. The packet processing actions include Drop, Permit, and Logging. A packet must match all the filtering criteria for the actions specified for the rule to apply.
Data filtering mechanism
Upon receiving a packet of a protocol that data filtering supports, the device performs the following operations:
1. Compares the packet with the security policies.
If the packet matches a security policy that is associated with a data filtering profile, the device extracts the application layer information from the packet.
2. Determines the actions to take on the packet by comparing the extracted application layer information with the data filtering rules in the data filtering policy:
¡ If the packet does not match any data filtering rules in the policy, the device permits the packet to pass.
¡ If the packet matches only one rule, the device takes the actions specified for the rule.
¡ If the packet matches multiple rules, the device determines the actions as follows:
- If the matching rules have both the permit and drop actions, the device takes the drop action.
- If the logging action is specified for any of the matching rules, the device logs the packet.
Restrictions and guidelines
Restrictions and guidelines: Regular expression-based keyword match pattern configuration
· The regular expression pattern can contain a maximum of four branches. For example, 'abc(c|d|e|\x3D)' is valid, and 'abc(c|onreset|onselect|onchange|style\x3D)' is invalid.
· Nested braces are not allowed. For example, 'ab((abcs*?))' is invalid.
· A branch cannot be specified after another branch. For example, 'ab(a|b)(c|d)^\\r\\n]+?' is invalid.
· A minimum of four non-wildcard characters must exist before an asterisk (*) or question mark (?). For example, 'abc*' is invalid and 'abcd*DoS\x2d\d{5}\x20\x2bxi\\r\\nJOIN' is valid.
Restrictions and guidelines: Data filtering profile configuration
After you create, edit, or delete a data filtering profile, the configuration will automatically take effect after 40 seconds by default. To make the configuration take effect immediately, click Submit.
Configure data filtering
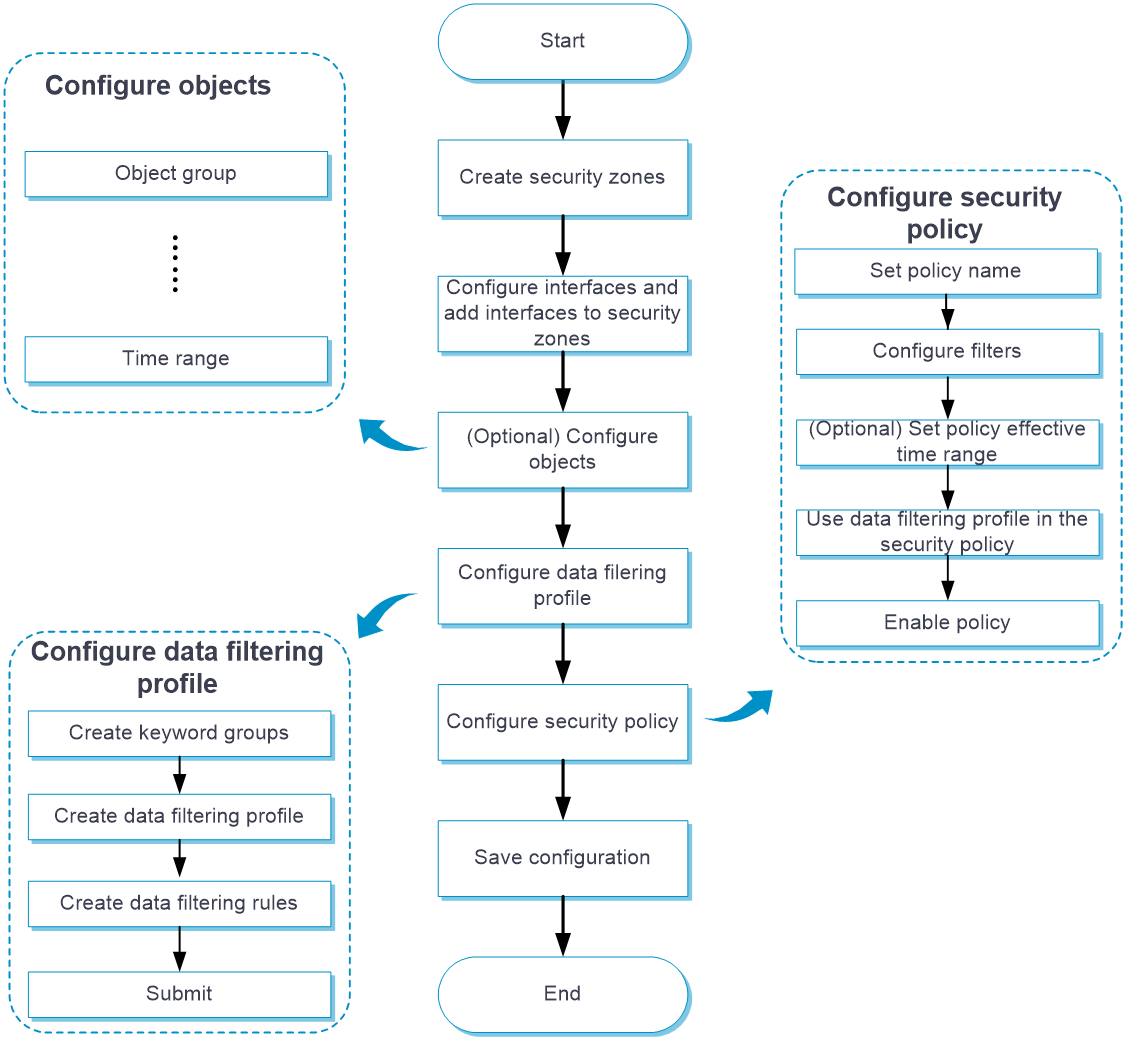
Configure data filtering as shown in Figure 1.
Figure 1 Data filtering configuration procedure
Configure a keyword group
Perform this task to create a keyword group and configure keywords in the keyword group.
Procedure
1. Click the Objects tab.
2. In the navigation pane, select APPSecurity > Data Filtering > Keyword Groups.
3. On the page that appears, click Create.
4. Create a keyword group.
Table 1 Keyword group configuration items
|
Item |
Description |
|
Name |
Enter a name for the keyword group. |
|
Description |
Enter a description for the keyword group. |
1. In the Predefined keyword list area, select Enable for a predefined keyword. For example, to identify packets that contain phone numbers, select Enable for Phone.
2. In the User-defined keyword list area, click Create.
3. Create a keyword.
Table 2 Keyword configuration items
|
Item |
Description |
|
Name |
Enter a name for the keyword. |
|
Type |
Select the type of the keyword match pattern. Options are: · Text—Select this option to configure a text-based match pattern for exact match. · Regular expression—Select this option to configure a regular expression-based match pattern for fuzzy match. |
|
Match pattern |
Enter the content of the keyword match pattern. |
4. Click OK.
The keyword is displayed on the user-defined keyword list.
You can add a maximum of 32 more keywords to the keyword group.
5. Click OK.
The keyword group is displayed on the Keyword Groups page.
Configure a data filtering profile
Perform this task to create a data filtering profile and configure data filtering rules in the profile.
Procedure
1. Click the Objects tab.
2. In the navigation pane, select APPSecurity > Data Filtering > Profiles.
3. On the page that appears, click Create.
4. Create a data filtering profile.
Table 3 Data filtering profile configuration items
|
Item |
Description |
|
Name |
Enter a name for the data filtering profile. |
|
Description |
Enter a description for the data filtering profile. |
5. In the Data filtering rules area, click Create.
6. Create a data filtering rule.
Table 4 Data filtering rule configuration items
|
Item |
Description |
|
Name |
Enter a name for the data filtering rule. |
|
Keyword group |
Select an existing keyword group or create a keyword group. |
|
Applications |
Select the application layer protocols of the applications to which the rule applies. Supported application layer protocols are FTP, HTTP, IMAP, NFS, POP3, RTMP, SMB, and SMTP. |
|
Direction |
Select the traffic direction to which the rule applies. Options are Upload, Download, and Both. |
|
Action |
Select the action for matching packets. Options are Permit and Drop. |
|
Logging |
Select whether to enable logging for matching packets. Options are Enable and Disable. |
7. Click OK.
The data filtering rule is displayed on the data filtering rule list of the data filtering profile.
8. Click OK.
The data filtering profile is displayed on the Data Filtering Profiles page.
9. Use the data filtering profile in a security policy. For more information about security policies, see security policy online help.
10. To make the configuration take effect immediately, click Submit.
If you do not perform this operation, the configuration will automatically take effect after 40 seconds.