- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 15-Public key management | 33.46 KB |
This help contains the following topics:
¡ Asymmetric key algorithm overview
¡ Managing local asymmetric key pairs
¡ Managing peer host public key
Introduction
The public key management feature is used to manage and advertise keys of asymmetric key algorithms.
Asymmetric key algorithm overview
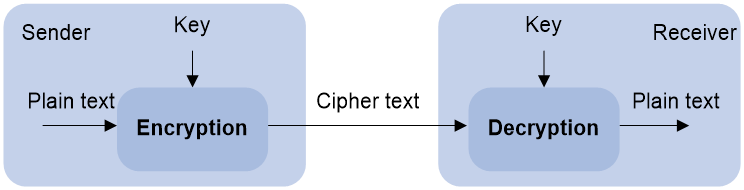
Asymmetric key algorithms are used by security applications to secure communications between two parties, as shown in Figure 1. Asymmetric key algorithms use two separate keys (one public and one private) for encryption and decryption. Symmetric key algorithms use only one key.
Figure 1 Encryption and decryption
A key owner can distribute the public key in plain text on the network but must keep the private key in privacy. It is mathematically infeasible to calculate the private key even if an attacker knows the algorithm and the public key.
Asymmetric key algorithms include Revest-Shamir-Adleman Algorithm (RSA), Digital Signature Algorithm (DSA), Elliptic Curve Digital Signature Algorithm (ECDSA), and SM2.
Security applications (such as SSH, SSL, and PKI) use the asymmetric key algorithms for encryption/decryption and digital signature.
Managing local asymmetric key pairs
Creating a local key pair
On the local device, you can create RSA, DSA, ECDSA, and SM2 key pairs.
Displaying or exporting a host public key
On the device, you can display or export the local host public keys.
· Display a host public key. After the key is displayed on the local device, record the key, for example, copy it to an unformatted file. On the peer device, you must literally enter the key.
· Export a host public key to a file in the specified format. Transfer the file to the peer device. On the peer device, import the key from the file.
· Export a host public key to the monitor screen in the specified format, and then save it to a file. Transfer the file to the peer device. On the peer device, import the key from the file.
Destroying a local key pair
To ensure security, destroy the local key pair and generate a new key pair in any of the following situations:
· The local key has leaked. An intrusion event might occur.
· The storage media of the device fails or is replaced, so the device does not have the corresponding private key for decryption/encryption and digital signature.
· The local certificate has expired.
Managing peer host public keys
To encrypt information sent to a peer device or authenticate the digital signature of the peer device, you must configure the peer device's public key on the local device. On the local device, you can import, display, and delete the host public key of the peer device.
You can configure the peer host public key by using the following methods:
· Import the peer host public key from a public key file (recommended).
You must first obtain the public key file from the peer device through FTP or TFTP. After you import the key, the local device automatically converts the imported public key to a string in the Public Key Cryptography Standards (PKCS) format.
· Manually enter (type or copy) the peer host public key.
You must first display the public key on the peer device and record the key. On the local device, you manually type or copy the key.
Restrictions and guidelines
When you configure a peer host public key, follow these restrictions and guidelines:
· When you manually enter the peer host public key, make sure the entered key is in the correct format. To obtain the peer host public key in the correct format, display the public key on the peer device as described in "Displaying or exporting a host public key." The format of the public key displayed in any other way might be incorrect. If the key is not in the correct format, the system discards the key and displays an error message.
· Always import rather than enter the peer host public key if you are not sure whether the device supports the format of the recorded peer host public key.
· The public key of an SM2 key pair cannot be imported.