- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Portal configuration
- 05-Port security configuration
- 06-Password control configuration
- 07-Keychain configuration
- 08-Public key management
- 09-PKI configuration
- 10-IPsec configuration
- 11-SSH configuration
- 12-SSL configuration
- 13-Attack detection and prevention configuration
- 14-TCP attack prevention configuration
- 15-IP source guard configuration
- 16-ARP attack protection configuration
- 17-ND attack defense configuration
- 18-uRPF configuration
- 19-MFF configuration
- 20-FIPS configuration
- 21-MACsec configuration
- 22-802.1X client configuration
- 23-Web authentication configuration
- 24-Object group configuration
- 25-Triple authentication configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 18-uRPF configuration | 184.70 KB |
Cooperation with default route
Displaying and maintaining uRPF
Cooperation with default route
Displaying and maintaining IPv6 uRPF
IPv6 uRPF configuration example
Configuring uRPF
Overview
Unicast Reverse Path Forwarding (uRPF) protects a network against source address spoofing attacks, such as DoS and DDoS attacks.
Attackers send packets with a forged source address to access a system that uses IP-based authentication, in the name of authorized users or even the administrator. Even if the attackers or other hosts cannot receive any response packets, the attacks are still disruptive to the attacked target.
Figure 1 Source address spoofing attack
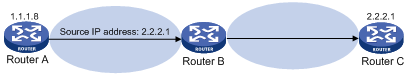
As shown in Figure 1, an attacker on Router A sends the server (Router B) requests with a forged source IP address 2.2.2.1 at a high rate. Router B sends response packets to IP address 2.2.2.1 (Router C). Consequently, both Router B and Router C are attacked. If the administrator disconnects Router C by mistake, the network service is interrupted.
Attackers can also send packets with different forged source addresses or attack multiple servers simultaneously to block connections or even break down the network.
uRPF can prevent these source address spoofing attacks. It checks whether an interface that receives a packet is the output interface of the FIB entry that matches the source address of the packet. If not, uRPF considers it a spoofing attack and discards the packet.
uRPF check modes
uRPF supports strict and loose modes.
· Strict uRPF check—To pass strict uRPF check, the source address of a packet and the receiving interface must match the destination address and output interface of a FIB entry. In some scenarios (for example, asymmetrical routing), strict uRPF might discard valid packets. Strict uRPF is often deployed between a PE and a CE.
· Loose uRPF check—To pass loose uRPF check, the source address of a packet must match the destination address of a FIB entry. Loose uRPF can avoid discarding valid packets, but might let go attack packets. Loose uRPF is often deployed between ISPs, especially in asymmetrical routing.
Cooperation with default route
When a default route exists, all packets that fail to match a specific FIB entry match the default route during uRPF check and thus are permitted to pass. To avoid this situation, you can disable uRPF from using any default route to discard such packets. If you allow using the default route (set by using allow-default-route), uRPF permits packets that only match the default route. By default, uRPF discards packets that can only match a default route. Typically, you do not need to configure the allow-default-route keyword on a PE device because it has no default route pointing to the CE. If you enable uRPF on a CE that has a default route pointing to the PE, select the allow-default-route keyword.
uRPF operation
Figure 2 shows how uRPF works.
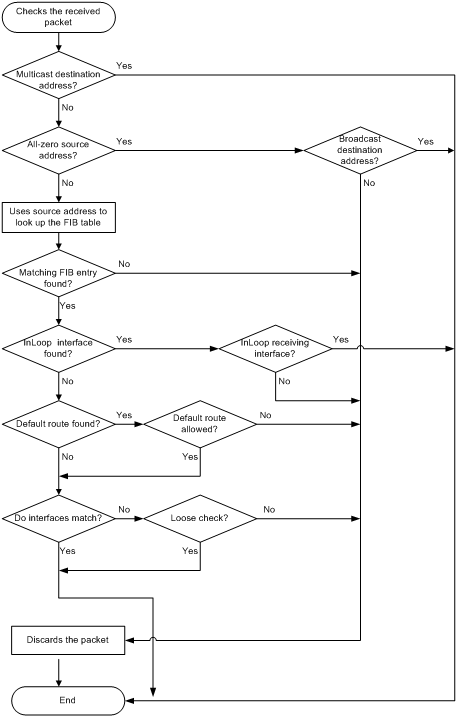
1. uRPF checks address validity:
¡ uRPF permits a packet with a multicast destination address.
¡ For a packet with an all-zero source address, uRPF permits the packet if it has a broadcast destination address. (A packet with source address 0.0.0.0 and destination address 255.255.255.255 might be a DHCP or BOOTP packet and cannot be discarded.) The packet is discarded if it has a non-broadcast destination address.
¡ uRPF proceeds to step 2 for other packets.
2. uRPF checks whether the source address matches a unicast route:
¡ If yes, uRPF proceeds to step 3.
¡ If no, uRPF discards the packet. A non-unicast source address matches a non-unicast route.
3. uRPF checks whether the matching route is to the host itself:
¡ If yes, the output interface of the matching route is an InLoop interface. uRPF checks whether the receiving interface of the packet is an InLoop interface. If yes, it does not check the packet. If no, uRPF discards the packet.
¡ If no, uRPF proceeds to step 4.
4. uRPF checks whether the matching route is a default route:
¡ If yes, uRPF checks whether the allow-default-route keyword is configured to allow using the default route. If yes, uRPF proceeds to step 5. If no, uRPF discards the packet.
¡ If no, uRPF proceeds to step 5.
5. uRPF checks whether the receiving interface matches the output interface of the matching FIB entry:
¡ If yes, uRPF forwards the packet.
¡ If no, uRPF checks whether the check mode is loose. If yes, the packet is forwarded. If no, the packet is discarded.
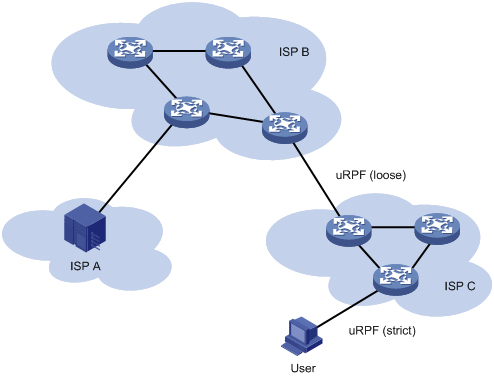
Network application
As shown in Figure 3, strict uRPF check is configured between an ISP network and a customer network. Loose uRPF check is configured between ISPs.
Enabling uRPF
uRPF checks only incoming packets on interfaces. You can enable uRPF globally. Global uRPF takes effect on all interfaces of the device.
Follow these guidelines when you enable uRPF:
· uRPF will cause short Layer 3 traffic interruption. As a best practice, configure uRPF at the early stage of the network configuration.
· uRPF is not supported on a VXLAN network that performs Layer 3 forwarding.
· uRPF does not take effect on tunneled packets. The processing of tunneled packets varies as follows:
¡ If loose uRPF is configured, the device allows the tunneled packets to pass through.
¡ If strict uRPF is configured, the device drops the tunneled packets.
· In an MPLS network, an egress node cannot perform strict uRPF check on packets from the penultimate hop to which the egress assigns an implicit null label. For more information about the implicit null label, see MPLS Configuration Guide.
· Do not configure the allow-default-route keyword for loose uRPF check. Otherwise, uRPF might fail to work.
To enable uRPF globally:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable uRPF globally. |
ip urpf { loose [ allow-default-route ] | strict [ allow-default-route ] } |
By default, uRPF is disabled. |
Displaying and maintaining uRPF
Execute display commands in any view.
|
Task |
Command |
|
(In standalone mode.) Display uRPF configuration. |
display ip urpf [ slot slot-number ] |
|
(In IRF mode.) Display uRPF configuration. |
display ip urpf [ chassis chassis-number slot slot-number ] |
uRPF configuration example
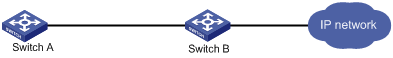
Network requirements
As shown in Figure 4, configure strict uRPF check on Switch B.
Configure strict uRPF check on Switch A and allow using the default route for uRPF check.
Configuration procedure
1. Configure strict uRPF check on Switch B.
<SwitchB> system-view
[SwitchB] ip urpf strict
2. Configure strict uRPF check on Switch A and allow using the default route for uRPF check.
<SwitchA> system-view
[SwitchA] ip urpf strict allow-default-route
Configuring IPv6 uRPF
Overview
Unicast Reverse Path Forwarding (uRPF) protects a network against source address spoofing attacks, such as DoS and DDoS attacks.
Attackers send packets with a forged source address to access a system that uses IP-based authentication, in the name of authorized users or even the administrator. Even if the attackers or other hosts cannot receive any response packets, the attacks are still disruptive to the attacked target.
Figure 5 Source address spoofing attack
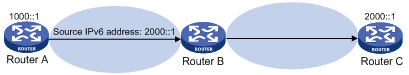
As shown in Figure 5, an attacker on Router A sends the server (Router B) requests with a forged source IPv6 address 2000::1 at a high rate. Router B sends response packets to IPv6 address 2000::1 (Router C). Consequently, both Router B and Router C are attacked. If the administrator disconnects Router C by mistake, the network service is interrupted.
Attackers can also send packets with different forged source addresses or attack multiple servers simultaneously to block connections or even break down the network.
IPv6 uRPF can prevent these source address spoofing attacks. It checks whether an interface that receives a packet is the output interface of the FIB entry that matches the source address of the packet. If not, uRPF considers it a spoofing attack and discards the packet.
IPv6 uRPF check modes
IPv6 uRPF supports strict and loose check modes.
· Strict IPv6 uRPF check—To pass strict IPv6 uRPF check, the source address of a packet and the receiving interface must match the destination address and output interface of an IPv6 FIB entry. In some scenarios (for example, asymmetrical routing), strict IPv6 uRPF might discard valid packets. Strict IPv6 uRPF is often deployed between a PE and a CE.
· Loose IPv6 uRPF check—To pass loose IPv6 uRPF check, the source address of a packet must match the destination address of an IPv6 FIB entry. Loose IPv6 uRPF can avoid discarding valid packets, but might let go attack packets. Loose IPv6 uRPF is often deployed between ISPs, especially in asymmetrical routing.
Cooperation with default route
When a default route exists, all packets that fail to match a specific IPv6 FIB entry match the default route during IPv6 uRPF check and thus are permitted to pass. If you allow using the default route (by using allow-default-route), IPv6 uRPF permits packets that only match the default route. By default, IPv6 uRPF discards packets that can only match a default route. Typically, you do not need to configure the allow-default-route keyword on a PE device because it has no default route pointing to the CE device. If you enable IPv6 uRPF on a CE that has a default route pointing to the PE, select the allow-default-route keyword.
IPv6 uRPF operation
Figure 6 shows how IPv6 uRPF works.
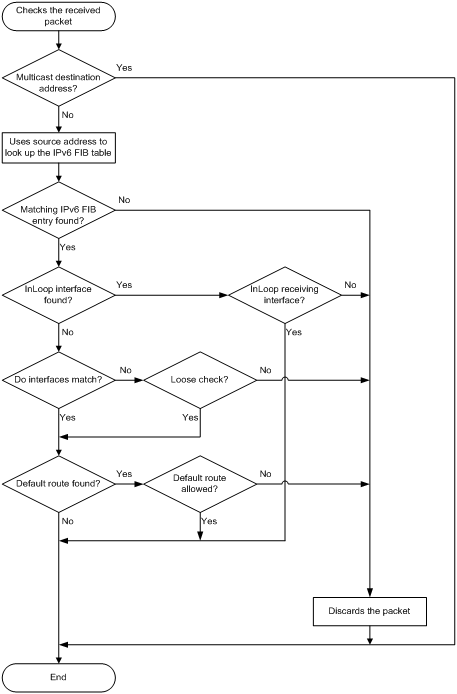
1. IPv6 uRPF checks whether the received packet carries a multicast destination address:
¡ If yes, IPv6 uRPF permits the packet.
¡ If no, IPv6 uRPF proceeds to step 2.
2. IPv6 uRPF checks whether the source address matches a unicast route:
¡ If yes, IPv6 uRPF proceeds to step 3.
¡ If no, IPv6 uRPF discards the packet. A non-unicast source address matches a non-unicast route.
3. IPv6 uRPF checks whether the matching route is to the host itself:
¡ If yes, the output interface of the matching route is an InLoop interface. IPv6 uRPF checks whether the receiving interface of the packet is an InLoop interface. If yes, IPv6 uRPF permits the packet. If no, IPv6 uRPF discards the packet. If the source address is a link-local address and is the receiving interface address, the packet is discarded.
¡ If no, IPv6 uRPF proceeds to step 4.
4. IPv6 uRPF checks whether the receiving interface matches the output interface of the matching FIB entry:
¡ If yes, IPv6 uRPF proceeds to step 5.
¡ If no, IPv6 uRPF checks whether the check mode is loose. If yes, IPv6 uRPF proceeds to step 5. If no, IPv6 uRPF discards the packet.
5. IPv6 uRPF checks whether the matching route is a default route:
¡ If yes, IPv6 uRPF checks whether the allow-default-route keyword is configured to allow using the default route. If yes, the packet is forwarded. If no, the packet is discarded.
¡ If no, IPv6 uRPF forwards the packet.
Network application
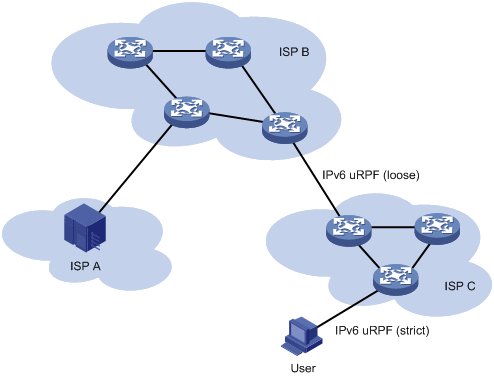
As shown in Figure 7, strict IPv6 uRPF check is configured between an ISP network and a customer network. Loose IPv6 uRPF check is configured between ISPs.
Enabling IPv6 uRPF
IPv6 uRPF checks only incoming packets on interfaces. You can enable IPv6 uRPF globally. Global IPv6 uRPF takes effect on all interfaces of the device.
Follow these guidelines when you enable IPv6 uRPF:
· IPv6 uRPF does not check packets received on the SA interface modules if the source IPv6 addresses of the packets have a prefix length longer than 64.
· IPv6 uRPF will cause short Layer 3 traffic interruption. As a best practice, configure IPv6 uRPF at the early stage of the network configuration.
· IPv6 uRPF is not supported on a VXLAN network that performs Layer 3 forwarding.
· IPv6 uRPF does not take effect on tunneled packets. The processing of tunneled packets varies as follows:
¡ If loose IPv6 uRPF is configured, the device allows the tunneled packets to pass through.
¡ If strict IPv6 uRPF is configured, the device drops the tunneled packets.
· In an MPLS network, an egress node cannot perform strict IPv6 uRPF check on packets from the penultimate hop to which the egress assigns an implicit null label. For more information about the implicit null label, see MPLS Configuration Guide.
· Do not configure the allow-default-route keyword for loose IPv6 uRPF check. Otherwise, IPv6 uRPF might fail to work.
To enable IPv6 uRPF globally:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IPv6 uRPF globally. |
ipv6 urpf { loose | strict } [ allow-default-route ] |
By default, IPv6 uRPF is disabled. |
Displaying and maintaining IPv6 uRPF
Execute display commands in any view.
|
Task |
Command |
|
(In standalone mode.) Display IPv6 uRPF configuration. |
display ipv6 urpf [ slot slot-number ] |
|
(In IRF mode.) Display IPv6 uRPF configuration. |
display ipv6 urpf [ chassis chassis-number slot slot-number ] |
IPv6 uRPF configuration example
Network requirements
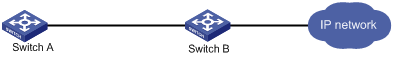
As shown in Figure 8, configure strict IPv6 uRPF check on Switch B.
Configure strict IPv6 uRPF check on Switch A and allow using the default route for IPv6 uRPF check.
Configuration procedure
1. Configure strict IPv6 uRPF check on Switch B.
<SwitchB> system-view
[SwitchB] ipv6 urpf strict
2. Configure strict uRPF check on Switch A and allow using the default route for IPv6 uRPF check.
<SwitchA> system-view
[SwitchA] ipv6 urpf strict allow-default-route
