- Table of Contents
-
- 03-Layer 2-LAN Switching Configuration Guide
- 00-Preface
- 01-Ethernet interface configuration
- 02-Loopback, null, and inloopback interface configuration
- 03-Bulk interface configuration
- 04-MAC address table configuration
- 05-Ethernet link aggregation configuration
- 06-Port isolation configuration
- 07-Spanning tree configuration
- 08-Loop detection configuration
- 09-VLAN configuration
- 10-VLAN mapping configuration
- 11-LLDP configuration
- 12-Service loopback group configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Spanning tree configuration | 516.48 KB |
Contents
Configuring spanning tree protocols
Calculation process of the STP algorithm
MSTP implementation on devices
Spanning tree configuration task lists
Configuration restrictions and guidelines
Setting the spanning tree mode
Configuring the root bridge or a secondary root bridge
Configuring the current device as the root bridge of a specific spanning tree
Configuring the current device as a secondary root bridge of a specific spanning tree
Configuring the device priority
Configuring the maximum hops of an MST region
Configuring the network diameter of a switched network
Configuration restrictions and guidelines
Configuring the timeout factor
Configuring the BPDU transmission rate
Configuration restrictions and guidelines
Configuring path costs of ports
Specifying a standard for the device to use when it calculates the default path cost
Configuring path costs of ports
Configuring the port link type
Configuration restrictions and guidelines
Configuring the mode a port uses to recognize and send MSTP packets
Enabling outputting port state transition information
Enabling the spanning tree feature
Performing mCheck in interface view
Configuration restrictions and guidelines
Digest Snooping configuration example
Configuring No Agreement Check
No Agreement Check configuration example
Configuring protection features
Configuring port role restriction
Configuring TC-BPDU transmission restriction
Displaying and maintaining the spanning tree
Spanning tree configuration example
Configuring spanning tree protocols
Spanning tree protocols eliminate loops in a physical link-redundant network by selectively blocking redundant links and putting them in a standby state.
The recent versions of STP include the Rapid Spanning Tree Protocol (RSTP) and the Multiple Spanning Tree Protocol (MSTP).
STP
STP was developed based on the 802.1d standard of IEEE to eliminate loops at the data link layer in a LAN. Networks often have redundant links as backups in case of failures, but loops are a very serious problem. Devices running STP detect loops in the network by exchanging information with one another, and eliminate loops by selectively blocking certain ports to prune the loop structure into a loop-free tree structure. This avoids proliferation and infinite cycling of packets that would occur in a loop network.
In the narrow sense, STP refers to IEEE 802.1d STP. In the broad sense, STP refers to the IEEE 802.1d STP and various enhanced spanning tree protocols derived from that protocol.
STP protocol packets
STP uses bridge protocol data units (BPDUs), also known as configuration messages, as its protocol packets. This chapter uses BPDUs to represent all types of spanning tree protocol packets.
STP-enabled network devices exchange BPDUs to establish a spanning tree. BPDUs contain sufficient information for the network devices to complete spanning tree calculation.
STP uses the following types of BPDUs:
· Configuration BPDUs—Used by the network devices to calculate a spanning tree and maintain the spanning tree topology.
· Topology change notification (TCN) BPDUs—Notify network devices of network topology changes.
Configuration BPDUs contain sufficient information for the network devices to complete spanning tree calculation. Important fields in a configuration BPDU include the following:
· Root bridge ID—Consisting of the priority and MAC address of the root bridge.
· Root path cost—Cost of the path to the root bridge denoted by the root identifier from the transmitting bridge.
· Designated bridge ID—Consisting of the priority and MAC address of the designated bridge.
· Designated port ID—Consisting of the priority and global port number of the designated port.
· Message age—Age of the configuration BPDU while it propagates in the network.
· Max age—Maximum age of the configuration BPDU stored on the switch.
· Hello time—Configuration BPDU transmission interval.
· Forward delay—Delay that STP bridges use to transit port state.
Basic concepts in STP
Root bridge
A tree network must have a root bridge. The entire network contains only one root bridge, and all the other bridges in the network are called "leaf nodes". The root bridge is not permanent, but can change with changes of the network topology.
Upon initialization of a network, each device generates and periodically sends configuration BPDUs, with itself as the root bridge. After network convergence, only the root bridge generates and periodically sends configuration BPDUs. The other devices only forward the BPDUs.
Root port
Designated bridge and designated port
|
Classification |
Designated bridge |
Designated port |
|
For a device |
Device directly connected to the local device and responsible for forwarding BPDUs to the local device |
Port through which the designated bridge forwards BPDUs to this device |
|
For a LAN |
Device responsible for forwarding BPDUs to this LAN segment |
Port through which the designated bridge forwards BPDUs to this LAN segment |
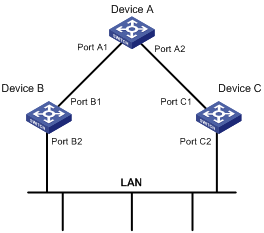
As shown in Figure 1, Device B and Device C are directly connected to a LAN. If Device A forwards BPDUs to Device B through port A1, the designated bridge for Device B is Device A, and the designated port of Device B is port A1 on Device A. If Device B forwards BPDUs to the LAN, the designated bridge for the LAN is Device B, and the designated port for the LAN is port B2 on Device B.
Figure 1 Designated bridges and designated ports
Path cost
Path cost is a reference value used for link selection in STP. STP calculates path costs to select the most robust links and block redundant links that are less robust, to prune the network into a loop-free tree.
Calculation process of the STP algorithm
The spanning tree calculation process described in the following sections is a simplified process for example only.
Calculation process
The STP algorithm uses the following calculation process:
1. Network initialization.
Upon initialization of a device, each port generates a BPDU with the port as the designated port, the device as the root bridge, 0 as the root path cost, and the device ID as the designated bridge ID.
2. Root bridge selection.
Initially, each STP-enabled device on the network assumes itself to be the root bridge, with its own device ID as the root bridge ID. By exchanging configuration BPDUs, the devices compare their root bridge IDs to elect the device with the smallest root bridge ID as the root bridge.
3. Root port and designated ports selection on the non-root bridges.
|
Step |
Description |
|
1 |
A non-root–bridge device regards the port on which it received the optimum configuration BPDU as the root port. Table 1 describes how the optimum configuration BPDU is selected. |
|
2 |
Based on the configuration BPDU and the path cost of the root port, the device calculates a designated port configuration BPDU for each of the other ports. · The root bridge ID is replaced with that of the configuration BPDU of the root port. · The root path cost is replaced with that of the configuration BPDU of the root port plus the path cost of the root port. · The designated bridge ID is replaced with the ID of this device. · The designated port ID is replaced with the ID of this port. |
|
3 |
The device compares the calculated configuration BPDU with the configuration BPDU on the port whose port role will be determined, and acts depending on the result of the comparison: · If the calculated configuration BPDU is superior, the device considers this port as the designated port, replaces the configuration BPDU on the port with the calculated configuration BPDU, and periodically sends the calculated configuration BPDU. · If the configuration BPDU on the port is superior, the device blocks this port without updating its configuration BPDU. The blocked port can receive BPDUs, but cannot send BPDUs or forward data traffic. |
When the network topology is stable, only the root port and designated ports forward user traffic. Other ports are all in the blocked state to receive BPDUs but not to forward BPDUs or user traffic.
Table 1 Selecting the optimum configuration BPDU
|
Step |
Actions |
|
1 |
Upon receiving a configuration BPDU on a port, the device compares the priority of the received configuration BPDU with that of the configuration BPDU generated by the port, and: · If the former priority is lower, the device discards the received configuration BPDU and keeps the configuration BPDU the port generated. · If the former priority is higher, the device replaces the content of the configuration BPDU generated by the port with the content of the received configuration BPDU. |
|
2 |
The device compares the configuration BPDUs of all the ports and chooses the optimum configuration BPDU. |
The following are the principles of configuration BPDU comparison:
a. The configuration BPDU with the lowest root bridge ID has the highest priority.
b. If configuration BPDUs have the same root bridge ID, their root path costs are compared. For example, the root path cost in a configuration BPDU plus the path cost of a receiving port is S. The configuration BPDU with the smallest S value has the highest priority.
c. If all configuration BPDUs have the same root bridge ID and S value, their designated bridge IDs, designated port IDs, and the IDs of the receiving ports are compared in sequence. The configuration BPDU that contains a smaller designated bridge ID, designated port ID, or receiving port ID is selected.
A tree-shape topology forms when the root bridge, root ports, and designated ports are selected.
Example of STP calculation
Figure 2 provides an example showing how the STP algorithm works.
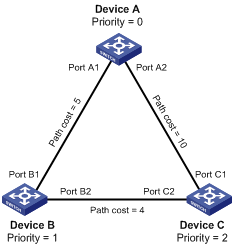
As shown in Figure 2, the priority values of Device A, Device B, and Device C are 0, 1, and 2, and the path costs of links among the three devices are 5, 10, and 4, respectively.
1. Device state initialization.
In Table 2, each configuration BPDU contains the following fields: root bridge ID, root path cost, designated bridge ID, and designated port ID.
Table 2 Initial state of each device
|
Device |
Port name |
Configuration BPDU on the port |
|
Device A |
Port A1 |
{0, 0, 0, Port A1} |
|
Port A2 |
{0, 0, 0, Port A2} |
|
|
Device B |
Port B1 |
{1, 0, 1, Port B1} |
|
Port B2 |
{1, 0, 1, Port B2} |
|
|
Device C |
Port C1 |
{2, 0, 2, Port C1} |
|
Port C2 |
{2, 0, 2, Port C2} |
2. Configuration BPDUs comparison on each device.
In Table 3, each configuration BPDU contains the following fields: root bridge ID, root path cost, designated bridge ID, and designated port ID.
Table 3 Comparison process and result on each device
|
Device |
Comparison process |
Configuration BPDU on ports after comparison |
|
Device A |
· Port A1 receives the configuration BPDU of Port B1 {1, 0, 1, Port B1}, finds that its existing configuration BPDU {0, 0, 0, Port A1} is superior to the received configuration BPDU, and discards the received one. · Port A2 receives the configuration BPDU of Port C1 {2, 0, 2, Port C1}, finds that its existing configuration BPDU {0, 0, 0, Port A2} is superior to the received configuration BPDU, and discards the received one. · Device A finds that it is both the root bridge and designated bridge in the configuration BPDUs of all its ports, and considers itself as the root bridge. It does not change the configuration BPDU of any port and starts to periodically send configuration BPDUs. |
· Port A1: {0, 0, 0, Port A1} · Port A2: {0, 0, 0, Port A2} |
|
Device B |
· Port B1 receives the configuration BPDU of Port A1 {0, 0, 0, Port A1}, finds that the received configuration BPDU is superior to its existing configuration BPDU {1, 0, 1, Port B1}, and updates its configuration BPDU. · Port B2 receives the configuration BPDU of Port C2 {2, 0, 2, Port C2}, finds that its existing configuration BPDU {1, 0, 1, Port B2} is superior to the received configuration BPDU, and discards the received one. |
· Port B1: {0, 0, 0, Port A1} · Port B2: {1, 0, 1, Port B2} |
|
· Device B compares the configuration BPDUs of all its ports, decides that the configuration BPDU of Port B1 is the optimum, and selects Port B1 as the root port with the configuration BPDU unchanged. · Based on the configuration BPDU and path cost of the root port, Device B calculates a designated port configuration BPDU for Port B2 {0, 5, 1, Port B2}, and compares it with the existing configuration BPDU of Port B2 {1, 0, 1, Port B2}. Device B finds that the calculated one is superior, decides that Port B2 is the designated port, replaces the configuration BPDU on Port B2 with the calculated one, and periodically sends the calculated configuration BPDU. |
· Root port (Port B1): {0, 0, 0, Port A1} · Designated port (Port B2): {0, 5, 1, Port B2} |
|
|
Device C |
· Port C1 receives the configuration BPDU of Port A2 {0, 0, 0, Port A2}, finds that the received configuration BPDU is superior to its existing configuration BPDU {2, 0, 2, Port C1}, and updates its configuration BPDU. · Port C2 receives the original configuration BPDU of Port B2 {1, 0, 1, Port B2}, finds that the received configuration BPDU is superior to the existing configuration BPDU {2, 0, 2, Port C2}, and updates its configuration BPDU. |
· Port C1: {0, 0, 0, Port A2} · Port C2: {1, 0, 1, Port B2} |
|
· Device C compares the configuration BPDUs of all its ports, decides that the configuration BPDU of Port C1 is the optimum, and selects Port C1 as the root port with the configuration BPDU unchanged. · Based on the configuration BPDU and path cost of the root port, Device C calculates the configuration BPDU of Port C2 {0, 10, 2, Port C2}, and compares it with the existing configuration BPDU of Port C2 {1, 0, 1, Port B2}. Device C finds that the calculated configuration BPDU is superior to the existing one, selects Port C2 as the designated port, and replaces the configuration BPDU of Port C2 with the calculated one. |
· Root port (Port C1): {0, 0, 0, Port A2} · Designated port (Port C2): {0, 10, 2, Port C2} |
|
|
· Port C2 receives the updated configuration BPDU of Port B2 {0, 5, 1, Port B2}, finds that the received configuration BPDU is superior to its existing configuration BPDU {0, 10, 2, Port C2}, and updates its configuration BPDU. · Port C1 receives a periodic configuration BPDU {0, 0, 0, Port A2} from Port A2, finds that it is the same as the existing configuration BPDU, and discards the received one. |
· Port C1: {0, 0, 0, Port A2} · Port C2: {0, 5, 1, Port B2} |
|
|
· Device C finds that the root path cost of Port C1 (10) (root path cost of the received configuration BPDU (0) plus path cost of Port C1 (10)) is larger than that of Port C2 (9) (root path cost of the received configuration BPDU (5) plus path cost of Port C2 (4)), decides that the configuration BPDU of Port C2 is the optimum, and selects Port C2 as the root port with the configuration BPDU unchanged. · Based on the configuration BPDU and path cost of the root port, Device C calculates a designated port configuration BPDU for Port C1 {0, 9, 2, Port C1} and compares it with the existing configuration BPDU of Port C1 {0, 0, 0, Port A2}. Device C finds that the existing configuration BPDU is superior to the calculated one and blocks Port C1 with the configuration BPDU unchanged. Then Port C1 does not forward data until a new event triggers a spanning tree calculation process, for example, the link between Device B and Device C is down. |
· Blocked port (Port C1): {0, 0, 0, Port A2} · Root port (Port C2): {0, 5, 1, Port B2} |
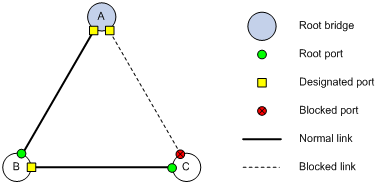
After the comparison processes described in Table 3, a spanning tree with Device A as the root bridge is established, and the topology is shown in Figure 3.
Figure 3 The final calculated spanning tree
The configuration BPDU forwarding mechanism of STP
The configuration BPDUs of STP are forwarded according to these guidelines:
· Upon network initiation, every device regards itself as the root bridge, generates configuration BPDUs with itself as the root, and sends the configuration BPDUs at a regular hello interval.
· If the root port received a configuration BPDU and the received configuration BPDU is superior to the configuration BPDU of the port, the device increases the message age carried in the configuration BPDU following a certain rule and starts a timer to time the configuration BPDU while sending this configuration BPDU through the designated port.
· If the configuration BPDU received on a designated port has a lower priority than the configuration BPDU of the local port, the port immediately sends its own configuration BPDU in response.
· If a path becomes faulty, the root port on this path no longer receives new configuration BPDUs and the old configuration BPDUs will be discarded due to timeout. The device generates a configuration BPDU with itself as the root and sends the BPDUs and TCN BPDUs. This triggers a new spanning tree calculation process to establish a new path to restore the network connectivity.
However, the newly calculated configuration BPDU cannot be propagated throughout the network immediately, so the old root ports and designated ports that have not detected the topology change continue forwarding data along the old path. If the new root ports and designated ports begin to forward data as soon as they are elected, a temporary loop might occur.
STP timers
The most important timing parameters in STP calculation are forward delay, hello time, and max age.
· Forward delay—Forward delay is the delay time for port state transition.
A path failure can cause spanning tree re-calculation to adapt the spanning tree structure to the change. However, the resulting new configuration BPDU cannot propagate throughout the network immediately. If the newly elected root ports and designated ports start to forward data immediately, a temporary loop will likely occur.
For this reason, as a mechanism for state transition in STP, the newly elected root ports or designated ports require twice the forward delay time before they transit to the forwarding state to make sure the new configuration BPDU has propagated throughout the network.
· Hello time—The device sends hello packets at the hello time interval to the neighboring devices to make sure the paths are fault-free.
· Max age—The device uses the max age to determine whether a stored configuration BPDU has expired and discards it if the max age is exceeded.
RSTP
RSTP achieves rapid network convergence by allowing a newly elected root port or designated port to enter the forwarding state much faster than STP.
If the old root port on the device has stopped forwarding data and the upstream designated port has started forwarding data, a newly elected RSTP root port rapidly enters the forwarding state.
A newly elected RSTP designated port rapidly enters the forwarding state if it is an edge port (a port that directly connects to a user terminal rather than to another network device or a shared LAN segment) or it connects to a point-to-point link. Edge ports directly enter the forwarding state. Connecting to a point-to-point link, a designated port enters the forwarding state immediately after the device receives a handshake response from the directly connected device.
MSTP
MSTP overcomes the following STP and RSTP limitations:
· STP limitations—STP does not support rapid state transition of ports. A newly elected port must wait twice the forward delay time before it transits to the forwarding state, even if it connects to a point-to-point link or is an edge port.
· RSTP limitations—Although RSTP enables faster network convergence than STP, RSTP fails to provide load balancing among VLANs. As with STP, all RSTP bridges in a LAN share one spanning tree and forward packets from all VLANs along this spanning tree.
MSTP features
Developed based on IEEE 802.1s, MSTP overcomes the limitations of STP and RSTP. In addition to supporting rapid network convergence, it provides a better load sharing mechanism for redundant links by allowing data flows of different VLANs to be forwarded along separate paths.
MSTP provides the following features:
· MSTP divides a switched network into multiple regions, each of which contains multiple spanning trees that are independent of one another.
· MSTP supports mapping VLANs to spanning tree instances by means of a VLAN-to-instance mapping table. MSTP can reduce communication overheads and resource usage by mapping multiple VLANs to one instance.
· MSTP prunes a loop network into a loop-free tree, which avoids proliferation and endless cycling of packets in a loop network. In addition, it supports load balancing of VLAN data by providing multiple redundant paths for data forwarding.
· MSTP is compatible with STP and RSTP.
MSTP basic concepts
Figure 4 shows a switched network that contains four MST regions, each MST region containing four MSTP devices. Figure 5 shows the networking topology of MST region 3.
Figure 4 Basic concepts in MSTP
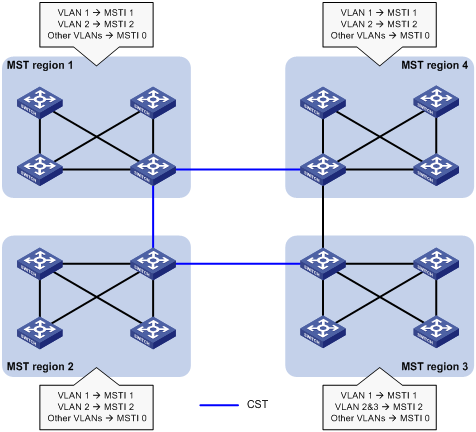
Figure 5 Network diagram and topology of MST region 3
MST region
A multiple spanning tree region (MST region) consists of multiple devices in a switched network and the network segments among them. All these devices have the following characteristics:
· A spanning tree protocol enabled
· Same region name
· Same VLAN-to-instance mapping configuration
· Same MSTP revision level
· Physically linked together
Multiple MST regions can exist in a switched network. You can assign multiple devices to the same MST region. In Figure 4, the switched network contains four MST regions, MST region 1 through MST region 4, and all devices in each MST region have the same MST region configuration.
MSTI
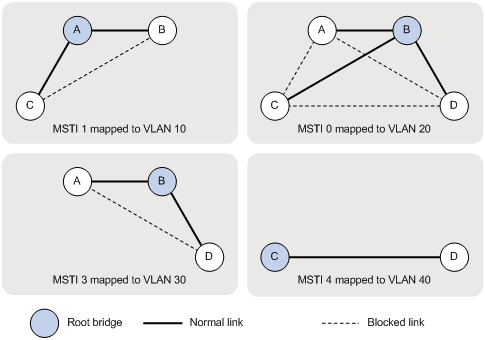
MSTP can generate multiple independent spanning trees in an MST region, and each spanning tree is mapped to the specific VLANs. Each spanning tree is referred to as a "multiple spanning tree instance (MSTI)".
In Figure 5, MST region 3 contains three MSTIs, MSTI 1, MSTI 2, and MSTI 0.
VLAN-to-instance mapping table
As an attribute of an MST region, the VLAN-to-instance mapping table describes the mapping relationships between VLANs and MSTIs.
In Figure 5, the VLAN-to-instance mapping table of MST region 3 is: VLAN 1 to MSTI 1, VLAN 2 and VLAN 3 to MSTI 2, and other VLANs to MSTI 0. MSTP achieves load balancing by means of the VLAN-to-instance mapping table.
CST
The common spanning tree (CST) is a single spanning tree that connects all MST regions in a switched network. If you regard each MST region as a device, the CST is a spanning tree calculated by these devices through STP or RSTP.
The blue lines in Figure 4 represent the CST.
IST
An internal spanning tree (IST) is a spanning tree that runs in an MST region. It is also called MSTI 0, a special MSTI to which all VLANs are mapped by default.
In Figure 4, MSTI 0 is the IST in MST region 3.
CIST
The common and internal spanning tree (CIST) is a single spanning tree that connects all devices in a switched network. It consists of the ISTs in all MST regions and the CST.
In Figure 4, the ISTs (MSTI 0) in all MST regions plus the inter-region CST constitute the CIST of the entire network.
Regional root
The root bridge of the IST or an MSTI within an MST region is the regional root of the IST or MSTI. Based on the topology, different spanning trees in an MST region might have different regional roots.
In MST region 3 in Figure 5, the regional root of MSTI 1 is Device B, the regional root of MSTI 2 is Device C, and the regional root of MSTI 0 (also known as the IST) is Device A.
Common root bridge
The common root bridge is the root bridge of the CIST.
In Figure 4, the common root bridge is a device in MST region 1.
Port roles
A port can play different roles in different MSTIs. As shown in Figure 6, an MST region contains Device A, Device B, Device C, and Device D. Port A1 and port A2 of Device A connect to the common root bridge. Port B2 and Port B3 of Device B form a loop. Port C3 and Port C4 of Device C connect to other MST regions. Port D3 of Device D directly connects to a host.
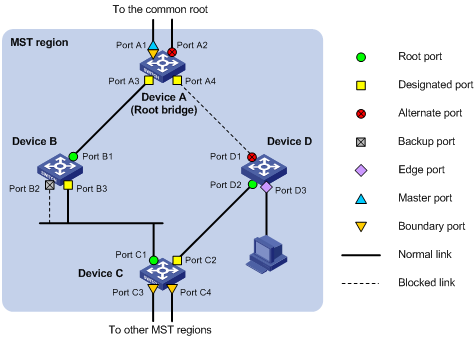
MSTP calculation involves the following port roles:
· Root port—Forwards data for a non-root bridge to the root bridge. The root bridge does not have any root port.
· Designated port—Forwards data to the downstream network segment or device.
· Alternate port—Serves as the backup port for a root port or master port. When the root port or master port is blocked, the alternate port takes over.
· Backup port—Serves as the backup port of a designated port. When the designated port is invalid, the backup port becomes the new designated port. A loop occurs when two ports of the same spanning tree device are connected, so the device blocks one of the ports. The blocked port acts as the backup.
· Edge port—Does not connect to any network device or network segment, but directly connects to a user host.
· Master port—Serves as a port on the shortest path from the local MST region to the common root bridge. The master port is not always located on the regional root. It is a root port on the IST or CIST and still a master port on the other MSTIs.
· Boundary port—Connects an MST region to another MST region or to an STP/RSTP-running device. In MSTP calculation, a boundary port's role on an MSTI is consistent with its role on the CIST. But that is not true with master ports. A master port on MSTIs is a root port on the CIST.
Port states
In MSTP, a port can be in one of the following states:
· Forwarding—The port receives and sends BPDUs, learns MAC addresses, and forwards user traffic.
· Learning—The port receives and sends BPDUs, learns MAC addresses, but does not forward user traffic. Learning is an intermediate port state.
· Discarding—The port receives and sends BPDUs, but does not learn MAC addresses or forward user traffic.
|
|
NOTE: When in different MSTIs, a port can be in different states. |
A port state is not exclusively associated with a port role. Table 4 lists the port states that each port role supports. (A check mark [√] indicates that the port supports this state, while a dash [—] indicates that the port does not support this state.)
Table 4 Port states that different port roles support
|
Port role (right) Port state (below) |
Root port/master port |
Designated port |
Alternate port |
Backup port |
|
Forwarding |
√ |
√ |
— |
— |
|
Learning |
√ |
√ |
— |
— |
|
Discarding |
√ |
√ |
√ |
√ |
How MSTP works
MSTP divides an entire Layer 2 network into multiple MST regions, which are connected by a calculated CST. Inside an MST region, multiple spanning trees, called MSTIs, are calculated. Among these MSTIs, MSTI 0 is the IST.
Like STP, MSTP uses configuration BPDUs to calculate spanning trees. An important difference is that an MSTP BPDU carries the MSTP configuration of the bridge from which the BPDU is sent.
CIST calculation
The calculation of a CIST tree is also the process of configuration BPDU comparison. During this process, the device with the highest priority is elected as the root bridge of the CIST. MSTP generates an IST within each MST region through calculation. At the same time, MSTP regards each MST region as a single device and generates a CST among these MST regions through calculation. The CST and ISTs constitute the CIST of the entire network.
MSTI calculation
Within an MST region, MSTP generates different MSTIs for different VLANs based on the VLAN-to-instance mappings. For each spanning tree, MSTP performs a separate calculation process similar to spanning tree calculation in STP. For more information, see "Calculation process of the STP algorithm."
In MSTP, a VLAN packet is forwarded along the following paths:
· Within an MST region, the packet is forwarded along the corresponding MSTI.
· Between two MST regions, the packet is forwarded along the CST.
MSTP implementation on devices
MSTP is compatible with STP and RSTP. Devices that are running MSTP and that are used for spanning tree calculation can identify STP and RSTP protocol packets.
In addition to basic MSTP features, the following features are provided for ease of management:
· Root bridge hold
· Root bridge backup
· Root guard
· BPDU guard
· TC-BPDU guard
· Port role restriction
· TC-BPDU transmission restriction
· Support for hot swapping of interface cards
Protocols and standards
MSTP is documented in the following protocols and standards:
· IEEE 802.1d, Media Access Control (MAC) Bridges
· IEEE 802.1w, Part 3: Media Access Control (MAC) Bridges—Amendment 2: Rapid Reconfiguration
· IEEE 802.1s, Virtual Bridged Local Area Networks—Amendment 3: Multiple Spanning Trees
· IEEE 802.1Q-REV/D1.3, Media Access Control (MAC) Bridges and Virtual Bridged Local Area Networks —Clause 13: Spanning tree Protocols
Spanning tree configuration task lists
Before configuring a spanning tree, you must determine the spanning tree protocol to be used (STP, RSTP, or MSTP) and plan the device roles (the root bridge or leaf node).
Configuration restrictions and guidelines
When you configure the spanning tree feature, follow these restrictions and guidelines:
· Configurations made in system view take effect globally. Configurations made in Ethernet interface view or WLAN mesh interface view take effect on the interface only. Configurations made in Layer 2 aggregate interface view take effect only on the aggregate interface. Configurations made on an aggregation member port can take effect only after the port is removed from the aggregation group.
· After you enable a spanning tree protocol on a Layer 2 aggregate interface, the system performs spanning tree calculation on the Layer 2 aggregate interface, but not on the aggregation member ports. The spanning tree protocol enable state and forwarding state of each selected member port is consistent with those of the corresponding Layer 2 aggregate interface.
· Though the member ports of an aggregation group do not participate in spanning tree calculation, the ports still reserve their spanning tree configurations for participating in spanning tree calculation after leaving the aggregation group.
STP configuration task list
RSTP configuration task list
MSTP configuration task list
Setting the spanning tree mode
The spanning tree modes include:
· STP mode—All ports of the device send STP BPDUs. Select this mode when the peer device of a port supports only STP.
· RSTP mode—All ports of the device send RSTP BPDUs. A port in this mode automatically transits to the STP mode when it receives STP BPDUs from the peer device, and a port in this mode does not transit to the MSTP mode when it receives MSTP BPDUs from the peer device.
· MSTP mode—All ports of the device send MSTP BPDUs. A port in this mode automatically transits to the STP mode when receiving STP BPDUs from the peer device, and a port in this mode does not transit to the RSTP mode when receiving RSTP BPDUs from the peer device.
MSTP mode is compatible with RSTP mode, and RSTP mode is compatible with STP mode.
To set the spanning tree mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the spanning tree mode. |
stp mode { mstp | rstp | stp } |
The default setting is the MSTP mode. |
|
|
NOTE: · In STP or RSTP mode, do not specify an MSTI. Otherwise, the spanning tree configuration does not take effect. · In MSTP mode, if you specify an MSTI, the spanning tree configuration takes effect on the specified MSTI. If you do not specify an MSTI, the spanning tree configuration takes effect on the CIST. |
Configuring an MST region
Two or more spanning tree devices belong to the same MST region only if they are configured to have the same format selector (0 by default, not configurable), MST region name, MST region revision level, and the same VLAN-to-instance mapping entries in the MST region, and they are connected through a physical link.
The configuration of MST region-related parameters (especially the VLAN-to-instance mapping table) might cause MSTP to begin a new spanning tree calculation. To reduce the possibility of topology instability, the MST region configuration takes effect only after you activate it by using the active region-configuration command, or enable a spanning tree protocol by using the stp global enable command if the spanning tree protocol is disabled.
To configure an MST region:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MST region view. |
stp region-configuration |
N/A |
|
3. Configure the MST region name. |
region-name name |
The default setting is the MAC address. |
|
4. Configure the VLAN-to-instance mapping table. |
· instance instance-id vlan vlan-id-list · vlan-mapping modulo modulo |
Use one of the commands. By default, all VLANs in an MST region are mapped to the CIST (or MSTI 0). |
|
5. Configure the MSTP revision level of the MST region. |
revision-level level |
The default setting is 0. |
|
6. (Optional.) Display the MST region configurations that are not activated yet. |
check region-configuration |
N/A |
|
7. Manually activate MST region configuration. |
active region-configuration |
N/A |
|
8. (Optional.) Display the activated configuration information of the MST region. |
display stp region-configuration |
Available in any view. |
Configuring the root bridge or a secondary root bridge
You can have the spanning tree protocol determine the root bridge of a spanning tree through MSTP calculation, or you can specify the current device as the root bridge or as a secondary root bridge.
A device has independent roles in different spanning trees. It can act as the root bridge in one spanning tree and as a secondary root bridge in another. However, one device cannot be the root bridge and a secondary root bridge in the same spanning tree.
A spanning tree can have only one root bridge. If two or more devices are selected as the root bridge in a spanning tree at the same time, the device with the lowest MAC address is chosen.
When the root bridge of an instance fails or is shut down, the secondary root bridge (if you have specified one) becomes the root bridge if you have not specified a new root bridge. If you specify multiple secondary root bridges for an instance, the secondary root bridge with the lowest MAC address is given priority.
You can specify one root bridge for each spanning tree, regardless of the device priority settings. Once you specify a device as the root bridge or a secondary root bridge, you cannot change its priority.
You can configure the current device as the root bridge by setting the device priority to 0. For the device priority configuration, see "Configuring the device priority."
Configuring the current device as the root bridge of a specific spanning tree
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the current device as the root bridge. |
·
In STP/RSTP mode: ·
In MSTP mode: |
By default, a device does not function as the root bridge. |
Configuring the current device as a secondary root bridge of a specific spanning tree
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the current device as a secondary root bridge. |
·
In STP/RSTP mode: ·
In MSTP mode: |
By default, a device does not function as a secondary root bridge. |
Configuring the device priority
Device priority is a factor in calculating the spanning tree. The priority of a device determines whether the device can be elected as the root bridge of a spanning tree. A lower value indicates a higher priority. You can set the priority of a device to a low value to specify the device as the root bridge of the spanning tree. A spanning tree device can have different priorities in different MSTIs.
During root bridge selection, if all devices in a spanning tree have the same priority, the one with the lowest MAC address is selected as the root bridge of the spanning tree. You cannot change the priority of a device after it is configured as the root bridge or as a secondary root bridge.
To configure the priority of a device in a specified MSTI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the priority of the current device. |
·
In STP/RSTP mode: ·
In MSTP mode: |
The default setting is 32768. |
Configuring the maximum hops of an MST region
Restrict the region size by setting the maximum hops of an MST region. The hop limit configured on the regional root bridge is used as the hop limit for the MST region.
Configuration BPDUs sent by the regional root bridge always have a hop count set to the maximum value. When a device receives this configuration BPDU, it decrements the hop count by one, and uses the new hop count in the BPDUs that it propagates. When the hop count of a BPDU reaches zero, it is discarded by the device that received it. Devices beyond the reach of the maximum hop can no longer participate in spanning tree calculations, so the size of the MST region is limited.
Make this configuration only on the root bridge. All other devices in the MST region use the maximum hop value set for the root bridge.
To configure the maximum number of hops of an MST region:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the maximum hops of the MST region. |
stp max-hops hops |
The default setting is 20. |
Configuring the network diameter of a switched network
Any two terminal devices in a switched network are connected through a specific path composed of a series of devices. The network diameter is the number of devices on the path composed of the most devices. The network diameter is a parameter that indicates the network size. A bigger network diameter indicates a larger network size.
Based on the network diameter you configured, the system automatically sets an optimal hello time, forward delay, and max age for the device. Each MST region is considered a device and the configured network diameter is effective only on the CIST (or the common root bridge) but not on other MSTIs.
To configure the network diameter of a switched network:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the network diameter of the switched network. |
stp bridge-diameter diameter |
The default setting is 7. |
Setting spanning tree timers
The following timers are used for spanning tree calculation:
· Forward delay—Delay time for port state transition. To prevent temporary loops on a network, the spanning tree feature sets an intermediate port state (the learning state) before it transits from the discarding state to the forwarding state. The feature also requires that the port transit its state after a forward delay timer to make sure the state transition of the local port stays synchronized with the peer.
· Hello time—Interval at which the device sends configuration BPDUs to detect link failures. If the device receives no configuration BPDUs within the timeout time, it recalculates the spanning tree. (Timeout time = timeout factor × 3 × hello time.)
· Max age—In the CIST of an MSTP network, the device uses the max age timer to determine if a configuration BPDU received by a port has expired. If it has, a new spanning tree calculation process starts. The max age timer does not take effect on other MSTIs except the CIST.
To avoid frequent network changes, make sure the timer settings meet the following formulas:
· 2 × (forward delay – 1 second) ≥ max age
· Max age ≥ 2 × (hello time + 1 second)
As a best practice, specify the network diameter instead of manually setting the spanning tree timers. The spanning tree protocols will automatically calculate the timers based on the network diameter. If the network diameter uses the default value, the timers also use their default values.
Set the timers only on the root bridge. The timer settings on the root bridge apply to all devices on the entire switched network.
Configuration restrictions and guidelines
When you configure spanning tree timers, follow these restrictions and guidelines:
· The length of the forward delay timer is related to the network diameter of the switched network. The larger the network diameter is, the longer the forward delay time should be. As a best practice, use the automatically calculated value because inappropriate forward delay setting might cause temporary redundant paths or increase the network convergence time.
· An appropriate hello time setting enables the device to promptly detect link failures on the network without using excessive network resources. If the hello time is too long, the device mistakes packet loss for a link failure and triggers a new spanning tree calculation process. If the hello time is too short, the device frequently sends the same configuration BPDUs, which waste device and network resources. As a best practice, use the default setting.
· If the max age timer is too short, the device frequently begins spanning tree calculations and might mistake network congestion as a link failure. If the max age timer is too long, the device might fail to promptly detect link failures and quickly launch spanning tree calculations, reducing the auto-sensing capability of the network. As a best practice, use the default setting.
Configuration procedure
To configure the spanning tree timers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the forward delay timer. |
stp timer forward-delay time |
The default setting is 15 seconds. |
|
3. Configure the hello timer. |
stp timer hello time |
The default setting is 2 seconds. |
|
4. Configure the max age timer. |
stp timer max-age time |
The default setting is 20 seconds. |
Configuring the timeout factor
The timeout factor is a parameter used to decide the timeout time, in the following formula: Timeout time = timeout factor × 3 × hello time.
After the network topology is stabilized, each non-root-bridge device forwards configuration BPDUs to the downstream devices at the hello interval to detect link failures. If a device does not receive a BPDU from the upstream device within nine times the hello time, it assumes that the upstream device has failed and starts a new spanning tree calculation process.
An upstream device might be too busy to forward configuration BPDUs in time, for example, many Layer 2 interfaces are configured on the upstream device. As a result, the downstream device fails to receive a BPDU within the timeout period and then starts an undesired spanning tree calculation. The calculation might fail, and it also wastes network resources. To prevent undesired spanning tree calculation and save network resources on a stable network, you can set the timeout factor to 5, 6, or 7.
To configure the timeout factor:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure the timeout factor of the device. |
stp timer-factor factor |
The default setting is 3. |
Configuring the BPDU transmission rate
The maximum number of BPDUs a port can send within each hello time equals the BPDU transmission rate plus the hello timer value. Configure an appropriate BPDU transmission rate based on the physical status of the port and the network structure.
The higher the BPDU transmission rate, the more BPDUs are sent within each hello time, and the more system resources are used. By setting an appropriate BPDU transmission rate, you can limit the rate at which the port sends BPDUs and prevent spanning tree protocols from using excessive network resources when the network topology changes. As a best practice, use the default setting.
To configure the BPDU transmission rate:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the BPDU transmission rate of the ports. |
stp transmit-limit limit |
The default setting is 10. |
Configuring edge ports
If a port directly connects to a user terminal rather than another device or a shared LAN segment, this port is regarded as an edge port. When network topology change occurs, an edge port will not cause a temporary loop. Because a device does not determine whether a port is directly connected to a terminal, you must manually configure the port as an edge port. After that, the port can rapidly transit from the blocked state to the forwarding state.
Configuration restrictions and guidelines
When you configure edge ports, follow these restrictions and guidelines:
· If BPDU guard is disabled, a port set as an edge port becomes a non-edge port again if it receives a BPDU from another port. To restore the edge port, re-enable it.
· If a port directly connects to a user terminal, configure it as an edge port and enable BPDU guard for it. This enables the port to quickly transit to the forwarding state when ensuring network security.
· On a port, the loop guard feature and the edge port setting are mutually exclusive.
Configuration procedure
To specify a port as an edge port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the current ports as edge ports. |
stp edged-port |
By default, all ports are non-edge ports. |
Configuring path costs of ports
Path cost is a parameter related to the rate of a port. On a spanning tree device, a port can have different path costs in different MSTIs. Setting appropriate path costs allows VLAN traffic flows to be forwarded along different physical links, achieving VLAN-based load balancing.
You can have the device automatically calculate the default path cost, or you can configure the path cost for ports.
Specifying a standard for the device to use when it calculates the default path cost
|
|
CAUTION: If you change the standard that the device uses to calculate the default path costs, you restore the path costs to the default. |
You can specify a standard for the device to use in automatic calculation for the default path cost. The device supports the following standards:
· dot1d-1998—The device calculates the default path cost for ports based on IEEE 802.1d-1998.
· dot1t—The device calculates the default path cost for ports based on IEEE 802.1t.
· legacy—The device calculates the default path cost for ports based on a private standard.
Table 5 shows the mapping between the link speed and the path cost.
Table 5 Mappings between the link speed and the path cost
|
Link speed |
Port type |
Path cost |
||
|
IEEE 802.1d-1998 |
IEEE 802.1t |
Private standard |
||
|
0 |
N/A |
65535 |
200000000 |
200000 |
|
10 Mbps |
Single port |
100 |
2000000 |
2000 |
|
Aggregate interface containing 2 Selected ports |
1000000 |
1800 |
||
|
Aggregate interface containing 3 Selected ports |
666666 |
1600 |
||
|
Aggregate interface containing 4 Selected ports |
500000 |
1400 |
||
|
100 Mbps |
Single port |
19 |
200000 |
200 |
|
Aggregate interface containing 2 Selected ports |
100000 |
180 |
||
|
Aggregate interface containing 3 Selected ports |
66666 |
160 |
||
|
Aggregate interface containing 4 Selected ports |
50000 |
140 |
||
|
1000 Mbps |
Single port |
4 |
20000 |
20 |
|
Aggregate interface containing 2 Selected ports |
10000 |
18 |
||
|
Aggregate interface containing 3 Selected ports |
6666 |
16 |
||
|
Aggregate interface containing 4 Selected ports |
5000 |
14 |
||
|
10 Gbps |
Single port |
2 |
2000 |
2 |
|
Aggregate interface containing 2 Selected ports |
1000 |
1 |
||
|
Aggregate interface containing 3 Selected ports |
666 |
1 |
||
|
Aggregate interface containing 4 Selected ports |
500 |
1 |
||
Configuration restrictions and guidelines
When you specify a standard for the device to use when it calculates the default path cost, follow these restrictions and guidelines:
· When it calculates the path cost for an aggregate interface, IEEE 802.1t takes into account the number of Selected ports in its aggregation group, but IEEE 802.1d-1998 does not. The calculation formula of IEEE 802.1t is: Path cost = 200,000,000/link speed (in 100 kbps), where link speed is the sum of the link speed values of the Selected ports in the aggregation group.
· IEEE 802.1d-1998 or the private standard always assigns the smallest possible value to a single port or an aggregate interface when the link speed of the port or interface exceeds 10 Gbps. The forwarding path selected based on this criterion might not be the best one. To solve this problem, use dot1t as the standard for default path cost calculation, or manually set the path cost for the port (see "Configuring path costs of ports").
Configuration procedure
To specify a standard for the device to use when it calculates the default path cost:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a standard for the device to use when it calculates the default path costs of its ports. |
stp pathcost-standard { dot1d-1998 | dot1t | legacy } |
The default setting is legacy. |
Configuring path costs of ports
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the path cost of the ports. |
·
In STP/RSTP mode: ·
In MSTP mode: |
By default, the system automatically calculates the path cost of each port. |
|
|
NOTE: When the path cost of a port changes, the system re-calculates the role of the port and initiates a state transition. |
Configuration example
# In MSTP mode, configure the device to calculate the default path costs of its ports by using IEEE 802.1d-1998, and set the path cost of FortyGigE 1/0/3 to 200 on MSTI 2.
<Sysname> system-view
[Sysname] stp pathcost-standard dot1d-1998
Cost of every port will be reset and automatically re-calculated after you change the current pathcost standard. Continue?[Y/N]:y
Cost of every port has been re-calculated.
[Sysname] interface fortygige 1/0/3
[Sysname-FortyGigE1/0/3] stp instance 2 cost 200
Configuring the port priority
The priority of a port is a factor that determines whether the port can be elected as the root port of a device. If all other conditions are the same, the port with the highest priority is elected as the root port.
On a spanning tree device, a port can have different priorities and play different roles in different spanning trees, so that data of different VLANs can be propagated along different physical paths, implementing per-VLAN load balancing. You can set port priority values based on the actual networking requirements.
To configure the priority of a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port priority. |
·
In STP/RSTP mode: ·
In MSTP mode: |
The default setting is 128 for all ports. |
|
|
NOTE: When the priority of a port changes, the system re-calculates the port role and initiates a state transition. |
Configuring the port link type
A point-to-point link directly connects two devices. If two root ports or designated ports are connected over a point-to-point link, they can rapidly transit to the forwarding state after a proposal-agreement handshake process.
Configuration restrictions and guidelines
When you configure the port link type, follow these restrictions and guidelines:
· You can configure the link type as point-to-point for a Layer 2 aggregate interface or a port that operates in full duplex mode. As a best practice, use the default setting for the device to automatically detect the port link type.
· The stp point-to-point force-false or stp point-to-point force-true command configured on a port in MSTP mode is effective on all MSTIs.
· If you configure a non-point-to-point link as a point-to-point link, the configuration might cause a temporary loop.
Configuration procedure
To configure the link type of a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port link type. |
stp point-to-point { auto | force-false | force-true } |
By default, the link type is auto where the port automatically detects the link type. |
Configuring the mode a port uses to recognize and send MSTP packets
A port can receive and send MSTP packets in the following formats:
· dot1s—802.1s-compliant standard format
· legacy—Compatible format
When the number of existing MSTIs exceeds 48, the port can send only 802.1s MSTP packets.
By default, the packet format recognition mode of a port is auto. The port automatically distinguishes the two MSTP packet formats, and determines the format of packets that it will send based on the recognized format.
You can configure the MSTP packet format on a port. When operating in MSTP mode after the configuration, the port sends only MSTP packets of the format that you have configured to communicate with devices that send packets of the same format.
A port in auto mode sends 802.1s MSTP packets by default. When the port receives an MSTP packet of a legacy format, the port starts to send packets only of the legacy format. This prevents the port from frequently changing the format of sent packets. To configure the port to send 802.1s MSTP packets, shut down and then bring up the port.
To configure the MSTP packet format to be supported on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the mode that the port uses to recognize/send MSTP packets. |
stp compliance { auto | dot1s | legacy } |
The default setting is auto. |
Enabling outputting port state transition information
In a large-scale spanning tree network, you can enable devices to output the port state transition information of all MSTIs or the specified MSTI in order to monitor the port states in real time.
To enable outputting port state transition information:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable outputting port state transition information. |
·
In STP/RSTP mode: ·
In MSTP mode: |
By default, this feature is enabled. |
Enabling the spanning tree feature
You must enable the spanning tree feature for the device before any other spanning tree related configurations can take effect. Make sure the spanning tree feature is enabled globally and on the desired ports.
You can disable the spanning tree feature for certain ports with the undo stp enable command to exclude them from spanning tree calculation and save CPU resources of the device.
To enable the spanning tree feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the spanning tree feature globally. |
stp global enable |
By default, the spanning tree feature is disabled globally. |
|
3. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
4. (Optional.) Enable the spanning tree feature for the port. |
stp enable |
By default, the spanning tree feature is enabled on all ports. |
Performing mCheck
The mCheck feature enables user intervention in the port status transition process.
If a port on a device that is running MSTP or RSTP connects to an STP device, this port automatically transits to STP mode when the port receives STP BPDUs. However, if the peer STP device is shut down or removed and the local device cannot detect the change, the local device cannot automatically transit back to the original mode. To forcibly transit the port to operate in the original mode, you can perform an mCheck operation.
Suppose a scenario where Device A, Device B, and Device C are connected in sequence. Device A runs STP, Device B does not run any spanning tree protocol, and Device C runs RSTP or MSTP. In this case, when Device C receives an STP BPDU transparently transmitted by Device B, the receiving port transits to the STP mode. If you configure Device B to run RSTP or MSTP with Device C, you must perform mCheck operations on the ports interconnecting Device B and Device C.
The following methods for performing mCheck produce the same result.
Performing mCheck globally
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Perform mCheck. |
stp global mcheck |
Performing mCheck in interface view
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
|
3. Perform mCheck. |
stp mcheck |
|
|
NOTE: An mCheck operation takes effect on a device that operates in MSTP or RSTP mode. |
Configuring Digest Snooping
As defined in IEEE 802.1s, connected devices are in the same region only when their MST region-related configurations (region name, revision level, and VLAN-to-instance mappings) are identical. A spanning tree device identifies devices in the same MST region by determining the configuration ID in BPDU packets. The configuration ID includes the region name, revision level, and configuration digest, which is 16-byte long and is the result calculated through the HMAC-MD5 algorithm based on VLAN-to-instance mappings.
Because spanning tree implementations vary by vendor, the configuration digests calculated through private keys are different. The devices of different vendors in the same MST region cannot communicate with each other.
To enable communication between an H3C device and a third-party device, enable the Digest Snooping feature on the port that connects the H3C device to the third-party device in the same MST region.
Configuration restrictions and guidelines
When you configure Digest Snooping, follow these restrictions and guidelines:
· Before you enable Digest Snooping, make sure associated devices of different vendors are connected and run spanning tree protocols.
· With Digest Snooping enabled, in-the-same-region verification does not require comparison of configuration digest, so the VLAN-to-instance mappings must be the same on associated ports.
· With Digest Snooping enabled globally, modify the VLAN-to-instance mappings or execute the undo stp region-configuration command to restore the default MST region configuration with caution. If the local device has different VLAN-to-instance mappings than its neighboring devices, loops or traffic interruption occurs.
· To make Digest Snooping take effect, you must enable Digest Snooping both globally and on associated ports. As a best practice, enable Digest Snooping on all associated ports first and then enable it globally. This will make the configuration take effect on all configured ports and reduce impact on the network.
· To prevent loops, do not enable Digest Snooping on MST region edge ports.
· As a best practice, enable Digest Snooping first and then the spanning tree feature. To avoid traffic interruption, do not configure Digest Snooping when the network is already working well.
Configuration procedure
You can enable Digest Snooping only on the H3C device that is connected to a third-party device that uses its private key to calculate the configuration digest.
To configure Digest Snooping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable Digest Snooping on the interface. |
stp config-digest-snooping |
By default, Digest Snooping is disabled on ports. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enable Digest Snooping globally. |
stp global config-digest-snooping |
By default, Digest Snooping is disabled globally. |
Digest Snooping configuration example
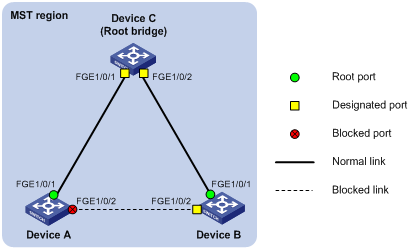
Network requirements
As shown in Figure 7, Device A and Device B connect to Device C, which is a third-party device. All these devices are in the same region.
Enable Digest Snooping on the ports of Device A and Device B that connect to Device C, so that the three devices can communicate with one another.
Configuration procedure
# Enable Digest Snooping on FortyGigE 1/0/1 of Device A and enable global Digest Snooping on Device A.
<DeviceA> system-view
[DeviceA] interface fortygige 1/0/1
[DeviceA-FortyGigE1/0/1] stp config-digest-snooping
[DeviceA-FortyGigE1/0/1] quit
[DeviceA] stp global config-digest-snooping
# Enable Digest Snooping on FortyGigE 1/0/1 of Device B and enable global Digest Snooping on Device B.
<DeviceB> system-view
[DeviceB] interface fortygige 1/0/1
[DeviceB-FortyGigE1/0/1] stp config-digest-snooping
[DeviceB-FortyGigE1/0/1] quit
[DeviceB] stp global config-digest-snooping
Configuring No Agreement Check
In RSTP and MSTP, the following types of messages are used for rapid state transition on designated ports:
· Proposal—Sent by designated ports to request rapid transition
· Agreement—Used to acknowledge rapid transition requests
Both RSTP and MSTP devices can perform rapid transition on a designated port only when the port receives an agreement packet from the downstream device. RSTP and MSTP devices have the following differences:
· For MSTP, the root port of the downstream device sends an agreement packet only after it receives an agreement packet from the upstream device.
· For RSTP, the downstream device sends an agreement packet regardless of whether an agreement packet from the upstream device is received.
Figure 8 Rapid state transition of an MSTP designated port
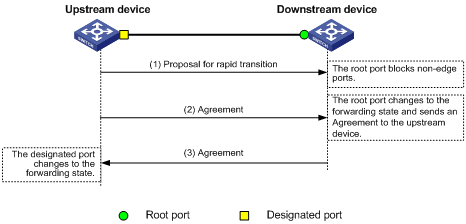
Figure 9 Rapid state transition of an RSTP designated port

If the upstream device is a third-party device, the rapid state transition implementation might be limited. For example, when the upstream device uses a rapid transition mechanism similar to that of RSTP, and the downstream device adopts MSTP and does not operate in RSTP mode, the root port on the downstream device receives no agreement packet from the upstream device and sends no agreement packets to the upstream device. As a result, the designated port of the upstream device fails to transit rapidly, and can only change to the forwarding state after a period twice the Forward Delay.
You can enable the No Agreement Check feature on the downstream device's port to enable the designated port of the upstream device to transit its state rapidly.
Configuration prerequisites
Before you configure the No Agreement Check feature, complete the following tasks:
· Connect a device to a third-party upstream device that supports spanning tree protocols through a point-to-point link.
· Configure the same region name, revision level and VLAN-to-instance mappings on the two devices, assigning them to the same region.
Configuration procedure
Enable the No Agreement Check feature on the root port.
To configure No Agreement Check:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable No Agreement Check. |
stp no-agreement-check |
By default, No Agreement Check is disabled. |
No Agreement Check configuration example
Network requirements
As shown in Figure 10:
· Device A connects to a third-party device that has a different spanning tree implementation. Both devices are in the same region.
· The third-party device (Device B) is the regional root bridge, and Device A is the downstream device.
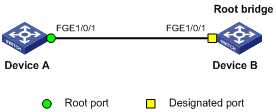
Configuration procedure
# Enable No Agreement Check on FortyGigE 1/0/1 of Device A.
<DeviceA> system-view
[DeviceA] interface fortygige 1/0/1
[DeviceA-FortyGigE1/0/1] stp no-agreement-check
Configuring protection features
A spanning tree device supports the following protection features:
· BPDU guard
· Root guard
· Loop guard
· Port role restriction
· TC-BPDU transmission restriction
· TC-BPDU guard
· Dispute guard
Enabling BPDU guard
For access layer devices, the access ports can directly connect to the user terminals (such as PCs) or file servers. The access ports are configured as edge ports to allow rapid transition. When these ports receive configuration BPDUs, the system automatically sets the ports as non-edge ports and starts a new spanning tree calculation process. This causes a change of network topology. Under normal conditions, these ports should not receive configuration BPDUs. However, if someone forges configuration BPDUs maliciously to attack the devices, the network will become unstable.
The spanning tree protocol provides the BPDU guard feature to protect the system against such attacks. With the BPDU guard feature enabled on the devices, when edge ports receive configuration BPDUs, the system closes these ports and notifies the NMS that these ports have been closed by the spanning tree protocol. The device reactivates the closed ports after a detection interval. For more information about this detection interval, see Fundamentals Configuration Guide.
BPDU guard does not take effect on loopback-testing-enabled ports. For more information about loopback testing, see "Configuring Ethernet interfaces."
Configure BPDU guard on a device with edge ports configured.
To enable BPDU guard:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the BPDU guard feature for the device. |
stp bpdu-protection |
By default, BPDU guard is disabled. |
Enabling root guard
The root bridge and secondary root bridge of a spanning tree should be located in the same MST region. Especially for the CIST, the root bridge and secondary root bridge are put in a high-bandwidth core region during network design. However, due to possible configuration errors or malicious attacks in the network, the legal root bridge might receive a configuration BPDU with a higher priority. Another device supersedes the current legal root bridge, causing an undesired change of the network topology. The traffic that should go over high-speed links is switched to low-speed links, resulting in network congestion.
To prevent this situation, MSTP provides the root guard feature. If the root guard feature is enabled on a port of a root bridge, this port plays the role of designated port on all MSTIs. After this port receives a configuration BPDU with a higher priority from an MSTI, it immediately sets that port to the listening state in the MSTI, without forwarding the packet. This is equivalent to disconnecting the link connected to this port in the MSTI. If the port receives no BPDUs with a higher priority within twice the forwarding delay, it reverts to its original state.
On a port, the loop guard feature and the root guard feature are mutually exclusive.
Configure root guard on a designated port.
To enable root guard:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable the root guard feature. |
stp root-protection |
By default, root guard is disabled. |
Enabling loop guard
By continuing to receive BPDUs from the upstream device, a device can maintain the state of the root port and blocked ports. However, link congestion or unidirectional link failures might cause these ports to fail to receive BPDUs from the upstream devices. The device reselects the port roles: Those ports in forwarding state that failed to receive upstream BPDUs become designated ports, and the blocked ports transit to the forwarding state, resulting in loops in the switched network. The loop guard feature can suppress the occurrence of such loops.
The initial state of a loop guard-enabled port is discarding in every MSTI. When the port receives BPDUs, it transits its state. Otherwise, it stays in the discarding state to prevent temporary loops.
Do not enable loop guard on a port that connects user terminals. Otherwise, the port stays in the discarding state in all MSTIs because it cannot receive BPDUs.
On a port, the loop guard feature is mutually exclusive with the root guard feature or the edge port setting.
Configure loop guard on the root port and alternate ports of a device.
To enable loop guard:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable the loop guard feature for the ports. |
stp loop-protection |
By default, loop guard is disabled. |
Configuring port role restriction
|
|
CAUTION: Use this feature with caution, because enabling port role restriction on a port might affect the connectivity of the spanning tree topology. |
The change to the bridge ID of a device in the user access network might cause a change to the spanning tree topology in the core network. To avoid this problem, you can enable port role restriction on a port. With this feature enabled, when the port receives a superior BPDU, it becomes an alternate port rather than a root port.
Make this configuration on the port that connects to the user access network.
To configure port role restriction:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable port role restriction. |
stp role-restriction |
By default, port role restriction is disabled. |
Configuring TC-BPDU transmission restriction
|
|
CAUTION: Enabling TC-BPDU transmission restriction on a port might cause the previous forwarding address table to fail to be updated when the topology changes. |
The topology change to the user access network might cause the forwarding address changes to the core network. When the user access network topology is unstable, the user access network might affect the core network. To avoid this problem, you can enable TC-BPDU transmission restriction on a port. With this feature enabled, when the port receives a TC-BPDU, it does not forward the TC-BPDU to other ports.
Make this configuration on the port that connects to the user access network.
To configure TC-BPDU transmission restriction:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable TC-BPDU transmission restriction. |
stp tc-restriction |
By default, TC-BPDU transmission restriction is disabled. |
Enabling TC-BPDU guard
When a device receives topology change (TC) BPDUs (the BPDUs that notify devices of topology changes), it flushes its forwarding address entries. If someone forges TC-BPDUs to attack the device, the device will receive a large number of TC-BPDUs within a short time and be busy with forwarding address entry flushing. This affects network stability.
With the TC-BPDU guard feature, you can set the maximum number of immediate forwarding address entry flushes that the device can perform within a specified period of time (10 seconds) after it receives the first TC-BPDU. For TC-BPDUs received in excess of the limit, the device performs a forwarding address entry flush when the time period expires. This prevents frequent flushing of forwarding address entries.
To enable TC-BPDU guard:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the TC-BPDU guard feature. |
stp tc-protection |
By default, TC-BPDU guard is enabled. As a best practice, do not disable this feature. |
|
3. (Optional.) Configure the maximum number of forwarding address entry flushes that the device can perform every 10 seconds. |
stp tc-protection threshold number |
The default setting is 6. |
Enabling dispute guard
Dispute guard can be triggered by unidirectional link failures. If an upstream port receives inferior BPDUs from a downstream designated port in forwarding or learning state because of a unidirectional link failure, a loop appears. Dispute guard blocks the upstream designated port to prevent the loop.
Dispute guard is enabled by default. You don't have to configure this feature.
As shown in Figure 11, in normal conditions, the spanning tree calculation result is as follows:
· Device A is the root bridge, and Port A1 is a designated port.
· Port B1 is blocked.
When the link between Port A1 and Port B1 fails in the direction of Port A1 to Port B1 and becomes unidirectional, the following events occur:
1. Port A1 can only receive BPDUs and cannot send BPDUs to Port B1.
2. Port B1 does not receive BPDUs from Port A1 for a certain period of time.
3. Device B determines itself as the root bridge.
4. Port B1 sends its BPDUs to Port A1.
5. Port A1 determines the received BPDUs are inferior to its own BPDUs. A dispute is detected.
6. Dispute guard is triggered and blocks Port A1 to prevent a loop.
Figure 11 Dispute guard triggering scenario

Displaying and maintaining the spanning tree
Execute display commands in any view and reset command in user view.
|
Task |
Command |
|
Display information about ports blocked by spanning tree protection features. |
display stp abnormal-port |
|
Display BPDU statistics on ports. |
display stp bpdu-statistics [ interface interface-type interface-number [ instance instance-list ] ] |
|
Display information about ports shut down by spanning tree protection features. |
display stp down-port |
|
Display the historical information of port role calculation for the specified MSTI or all MSTIs (in standalone mode). |
display stp [ instance instance-list ] history [ slot slot-number ] |
|
Display the historical information of port role calculation for the specified MSTI or all MSTIs (in IRF mode). |
display stp [ instance instance-list ] history [ chassis chassis-number slot slot-number ] |
|
Display the statistics of TC/TCN BPDUs sent and received by all ports in the specified MSTI or all MSTIs (in standalone mode). |
display stp [ instance instance-list ] tc [ slot slot-number ] |
|
Display the statistics of TC/TCN BPDUs sent and received by all ports in the specified MSTI or all MSTIs (in IRF mode). |
display stp [ instance instance-list ] tc [ chassis chassis-number slot slot-number ] |
|
Display the spanning tree status and statistics (in standalone mode). |
display stp [ instance instance-list ] [ interface interface-list | slot slot-number ] [ brief ] |
|
Display the spanning tree status and statistics (in IRF mode). |
display stp [ instance instance-list ] [ interface interface-list | chassis chassis-number slot slot-number ] [ brief ] |
|
Display the MST region configuration information that has taken effect. |
display stp region-configuration |
|
Display the root bridge information of all MSTIs. |
display stp root |
|
Clear the spanning tree statistics. |
reset stp [ interface interface-list ] |
Spanning tree configuration example
Network requirements
As shown in Figure 12, all devices on the network are in the same MST region. Device A and Device B work at the distribution layer. Device C and Device D work at the access layer.
Configure MSTP so that packets of different VLANs are forwarded along different spanning trees: Packets of VLAN 10 are forwarded along MSTI 1, those of VLAN 30 are forwarded along MSTI 3, those of VLAN 40 are forwarded along MSTI 4, and those of VLAN 20 are forwarded along MSTI 0.
VLAN 10 and VLAN 30 are terminated on the distribution layer devices, and VLAN 40 is terminated on the access layer devices. The root bridges of MSTI 1 and MSTI 3 are Device A and Device B, respectively, and the root bridge of MSTI 4 is Device C.
Configuration procedure
1. Configure VLANs and VLAN member ports: (Details not shown.)
¡ Create VLAN 10, VLAN 20, and VLAN 30 on both Device A and Device B.
¡ Create VLAN 10, VLAN 20, and VLAN 40 on Device C.
¡ Create VLAN 20, VLAN 30, and VLAN 40 on Device D.
¡ Configure the ports on these devices as trunk ports and assign them to related VLANs.
2. Configure Device A:
# Enter MST region view, and configure the MST region name as example.
<DeviceA> system-view
[DeviceA] stp region-configuration
[DeviceA-mst-region] region-name example
# Map VLAN 10, VLAN 30, and VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively.
[DeviceA-mst-region] instance 1 vlan 10
[DeviceA-mst-region] instance 3 vlan 30
[DeviceA-mst-region] instance 4 vlan 40
# Configure the revision level of the MST region as 0.
[DeviceA-mst-region] revision-level 0
# Activate MST region configuration.
[DeviceA-mst-region] active region-configuration
[DeviceA-mst-region] quit
# Specify the current device as the root bridge of MSTI 1.
[DeviceA] stp instance 1 root primary
# Enable the spanning tree feature globally.
[DeviceA] stp global enable
3. Configure Device B:
# Enter MST region view, and configure the MST region name as example.
<DeviceB> system-view
[DeviceB] stp region-configuration
[DeviceB-mst-region] region-name example
# Map VLAN 10, VLAN 30, and VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively.
[DeviceB-mst-region] instance 1 vlan 10
[DeviceB-mst-region] instance 3 vlan 30
[DeviceB-mst-region] instance 4 vlan 40
# Configure the revision level of the MST region as 0.
[DeviceB-mst-region] revision-level 0
# Activate MST region configuration.
[DeviceB-mst-region] active region-configuration
[DeviceB-mst-region] quit
# Specify the current device as the root bridge of MSTI 3.
[DeviceB] stp instance 3 root primary
# Enable the spanning tree feature globally.
[DeviceB] stp global enable
4. Configure Device C:
# Enter MST region view, and configure the MST region name as example.
<DeviceC> system-view
[DeviceC] stp region-configuration
[DeviceC-mst-region] region-name example
# Map VLAN 10, VLAN 30, and VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively.
[DeviceC-mst-region] instance 1 vlan 10
[DeviceC-mst-region] instance 3 vlan 30
[DeviceC-mst-region] instance 4 vlan 40
# Configure the revision level of the MST region as 0.
[DeviceC-mst-region] revision-level 0
# Activate MST region configuration.
[DeviceC-mst-region] active region-configuration
[DeviceC-mst-region] quit
# Specify the current device as the root bridge of MSTI 4.
[DeviceC] stp instance 4 root primary
# Enable the spanning tree feature globally.
[DeviceC] stp global enable
5. Configure Device D:
# Enter MST region view, and configure the MST region name as example.
<DeviceD> system-view
[DeviceD] stp region-configuration
[DeviceD-mst-region] region-name example
# Map VLAN 10, VLAN 30, and VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively.
[DeviceD-mst-region] instance 1 vlan 10
[DeviceD-mst-region] instance 3 vlan 30
[DeviceD-mst-region] instance 4 vlan 40
# Configure the revision level of the MST region as 0.
[DeviceD-mst-region] revision-level 0
# Activate MST region configuration.
[DeviceD-mst-region] active region-configuration
[DeviceD-mst-region] quit
# Enable the spanning tree feature globally.
[DeviceD] stp global enable
Verifying the configuration
In this example, suppose that Device B has the lowest root bridge ID. As a result, Device B is elected as the root bridge in MSTI 0.
You can use the display stp brief command to display brief spanning tree information on each device after the network is stable.
# Display brief spanning tree information on Device A.
[DeviceA] display stp brief
[DeviceA] display stp brief
MSTID Port Role STP State Protection
0 FortyGigE1/0/1 ALTE DISCARDING NONE
0 FortyGigE1/0/2 DESI FORWARDING NONE
0 FortyGigE1/0/3 ROOT FORWARDING NONE
1 FortyGigE1/0/1 DESI FORWARDING NONE
1 FortyGigE1/0/3 DESI FORWARDING NONE
3 FortyGigE1/0/2 DESI FORWARDING NONE
3 FortyGigE1/0/3 ROOT FORWARDING NONE
# Display brief spanning tree information on Device B.
[DeviceB] display stp brief
MSTID Port Role STP State Protection
0 FortyGigE1/0/1 DESI FORWARDING NONE
0 FortyGigE1/0/2 DESI FORWARDING NONE
0 FortyGigE1/0/3 DESI FORWARDING NONE
1 FortyGigE1/0/2 DESI FORWARDING NONE
1 FortyGigE1/0/3 ROOT FORWARDING NONE
3 FortyGigE1/0/1 DESI FORWARDING NONE
3 FortyGigE1/0/3 DESI FORWARDING NONE
# Display brief spanning tree information on Device C.
[DeviceC] display stp brief
MSTID Port Role STP State Protection
0 FortyGigE1/0/1 DESI FORWARDING NONE
0 FortyGigE1/0/2 ROOT FORWARDING NONE
0 FortyGigE1/0/3 DESI FORWARDING NONE
1 FortyGigE1/0/1 ROOT FORWARDING NONE
1 FortyGigE1/0/2 ALTE DISCARDING NONE
4 FortyGigE1/0/3 DESI FORWARDING NONE
# Display brief spanning tree information on Device D.
[DeviceD] display stp brief
MSTID Port Role STP State Protection
0 FortyGigE1/0/1 ROOT FORWARDING NONE
0 FortyGigE1/0/2 ALTE DISCARDING NONE
0 FortyGigE1/0/3 ALTE DISCARDING NONE
3 FortyGigE1/0/1 ROOT FORWARDING NONE
3 FortyGigE1/0/2 ALTE DISCARDING NONE
4 FortyGigE1/0/3 ROOT FORWARDING NONE
Based on the output, you can draw each MSTI mapped to each VLAN, as shown in Figure 13.
Figure 13 MSTIs mapped to different VLANs