- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-GRE configuration | 196.13 KB |
Contents
GRE tunnel operating principle
Displaying and maintaining GRE
Configuring an IPv4 over IPv4 GRE tunnel
Configuring an IPv4 over IPv6 GRE tunnel
Configuring GRE
Overview
GRE encapsulation format
Figure 1 GRE encapsulation format
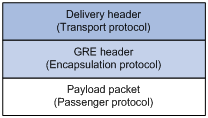
As shown in Figure 1, a GRE-tunneled packet includes the following parts:
· Payload packet—Original packet. The protocol type of the payload packet is called the passenger protocol. The passenger protocol can be any network layer protocol.
· GRE header—Header that is added to the payload packet to change the payload packet to a GRE packet. A GRE header includes the number of encapsulations, version, passenger protocol type, checksum, and key. GRE is called the encapsulation protocol.
· Delivery header—Header that is added to the GRE packet to deliver it to the tunnel end. The transport protocol (or delivery protocol) is the network layer protocol that transfers GRE packets.
The device supports GRE tunnels with IPv4 and IPv6 as the transport protocols. When the transport protocol is IPv4, the GRE tunnel mode is GRE over IPv4 (GRE/IPv4). When the transport protocol is IPv6, the GRE tunnel mode is GRE over IPv6 (GRE/IPv6).
GRE tunnel operating principle
Figure 2 IPv6 networks interconnected through a GRE tunnel
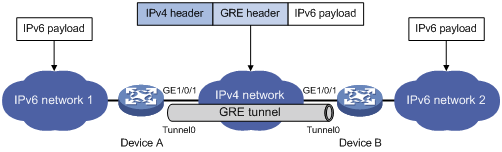
As shown in Figure 2, an IPv6 protocol packet traverses an IPv4 network through a GRE tunnel as follows:
1. After receiving an IPv6 packet from the interface connected to IPv6 network 1, Device A processes the packet as follows:
a. Looks up the routing table to identify the outgoing interface for the IPv6 packet.
b. Submits the IPv6 packet to the outgoing interface—the GRE tunnel interface Tunnel 0.
2. Upon receiving the packet, the tunnel interface encapsulates the packet with GRE and then with IPv4. In the IPv4 header:
? The source address is the tunnel's source address (the IP address of interface GigabitEthernet 1/0/1 of Device A).
? The destination address is the tunnel's destination address (the IP address of interface GigabitEthernet 1/0/1 of Device B).
3. Device A looks up the routing table according to the destination address in the IPv4 header, and forwards the IPv4 packet out of the physical interface (GigabitEthernet 1/0/1) of the GRE tunnel.
4. When the IPv4 arrives at the GRE tunnel destination Device B, Device B checks the destination address. Because the destination is Device B itself and the protocol number in the IP header is 47 (the protocol number for GRE), Device B submits the packet to GRE for de-encapsulation.
5. GRE first removes the IPv4 header, and then checks the GRE key, checksum, and packet sequence number. After GRE finishes the checking, it removes the GRE header, and submits the payload to the IPv6 protocol for forwarding.
|
|
NOTE: GRE encapsulation and de-encapsulation can decrease the forwarding efficiency of tunnel-end devices. |
GRE security mechanisms
GRE supports the following security mechanisms:
· GRE key—Ensures packet validity. The sender adds a GRE key into a packet. The receiver compares the GRE key with its own GRE key. If the two keys are the same, the receiver accepts the packet. If the two keys are different, the receiver drops the packet.
· GRE checksum—Ensures packet integrity. The sender calculates a checksum for the GRE header and payload and sends the packet containing the checksum to the tunnel peer. The receiver calculates a checksum for the received packet and compares it with that carried in the packet. If the checksums are the same, the receiver considers the packet intact and continues to process the packet. If the checksums are different, the receiver discards the packet.
GRE application scenarios
The following shows typical GRE application scenarios:
Connecting networks running different protocols over a single backbone
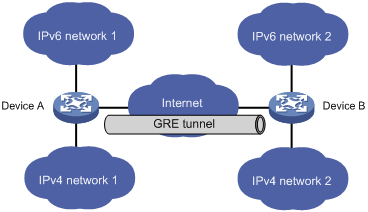
As shown in Figure 3, IPv6 network 1 and IPv6 network 2 are IPv6 networks, and IPv4 network 1 and IPv4 network 2 are IPv4 networks. Through the GRE tunnel between Device A and Device B, IPv6 network 1 can communicate with IPv6 network 2 and IPv4 network 1 can communicate with IPv4 network 2, without affecting each other.
Enlarging network scope
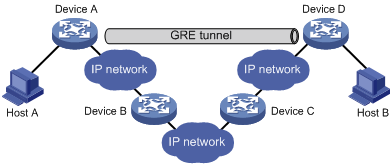
In an IP network, the maximum TTL value of a packet is 255. If two devices have more than 255 hops in between, they cannot communicate with each other. By using a GRE tunnel, you can hide some hops to enlarge the network scope. As shown in Figure 4, only the tunnel-end devices (Device A and Device D) of the GRE tunnel are counted in hop count calculation. Therefore, there are only three hops between Host A and Host B.
Protocols and standards
· RFC 1701, Generic Routing Encapsulation (GRE)
· RFC 1702, Generic Routing Encapsulation over IPv4 networks
· RFC 2784, Generic Routing Encapsulation (GRE)
· RFC 2890, Key and Sequence Number Extensions to GRE
Configuring a GRE/IPv4 tunnel
Perform this task to configure a GRE tunnel on an IPv4 network.
Configuration guidelines
Follow these guidelines when you configure a GRE/IPv4 tunnel:
· You must configure the tunnel source address and destination address at both ends of a tunnel. The tunnel source or destination address at one end must be the tunnel destination or source address at the other end.
· H3C recommends not configuring the same tunnel source and destination addresses for local tunnel interfaces that use the same tunnel mode.
· You can enable or disable GRE checksum at each end of a tunnel. If GRE checksum is enabled at a tunnel end, the tunnel end sends packets carrying the checksum to the peer end. A tunnel end checks the GRE checksum of a received packet if the packet carries a GRE checksum, whether or not the tunnel end is enabled with GRE checksum.
· To ensure correct packet forwarding, identify whether the destination network of packets and the IP address of the local tunnel interface are on the same subnet. If they are not, configure a route reaching the destination network through the tunnel interface. You can configure the route by using one of the following methods:
? Configure a static route, using the local tunnel interface as the outgoing interface of the route.
? Enable a dynamic routing protocol on both the tunnel interface and the interface connecting the private network. This allows the dynamic routing protocol to establish a routing entry with the tunnel interface as the outgoing interface.
· The IP address of the tunnel interface and the tunnel destination address configured on the tunnel interface must be in different subnets.
Configuration procedure
To configure a GRE/IPv4 tunnel:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Create a GRE tunnel interface, and specify the tunnel mode as GRE/IPv4. |
interface tunnel interface-number mode gre |
By default, the device has no tunnel interface. You must configure the same tunnel mode on both ends of a tunnel. Otherwise, packet delivery might fail. |
|
|
3. Configure an IPv4 or IPv6 address for the tunnel interface. |
For information about how to assign an IPv4 address to an interface, see "Configuring IP addressing." For information about how to assign an IPv6 address to an interface, see "Configuring basic IPv6 settings." |
By default, no IPv4 or IPv6 address is configured for a tunnel interface. When the passenger protocol is IPv4, configure an IPv4 address for the tunnel interface. When the passenger protocol is IPv6, configure an IPv6 address for the tunnel interface. |
|
|
4. Configure a source address or source interface for the tunnel interface. |
source { ip-address | interface-type interface-number } |
By default, no source address or interface is configured for a tunnel interface. If you configure a source address for a tunnel interface, the tunnel interface uses the source address as the source address of the encapsulated packets. If you configure a source interface for a tunnel interface, the tunnel interface uses the primary IP address of the source interface as the source address of the encapsulated packets. |
|
|
5. Configure a destination address for the tunnel interface. |
destination ip-address |
By default, no destination address is configured for a tunnel interface. The destination address is the address of the physical interface that the tunnel remote end uses to receive packets from the GRE tunnel. The tunnel local end uses this address as the destination address of the encapsulated packets. |
|
|
6. (Optional.) Configure a description for the tunnel interface. |
description text |
By default, the description for a tunnel interface is Tunnelnumber Interface. |
|
|
7. (Optional.) Set the MTU of the tunnel interface. |
mtu size |
By default, if the tunnel interface has never been up, the MTU is 64000 bytes. If the tunnel interface is up, its MTU is identical to the outgoing interface's MTU minus the length of the tunnel headers. The outgoing interface is automatically obtained through routing table lookup based on the tunnel destination address. |
|
|
8. (Optional.) Set the expected bandwidth for the tunnel interface. |
bandwidth bandwidth-value |
The default expected bandwidth (in kbps) is the interface maximum rate divided by 1000. The expected bandwidth for the tunnel interface affects the link cost value. |
|
|
9. (Optional.) Set the ToS for tunneled packets. |
tunnel tos tos-value |
The default setting is the same as the ToS of the original packets. |
|
|
10. (Optional.) Set the TTL for tunneled packets. |
tunnel ttl ttl-value |
The default TTL for tunneled packets is 255. |
|
|
11. (Optional.) Enable GRE keepalive, and set the keepalive interval and keepalive number. |
keepalive [ interval [ times ] ] |
By default, GRE keepalive is disabled. |
|
|
12. (Optional.) Enable GRE checksum. |
gre checksum |
By default, GRE checksum is disabled. |
|
|
13. (Optional.) Configure a GRE key for the GRE tunnel interface. |
gre key key-number |
By default, no GRE key is configured for a GRE tunnel interface. The two ends of a GRE tunnel must have the same key or both have no key. |
|
|
14. (Optional.) Set the DF bit for encapsulated packets. |
tunnel dfbit enable |
By default, the DF bit is not set, allowing encapsulated packets to be fragmented. |
|
|
15. (Optional.) Restore the default settings of the tunnel interface. |
default |
N/A |
|
|
16. (Optional.) Shut down the tunnel interface. |
shutdown |
By default, the tunnel interface is not in the Administratively DOWN state. |
|
Configuring a GRE/IPv6 tunnel
Perform this task to configure a GRE tunnel on an IPv6 network.
Configuration guidelines
Follow these guidelines when you configure a GRE/IPv6 tunnel:
· You must configure the tunnel source address and destination address at both ends of a tunnel. The tunnel source or destination address at one end must be the tunnel destination or source address at the other end.
· H3C recommends not configuring the same tunnel source and destination addresses for local tunnel interfaces that use the same tunnel mode.
· You can enable or disable GRE checksum at each end of a tunnel. If GRE checksum is enabled at a tunnel end, the tunnel end sends packets carrying the checksum to the peer end. A tunnel end checks the GRE checksum of a received packet if the packet carries a GRE checksum, whether or not the tunnel end is enabled with GRE checksum.
· To ensure correct packet forwarding, identify whether the destination network of packets and the IP address of the local tunnel interface are on the same subnet. If they are not, configure a route reaching the destination network through the tunnel interface. You can configure the route by using the following methods:
? Configure a static route, using the local tunnel interface as the outgoing interface of the route.
? Enable a dynamic routing protocol on both the tunnel interface and the interface connecting the private network. This allows the dynamic routing protocol to establish a routing entry with the tunnel interface as the outgoing interface.
· The IP address of the tunnel interface and the tunnel destination address configured on the tunnel interface must be in different subnets.
Configuration procedure
To configure a GRE/IPv6 tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a GRE tunnel interface, and specify the tunnel mode as GRE/IPv6. |
interface tunnel interface-number mode gre ipv6 |
By default, the device has no tunnel interface. You must configure the same tunnel mode on both ends of a tunnel. Otherwise, packet delivery might fail. |
|
3. Configure an IPv4 or IPv6 address for the tunnel interface. |
For information about how to assign an IPv4 address to an interface, see "Configuring IP addressing." For information about how to assign an IPv6 address to an interface, see "Configuring basic IPv6 settings." |
By default, no IPv4 or IPv6 address is configured for a tunnel interface. When the passenger protocol is IPv4, configure an IPv4 address for the tunnel interface. When the passenger protocol is IPv6, configure an IPv6 address for the tunnel interface. |
|
4. Configure a source IPv6 address or source interface for the tunnel interface. |
source { ipv6-address | interface-type interface-number } |
By default, no source IPv6 address or interface is configured for a tunnel interface. If you configure a source IPv6 address for a tunnel interface, the tunnel interface uses the source IPv6 address as the source IPv6 address of the encapsulated packets. If you configure a source interface for a tunnel interface, the tunnel interface uses the IPv6 address of the source interface as the source IPv6 address of the encapsulated packets. |
|
5. Configure a destination IPv6 address for the tunnel interface. |
destination ipv6-address |
By default, no destination IPv6 address is configured for a tunnel interface. The destination IPv6 address is the IPv6 address of the physical interface that the tunnel remote end uses to receive packets from the GRE tunnel. The tunnel local end uses this address as the destination IPv6 address of the encapsulated packets. |
|
6. (Optional.) Configure a description for the tunnel interface. |
description text |
By default, the description for a tunnel interface is Tunnelnumber Interface. |
|
7. (Optional.) Set the MTU of the tunnel interface. |
mtu size |
By default, if the tunnel interface has never been up, the MTU is 64000 bytes. If the tunnel interface is up, its MTU is identical to the outgoing interface's MTU minus the length of the tunnel headers. The outgoing interface is automatically obtained through routing table lookup based on the tunnel destination address. |
|
8. (Optional.) Set the expected bandwidth for the tunnel interface. |
bandwidth bandwidth-value |
The default expected bandwidth (in kbps) is the interface maximum rate divided by 1000. The expected bandwidth for the tunnel interface affects the link cost value. |
|
9. (Optional.) Set the ToS for tunneled packets. |
tunnel tos tos-value |
The default setting is the same as the ToS of the original packets. |
|
10. (Optional.) Set the TTL for tunneled packets. |
tunnel ttl ttl-value |
The default TTL for tunneled packets is 255. |
|
11. (Optional.) Enable GRE checksum. |
gre checksum |
By default, GRE checksum is disabled. |
|
12. (Optional.) Configure a GRE key for the tunnel interface. |
gre key key-number |
By default, no GRE key is configured for a GRE tunnel interface. The two ends of a GRE tunnel must have the same key or both have no key. |
|
13. (Optional.) Restore the default settings of the tunnel interface. |
default |
N/A |
|
14. (Optional.) Shut down the tunnel interface. |
shutdown |
By default, the tunnel interface is not in the Administratively DOWN state. |
Displaying and maintaining GRE
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
Remarks |
|
Display information about tunnel interfaces. |
display interface [ tunnel [ number ] ] [ brief [ description | down ] ] |
N/A |
|
Display IPv6 information about tunnel interface. |
display ipv6 interface [ tunnel [ number ] ] [ brief ] |
For more information about this command, see Layer 3—IP Services Command Reference. |
|
Clear tunnel interface statistics. |
reset counters interface [ tunnel [ number ] ] |
N/A |
GRE configuration examples
Configuring an IPv4 over IPv4 GRE tunnel
Network requirements
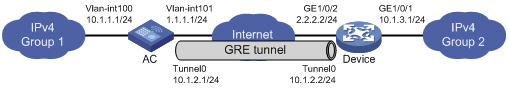
Group 1 and Group 2 are two private IPv4 networks. The two networks both use private network addresses. Establish a GRE tunnel between the AC and the device to interconnect the two private IPv4 networks Group 1 and Group 2.
Figure 5 Network diagram
Configuration procedure
Before performing the following configuration, configure an IP address for each interface, and make sure the AC and the device can reach each other.
1. Configure the AC:
# Create tunnel interface Tunnel 0, and specify the tunnel mode as GRE/IPv4.
[AC] interface tunnel 0 mode gre
# Configure an IP address for the tunnel interface.
[AC-Tunnel0] ip address 10.1.2.1 255.255.255.0
# Configure the source address of tunnel interface as the IP address of VLAN-interface 101 on the AC.
[AC-Tunnel0] source 1.1.1.1
# Configure the destination address of the tunnel interface as the IP address of GigabitEthernet 1/0/2 on the device.
[AC-Tunnel0] destination 2.2.2.2
[AC-Tunnel0] quit
# Configure a static route from the AC through the tunnel interface to Group 2.
[AC] ip route-static 10.1.3.0 255.255.255.0 tunnel 0
2. Configure the device:
# Create tunnel interface Tunnel 0, and specify the tunnel mode as GRE/IPv4.
[Device] interface tunnel 0 mode gre
# Configure an IP address for the tunnel interface.
[Device-Tunnel0] ip address 10.1.2.2 255.255.255.0
# Configure the source address of tunnel interface as the IP address of GigabitEthernet 1/0/2 on the device.
[Device-Tunnel0] source 2.2.2.2
# Configure the destination address of the tunnel interface as the IP address of VLAN-interface 101 on the AC.
[Device-Tunnel0] destination 1.1.1.1
[Device-Tunnel0] quit
# Configure a static route from the device through the tunnel interface to Group 1.
[Device] ip route-static 10.1.1.0 255.255.255.0 Tunnel 0
Verifying the configuration
# Display tunnel interface information on the AC.
[AC] display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum transmission unit: 64000
Internet address: 10.1.2.1/24 (primary)
Tunnel source 1.1.1.1 (Vlan-interface101), destination 2.2.2.2
Tunnel keepalive disabled
Tunnel TTL 255
Tunnel protocol/transport GRE/IP
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Display tunnel interface information on the device.
[Device] display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum transmission unit: 64000
Internet address: 10.1.2.2/24 (primary)
Tunnel source 2.2.2.2, destination 1.1.1.1
Tunnel keepalive disabled
Tunnel TTL 255
Tunnel protocol/transport GRE/IP
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# From the device, ping the IP address of VLAN-interface 100 on the AC.
[Device] ping -a 10.1.3.1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1) from 10.1.3.1: 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=11.000 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/2.400/11.000/4.317 ms
The output shows that the device can successfully ping the AC.
Configuring an IPv4 over IPv6 GRE tunnel
Network requirements
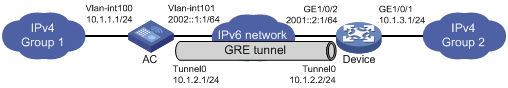
Two IPv4 subnets Group 1 and Group 2 are connected to an IPv6 network. Create a GRE/IPv6 tunnel between the AC and the device, so the two IPv4 subnets can communicate with each other through the GRE tunnel over the IPv6 network.
Figure 6 Network diagram
Configuration procedure
Before performing the following configuration, configure an IP address for each interface, and make sure the AC and the device can reach each other.
1. Configure the AC:
# Create tunnel interface Tunnel 0, and specify the tunnel mode as GRE/ IPv6.
[AC] interface tunnel 0 mode gre ipv6
# Configure an IP address for the tunnel interface.
[AC-Tunnel0] ip address 10.1.2.1 255.255.255.0
# Configure the source address of the tunnel interface as the IPv6 address of VLAN-interface 101 on the AC.
[AC-Tunnel0] source 2002::1:1
# Configure the destination address of the tunnel interface as the IPv6 address of GigabitEthernet 1/0/2 on the device.
[AC-Tunnel0] destination 2001::2:1
[AC-Tunnel0] quit
# Configure a static route from the AC through the tunnel interface to Group 2.
[AC] ip route-static 10.1.3.0 255.255.255.0 tunnel 0
2. Configure the device:
# Create tunnel interface Tunnel 0, and specify the tunnel mode as GRE/IPv6.
[Device] interface tunnel 0 mode gre ipv6
# Configure an IP address for the tunnel interface.
[Device-Tunnel0] ip address 10.1.2.2 255.255.255.0
# Configure the source address of tunnel interface as the IPv6 address of GigabitEthernet 1/0/2 on the device.
[Device-Tunnel0] source 2001::2:1
# Configure the destination address of the tunnel interface as the IPv6 address of VLAN-interface 101 on the AC.
[Device-Tunnel0] destination 2002::1:1
[Device-Tunnel0] quit
# Configure a static route from the device through the tunnel interface to Group 1.
[Device] ip route-static 10.1.1.0 255.255.255.0 tunnel 0
Verifying the configuration
# Display tunnel interface information on the AC.
[AC] display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum transmission unit: 64000
Internet address: 10.1.2.1/24 (primary)
Tunnel source 2002::1:1, destination 2001::2:1
Tunnel TTL 255
Tunnel protocol/transport GRE/IPv6
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Display tunnel interface information on the device.
[Device] display interface tunnel 0
Tunnel0
Current state: UP
Line protocol state: UP
Description: Tunnel0 Interface
Bandwidth: 64kbps
Maximum transmission unit: 64000
Internet address: 10.1.2.2/24 (primary)
Tunnel source 2001::2:1, destination 2002::1:1
Tunnel TTL 255
Tunnel protocol/transport GRE/IPv6
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# From the device, ping the IP address of VLAN-interface 100 on the AC.
[Device] ping -a 10.1.3.1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1) from 10.1.3.1: 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=2.000 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=1.000 ms
--- Ping statistics for 10.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/1.000/2.000/0.632 ms
The output shows that the device can successfully ping the AC.
Troubleshooting GRE
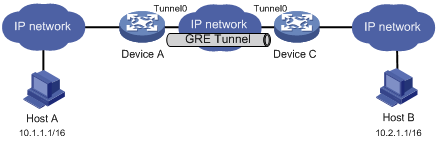
The key to configuring GRE is to keep the configuration consistent. Most faults can be located by using the debugging gre or debugging tunnel command. This section analyzes one type of fault for illustration, with the scenario shown in Figure 7.
Symptom
The interfaces at both ends of the tunnel are configured correctly and can ping each other, but Host A and Host B cannot ping each other.
Analysis
It might be because that Device A or Device C has no route to reach the peer network.
Solution
1. Execute the display ip routing-table command on Device A and Device C to view whether Device A has a route over tunnel 0 to 10.2.0.0/16 and whether Device C has a route over tunnel 0 to 10.1.0.0/16.
2. If such a route does not exist, execute the ip route-static command in system view to add the route. Take Device A as an example:
[DeviceA] ip route-static 10.2.0.0 255.255.0.0 tunnel 0
