- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-NAT configuration | 356.99 KB |
Contents
Feature and hardware compatibility
Command and hardware compatibility
Configuring outbound one-to-one static NAT
Configuring outbound net-to-net static NAT
Configuring inbound one-to-one static NAT
Configuring inbound net-to-net static NAT
Configuration restrictions and guidelines
Configuring outbound dynamic NAT
Configuring inbound dynamic NAT
Configuring load sharing NAT Server
Configuring ACL-based NAT Server
Enabling global mapping sharing for dynamic NAT444
Modifying the priority of a NAT rule
Modifying the priority of an outbound dynamic NAT rule
Modifying the priority of an inbound dynamic NAT rule
Modifying the priority of a one-to-one static inbound NAT rule
Modifying the priority of a one-to-one static outbound NAT rule
Modifying the priority of an ACL-based NAT server rule
Configuring NAT with DNS mapping
Configuring NAT session logging
Configuring NAT444 user logging
Configuring NAT444 alarm logging
Configuring port block usage threshold for dynamic NAT444
Enabling sending ICMP error messages for NAT failures
Displaying and maintaining NAT
Configuring NAT
Overview
Network Address Translation (NAT) translates an IP address in the IP packet header to another IP address. Typically, NAT is configured on gateways to enable private hosts to access external networks and external hosts to access private network resources such as a Web server.
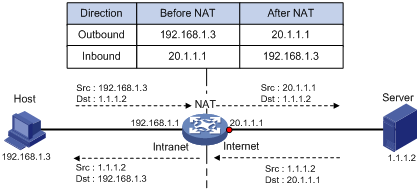
As shown in Figure 1:
1. Upon receiving a request from the host to the server, NAT translates the private source address 192.168.1.3 to the public address 20.1.1.1 and forwards the NATed packet. NAT adds a mapping for the two addresses to its NAT table.
2. Upon receiving a response from the server, NAT translates the destination public address to the private address, and forwards the packet to the host.
The NAT operation is transparent to the terminals. NAT hides the private network from the external users and shows that the IP address of the internal host is 20.1.1.1.
Terminology
The following describes NAT terminologies:
· NAT device—A device configured with NAT.
· NAT interface—An interface enabled with NAT.
· NAT entry—Stores the mapping between a private address and a public address. For more information, see "NAT entries."
· Easy IP—Uses the IP address of an interface as the public address. The IP address of the interface is obtained through DHCP or PPPoE.
NAT types
Traditional NAT
Traditional NAT applies to the interface connected to the public network. It translates the source IP addresses of outgoing packets and destination IP addresses of incoming packets.
Bidirectional NAT
NAT translates the source and destination IP addresses of incoming packets on the receiving interface and outgoing packets on the sending interface.
Bidirectional NAT is applied when source and destination addresses overlap.
Twice NAT
Twice NAT translates the destination IP address on the receiving interface, and the source IP address on the sending interface. The receiving and sending interfaces are both NAT interfaces.
Twice NAT allows internal networks with overlapping addresses to access each other.
NAT control
You can use ACLs to implement NAT control. The match criteria in the ACLs include the source IP address, source port number, destination IP address, destination port number, and transport layer protocol. Only packets permitted by an ACL are processed by NAT.
Compatibility information
Feature and hardware compatibility
|
Hardware series |
Model |
NAT compatibility |
|
WX1800H series |
WX1804H WX1810H WX1820H |
Yes |
|
WX2500H series |
WX2510H WX2540H WX2560H |
Yes |
|
WX3000H series |
WX3010H WX3010H-L WX3010H-X WX3024H WX3024H-L |
Yes: · WX3010H · WX3010H-X · WX3024H No: · WX3010H-L · WX3024H-L |
|
WX3500H series |
WX3508H WX3510H WX3520H WX3540H |
Yes |
|
WX5500E series |
WX5510E WX5540E |
Yes |
|
WX5500H series |
WX5540H WX5560H WX5580H |
Yes |
|
Access controller modules |
LSUM1WCME0 EWPXM1WCME0 LSQM1WCMX20 LSUM1WCMX20RT LSQM1WCMX40 LSUM1WCMX40RT EWPXM2WCMD0F EWPXM1MAC0F |
Yes |
Command and hardware compatibility
The WX1800H series, WX2500H series, and WX3000H series access controllers do not support the slot keyword or the slot-number argument.
NAT implementations
Static NAT
Static NAT creates a fixed mapping between a private address and a public address. Static NAT allows bidirectional connection initiation, both from and to the internal host. Static NAT applies to regular communications.
Dynamic NAT
Dynamic NAT uses an address pool to translate addresses. Dynamic NAT includes Not Port Address Translation (NO-PAT) and Port Address Translation (PAT) modes.
NO-PAT
NO-PAT translates a private address to a public address. The public address cannot be used by another internal host until it is released.
NO-PAT supports all IP packets.
PAT
PAT translates multiple private addresses to a single public address by mapping the private address and source port to the public address and a unique port. PAT supports TCP and UDP packets, and ICMP request packets.
Figure 2 PAT operation
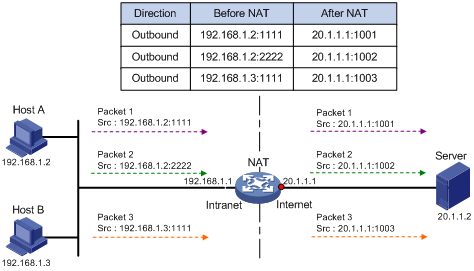
As shown in Figure 2, PAT translates the source IP addresses of the three packets to the same public address and translates their port numbers to different port numbers. Upon receiving a response, PAT translates the destination address and port number of the response, and forwards it to the target host.
PAT supports the following mappings:
· Endpoint-Independent Mapping (EIM)—Uses the same IP and port mapping (EIM entry) for packets from the same source IP and port to any destinations. EIM allows external hosts to initiate connections to the translated IP addresses and ports of internal hosts. It allows internal hosts behind different NAT gateways to access each other.
· Address and Port-Dependent Mapping (ADPM)—Uses different IP and port mappings for packets from the same source IP and port to different destination IP addresses and ports. APDM allows an external host to initiate connections to an internal host only under the condition that the internal host has previously accessed the external host. It is secure, but it does not allow internal hosts behind different NAT gateways to access each other.
NAT Server
The NAT Server feature maps a public address and port number to the private IP address and port number of an internal server. This feature allows servers in the private network to provide services for external users.
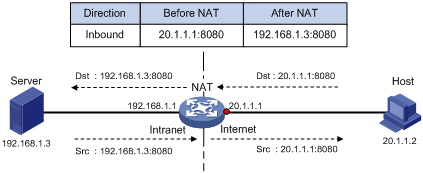
Figure 3 displays how NAT Server works:
1. Upon receiving a request from the host, NAT translates the public destination IP address and port number to the private IP address and port number of the internal server.
2. Upon receiving a response from the server, NAT translates the private source IP address and port number to the public IP address and port number.
NAT444
NAT444 provides carrier-grade NAT. It is a preferred solution for carriers to mitigate IPv4 address exhaustion. It introduces a second layer of NAT on the carrier side, with few changes on the customer side and the application server side.
NAT444 provides port block-based PAT translation. It maps multiple private IP addresses to one public IP address and uses a different port block for each private IP address. For example, the private IP address 10.1.1.1 of an internal host is mapped to the public IP address 202.1.1.1 and port block 10001 to 10256. When the internal host accesses public hosts, the source IP address 10.1.1.1 is translated to 202.1.1.1, and the source ports are translated to ports in the port block 10001 to 10256.
NAT444 includes static NAT444 and dynamic NAT444.
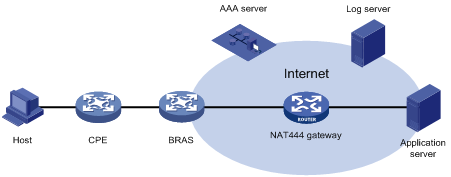
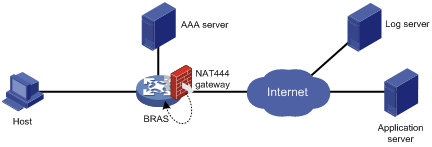
As shown in Figure 4, the NAT444 architecture includes the following entities:
· CPE—Provides NAT services on the customer side.
· BRAS—Provides Internet access services.
· NAT444 gateway—Provides carrier-grade NAT services.
· AAA server—Cooperates with BRAS to provide user authentication, authorization, and accounting services.
· Log server—Records user access logs and responds to queries for user access information.
The AAA server authenticates the internal users and starts accounting after users pass the authentication. The BRAS device assigns private IP addresses to authenticated users. When a user accesses the external network, the NAT444 gateway assigns the user a public IP address and port block, and sends the mapping to the log server. The next time the user accesses the external network, the NAT444 gateway assigns a new mapping if the former mapping ages out and sends the new mapping to the log server. The log server uses the mappings for user tracing.
Figure 4 NAT444 application diagram
Static NAT444
The NAT444 gateway computes a static NAT444 mapping before address translation. The mapping is between a private IP address and a public IP address with a port block.
The NAT444 gateway uses private IP addresses, public IP addresses, a port range, and a port block size to compute static mappings:
1. Divides the port range by the port block size to get the number of available port blocks for each public IP address.
This value is the base number for mapping.
2. Sorts the port blocks in ascending order of the start port number in each block.
3. Sorts the private IP addresses and the public IP addresses separately in ascending order.
4. Maps the first base number of private IP addresses to the first public IP address and its port blocks in ascending order.
For example, the number of available port blocks of each public IP address is m. The first m private IP addresses are mapped to the first public IP address and the m port blocks in ascending order. The next m private IP addresses are mapped to the second IP address and the m port blocks in ascending order. The other static NAT444 mappings are created by analogy.
Dynamic NAT444
Dynamic NAT444 works as follows:
1. Creates a mapping from the internal host's private IP address to a public IP address and a port block when the host initiates a connection to the public network.
2. Translates the private IP address to the public IP address, and the source ports to ports in the selected port block for subsequent connections from the private IP address.
3. Withdraws the port block and deletes the dynamic NAT444 mapping when all connections from the private IP address are disconnected.
Dynamic NAT444 uses ACLs to implement translation control. It processes only packets that match an ACL permit rule.
Dynamic NAT444 supports port block extending. If the ports in the port block for a private address are all occupied, dynamic NAT444 translates the source port to a port in an extended port block.
NAT444 gateway unified with BRAS device
NAT444 gateway and BRAS device unification is supported only for PPP users.
To unify the NAT444 gateway and BRAS device, specify the user address type in the ISP domain. Supported user address types include private IPv4 address and private-DS address.
As shown in Figure 5, the NAT444 gateway and BRAS device function as follows after the unification:
1. After a user of the specified address type passes authentication and obtains a private address, NAT444 immediately assigns a public IP address and a port block to the user.
2. NAT444 sends the NAT444 mapping to the BRAS.
3. The BRAS records the mapping and reports it to the AAA server.
Compared to the separation of BRAS and NAT444, the unification provides the following functions:
· If the NAT444 resources have been used up, the BRAS logs off the user, which ensures accurate accounting on the AAA server.
· The AAA server maintains one mapping for each online user until the user goes offline. This solution implements user tracing without requiring an extra log server.
Figure 5 NAT444 gateway unified with BRAS device
|
|
NOTE: If the NAT444 configuration changes, NAT444 mappings for online users also change. The change cannot be synchronized to the AAA server, affecting user tracing accuracy. H3C recommends that you log off the users immediately after you change the NAT444 configuration. When the users come online, NAT444 creates new mappings for them. |
NAT entries
NAT session entry
NAT creates a NAT session entry for a session and creates an address mapping for the first packet in the session.
A NAT session entry contains extended NAT information, such as interface and translation method. Subsequent packets of the session are translated by using this entry.
The session management module maintains the updating and aging of NAT session entries. For information about session management, see Security Configuration Guide.
EIM entry
An EIM entry maps a private address/port to a public address/port. The same EIM entry applies to subsequent connections originating from the same source IP and port.
An EIM entry ages out after all related NAT session entries age out.
NO-PAT entry
A NO-PAT entry maps a private address to a public address. The same mapping applies to subsequent connections originating from the same source IP.
A NO-PAT entry can also be created during the ALG process for NAT. For information about NAT with ALG, see "NAT with ALG."
A NO-PAT entry ages out after all related NAT session entries age out.
NAT444 entry
A NAT444 entry maps a private IP address to a public IP address and a port block.
NAT444 entries include static and dynamic NAT444 mappings. For information about these mappings, see "Static NAT444" and "Dynamic NAT444."
Using NAT with other features
NAT with DNS mapping
NAT with DNS mapping allows an internal host to access an internal server on the same private network by using the domain name of the internal server when the DNS server is on the public network.
NAT with DNS mapping must operate with the NAT Server feature.
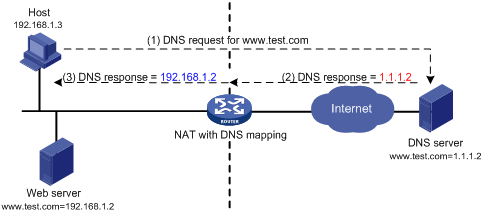
As shown in Figure 6, NAT with DNS mapping works as follows:
1. The host sends a DNS request containing the domain name of the internal Web server.
2. Upon receiving the DNS response, the NAT device performs a DNS mapping lookup by using the domain name in the response. A DNS mapping for NAT maps the domain name to the public IP address, public port number, and the protocol type for the internal server.
3. If a match is found, the NAT continues to compare the public address, public port number, and the protocol type with the NAT Server configuration. The NAT Server configuration maps the public IP address and port number to the private IP address and port number for the internal server.
4. If a match is found, NAT translates the public IP address in the response into the private IP address of the Web server.
5. The internal host receives the DNS response, and obtains the private IP address of the Web server.
DNS mapping can also be used by DNS ALG. The DNS reply from the external DNS server contains only the domain name and public IP address of the internal server in the payload. The NAT interface might have multiple internal servers configured with the same public IP address but different private IP addresses. DNS ALG might find an incorrect internal server by using only the public IP address. If a DNS mapping is configured, DNS ALG can obtain the public IP address, public port number, and protocol type of the internal server by using the domain name. Then it can find the correct internal server by using the public IP address, public port number, and protocol type of the internal server.
NAT with ALG
NAT with ALG translates address or port information in the application layer payloads to ensure connection establishment.
For example, an FTP application includes a data connection and a control connection. The IP address and port number for the data connection depend on the payload information of the control connection. This requires NAT with ALG to translate the address and port information for data connection establishment.
NAT configuration task list
|
Tasks at a glance |
Remarks |
|
Perform one or more of the following tasks: |
If you perform all the tasks on an interface, the NAT rules are sorted in the following order: · NAT Server. · Static NAT. · Static NAT444. · Dynamic NAT and dynamic NAT444. |
|
(Optional.) Modifying the priority of a NAT rule |
N/A |
|
(Optional.) Configuring NAT with DNS mapping |
N/A |
|
(Optional.) Configuring NAT with ALG |
N/A |
|
(Optional.) Configuring NAT logging |
N/A |
|
(Optional.) Enabling sending ICMP error messages for NAT failures |
N/A |
Configuring static NAT
Static NAT includes one-to-one static NAT and net-to-net static NAT for outbound and inbound translation. Do not configure inbound static NAT alone. Typically, inbound static NAT functions with outbound dynamic NAT, NAT Server, or outbound static NAT to implement bidirectional NAT.
Configuration prerequisites
Perform the following tasks before configuring static NAT:
· Configure an ACL to identify the IP addresses to be translated. The match criteria include the source IP address, source port number, destination IP address, destination port number, and transport layer protocol. For more information about ACLs, see ACL and QoS Configuration Guide.
· Manually add a route for inbound static NAT. Use local-ip or local-network as the destination address, and use global-ip, an address in global-network, or the next hop directly connected to the output interface as the next hop.
Configuring outbound one-to-one static NAT
For address translation from a private IP address to a public IP address, configure outbound one-to-one static NAT on the interface connected to the external network.
· When the source IP address of a packet from the private network matches the local-ip, the source IP address is translated into the global-ip.
· When the destination IP address of a packet from the public network matches the global-ip, the destination IP address is translated into the local-ip.
To configure outbound one-to-one static NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a one-to-one mapping for outbound static NAT. |
nat static outbound local-ip [ acl { acl-number | name acl-name } [ reversible ] ] global-ip [ rule rule-name ] [ priority priority ] [ disable ] |
By default, no mappings exist. If you specify the acl keyword, NAT processes only packets matching the permit rule in the ACL. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable static NAT on the interface. |
nat static enable |
By default, static NAT is disabled. |
Configuring outbound net-to-net static NAT
For address translation from a private network to a public network, configure outbound net-to-net static NAT on the interface connected to the external network.
· When the source IP address of a packet from the private network matches the private address range, the source IP address is translated into a public address in the public address range.
· When the destination IP address of a packet from the public network matches the public address range, the destination IP address is translated into a private address in the private address range.
To configure outbound net-to-net static NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a net-to-net mapping for outbound static NAT. |
nat static outbound net-to-net local-start-address local-end-address [ acl { acl-number | name acl-name } [ reversible ] ] global global-network { mask-length | mask } [ rule rule-name ] [ priority priority ] [ disable ] |
By default, no mappings exist. If you specify the acl keyword, NAT processes only packets permitted by the ACL. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable static NAT on the interface. |
nat static enable |
By default, static NAT is disabled. |
Configuring inbound one-to-one static NAT
For address translation from a public IP address to a private IP address, configure inbound one-to-one static NAT.
· When the source IP address of a packet from the public network to the private network matches the global-ip, the source IP address is translated into the local-ip.
· When the destination IP address of a packet from the private network to the public network matches the local-ip, the destination IP address is translated into the global-ip.
To configure inbound one-to-one static NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a one-to-one mapping for inbound static NAT. |
nat static inbound global-ip [ acl { acl-number | name acl-name } [ reversible ] ] local-ip [ rule rule-name ] [ priority priority ] [ disable ] |
By default, no mappings exist. If you specify the acl keyword, NAT processes only packets permitted by the ACL. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable static NAT on the interface. |
nat static enable |
By default, static NAT is disabled. |
Configuring inbound net-to-net static NAT
For address translation from a public network to a private network, configure inbound net-to-net static NAT.
· When the source IP address of a packet from the public network matches the public address range, the source IP address is translated into a private address in the private address range.
· When the destination IP address of a packet from the private network matches the private address range, the destination IP address is translated into a public address in the public address range.
To configure inbound net-to-net static NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a net-to-net mapping for inbound static NAT. |
nat static inbound net-to-net global-start-address global-end-address [ acl { acl-number | name acl-name } [ reversible ] ] local local-network { mask-length | mask } [ rule rule-name ] [ priority priority ] [ disable ] |
By default, no mappings exist. If you specify the acl keyword, NAT processes only packets permitted by the ACL. |
|
3. Enter interface view. |
interface interface-type interface-number |
N/A |
|
4. Enable static NAT on the interface. |
nat static enable |
By default, static NAT is disabled. |
Configuring dynamic NAT
Dynamic NAT translates a group of private IP addresses into a smaller number of public addresses. You can specify an address group (or the IP address of an interface) and an ACL to implement dynamic NAT.
Configuration restrictions and guidelines
When you configure dynamic NAT, follow these restrictions and guidelines:
· You can configure multiple inbound or outbound dynamic NAT rules.
· A NAT rule with an ACL takes precedence over a rule without any ACL.
· If two ACL-based dynamic NAT rules are configured, the rule with the higher ACL number has higher priority.
Configuration prerequisites
Perform the following tasks before configuring dynamic NAT:
· Configure an ACL to identify the IP addresses to be translated. The match criteria include the source IP address, source port number, destination IP address, destination port number, and transport layer protocol. For more information about ACLs, see ACL and QoS Configuration Guide.
· Determine whether to enable the Easy IP feature. If you use the IP address of an interface as the public address, you are configuring Easy IP.
· Determine a public IP address pool for address translation.
· Determine whether to translate port numbers. Use NO-PAT to translate only IP addresses and PAT to translate both IP addresses and port numbers.
Configuring outbound dynamic NAT
To translate private IP addresses into public IP addresses, configure outbound dynamic NAT on the interface connected to the external network.
The source IP addresses of the outgoing packets that match the ACL permit rule are translated into IP addresses in the address group.
The reversible keyword enables the device to perform the following operations:
· Compare the destination IP address in the first packet from the public network with existing NO-PAT entries.
· Translate the destination address into the private address in a matching NO-PAT entry.
To configure outbound dynamic NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure an address group and enter its view. |
nat address-group group-number [ name group-name ] |
By default, no address group exists. |
|
3. Add an address range to the address group. |
address start-address end-address |
By default, no address range exists. You can add multiple address ranges to an address group. The address ranges must not overlap. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Configure outbound dynamic NAT. |
· Configure NO-PAT: · Configure PAT: |
By default, outbound dynamic NAT is not configured. You can configure multiple outbound dynamic NAT rules on an interface. |
|
7. Return to system view. |
quit |
N/A |
|
8. (Optional.) Configure a PAT mapping mode. |
nat mapping-behavior endpoint-independent [ acl { acl-number | name acl-name } ] |
The default mapping mode is Address and Port-Dependent Mapping. This command takes effect only on outbound dynamic NAT for PAT. |
Configuring inbound dynamic NAT
Inbound dynamic NAT enables translation from public IP addresses to private IP addresses. Do not configure it alone. Typically, inbound dynamic NAT functions with outbound dynamic NAT, NAT Server, or outbound static NAT to implement bidirectional NAT.
The source IP address of a received packet that is permitted by the ACL is translated into a public address in the address group.
The add-route keyword enables the device to automatically add a route destined for the private address when an inbound dynamic NAT rule is matched. The output interface is the NAT interface, and the next hop is the source address before translation. If you do not specify this keyword, you must manually add the route. H3C recommends that you manually create a route because it takes time to automatically add routes.
The reversible keyword enables the device to perform the following operations:
· Compare the destination IP address in the first packet from the private network with existing NO-PAT entries.
· Translate the destination address into the public address in a matching NO-PAT entry.
Inbound dynamic NAT does not support Easy IP.
To configure inbound dynamic NAT:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure an address group and enter its view. |
nat address-group group-number [ name group-name ] |
By default, no address group exists. |
|
3. Add an address range to the address group. |
address start-address end-address |
By default, no address range exists. You can add multiple address ranges to an address group. The address ranges must not overlap. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Configure inbound dynamic NAT. |
nat inbound { acl-number | name acl-name } address-group { group-number | name group-name } [ no-pat [ reversible ] [ add-route ] ] [ rule rule-name ] [ priority priority ] [ disable ] [ description text ] |
By default, inbound dynamic NAT is not configured. You can configure multiple inbound dynamic NAT rules on an interface. |
Configuring NAT Server
To configure NAT Server, map a public IP address and port number to the private IP address and port number of an internal server on the interface connected to the external network.
If you specify the acl keyword for the common NAT Server or load sharing NAT Server configuration, only packets matching the ACL permit rule are translated. The match criteria include the source IP address, source port number, destination IP address, destination port number, and transport layer protocol.
Configuring common NAT Server
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure one or more common NAT Server mappings. |
· A single public address with a single or no public port: · A single public address with consecutive public ports: · Consecutive public addresses with a single or no public port: · Consecutive public addresses with a single public port: |
By default, no NAT Server mapping exists. You can configure multiple NAT Server mappings on an interface. |
Configuring load sharing NAT Server
You can add multiple internal servers to an internal server group so that these servers provide the same service for external hosts. The NAT device chooses one internal server based on the weight and number of connections of the servers to respond to a request from an external host to the public address of the internal server group.
To configure load sharing NAT Server:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a NAT Server group and enter its view. |
nat server-group group-number |
By default, no NAT Server group exists. |
|
3. Add an internal server into the group. |
inside ip inside-ip port port-number [ weight weight-value ] |
By default, no internal server is in the group. You can add multiple internal servers to a group. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter interface view. |
interface interface-type interface-number |
N/A |
|
6. Configure load sharing NAT Server. |
nat server protocol pro-type global { { global-address | current-interface | interface interface-type interface-number } { global-port | global-port1 global-port2 } | global-address1 global-address2 global-port } inside server-group group-number [ acl { acl-number | name acl-name } ] [ rule rule-name ] [ disable ] |
By default, no load sharing NAT Server mapping exists. You can configure multiple load sharing NAT Server mappings on an interface. |
Configuring ACL-based NAT Server
ACL-based NAT Server is an extension of common NAT Server. Common NAT Server maps the private IP address of the internal server to a single public IP address. ACL-based NAT Server maps the private IP address of the internal server to a set of public IP addresses defined by an ACL. If the destination address of a packet matches a permit rule, the destination address is translated into the private IP address of the internal server.
To configure ACL-based NAT Server:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure ACL-based NAT Server. |
nat server global { global-acl-number | name global-acl-name } inside local-address [ local-port ] [ rule rule-name ] [ priority priority ] [ disable ] |
By default, no ACL-based NAT Server mapping exists. You can configure multiple NAT Server mappings on an interface. |
Configuring NAT444
NAT444 provides outbound address translation, and it is configured on the interface connected to the public network.
Configuring static NAT444
Static NAT444 is applicable when the private IP addresses are fixed.
To configure static NAT444:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a NAT port block group, and enter its view. |
nat port-block-group group-number |
By default, no port block group exists. |
|
3. Add a private IP address range to the port block group. |
local-ip-address start-address end-address |
By default, no private IP address range exists in the port block group. You can add multiple private IP address ranges to one port block group, but they cannot overlap. |
|
4. Add a public IP address range to the port block group. |
global-ip-pool start-address end-address |
By default, no public IP address range exists in the port block group. You can add multiple public IP address ranges to one port block group, but they cannot overlap. |
|
5. Configure the port range for the public IP addresses. |
port-range start-port-number end-port-number |
By default, the port range is 1 to 65535. |
|
6. Set the port block size. |
block-size block-size |
By default, the port block size is 256. |
|
7. Return to system view. |
quit |
N/A |
|
8. Enter interface view. |
interface interface-type interface-number |
N/A |
|
9. Apply the port block group to the outbound direction of the interface. |
nat outbound port-block-group group-number [ rule rule-name ] |
By default, no port block group is applied to the interface. You can apply multiple port block groups to one interface. |
|
10. Return to system view. |
quit |
N/A |
|
11. (Optional.) Configure a PAT mapping mode. |
nat mapping-behavior endpoint-independent [ acl { acl-number | name acl-name } ] |
The default mapping mode is Address and Port-Dependent Mapping. |
Configuring dynamic NAT444
Dynamic NAT444 is applicable when the private IP addresses are not fixed.
To configure dynamic NAT444:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a NAT address group, and enter its view. |
nat address-group group-number [ name group-name ] |
By default, no NAT address group exists. |
|
3. Add a public IP address range to the NAT address group. |
address start-address end-address |
By default, no public IP address range exists in the NAT address group. You can add multiple public IP address ranges to an address group, but they cannot overlap. |
|
4. Configure the port range for the public IP addresses. |
port-range start-port-number end-port-number |
By default, the port range is 1 to 65535. The configuration takes effect only on PAT translation mode. |
|
5. Configure port block parameters. |
port-block block-size block-size [ extended-block-number extended-block-number ] |
By default, no port block parameter exists. The configuration takes effect only on PAT translation mode. |
|
6. Return to system view. |
quit |
N/A |
|
7. Enter interface view. |
interface interface-type interface-number |
N/A |
|
8. Configure PAT for outbound dynamic NAT. |
nat outbound [ acl-number | name acl-name ] [ address-group group-number | name group-name } ] [ port-preserved ] [ rule rule-name ] [ priority priority ] |
By default, outbound dynamic NAT is not configured. The port-preserved keyword does not take effect on dynamic NAT444. |
|
9. Return to system view. |
quit |
N/A |
|
10. (Optional.) Configure a PAT mapping mode. |
nat mapping-behavior endpoint-independent [ acl { acl-number | name acl-name } ] |
The default mapping mode is Address and Port-Dependent Mapping. |
Enabling global mapping sharing for dynamic NAT444
When multiple interfaces have dynamic NAT444 configured, the interfaces might create different NAT444 mappings for packets from the same IP address. You can perform this task to configure the interfaces to share the same NAT444 mapping for translating packets from the same IP address.
To enable global mapping sharing for dynamic NAT444:
|
Step |
Command |
Remarks |
|
11. Enter system view. |
system-view |
N/A |
|
12. Enable global mapping sharing for dynamic NAT444. |
nat port-block global-share enable |
By default, global mapping sharing is disabled for dynamic NAT444. |
Modifying the priority of a NAT rule
Modifying the priority of an outbound dynamic NAT rule
To modify the priority of an outbound dynamic NAT rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Modify the priority of an outbound dynamic NAT rule. |
nat outbound rule move nat-rule-name1 { after | before } nat-rule-name2 |
This command takes effect only on an outbound dynamic NAT rule that has a name. |
Modifying the priority of an inbound dynamic NAT rule
To modify the priority of an inbound dynamic NAT rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Modify the priority of an inbound dynamic NAT rule. |
nat inbound rule move nat-rule-name1 { after | before } nat-rule-name2 |
This command takes effect only on an inbound dynamic NAT rule that has a name. |
Modifying the priority of a one-to-one static inbound NAT rule
To modify the priority of a one-to-one static inbound NAT rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Modify the priority of a one-to-one static inbound NAT rule. |
nat static inbound rule move nat-rule-name1 { after | before } nat-rule-name2 |
This command takes effect only on a one-to-one static inbound NAT rule that has a name. |
Modifying the priority of a one-to-one static outbound NAT rule
To modify the priority of a one-to-one static outbound NAT rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Modify the priority of a one-to-one static outbound NAT rule. |
nat static outbound rule move nat-rule-name1 { after | before } nat-rule-name2 |
This command takes effect only on a one-to-one static outbound NAT rule that has a name. |
Modifying the priority of an ACL-based NAT server rule
To modify the priority of an ACL-based NAT server rule:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Modify the priority of an ACL-based NAT server rule. |
nat server rule move nat-rule-name1 { after | before } nat-rule-name2 |
This command takes effect only on an ACL-based NAT server rule that has a name. |
Configuring NAT with DNS mapping
NAT with DNS mapping must operate together with NAT Server and NAT with ALG.
To configure NAT with DNS mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a DNS mapping for NAT. |
nat dns-map domain domain-name protocol pro-type { interface interface-type interface-number | ip global-ip } port global-port |
By default, no DNS mapping for NAT exists. You can configure multiple DNS mappings for NAT. |
Configuring NAT with ALG
Configure NAT with ALG for a protocol to translate the IP addresses and port numbers in the payloads for application layer packets.
To configure NAT with ALG:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure NAT with ALG for a protocol or all protocols. |
nat alg { all | dns | ftp | h323 | icmp-error | ils | mgcp | nbt | pptp | rsh | rtsp | sccp | sip | sqlnet | tftp | xdmcp } |
By default, NAT with ALG is enabled for DNS, FTP, ICMP error messages, RTSP, and PPTP, and is disabled for the other supported protocols. |
Configuring NAT logging
Configuring NAT session logging
NAT session logging records NAT session information, including translation information and access information.
A NAT device generates NAT session logs for the following events:
· NAT session establishment.
· NAT session removal. This event occurs when you add a configuration with a higher priority, remove a configuration, change ACLs, when a NAT session ages out, or when you manually delete a NAT session.
· Active NAT session logging.
To enable NAT session logging:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enable NAT logging. |
nat log enable [ acl { acl-number | name acl-name } ] |
By default, NAT logging is disabled. |
|
|
3. Enable NAT session logging. |
· For NAT session establishment events: · For NAT session removal events: · For active NAT flows: |
By default, NAT session logging is disabled. |
|
Configuring NAT444 user logging
NAT444 user logs are used for user tracing. The NAT444 gateway generates a user log whenever it assigns or withdraws a port block. The log includes the private IP address, public IP address, and port block. You can use the public IP address and port numbers to locate the user's private IP address from the user logs.
A NAT444 gateway generates NAT user logs when one of the following events occurs:
· A port block is assigned.
For NAT444 with static mappings, the NAT444 gateway generates a user log when it translates the first connection from a private IP address.
For NAT444 with dynamic mappings, the NAT444 gateway generates a user log when it assigns or extends a port block for a private IP address.
· A port block is withdrawn.
For NAT444 with static mappings, the NAT444 gateway generates a user log when all connections from a private IP address are disconnected.
For NAT444 with dynamic mappings, the NAT444 gateway generates a user log when all the following conditions are met:
¡ All connections from a private IP address are disconnected.
¡ The port blocks (including the extended ones) assigned to the private IP address are withdrawn.
¡ The corresponding mapping entry is deleted.
Before configuring NAT444 user logging, you must configure the custom NAT444 log generation and outputting features. For more information, see Network Management and Monitoring Configuration Guide.
To configure NAT444 user logging:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enable NAT logging. |
nat log enable [ acl { acl-number | name acl-name } ] |
By default, NAT logging is disabled. The acl keyword does not take effect on NAT444 user logging. |
|
|
3. Enable NAT444 user logging. |
· For port block assignment: · For port block withdrawal: |
By default, NAT444 user logging is disabled. You can enable logging for both port block assignment and withdrawal. |
|
Configuring NAT444 alarm logging
If the public IP addresses, port blocks, or ports in selected port blocks (including extended ones) are all occupied, the NAT444 gateway cannot perform address translation and packets will be dropped. To monitor the usage of public IP addresses and port block resources, you can configure NAT444 alarm logging.
A NAT444 gateway generates alarm logs when one of the following occurs:
· The ports in the selected port block of a static NAT444 mapping are all occupied.
· The ports in the selected port blocks (including extended ones) of a dynamic NAT444 mapping are all occupied.
· The public IP addresses and port blocks for dynamic NAT444 mappings are all assigned.
Before configuring NAT444 alarm logging, you must configure the custom NAT444 log generation and outputting features. For more information, see Network Management and Monitoring Configuration Guide.
To configure NAT444 alarm logging:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
2. Enable NAT logging. |
nat log enable [ acl { acl-number | name acl-name } ] |
By default, NAT logging is disabled. The acl keyword does not take effect on NAT444 alarm logging. |
|
|
3. Enable NAT444 alarm logging. |
nat log alarm |
By default, NAT444 alarm logging is disabled. |
|
Configuring port block usage threshold for dynamic NAT444
The system generates alarm logs if the port block usage exceeds the threshold.
To configure the port block usage threshold for dynamic NAT444:
|
Step |
Command |
Remarks |
|
4. Enter system view. |
system-view |
N/A |
|
5. Configure the port block usage threshold for dynamic NAT444. |
nat log port-block usage threshold threshold-value |
The default threshold is 90%. |
Enabling sending ICMP error messages for NAT failures
Disabling sending ICMP error messages for NAT failures reduces useless packets, saves bandwidth, and avoids exposing the firewall IP address to the public network.
This feature is required for traceroute.
To enable sending ICMP error messages for NAT failures:
|
Step |
Command |
Remarks |
|
|
1. Enter system view. |
system-view |
N/A |
|
|
nat icmp-error reply |
By default, no ICMP error messages are sent for NAT failures. |
||
Displaying and maintaining NAT
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the NAT with ALG status for all supported protocols. |
display nat alg |
|
Display all NAT configuration information. |
display nat all |
|
Display NAT address group information. |
display nat address-group [ group-number ] |
|
Display NAT with DNS mapping configuration. |
display nat dns-map |
|
Display information about NAT EIM entries. |
display nat eim [ slot slot-number ] |
|
Display information about inbound dynamic NAT. |
display nat inbound |
|
Display NAT logging configuration. |
display nat log |
|
Display information about NAT NO-PAT entries. |
display nat no-pat [ slot slot-number ] |
|
Display information about outbound dynamic NAT. |
display nat outbound |
|
Display NAT Server configuration. |
display nat server |
|
Display internal server group configuration. |
display nat server-group [ group-number ] |
|
Display sessions that have been NATed. |
display nat session [ { source-ip source-ip | destination-ip destination-ip } * ] [ slot slot-number ] [ verbose ] |
|
Display static NAT mappings. |
display nat static |
|
Display NAT statistics. |
display nat statistics [ summary ] [ slot slot-number ] |
|
Display information about port block group application for NAT444. |
display nat outbound port-block-group |
|
Display information about NAT port block groups. |
display nat port-block-group [ group-number ] |
|
Display NAT444 mappings. |
display nat port-block { dynamic | static } [ slot slot-number ] |
|
Display the port block usage for dynamic NAT444 address groups |
display nat port-block-usage [ address-group group-id ] [ slot slot-number ] |
|
Clear NAT sessions. |
reset nat session [ slot slot-number ] |
NAT configuration examples
Outbound one-to-one static NAT configuration example
Network requirements
Configure static NAT to allow the client at 10.110.10.8/24 to access the Internet.
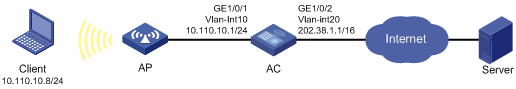
Configuration procedure
# Assign IP addresses to interfaces. (Details not shown.)
# Configure a one-to-one static NAT mapping between the private address 10.110.10.8 and the public address 202.38.1.100.
<AC> system-view
[AC] nat static outbound 10.110.10.8 202.38.1.100
# Enable static NAT on VLAN-interface 20.
[AC] interface vlan-interface 20
[AC-Vlan-interface20] nat static enable
Verifying the configuration
# Verify that the client at 10.110.10.8/24 can access the server on the Internet. (Details not shown.)
# Display static NAT configuration.
[AC] display nat static
Static NAT mappings:
Totally 1 outbound static NAT mappings.
IP-to-IP:
Local IP : 10.110.10.8
Global IP : 202.38.1.100
Config status: Active
Interfaces enabled with static NAT:
Totally 1 interfaces enabled with static NAT.
Interface: Vlan-interface20
Config status: Active
# Display NAT session information.
[AC] display nat session verbose
Initiator:
Source IP/port: 10.110.10.8/42496
Destination IP/port: 202.38.1.111/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: Vlan-interface10
Responder:
Source IP/port: 202.38.1.111/42496
Destination IP/port: 202.38.1.100/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: Vlan-interface20
State: ICMP_REPLY
Application: INVALID
Start time: 2012-08-16 09:30:49 TTL: 27s
Initiator->Responder: 5 packets 420 bytes
Responder->Initiator: 5 packets 420 bytes
Total sessions found: 1
Outbound dynamic NAT configuration example
Network requirements
As shown in Figure 8, a company has a private address 192.168.0.0/16 and two public IP addresses 202.38.1.2 and 202.38.1.3. Configure outbound dynamic NAT to allow only internal users on subnet 192.168.1.0/24 to access the Internet.
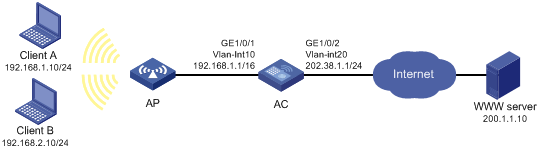
Configuration procedure
# Assign IP addresses to interfaces. (Details not shown.)
# Configure address group 0, and add an address range from 202.38.1.2 to 202.38.1.3 to the group.
<AC> system-view
[AC] nat address-group 0
[AC-address-group-0] address 202.38.1.2 202.38.1.3
[AC-address-group-0] quit
# Configure ACL 2000, and create a rule to permit packets only from subnet 192.168.1.0/24 to pass through.
[AC] acl basic 2000
[AC-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255
[AC-acl-ipv4-basic-2000] quit
# Enable outbound dynamic PAT on interface VLAN-interface 20. The source IP addresses of the packets permitted by the ACL rule is translated into the addresses in address group 0.
[AC] interface vlan-interface 20
[AC-Vlan-interface20] nat outbound 2000 address-group 0
Verifying the configuration
# Verify that Client A can access the WWW server, but Client B cannot. (Details not shown.)
# Display all NAT configuration and statistics.
[AC] display nat all
NAT address group information:
Totally 1 NAT address groups.
Address group 0:
Port range: 1-65535
Address information:
Start address End address
202.38.1.2 202.38.1.3
NAT outbound information:
Totally 1 NAT outbound rules.
Interface: Vlan-interface20
ACL: 2000
Address group: 0
Port-preserved: N NO-PAT: N Reversible: N
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Disabled
H323 : Disabled
ICMP-ERROR : Enabled
ILS : Disabled
MGCP : Disabled
NBT : Disabled
PPTP : Enabled
RTSP : Enabled
RSH : Disabled
SCCP : Disabled
SIP : Disabled
SQLNET : Disabled
TFTP : Disabled
XDMCP : Disabled
# Display NAT session information generated when Client A accesses the WWW server.
[AC] display nat session verbose
Initiator:
Source IP/port: 192.168.1.10/52992
Destination IP/port: 200.1.1.10/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: Vlan-interface10
Responder:
Source IP/port: 200.1.1.10/4
Destination IP/port: 202.38.1.3/0
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: ICMP(1)
Inbound interface: Vlan-interface20
State: ICMP_REPLY
Application: INVALID
Start time: 2012-08-15 14:53:29 TTL: 12s
Initiator->Responder: 1 packets 84 bytes
Responder->Initiator: 1 packets 84 bytes
