- Table of Contents
-
- 09-ACL and QoS Configuration Examples
- 00-S12500_ACL_Configuration_Examples
- 01-S12500_Packet_Filtering_Configuration_Examples
- 02-S12500_Priority_Mapping_and_Priority_Marking_Configuration_Examples
- 03-S12500_Traffic_Policing_Configuration_Examples
- 04-S12500_GTS_Configuration_Examples
- 05-S12500_Queue_Scheduling_Configuration_Examples
- 06-S12500_Control_Plane-Based_QoS_Policy_Configuration_Examples
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 00-S12500_ACL_Configuration_Examples | 143.04 KB |
Contents
Example: Configuring an Ethernet Frame Header ACL
Configuration restrictions and guidelines
Example: Configuring an IPv4 advanced ACL
Example: Configuring an IPv6 advanced ACL
Configuration restrictions and guidelines
Example: Configuring a usesr-defined ACL
Configuration restrictions and guidelines
Introduction
This document provides access control list (ACL) configuration examples.
An ACL is a set of rules for identifying traffic based on matching criteria such as source IP address, destination IP address, and port number. When a packet matches an ACL rule, the device performs the predefined action such as dropping, forwarding, and priority marking.
Prerequisites
The configuration examples in this document were created and verified in a lab environment, and all the devices started with the factory default configuration. When you are working in a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of H3C ACL.
Example: Configuring an Ethernet Frame Header ACL
Network requirements
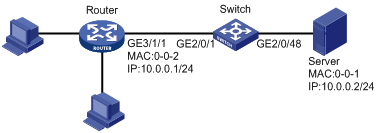
As shown in Figure 1, configure an Ethernet frame header ACL on interface GigabitEthernet 2/0/1 to deny the hosts' access to the Server from 12:00 to 18:00 on the working days.
Software version used
This configuration example was created and verified on S12500-CMW520-R1825P01.
Configuration restrictions and guidelines
An EB/EC2 card refers to the interface cards prefixed with EB/EC2. An Ethernet frame header ACL on an EB/EC2 card can take effect on IPv4 packets only when the EB/EC2 card is in advanced ACL hardware mode. Check whether an EB/EC2 card is used on GigabitEthernet 2/0/1:
· If an EB/EC2 card is used, use the display acl mode command to display the ACL hardware mode. If the card is in basic ACL hardware mode, use the acl mode advanced command to change the mode to the advanced mode. By default, an EB/EC2 card is in advanced ACL hardware mode.
· If the card is not an EB/EC2 card, no ACL hardware mode configuration is needed. The card supports Ethernet frame header ACLs by default.
In example, an EB/EC2 card is in slot 2 that connects to GigabitEthernet 2/0/1, and the card is in advanced ACL mode.
Configuration procedures
# Create time range time_1.
<Switch> system-view
[Switch] time-range time_1 12:00 to 18:00 working-day
# Configure Ethernet frame header ACL 4000 to identify the target packets and reference the time range time_1.
[Switch] acl number 4000
[Switch-acl-ethernetframe-4000] rule permit source-mac 0000-0000-0002 ffff-ffff-ffff dest-mac 0000-0000-0001 ffff-ffff-ffff type 0800 ffff time-range time_1
[Switch-acl-ethernetframe-4000] quit
# Create a traffic class named c_deny, and configure ACL 4000 as the match criteria.
[Switch] traffic classifier c_deny
[Switch-classifier-c_deny] if-match acl 4000
[Switch-classifier-c_deny] quit
# Create a traffic behavior named b_deny, and configure the traffic filtering action as deny for the behavior.
[Switch] traffic behavior b_deny
[Switch-behavior-b_deny] filter deny
[Switch-behavior-b_deny] quit
# Create a QoS policy named Q_deny, and associate traffic class c_deny with the behavior b_deny in the policy.
[Switch] qos policy Q_deny
[Switch-qospolicy-Q_deny] classifier c_deny behavior b_deny
[Switch-qospolicy-Q_deny] quit
# Apply QoS policy Q_deny in the inbound direction of interface GigabitEthernet 2/0/1.
[Switch] interface GigabitEthernet 2/0/1
[Switch-GigabitEthernet2/0/1] undo shutdown
[Switch-GigabitEthernet2/0/1] qos apply policy Q_deny inbound
[Switch-GigabitEthernet2/0/1] quit
Verifying the configuration
# Display the QoS configuration and operation information on GigabitEthernet 2/0/1.
[Switch] display qos policy interface GigabitEthernet 2/0/1
Interface: GigabitEthernet2/0/1
Direction: Inbound
Policy: Q_deny
Classifier: c_deny
Operator: AND
Rule(s) : If-match acl 4000
Behavior: b_deny
Filter Enable: deny
After the configuration, from 12:00 to 18:00 on the working days the Server does not receive any IPv4 packets with the source MAC address 0-0-2 and destination MAC address 0-0-1.
Configuration files
#
time-range time_1 12:00 to 18:00 working-day
#
acl number 4000
rule 0 permit type 0800 ffff source-mac 0000-0000-0002 ffff-ffff-ffff dest-mac 0000-0000-0001 ffff-ffff-ffff time-range time_1
#
vlan 1
#
traffic classifier c_deny operator and
if-match acl 4000
#
traffic behavior b_deny
filter deny
#
qos policy Q_deny
classifier c_deny behavior b_deny
#
interface GigabitEthernet2/0/1
port link-mode bridge
qos apply policy Q_deny inbound
#
Example: Configuring an IPv4 advanced ACL
Network requirements
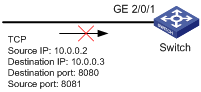
As shown in Figure 2, configure an IPv4 advanced ACL for QoS on interface GigabitEthernet 2/0/1 to filter incoming TCP packets with the source IP address 10.0.0.2, source port 8081, destination IP address 10.0.0.3, and destination port 8080.
Software version used
This configuration example was created and verified on S12500-CMW520-R1825P01.
Configuration procedures
# Configure advanced IPv4 ACL 3000.
<Switch> system-view
[Switch] acl number 3000
[Switch-acl-adv-3000] rule permit tcp destination-port eq 8080 source-port eq 8081 source 10.0.0.2 0 destination 10.0.0.3 0
[Switch-acl-adv-3000] quit
# Create a traffic class named c_deny, and configure ACL 3000 as the match criteria.
[Switch] traffic classifier c_deny
[Switch-classifier-c_deny] if-match acl 3000
[Switch-classifier-c_deny] quit
# Create a traffic behavior named b_deny, and configure the traffic filtering action as deny for the behavior.
[Switch] traffic behavior b_deny
[Switch-behavior-b_deny] filter deny
[Switch-behavior-b_deny] quit
# Create a QoS policy named Q_deny, and associate traffic class c_deny with the behavior b_deny in QoS policy Q_deny.
[Switch] qos policy Q_deny
[Switch-qospolicy-Q_deny] classifier c_deny behavior b_deny
[Switch-qospolicy-Q_deny] quit
# Apply the QoS policy Q_deny to the inbound direction of interface GigabitEthernet 2/0/1.
[Switch] interface GigabitEthernet 2/0/1
[Switch-GigabitEthernet2/0/1] qos apply policy Q_deny inbound
[Switch-GigabitEthernet2/0/1] undo shutdown
[Switch-GigabitEthernet2/0/1] quit
Verifying the configuration
# Display the QoS configuration and operation information on GigabitEthernet 2/0/1.
[Switch] display qos policy interface GigabitEthernet 2/0/1
Interface: GigabitEthernet2/0/1
Direction: Inbound
Policy: Q_deny
Classifier: c_deny
Operator: AND
Rule(s) : If-match acl 3000
Behavior: b_deny
Filter Enable: deny
After the configuration, the TCP packets that match the ACL in the inbound direction of GigabitEthernet 2/0/1 are denied and the other packets are allowed to pass through.
Configuration files
#
acl number 3000
rule 0 permit tcp source 10.0.0.2 0 source-port eq 8081 destination 10.0.0.3 0 destination-port eq 8080
#
vlan 1
#
traffic classifier c_deny operator and
if-match acl 3000
#
traffic behavior b_deny
filter deny
#
qos policy Q_deny
classifier c_deny behavior b_deny
#
interface GigabitEthernet2/0/1
port link-mode bridge
qos apply policy Q_deny inbound
#
Example: Configuring an IPv6 advanced ACL
Network requirements
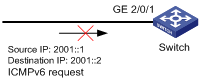
As shown in Figure 3, configure an IPv6 advanced ACL for QoS on interface GigabitEthernet 2/0/1 to filter incoming ICMPv6 echo-request packets with source IPv6 address 2001::1 and destination IPv6 address 2001::2.
Software version used
This configuration example was created and verified on S12500-CMW520-R1825P01.
Configuration restrictions and guidelines
Because support for IPv6 ACLs depends on the card type, you must first identify the type card being used.
· If an EB/EC2 card is used, make sure the EB/EC2 card is advanced ACL hardware mode because EB/EC2 cards only in this mode can support IPv6 ACLs. You can use the display acl mode command to display the ACL hardware mode. If the card is in basic ACL hardware mode, use the acl mode advanced command to change the mode to the advanced mode. By default, an EB/EC2 card is in advanced ACL hardware mode.
· IF an EC1 or EF card (interface card prefixed with EC1 or EF) is used, execute the acl ipv6 enable command in system view to enable the support for IPv6 ACLs. These types of cards do not support IPv6 ACLs by default.
In example, an EB/EC2 card is in slot 2 that connects to GigabitEthernet 2/0/1, and the card is in advanced ACL mode.
Configuration procedures
# Create IPv6 advanced ACL 3000.
<Switch> system-view
[Switch] acl ipv6 number 3000
# Configure an ACL rule to identify ICMPv6 echo-request messages with source IPv6 address 2001::1 and destination IPv6 address 2001::2.
[Switch-acl6-adv-3000] rule permit icmpv6 icmp6-type echo-request source 2001::1 128 destination 2001::2 128
[Switch-acl6-adv-3000] quit
# Create a traffic class named c_deny and configure ACL 3000 as the match criteria.
[Switch] traffic classifier c_deny
[Switch-classifier-c_deny] if-match acl ipv6 3000
[Switch-classifier-c_deny] quit
# Create a traffic behavior named b_deny and configure the traffic filtering action as deny for the behavior.
[Switch] traffic behavior b_deny
[Switch-behavior-b_deny] filter deny
[Switch-behavior-b_deny] quit
# Create a QoS policy named Q_deny and associate traffic class c_deny with the behavior b_deny in the policy.
[Switch] qos policy Q_deny
[Switch-qospolicy-Q_deny] classifier c_deny behavior b_deny
[Switch-qospolicy-Q_deny] quit
# Apply QoS policy Q_deny to the inbound direction of interface GigabitEthernet 2/0/1.
[Switch] interface GigabitEthernet 2/0/1
[Switch-GigabitEthernet2/0/1] qos apply policy Q_deny inbound
[Switch-GigabitEthernet2/0/1] undo shutdown
[Switch-GigabitEthernet2/0/1] quit
Verifying the configuration
# Display the QoS configuration and operation information on GigabitEthernet 2/0/1.
[Switch] display qos policy interface GigabitEthernet 2/0/1
Interface: GigabitEthernet2/0/1
Direction: Inbound
Policy: Q_deny
Classifier: c_deny
Operator: AND
Rule(s) : If-match acl ipv6 3000
Behavior: b_deny
Filter Enable: deny
After the configuration, all received ICMPv6 echo-requests matching the ACL rule are denied and all the other packets are allowed to pass through.
Configuration files
#
acl ipv6 number 3000
rule 0 permit icmpv6 source 2001::1/128 destination 2001::2/128 icmp6-type echo-request
#
vlan 1
#
traffic classifier c_deny operator and
if-match acl ipv6 3000
#
traffic behavior b_deny
filter deny
#
qos policy Q_deny
classifier c_deny behavior b_deny
#
interface GigabitEthernet2/0/1
port link-mode bridge
qos apply policy Q_deny inbound
#
Example: Configuring a usesr-defined ACL
Network requirements
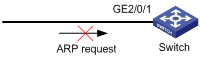
As shown in Figure 4, configure a user-defined ACL for QoS on interface GigabitEthernet 2/0/1 to filter all incoming ARP request packets.
Software version used
This configuration example was created and verified on S12500-CMW520-R1825P01.
Configuration restrictions and guidelines
· Because support for user-defined ACLs depends on the card type, you must first identify the type card being used.
? If an EB/EC2 card is used, make sure the EB/EC2 card is advanced ACL hardware mode because EB/EC2 cards only in this mode can support user-defined ACLs. You can use the display acl mode command to display the ACL hardware mode. If the card is in basic ACL hardware mode, use the acl mode advanced command to change the mode to the advanced mode. By default, an EB/EC2 card is in advanced ACL hardware mode.
? IF an EC1 or EF card is used, execute the acl ipv6 enable command in system view to enable the support for user-defined ACLs. These types of cards do not support user-defined ACLs by default.
? In example, an EB/EC2 card is in slot 2 that connects to GigabitEthernet 2/0/1, and the card is in advanced ACL mode.
· A user-defined ACL rule cannot be modified. You must create a new one to override the old one.
· For a user-defined ACL, the rule order can only be config. The rules in an ACL are in ascending order of rule ID.
Configuration procedures
# Create user-defined ACL 5000.
<Switch> system-view
[Switch] acl number 5000
# Configure an ACL rule to identify ARP requests that carry 0x0806 for the Layer 2 protocol type field and 0x0001 for the operation type filed.
[Switch-acl-user-5000] rule permit l2 0806 ffff 0 l2 0001 ffff 8
[Switch-acl-user-5000] quit
# Create a traffic class named c_deny, and configure ACL 5000 as the match criteria.
[Switch] traffic classifier c_deny
[Switch-classifier-c_deny] if-match acl 5000
[Switch-classifier-c_deny] quit
# Create a traffic behavior named b_deny, and configure the traffic filtering action as deny for the behavior.
[Switch] traffic behavior b_deny
[Switch-behavior-b_deny] filter deny
[Switch-behavior-b_deny] quit
# Create a QoS policy named Q_deny, and associate traffic class c_deny with the behavior b_deny in the policy.
[Switch] qos policy Q_deny
[Switch-qospolicy-Q_deny] classifier c_deny behavior b_deny
[Switch-qospolicy-Q_deny] quit
# Apply QoS policy Q_deny in the inbound direction of interface GigabitEthernet 2/0/1.
[Switch] interface GigabitEthernet 2/0/1
[Switch-GigabitEthernet2/0/1] undo shutdown
[Switch-GigabitEthernet2/0/1] qos apply policy Q_deny inbound
[Switch-GigabitEthernet2/0/1] quit
Verifying the configuration
# Display the QoS configuration and operation information on GigabitEthernet 2/0/1.
[Switch] display qos policy interface GigabitEthernet 2/0/1
Interface: GigabitEthernet2/0/1
Direction: Inbound
Policy: Q_deny
Classifier: c_deny
Operator: AND
Rule(s) : If-match acl 5000
Behavior: b_deny
Filter Enable: deny
After the configuration, no response are received for the ARP requests sent to GigabitEthernet 2/0/1. No ARP requests are allowed to pass through GigabitEthernet 2/0/1.
Configuration files
#
acl number 5000
rule 0 permit l2 08060000000000000001 ffff000000000000ffff 0
#
vlan 1
#
traffic classifier c_deny operator and
if-match acl 5000
#
traffic behavior b_deny
filter deny
#
qos policy Q_deny
classifier c_deny behavior b_deny
#
interface GigabitEthernet2/0/1
port link-mode bridge
qos apply policy Q_deny inbound
#
Related documentation
· H3C S12500 Routing Switch Series ACL and QoS Configuration Guide
· H3C S12500 Routing Switch Series ACL and QoS Command Reference
