- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-IP L3VPN over SRv6 configuration | 257.31 KB |
Configuring IP L3VPN over SRv6
IP L3VPN over SRv6 tasks at a glance
Applying a locator to a BGP VPN instance
Configuring PEs to exchange BGP VPNv4 or VPNv6 routes
Configuring IPv6 peers to exchange SRv6 SIDs
Configuring BGP VPNv4 or VPNv6 routes
Restrictions and guidelines for BGP VPNv4 or VPNv6 route configuration
Controlling BGP VPNv4 or VPNv6 route advertisement and reception
Setting a preferred value for received BGP VPNv4 or VPNv6 routes
Configuring BGP VPNv4 or VPNv6 route reflection
Configuring BGP VPNv4 or VPNv6 route attributes
Configuring BGP VPNv4 or VPNv6 route distribution filtering policies
Configuring the BGP Additional Paths feature
Specifying a source address for the outer IPv6 header of SRv6-encapsulated packets
Verifying and maintaining IP L3VPN over SRv6
Displaying the configuration and running status of IP L3VPN over SRv6 VPN
Clearing flap statistics for BGP VPNv4 routes
IP L3VPN over SRv6 configuration examples
Example: Configuring IP L3VPN over SRv6 in SRv6 BE mode
Configuring IP L3VPN over SRv6
About IP L3VPN over SRv6
IP L3VPN over SRv6 uses SRv6 tunnels to carry IP L3VPN services. This technology establishes SRv6 tunnels among geographically dispersed customer sites over an IPv6 network and transparently forwards Layer 3 customer traffic to remote sites over the IPv6 network through the tunnels. For more information about MPLS L3VPN configuration, see MPLS Configuration Guide.
Basic principle
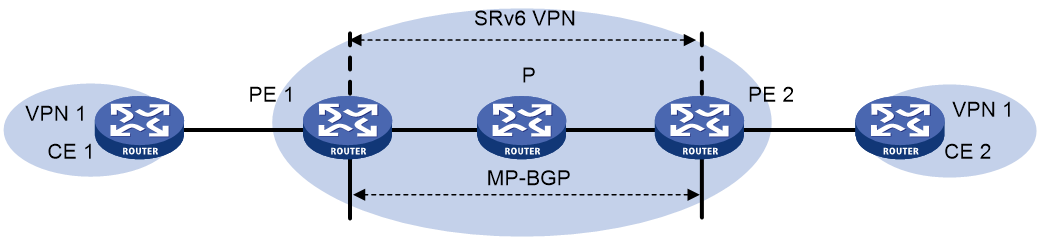
Figure 1 shows a typical IP L3VPN over SRv6 network.
· PE 1 and PE 2 use BGP to advertise IPv4 or IPv6 VPN routes to each other over the IPv6 backbone network. The VPN routes contain private network routing information and SID information.
· The PEs have an SRv6 tunnel between them and they use the SRv6 tunnel to forward VPN traffic across sites.
· The devices in the IPv6 backbone network forward the SRv6-encapsulated VPN traffic through the optimal path calculated by IGP.
IP L3VPN over SRv6 connects geographically dispersed sites that belong to the same VPN over the IPv6 backbone network.
Route advertisement
The route advertisement process of IPv4 L3VPN over SRv6 is similar to that of IPv6 L3VPN over SRv6. This section uses IPv4 L3VPN over SRv6 to illustrate the process.
As shown in Figure 1, local routes of CE 1 are advertised to CE 2 by using the following process:
1. CE 1 uses static routing, RIP, OSPF, IS-IS, EBGP, or IBGP to advertise private network routes of the local site to PE 1.
2. After learning the route information of CE 1, PE 1 stores the private routes to the routing table of the VPN instance. In this example, VPN instance 1 is used. Then, PE 1 converts the routes to BGP VPNv4 routes and advertises the BGP VPNv4 routes to PE 2 by using MP-BGP. The BGP VPNv4 routes carry the RD, RT, and SID attributes (the SID attribute is used as the private network label). All private network routes of the VPN instance are allocated the same End.DT4 SID.
3. When PE 2 receives the routes advertised by PE 1, it adds the routes to the routing table of VPN 1, converts the routes to IPv4 routes, and advertises the IPv4 routes to CE 2.
4. By adding the received IPv4 routes to the routing table, CE 2 learns the private network routes of CE 1.
Packet forwarding
The packet forwarding process is similar for IPv4 L3VPN over SRv6 and IPv6 L3VPN over SRv6. This section uses IPv4 L3VPN over SRv6 and VPN sites to illustrate the process.
As shown in Figure 1, CE 2 forwards an IPv4 packet to CE 1 as follows:
1. CE 2 sends the IPv4 packet to PE 2.
2. PE 2 receives the packet on an interface associated with VPN 1. PE 2 searches for a route that matches the destination IPv4 address of the packet in the routing table of VPN 1. The corresponding End.DT4 SID is found. Then, PE 2 encapsulates an outer IPv6 header for the packet. The End.DT4 SID is encapsulated in the outer IPv6 header as the destination address.
3. PE 2 searches the IPv6 routing table based on the End.DT4 SID for the optimal IGP route and forwards the packet to P through the route.
4. P searches the IPv6 routing table based on the End.DT4 SID for the optimal IGP route and forwards the packet to PE 1 through the route.
5. When PE 1 receives the packet, it processes the packet as follows:
a. Searches the local SID forwarding table for the End.DT4 SID.
b. Removes the outer IPv6 header.
c. Matches the packet to VPN 1 based on the SID, searches the routing table of VPN 1 for the optimal route, and forwards the packet to CE 1.
IP L3VPN over SRv6 tasks at a glance
To configure IP L3VPN over SRv6, perform the following tasks:
1. Configuring a VPN instance and associating interfaces connected to CEs with the VPN instance
Perform this task on PEs. For more information, see MPLS L3VPN in MPLS Configuration Guide.
2. Configuring route exchange between a PE and a CE
Configure an IPv4 routing protocol (static routing, RIP, OSPF, IS-IS, EBGP, or IBGP) or an IPv6 routing protocol (IPv6 static routing, RIPng, OSPFv3, IPv6 IS-IS, EBGP, or IBGP) to exchange routes between a PE and a CE
On the CE, configure an IPv4 or IPv6 routing protocol to advertise routes of the local site to the PE. On the PE, associate the routing protocol with the VPN instance. For more information about routing protocol configurations, see Layer 3—IP Routing Configuration Guide.
3. Configuring route exchange between PEs
Perform this task to manually configure End.DT4 or End.DT6 SIDs.
b. Applying a locator to a BGP VPN instance
BGP can advertise SRv6 SIDs through BGP routes only after you apply a locator to BGP.
c. Configuring PEs to exchange BGP VPNv4 or VPNv6 routes
d. Configuring IPv6 peers to exchange SRv6 SIDs
This feature enables PEs to exchange End.DT4 or End.DT6 SIDs through BGP VPNv4 or VPNv6 routes.
e. (Optional.) Configuring BGP VPNv4 or VPNv6 routes
4. Specifying a source address for the outer IPv6 header of SRv6-encapsulated packets
This feature specifies the source address of the outer IPv6 header for SRv6 packets that are delivered between two private network sites over the backbone network.
Configuring SRv6 SIDs
Restrictions and guidelines
If PEs advertise BGP VPNv4 or VPNv6 routes to each other, you must specify a VPN instance when configuring an opcode.
When you configure SRv6 SIDs, make sure the IPv6 address for a locator is the main IPv6 address for an interface.
Procedure
1. Enter system view.
system-view
2. Enable SRv6 and enter SRv6 view.
segment-routing ipv6
3. Configure a locator and enter SRv6 locator view.
locator locator-name [ ipv6-prefix ipv6-address prefix-length [ args args-length | static static-length ] * ]
4. Configure an opcode. Perform one of the following tasks:
¡ Configure End.DT4 SIDs.
opcode { opcode | hex hex-opcode } end-dt4 [ vpn-instance vpn-instance-name ]
The specified VPN instance must exist. The same End.DT4 SIDs cannot be configured in different VPN instances.
¡ Configure End.DT6 SIDs.
opcode { opcode | hex hex-opcode } end-dt6 [ vpn-instance vpn-instance-name ]
The specified VPN instance must exist. The same End.DT6 SIDs cannot be configured in different VPN instances.
Applying a locator to a BGP VPN instance
About this task
Use this feature in BGP-VPN IPv4 or IPv6 unicast address family view of a VPN instance to apply for SRv6 SIDs for the private network routes of the VPN instance.
Use this feature if the device will use End.DT4 or End.DT6 SIDs to deliver VPN traffic across sites.
Restrictions and guidelines
The VPN instance of the specified locator must be the same as the VPN instance of the private network. To specify a VPN instance for a locator, use the opcode end-dt4 or opcode end-dt6 command in SRv6 locator view.
Prerequisites
Before you perform this task, you must create the specified locator.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP-VPN instance view.
ip vpn-instance vpn-instance-name
4. Enter BGP-VPN IPv4 unicast address family view or BGP-VPN IPv6 unicast address family view.
¡ Enter BGP-VPN IPv4 unicast address family view.
address-family ipv4 [ unicast ]
¡ Enter BGP-VPN IPv6 unicast address family view.
address-family ipv6 [ unicast ]
5. Apply a locator to the BGP VPN instance.
¡ Apply a common locator to the BGP VPN instance.
segment-routing ipv6 locator locator-name [ auto-sid-disable ]
¡ Apply an anycast locator to the BGP VPN instance.
segment-routing ipv6 locator locator-name anycast
After configuring this command, you must configure the peer prefix-sid command with the anycast keyword in order to exchange SRv6 SID information in the anycast locator with the specified peer.
By default, no locator is applied to a BGP VPN instance.
Configuring PEs to exchange BGP VPNv4 or VPNv6 routes
Restrictions and guidelines
For more information about the commands in this section, see BGP in Layer 3—IP Routing Command Reference.
To ensure optimal route selection and SRv6 tunnel traffic forwarding, make sure a pair of PEs are not both IPv4 and IPv6 peers to each other.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Specify a remote PE as an IPv6 peer.
peer { group-name | ipv6-address [ prefix-length ] } as-number as-number
4. Specify a source interface (IPv6 address) for establishing TCP connections to an IPv6 peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } connect-interface interface-type interface-number
By default, BGP uses the output interface in the optimal route destined for a BGP peer or peer group as the source interface for establishing TCP connections.
5. Create the BGP VPNv4 or VPNv6 address family and enter its view.
¡ Create the BGP VPNv4 address family and enter its view.
address-family vpnv4
¡ Create the BGP VPNv6 address family and enter its view.
address-family vpnv6
6. Enable BGP to exchange VPNv4 or VPNv6 routing information with an IPv6 peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } enable
By default, BGP cannot exchange VPNv4 or VPNv6 routing information with an IPv6 peer or peer group.
Configuring IPv6 peers to exchange SRv6 SIDs
About this task
Perform this task to configure IPv6 peers to exchange SRv6 SID information through BGP VPNv4 or VPNv6 routes.
Procedure
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Enable BGP to exchange SRv6 SID information with an IPv6 peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } prefix-sid [ anycast ]
By default, BGP cannot exchange SRv6 SID information with an IPv6 peer or peer group.
After specifying the anycast keyword, you must configure the segment-routing ipv6 locator anycast command in order to exchange SRv6 SID information in the anycast locator with the specified peer.
Configuring BGP VPNv4 or VPNv6 routes
Restrictions and guidelines for BGP VPNv4 or VPNv6 route configuration
For more information about the commands in this section, see BGP in Layer 3—IP Routing Command Reference.
Controlling BGP VPNv4 or VPNv6 route advertisement and reception
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Set the maximum number of routes that BGP can receive from a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } route-limit prefix-number [ { alert-only | discard | reconnect reconnect-time } | percentage-value ] *
By default, the number of routes that BGP can receive from a peer or peer group is not limited.
5. Save all route updates from a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } keep-all-routes
By default, route updates from peers and peer groups are not saved.
Setting a preferred value for received BGP VPNv4 or VPNv6 routes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Set a preferred value for routes received from a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } preferred-value value
By default, the preferred value is 0 for routes received from a peer or peer group.
Configuring BGP VPNv4 or VPNv6 route reflection
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the router as a route reflector (RR) and specify a peer or peer group as its client.
peer { group-name | ipv6-address [ prefix-length ] } reflect-client
By default, no RR or client is configured.
5. (Optional.) Enable route reflection between clients.
reflect between-clients
By default, route reflection between clients is enabled.
6. (Optional.) Configure the cluster ID of the RR.
reflector cluster-id { cluster-id | ip-address }
By default, an RR uses its own router ID as the cluster ID.
7. (Optional.) Create an RR reflection policy.
rr-filter { ext-comm-list-number | ext-comm-list-name }
By default, an RR does not filter reflected routes.
8. (Optional.) Enable the RR to change the attributes of routes to be reflected.
reflect change-path-attribute
By default, the RR cannot change the attributes of routes to be reflected.
Configuring BGP VPNv4 or VPNv6 route attributes
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the NEXT_HOP attribute. Choose one option as needed:
¡ Specify the router as the next hop for routes sent to a peer or peer group.
peer { group-name | ipv4-address [ mask-length ] | ipv6-address [ prefix-length ] } next-hop-local
¡ Configure the device to not change the next hop of routes advertised to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } next-hop-invariable
By default, the router sets itself as the next hop for routes sent to a peer or peer group.
The peer next-hop-local and peer next-hop-invariable commands are mutually exclusive.
5. Configure the AS_PATH attribute.
¡ Permit the local AS number to appear in routes from a peer or peer group and set the appearance times.
peer { group-name | ipv6-address [ prefix-length ] } allow-as-loop [ number ]
By default, the local AS number is not allowed in routes from a peer or peer group.
¡ Remove private AS numbers from the AS_PATH attribute of updates sent to an EBGP peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } public-as-only [ { force | limited } [ replace ] [ include-peer-as ] ]
By default, BGP updates sent to an EBGP peer or peer group can carry both public and private AS numbers.
6. Advertise the COMMUNITY attribute to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } advertise-community
By default, the COMMUNITY attribute is not advertised.
7. Configure the SoO attribute for a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } soo site-of-origin
By default, no SoO attribute is configured for a peer or peer group.
8. Enable BGP to filter next hop routes obtained through recursive lookup based on a routing policy.
nexthop recursive-lookup route-policy route-policy-name
By default, BGP does not filter next hop routes obtained through recursive lookup based on a routing policy.
|
CAUTION: If all next hops routes obtained through recursive lookup in an address family fail to match the specified routing policy, all BGP routes in the address family become unreachable. To avoid this issue, before configuring the command, make sure the target next hop routes can match the permit-mode node in the routing policy. |
Configuring BGP VPNv4 or VPNv6 route distribution filtering policies
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Specify an ACL or IP prefix list to filter advertised BGP routes.
filter-policy { ipv4-acl-number | name ipv4-acl-name | prefix-list prefix-list-name } export [ protocol process-id ]
By default, no ACL or IP prefix list is specified to filter advertised BGP routes.
5. Specify an ACL or IP prefix list to filter received BGP routes.
filter-policy { ipv4-acl-number | name ipv4-acl-name | prefix-list prefix-list-name } import
By default, no ACL or IP prefix list is specified to filter received BGP routes.
6. Specify an IP prefix list to filter BGP routes for a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } prefix-list prefix-list-name { export | import }
By default, no IP prefix list is specified to filter BGP routes for a peer or peer group.
7. Apply a routing policy to routes received from or advertised to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } route-policy route-policy-name { export | import }
By default, no routing policy is applied to routes received from or advertised to a peer or peer group.
8. Enable route target filtering of received VPNv4 or VPNv6 routes.
policy vpn-target
By default, the route target filtering feature is enabled for received VPNv4 or VPNv6 routes. BGP adds an VPNv4 or VPNv6 route to the routing table only when the export route targets of the route match the local import route targets.
9. Filter BGP peers based on the first AS number in EBGP routes.
peer-as-check enable
By default, the device does not filter BGP peers based on the first AS number in EBGP routes. Upon receiving an EBGP route, the device advertises the route to all peers except the advertising peer.
With this command configured, BGP checks the first AS number in the AS_PATH attribute of EBGP routes. It will not advertise an EBGP route to a EBGP peer if the first AS number in the route is the same as the AS number of the EBGP peer.
Configuring the BGP Additional Paths feature
1. Enter system view.
system-view
2. Enter BGP instance view.
bgp as-number [ instance instance-name ]
3. Enter BGP VPNv4 address family view or BGP VPNv6 address family view.
¡ Enter BGP VPNv4 address family view.
address-family vpnv4
¡ Enter BGP VPNv6 address family view.
address-family vpnv6
4. Configure the BGP Additional Paths capabilities.
peer { group-name | ipv6-address [ prefix-length ] } additional-paths { receive | send } *
By default, no BGP Additional Paths capabilities are configured.
5. Set the maximum number of Add-Path optimal routes that can be advertised to a peer or peer group.
peer { group-name | ipv6-address [ prefix-length ] } advertise additional-paths best number
By default, only one Add-Path optimal route can be advertised to a peer or peer group.
6. Set the maximum number of Add-Path optimal routes that can be advertised to all peers.
additional-paths select-best best-number
By default, a maximum number of one Add-Path optimal route can be advertised to all peers.
7. (Optional.) Set the optimal route selection delay timer.
route-select delay delay-value
By default, the optimal route selection delay timer is 0 seconds, which indicates that optimal route selection is not delayed.
Specifying a source address for the outer IPv6 header of SRv6-encapsulated packets
Restrictions and guidelines
To ensure correct traffic forwarding in an IP L3VPN over SRv6 network, you must specify a source address for the outer IPv6 header of SRv6-encapsulated packets.
You cannot specify a loopback address, link-local address, multicast address, or unspecified address as the source IPv6 address. You must specify an IPv6 address of the local device as the source IPv6 address, and make sure the IPv6 address has been advertised by a routing protocol. As a best practice, specify a loopback interface address of the local device as the source IPv6 address.
Procedure
1. Enter system view.
system-view
2. Enter SRv6 view.
segment-routing ipv6
3. Specify a source address for the outer IPv6 header of SRv6-encapsulated packets.
encapsulation source-address ipv6-address [ ip-ttl ttl-value ]
By default, no source address is specified for the outer IPv6 header of SRv6-encapsulated packets.
Verifying and maintaining IP L3VPN over SRv6
Displaying the configuration and running status of IP L3VPN over SRv6 VPN
For more information about the commands in this section, see basic BGP commands in Layer 3—IP Routing Command Reference.
Perform display tasks in any view.
· Display BGP VPNv4 peer or peer group information.
display bgp [ instance instance-name ] peer vpnv4 { ipv6-address prefix-length | ipv6-address { log-info | verbose } }
· Display BGP update group information for VPNv4 address family.
display bgp [ instance instance-name ] update-group vpnv4 ipv6-address
· Display BGP VPNv6 peer or peer group information.
display bgp [ instance instance-name ] peer vpnv6 [ vpn-instance vpn-instance-name ] [ ipv6-address prefix-length | { ipv6-address | group-name group-name } log-info | [ ipv6-address ] verbose ]
· Display BGP update group information for VPNv6 address family.
display bgp [ instance instance-name ] update-group vpnv6 [ vpn-instance vpn-instance-name ] [ ipv6-address ]
Resetting BGP sessions
About this task
For BGP setting changes to take effect, you must reset or soft-reset BGP sessions. Soft-resetting BGP sessions updates BGP routing information without tearing down the BGP sessions. Resetting BGP sessions updates BGP routing information by tearing down and re-establishing the BGP sessions. Soft-reset requires that both the local router and the peer support ROUTE-REFRESH messages.
Procedure
For more information about the commands, see basic BGP commands in Layer 3—IP Routing Command Reference.
Perform the tasks in user view.
· Soft-reset BGP sessions of the BGP VPNv4 address family.
refresh bgp [ instance instance-name ] ipv6-address [ prefix-length ] { export | import } vpnv4
· Reset BGP sessions of the BGP VPNv4 address family.
reset bgp [ instance instance-name ] ipv6-address [ prefix-length ] vpnv4
Clearing flap statistics for BGP VPNv4 routes
To clear flap statistics for BGP VPNv4 routes, execute the following command in user view:
reset bgp [ instance instance-name ] flap-info vpnv4 [ ipv4-address [ mask | mask-length ] | as-path-acl as-path-acl-number | peer ipv6-address [ prefix-length ] ]
IP L3VPN over SRv6 configuration examples
Example: Configuring IP L3VPN over SRv6 in SRv6 BE mode
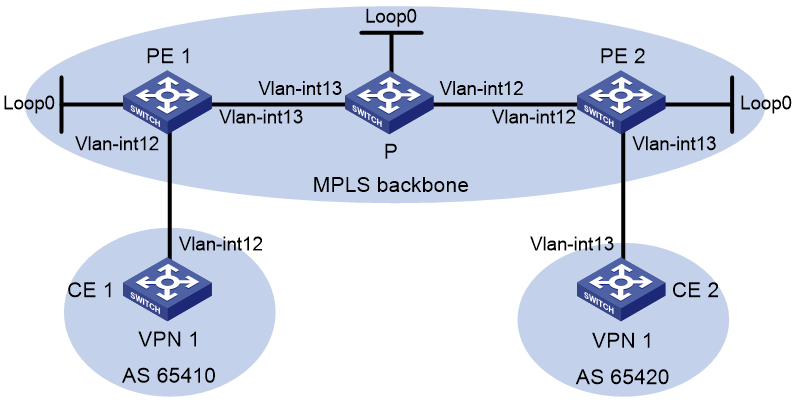
Network configuration
As shown in Figure 2, the backbone network is an IPv6 network, and VPN 1 is an IPv4 network. Deploy IP L3VPN over SRv6 between PE 1 and PE 2 and use an SRv6 tunnel to transmit VPNv4 traffic between the PEs.
· Configure EBGP to exchange VPN routing information between the CEs and PEs.
· Configure IPv6 IS-IS on the PEs in the same AS to realize IPv6 network connectivity.
· Configure MP-IBGP to exchange VPNv4 routing information between the PEs.
Table 1 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
CE 1 |
VLAN-interface 12 |
10.1.1.2/24 |
PE 2 |
Loopback 0 |
3::3/128 |
|
PE 1 |
Loopback 0 |
1::1/128 |
|
VLAN-interface 13 |
10.2.1.1/24 |
|
|
VLAN-interface 12 |
10.1.1.1/24 |
|
VLAN-interface 12 |
2002::1/96 |
|
|
VLAN-interface 13 |
2001::1/96 |
CE 2 |
VLAN-interface 13 |
10.2.1.2/24 |
|
P |
Loopback 0 |
2::2/128 |
|
|
|
|
|
VLAN-interface 13 |
2001::2/96 |
|
|
|
|
|
VLAN-interface 12 |
2002::2/96 |
|
|
|
Procedure
1. Configure IPv6 IS-IS on the PEs and device P for network connectivity between the devices:
# Configure PE 1.
<PE1> system-view
[PE1] isis 1
[PE1-isis-1] is-level level-1
[PE1-isis-1] cost-style wide
[PE1-isis-1] network-entity 10.1111.1111.1111.00
[PE1-isis-1] address-family ipv6 unicast
[PE1-isis-1-ipv6] quit
[PE1-isis-1] quit
[PE1] interface loopback 0
[PE1-LoopBack0] ipv6 address 1::1 128
[PE1-LoopBack0] isis ipv6 enable 1
[PE1-LoopBack0] quit
[PE1] interface vlan-interface 13
[PE1-Vlan-interface13] ipv6 address 2001::1 96
[PE1-Vlan-interface13] isis ipv6 enable
[PE1-Vlan-interface13] quit
# Configure P.
<P> system-view
[P] isis
[P-isis-1] is-level level-1
[P-isis-1] cost-style wide
[P-isis-1] network-entity 10.2222.2222.2222.00
[P-isis-1] address-family ipv6 unicast
[P-isis-1-ipv6] quit
[P-isis-1] quit
[P] interface loopback 0
[P-LoopBack0] ipv6 address 2::2 128
[P-LoopBack0] isis ipv6 enable
[P-LoopBack0] quit
[P] interface vlan-interface 13
[P-Vlan-interface13] ipv6 address 2001::2 96
[P-Vlan-interface13] isis ipv6 enable
[P-Vlan-interface13] quit
[P] interface vlan-interface 12
[P-Vlan-interface12] ipv6 address 2002::2 96
[P-Vlan-interface12] isis ipv6 enable
[P-Vlan-interface12] quit
# Configure PE 2.
<PE2> system-view
[PE2] isis
[PE2-isis-1] is-level level-1
[PE2-isis-1] cost-style wide
[PE2-isis-1] network-entity 10.3333.3333.3333.00
[PE2-isis-1] address-family ipv6 unicast
[PE2-isis-1-ipv6] quit
[PE2-isis-1] quit
[PE2] interface loopback 0
[PE2-LoopBack0] ipv6 address 3::3 128
[PE2-LoopBack0] isis ipv6 enable
[PE2-LoopBack0] quit
[PE2] interface vlan-interface 12
[PE2-Vlan-interface12] ipv6 address 2002::1 96
[PE2-Vlan-interface12] isis ipv6 enable
[PE2-Vlan-interface12] quit
# Verify that PE 1, P, and PE 2 have established IPv6 IS-IS neighbor relationships and the neighbor state is up.
[PE1] display isis peer
[P] display isis peer
[PE2] display isis peer
# Verify that PE 1 and PE 2 each learn a route destined for the loopback interface of each other.
[PE1] display isis route ipv6
[PE2] display isis route ipv6
2. Configure VPN instance settings on PE 1 and PE 2 and verify that each CE can access its local PE:
# Configure PE 1.
[PE1] ip vpn-instance vpn1
[PE1-vpn-instance-vpn1] route-distinguisher 100:1
[PE1-vpn-instance-vpn1] vpn-target 111:1
[PE1-vpn-instance-vpn1] address-family ipv4
[PE1-vpn-ipv4-vpn1] vpn-target 111:1
[PE1-vpn-ipv4-vpn1] quit
[PE1-vpn-instance-vpn1] address-family ipv6
[PE1-vpn-ipv6-vpn1] vpn-target 111:1
[PE1-vpn-ipv6-vpn1] quit
[PE1-vpn-instance-vpn1] quit
[PE1] interface vlan-interface 12
[PE1-Vlan-interface12] ip binding vpn-instance vpn1
[PE1-Vlan-interface12] ip address 10.1.1.1 24
[PE1-Vlan-interface12] quit
# Configure PE 2.
[PE2] ip vpn-instance vpn1
[PE2-vpn-instance-vpn1] route-distinguisher 100:1
[PE2-vpn-instance-vpn1] vpn-target 111:1
[PE2-vpn-instance-vpn1] address-family ipv4
[PE2-vpn-ipv4-vpn1] vpn-target 111:1
[PE2-vpn-ipv4-vpn1] quit
[PE2-vpn-instance-vpn1] address-family ipv6
[PE2-vpn-ipv6-vpn1] vpn-target 111:1
[PE2-vpn-ipv6-vpn1] quit
[PE2-vpn-instance-vpn1] quit
[PE2] interface vlan-interface 13
[PE2-Vlan-interface13] ip binding vpn-instance vpn1
[PE2-Vlan-interface13] ip address 10.2.1.1 24
[PE2-Vlan-interface13] quit
# Configure IP addresses for the interfaces on the CEs, as shown in Figure 2. (Details not shown.)
# Display VPN instance settings on each PE. This step uses PE 1 as an example.
[PE1] display ip vpn-instance
Total VPN-Instances configured : 1
Total IPv4 VPN-Instances configured : 1
Total IPv6 VPN-Instances configured : 1
VPN-Instance Name RD Address family Create time
vpn1 100:1 N/A 2019/08/12 13:59:39
# Verify that each PE can ping its local CE. This step uses PE 1 and CE 1 as an example.
[PE1] ping -vpn-instance vpn1 10.1.1.2
Ping 10.1.1.2 (10.1.1.2): 56 data bytes, press CTRL+C to break
56 bytes from 10.1.1.2: icmp_seq=0 ttl=255 time=2.000 ms
56 bytes from 10.1.1.2: icmp_seq=1 ttl=255 time=0.000 ms
56 bytes from 10.1.1.2: icmp_seq=2 ttl=255 time=1.000 ms
56 bytes from 10.1.1.2: icmp_seq=3 ttl=255 time=0.000 ms
56 bytes from 10.1.1.2: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.1.2 in VPN instance vpn1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.600/2.000/0.800 ms
3. Set up an EBGP peer relationship between each PE and its local CE and distribute VPN routes to EBGP:
# Configure CE 1.
<CE1> system-view
[CE1] bgp 65410
[CE1-bgp-default] peer 10.1.1.1 as-number 100
[CE1-bgp-default] address-family ipv4 unicast
[CE1-bgp-default-ipv4] peer 10.1.1.1 enable
[CE1-bgp-default-ipv4] import-route direct
[CE1-bgp-default-ipv4] quit
[CE1-bgp-default] quit
# Configure CE 2 in the same way as CE 1 is configured. (Details not shown.)
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] router-id 1.1.1.1
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] peer 10.1.1.2 as-number 65410
[PE1-bgp-default-vpn1] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn1] peer 10.1.1.2 enable
[PE1-bgp-default-ipv4-vpn1] quit
[PE1-bgp-default-vpn1] quit
# Configure PE 2 in the same way PE 1 is configured. (Details not shown.)
# Verify that the PEs have established BGP peer relationships with their local CEs and the peers are in established state.
[PE1] display bgp peer ipv4 vpn-instance
[PE2] display bgp peer ipv4 vpn-instance
4. Set up an MP-IBGP peer relationship between PE 1 and PE 2:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] peer 3::3 as-number 100
[PE1-bgp-default] peer 3::3 connect-interface loopback 0
[PE1-bgp-default] address-family vpnv4
[PE1-bgp-default-vpnv4] peer 3::3 enable
[PE1-bgp-default-vpnv4] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] peer 1::1 as-number 100
[PE2-bgp-default] peer 1::1 connect-interface loopback 0
[PE2-bgp-default] address-family vpnv4
[PE2-bgp-default-vpnv4] peer 1::1 enable
[PE2-bgp-default-vpnv4] quit
[PE2-bgp-default] quit
# Verify that the PEs have established a BGP peer relationship and the peers are in established state.
[PE1] display bgp peer vpnv4
[PE2] display bgp peer vpnv4
5. Specify a source address for the outer IPv6 header of SRv6-encapsulated packets on PE 1 and PE 2:
# Configure PE 1.
[PE1] segment-routing ipv6
[PE1-segment-routing-ipv6] encapsulation source-address 1::1
# Configure PE 2.
[PE2] segment-routing ipv6
[PE2-segment-routing-ipv6] encapsulation source-address 3::3
6. Configure the destination address (End.DT4 SID) of the outer IPv6 header for SRv6-encapsulated packets:
# Configure PE 1.
[PE1-segment-routing-ipv6] locator aaa ipv6-prefix 1:2::1:0 96 static 8
[PE1-segment-routing-ipv6-locator-aaa] quit
[PE1-segment-routing-ipv6] quit
[PE1] isis 1
[PE1-isis-1] address-family ipv6 unicast
[PE1-isis-1-ipv6] segment-routing ipv6 locator aaa
[PE1-isis-1-ipv6] quit
[PE1-isis-1] quit
# Configure PE 2.
[PE2-segment-routing-ipv6] locator bbb ipv6-prefix 6:5::1:0 96 static 8
[PE2-segment-routing-ipv6-locator-bbb] quit
[PE2-segment-routing-ipv6] quit
[PE2] isis 1
[PE2-isis-1] address-family ipv6 unicast
[PE2-isis-1-ipv6] segment-routing ipv6 locator bbb
[PE2-isis-1-ipv6] quit
[PE2-isis-1] quit
# Verify that the PEs have distributed the End.DT4 SIDs to the routing table and generated SRv6 routes. This step uses PE 1 as an example.
[PE1] display ipv6 routing-table protocol srv6
Summary count : 1
SRv6 Routing table status : <Active>
Summary count : 1
Destination: 1:2::101/128 Protocol : SRv6
NextHop : ::1 Preference: 4
Interface : InLoop0 Cost : 0
SRv6 Routing table status : <Inactive>
Summary count : 0
7. Add End.DT4 SIDs to private network routes on PE 1 and PE 2:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn1] segment-routing ipv6 locator aaa
[PE1-bgp-default-ipv4-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] address-family ipv4 unicast
[PE2-bgp-default-ipv4-vpn1] segment-routing ipv6 locator bbb
[PE2-bgp-default-ipv4-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
8. Enable IPv6 peers on the PEs to exchange End.DT4 SIDs and enable the SID-route-recursion feature:
# Configure PE 1.
[PE1] bgp 100
[PE1-bgp-default] address-family vpnv4
[PE1-bgp-default-vpnv4] peer 3::3 prefix-sid
[PE1-bgp-default-vpnv4] quit
[PE1-bgp-default] ip vpn-instance vpn1
[PE1-bgp-default-vpn1] address-family ipv4 unicast
[PE1-bgp-default-ipv4-vpn1] segment-routing ipv6 best-effort
[PE1-bgp-default-ipv4-vpn1] quit
[PE1-bgp-default-vpn1] quit
[PE1-bgp-default] quit
# Configure PE 2.
[PE2] bgp 100
[PE2-bgp-default] address-family vpnv4
[PE2-bgp-default-vpnv4] peer 1::1 prefix-sid
[PE2-bgp-default-vpnv4] quit
[PE2-bgp-default] ip vpn-instance vpn1
[PE2-bgp-default-vpn1] address-family ipv4 unicast
[PE2-bgp-default-ipv4-vpn1] segment-routing ipv6 best-effort
[PE2-bgp-default-ipv4-vpn1] quit
[PE2-bgp-default-vpn1] quit
[PE2-bgp-default] quit
# Display BGP VPNv4 routing information on each PE and verify that the routes advertised by the PEs have the SID attribute. This step uses PE 1 as an example.
[PE1] display bgp routing-table vpnv4 10.2.1.0
BGP local router ID: 1.1.1.1
Local AS number: 100
Route distinguisher: 100:1(vpn1)
Total number of routes: 1
Paths: 1 available, 1 best
BGP routing table information of 10.2.1.0/24:
From : 3::3 (3.3.3.3)
Rely nexthop : FE80::2A96:34FF:FE9D:216
Original nexthop: 3::3
Out interface : Vlan-interface13
Route age : 00h14m23s
OutLabel : 3
Ext-Community : <RT: 111:1>
RxPathID : 0x0
TxPathID : 0x0
PrefixSID : End.DT4 SID <6:5::101>
AS-path : 65420
Origin : incomplete
Attribute value : MED 0, localpref 100, pref-val 0
State : valid, internal, best
IP precedence : N/A
QoS local ID : N/A
Traffic index : N/A
Tunnel policy : NULL
Rely tunnel IDs : N/A
Verifying the configuration
# Display IPv4 routing table information on the PEs and verify that each PE has a route destined for the remote CE and the next hop of the route is the End.DT4 SID of the route. This step uses PE 1 as an example.
[PE1] display ip routing-table vpn-instance vpn1
Destinations : 11 Routes : 11
Destination/Mask Proto Pre Cost NextHop Interface
0.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.0/24 Direct 0 0 10.1.1.1 Vlan12
10.1.1.0/32 Direct 0 0 10.1.1.1 Vlan12
10.1.1.1/32 Direct 0 0 127.0.0.1 InLoop0
10.1.1.255/32 Direct 0 0 10.1.1.1 Vlan12
10.2.1.0/24 BGP 255 0 6:5:: Vlan13
127.0.0.0/8 Direct 0 0 127.0.0.1 InLoop0
127.0.0.0/32 Direct 0 0 127.0.0.1 InLoop0
127.0.0.1/32 Direct 0 0 127.0.0.1 InLoop0
127.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
255.255.255.255/32 Direct 0 0 127.0.0.1 InLoop0
# Verify that CE 1 and CE 2 can ping each other. (Details not shown.)