- Table of Contents
-
- 19-Security Configuration Guide
- 00-Preface
- 01-Object group configuration
- 02-Keychain configuration
- 03-Public key management
- 04-PKI configuration
- 05-Crypto engine configuration
- 06-SSH configuration
- 07-SSL configuration
- 08-Security zone configuration
- 09-Packet filter configuration
- 10-ASPF configuration
- 11-Security policy configuration
- 12-Session management
- 13-ARP attack protection configuration
- 14-ND attack defense configuration
- 15-Attack detection and prevention configuration
- 16-mGRE configuration
- 17-Connection limit configuration
- 18-IP-based attack prevention configuration
- 19-IP source guard configuration
- 20-uRPF configuration
- 21-APR configuration
- 22-FIPS configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 14-ND attack defense configuration | 88.63 KB |
Contents
ND attack defense tasks at a glance
Enabling source MAC consistency check for ND messages
Enabling SNMP notifications for ND
Configuring ND keepalive entry scanning
About ND keepalive entry scanning
Configuring ND keepalive entry scanning
Display and maintenance commands for ND keepalive entry scanning
Configuring ND attack defense
About ND attack defense
IPv6 Neighbor Discovery (ND) attack defense is able to identify forged ND messages to prevent ND attacks.
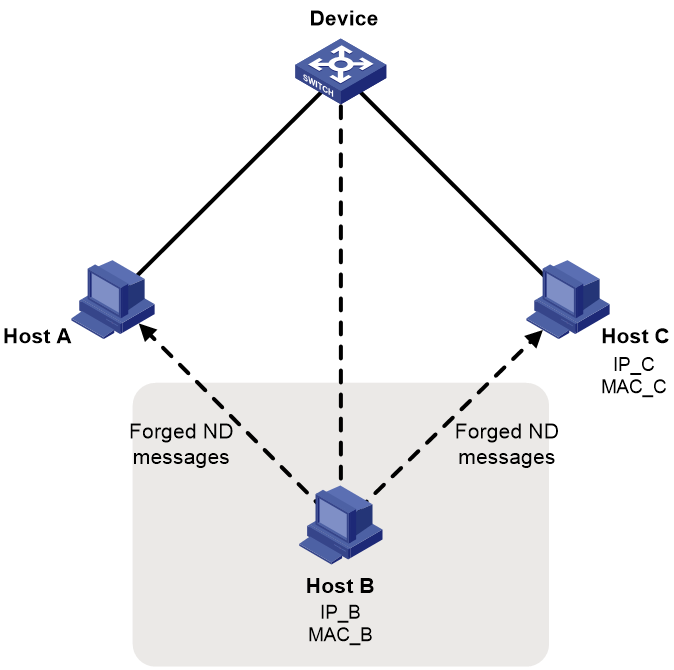
The IPv6 ND protocol does not provide any security mechanisms and is vulnerable to network attacks. As shown in Figure 1, an attacker can send the following forged ICMPv6 messages to perform ND attacks:
· Forged NS/NA/RS messages with an IPv6 address of a victim host. The gateway and other hosts update the ND entry for the victim with incorrect address information. As a result, all packets intended for the victim are sent to the attacking terminal.
· Forged RA messages with the IPv6 address of a victim gateway. As a result, all hosts attached to the victim gateway maintain incorrect IPv6 configuration parameters and ND entries.
ND attack defense tasks at a glance
The following ND attack defense tasks are optional.
· Enabling source MAC consistency check for ND messages
· Enabling SNMP notifications for ND
· Configuring ND keepalive entry scanning
Enabling source MAC consistency check for ND messages
About this task
The source MAC consistency check feature is typically configured on gateways to prevent ND attacks.
This feature checks the source MAC address and the source link-layer address for consistency for each arriving ND message.
· If the source MAC address and the source link-layer address are not the same, the device drops the packet.
· If the addresses are the same, the device continues learning ND entries.
The ND logging feature logs source MAC inconsistency events, and it sends the log messages to the information center. The information center can then output log messages from different source modules to different destinations. For more information about the information center, see System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable source MAC consistency check for ND messages.
ipv6 nd mac-check enable
By default, source MAC consistency check is disabled for ND messages.
3. (Optional.) Enable the ND logging feature.
ipv6 nd check log enable
By default, the ND logging feature is disabled.
As a best practice, disable the ND logging feature to avoid excessive ND logs.
Enabling ND scanning
About this task
The device automatically creates ND entries by NS and NA messages when triggered by traffic. If no traffic is received or sent in a period of time, the ND entries cannot be created or updated in time.
To resolve this issue, you can enable the automatic ND scanning feature on the device. This feature enables the device to periodically send ND packets (NS requests) at a specified rate to the IPv6 addresses not in the specified ND entries.
Restrictions and guidelines
You can specify the source address for the sending NS requests when you enable automatic ND scanning on an interface:
· If you do not specify the source address, the interface uses its IPv6 address as the source address. The interface scans the IPv6 addresses that belong to both the automatic ND scanning range and the subnet of the interface IPv6 address.
If the interface is configured with multiple subnet IPv6 addresses and the addresses are also in the scanning range, the source address is the IPv6 address with the longest prefix. If the prefixes are in the same length, the source address is the primary IPv6 address for the interface.
· If you specify the source address, the interface uses the specified source address, and it scans all the IPv6 addresses in the automatic ND scanning range.
To avoid any impact on device performance, use automatic ND scanning only on networks where users come online and go offline frequently.
Procedure
1. Enter system view.
system-view
2. (Optional.) Set the ND packet sending rate for automatic ND scanning.
ipv6 nd scan auto send-rate { ppm ppm | pps }
By default, the device sends ND packets at the rate of 48 pps during automatic ND scanning.
3. Enter interface view.
interface interface-type interface-number
4. Enable automatic ND scanning.
ipv6 nd scan auto enable start-ipv6-address to end-ipv6-address [ source-addr source-ipv6-address ]
By default, automatic ND scanning is disabled.
Enabling SNMP notifications for ND
About this task
Enable SNMP notifications for ND as required.
· If you enable ND entry limit notifications, the device sends the current ND entry information as a notification to the SNMP module when the number of ND entries exceeds the alarm threshold.
· If you enable endpoint and local device conflict notifications, the device sends a notification to the SNMP module when an endpoint and local device conflict occurs. The notification includes the source IPv6 address, source MAC address, destination IPv6 address, and destination MAC address in the conflicting ND packet.
· If you enable rate limit notifications for sending ND Miss messages and ND packets, the device sends the highest threshold-crossed rate as a notification to the SNMP module. When the device receives an IP packet in which the destination IP address is unresolvable, it sends a ND Miss message to the CPU.
· If you enable user IPv6 address conflict notifications, the device sends a notification to the SNMP module when a user IPv6 address conflict occurs. The notification includes the source IPv6 and MAC addresses in the conflicting ND packet, and MAC address in the corresponding local ND entry.
For ND event notifications to be sent correctly, you must also configure SNMP on the device. For more information, see SNMP configuration in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for ND.
snmp-agent trap enable nd [ entry-limit | local-conflict | nd-miss | user-ip-conflict ] *
By default, SNMP notifications for ND are disabled.
If you do not specify any keywords, this command enables all SNMP notifications for ND.
Configuring ND keepalive entry scanning
About ND keepalive entry scanning
In a large-scale network, it takes a long time for ND scanning to identify the hosts that go offline abnormally if you specify a large scanning range. After you enable ND keepalive entry scanning, the system can quickly locate those hosts and monitor the host status within the aging time.
You can set the aging time for ND keepalive entries in both system view and interface view. The aging time set in interface view takes precedence over the aging time set in system view. In interface view, the default aging time for ND keepalive entries is the aging time set in system view.
When users come online, the system generates dynamic ND entries. Enabled with ND keepalive entry scanning, the system also creates online keepalive entries when users come online. If users go offline, the corresponding ND entries are deleted and the status of the keepalive entries is set to offline. The device sends NS packets at intervals to the IPv6 addresses in the offline keepalive entries until the keepalive entries become online again or are deleted when the aging time expires. The interval varies with the number of NS packets that have been sent to the IPv6 address in an offline keepalive entry.
Configuring ND keepalive entry scanning
1. Enter system view.
system-view
2. (Optional.) Set the NS packet sending rate for keepalive entry scanning.
ipv6 nd scan keepalive send-rate pps
By default, the device sends NS packets at a rate of 48 pps during keepalive entry scanning.
3. (Optional.) Set the aging time for ND keepalive entries.
ipv6 nd scan keepalive aging-time time
By default, the aging time for ND keepalive entries in system view is 60 minutes. The aging time for ND keepalive entries in interface view is the aging time set in system view.
4. Enter interface view.
interface interface-type interface-number
5. Enable the ND keepalive entry scanning feature.
ipv6 nd scan keepalive enable
By default, the ND keepalive entry scanning is disabled on an interface.
Display and maintenance commands for ND keepalive entry scanning
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display ND keepalive entries. |
display ipv6 nd scan keepalive entry [ interface interface-type interface-number ] [ count ] |
|
Display statistics about NS packets sent to the IPv6 addresses in offline keepalive entries. |
display ipv6 nd scan keepalive statistics [ slot slot-number ] [ interface interface-type interface-number ] |
|
Clear statistics about NS packets sent to the IPv6 addresses in offline keepalive entries. |
reset ipv6 nd scan keepalive statistics [ slot slot-number ] |