- Table of Contents
-
- 15-BRAS Services Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-ANCP configuration
- 03-PPP configuration
- 04-Value-added services configuration
- 05-DHCP configuration
- 06-DHCPv6 configuration
- 07-User profile configuration
- 08-Connection limit configuration
- 09-L2TP configuration
- 10-PPPoE configuration
- 11-IPoE configuration
- 12-UCM configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 08-Connection limit configuration | 173.05 KB |
Connection limit tasks at a glance
Creating a connection limit policy
Configuring the connection limit policy
About connection limit policies
Restrictions and guidelines for connection limit policy configuration
Configuring an IPv4 connection limit policy
Configuring an IPv6 connection limit policy
Applying the connection limit policy
About connection limit application
Restrictions and guidelines for connection limit application
Applying a connection limit policy to an interface
Applying a connection limit policy globally
Configuring logging suppression
Display and maintenance commands for connection limits
Connection limit configuration examples
Example: Configuring connection limits
Troubleshooting connection limits
ACLs in the connection limit rules with overlapping segments
Configuring connection limits (user profile-based)
Prerequisites for connection limits
Connection limit configuration examples
Example: Configuring connection limits
Configuring connection limits
About connection limits
The connection limit feature enables the device to monitor and limit the number of established connections.
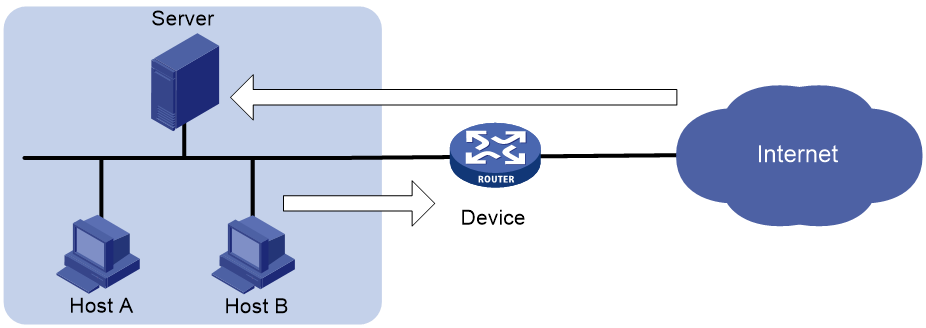
As shown in Figure 1, configure the connection limit feature to resolve the following issues:
· If Host B initiates a large number of connections in a short period of time, it might exhaust system resources and cause Host A to be unable to access the Internet.
· If the internal server receives a large number of connection requests in a short period of time, the server cannot process other requests.
Connection limit tasks at a glance
To configure connection limits, perform the following tasks:
1. Creating a connection limit policy
2. Configuring the connection limit policy
¡ Configuring an IPv4 connection limit policy
¡ Configuring an IPv6 connection limit policy
3. Applying the connection limit policy
¡ Applying a connection limit policy to an interface
¡ Applying a connection limit policy globally
4. Configuring logging suppression
Creating a connection limit policy
1. Enter system view.
system-view
2. Create a connection limit policy and enter its view.
connection-limit { ipv6-policy | policy } policy-id
Configuring the connection limit policy
About connection limit policies
To use a connection limit policy, you need to add limit rules to the policy. Each rule defines a range of connections and the criteria for limiting the connections. Connections in the range will be limited based on the criteria. When the number of matching connections reaches the upper limit, the device does not accept new connections until the number of connections drops below the lower limit. The device will send logs when the number of connections exceeds the upper limit and when the number of connections drops below the lower limit. The connections that do not match any connection limit rules are not limited.
In each connection limit rule, an ACL is used to define the connection range. In addition, the rule also uses the following filtering methods to further limit the connections:
· per-destination—Limits user connections by destination IP address.
· per-service—Limits user connections by service (transport layer protocol and service port).
· per-source—Limits user connections by source IP address.
You can select more than one filtering method, and the selected methods take effect at the same time. For example, if you specify both per-destination and per-service, the user connections using the same service and destined to the same IP address are limited. If you do not specify any filtering methods in a limit rule, all user connections in the range are limited.
Restrictions and guidelines for connection limit policy configuration
When a connection limit policy is applied, connections on the device match all limit rules in the policy in ascending order of rule IDs. As a best practice, specify a smaller range and more filtering methods in a rule with a smaller ID.
Configuring an IPv4 connection limit policy
1. Enter system view.
system-view
2. Create an IPv4 connection limit policy and enter its view.
connection-limit policy policy-id
3. Configure a connection limit rule.
limit limit-id acl { acl-number | name acl-name } [ per-destination | per-service | per-source ] * amount max-amount min-amount
4. (Optional.) Configure a description for the connection limit policy.
description text
By default, an IPv4 connection limit policy does not have a description.
Configuring an IPv6 connection limit policy
1. Enter system view.
system-view
2. Create an IPv6 connection limit policy and enter its view.
connection-limit ipv6-policy policy-id
3. Configure a connection limit rule.
limit limit-id acl ipv6 { acl-number | name acl-name } [ per-destination | per-service | per-source ] * amount max-amount min-amount
4. (Optional.) Configure a description for the connection limit policy.
description text
By default, an IPv6 connection limit policy does not have a description.
Applying the connection limit policy
About connection limit application
To make a connection limit policy take effect, apply it globally or to an interface. The connection limit policy applied to an interface takes effect only on the specified connections on the interface. The connection limit policy applied globally takes effect on all the specified connections on the device.
Different connection limit policies can be applied to individual interfaces as well as globally on the device. In this case, the device matches connections against these policies in the order of the policy on the inbound interface, the global policy, and the policy on the outbound interface. It cannot accept new connections as long as the number of connections reaches the smallest upper connection limit defined by these policies.
Restrictions and guidelines for connection limit application
A connection limit policy or its modification takes effect only on new connections. It does not take effect on existing connections.
On an IRF fabric where session synchronization is enabled, connection limit policies applied to a subordinate device do not take effect on sessions switched from the master device.
Applying a connection limit policy to an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Apply a connection limit policy to the interface.
connection-limit apply { ipv6-policy | policy } policy-id
By default, no connection limit policy is applied to an interface.
Only one IPv4 connection limit policy and one IPv6 connection limit policy can be applied to an interface. A new IPv4 or IPv6 connection limit policy overwrites the old policy.
Applying a connection limit policy globally
1. Enter system view.
system-view
2. Apply a connection limit policy globally.
connection-limit apply global { ipv6-policy | policy } policy-id
By default, no connection limit policy is applied globally.
Only one IPv4 connection limit policy and one IPv6 connection limit policy can be applied globally. A new IPv4 or IPv6 connection limit policy overwrites the old policy.
Configuring logging suppression
About this task
By default, the device records a log message each time a connection limit rule is matched. If a connection limit rule is matched frequently in a short period after the upper limit is reached, the device records a large number of repeated log messages for the rule. This feature suppresses the generation of repeated log messages for the same rule in the specified period.
Procedure
1. Enter system view.
system-view
2. Set the logging suppression interval.
connection-limit log-suppress interval time-value
By default, connection limit log messages are not suppressed.
Display and maintenance commands for connection limits
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the connection limit policy information. |
display connection-limit { ipv6-policy | policy } { all | policy-id } |
|
Display the connection limit statistics globally or on an interface. |
display connection-limit statistics { global | interface interface-type interface-number | user-id user-id } [ slot slot-number ] |
|
Display statistics about connections matching connection limit rules globally or on an interface. |
display connection-limit ipv6-stat-nodes { global | interface interface-type interface-number } [ slot slot-number ] [ destination destination-ip | service-port port-number | source source-ip ] * [ count ] |
|
Clear the connection limit statistics globally or on an interface. |
reset connection-limit statistics { global | interface interface-type interface-number } [ slot slot-number ] |
Connection limit configuration examples
Example: Configuring connection limits
Network configuration
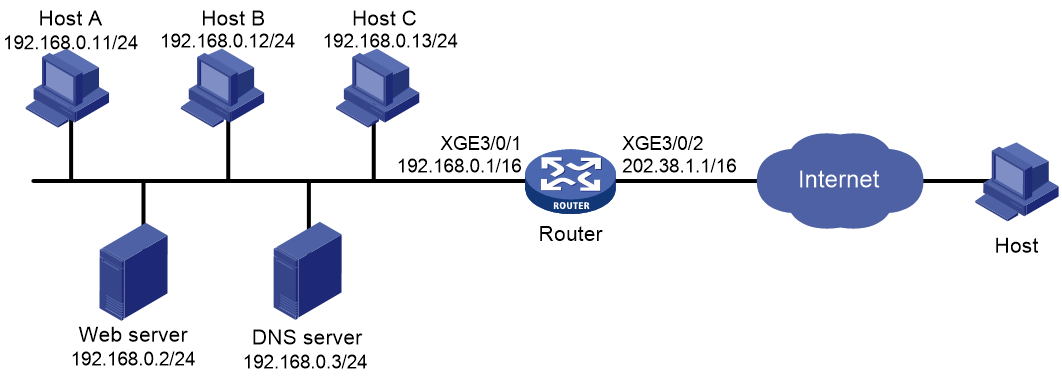
As shown in Figure 2, a company has five public IP addresses: 202.38.1.1/24 to 202.38.1.5/24. The internal network address is 192.168.0.0/16. Configure NAT so that the internal users can access the Internet and external users can access the internal servers. Configure connection limits to meet the following requirements:
· All hosts on segment 192.168.0.0/24 can establish a maximum of 100000 connections to the external network.
· Each host on segment 192.168.0.0/24 can establish a maximum of 100 connections to the external network.
· A maximum of 10000 query requests from DNS clients to the DNS server are allowed at the same time.
· A maximum of 10000 connection requests from Web clients to the Web server are allowed at the same time.
Restrictions and guidelines
The following example only describes how to configure connection limits. For information about NAT configuration and internal server configuration, see NAT Configuration Guide.
Procedure
# Create ACL 3000 to permit packets from all hosts on the internal network.
<Router> system-view
[Router] acl advanced 3000
[Router-acl-ipv4-adv-3000] rule permit ip source 192.168.0.0 0.0.0.255
[Router-acl-ipv4-adv-3000] quit
# Create ACL 3001 to permit packets to the Web server and the DNS server.
[Router] acl advanced 3001
[Router-acl-ipv4-adv-3001] rule permit ip destination 192.168.0.2 0
[Router-acl-ipv4-adv-3001] rule permit ip destination 192.168.0.3 0
[Router-acl-ipv4-adv-3001] quit
# Create connection limit policy 1.
[Router] connection-limit policy 1
# Configure connection limit rule 1 to permit a maximum of 100000 connections from all the hosts that match ACL 3000. When the number of connections exceeds 100000, new connections cannot be established until the number drops below 95000.
[Router-connection-limit-policy-1] limit 1 acl 3000 amount 100000 95000
# Configure connection limit rule 2 to permit a maximum of 10000 connections to the servers that match ACL 3001. When the number of connections exceeds 10000, new connections cannot be established until the number drops below 9800.
[Router-connection-limit-policy-1] limit 2 acl 3001 per-destination amount 10000 9800
[Router-connection-limit-policy-1] quit
# Create connection limit policy 2.
[Router] connection-limit policy 2
# Configure connection limit rule 1 to permit a maximum of 100 connections from each host matching ACL 3000. When the number of connections exceeds 100, new connections cannot be established until the number drops below 90.
[Router-connection-limit-policy-2] limit 1 acl 3000 per-source amount 100 90
[Router-connection-limit-policy-2] quit
# Apply connection limit policy 1 globally.
[Router] connection-limit apply global policy 1
# Apply connection limit policy 2 to inbound interface Ten-GigabitEthernet 3/0/1.
[Router] interface ten-gigabitethernet 3/0/1
[Router-Ten-GigabitEthernet3/0/1] connection-limit apply policy 2
[Router-Ten-GigabitEthernet3/0/1] quit
Verifying the configuration
# Display information about the connection limit policy.
[Router] display connection-limit policy 1
IPv4 connection limit policy 1 has been applied 1 times, and has 2 limit rules.
Limit rule list:
Policy Rule StatType HiThres LoThres ACL
------------------------------------------------------------
1 1 -- 100000 95000 3000
2 Dst 10000 9800 3001
Applied list:
Global
[Router] display connection-limit policy 2
IPv4 connection limit policy 2 has been applied 1 times, and has 1 limit rules.
Limit rule list:
Policy Rule StatType HiThres LoThres ACL
------------------------------------------------------------
2 1 Src 100 90 3000
Applied list:
Ten-GigabitEthernet3/0/1
Troubleshooting connection limits
ACLs in the connection limit rules with overlapping segments
Symptom
A connection limit policy has two rules. Rule 1 sets the upper limit to 10 for the connections from each host on segment 192.168.0.0/24. Rule 2 sets the upper limit to 100 for the connections from 192.168.0.100/24.
<Device> system-view
[Device] acl basic 2001
[Device-acl-ipv4-basic-2001] rule permit source 192.168.0.0 0.0.0.255
[Device-acl-ipv4-basic-2001] quit
[Device] acl basic 2002
[Device-acl-ipv4-basic-2002] rule permit source 192.168.0.100 0
[Device-acl-ipv4-basic-2002] quit
[Device] connection-limit policy 1
[Device-connection-limit-policy-1] limit 1 acl 2001 per-destination amount 10 5
[Device-connection-limit-policy-1] limit 2 acl 2002 per-destination amount 100 10
[Device-connection-limit-policy-1] quit
As a result, the host at 192.168.0.100 can only initiate a maximum of 10 connections to the external network.
Solution
To resolve the issue:
1. Rearrange the two connection limit rules by exchanging their rule IDs.
2. If the issue persists, contact H3C Support.
Configuring connection limits (user profile-based)
About connection limits
The connection limit feature enables the device to assign user profiles to control the number of established connections and establishment rate on a per-user basis. This feature facilitates accurate allocation of system resources and improves access efficiency when multiple users are present.
After the user passes authentication, the device checks the associated user profile, and performs either of the following actions:
· If the user profile exists and has a connection limit policy in its view, the device restricts user access according to the connection limit policy.
· If no user profile exists or the user profile does not have a connection limit policy, the device allows user access without limiting the connections initiated by the user.
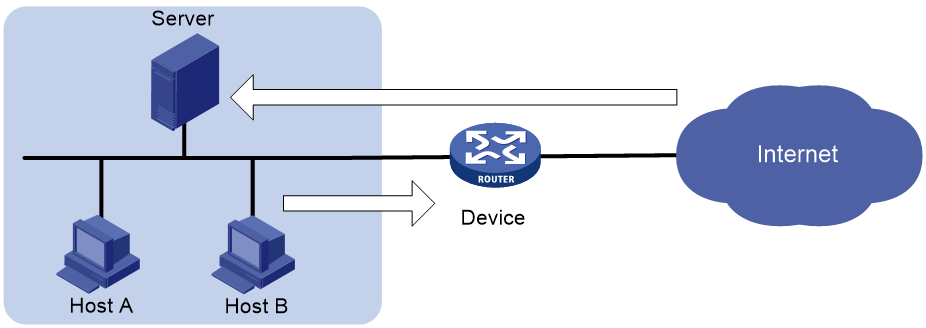
As shown in Figure 3, configure the connection limit feature to resolve the following issues:
· If Host B initiates a large number of connections in a short period of time, it might exhaust system resources and cause Host A to be unable to access the Internet.
· If the internal server receives a large number of connection requests in a short period of time, the server cannot process other requests.
Prerequisites for connection limits
The connection limit feature must work with an authentication server.
Before configuring connection limits, complete either of the following tasks:
· For remote authentication, specify the user profile to be associated with the user's account on the remote server.
· For local authentication, specify the user's authorized user profile in local user view on the device. For information about configuring local users, see "Configuring AAA."
Configuring connection limits
1. Enter system view.
system-view
2. Create a user profile and enter user profile view.
user-profile profile-name
For more information about this command, see BRAS Services Command Reference.
3. Set the maximum number of user connections.
connection-limit amount amount
By default, the number of user connections is not limited.
If you execute this command multiple times, the most recent configuration takes effect. If the configured maximum number is smaller than the current number of connections, the configuration takes effect after the number of non-aged connections is smaller than the configured maximum number.
4. Set the maximum connection establishment rate.
connection-limit rate rate
By default, the connection establishment rate is not limited.
5. (Optional.) Display user profile configuration and online user information.
display user-profile [ name profile-name ] [ slot slot-number ]
For more information about this command, see BRAS Services Command Reference.
Connection limit configuration examples
Example: Configuring connection limits
Network configuration
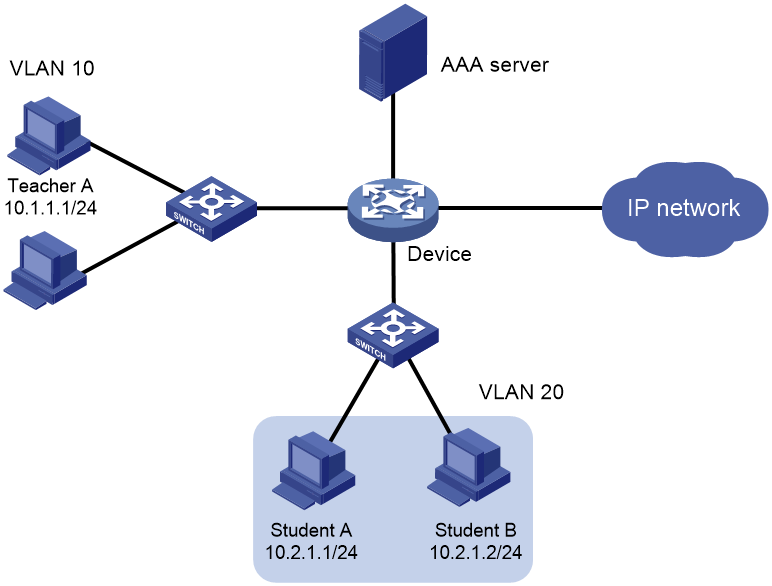
As shown in Figure 4, all users must pass AAA authentication before they can access the public network. To ensure higher priority for Teacher A's connections than students' connections, perform the following tasks on the device:
· Limit Teacher A to establish a maximum of 100 connections to the public network.
· Limit each student to establish a maximum of 10 connections to the public network.
Procedure
1. Configure the AAA server.
# Configure accounts for the teacher and the students. Specify the associated user profile names of the teacher and the students as teacher and student, respectively. (Details not shown.)
2. Configure the device.
# Configure AAA authentication. (Details not shown.)
# Create user profile teacher, and set the maximum number of connections to 100.
<Device> system-view
[Device] user-profile teacher
[Device-user-profile-teacher] connection-limit amount 100
[Device-user-profile-teacher] quit
# Create user profile student, and set the maximum number of connections to 10.
[Device] user-profile student
[Device-user-profile-student] connection-limit amount 10
[Device-user-profile-student] quit
Verifying the configuration
# Display configuration information about the user profile-based connection limits.
[Device] display user-profile
User-Profile: teacher
Connection-limit amount: 100
User-Profile: student
Connection-limit amount: 10
The output shows that the teacher and students can establish only 100 and 10 connections, respectively, to the public network after they pass authentication.