- Table of Contents
-
- 13-Security Configuration Guide
- 00-Preface
- 01-DAE proxy configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-IP-based attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-SAVA configuration
- 18-SAVA-P configuration
- 19-Crypto engine configuration
- 20-SMA configuration
- 21-Trust level configuration
- 22-Encryption card user management configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 22-Encryption card user management configuration | 171.02 KB |
Contents
Encryption card user management
About encryption card user management
Restrictions and guidelines: Encryption card user management
Encryption card user management tasks at a glance
Backing up the data on the encryption card
Restoring encryption card data
Clearing the operator information and key information on the encryption card
Configuring the administrator authorizations on data restoration to an encryption card
Restoring the backup data to another encryption card
Display and maintenance commands for encryption card user management
Encryption card user management configuration examples
Example: Configuring basic encryption card user management
Encryption card user management
About encryption card user management
Encryption card user management is a feature for user permission management. In collaboration with network data encryption service processing unit (encryption service base card) and network data encryption card (encryption card), it uses SM algorithms (SM2, SM3, and SM4) to protect the transmitted user data.
Encryption card user role
An encryption card is equipped with six USB keys from factory. You can assign the following user roles to the encryption card with the USB keys:
· Administrator—Administrators have the highest management permissions. The administrators can add or delete operators, change operators' passwords, generate or destroy local SM2 key pairs, and clear the information on the encryption card.
You must add three administrators for one encryption card. To operate on the encryption card, two administrators must have logged in to the encryption card.
· Operator—Operators can use SM algorithms to protect user data. The configurations related to SM algorithms take effect only after operators log in to the encryption card. For more information about SM2, SM3, and SM4 algorithms, see IPsec commands in Security Command Reference.
An encryption card allows only one operator to log in at a time.
To add an administrator or operator, plug a USB key into the encryption card and assign the corresponding user role.
You can use the USB keys not assigned with user roles to back up the data on the encryption card.
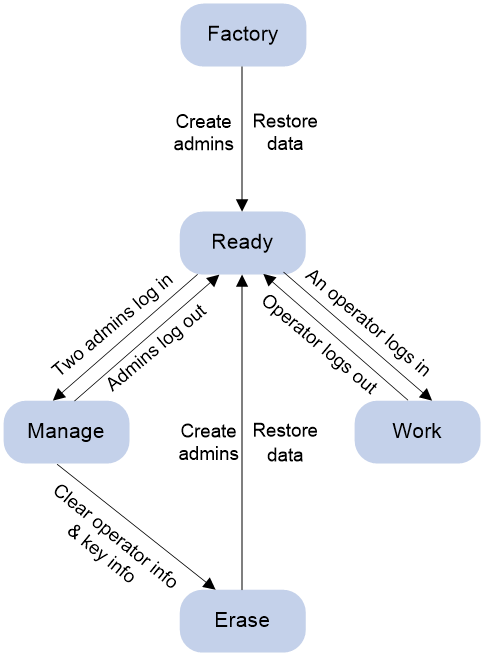
Encryption card state
You can perform the corresponding operations when the encryption card is in specific states. The state change mechanism of the encryption card is as follows:
Figure 1 Encryption card state change mechanism
Table 1 shows different states of the encryption card.
Table 1 Encryption card states
|
State |
Executable operations |
|
Factory |
· Create administrators. · Administrators authorize data restoration to an encryption card. · Restore the data on a backup USB key to another encryption card. |
|
Ready |
· Administrators can log in to the encryption card. · Operators can log in to the encryption card. |
|
Manage |
· Create operators. · Delete all operators of the encryption card. · Change operators' passwords. · Generate or destroy local SM2 key pairs. For more information the configuration details, see public key management in Security Configuration Guide. · Clear the operator information and key information on the encryption card. · Back up all data on the encryption card to the backup USB key. |
|
Work |
Use SM algorithms to protect the transmitted user data. For more information about the SM algorithms, see IPsec configuration in Security Configuration Guide. |
|
Erase |
· Administrators authorize data restoration to an encryption card. · Restore the data on a backup USB key to another encryption card. · Create new administrators to overwrite existing ones. |
Restrictions and guidelines: Encryption card user management
For successful configuration, make sure the USB keys are inserted into the USB AUTH ports on MIC-SM interface subcards.
The written data on the USB keys of an encryption card cannot be erased. The USB keys for an encryption card cannot be used for another encryption card. To clear data on the USB keys, contact H3C Support.
Encryption card user management tasks at a glance
To configure encryption card user management, perform the following tasks:
1. Adding encryption card users
4. (Optional.) Changing operators' passwords
5. (Optional.) Deleting all operators
6. (Optional.) Backing up the data on the encryption card
7. Restore the backup data to another encryption card:
¡ Clearing the operator information and key information on the encryption card
This task is required when user information and key information exist on the target encryption card.
¡ Configuring the administrator authorizations on data restoration to an encryption card
¡ Restoring the backup data to another encryption card
Adding encryption card users
About this task
You must add administrators and operators for an encryption card. To add users for an encryption card, perform the following operations:
1. Plug a new USB key into the encryption card.
2. Assign a user role for the USB key and set the login password.
3. Unplug the USB key with the assigned user role.
4. Repeat the previous steps to add all needed users.
Restrictions and guidelines
You must add three administrators for one encryption card.
The user roles assigned to the USB keys for an encryption card cannot be changed.
To successfully create administrators for an encryption card, make sure the encryption service base card and the encryption card work normally.
To create operators for an encryption card, make sure you have created three administrators for the encryption card and the encryption card has two login administrators.
Procedure
1. Enter system view.
system-view
2. Add an administrator or operator for the encryption card, and set the login password.
In standalone mode:
encryption-card add user role { admin | operator } slot slot-number
In IRF mode:
encryption-card add user role { admin | operator } chassis chassis-number slot slot-number
Configuring user login
About this task
You can configure users to log in to the encryption card.
To manage operators and key information, make sure you have created three administrators for the encryption card and the encryption card has two login administrators. To configure administrators to log in:
1. Plug an administrator USB key into the encryption card.
3. Unplug the administrator USB key.
4. Plug another administrator USB key into the encryption card.
5. Repeat steps 2 and 3 to configure the second administrator to log in.
For an operator to log in, make sure you have created the administrators and the operator. Only one operator can log in to the encryption card at a time. To configure an operator to log in:
1. Plug an operator USB key into the encryption card.
2. Enter the password set when the operator is created to configure the operator to log in.
3. Unplug the operator USB key.
Restrictions and guidelines
An administrator and an operator cannot both log in to the encryption card.
Procedure
1. Enter system view.
system-view
2. Configure an administrator or operator to log in to the encryption card.
In standalone mode:
encryption-card login user-role { admin | operator } slot slot-number
In IRF mode:
encryption-card login user-role { admin | operator } chassis chassis-number slot slot-number
Configuring user logout
Restrictions and guidelines
To configure all administrators or operators to log out the encryption card, no USB key needs to be plugged in.
Procedure
1. Enter system view.
system-view
2. Configure all administrators or operators to log out the encryption card.
In standalone mode:
encryption-card logout user-role { admin | operator } slot slot-number
In IRF mode:
encryption-card logout user-role { admin | operator } chassis chassis-number slot slot-number
Changing operators' passwords
Restrictions and guidelines
To change an operator's password, make sure the encryption card has two login administrators and the operator USB key is plugged in the encryption card.
Procedure
1. Enter system view.
system-view
2. Change an operator's password.
In standalone mode:
encryption-card operator change-password slot slot-number
In IRF mode:
encryption-card operator change-password chassis chassis-number slot slot-number
Deleting all operators
Restrictions and guidelines
To delete all operators of an encryption card, make sure the encryption card has two login administrators. No USB key needs to be plugged in.
Procedure
1. Enter system view.
system-view
In standalone mode:
encryption-card delete operator slot slot-number
In IRF mode:
encryption-card delete operator chassis chassis-number slot slot-number
Backing up the data on the encryption card
About this task
For data security, you can back up all data (including user information and key information) on the encryption card to a new USB key.
To back up encryption card data:
1. Configure two administrators to log in to the encryption card. For more information, see "Configuring user login."
2. Plug a new USB key into the encryption card.
3. Back up the data on the encryption card to the USB key.
4. Unplug the USB key.
Restrictions and guidelines
To back up encryption card data, make sure the encryption card has two login administrators and a new USB key for data backup is plugged in.
Procedure
1. Enter system view.
system-view
2. Back up the data on the encryption card to the backup USB key.
In standalone mode:
encryption-card backup info slot slot-number
In IRF mode:
encryption-card backup info chassis chassis-number slot slot-number
Restoring encryption card data
In case of card fault, restore the backup data of an old encryption card to another encryption card.
To restore the backup data to a new encryption card:
1. Make sure the encryption service base card is powered off, and then uninstall the old encryption card and install the new encryption card.
2. Power on the encryption service base card, and make sure the encryption service base card and the new encryption card work normally.
3. Plug an administrator USB key of the old encryption card into the new encryption card.
4. Configure the administrator to authorize encryption card data restoration (by using the encryption-card admin-authorization restoration command), and enter the login password of the administrator.
5. Unplug the administrator USB key.
6. Plug another administrator USB key of the old encryption card into the new encryption card.
7. Repeat step 4 to configure encryption card data restoration authorization by the second administrator.
8. Unplug the second administrator USB key.
9. Plug the backup USB key of the old encryption card into the new encryption card.
10. Use the encryption-card restore info command to restore the backup data to the new encryption card.
11. Unplug the backup USB key after data restoration.
To restore the backup data to a reused encryption card:
1. Make sure the encryption service base card is powered off, and then uninstall the old encryption card and install the reused encryption card.
2. Power on the encryption service base card, and make sure the encryption service base card and the reused encryption card work normally.
3. Configure two administrators of the reused encryption card to log in. For more information, see "Configuring user login."
4. Clear the operator information and key information on the reused encryption card (by using the encryption-card delete info command).
The state of the reused encryption card changes from Manage to Erase.
5. Plug an administrator USB key of the old encryption card into the reused encryption card.
6. Configure the administrator to authorize encryption card data restoration (by using the encryption-card admin-authorization restoration command), and enter the login password of the administrator.
7. Unplug the administrator USB key.
8. Plug another administrator USB key of the old encryption card into the reused encryption card.
9. Repeat step 6 to configure encryption card data restoration authorization by the second administrator.
10. Unplug the second administrator USB key.
11. Plug the backup USB key of the old encryption card into the reused encryption card.
12. Use the encryption-card restore info command to restore the backup data to the reused encryption card.
13. Unplug the backup USB key after data restoration.
Clearing the operator information and key information on the encryption card
Restrictions and guidelines
To clear the operator information and key information on an encryption card, make sure the encryption card has two login administrators. No USB key needs to be plugged in.
The clear operation will cause the factory-equipped USB keys of the encryption card unable to work. The cleared data cannot be restored. Before performing the clear operation, determine whether to back up the data on the encryption card.
Procedure
1. Enter system view.
system-view
2. Clear the operator information and key information on the encryption card.
In standalone mode:
encryption-card delete info slot slot-number
In IRF mode:
encryption-card delete info chassis chassis-number slot slot-number
Configuring the administrator authorizations on data restoration to an encryption card
About this task
Before restoring the backup data of the old encryption card to another encryption card (by using the encryption-card restore info command), you must configure the administrators of the old encryption card to authorize encryption card data restoration to the target encryption card.
Restrictions and guidelines
This feature is supported only when the encryption card is in Factory or Erase state.
For successful data restoration to the target encryption card, it must have the authorization of two administrators.
Procedure
1. Enter system view.
system-view
2. Configure an administrator to authorize encryption card data restoration.
In standalone mode:
encryption-card admin-authorization restoration slot slot-number
In IRF mode:
encryption-card admin-authorization restoration chassis chassis-number slot slot-number
Restoring the backup data to another encryption card
About this task
You can use this feature to restore the data from a backup USB key of an encryption card to another encryption card.
Restrictions and guidelines
This feature is supported only when the encryption card is in Factory or Erase state.
Before restoring the backup data to another encryption card, you must perform the following operations:
1. Plug an administrator USB key of the old encryption card into the target encryption card.
2. Configure the administrator to authorize encryption card data restoration on the target encryption card (by using the encryption-card admin-authorization restoration command).
3. Unplug the administrator USB key.
4. Repeat the above steps for the second administrator USB key of the old encryption card.
Procedure
1. Enter system view.
system-view
2. Restore the backup data on a backup USB key to the specified encryption card.
In standalone mode:
encryption-card restore info slot slot-number
In IRF mode:
encryption-card restore info chassis chassis-number slot slot-number
Display and maintenance commands for encryption card user management
Execute the display command in any view.
|
Task |
Command |
|
Display the state of the encryption card. |
In standalone mode: display encryption-card state slot slot-number In IRF mode: display encryption-card state chassis chassis-number slot slot-number |
Encryption card user management configuration examples
Example: Configuring basic encryption card user management
Network configuration
As shown in Figure 2, configure the devices to meet the following requirements:
· Use SM algorithms to encrypt and decrypt data transmitted between the devices.
· Back up the encryption card data on Device B.
· When the encryption card on Device B fails, replace the card with a new encryption card. Then, restore the backup data to the new encryption card of Device B.
Prerequisites
Install an encryption service base card and an encryption card on each of Device A and Device B. Make sure the cards work normally. (Details not shown.)
Configuring Device A
1. Add three administrators for the encryption card of Device A:
# Plug a new USB key into the encryption card.
# Specify the user role as administrator for the USB key and set the login password.
<DeviceA> system-view
[DeviceA] encryption-card add user role admin slot 1
The USB key is steady. Continue? [Y/N]:y
Enter password:
Confirm password:
Operation succeeded.
# Unplug the USB key.
# Plug the second new USB key into the encryption card. Specify the user role as administrator and set the login password.
[DeviceA] encryption-card add user role admin slot 1
The USB key is steady. Continue? [Y/N]:y
Enter password:
Confirm password:
Operation succeeded.
# Unplug the second USB key.
# Plug the third new USB key into the encryption card. Specify the user role as administrator and set the login password.
[DeviceA] encryption-card add user role admin slot 1
The USB key is steady. Continue? [Y/N]:y
Enter password:
Confirm password:
Operation succeeded.
# Unplug the third USB key.
2. Configure two administrators to log in to the encryption card:
# Plug an administrator USB key into the encryption card.
# Configure the administrator to log in.
[DeviceA] encryption-card login user-role admin slot 1
The USB key is steady. Continue? [Y/N]: y
Password:
Operation succeeded.
# Unplug the administrator USB key.
# Plug another administrator USB key into the encryption card.
# Configure the second administrator to log in.
[DeviceA] encryption-card login user-role admin slot 1
The USB key is steady. Continue? [Y/N]: y
Password:
Operation succeeded.
# Unplug the second administrator USB key.
3. Add an operator for the encryption card of Device A:
# Plug a new USB key into the encryption card.
# Specify the user role as operator for the USB key and set the login password.
[DeviceA] encryption-card add user role operator slot 1
The USB key is steady. Continue? [Y/N]:y
Enter password:
Confirm password:
Operation succeeded.
# Unplug the USB key.
4. Log all administrators out of the encryption card.
[DeviceA] encryption-card logout user-role admin slot 1
The admin logout operation success!
5. Configure the operator to log in to the encryption card:
# Plug the operator USB key into the encryption card.
# Configure the operator to log in.
[DeviceA] encryption-card login user-role operator slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the operator USB key.
Configuring Device B
Repeat steps 1 to 6 in "Configuring Device A."
7. Back up the data on the encryption card of Device B:
# Configure two administrators to log in to the encryption card. For more information, see step 2 in "Configuring Device A."
# Plug a new USB key into the encryption card.
# Back up the data on the encryption card to the USB key.
[DeviceB] encryption-card backup info slot 1
The USB key is steady. Continue? [Y/N]:y
Enter password:
Confirm:
Operation succeeded.
# Unplug the backup USB key.
8. Replace the old encryption card of Device B with a new encryption card:
# Make sure the encryption service base card of Device B is powered off, and then uninstall the old encryption card and install the new encryption card on Device B.
# Power on the encryption service base card of Device B, and make sure the encryption service base card and the new encryption card work normally.
9. Restore the backup data to the new encryption card of Device B:
# Plug an administrator USB key of the old encryption card into the new encryption card.
# Configure the administrator to authorize encryption card data restoration.
[DeviceB] encryption-card admin-authorization restoration slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the administrator USB key.
# Plug another administrator USB key of the old encryption card into the new encryption card.
# Configure the second administrator to authorize encryption card data restoration.
[DeviceB] encryption-card admin-authorization restoration slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the second administrator USB key.
# Plug the data backup USB key into the new encryption card.
# Restore the backup data to the new encryption card.
[DeviceB] encryption-card restore info slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the backup USB key after data restoration.
Verifying the configuration
Verify that you can use the USB keys of the old encryption card on the new encryption card of Device B.
# Plug an administrator USB key of the old encryption card into the new encryption card.
# Configure the administrator to log in to the new encryption card.
[DeviceB] encryption-card login user-role admin slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the administrator USB key.
# Plug another administrator USB key of the old encryption card into the new encryption card, and configure the second administrator to log in to the new encryption card.
[DeviceB] encryption-card login user-role admin slot 1
The USB key is steady. Continue? [Y/N]:y
Password:
Operation succeeded.
# Unplug the second administrator USB key.
The output shows that the administrators of the old encryption card can log in to and manage the new encryption card.