- Table of Contents
-
- 13-Security Configuration Guide
- 00-Preface
- 01-DAE proxy configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-IP-based attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-SAVA configuration
- 18-SAVA-P configuration
- 19-Crypto engine configuration
- 20-SMA configuration
- 21-Trust level configuration
- 22-Encryption card user management configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 20-SMA configuration | 204.88 KB |
Restrictions and guidelines: Configuring SMA
Display and maintenance commands for SMA
Configuring SMA
About SMA
State Machine Based Anti-Spoofing (SMA) prevents IPv6 spoofing attacks between autonomous systems by verifying source IPv6 addresses.
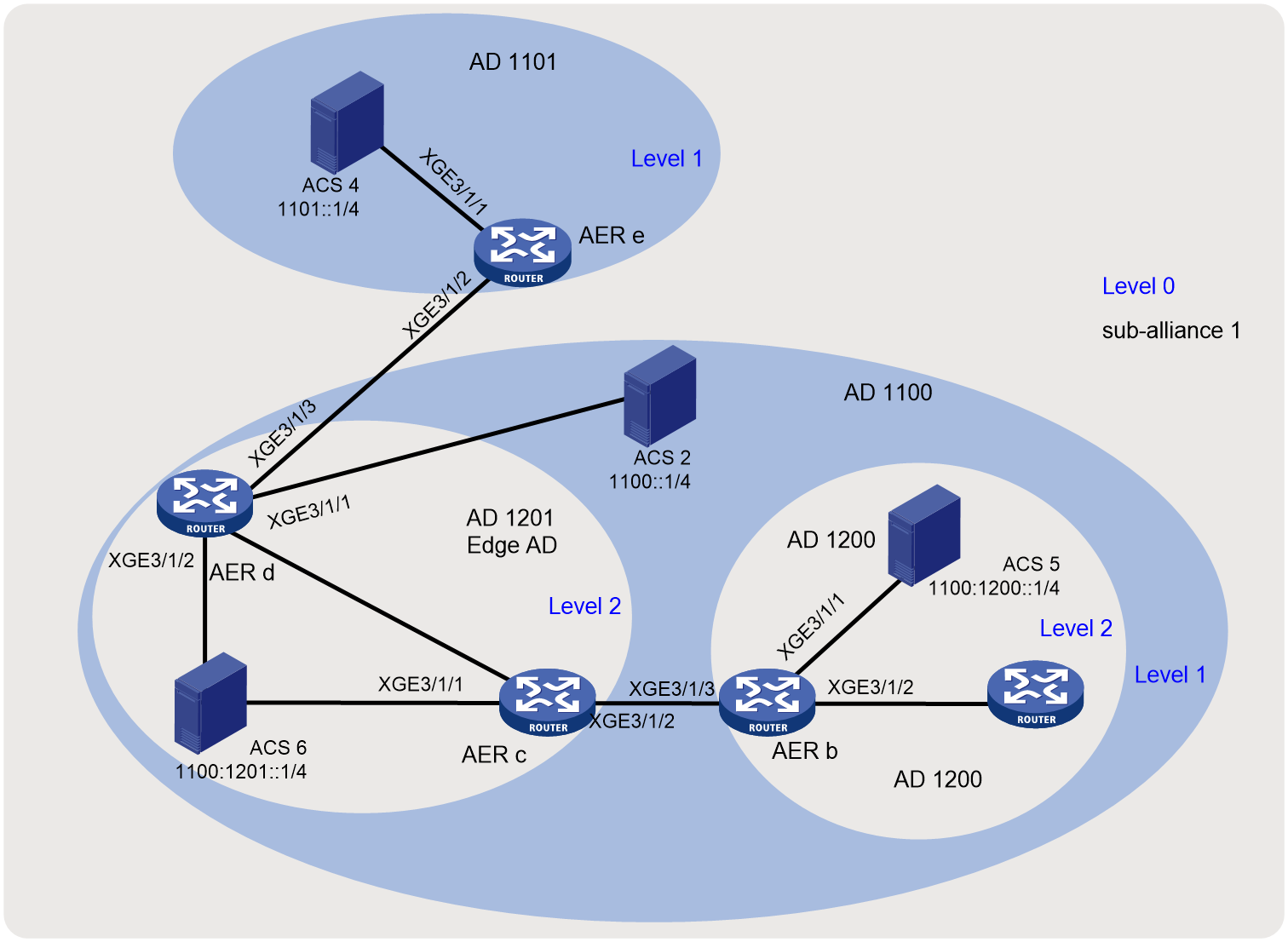
SMA network
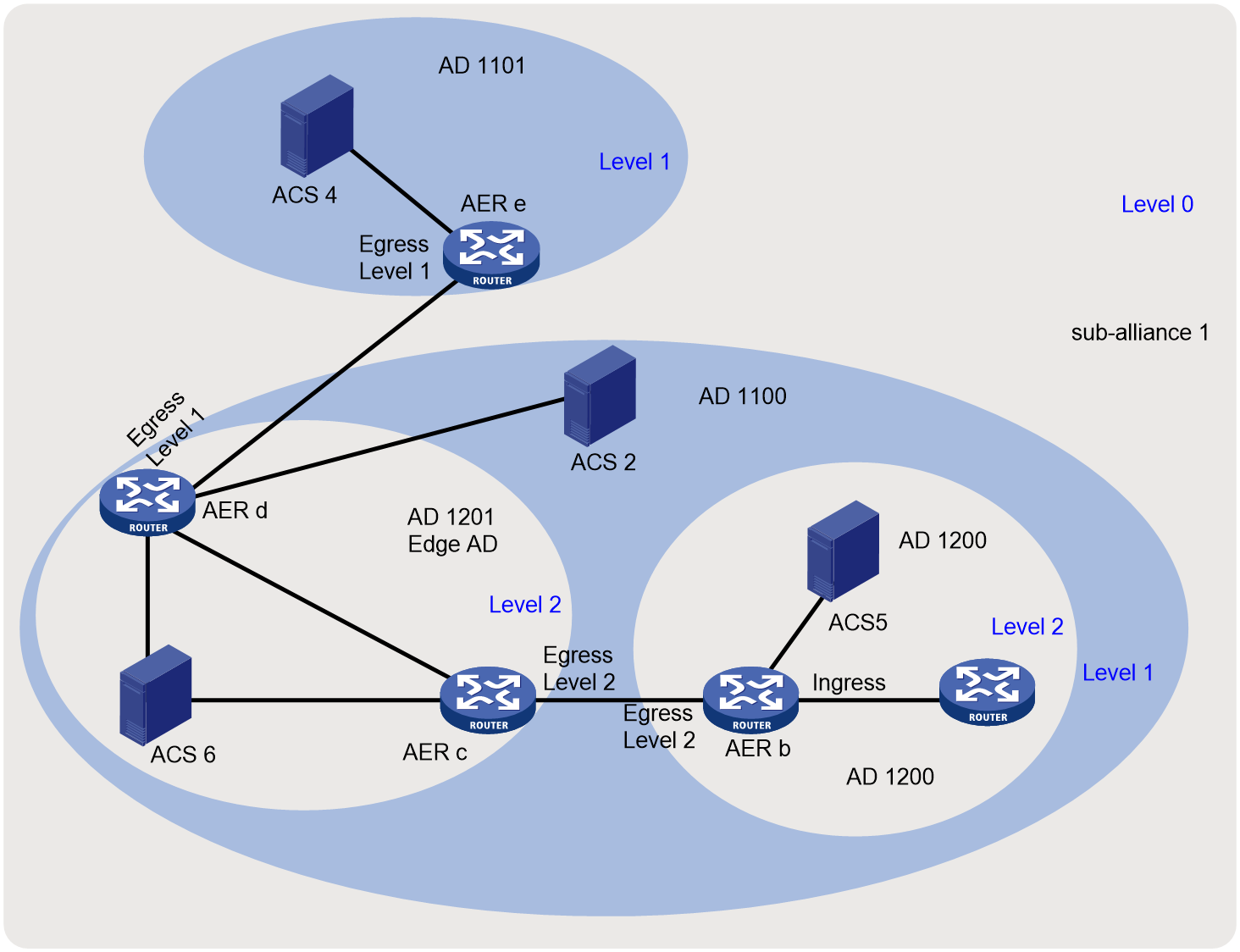
As shown in Figure 1, an SMA network mainly contains the following components: AS Control Server (ACS) and AS Edge Router (AER).
Figure 1 SMA network diagram
· Sub-trust alliance (hereinafter referred to as sub-alliance)—A group of ADs that trust each other. It is identified by a sub-alliance ID.
· Trust alliance (hereinafter referred to as alliance)—Collection of all ADs in the SMA system.
· Address domain (AD)—A group of IP address ranges managed by the same organization. It is the management object of a sub-alliance and is identified by an AD ID (AD 11.1, AD 1200, and AD 1201 for example). You can divide ADs in the same sub-alliance into a maximum of four levels to form a hierarchy structure. Smaller the level number, higher the level. For example, create level 0 for a city, create level 1 for an institution in the city, and create level 2 for a building or department of the institution. ADs contain the following types:
¡ Edge AD—An AD that connects the local level to another level, for example, AD 1201 in the figure.
¡ Non-edge AD.
If you create ADs of a lower level in an AD, for example, a level-1 AD in the level-0 AD, all devices (except for ACSs) in the original AD must be added to an AD of the lower level. As shown in Figure 1, all devices in the level-0 AD are in a level-1 AD.
· AS Control Server (ACS)—Required in each AD at every level. An ACS performs the following tasks:
¡ Exchanges IPv6 prefix and state machine information with ACSs of other sub-alliances in the same alliance.
¡ Sends alliance mapping, IPv6 prefix, and tag information to AERs of the local AD.
· AS Edge Router (AER)—Receives IPv6 prefix and tag information notified by ACSs and forwards packets between ADs. An AER can provide services for multiple ACSs at different levels. An AER has the following types of interfaces:
¡ Ingress interface—Connected to an SMA-disabled router in the local AD.
¡ Egress interface—Connected to an AER in another AD.
|
|
NOTE: · For security purposes, you can configure the ACSs to establish SSL links with each other and AERs. · The device can operate only as an AER. |
SMA processes for packets
SMA provides inter-AD IPv6 source address validation. It enforces source address validity on AERs. An AER validates source IPv6 addresses of packets between the local AD and other ADs in the same trust alliance.
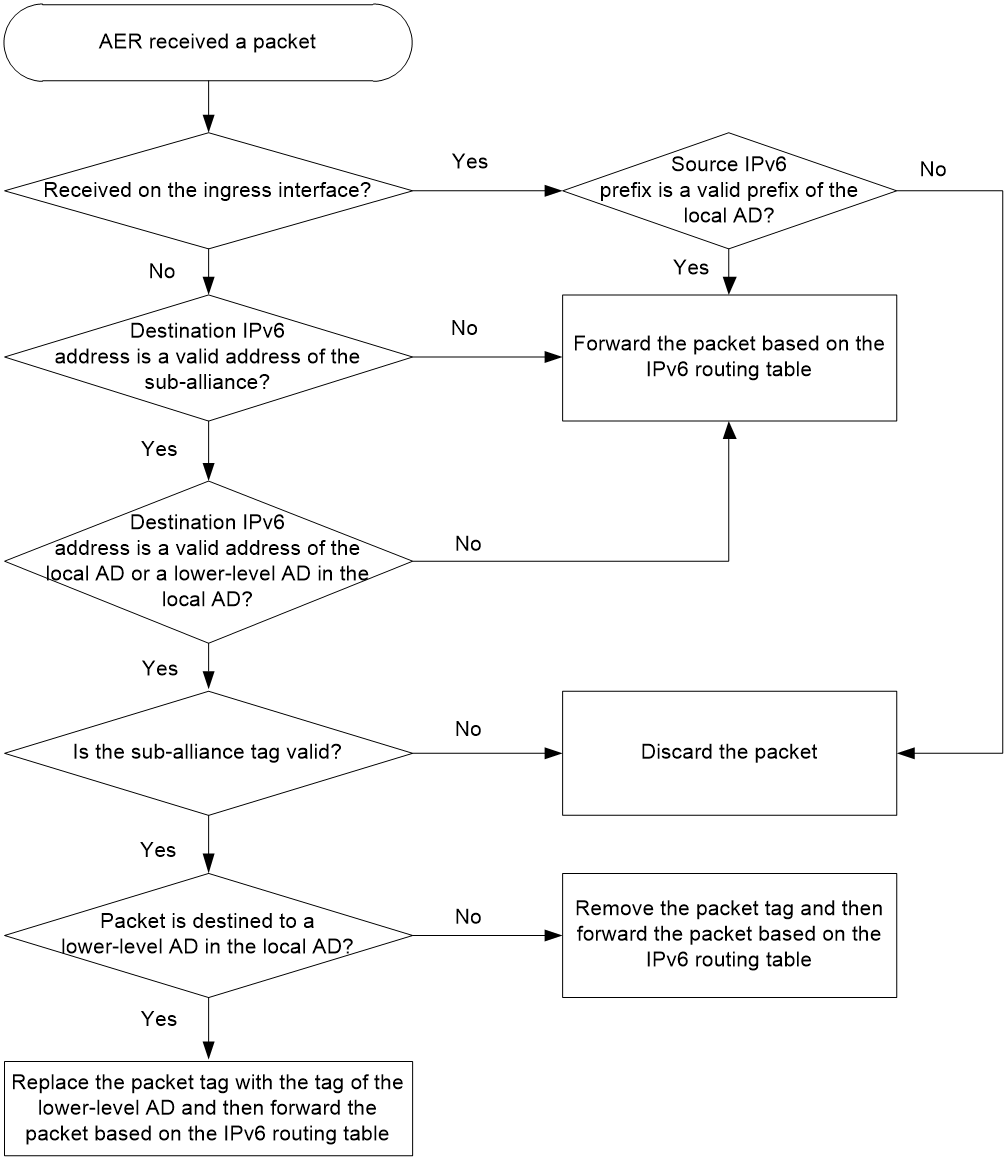
For incoming packets from other ADs to the local AD
An AER processes a received packet as follows:
1. Examine the interface type.
¡ If the interface is the ingress interface, the AER proceeds to step 2.
¡ If the interface is the egress interface, the AER proceeds to step 3.
2. Examine whether the source IPv6 prefix is a valid IPv6 prefix of the local AD.
¡ If yes, the AER forwards the packet based on the IPv6 routing table.
¡ If no, the AER discards the packet.
3. Examine whether the destination IPv6 prefix is a valid IPv6 prefix of the sub-alliance.
¡ If yes, the AER proceeds to the next step.
¡ If no, the AER forwards the packet based on the IPv6 routing table.
4. Examine whether the destination IPv6 address is a valid address of the local AD or an AD at a lower level in the local AD.
¡ If yes, the AER proceeds to the next step.
¡ If no, the AER forwards the packet based on the IPv6 routing table.
5. Examine the validity of the sub-alliance tag.
¡ If the tag is valid, the AER proceeds to the next step.
¡ If the tag is invalid, the AER discards the packet.
6. Examine whether the packet is destined to an AD at a lower level in the local AD.
¡ If yes, the AER replaces the packet tag with the tag of the lower-level AD, and then forwards the packet based on the IPv6 routing table.
The lower-level AER processes the packet in the same way.
¡ If no, the AER removes the packet tag, and then forwards the packet based on the IPv6 routing table.
Figure 2 Incoming packet processing workflow
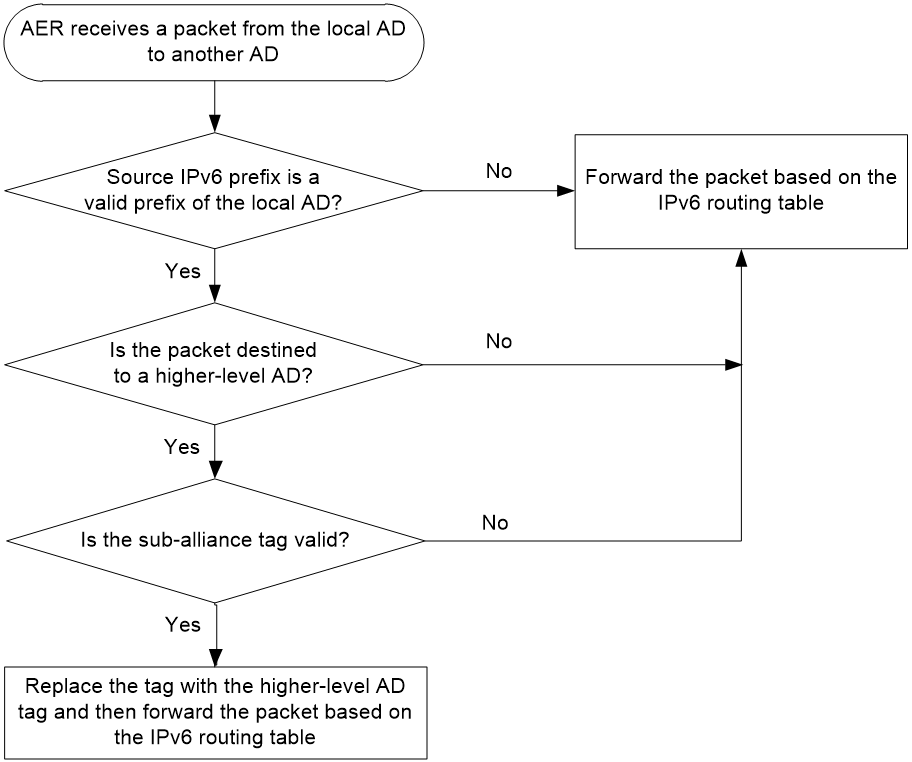
For outgoing packets from the local AD to another AD
An AER processes an outgoing packet as follows:
1. Examine whether the source IPv6 prefix is a valid prefix of the local AD.
¡ If yes, the AER adds a tag to the packet and then forwards the packet based on the IPv6 routing table.
¡ If no, the AER proceeds to the next step.
2. Examine whether the packet is destined to a higher-level AD of the local AD.
¡ If yes, the AER proceeds to the next step.
¡ If no, the AER forwards the packet based on the IPv6 routing table.
3. Examine the validity of the sub-alliance tag.
¡ If yes, the AER replaces the tag with the higher-level AD tag and then forwards the packet based on the IPv6 routing table.
¡ If no, the AER discards the packet.
Figure 3 Outgoing packet processing workflow
Prerequisites for SMA
Before you configure SMA on each AER, synchronize clocks for all devices in the alliance, including the ACSs and AERs. On an AER, use the clock datetime command to configure the system time. For more information about the clock datetime command, see Fundamentals Command Reference.
Restrictions and guidelines: Configuring SMA
Only the following cards support this feature:
Table 1 Card information
|
Card type |
Card mark |
|
CEPC |
CEPC-XP4LX, CEPC-XP24LX, CEPC-XP48RX, CEPC-CP4RX, CEPC-CP4RXA, CEPC-CP4RX-L, CEPC-CQ8L, CEPC-CQ8LA, CEPC-CQ8L1A, CEPC-CQ16L1 |
|
CSPEX |
CSPEX-1304X, CSPEX-1404X, CSPEX-1502X, CSPEX-1504X, CSPEX-1504XA, CSPEX-1602X, CSPEX-1602XA, CSPEX-1804X, CSPEX-1512X, CSPEX-1612X, CSPEX-1812X, CSPEX-1802X, CSPEX-1802XA, CSPEX-2612XA, CSPEX-1812X-E, CSPEX-2304X-G, CSPEX-1502XA |
|
SPE |
RX-SPE200, RX-SPE200-E |
SMA tasks at a glance
To configure SMA, perform the following tasks:
2. Enabling AER packet filtering
Configuring SMA basics
1. Enter system view.
system-view
2. Enable SMA.
sma-anti-spoof ipv6 enable
By default, SMA is disabled.
3. Configure a link between the AER and the ACSs in ADs at the specified level.
sma-anti-spoof ipv6 server ipv6-address client client-ipv6-address [ ssl-client-policy policy-name ] address-domain-level level-value
By default, no link is configured between the AER and an ACS.
If you do not specify an SSL client policy, the command configures a TCP link between the AER and the ACS. For information about configuring an SSL client policy, see "Configuring SSL."
4. Specify an AD for the AER.
sma-anti-spoof ipv6 address-domain domain-id
By default, no AD is specified for an AER.
5. Specify a sub-alliance for the AER.
sma-anti-spoof ipv6 sub-alliance sub-alli-number
By default, no sub-alliance is specified for an AER.
6. Enter interface view.
interface interface-type interface-number
7. Specify the SMA interface type.
sma-anti-spoof ipv6 port-type { egress level level-value | ingress }
By default, no SMA interface is specified.
Enabling AER packet filtering
About this task
In an SMA network, upon receiving a packet to the ACS in the local AD, the AER removes the SMA-Option from the packet and then directly forwards the packet to the ACS without verifying the packet tag. This prevents ACS communication failures caused by AER errors. However, packet forwarding without tag verification might cause security issues.
To solve the issue, you can enable AER packet filtering for the AER to verify the validity of tags in packets destined to its ACS and drop packets that fail the verification.
Procedure
1. Enter system view.
system-view
2. Enable AER packet filtering.
sma-anti-spoof ipv6 filter enable
By default, AER packet filtering is disabled.
Display and maintenance commands for SMA
Execute display commands in any view.
|
Task |
Command |
|
Display IPv6 prefix information. |
In standalone mode: display sma-anti-spoof ipv6 address-prefix [ acs address-domain-level level-value ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display sma-anti-spoof ipv6 address-prefix [ acs address-domain-level level-value ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display SMA tag information for all AD pairs. |
In standalone mode: display sma-anti-spoof ipv6 packet-tag [ acs address-domain-level level-value ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display sma-anti-spoof ipv6 packet-tag [ acs address-domain-level level-value ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
SMA configuration examples
Example: Configuring SMA using SSL links
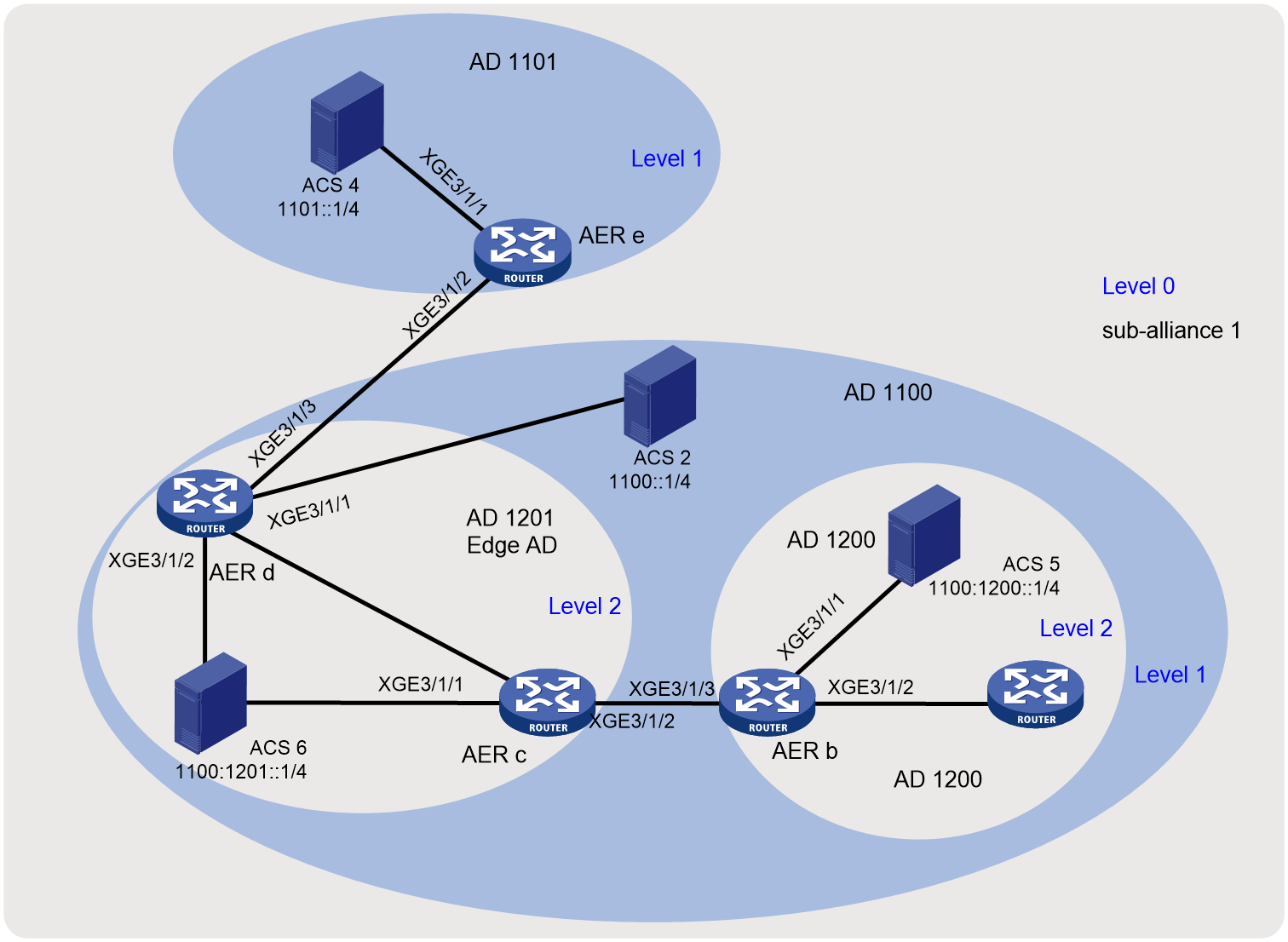
Network requirements
As shown in Figure 4, configure ACSs and AERs to use SMA with SSL links to prevent IPv6 source address spoofing.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
AER e |
XGE3/1/1 |
1101::2/4 |
AER c |
XGE3/1/1 |
1100:1201::3/4 |
|
AER d |
XGE3/1/1 |
1100::2/4 |
AER b |
XGE3/1/3 |
1100:1200::2/4 |
|
|
XGE3/1/2 |
1100:1201::2/4 |
|
|
|
Prerequisites
Synchronize clocks for all devices in the alliance.
Procedure
1. Configure ACSs. (Details not shown.)
2. Configure AER b.
# Configure an IPv6 address for AER b. (Details not shown.)
# Create SSL client policy sma on AER b.
<AERb> system-view
[AERb] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AERb-ssl-client-policy-sma] undo server-verify enable
[AERb-ssl-client-policy-sma] quit
# Enable SMA on AER b and configure an SSL link between AER b and ACS 5.
[AERb] sma-anti-spoof ipv6 enable
[AERb] sma-anti-spoof ipv6 server 1100:1200::1 client 1100:1200::2 ssl-client-policy sma address-domain-level 2
# Specify AD 1200 for AER b.
[AERb] sma-anti-spoof ipv6 address-domain 1200
# Specify sub-alliance 1 for AER b.
[AERb] sma-anti-spoof ipv6 sub-alliance 1
# Configure SMA interfaces for AER b.
[AERb] interface ten-gigabitethernet 3/1/2
[AERb-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type ingress
[AERb-Ten-GigabitEthernet3/1/2] quit
[AERb] interface Ten-GigabitEthernet 3/1/3
[AERb-Ten-GigabitEthernet3/1/3] sma-anti-spoof ipv6 port-type egress level 2
[AERb-Ten-GigabitEthernet3/1/3] quit
3. Configure AER c.
# Configure an IPv6 address for AER c. (Details not shown.)
# Create SSL client policy sma on AER c.
<AERc> system-view
[AERc] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AERc-ssl-client-policy-sma] undo server-verify enable
[AERc-ssl-client-policy-sma] quit
# Enable SMA on AER c and configure an SSL link between AER c and ACS 6.
[AERc] sma-anti-spoof ipv6 enable
[AERc] sma-anti-spoof ipv6 server 1100:1201::1 client 1100:1201::3 ssl-client-policy sma address-domain-level 2
# Specify AD 1201 for AER c.
[AERc] sma-anti-spoof ipv6 address-domain 1201
# Specify sub-alliance 1 for AER c.
[AERc] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER c.
[AERc] interface ten-gigabitethernet 3/1/2
[AERc-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type egress level 2
[AERc-Ten-GigabitEthernet3/1/2] quit
4. Configure AER d.
# Configure IPv6 addresses for AER d. (Details not shown.)
# Create SSL client policy sma on AER d.
<AERd> system-view
[AERd] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AERd-ssl-client-policy-sma] undo server-verify enable
[AERd-ssl-client-policy-sma] quit
# Enable SMA on AER d and configure AER d to establish SSL links with ACS 6 and ACS 2.
[AERd] sma-anti-spoof ipv6 enable
[AERd] sma-anti-spoof ipv6 server 1100:1201::1 client 1100:1201::2 ssl-client-policy sma address-domain-level 2
[AERd] sma-anti-spoof ipv6 server 1100::1 client 1100::2 ssl-client-policy sma address-domain-level 1
# Specify AD 1201 for AER d.
[AERd] sma-anti-spoof ipv6 address-domain 1201
# Specify sub-alliance 1 for AER d.
[AERd] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER d.
[AERd] interface ten-gigabitethernet 3/1/3
[AERd-Ten-GigabitEthernet3/1/3] sma-anti-spoof ipv6 port-type egress level 1
[AERd-Ten-GigabitEthernet3/1/3] quit
5. Configure AER e.
# Configure an IPv6 address for AER e. (Details not shown.)
# Create SSL client policy sma on AER e.
<AERe> system-view
[AERe] ssl client-policy sma
# Disable the SSL client from authenticating SSL servers through digital certificates if SSL server authentication is not required. Server authentication is enabled by default.
[AERe-ssl-client-policy-sma] undo server-verify enable
[AERe-ssl-client-policy-sma] quit
# Enable SMA on AER d and configure an SSL link between AER e and ACS 4.
[AERe] sma-anti-spoof ipv6 enable
[AERe] sma-anti-spoof ipv6 server 1101::1 client 1101::2 ssl-client-policy sma address-domain-level 2
# Specify AD 1101 for AER e.
[AERe] sma-anti-spoof ipv6 address-domain 1101
# Specify sub-alliance 1 for AER e.
[AERe] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER e.
[AERe] interface ten-gigabitethernet 3/1/2
[AERe-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type egress level 1
[AERe-Ten-GigabitEthernet3/1/2] quit
Verifying the configuration
# Verify that the AERs can obtain IPv6 prefixes and SMA tags from the corresponding ACS.
[AERe] display sma-anti-spoof ipv6 address-prefix
Alliance number: 1
ACS address-domain level: 1
Address-domain ID: 1100
IPv6 prefix: 1100::/16
Effective at: Oct 1 00:00:00 2020
Address-domain level: 1
Common level: 0
Address-domain cnt: 2
Address-domain list: 1 1100
IPv6 prefix: 11A0:1000::/32
Effective at: Oct 1 00:00:00 2020
Address-domain level: 1
Common level: 0
Address-domain cnt: 2
Address-domain list: 1 1100
[AERe] display sma-anti-spoof ipv6 packet-tag
Alliance number: 1
ACS address-domain level: 1
Source address-domain ID: 1100
Destination address-domain ID: 1101
Tag: 0xBB66D753D858E1ED
Transition interval: 10s
Source address-domain ID: 1101
Destination address-domain ID: 1100
Tag: 0x1D447D157A3EC032
Transition interval: 10s
Source address-domain ID: 1101
Destination address-domain ID: 2147483649
Tag: 0x58420DA937580F19
Transition interval: 10s
Source address-domain ID: 2147483649
Destination address-domain ID: 1101
Tag: 0x3DBB48D95D463C1B
Transition interval: 10s
Example: Configuring SMA using TCP links
Network requirements
As shown in Figure 5, configure ACSs and AERs to use SMA with TCP links to prevent IPv6 source address spoofing.
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
AER e |
XGE3/1/1 |
1101::2/4 |
AER c |
XGE3/1/1 |
1100:1201::3/4 |
|
AER d |
XGE3/1/1 |
1100::2/4 |
AER b |
XGE3/1/3 |
1100:1200::2/4 |
|
|
XGE3/1/2 |
1100:1201::2/4 |
|
|
|
Prerequisites
Synchronize clocks for all devices in the alliance.
Procedure
1. Configure ACSs. (Details not shown.)
2. Configure AER b.
# Configure an IPv6 address for AER b. (Details not shown.)
# Enable SMA on AER b and configure an TCP link between AER b and ACS 5.
[AERb] sma-anti-spoof ipv6 enable
[AERb] sma-anti-spoof ipv6 server 1100:1200::1 client 1100:1200::2 address-domain-level 2
# Specify AD 1200 for AER b.
[AERb] sma-anti-spoof ipv6 address-domain 1200
# Specify sub-alliance 1 for AER b.
[AERb] sma-anti-spoof ipv6 sub-alliance 1
# Configure SMA interfaces for AER b.
[AERb] interface ten-gigabitethernet 3/1/2
[AERb-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type ingress
[AERb-Ten-GigabitEthernet3/1/2] quit
[AERb] interface Ten-GigabitEthernet 3/1/3
[AERb-Ten-GigabitEthernet3/1/3] sma-anti-spoof ipv6 port-type egress level 2
[AERb-Ten-GigabitEthernet3/1/3] quit
3. Configure AER c.
# Configure an IPv6 address for AER c. (Details not shown.)
# Enable SMA on AER c and configure an TCP link between AER c and ACS 6.
[AERc] sma-anti-spoof ipv6 enable
[AERc] sma-anti-spoof ipv6 server 1100:1201::1 client 1100:1201::3 address-domain-level 2
# Specify AD 1201 for AER c.
[AERc] sma-anti-spoof ipv6 address-domain 1201
# Specify sub-alliance 1 for AER c.
[AERc] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER c.
[AERc] interface ten-gigabitethernet 3/1/2
[AERc-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type egress level 2
[AERc-Ten-GigabitEthernet3/1/2] quit
4. Configure AER d.
# Configure IPv6 addresses for AER d. (Details not shown.)
# Enable SMA on AER d and configure AER d to establish TCP links with ACS 6 and ACS 2.
[AERd] sma-anti-spoof ipv6 enable
[AERd] sma-anti-spoof ipv6 server 1100:1201::1 client 1100:1201::2 address-domain-level 2
[AERd] sma-anti-spoof ipv6 server 1100::1 client 1100::2 address-domain-level 1
# Specify AD 1201 for AER d.
[AERd] sma-anti-spoof ipv6 address-domain 1201
# Specify sub-alliance 1 for AER d.
[AERd] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER d.
[AERd] interface ten-gigabitethernet 3/1/3
[AERd-Ten-GigabitEthernet3/1/3] sma-anti-spoof ipv6 port-type egress level 1
[AERd-Ten-GigabitEthernet3/1/3] quit
5. Configure AER e.
# Configure an IPv6 address for AER e. (Details not shown.)
# Enable SMA on AER d and configure a TCP link between AER e and ACS 4.
[AERe] sma-anti-spoof ipv6 enable
[AERe] sma-anti-spoof ipv6 server 1101::1 client 1101::2 address-domain-level 2
# Specify AD 1101 for AER e.
[AERe] sma-anti-spoof ipv6 address-domain 1101
# Specify sub-alliance 1 for AER e.
[AERe] sma-anti-spoof ipv6 sub-alliance 1
# Configure the SMA interface for AER e.
[AERe] interface ten-gigabitethernet 3/1/2
[AERe-Ten-GigabitEthernet3/1/2] sma-anti-spoof ipv6 port-type egress level 1
[AERe-Ten-GigabitEthernet3/1/2] quit
Verifying the configuration
# Verify that the AERs can obtain IPv6 prefixes and SMA tags from the corresponding ACS.
[AERe] display sma-anti-spoof ipv6 address-prefix
Alliance number: 1
ACS address-domain level: 1
Address-domain ID: 1100
IPv6 prefix: 1100::/16
Effective at: Oct 1 00:00:00 2020
Address-domain level: 1
Common level: 0
Address-domain cnt: 2
Address-domain list: 1 1100
IPv6 prefix: 11A0:1000::/32
Effective at: Oct 1 00:00:00 2020
Address-domain level: 1
Common level: 0
Address-domain cnt: 2
Address-domain list: 1 1100
[AERe] display sma-anti-spoof ipv6 packet-tag
Alliance number: 1
ACS address-domain level: 1
Source address-domain ID: 1100
Destination address-domain ID: 1101
Tag: 0xBB66D753D858E1ED
Transition interval: 10s
Source address-domain ID: 1101
Destination address-domain ID: 1100
Tag: 0x1D447D157A3EC032
Transition interval: 10s
Source address-domain ID: 1101
Destination address-domain ID: 2147483649
Tag: 0x58420DA937580F19
Transition interval: 10s
Source address-domain ID: 2147483649
Destination address-domain ID: 1101
Tag: 0x3DBB48D95D463C1B