- Table of Contents
-
- 07-Layer 3—IP Routing Configuration Guide
- 00-Preface
- 01-Basic IP routing configuration
- 02-Static routing configuration
- 03-RIP configuration
- 04-OSPF configuration
- 05-IS-IS configuration
- 06-EIGRP configuration
- 07-BGP configuration
- 08-Policy-based routing configuration
- 09-IPv6 static routing configuration
- 10-RIPng configuration
- 11-OSPFv3 configuration
- 12-IPv6 policy-based routing configuration
- 13-Routing policy configuration
- 14-DCN configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-IS-IS configuration | 2.23 MB |
Contents
Enabling a lightweight IS-IS process
Setting the IS level and circuit level
Configuring P2P network type for an interface
Configuring IS-IS multi-instance processes
Configuring IS-IS route control
Changing the link cost of a Layer 3 aggregate interface when its bandwidth falls below the threshold
Enabling IS-IS to advertise the maximum link cost to neighbors
Specifying a preference for IS-IS
Configuring the maximum number of ECMP routes
Configuring IS-IS route summarization
Configuring IS-IS route redistribution
Filtering routes calculated from received LSPs
Configuring IS-IS route leaking
Advertising IS-IS link state information to other protocols
Configuring the IPv6 IS-IS link tag feature
Configuring IS-IS to advertise network performance parameters
About IS-IS network performance parameters
Enabling IS-IS to advertise link attributes in LSPs
Advertising link delay information
Advertising link bandwidth information
Advertising link loss information
Configuring IS-IS flexible algorithm
About IS-IS flexible algorithm
IS-IS flexible algorithm tasks at a glance
Mapping an affinity attribute name to an affinity bit
Assigning affinity attributes to IS-IS links
Configuring a flexible algorithm
Configuring the metric type of a flexible algorithm
Configuring flexible algorithm FRR
Configuring flexible algorithm TI-LFA FRR
Set the priority of an FRR backup path selection policy
Applying a flexible algorithm to SR-MPLS
Configuring color attribute-based traffic redirection
Applying a flexible algorithm to SRv6
Enabling trust level-based FAD advertisement
Specifying the interval for sending IS-IS hello packets
Specifying the interval for sending IS-IS CSNP packets
Setting the maximum age of LSPs
Setting the LSP refresh interval and generation interval
Setting the LSP receiving interval
Setting the lifetime for expired LSPs in the LSDB
Setting the SPF calculation interval
Configuring IS-IS packet-related features
Configuring a DIS priority for an interface
Configuring the administrative tag value for an interface
Specifying the IS-IS hello multiplier
Disabling an interface from sending/receiving IS-IS packets
Enabling an interface to send small hello packets
Enabling LSP fragment extension
Controlling LSP generation, advertisement and reception
Configuring IS-IS route update suppression
Configuring advanced IS-IS features
Enabling source address check for hello packets on a P2P interface
Configuring convergence priorities for specific routes
Setting IS-IS interface cost upon LSDB overload
Configuring system ID to host name mappings
Enabling BIER for an IS-IS process
Configuring IS-IS logging and SNMP notifications
Enabling the logging of neighbor state changes
Setting the maximum number of log entries that can be recorded
Setting the maximum number of advertisement sources that trigger LSP update logging
Setting the maximum number of IS-IS neighbor relationship troubleshooting entries
Configuring IS-IS network management
Configuring IS-IS fast convergence
Enhancing IS-IS network security
Configuring neighbor relationship authentication
Configuring area authentication
Configuring routing domain authentication
Enabling IS-IS to adjust the interface cost according to the BFD session state
Suppressing BFD session state-based interface cost adjustment upon BFD session flapping
Controlling adjacency establishment and maintenance based on BFD session state
Configuring IS-IS remote LFA FRR
Setting the priority for FRR backup path selection policies
Enabling IS-IS to adjust the interface cost according to the link quality
Configuring IS-IS neighbor flapping suppression
Configuring IS-IS member port flapping suppression
Display and maintenance commands for IS-IS
Displaying and maintaining IPv4 IS-IS
Displaying and maintaining IPv6 IS-IS
Example: Configuring basic IS-IS
Example: Configuring DIS election
Example: Configuring IS-IS route redistribution
Example: Configuring IS-IS authentication
Example: Configuring BFD for IS-IS
Example: Configuring IS-IS LFA FRR
Example: Configuring IS-IS remote LFA FRR
Example: Configuring IS-IS multi-instance processes
IPv6 IS-IS configuration examples
Example: Configuring IPv6 IS-IS basics
Example: Configuring BFD for IPv6 IS-IS
Example: Configuring IPv6 IS-IS FRR
Applying a flexible algorithm to IS-IS SRv6
Configuring IS-IS
About IS-IS
IS-IS is an IGP used within an AS. It uses the SPF algorithm for route calculation.
Terminology
· Intermediate system—Similar to a router in TCP/IP, IS is the basic unit used in an IS-IS routing domain to generate and propagate routing information. Throughout this chapter, an IS refers to a router.
· End system—Similar to a host in TCP/IP, an ES does not run IS-IS. ISO defines the ES-IS protocol for communication between an ES and an IS.
· Routing domain—An RD comprises a group of ISs that exchange routing information with each other by using the same routing protocol.
· Area—An IS-IS routing domain can be split into multiple areas.
· Link State Database—All link states in the network form the LSDB. Each IS has a minimum of one LSDB. An IS uses the SPF algorithm and LSDB to generate IS-IS routes.
· Link State Protocol Data Unit or Link State Packet—An IS advertises link state information in an LSP.
· Network Protocol Data Unit—An NPDU is a network layer protocol packet in OSI, similar to an IP packet in TCP/IP.
· Designated IS—A DIS is elected on a broadcast network.
· Network service access point—An NSAP is an OSI network layer address. The NSAP identifies an abstract network service access point and describes the network address format in the OSI reference model.
IS-IS address
As shown in Figure 1, an NSAP address comprises the Initial Domain Part (IDP) and the Domain Specific Part (DSP). The IDP is analogous to the network ID of an IP address, and the DSP is analogous to the subnet and host ID.
The IDP includes the Authority and Format Identifier (AFI) and the Initial Domain Identifier (IDI).
The DSP includes:
· High Order Part of DSP (HO-DSP)—Identifies the area.
· System ID—Identifies the host.
· SEL—Also known as the N-SEL or the NSAP selector (SEL). It is similar to the protocol identifier in IP and is used to identify the type of service. Different transport layer protocols correspond to different SELs.
The IDP and DSP are variable in length. The length of an NSAP address is in the range of 8 to 20 bytes.
Figure 1 NSAP address format
An IS-IS address contains the following components:
· Area address
The area address comprises the IDP and the HO-DSP of the DSP, which identify the area and the routing domain. Different routing domains cannot have the same area address.
Typically, a router only needs one area address, and all nodes in the same area must have the same area address. To support smooth area merging, partitioning, and switching, a router can have a maximum of three area addresses.
· System ID
A system ID uniquely identifies a host or router. It has a fixed length of 48 bits (6 bytes).
The system ID of a device can be generated from the router ID. For example, suppose a router uses the IP address 168.10.1.1 of Loopback 0 as the router ID. The system ID can be obtained in the following steps:
a. Extend each decimal number of the IP address to three digits by adding 0s from the left, such as 168.010.001.001.
b. Divide the extended IP address into three sections that each has four digits to get the system ID 1680.1000.1001.
If you use other methods to define a system ID, make sure that it can uniquely identify the host or router.
· SEL
An SEL is used to identify the type of service. Different transport layer protocols correspond to different SELs. It has a fixed length of 8 bits. All SELs in IP are 00.
NET
A network entity title (NET) identifies the network layer information of an IS. It does not include transport layer information. A NET is a special NSAP address with the SEL being 0. The length of a NET is in the range of 8 to 20 bytes, same as a NSAP address.
A NET includes the following parts:
· Area ID—Has a length of 1 to 13 bytes.
· System ID—A system ID uniquely identifies a host or router in the area and has a fixed length of 6 bytes.
· SEL—Has a value of 0 and a fixed length of 1 byte.
For example, for a NET ab.cdef.1234.5678.9abc.00, the area ID is ab.cdef, the system ID is 1234.5678.9abc, and the SEL is 00.
Typically, a router only needs one NET, but it can have a maximum of three NETs for smooth area merging and partitioning. When you configure multiple NETs, make sure the system IDs are the same.
IS-IS area
IS-IS has a 2-level hierarchy to support large-scale networks. A large-scale routing domain is divided into multiple areas. Typically, a Level-1 router is deployed within an area. A Level-2 router is deployed between areas. A Level-1-2 router is deployed between Level-1 and Level-2 routers.
Level-1 router
A Level-1 router establishes neighbor relationships with Level-1 and Level-1-2 routers in the same area. It maintains an LSDB comprising intra-area routing information. A Level-1 router forwards packets destined for external areas to the nearest Level-1-2 router. Level-1 routers in different areas cannot establish neighbor relationships.
Level-2 router
A Level-2 router establishes neighbor relationships with Level-2 and Level-1-2 routers in the same area or in different areas. It maintains a Level-2 LSDB containing inter-area routing information. All the Level-2 and Level-1-2 routers must be contiguous to form the backbone of the IS-IS routing domain. Level-2 routers can establish neighbor relationships even if they are in different areas.
Level-1-2 router
A router with both Level-1 and Level-2 router functions is a Level-1-2 router. It can establish Level-1 neighbor relationships with Level-1 and Level-1-2 routers in the same area. It can establish Level-2 neighbor relationships with Level-2 and Level-1-2 routers in different areas. A Level-1 router can reach other areas only through a Level-1-2 router. The Level-1-2 router maintains two LSDBs, a Level-1 LSDB for intra-area routing and a Level-2 LSDB for inter-area routing.
IS-IS topology
Figure 2 shows one IS-IS network topology. Area 1 is the backbone that comprises a set of Level-2 routers. The other four areas are non-backbone areas connected to the backbone through Level-1-2 routers.
Figure 3 shows another IS-IS topology. No area is defined as the backbone in this topology. The backbone comprises all contiguous Level-2 and Level-1-2 routers in different areas. The IS-IS backbone does not need to be a specific area.
Both the Level-1 and Level-2 routers use the SPF algorithm to generate the shortest path tree.
Route leaking
Level-2 and Level-1-2 routers form a Level-2 area. An IS-IS routing domain comprises only one Level-2 area and multiple Level-1 areas. A Level-1 area must connect to the Level-1-2 area rather than another Level-1 area.
Level-1-2 routers send the routing information of Level-1 areas to the Level-2 area. Level-2 routers know the routing information of the entire IS-IS routing domain. By default, a Level-2 router does not advertise the routing information of other areas to a Level-1 area. A Level-1 router simply sends packets destined for other areas to the nearest Level-1-2 router. The path passing through the Level-1-2 router might not be the best. To resolve this issue, IS-IS provides the route leaking feature.
Route leaking enables a Level-1-2 router to advertise the routes of other areas to the connected Level-1 area so that the Level-1 routers can select the optimal routes.
IS-IS network types
IS-IS supports broadcast networks (for example, Ethernet and Token Ring) and point-to-point networks (for example, PPP and HDLC).
For an NBMA interface, such as an ATM interface, you must configure point-to-point or broadcast subinterfaces. IS-IS cannot run on P2MP links.
DIS and pseudonodes
IS-IS routers on a broadcast network must elect a DIS.
The Level-1 and Level-2 DISs are elected separately. You can assign different priorities to a router for different level DIS elections. The higher the router priority, the more likely the router becomes the DIS. If multiple routers with the same highest DIS priority exist, the one with the highest Subnetwork Point of Attachment (SNPA) address will be elected. On a broadcast network, the SNPA address is the MAC address. A router can be the DIS for different levels.
IS-IS DIS election differs from OSPF DIS election in the following ways:
· A router with priority 0 can also participate in the DIS election.
· When a router with a higher priority is added to the network, an LSP flooding process is performed to elect the router as the new DIS.
As shown in Figure 4, the same level routers on a network, including non-DIS routers, establish adjacency with each other.
Figure 4 DIS in the IS-IS broadcast network
The DIS creates and updates pseudonodes, and generates LSPs for the pseudonodes, to describe all routers on the network.
A pseudonode represents a virtual node on the broadcast network. It is not a real router. In IS-IS, it is identified by the system ID of the DIS and a 1-byte Circuit ID (a non-zero value).
Using pseudonodes simplifies network topology and can reduce the amount of resources consumed by SPF.
|
|
NOTE: On an IS-IS broadcast network, all routers establish adjacency relationships, but they synchronize their LSDBs through the DIS. On a broadcast network, the device can establish up to 255 neighbor relationships, because the Circuit ID is only one byte long. If the number of broadcast links that require neighbor relationship establishment exceeds 255, the device does not establish IS-IS neighbor relationships on the excess broadcast links. |
IS-IS PDUs
PDU
IS-IS PDUs are encapsulated into link layer frames. An IS-IS PDU has two parts, the headers and the variable length fields. The headers comprise the PDU common header and the PDU specific header. All PDUs have the same PDU common header. The specific headers vary by PDU type.
Figure 5 PDU format
Table 1 PDU types
|
Type |
PDU Type |
Acronym |
|
15 |
Level-1 LAN IS-IS hello PDU |
L1 LAN IIH |
|
16 |
Level-2 LAN IS-IS hello PDU |
L2 LAN IIH |
|
17 |
Point-to-Point IS-IS hello PDU |
P2P IIH |
|
18 |
Level-1 Link State PDU |
L1 LSP |
|
20 |
Level-2 Link State PDU |
L2 LSP |
|
24 |
Level-1 Complete Sequence Numbers PDU |
L1 CSNP |
|
25 |
Level-2 Complete Sequence Numbers PDU |
L2 CSNP |
|
26 |
Level-1 Partial Sequence Numbers PDU |
L1 PSNP |
|
27 |
Level-2 Partial Sequence Numbers PDU |
L2 PSNP |
Hello PDU
IS-to-IS hello (IIH) PDUs are used by routers to establish and maintain neighbor relationships. On broadcast networks, Level-1 routers use Level-1 LAN IIHs, and Level-2 routers use Level-2 LAN IIHs. The P2P IIHs are used on point-to-point networks.
LSP
The LSPs carry link state information. LSPs include Level-1 LSPs and Level-2 LSPs. The Level-2 LSPs are sent by the Level-2 routers, and the Level-1 LSPs are sent by the Level-1 routers. The Level-1-2 router can send both types of LSPs.
SNP
A sequence number PDU (SNP) describes the complete or partial LSPs for LSDB synchronization.
SNPs include CSNP and PSNP, which are further divided into Level-1 CSNP, Level-2 CSNP, Level-1 PSNP, and Level-2 PSNP.
A CSNP describes the summary of all LSPs for LSDB synchronization between neighboring routers. On broadcast networks, CSNPs are sent by the DIS periodically (every 10 seconds by default). On point-to-point networks, CSNPs are sent only during the first adjacency establishment.
A PSNP only contains the sequence numbers of one or multiple latest received LSPs. It can acknowledge multiple LSPs at one time. When LSDBs are not synchronized, a PSNP is used to request missing LSPs from a neighbor.
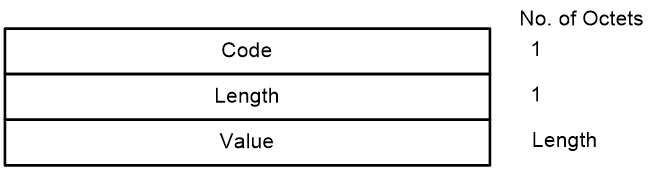
CLV
The variable fields of PDU comprise multiple Code-Length-Value (CLV) triplets.
Figure 6 CLV format
Table 2 shows that different PDUs contain different CLVs. Codes 1 through 10 are defined in ISO 10589 (code 3 and 5 are not shown in the table). Codes 128 through 132 are defined in RFC 1195. Codes 222 through 237 are defined in RFC 5120.
Table 2 CLV codes and PDU types
|
CLV Code |
Name |
PDU Type |
|
1 |
Area Addresses |
IIH, LSP |
|
2 |
IS Neighbors (LSP) |
LSP |
|
4 |
Partition Designated Level 2 IS |
L2 LSP |
|
6 |
IS Neighbors (MAC Address) |
LAN IIH |
|
7 |
IS Neighbors (SNPA Address) |
LAN IIH |
|
8 |
Padding |
IIH |
|
9 |
LSP Entries |
SNP |
|
10 |
Authentication Information |
IIH, LSP, SNP |
|
128 |
IP Internal Reachability Information |
LSP |
|
129 |
Protocols Supported |
IIH, LSP |
|
130 |
IP External Reachability Information |
L2 LSP |
|
131 |
Inter-Domain Routing Protocol Information |
L2 LSP |
|
132 |
IP Interface Address |
IIH, LSP |
|
222 |
MT-ISN |
LSP |
|
229 |
M-Topologies |
IIH, LSP |
|
235 |
MT IP. Reach |
LSP |
|
237 |
MT IPv6 IP. Reach |
LSP |
IPv6 IS-IS
IS-IS supports multiple network protocols, including IPv6. To support IPv6, the IETF added two type-length-values (TLVs) and a new network layer protocol identifier (NLPID).
The TLVs are as follows:
· IPv6 Reachability—Contains routing prefix and metric information to describe network reachability and has a type value of 236 (0xEC).
· IPv6 Interface Address—Same as the "IP Interface Address" TLV in IPv4 ISIS, except that the 32-bit IPv4 address is translated to the 128-bit IPv6 address.
The new NLPID is an 8-bit field that identifies which network layer protocol is supported. For IPv6, the NLPID is 142 (0x8E).
IS-IS GR
IS-IS GR ensures the service continuity of an IS-IS-enabled router during active/standby switchover or IS-IS restart.
IS-IS NSR
Nonstop routing (NSR) backs up necessary IS-IS information from the active process to the standby process, such as IS-IS neighbor information and link state information. After an active/standby switchover, NSR can complete link state recovery and route regeneration without tearing down adjacencies or impacting forwarding services.
NSR does not require the cooperation of neighboring devices to recover routing information, and it is typically used more often than GR.
Protocols and standards
· ISO 8348, Ad2 Network Services Access Points
· ISO 9542, ES-IS Routing Protocol
· ISO 10589, ISO IS-IS Routing Protocol
· RFC 1195, Use of OSI IS-IS for Routing in TCP/IP and Dual Environments
· RFC 2973, IS-IS Mesh Groups
· RFC 3277, IS-IS Transient Blackhole Avoidance
· RFC 3358, Optional Checksums in ISIS
· RFC 3359, Reserved Type, Length and Value (TLV) Codepoints in Intermediate System to Intermediate System
· RFC 3563, Cooperative Agreement Between the ISOC/IETF and ISO/IEC Joint Technical Committee 1/Sub Committee 6 (JTC1/SC6) on IS-IS Routing Protocol Development
· RFC 3719, Recommendations for Interoperable Networks using Intermediate System to Intermediate System (IS-IS)
· RFC 3787, Recommendations for Interoperable IP Networks using Intermediate System to Intermediate System (IS-IS)
· RFC 4444, Management Information Base for Intermediate System to Intermediate System (IS-IS)
· RFC 4972, Routing Extensions for Discovery of Multiprotocol (MPLS) Label Switch Router (LSR) Traffic Engineering (TE) Mesh Membership
· RFC 5029, Definition of an IS-IS Link Attribute Sub-TLV
· RFC 5089, IS-IS Protocol Extensions for Path Computation Element (PCE) Discovery
· RFC 5130, A Policy Control Mechanism in IS-IS Using Administrative Tags
· RFC 5301, Dynamic Hostname Exchange Mechanism for IS-IS
· RFC 5302, Domain-Wide Prefix Distribution with Two-Level IS-IS
· RFC 5303, Three-Way Handshake for IS-IS Point-to-Point Adjacencies
· RFC 5304, IS-IS Cryptographic Authentication
· RFC 5305, IS-IS Extensions for Traffic Engineering
· RFC 5306, Restart Signaling for IS-IS
· RFC 5308, Routing IPv6 with IS-IS
· RFC 5310, IS-IS Generic Cryptographic Authentication
· RFC 5311, Simplified Extension of Link State PDU (LSP) Space for IS-IS
· RFC 6165, Extensions to IS-IS for Layer-2 Systems
· RFC 6213, IS-IS BFD-Enabled TLV
· RFC 6232, Purge Originator Identification TLV for IS-IS
· RFC 6233, IS-IS Registry Extension for Purges
· RFC 6329, IS-IS Extensions Supporting IEEE 802.1aq Shortest Path Bridging
· RFC 6571, Loop-Free Alternate (LFA) Applicability in Service Provider (SP) Networks
· RFC 6823, Advertising Generic Information in IS-IS
· RFC 7142, OSI IS-IS Intra-domain Routing Protocol
· RFC 7356, IS-IS Flooding Scope Link State PDUs (LSPs)
· RFC 7370, Updates to the IS-IS TLV Codepoints Registry
· RFC 7602, IS-IS Extended Sequence Number TLV
· RFC 7645, The Keying and Authentication for Routing Protocol (KARP) IS-IS Security Analysis
· RFC 7775, IS-IS Route Preference for Extended IP and IPv6 Reachability
· RFC 7794, IS-IS Prefix Attributes for Extended IPv4 and IPv6 Reachability
· RFC 7810, IS-IS Traffic Engineering (TE) Metric Extensions
· RFC 7813, IS-IS Path Control and Reservation
· RFC 7917, Advertising Node Administrative Tags in IS-IS
· RFC 7981, IS-IS Extensions for Advertising Router Information
· RFC 7987, IS-IS Minimum Remaining Lifetime
IPv4 IS-IS tasks at a glance
To configure IPv4 IS-IS, perform the following tasks:
b. (Optional.) Enabling a lightweight IS-IS process
c. (Optional.) Setting the IS level and circuit level
d. (Optional.) Configuring P2P network type for an interface
e. (Optional.) Configuring IS-IS multi-instance processes
2. (Optional.) Configuring IS-IS route control
¡ Changing the link cost of a Layer 3 aggregate interface when its bandwidth falls below the threshold
¡ Enabling IS-IS to advertise the maximum link cost to neighbors
¡ Specifying a preference for IS-IS
¡ Configuring the maximum number of ECMP routes
¡ Configuring IS-IS route summarization
¡ Configuring IS-IS route redistribution
¡ Filtering routes calculated from received LSPs
¡ Configuring IS-IS route leaking
¡ Advertising IS-IS link state information to other protocols
3. (Optional.) Configuring IS-IS to advertise network performance parameters
¡ Enabling IS-IS to advertise link attributes in LSPs
¡ Advertising link delay information
¡ Advertising link bandwidth information
¡ Advertising link loss information
4. (Optional.) Configuring IS-IS flexible algorithm
5. (Optional.) Configuring IS-IS timers
¡ Specifying the interval for sending IS-IS hello packets
¡ Specifying the interval for sending IS-IS CSNP packets
¡ Setting the maximum age of LSPs
¡ Setting the LSP refresh interval and generation interval
¡ Setting LSP sending intervals
¡ Setting the LSP receiving interval
¡ Setting the lifetime for expired LSPs in the LSDB
¡ Setting the SPF calculation interval
6. (Optional.) Configuring IS-IS packet-related features
¡ Configuring a DIS priority for an interface
¡ Configuring the administrative tag value for an interface
¡ Specifying the IS-IS hello multiplier
¡ Disabling an interface from sending/receiving IS-IS packets
¡ Enabling an interface to send small hello packets
¡ Enabling LSP fragment extension
7. (Optional.) Controlling LSP generation, advertisement and reception
¡ Configuring IS-IS route update suppression
8. (Optional.) Configuring advanced IS-IS features
¡ Enabling source address check for hello packets on a P2P interface
¡ Configuring convergence priorities for specific routes
¡ Setting the LSDB overload bit
¡ Setting IS-IS interface cost upon LSDB overload
¡ Configuring system ID to host name mappings
9. (Optional.) Configuring IS-IS logging and SNMP notifications
¡ Enabling the logging of neighbor state changes
¡ Setting the maximum number of log entries that can be recorded
¡ Setting the maximum number of advertisement sources that trigger LSP update logging
¡ Setting the maximum number of IS-IS neighbor relationship troubleshooting entries
¡ Configuring IS-IS network management
10. (Optional.) Configuring IS-IS fast convergence
11. (Optional.) Enhancing IS-IS network security
¡ Configuring neighbor relationship authentication
¡ Configuring area authentication
¡ Configuring routing domain authentication
12. (Optional.) Enhancing IS-IS network reliability:
¡ Enabling IS-IS to adjust the interface cost according to the link quality
¡ Configuring IS-IS neighbor flapping suppression
¡ Configuring IS-IS member port flapping suppression
IPv6 IS-IS tasks at a glance
To configure IPv6 IS-IS, perform the following tasks:
b. (Optional.) Enabling a lightweight IS-IS process
c. (Optional.) Setting the IS level and circuit level
d. (Optional.) Configuring P2P network type for an interface
e. (Optional.) Configuring IS-IS multi-instance processes
2. (Optional.) Configuring IPv6 IS-IS MTR
3. (Optional.) Configuring IS-IS route control
¡ Changing the link cost of a Layer 3 aggregate interface when its bandwidth falls below the threshold
¡ Enabling IS-IS to advertise the maximum link cost to neighbors
¡ Specifying a preference for IS-IS
¡ Configuring the maximum number of ECMP routes
¡ Configuring IS-IS route summarization
¡ Configuring IS-IS route redistribution
¡ Filtering routes calculated from received LSPs
¡ Configuring IS-IS route leaking
¡ Advertising IS-IS link state information to other protocols
¡ Configuring the IPv6 IS-IS link tag feature
4. (Optional.) Configuring IS-IS to advertise network performance parameters
¡ Enabling IS-IS to advertise link attributes in LSPs
¡ Advertising link delay information
¡ Advertising link bandwidth information
¡ Advertising link loss information
5. (Optional.) Configuring IS-IS flexible algorithm
6. (Optional.) Configuring IS-IS timers
¡ Specifying the interval for sending IS-IS hello packets
¡ Specifying the interval for sending IS-IS CSNP packets
¡ Setting the maximum age of LSPs
¡ Setting the LSP refresh interval and generation interval
¡ Setting LSP sending intervals
¡ Setting the LSP receiving interval
¡ Setting the lifetime for expired LSPs in the LSDB
¡ Setting the SPF calculation interval
7. (Optional.) Configuring IS-IS packet-related features
¡ Configuring a DIS priority for an interface
¡ Configuring the administrative tag value for an interface
¡ Specifying the IS-IS hello multiplier
¡ Disabling an interface from sending/receiving IS-IS packets
¡ Enabling an interface to send small hello packets
¡ Enabling LSP fragment extension
8. (Optional.) Controlling LSP generation, advertisement and reception
¡ Configuring IS-IS route update suppression
9. (Optional.) Configuring advanced IS-IS features
¡ Enabling source address check for hello packets on a P2P interface
¡ Configuring convergence priorities for specific routes
¡ Setting the LSDB overload bit
¡ Setting IS-IS interface cost upon LSDB overload
¡ Configuring system ID to host name mappings
10. (Optional.) Enabling BIER for an IS-IS process
11. (Optional.) Configuring IS-IS logging and SNMP notifications
¡ Enabling the logging of neighbor state changes
¡ Setting the maximum number of log entries that can be recorded
¡ Setting the maximum number of advertisement sources that trigger LSP update logging
¡ Setting the maximum number of IS-IS neighbor relationship troubleshooting entries
¡ Configuring IS-IS network management
12. (Optional.) Configuring IS-IS fast convergence
13. (Optional.) Enhancing IS-IS network security
¡ Configuring neighbor relationship authentication
¡ Configuring area authentication
¡ Configuring routing domain authentication
14. (Optional.) Enhancing IS-IS network reliability:
¡ Enabling IS-IS to adjust the interface cost according to the link quality
¡ Configuring IS-IS neighbor flapping suppression
¡ Configuring IS-IS member port flapping suppression
Configuring basic IS-IS
Enabling IPv4 IS-IS
1. Enter system view.
system-view
2. Enable IS-IS and enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
By default, IS-IS is disabled.
3. Assign a NET.
network-entity net
By default, NET is not assigned.
|
CAUTION: When you execute the network-entity command together with the cost-style and is-level commands for the same IS-IS process, execute the network-entity command at last. Incorrect configuration order might cause data loss because the IS-IS process will restart. |
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Enable IS-IS on the interface.
isis enable [ process-id ]
By default, IS-IS is disabled.
Enabling IPv6 IS-IS
1. Enter system view.
system-view
2. Enable an IS-IS process and enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
By default, no IS-IS process is enabled.
3. Configure the NET for the IS-IS process.
network-entity net
By default, the NET is not configured.
|
CAUTION: When you execute the network-entity command together with the cost-style and is-level commands for the same IS-IS process, execute the network-entity command at last. Incorrect configuration order might cause data loss because the IS-IS process will restart. |
4. Create the IPv6 address family and enter its view.
address-family ipv6 [ unicast ]
5. Return to IS-IS view.
quit
6. Return to system view.
quit
7. Enter interface view.
interface interface-type interface-number
8. Enable IPv6 for IS-IS on the interface.
isis ipv6 enable [ process-id ]
By default, IPv6 is disabled for IS-IS on an interface.
Enabling a lightweight IS-IS process
About this task
Enabling multiple IS-IS processes on a device might cause memory insufficiency. To resolve this issue, perform this task to enable lightweight IS-IS processes.
Restrictions and guidelines
Although lightweight processes use less memory resources than traditional processes, device performance might degrade when a large number of neighbors and routes exist. As a best practice, plan the number of lightweight IS-IS processes to be enabled on the basis of the device resource condition.
Procedure
1. Enter system view.
system-view
2. Enable a lightweight IS-IS process and enter its view.
isis [ process-id ] lite [ vpn-instance vpn-instance-name ]
Setting the IS level and circuit level
About this task
Follow these guidelines when you configure the IS level for routers in only one area:
· Set the IS level of all routers to Level-1 or Level-2 rather than different levels because the routers do not need to maintain two identical LSDBs.
· Set the IS level to Level-2 on all routers in an IP network for good scalability.
For an interface of a Level-1 or Level-2 router, the circuit level can only be Level-1 or Level-2. For an interface of a Level-1-2 router, the default circuit level is Level-1-2. If the router only needs to form Level-1 or Level-2 neighbor relationships, set the circuit level for its interfaces to Level-1 or Level-2. This will limit neighbor relationship establishment.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify the IS level.
is-level { level-1 | level-1-2 | level-2 }
By default, the IS level is Level-1-2.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Specify the circuit level.
isis circuit-level [ level-1 | level-1-2 | level-2 ]
By default, an interface can establish either the Level-1 or Level-2 adjacency.
Configuring P2P network type for an interface
About this task
Interfaces with different network types operate differently. For example, broadcast interfaces on a network must elect the DIS and flood CSNP packets to synchronize the LSDBs. However, P2P interfaces on a network do not need to elect the DIS, and have a different LSDB synchronization mechanism.
If only two routers exist on a broadcast network, set the network type of attached interfaces to P2P. This avoids DIS election and CSNP flooding, saving network bandwidth and speeding up network convergence.
Restrictions and guidelines
For an NBMA interface, such as an ATM interface, you must configure point-to-point or broadcast subinterfaces.
The local device and the remote device might fail to establish a neighbor relationship when their hello packets use different destination MAC addresses. To avoid this issue, use the isis circuit-type p2p mac-by-level command on both the local device and the remote device to ensure that their hello packets use the same destination MAC address.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure P2P network type for an interface.
isis [ process-id process-id ] circuit-type p2p
By default, the network type of an interface varies by physical interface.
Perform this task only for a broadcast network that has up to two attached routers.
4. (Optional.) Enable the P2P interface to determine the destination MAC address of hello packets by IS-IS level.
isis circuit-type p2p mac-by-level
By default, the destination MAC address is 0900-2b00-0005 for the Level-1 hello packets and the Level-2 hello packets sent from a P2P interface.
After you configure this command, the destination MAC address is 0180-c200-0014 for Level-1 hello packets and is 0180-c200-0015 for Level-2 hello packets.
Configuring IS-IS multi-instance processes
About this task
|
|
NOTE: IS-IS processes not enabled with the multi-instance process feature are called traditional IS-IS processes. IS-IS processes enabled with the multi-instance process feature are called IS-IS multi-instance processes. |
By default, an interface supports only one IS-IS process. To configure multiple IS-IS processes on a device, you must add more interfaces to the device and configure the interfaces manually. To simplify configuration, use the IS-IS multi-instance process feature to configure multiple IS-IS multi-instance processes as well as a traditional IS-IS process on an interface.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable the IS-IS multi-instance process and specify an instance ID for the process.
multi-instance enable iid iid-value
By default, IS-IS multi-instance process is disabled.
4. Configure IS-IS multi-instance processes on an interface:
a. Return to system view.
quit
b. Enter interface view.
interface interface-type interface-number
c. Enable an IS-IS multi-instance process on the interface:
IPv4:
isis enable [ process-id ]
By default, IPv4 IS-IS is disabled on an interface, and the interface is not enabled with any IS-IS processes.
IPv6:
isis ipv6 enable [ process-id ]
By default, IPv6 IS-IS is disabled on an interface, and the interface is not enabled with any IS-IS processes.
Configuring IPv6 IS-IS MTR
About this task
On a network, IPv4 and IPv6 topologies must be consistent so that both IPv6 IS-IS and IPv4 IS-IS can use the SPF algorithm to perform route calculation. If they are different, routers supporting both IPv4 and IPv6 might send IPv6 packets to routers that do not support IPv6, resulting in packet loss.
To resolve this issue, configure IPv6 IS-IS MTR to perform route calculation separately in IPv4 and IPv6 topologies.
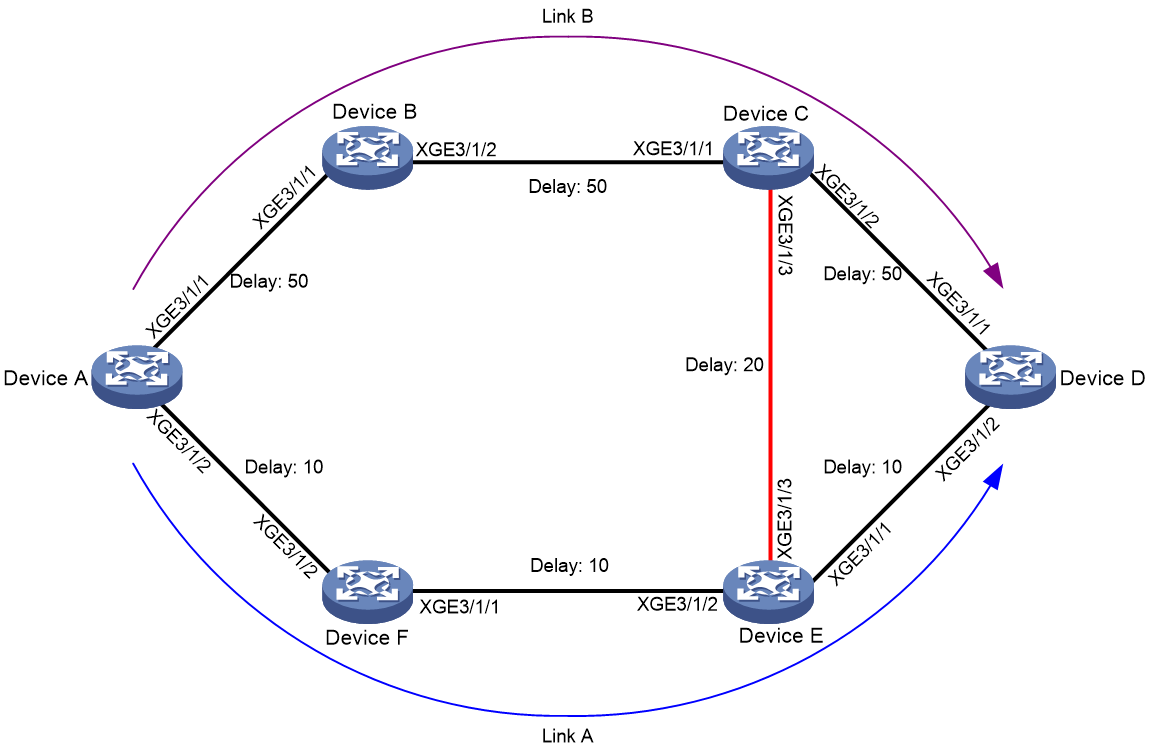
As shown in Figure 7, the numbers refer to the link costs. Router A, Router B, and Router D support both IPv4 and IPv6. Router C supports only IPv4 and cannot forward IPv6 packets.
Enable IPv6 IS-IS MTR on Router A, Router B, Router C, and Router D to make them perform route calculation separately in IPv4 and IPv6 topologies. With this configuration, Router A does not forward IPv6 packets destined to Router D through Router B, avoiding packet loss.
Restrictions and guidelines
As a best practice to avoid route calculation failures, configure this feature when both IPv4 and IPv6 topologies exist in the network.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify an IS-IS cost style.
cost-style { compatible | wide | wide-compatible }
By default, IS-IS only transmits and receives packets using the narrow cost style.
4. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
5. Enable IPv6 IS-IS MTR.
multi-topology [ compatible ]
By default, IPv6 IS-IS MTR is disabled.
Configuring IS-IS route control
Configuring IS-IS link cost
About this task
The IS-IS cost of an interface is determined in the following order:
1. IS-IS cost specified in interface view.
2. IS-IS cost specified in system view.
The cost is applied to the interfaces associated with the IS-IS process.
3. Automatically calculated cost.
If the cost style is wide or wide-compatible, IS-IS automatically calculates the cost using the formula: Interface cost = (Bandwidth reference value / Expected interface bandwidth) × 10, in the range of 1 to 16777214. For other cost styles, Table 3 applies.
Configure the expected bandwidth of an interface with the bandwidth command.
Table 3 Automatic cost calculation scheme for cost styles other than wide and wide-compatible
|
Interface bandwidth |
Interface cost |
|
≤ 10 Mbps |
60 |
|
≤ 100 Mbps |
50 |
|
≤ 155 Mbps |
40 |
|
≤ 622 Mbps |
30 |
|
≤ 2500 Mbps |
20 |
|
> 2500 Mbps |
10 |
4. If none of the above costs is used, a default cost of 10 applies.
Configuring an IPv4 IS-IS cost for an interface
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. (Optional.) Specify an IS-IS cost style.
cost-style { narrow | wide | wide-compatible | { compatible | narrow-compatible } [ relax-spf-limit ] }
By default, the IS-IS cost type is narrow.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Specify a cost for the IS-IS interface.
isis [ process-id process-id ] cost cost-value [ level-1 | level-2 ]
By default, no cost for the interface is specified.
Configuring a global IPv4 IS-IS cost
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify a global IS-IS cost.
circuit-cost cost-value [ level-1 | level-2 ]
By default, no global cost is specified.
Enabling automatic IPv4 IS-IS cost calculation
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable automatic IS-IS cost calculation.
auto-cost enable
By default, automatic IS-IS cost calculation is disabled.
4. (Optional.) Configure a bandwidth reference value for automatic IS-IS cost calculation.
bandwidth-reference value
The default setting is 100 Mbps.
Configuring an IPv6 IS-IS cost for an interface
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. (Optional.) Specify an IS-IS cost style.
cost-style { narrow | wide | wide-compatible | { compatible | narrow-compatible } [ relax-spf-limit ] }
By default, the IS-IS cost type is narrow.
4. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
5. Return to IS-IS view.
quit
6. Return to system view.
quit
7. Enter interface view.
interface interface-type interface-number
8. Enable IPv6 for IS-IS on the interface.
isis ipv6 enable [ process-id ]
By default, IPv6 is disabled for IS-IS on an interface.
9. Specify an IPv6 cost for the IS-IS interface.
isis [ process-id process-id ] ipv6 cost cost-value [ level-1 | level-2 ]
By default, no IPv6 cost is specified for the interface.
Configuring a global IPv6 IS-IS cost
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Specify a global IPv6 IS-IS cost.
circuit-cost cost-value [ level-1 | level-2 ]
By default, no global IPv6 cost is specified.
Enabling automatic IPv6 IS-IS cost calculation
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. (Optional.) Specify an IS-IS cost style.
cost-style { narrow | wide | wide-compatible | { compatible | narrow-compatible } [ relax-spf-limit ] }
4. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
5. Enable automatic IPv6 IS-IS cost calculation.
auto-cost enable
By default, automatic IPv6 IS-IS cost calculation is disabled.
6. (Optional.) Configure a bandwidth reference value for automatic IPv6 IS-IS cost calculation.
bandwidth-reference value
By default, the bandwidth reference value is 100 Mbps.
Changing the link cost of a Layer 3 aggregate interface when its bandwidth falls below the threshold
About this task
When a member port of a Layer 3 aggregate interface goes down, the bandwidth of the aggregate interface decreases and services might be interrupted. To resolve this issue, perform this task to change the link cost of a Layer 3 aggregate interface as follows:
· When the bandwidth of the Layer 3 aggregate interface falls below the specified threshold, the aggregate interface uses the specified link cost. Make sure the link cost you specified is larger than the original link cost, so that IS-IS can select an optimal path for traffic forwarding.
· When the bandwidth of the Layer 3 aggregate interface is equal to or larger than the bandwidth threshold, the aggregate interface uses the original link cost.
For more information about IS-IS link cost, see "Configuring IS-IS link cost."
Procedure
1. Enter system view.
system-view
2. Enter Layer 3 aggregate interface view or Layer 3 aggregate subinterface view.
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number [ pex ]
¡ Enter Layer 3 aggregate interface view or Layer 3 aggregate subinterface view.
interface route-aggregation interface-number.subnumber
3. Change the link cost of the interface to the specified value when the bandwidth of the interface falls below the specified threshold.
IPv4:
isis cost-fallback cost-value threshold bandwidth-value [ level-1 | level-2 ]
IPv6:
isis ipv6 cost-fallback cost-value threshold bandwidth-value [ level-1 | level-2 ]
By default, a Layer 3 aggregate interface uses the original link cost.
Enabling IS-IS to advertise the maximum link cost to neighbors
About this task
On an IS-IS network, when a link recovers from failures or the state of an interface changes, IS-IS will re-establish neighbor relationships and perform route convergence. During the route convergence process, routing loops and traffic loss might occur because the convergence speeds of the nodes are different. To address this issue, enable IS-IS to advertise the maximum link cost to neighbors within the specified period of time, so the traffic forwarding path remains unchanged. After the specified period of time, IS-IS advertises the original link cost to neighbors and performs optimal route selection again.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable IS-IS to advertise the maximum link cost to neighbors within the specified period of time.
isis peer hold-max-cost duration time
By default, IS-IS advertises the original link cost to neighbors during a route convergence.
Specifying a preference for IS-IS
About this task
If multiple routing protocols find routes to the same destination, the route found by the routing protocol that has the highest preference is selected as the optimal route.
Perform this task to assign a preference to IS-IS directly or by using a routing policy. For more information about the routing policy, see "Configuring routing policies."
Configuring a preference for IPv4 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Configure a preference for IPv4 IS-IS.
preference { preference | route-policy route-policy-name } *
The default setting is 15.
Configuring a preference for IPv6 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Configure a preference for IPv6 IS-IS.
preference { preference | route-policy route-policy-name } *
The default setting is 15.
Configuring the maximum number of ECMP routes
Perform this task to implement load sharing over ECMP routes.
Configuring the maximum number of ECMP routes for IPv4 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Specify the maximum number of ECMP routes.
maximum load-balancing number
By default, the maximum number of IPv4 IS-IS ECMP routes is 64.
Configuring the maximum number of ECMP routes for IPv6 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Specify the maximum number of ECMP routes.
maximum load-balancing number
By default, the maximum number of IPv6 IS-IS ECMP routes equals the maximum number of ECMP routes, which is configurable by using the max-ecmp-num command.
Configuring IS-IS route summarization
About this task
Perform this task to summarize specific routes, including IS-IS routes and redistributed routes, into a single route. Route summarization can reduce the routing table size and the LSDB scale.
Route summarization applies only to locally generated LSPs.
Configuring IPv4 IS-IS route summarization
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Configure IPv4 IS-IS route summarization.
summary ip-address { mask-length | mask } [ avoid-feedback | generate_null0_route | [ level-1 | level-1-2 | level-2 ] | tag tag ] *
By default, IPv4 IS-IS route summarization is not configured.
The cost of the summary route is the lowest one among the costs of the more-specific routes.
Configuring IPv6 IS-IS route summarization
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Configure IPv6 IS-IS route summarization.
summary ipv6-prefix prefix-length [ avoid-feedback | generate_null0_route | [ level-1 | level-1-2 | level-2 ] | tag tag ] *
By default, IPv6 IS-IS route summarization is not configured.
Advertising a default route
About this task
IS-IS cannot redistribute a default route to its neighbors. This task enables IS-IS to advertise a default route of 0.0.0.0/0 in an LSP to the same-level neighbors. Upon receiving the default route, the neighbors add it into their routing table.
When multiple devices exist in the IS-IS network, configuring default route advertisement is more flexible than configuring default static routes. For example, if multiple border devices exist in the IS-IS routing domain, you can configure a routing policy to control the advertisement of default routes and prevent routing blackholes.
Advertising an IPv4 IS-IS default route
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Advertise a Level-1 or Level-2 default route.
default-route-advertise [ avoid-learning | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
By default, IPv4 IS-IS does not advertise a Level-1 or Level-2 default route.
Advertising an IPv6 IS-IS default route
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Advertise a Level-1 or Level-2 default route.
default-route-advertise [ avoid-learning | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
By default, IPv6 IS-IS does not advertise a Level-1 or Level-2 default route.
Configuring IS-IS route redistribution
About this task
After you enable default route advertisement for a border device in the IS-IS routing domain, the border device acts as a gateway to external routing domains for other devices in the same routing domain. The service burden on the border device will be heavy when it receives a large number of packets from other devices. Besides, selecting the optimal route to an external routing domain might be an issue when multiple border devices exist in the IS-IS routing domain. To resolve these issues, you can perform this task to redistribute routes from other routing protocols into IS-IS.
You can configure the cost value for redistributed IGP routes and BGP routes. With an ACL, IP prefix list, or routing policy, IS-IS can filter redistributed routes. IS-IS adds only matching routes into its routing table, and then advertises them in LSPs.
To avoid the potential impact on the performance of some network devices, you can specify the maximum number of redistributed routes.
Configuring IPv4 IS-IS route redistribution
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Redistribute routes from other routing protocols or other IS-IS processes.
import-route bgp [ as-number ] [ allow-ibgp ] [ cost cost-value | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route bgp [ as-number ] [ allow-ibgp ] inherit-cost [ [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route { direct | static | unr } [ cost cost-value | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route { direct | static | unr } inherit-cost [ [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route eigrp [ eigrp-as | all-as ] [ allow-direct | cost cost-value | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route eigrp [ eigrp-as | all-as ] inherit-cost [ allow-direct | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route rip [ process-id | all-processes ] [ allow-direct | cost cost-value | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route rip [ process-id | all-processes ] inherit-cost [ allow-direct | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
import-route { isis | ospf } [ process-id | all-processes ] [ allow-direct | cost cost-value | cost-type { external | internal } | [ level-1 | level-1-2 | level-2 ] | no-sid | route-policy route-policy-name | tag tag ] *
import-route { isis | ospf } [ process-id | all-processes ] inherit-cost [ allow-direct | [ level-1 | level-1-2 | level-2 ] | no-sid | route-policy route-policy-name | tag tag ] *
By default, IS-IS does not redistribute routes.
This command redistributes only active routes. To display active routes, use the display ip routing-table protocol command.
4. (Optional.) Configure the maximum number of redistributed Level 1/Level 2 IPv4 routes.
import-route limit number
By default, the maximum number of redistributed Level 1/Level 2 IPv4 routes is not configured.
5. (Optional.) Enable IPv4 IS-IS to filter redistributed routes.
filter-policy { ipv4-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } export [ bgp | direct | eigrp eigrp-as | { isis | ospf | rip } process-id | static | unr ]
By default, IPv4 IS-IS does not filter redistributed routes.
6. (Optional.) Exclude redistributed IPv4 routes from route calculation.
import-route no-route-calculate
By default, redistributed IPv4 routes can participate in route calculation.
Configuring IPv6 IS-IS route redistribution
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Redistribute routes from other routing protocols or other IS-IS processes.
import-route protocol [ as-number | process-id ] [ allow-ibgp ] [ allow-direct | [ cost cost-value | inherit-cost ] | [ level-1 | level-1-2 | level-2 ] | route-policy route-policy-name | tag tag ] *
By default, no route is redistributed.
5. (Optional.) Configure the maximum number of redistributed Level 1/Level 2 IPv6 routes.
import-route limit number
The default for this command varies by device model.
6. (Optional.) Enable IPv6 IS-IS to filter redistributed routes.
filter-policy { ipv6-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } export [ bgp4+ | direct | { isisv6 | ospfv3 | ripng } process-id | static | unr ]
By default, IPv6 IS-IS does not filter redistributed routes.
7. (Optional.) Exclude redistributed IPv6 routes from route calculation.
import-route no-route-calculate
By default, redistributed IPv6 routes can participate in route calculation.
Filtering routes calculated from received LSPs
About this task
IS-IS saves LSPs received from neighbors in the LSDB, and uses the SPF algorithm to calculate the shortest path tree with itself as the root. IS-IS installs the calculated routes to the IS-IS routing table and the optimal routes to the IP routing table.
Perform this task to filter calculated routes. Only routes that are not filtered can be added to the IP routing table. The filtered routes retain in the IS-IS routing table and can be advertised to neighbors.
Filtering IPv4 IS-IS routes calculated from received LSPs
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Filter routes calculated using received LSPs.
filter-policy { ipv4-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } import
By default, IPv4 IS-IS route filtering is not configured.
Filtering IPv6 IS-IS routes calculated from received LSPs
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Filter routes calculated using received LSPs.
filter-policy { ipv6-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } import
By default, IPv6 IS-IS route filtering is not configured.
Configuring IS-IS route leaking
About this task
By default, the Level-2 router does not advertise the routes of the Level-2 area and other Level-1 areas to a Level-1 area. The Level-1 routers in that Level-1 area sends packets destined for other areas to the nearest Level-1-2 router. As a result, IS-IS cannot use the optimal route to forward these packets. To resolve this issue, perform this task to configure IS-IS route leaking.
After you configure route leaking on a Level-1-2 router, this feature functions as follows:
1. Filters routes with the specified criteria.
2. Imports the desired routes from other Level-1 areas and the Level-2 area into the Level-1 area to which the Level-1-2 router belongs.
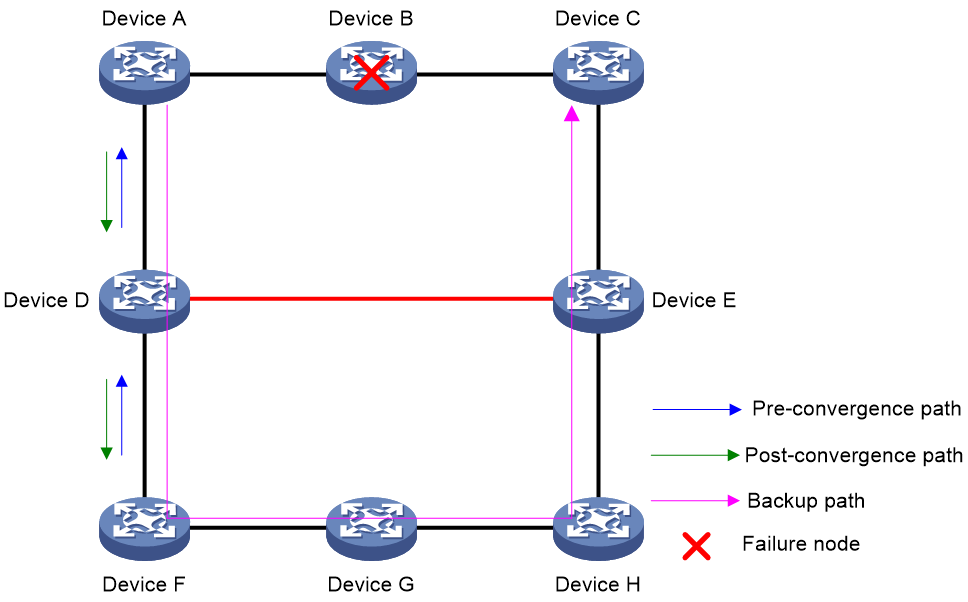
As shown in Figure 8, the optimal path from Device A to Device F is Device A > Device B > Device D > Device E > Device F and the total cost is 40. By default, the actual path to Device F on Device A is Device A > Device C > Device E > Device F and the total cost is 70. After you configure route leaking on Device C and Device D, IS-IS will use the Device A > Device B > Device D > Device E > Device F path to forward traffic from Device A to Device F.
Perform this task to control route advertisement (route leaking) between Level-1 and Level-2.
You can configure IS-IS to advertise routes from Level-2 to Level-1, and to not advertise routes from Level-1 to Level-2.
Configuring IPv4 IS-IS route leaking
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Configure route leaking from Level-1 to Level-2.
import-route isis level-1 into level-2 [ filter-policy { ipv4-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } | no-sid | tag tag ] *
By default, IS-IS advertises routes from Level-1 to Level-2.
4. Configure route leaking from Level-2 to Level-1.
import-route isis level-2 into level-1 [ filter-policy { ipv4-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } | no-sid | tag tag ] *
By default, IS-IS does not advertise routes from Level-2 to Level-1.
Configuring IPv6 IS-IS route leaking
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Configure route leaking from Level-2 to Level-1.
import-route isisv6 level-2 into level-1 [ filter-policy { ipv6-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } | tag tag ] *
By default, IS-IS does not advertise routes from Level-2 to Level-1.
5. Configure route leaking from Level-1 to Level-2.
import-route isisv6 level-1 into level-2 [ filter-policy { ipv6-acl-number | prefix-list prefix-list-name | route-policy route-policy-name } | tag tag ] *
By default, IS-IS advertises routes from Level-1 to Level-2.
Advertising IS-IS link state information to other protocols
About this task
After the device advertises IS-IS link state information to other protocols, such as BGP and SR-MPLS TE Policy, these protocols can then advertise the information for intended applications.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Advertise IS-IS link state information to BGP.
distribute { bgp-ls | link-state } [ instance-id id ] [ level-1 | level-2 ]
By default, the device does not advertise IS-IS link state information to any other protocol.
Configuring the IPv6 IS-IS link tag feature
About this task
Set an IPv6 IS-IS link tag for a device (for example, Device A) and enable IPv6 IS-IS link tag inheritance on another device (for example, Device B) to filter routes as follows:
1. Device A advertises the IPv6 IS-IS link tag in LSPs.
2. After receiving the LSPs advertised by Device A, Device B inherits the IPv6 IS-IS link tag advertised by Device A.
If Device B receives multiple link tags from Device A, Device B selects and inherits only one tag.
3. Device B configures the link tag as the route tag for all routes that pass the link.
Then, the route tag can be used for route filtering.
This feature is usually used in Source Address Validation Architecture (SAVA) scenarios to ensure the consistency of IPv6 SAVA entries on multiple gateway devices:
1. Set an IPv6 IS-IS link tag for the customer-side interface on the gateway device that advertises IPv6 SAVA entries.
2. Enable IPv6 IS-IS link tag inheritance on the gateway device that receives IPv6 SAVA entries. The device generates an IPv6 SAVA entry based on a route prefix if the following two tags are the same:
¡ The route tag configured by executing the ipv6 sava import remote-route-tag command.
¡ The IPv6 IS-IS link tag that the route inherits.
For more information about SAVA and IPv6 SAVA entries, see SAVA configuration in Security Configuration Guide.
Setting an IPv6 IS-IS link tag for an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Set an IPv6 IS-IS link tag for the interface.
isis ipv6 link-tag tag
By default, no IPv6 IS-IS link tag is configured for the interface.
Enabling IPv6 IS-IS link tag inheritance
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IPv6 IS-IS link tag inheritance.
link-tag inherit enable
By default, IPv6 IS-IS link tag inheritance is disabled.
Configuring IS-IS to advertise network performance parameters
About IS-IS network performance parameters
A controller in a network performance-sensitive scenario uses parameters that can reflect the network performance as route calculation metrics.
Perform this task to enable IS-IS to advertise network performance parameters and report the information to the controller through BGP-LS. Then, the controller performs optimal route calculation based on the network performance parameters.
Network performance parameters include the following:
· Delay—Unidirectional link delay performance metrics, including:
¡ Average link delay—Average unidirectional link delay.
¡ Min/Max link delay—Minimum/maximum unidirectional link delay.
¡ Average link delay variation—Average unidirectional link delay variation.
· Bandwidth—Unidirectional link bandwidth performance metrics, including:
¡ Remaining bandwidth—Remaining unidirectional link bandwidth.
¡ Available bandwidth—Available unidirectional link bandwidth.
¡ Utilized bandwidth—Unidirectional link bandwidth usage.
· Link loss—Unidirectional link loss performance metric.
Restrictions and guidelines
To enable IS-IS to advertise link attributes in LSPs, perform one or more of the following tasks as needed:
· Execute the advertise link-attributes command to enable IS-IS to advertise link attributes in LSPs.
· Enable MPLS TE on the device that runs IPv4 IS-IS and the interface enabled with IPv4 IS-IS. For more information, see MPLS TE configuration in MPLS Configuration Guide.
· Enable IPv6 TE on the device that runs IPv6 IS-IS. For more information, see SRv6 configuration in Segment Routing Configuration Guide.
· Execute the te attribute enable command to enable IS-IS to advertise TE attributes.
Enabling IS-IS to advertise link attributes in LSPs
About this task
Perform this task to enable IS-IS to advertise network performance parameters through sub-TLVs in the extended IS reachability TLV (type 22).
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv6 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IS-IS to advertise link attributes in LSPs.
advertise link-attributes
By default, IS-IS does not advertise link attributes in LSPs.
Advertising link delay information
About this task
Perform this task to enable IS-IS to advertise link delay information and report the information to the controller through BGP-LS. Then, the controller performs optimal route calculation based on the link delay information.
Perform either of the following tasks to obtain link delay information of an interface:
· Static configuration—Execute the isis link-delay command to manually configure link delay parameters on the interface.
· Dynamic acquisition—Execute the test-session bind interface command to bind the interface as the out interface of a TWAMP Light test session. Then, TWAMP Light will send the detected link delay information to the interface, and the interface will immediately report the link delay information to IS-IS. For more information about TWAMP Light, see NQA configuration in Network Management and Monitoring Configuration Guide.
In dynamic acquisition mode, NQA TWAMP-light advertises link delay information to the associated interface at rather short intervals. As a result, the interface reports link delay information to IS-IS frequently. As a result, IS-IS needs to frequently process the link delay information and reports the information to the controller through BGP-LS, which consumes a lot of device and network resources. To resolve this issue, you can configure IS-IS to suppress advertisement of link delay information.
Link delay advertisement suppression works as follows:
· NQA TWAMP Light sends the detected link delay information to the associated interface at intervals, and then the interface will report the link delay information to IS-IS.
· IS-IS advertises link delay information through BGP-LS at intervals specified by the time-value argument. IS-IS does not advertise link delay information within the suppression timer except for the following conditions:
¡ The variation ratio between two consecutive minimum delays is larger than or equivalent to the suppression threshold for the delay variation ratio.
¡ The absolute value of the difference between two consecutive minimum delays is larger than or equivalent to the suppression threshold for the absolute value of the delay variation.
Restrictions and guidelines
For an interface, static link delay parameters take precedence over the parameters obtained through dynamic acquisition.
As a best practice, set the link delay advertisement suppression interval to be larger than or equivalent to the NQA delay measurement interval.
Configuring link delay parameters
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure link delay parameters.
isis link-delay { average average-delay-value | min min-delay-value max max-delay-value | variation variation-value } *
By default, link delay parameters are not configured.
Enabling IS-IS to advertise link delay information
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv4 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IS-IS to advertise link delay information.
metric-delay advertisement enable [ level-1 | level-2 ]
By default, IS-IS does not advertise link delay information.
Configuring IS-IS to suppress link delay information advertisement
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS to suppress link delay information advertisement.
metric-delay suppression timer time-value percent-threshold percent-value absolute-threshold absolute-value
By default, IS-IS suppresses link delay information advertisement.
If you set an argument to 0, the corresponding suppression mechanism does not take effect. If you set all arguments to 0, IS-IS does not suppress link delay information advertisement.
Advertising link bandwidth information
About this task
Perform this task to enable IS-IS to advertise link bandwidth information and report the information to the controller through BGP-LS. Then, the controller performs optimal route calculation based on the link bandwidth information.
By default, an interface reports link bandwidth information to IS-IS at short intervals, for example, 100 milliseconds. As a result, IS-IS needs to frequently process the link bandwidth information and reports the information to the controller through BGP-LS, which consumes a lot of device and network resources. To resolve this issue, you can configure IS-IS to suppress advertisement of link bandwidth information.
Link bandwidth advertisement suppression works as follows:
· An interface reports link bandwidth information to IS-IS at negotiated intervals.
· IS-IS advertises link bandwidth information through BGP-LS at intervals specified by the time-value argument.
Restrictions and guidelines
As a best practice, set the link bandwidth advertisement suppression interval to be larger than or equivalent to the Ethernet interface bandwidth measurement interval.
Enabling IS-IS to advertise link bandwidth information
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv4 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IS-IS to advertise link bandwidth information.
metric-bandwidth advertisement enable [ level-1 | level-2 ]
By default, IS-IS does not advertise link bandwidth information.
Configuring IS-IS to suppress link bandwidth information advertisement
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS to suppress link bandwidth information advertisement.
metric-bandwidth suppression timer time-value
By default, IS-IS suppresses link bandwidth information advertisement.
If you set the time-value argument to 0, IS-IS does not suppress link bandwidth information advertisement.
Advertising link loss information
About this task
Perform this task to enable IS-IS to advertise link loss information and report the information to the controller through BGP-LS. Then, the controller performs optimal route calculation based on the link loss information.
Perform either of the following tasks to obtain link loss information of an interface:
· Static configuration—Execute the isis link-loss command to manually configure the link loss of an interface.
· Dynamic acquisition—Execute the test-session bind interface command to bind the interface as the out interface of a TWAMP Light test session. Then, TWAMP Light will send the detected link loss information to the interface, and the interface will immediately report the link loss information to IS-IS. For more information about TWAMP Light, see NQA configuration in Network Management and Monitoring Configuration Guide.
In dynamic acquisition mode, NQA TWAMP-ligh advertises link loss information to the associated interface at rather short intervals. As a result, the interface reports link loss information to IS-IS frequently. As a result, IS-IS needs to frequently process the link loss information and reports the information to the controller through BGP-LS, which consumes a lot of device and network resources. To resolve this issue, you can configure IS-IS to suppress advertisement of link loss information.
Link loss advertisement suppression works as follows:
· NQA TWAMP Light sends the detected link loss information to the associated interface at intervals, and then the interface will report the link loss information to IS-IS.
· IS-IS advertises link loss information through BGP-LS at intervals specified by the time-value argument. IS-IS does not advertise link loss information within the suppression timer except for the following conditions:
¡ The variation ratio between two consecutive link loss values is larger than or equivalent to the suppression threshold for the link loss variation ratio.
¡ The absolute value of the difference between two consecutive link loss values is larger than or equivalent to the suppression threshold for the absolute link loss variation.
Restrictions and guidelines
For the same interface, the isis link-loss command takes precedence over the test-session bind interface command.
As a best practice, the suppression timer you specified should not be less than the NQA measurement interval. For more information about NQA, see NQA configuration in Network Management and Monitoring Configuration Guide.
Configuring link loss parameters
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure link loss parameters.
isis link-loss loss-value
By default, link loss parameters are not configured.
Enabling IS-IS to advertise link loss information
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv4 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IS-IS to advertise link loss information.
metric-link-loss advertisement enable [ level-1 | level-2 ]
By default, IS-IS does not advertise link loss information.
Configuring IS-IS to suppress link loss information advertisement
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS to suppress link loss information advertisement.
metric-link-loss suppression timer timer-value percent-threshold percent-value absolute-threshold absolute-value
By default, IS-IS suppresses link loss information advertisement.
If you set an argument to 0, the corresponding suppression mechanism does not take effect. If you set all arguments to 0, IS-IS does not suppress link loss information advertisement.
Configuring IS-IS flexible algorithm
About IS-IS flexible algorithm
IS-IS traditionally calculates optimal paths based on the IGP metric values of all links. This might not meet the traffic requirements. Flexible algorithm allows users to control path selection flexibly by customizing path calculation methods.
Flexible algorithm concepts
· FAD—Flexible algorithm definition, a composite of calculation type, metric type, and constraints.
· Calculation type—Algorithm used for path calculation. In the current software version, only the SPF algorithm is supported.
· Metric type—Metric type used for optimal path calculation. Available metric types include IS-IS link cost, link delay, and TE cost. For more information about TE cost, see MPLS TE configuration in MPLS TE Configuration Guide.
· Constraint—Link filter criteria for topology generation. You can use a set of constraints to exclude links with specific affinities from or include them in the flexible algorithm topology. Flexible algorithms use the following link attributes:
¡ Affinity attribute—A link attribute, also known as link color. IS-IS uses LSPs that contain extended administrative group sub-TLVs to advertise FAD constraints, including flexible algorithm exclude admin group sub-TLV, flexible algorithm include-any admin group sub-TLV, and flexible algorithm include-all admin group sub-TLV, which are corresponding to the exclude-any, include-any, and include-all rules, respectively.
¡ SRLG—A Shared Risk Link Group (SRLG) is a set of links that share a resource. If one link in the group fails, the other links might also fail. IS-IS uses LSPs that contain flexible algorithm exclude SRLG sub-TLVs to advertise SRLGs that FAD excludes. For more information about SRLG, see MPLS TE configuration in MPLS Configuration Guide.
· Flexible algorithm ID—Unique identifier of a flexible algorithm. The ID range is 128 to 255.
Flexible algorithm topology
The flexible algorithm topology is the scope of path calculation. It consists of links selected by the flexible algorithm based on the link constraints. The flexible algorithm excludes a node or a link from the topology in one of the following scenarios:
· The node is not configured with the flexible algorithm.
· The link meets one of the following requirements:
¡ An exclude-any constraint exists in the FAD and the link has an affinity that is included in the constraint.
¡ An exclude SRLG constraint exists in the FAD and the link in an SRLG defined by the constraint.
¡ An include-any constraint exists in the FAD and the link does not have any affinity that is included in the constraint.
¡ An include-all constraint exists in the FAD and the link does not have all the affinities that are included in the constraint.
¡ The metric type in the FAD is not IS-IS link cost and the link does not advertise the cost of the metric type.
As shown in Figure 9, when no flexible algorithm is configured, all nodes calculate optimal paths by IS-IS link cost.
Figure 9 Topology without flexible algorithm 130
For comparison, you can configure flexible algorithm 130 for all nodes except Router F. The FAD of flexible algorithm 130 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute red.
In the new topology shown in Figure 10, all nodes calculate optimal paths based on the calculation type and metric type in the FAD.
Figure 10 Topology with flexible algorithm 130
IS-IS flexible algorithm tasks at a glance
To configure IS-IS flexible algorithm, perform the following tasks:
· Configuring the definition of a flexible algorithm
a. Mapping an affinity attribute name to an affinity bit
b. Assigning affinity attributes to IS-IS links
c. Configuring a flexible algorithm
d. (Optional.) Configuring the metric type of a flexible algorithm
· (Optional.) Improving the reliability of a flexible algorithm
¡ Configuring flexible algorithm FRR
¡ Configuring flexible algorithm TI-LFA FRR
¡ Set the priority of an FRR backup path selection policy
· Configuring SR-MPLS flexible algorithm:
¡ Applying a flexible algorithm to SR-MPLS
¡ Configuring color attribute-based traffic redirection
· (Optional.) Applying a flexible algorithm to SRv6
· (Optional.) Enabling trust level-based FAD advertisement
Prerequisites
Configure segment routing before configuring IS-IS flexible algorithms. For more information about SR-MPLS, see SR-MPLS configuration in Segment Routing Configuration Guide. For more information about SRv6, see SRv6 configuration in Segment Routing Configuration Guide.
Mapping an affinity attribute name to an affinity bit
About this task
IS-IS supports a maximum of 256 affinity bits. They are numbered from 0 to 255. You can perform this task to map different affinity attribute names to these bits. As shown in Figure 11, affinity attribute name blue is mapped to bit 1, and red to bit 5.
This feature enables you to configure affinity attributes for links or define the flexible algorithm topology by specifying only the affinity attribute names.
Figure 11 Mapping an affinity attribute to an affinity bit
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Map an affinity attribute name to an affinity bit.
affinity-map affinity-name bit-position bit
By default, no affinity attribute name is mapped to an affinity bit.
Assigning affinity attributes to IS-IS links
About this task
If you perform this task on an IS-IS interface, the links between the interface and its neighbors will carry specific affinity attributes. In a flexible algorithm scenario, these links will be filtered for path calculation based on the link constraints in the FAD.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Assign affinity attributes to IS-IS links.
isis process-id affinity flex-algo { affinity-name }&<1-32>
By default, an IS-IS link has no affinity attributes.
Configuring a flexible algorithm
About this task
An IS-IS node cannot participate in the path calculation for a flexible algorithm unless you configure the flexible algorithm for the node. To use a flexible algorithm for path calculation, you must make sure a minimum of one node can advertises the FAD of that flexible algorithm in LSPs.
Each node that participates in the path calculation for a flexible algorithm can have a different FAD. To avoid routing loops in an FAD advertisement scope (IS-IS area), these nodes must use the same FAD. By convention, a node selects an FAD as follows:
· The FAD with the highest priority will be selected from the FADs advertised within the IS-IS routing domain. If the node does not advertise an FAD, it selects the FAD with the highest priority from the received FADs.
· The FAD with the greatest system ID will be selected from the FADs that have the highest priority.
Procedure
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Create a flexible algorithm and enter its view.
flex-algo flex-algo-id
4. Configure a priority for the flexible algorithm.
priority priority-value
By default, the priority of a flexible algorithm is 128.
5. Configure the link constraints for a flexible algorithm.
¡ Exclude links that have a minimum of one specified affinity attribute.
affinity exclude-any affinity-name&<1-32>
¡ Include links that have a minimum of one specified affinity attribute.
affinity include-any affinity-name&<1-32>
¡ Include links that have all specified affinity attribute.
affinity include-all affinity-name&<1-32>
¡ Specify the SRLG links to be excluded.
exclude-srlg srlg-value&<1-32>
By default, all nodes configured to participate in the path calculation for a flexible algorithm are not excluded from the topology.
6. Enable FAD advertisement on a node.
advertise-definition enable
By default, a node does not advertise the FAD.
Configuring the metric type of a flexible algorithm
About metric type configuration for flexible algorithm
By default, the flexible algorithm uses IS-IS link cost for optimal path calculation. In some scenarios, the paths calculated by the flexible algorithm might not be optimal. To resolve this issue, configure the flexible algorithm to use another metric type for optimal path calculation.
The flexible algorithm supports the following metric types:
· IS-IS link cost.
· Link delay. The flexible algorithm uses the minimum link delay for optimal path calculation.
· TE cost. The flexible algorithm can use the TE cost reported by MPLS TE or the TE cost specified for the flexible algorithm on the interface. The TE cost specified for the flexible algorithm on the interface takes precedence over the TE cost reported by MPLS TE.
Restrictions and guidelines
To enable a flexible algorithm to use link delay for optimal path calculation, enable IS-IS link delay advertisement on all interfaces that participate in path calculation.
To enable a flexible algorithm to use the TE cost reported by MPLS TE for optimal path calculation, make sure the following requirements are met:
· MPLS TE is enabled for each node that participates in path calculation for that flexible algorithm.
· MPLS and MPLS TE are enabled on each interface that participates in path calculation for that flexible algorithm.
· TE attribute advertisement has been enabled or IPv6 TE has been enabled for the IS-IS process. To enable TE attribute advertisement, execute the te attribute enable command. To enable IPv6 TE, execute the router-id command.
· Application-specific link attribute advertisement has been enabled for IS-IS. To enable application-specific link attribute advertisement, execute the advertise application link-attributes command.
Configuring the metric type as link delay
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv6 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IS-IS link delay advertisement.
metric-delay advertisement enable [ level-1 | level-2 ]
By default, IS-IS link delay advertisement is disabled.
5. Enable IS-IS to advertise application-specific link attributes.
advertise application link-attributes { bandwidth | delay | link-loss | unidirectional-bandwidth | srlg | te } [ asla-only ]
advertise application link-attributes { te [ suppression ] | srlg [ suppression ] } *
By default, IS-IS does not advertise any application-specific link attributes.
6. Return to IS-IS view.
quit
7. Enter flexible algorithm view.
flex-algo flex-algo-id
8. Configure the metric type as link delay.
metric-type delay
By default, the metric type is IS-IS link cost.
Configuring the metric type as TE cost reported by MPLS TE
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable IS-IS to advertise TE attributes.
te attribute enable [ level-1 | level-2 ]
By default, IS-IS does not advertise TE attributes.
4. Enter IS-IS IPv4 address family view or IS-IS IPv6 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
5. Enable IS-IS to advertise application-specific link attributes.
advertise application link-attributes { bandwidth | delay | link-loss | unidirectional-bandwidth | srlg | te } [ asla-only ]
advertise application link-attributes { te [ suppression ] | srlg [ suppression ] } *
By default, IS-IS does not advertise any application-specific link attributes.
6. Return to IS-IS view.
quit
7. Enter flexible algorithm view.
flex-algo flex-algo-id
8. Configure the metric type as TE cost.
metric-type te-cost
By default, the metric type is IS-IS link cost.
Configuring the metric type as TE cost specified on the IS-IS interface
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Configure the metric type as TE cost.
metric-type te-cost
By default, the metric type is IS-IS link cost.
5. Return to IS-IS view.
quit
6. Return to system view.
quit
7. Enter interface view.
interface interface-type interface-number
8. Specify the TE cost for flexible algorithm.
isis te-metric flex-algo metric-value
By default, the TE cost for flexible algorithm is not specified on an interface.
Configuring flexible algorithm FRR
About this task
The flexible algorithm FRR is similar to IS-IS LFA FRR, because it uses LFA to calculate a loop-free backup path with the lowest cost based on the topology.
For illustration, flexible algorithm 130 is configured for all nodes in Figure 12. The FAD of flexible algorithm 130 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute red.
Figure 12 Topology without flexible algorithm 130
In Figure 13, after you enable FRR, flexible algorithm 130 uses LFA to calculate a primary path and a backup path from Router A to Router D.
Figure 13 Topology with flexible algorithm 130
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Enable flexible algorithm FRR.
fast-reroute enable
By default, flexible algorithm FRR is enabled.
If no backup paths exist in the topology, execute the undo fast-reroute enable command to disable flexible algorithm FRR to save device resources.
Configuring flexible algorithm TI-LFA FRR
About TI-LFA FRR
Topology-Independent Loop-free Alternate Fast Reroute (TI-LFA FRR) is an enhanced version of LFA FRR. TI-LFA FRR uses the same algorithms to calculate P space and Q space as Remote LFA FRR. This feature can protect a topology without PQ nodes.
For more information about P space and Q space, see "Configuring IS-IS remote LFA FRR."
For more information about TI-LFA FRR path calculation, see SRv6 configuration in Segment Routing Configuration Guide.
TI-LFA FRR protection types
The following TI-LFA traffic protection types are available:
· Link protection—Protects traffic that traverses a specific link.
· Node protection—Protects traffic that traverses a specific node.
Node protection takes precedence over link protection.
TI-LFA FRR path calculation
TI-LFA FRR uses the common algorithm to calculate backup paths for a flexible algorithm. The only difference is that TI-LFA FRR calculates backup paths for a flexible algorithm according to the FAD and topology of that flexible algorithm.
As shown in Figure 14, Router B is the source node and Router A is the destination node.
The number on each link represents the link cost. A data flow traverses from Router B to Router A. To avoid traffic loss against Router B failure, TI-LFA FRR calculates the backup path: Router B > Router C > Router E > Router F > Router A.
Figure 14 TI-LFA FRR backup path calculation without a flexible algorithm
As shown in Figure 15, flexible algorithm 130 is configured for each node. The FAD of flexible algorithm 130 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute red.
In this case, the backup path calculated by TI-LFA FRR is Router B > Router C > Router D > Router E > Router F > Router A.
Figure 15 TI-LFA FRR backup path calculation with a flexible algorithm
FRR microloop avoidance for a flexible algorithm
When a link or node fails, TI-LFA FRR switches the traffic to the backup path to ensure continuous data forwarding. During the route convergence process, microloops might occur and cause packet loss and disorder if the route convergence on each device is not simultaneous.
As shown in Figure 16, flexible algorithm 128 is configured for all nodes on the network and TI-LFA is enabled for that flexible algorithm. The FAD of flexible algorithm 128 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost. The link cost of each link in Figure 16 is 10.
· Constraint—Exclude affinity attribute red.
If no node failures occur, Device A forwards traffic to Device C along the path: Device A > Device B > Device C. If Device B fails, traffic to Device C will be switched to the backup path calculated by TI-LFA. After Device A finishes route convergence, traffic to Device C will be forwarded along the post-convergence path. If Device D has not finished route convergence and still forward traffic along the pre-convergence path, a loop is formed between Device A and Device D. The loop exists until Device D finishes route convergence.
Figure 16 TI-LFA FRR microloop avoidance after a node failed
FRR microloop avoidance can resolve this issue. After you enable this feature for Device A, Device A first switches traffic to the backup path calculated by TI-LFA when Device B fails. Device A does not start route convergence unless Device D and Device F finish route convergence. After Device A also finishes route convergence, Device A switches the traffic to the post-convergence route.
SR microloop avoidance for a flexible algorithm
FRR microloop avoidance for a flexible algorithm provides microloop avoidance after a network failure. SR microloop avoidance for a flexible algorithm provides microloop avoidance both after a network failure and after a failure recovery.
After a network failure occurs or recovers in a scenario where flexible algorithm is used for path calculation, route convergence occurs on relevant network devices. Because of non-simultaneous convergence on network devices, microloops might be formed. After you configure SR microloop avoidance for a flexible algorithm, the devices will forward traffic along the specified path before route convergence is finished on all the relevant network devices. Because the forwarding path is independent of route convergence, microloops are avoided. To leave sufficient time for IS-IS to finish route convergence, set the SR microloop avoidance delay timer. Before the timer expires, failure relevant devices will forward traffic along the specified path. After the timer expires, IS-IS route convergence should have finished and traffic will traverse along the IS-IS-calculated path.
This section introduces only SR microloop avoidance after a failure recovery.
As shown in Figure 17, flexible algorithm TI-LFA is deployed on all network nodes. The FAD is as follows:
· Use the SPF algorithm.
· Calculate the smallest cost path based on IS-IS link cost. Assume that the cost is 10 for all links.
· Exclude links with affinity attribute red.
Before the link between Device B and Device C recovers, traffic traverses along the backup path. After the link recovers, Device A will forward the traffic to Device B if Device A finishes route convergence before Device B. Before Device B also finishes route convergence, Device B still forwards the traffic along the backup path. A loop is formed between Device A and Device B.
SR microloop avoidance can resolve this issue. After the link recovers, SR microloop avoidance automatically calculates the optimal path from Device A to Device C and forwards traffic along the path. To forward a packet along the newly calculated path, Device A adds end-to-end path information, for example, the adjacency SID from Device B to Device C to the packet and then sends the packet to Device B. Then, Device B forwards the packet to Device C based on the path information.
When the SR microloop avoidance delay timer expires, Device B should have finished route convergence. Device A does not add path information to packets anymore, and it forwards packets to Device C as usual.
Restrictions and guidelines
If you configure both FRR microloop avoidance and SR microloop avoidance for a flexible algorithm, SR microloop avoidance takes effect.
Enabling TI-LFA FRR
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Enable TI-LFA FRR.
fast-reroute ti-lfa enable
By default, TI-LFA FRR is enabled.
5. (Optional.) Enable Level-1 TI-LFA to use a Level-2 path as the backup path.
a. Return to IS-IS view.
quit
b. Enter IS-IS IPv4 address family view or IS-IS IPv6 address family view.
address-family { ipv4 | ipv6 } [ unicast ]
c. Enable Level-1 TI-LFA to use a Level-2 path as the backup path.
inter-level-tilfa level-1 enable [ prefer ]
By default, Level-1 TI-LFA cannot use a Level-2 path as the backup path.
If you execute this command together with the fast-reroute lfa ecmp-shared command in IS-IS IPv4 unicast address family view, this command does not take effect.
If you execute this command together with the fast-reroute lfa ecmp-shared command in IS-IS IPv6 unicast address family view, this command does not take effect.
Configuring FRR microloop avoidance
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Enable FRR microloop avoidance.
fast-reroute microloop-avoidance enable
By default, FRR microloop avoidance is enabled.
5. Set the RIB update delay timer for FRR microloop avoidance.
fast-reroute microloop-avoidance rib-update-delay delay-time [ level-1 | level-2 ]
By default, the RIB update delay timer is 5000 milliseconds.
Configuring SR microloop avoidance
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Enable SR microloop avoidance for the flexible algorithm.
segment-routing microloop-avoidance enable
By default, SR microloop avoidance is enabled for the flexible algorithm.
5. Set the SR microloop avoidance delay timer.
segment-routing microloop-avoidance rib-update-delay delay-time [ level-1 | level-2 ]
By default, the SR microloop avoidance delay timer is 5000 milliseconds.
6. (Optional.) Configure SR microloop avoidance to encapsulate only strict SIDs in the SID list.
segment-routing microloop-avoidance strict-sid-only
By default, the strict-SI-only feature is not configured for SR microloop avoidance.
Set the priority of an FRR backup path selection policy
About this task
IS-IS flexible algorithm FRR selects a backup path based on the following policies:
· Node-protection policy—Selects the path that involves a specific node.
· Lowest-cost policy—Selects the path that has the lowest cost.
As shown in Figure 18, flexible algorithm 128 is configured for all nodes on the network. The FAD of flexible algorithm 128 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute blue.
Traffic forwarding path Device A->Device E->Device F->Device G->Device H has three backup paths. You can set the priority of each backup path selection policy as follows to control backup path selection:
· To select path Device A->Device E->Device F->Device C->Device D ->Device H that involves Device E, set a higher priority for the node-protection policy than the lowest-cost policy.
· To select path Device A->Device B->Device C->Device F->Device G ->Device H that has the lowest cost, set a higher priority for the lowest-cost policy than the node-protection policy.
Figure 18 IS-IS FRR backup path selection
Restrictions and guidelines
If the node-protection policy has a higher priority but the backup path calculation fails, IS-IS uses the lowest-cost policy for further calculation. If the backup path calculation still fails, IS-IS does not perform further backup path calculation.
If the lowest-cost policy has a higher priority but the backup path calculation fails, IS-IS does not perform further backup path calculation.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Set the priority for a backup path selection policy.
fast-reroute tiebreaker { lowest-cost | node-protecting } preference preference [ level-1 | level-2 ]
By default, the priority values of the node-protection and lowest-cost backup path selection policies are 40 and 20, respectively.
Applying a flexible algorithm to SR-MPLS
About this task
IS-IS advertises a prefix SID together with the algorithm ID associated to that prefix SID. By default, the algorithm ID associated to a prefix SID is 0. In this case, IS-IS uses the SPF algorithm and IS-IS link cost to calculate the optimal path to the prefix of that prefix SID.
After you associate a prefix SID to a flexible algorithm, IS-IS uses the flexible algorithm to calculate the optimal path to the prefix of that prefix SID. For example, you can associate the prefix SID configure on the loopback interface of Router F to flexible algorithm 130. The FAD of flexible algorithm 130 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute blue.
SID index value 201 is assigned to loopback address 1.1.1.1/32 on Router F. The incoming label calculated by Router F is 16201. After using flexible algorithm 130 to calculate the optimal path to 1.1.1.1/32, Router A creates a label forwarding entry. The incoming label is 16201, the outgoing label is 16201, and the next hop is Router C. Figure 19 shows the established SRLSP from Router A to Router F.
Figure 19 SRLSP from Router A to Router F with flexible algorithm 130
Procedure
1. Enter system view.
system-view
2. Enter loopback interface view.
interface loopback interface-number
3. Associate an IS-IS prefix SID to a flexible algorithm.
isis [ process-id process-id ] prefix-sid algorithm algorithm-id { absolute absolute-value | index index-value } [ n-flag-clear | { explicit-null | no-php } ] *
By default, an IS-IS prefix SID is not associated to any flexible algorithm.
For more information about this command, see SR-MPLS commands in Segment Routing Command Reference.
Configuring color attribute-based traffic redirection
About this task
Configure this feature to forward packets through the path calculated by the specified flexible algorithm in an SR MPLS network where multiple paths exist between the source and destination nodes.
After you configure this feature, an SR node processes a received BGP route that carries the color attribute as follows:
1. Finds the flexible algorithm mapped to the color attribute.
2. Finds the path calculated by the flexible algorithm based on the destination address of the BGP route.
3. Recurses the BGP route to the path.
Then, the SR node will forward packets that match the BGP route through the path.
If a BGP route received by the SR node does not carry the extended community attribute, you can perform either of the following tasks to specify a color attribute for the route:
· Add a color value to the route by using a routing policy.
· Execute the default-color command to specify a default color value for the route. For more information about the default-color command, see SR-MPLS TE policy commands in Segment Routing Command Reference.
The color value specified through the routing policy takes precedence.
Procedure
1. Enter system view.
system-view
2. Enter segment routing view.
segment-routing
3. Create and enter SR flexible algorithm view.
flex-algo
4. Map a color attribute to a flexible algorithm.
color-mapping color-value flex-algo flex-algo-id
By default, a color attribute is not mapped to any flexible algorithm.
Applying a flexible algorithm to SRv6
About this task
With SRv6 enabled, IS-IS advertises SRv6 locator TLVs in LSPs. You can identify the algorithm associated to the locator by checking the algorithm field in an SRv6 locator TLV. By default, IS-IS uses the SPF algorithm to calculate the shortest path to an SRv6 locator, and the value for the algorithm field is 0.
If you associate an SRv6 locator to a flexible algorithm, IS-IS uses the flexible algorithm to calculate the shortest path to the locator. For example, you can associate the SRv6 locators in Figure 20 to flexible algorithm 130. The FAD of flexible algorithm 130 is as follows:
· Calculation type—SPF algorithm.
· Metric type—IS-IS link cost.
· Constraint—Exclude affinity attribute blue.
As shown in Figure 20, Router A uses the SPF algorithm to calculate the optimal path to locator 2001:0:8:6::/64 based on the topology of flexible algorithm 130.
Figure 20 Optimal path calculated by flexible algorithm 130
Restrictions and guidelines
You must associate an SRv6 locator to a flexible algorithm that already exists, or IS-IS will not advertise the locator.
Procedure
1. Enter system view.
system-view
2. Enable SRv6 and enter SRv6 view.
segment-routing ipv6
By default, SRv6 is disabled.
For more information about this command, see SRv6 configuration in Segment Routing Configuration Guide.
3. Configure a locator and enter SRv6 locator view.
locator locator-name [ ipv6-prefix ipv6-address prefix-length [ args args-length | static static-length ] * ]
For more information about this command, see SRv6 configuration in Segment Routing Configuration Guide.
4. Associate the locator to a flexible algorithm.
flex-algo algorithm algo-id
By default, a locator is not associated to any flexible algorithm.
For more information about this command, see SRv6 configuration in Segment Routing Configuration Guide.
Enabling trust level-based FAD advertisement
About this task
This feature can control FAD advertisement accroding to the trust level and flexible algorithm mappings. For more information about trust level configuration, see trust level configuration in Security Configuration Guide.
Provided that the trust level of the device is X and the security level of flexible algorithm N is M, the device advertises flexible algorithm N as follows:
· If M is not higher than X, the device advertises flexible algorithm N and generates a network topology based on the flexible algorithm.
· If M is higher than X, the device does not advertise flexible algorithm N.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter flexible algorithm view.
flex-algo flex-algo-id
4. Enable trust level-based FAD advertisement for the flexible algorithm.
trust-level-mapping enable
By default, trust level-based FAD advertisement is disabled. If you create a flexible algorithm on a trust level client or server, the device advertises the flexible algorithm.
Configuring IS-IS timers
Specifying the interval for sending IS-IS hello packets
About this task
IS-IS uses hello packets to maintain neighbor relationships. If a neighbor does not receive any hello packets from the router within the advertised hold time, it considers the router down and recalculates the routes. The hold time is the hello multiplier multiplied by the hello interval.
Restrictions and guidelines
The interval between hello packets sent by the DIS is 1/3 the hello interval set with the isis timer hello command.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the interval for sending hello packets.
isis timer hello seconds [ level-1 | level-2 ]
The default setting is 10 seconds.
Specifying the interval for sending IS-IS CSNP packets
About this task
On a broadcast network, perform this task on the DIS that uses CSNP packets to synchronize LSDBs.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the interval for sending CSNP packets on the DIS of a broadcast network.
isis timer csnp seconds [ level-1 | level-2 ]
The default setting is 10 seconds.
Setting the maximum age of LSPs
About this task
Each LSP has an age that decreases in the LSDB. Any LSP with an age of 0 is deleted from the LSDB. You can adjust the age value based on the scale of a network.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the maximum LSP age.
timer lsp-max-age seconds
The default setting is 1200 seconds.
Setting the LSP refresh interval and generation interval
About this task
Each router needs to refresh its LSPs at a configurable interval and send them to other routers to prevent valid routes from aging out. A smaller refresh interval speeds up network convergence but consumes more bandwidth.
When network topology changes such as neighbor state, interface metric, system ID, or area ID changes occur, the router generates an LSP after a configurable interval. If such a change occurs frequently, excessive LSPs are generated, consuming a large amount of router resources and bandwidth. To solve the problem, you can adjust the LSP generation interval.
Restrictions and guidelines
Follow these restrictions and guidelines when you configure the timer lsp-generation command:
· If you specify only the maximum-interval argument, the LSP generation interval is maximum-interval.
· If you do not specify the incremental-interval argument, the LSP generation interval is in the range of minimum-interval to maximum-interval.
· If you specify the incremental-interval argument, the LSP generation interval is as follows:
¡ When network changes are not frequent, the minimum-interval is adopted.
¡ When network changes are frequent, the LSP generation interval increases by incremental-interval × 2n-2 (n is the number of calculation times) each time a generation occurs until the maximum-interval is reached.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the LSP refresh interval.
timer lsp-refresh seconds
By default, the LSP refresh interval is 900 seconds.
4. Set the LSP generation interval.
timer lsp-generation maximum-interval [ minimum-interval [ incremental-interval ] ] [ level-1 | level-2 ]
By default:
¡ The maximum interval is 5 seconds.
¡ The minimum interval is 50 milliseconds.
¡ The incremental interval is 200 milliseconds.
Setting LSP sending intervals
About this task
If a change occurs in the LSDB, IS-IS advertises the changed LSP to neighbors. You can specify the minimum interval for sending these LSPs to control the amount of LSPs on the network.
On a P2P link, IS-IS requires an advertised LSP be acknowledged. If no acknowledgment is received within a configurable interval, IS-IS will retransmit the LSP.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the minimum interval for sending LSPs and the maximum LSP number that can be sent at a time.
isis timer lsp time [ count count ]
By default, the minimum interval is 33 milliseconds, and the maximum LSP number that can be sent at a time is 5.
4. Specify the LSP retransmission interval on a P2P link.
isis timer retransmit seconds
By default, the LSP retransmission interval on a P2P link is 5 seconds.
Setting the LSP receiving interval
About this task
When the network is stable, IS-IS uses the minimum receiving interval. When the network changes frequently, the receiving interval increases by the incremental interval each time the same LSP is received until the maximum receiving interval is reached.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the LSP receiving interval.
timer lsp-arrival maximum-interval [ minimum-interval [ incremental-interval ] ] [ level-1 | level-2 ]
By default, the LSP receiving interval is not set.
Setting the lifetime for expired LSPs in the LSDB
About this task
Each IS-IS LSP has a maximum lifetime. After a device receives an LSP, the lifetime of this LSP decreases. The LSP will expire if the following conditions exist:
· The device does not receive any update for the LSP.
· The lifetime of the LSP has decreased to 0.
If the device still does not receive any update for the expired LSP within a specific period of time, it will delete the LSP from its LSDB.
Some LSPs might expire before flooding and are deleted from the LSDB, especially when IS-IS has multiple neighbors and the LSDB contains a large number of LSPs. As a result, IS-IS might take a long time to complete route learning, if the LSP advertisement sources cannot update LSPs in time.
To resolve this issue, perform this task to increase the lifetime for expired LSPs. Then, IS-IS can flood out the expired LSPs before they are deleted, which ensures the LSP advertisement sources can update LSPs in time.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Setting the lifetime for expired LSPs in the LSDB.
timer aging-lsp-lifetime { non-self-originate | self-originate } lifetime
By default, the lifetime for an expired LSP varies by the source of this LSP as follows:
¡ If this LSP is generated by the local device, the lifetime is 1200 seconds.
¡ If this LSP is received from another device, the lifetime is 60 seconds.
Setting the SPF calculation interval
About this task
Based on the LSDB, an IS-IS router uses the SPF algorithm to calculate the shortest path tree with itself being the root, and uses the shortest path tree to determine the next hop to a destination network. By adjusting the SPF calculation interval, you can prevent bandwidth and router resources from being over consumed due to frequent topology changes.
When network changes are not frequent, the minimum-interval is adopted. If network changes become frequent, the SPF calculation interval increases by incremental-interval × 2n-2 (n is the number of calculation times) each time a calculation occurs until the maximum-interval is reached.
Setting the IPv4 SPF calculation interval
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the SPF calculation interval.
timer spf { maximum-interval [ minimum-interval [ incremental-interval [ conservative ] ] ] | millisecond millisecond-interval } [ exclude-prc ]
By default:
¡ The maximum interval is 5 seconds.
¡ The minimum interval is 50 milliseconds.
¡ The incremental interval is 200 milliseconds.
Setting the IPv6 SPF calculation interval
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Set the SPF calculation interval.
timer spf { maximum-interval [ minimum-interval [ incremental-interval [ conservative ] ] ] | millisecond millisecond-interval } [ exclude-prc ]
By default:
¡ The maximum interval is 5 seconds.
¡ The minimum interval is 50 milliseconds.
¡ The incremental interval is 200 milliseconds.
Configuring IS-IS packet-related features
Configuring a DIS priority for an interface
About this task
On a broadcast network, IS-IS must elect a router as the DIS at a routing level. You can specify a DIS priority at a level for an interface. The greater the interface's priority, the more likely it becomes the DIS. If multiple routers in the broadcast network have the same highest DIS priority, the router with the highest MAC address becomes the DIS.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure a DIS priority for the interface.
isis dis-priority priority [ level-1 | level-2 ]
The default setting is 64.
Configuring the administrative tag value for an interface
About this task
This task simplifies route management by allowing IS-IS to control IP address prefixes with the administrative tag.
As shown in Figure 21, Device A needs to communicate with Device B, Device C, and Device D. For security purposes, other devices in areas 2, 3, and 5 cannot receive the packets sent by Device A. To resolve this issue, perform the following task:
1. Configure the same administrative tag value for the IS-IS interfaces on Device B, Device C, and Device D.
2. Configure route leaking from Level-2 to Level-1 on the Level-1-2 device in Area 4 and specify the same tag value as the route filter.
As shown in Figure 22, the IS-IS network topology on Device A is updated after you perform the above task.
Figure 21 IS-IS network diagram without the administrative tag
Figure 22 IS-IS network diagram with the administrative tag
Configuring the IPv4 IS-IS administrative tag value for an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the IPv4 IS-IS administrative tag value for the interface.
isis tag tag
By default, the IPv4 IS-IS administrative tag value of the interface is not configured.
IS-IS adds the administrative tag to the network address information in LSPs only if the following conditions exist:
¡ An administrative tag value is specified.
¡ The link cost style is wide, wide-compatible, or compatible.
Configuring the IPv6 IS-IS administrative tag value for an interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the IPv6 IS-IS administrative tag value for the interface.
isis ipv6 tag tag
By default, the IPv6 IS-IS administrative tag value of the interface is not configured.
After you specify an administrative tag value, IS-IS always adds the specified tag value to the IPv6 prefix information in LSPs, regardless of the link cost style.
Specifying the IS-IS hello multiplier
About this task
The hello multiplier is the number of hello packets a neighbor must miss before it declares that the router is down.
If a neighbor receives no hello packets from the router within the advertised hold time, it considers the router down and recalculates the routes. The hold time is the hello multiplier multiplied by the hello interval.
On a broadcast link, Level-1 and Level-2 hello packets are advertised separately. You must set a hello multiplier for each level.
On a P2P link, Level-1 and Level-2 hello packets are advertised in P2P hello packets. You do not need to specify Level-1 or Level-2.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the hello multiplier.
isis timer holding-multiplier value [ level-1 | level-2 ]
The default setting is 3.
Disabling an interface from sending/receiving IS-IS packets
About this task
After being disabled from sending and receiving hello packets, an interface cannot form any neighbor relationship, but can advertise directly connected networks in LSPs through other interfaces. This can save bandwidth and CPU resources, and ensures that other routers know networks directly connected to the interface.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Disable the interface from sending and receiving IS-IS packets.
isis silent
By default, the interface can send and receive IS-IS packets.
Enabling an interface to send small hello packets
About this task
IS-IS messages cannot be fragmented at the IP layer because they are directly encapsulated in frames. Any two IS-IS neighboring routers must negotiate a common MTU. To avoid sending big hellos to save bandwidth, enable the interface to send small hello packets without CLVs.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable the interface to send small hello packets without CLVs.
isis small-hello
By default, the interface sends standard hello packets.
Setting LSP lengths
About this task
IS-IS messages cannot be fragmented at the IP layer because they are directly encapsulated in frames. IS-IS routers in an area must send LSPs smaller than the smallest interface MTU in the area.
If the IS-IS routers have different interface MTUs, configure the maximum size of generated LSP packets to be smaller than the smallest interface MTU in the area. Without the configuration, the routers must dynamically adjust the LSP packet size to fit the smallest interface MTU, which takes time and affects other services.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify the maximum length of generated Level-1 LSPs or Level-2 LSPs.
lsp-length originate size [ level-1 | level-2 ]
By default, the maximum length of generated Level-1 LSPs or Level-2 LSPs is 1497 bytes.
4. Specify the maximum length of received LSPs.
lsp-length receive size
By default, the maximum length of received LSPs is 1497 bytes.
Enabling LSP flash flooding
About this task
Changed LSPs can trigger SPF recalculation. To advertise the changed LSPs before the router recalculates routes for faster network convergence, enable LSP flash flooding.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable LSP flash flooding.
flash-flood [ flood-count flooding-count | max-timer-interval flooding-interval | [ level-1 | level-2 ] ] *
By default, LSP flash flooding is disabled.
Enabling LSP fragment extension
About this task
When the LSP capacity of a device is insufficient, enable LSP fragment extension to expand the LSP capacity. These LSPs can then carry more IS-IS information, including redistributed routes and TLVs. If IS-IS fails to add some redistributed routes or TLVs into an LSP, it will automatically try to re-add those redistributed routes and TLVs into the LSP after LSP fragment extension.
The LSP fragment extension feature involves the following concepts:
· Originating System—IS-IS process.
· Normal System ID—System ID of the originating system.
· Additional System ID—Unique identifier assigned to a virtual system.
· Virtual System—System used to generate extended LSP fragments. Each extended LSP fragment carries the additional system ID of the virtual system in its LSP ID.
· IS Alias ID TLV—TLV that describes the relationship between the originating system and the virtual system.
By default, an IS-IS process can generate a maximum of 256 LSP fragments. The number of routes that these LSP fragments can carry is limited. To resolve this issue, the LSP fragment extension feature introduces the concept of additional system ID. Each additional system ID can generate 256 extended LSP fragments. When the LSP capacity of the originating system is insufficient, IS-IS adds the overflowing route information together with the IS Alias ID TLV into the extended LSPs of a virtual system.
As shown in Figure 23, both Device A and Device B support LSP fragment extension. With LSP fragment extension enabled, Device A advertises some route information in the LSPs generated by Device A1 and Device A2. On receipt of these LSPs, Device B reads the IS Alias ID TLVs and determines that Device A is the originating system. The route information received from Device A1 and Device A2 is actually generated by Device A. In this situation, virtual systems do not participate in route calculation.
Figure 23 IS-IS LSP fragment extension
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable LSP fragment extension.
lsp-fragments-extend [ level-1 | level-1-2 | level-2 ]
By default, LSP fragment extension is disabled.
The MTUs of all interfaces running the IS-IS process must not be less than 512. Otherwise, LSP fragment extension does not take effect.
4. Configure a virtual system ID.
virtual-system virtual-system-id
By default, no virtual system ID is configured.
Configure a minimum of one virtual system to generate extended LSP fragments.
Controlling LSP generation, advertisement and reception
Limiting LSP flooding
About this task
Multiple P2P links might exist on an NBMA network such as ATM and FR. As shown in Figure 24, Routers A, B, C and D run IS-IS. When Router A generates an LSP, it floods the LSP out of Serial3/1/1:0, Serial3/1/2:0, and Serial3/1/3:0. After Router D receives the LSP from Serial3/1/3:0, it floods it out of Serial3/1/1:0 and Serial3/1/2:0 to Router B and Router C. However, Router B and Router C have already received the LSP from Router A. Repeated LSP flooding consumes extra bandwidth.
Figure 24 Network diagram of a fully meshed network
To avoid this issue, you can add interfaces to a mesh group or block some interfaces.
· An interface in a mesh group floods a received LSP only to interfaces not in the mesh group.
· A blocked interface sends LSPs only after receiving LSP requests.
Restrictions and guidelines
Before you configure this task, you must consider redundancy for interfaces in case LSP packets cannot be flooded because of link failures.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Limit LSP flooding.
¡ Add the interface to a mesh group.
isis mesh-group mesh-group-number
¡ Block the interface.
isis mesh-group mesh-blocked
By default, the interface does not belong to any mesh group and is not blocked.
The commands take effect only on P2P interfaces.
Configuring IS-IS route update suppression
About this task
Perform this task to protect network resources and routers from being overwhelmed by LSPs when route flapping occurs.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS route update suppression.
¡ Suppress LSP generation.
timer lsp-generation suppress-flapping delay-interval [ threshold threshold-value] [ level-1 | level-2 ]
By default, IS-IS does not suppress LSP generation.
¡ Suppress LSP flooding.
timer lsp-flood suppress-flapping delay-interval [ threshold threshold-value ] [ level-1 | level-2 ]
By default, IS-IS does not suppress LSP flooding.
¡ Suppress route calculation.
timer route-calculate suppress-flapping delay-interval [ threshold threshold-value ] [ level-1 | level-2 ]
By default, IS-IS does not suppress route calculation.
¡ Suppress route calculation after fragment 0 of a purge LSP is received.
timer purge-zero-lsp route-calculate-delay delay-interval [ level-1 | level-2 ]
By default, IS-IS suppresses route calculation for 10 seconds after fragment 0 of a purge LSP is received.
Configuring advanced IS-IS features
Enabling source address check for hello packets on a P2P interface
About this task
An IS-IS P2P interface can have a peer on a different network. Perform this task to configure an IS-IS P2P interface to establish neighbor relationship only with a peer on the same network.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable source address check for hello packets on a P2P interface.
isis peer-ip-check
By default, an IS-IS P2P interface can have a peer on a different network.
Configuring convergence priorities for specific routes
About this task
A topology change causes IS-IS routing convergence. To improve convergence speed, you can assign convergence priorities to IS-IS routes. Convergence priority levels are critical, high, medium, and low. The higher the convergence priority, the faster the convergence speed.
After you use the prefix-priority command, IS-IS sets the convergence priorities for IS-IS routes as follows:
· IS-IS sets the convergence priorities for routes that already exist according to the configuration of the prefix-priority command.
· IS-IS sets the convergence priorities for subsequent routes according to the filter result of the prefix-priority command.
· When a route matches the rules of multiple convergence priorities, it uses the highest priority.
Configuring convergence priorities for specific IPv4 IS-IS routes
1. Enter system view.
system-view
2. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
3. Assign convergence priorities to specific IPv4 IS-IS routes.
¡ Assign a convergence priority to IPv4 IS-IS routes matching the specified prefix list.
prefix-priority { critical | high | medium } { prefix-list prefix-list-name | tag tag-value }
¡ Assign a convergence priority to IPv4 IS-IS routes by using a route policy.
prefix-priority route-policy route-policy-name
By default, IPv4 IS-IS routes, except IS-IS host routes, have the low convergence priority.
Configuring convergence priorities for specific IPv6 IS-IS routes
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Assign convergence priorities to specific IPv6 IS-IS routes.
prefix-priority { critical | high | medium } { prefix-list prefix-list-name | tag tag-value }
prefix-priority route-policy route-policy-name
By default, IPv6 IS-IS routes, except IS-IS host routes, have the low convergence priority.
Setting the LSDB overload bit
About this task
By setting the overload bit in sent LSPs, an IS-IS device informs other devices of failures that make it unable to select routes and forward packets. The device is then excluded from the SPF calculation by other devices except its direct routes.
When an IS-IS device cannot record the complete LSDB, for example, because of memory insufficiency, it will calculate routes incorrectly. To make troubleshooting easier, temporarily isolate the device from the IS-IS network by setting the overload bit. To locate the faulty device, you can temporarily isolate the suspects from the IS-IS network by setting the overload bit.
As shown in Figure 25, the path from Device A to the IP network should be Device A > Device D > Device E > IP network. After you set the overload bit in the LSPs sent by Device D, the path from Device A to the IP network becomes Device A > Device B > Device C > Device E > IP network. If the packets from Device A are destined for Device D's directly-connected networks, the forwarding path does not change.
Setting the LSDB overload bit for IPv4 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the overload bit.
set-overload [ on-startup [ [ start-from-nbr system-id [ timeout1 [ nbr-timeout ] ] ] | timeout2 | wait-for-bgp [ timeout3 ] ] [ route-delay-distribute delay-time ] [ send-sa-bit [ duration ] ] [ route-max-metric ] ] [ allow { external | interlevel } * ]
By default, the overload bit is not set.
Setting the LSDB overload bit for IPv6 IS-IS
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Set the overload bit.
set-overload [ on-startup [ [ start-from-nbr system-id [ timeout1 [ nbr-timeout ] ] ] | timeout2 | wait-for-bgp4+ [ timeout3 ] ] [ route-delay-distribute delay-time ] [ send-sa-bit [ duration ] ] [ route-max-metric ] ] [ allow { external | interlevel } * ]
By default, the overload bit is not set.
Setting IS-IS interface cost upon LSDB overload
About this task
Perform this task to prevent neighbor devices from sending traffic to an overloaded device in an anycast scenario.
Upon entering the overload state, the device sends an LSP with the OL bit set to its neighbors. The neighbor that receives the LSP performs path calculation and forwards packets as follows:
· For packets destined to a network not directly connected to the overloaded device, the neighbor device does not forward the packets to the overloaded device.
· For packets destined to the network directly connected to the overloaded device, the neighbor device forwards the packets to the overloaded device.
These processing methods might cause problems in an anycast scenario where the destination address of packets is an anycast address. The neighbor device will send such packets to the anycast node with the smallest cost, and that node might have already entered the overload state. To avoid such problems, perform this task to enable an overloaded device to increase its cost. Neighbors will not select the device during path calculation.
The command takes effect when the device enters the overload state as follows:
· When the device is in overload state, the system increases the cost of all IS-IS interfaces on the device. Neighbors will not select the device during path calculation.
· When the device exits the overload state or you execute the undo overload adjust-cost command, the IS-IS interfaces resume their original costs.
Restrictions and guidelines
Follow these guidelines when you set IS-IS interface cost upon LSDB overload:
· If route calculation is not performed separately for IPv4 and IPv6 topologies, the configuration takes effect as follows:
¡ The configuration in IS-IS view applies to both IPv4 and IPv6 IS-IS interfaces.
¡ The configuration in IPv6 address family view does not take effect.
· If route calculation is performed separately for IPv4 and IPv6 topologies, the configuration takes effect as follows:
¡ The configuration in IS-IS view applies only to IPv4 IS-IS interfaces.
¡ The configuration in IPv6 address family view applies only to IPv6 IS-IS interfaces.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view or IPv6 address family view.
¡ Enter IS-IS view:
isis [ process-id ] [ vpn-instance vpn-instance-name ]
¡ Execute the following commands in sequence to enter IPv6 address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv6 [ unicast ]
3. Set the cost for all IS-IS interfaces when the device enters the overload state.
overload adjust-cost { cost-offset | max }
By default, the device does not change the cost for any IS-IS interfaces when it enters the overload state.
Configuring IS-IS isolation
About this task
Isolation is a method used for network device maintenance. It gracefully removes a device from the packet forwarding path for maintenance and gracefully adds the device to the network after maintenance.
To reduce impact on traffic forwarding, you can isolate a device before upgrading it. IS-IS isolation works as follows:
1. After IS-IS isolation is enabled for a device, IS-IS sets the overload bit in the LSPs advertised by the device and sets the link cost to the maximum value.
2. Each neighbor of the device reselects an optimal route based on the LSPs and stops forwarding traffic to the device. The device is fully isolated from the network and you can upgrade the device.
3. After the maintenance, disable IS-IS isolation on the device by using the undo isolate enable command. The device can return to the network gracefully after the overload bit is cleared and the link cost restores to the original value.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS isolation.
a. Enable IS-IS isolation to gracefully remove the device from the network.
isolate enable
b. Disable IS-IS isolation to gracefully add the device to the network.
undo isolate enable
By default, IS-IS isolation is disabled.
Configuring IS-IS shutdown
About this task
For maintenance purposes, you can use this feature to shut down IS-IS processes on the device with small impact on the network. If you shut down an IS-IS process, it will perform the following operations:
· Change the state of all neighbors to down.
· Stop receiving and sending IS-IS packets.
· Clear its neighbor, LSDB, and IS-IS route information.
If the neighbors do not receive any hello packets from the IS-IS process within the hold time, they consider the process down and recalculate the routes.
After maintenance, you can use the undo shutdown process command to restart the IS-IS process for neighbor relationship re-establishment.
This feature shuts down an IS-IS process while retaining the process-associated settings to facilitate your maintenance.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
a. Shut down an IS-IS process to isolate it from the network.
shutdown process
b. Restart the IS-IS process to add it back to the network.
undo shutdown process
By default, the IS-IS process is not shut down.
Configuring the ATT bit
About this task
The ATT bit is used to identify the connection status between a Level-1 area and other areas. By default, a Level-1-2 router sets the ATT bit for Level-1 LSPs as follows:
· The Level-1-2 router sets the ATT bit in Level-1 LSPs to inform the Level-1 routers that it can reach other areas. After a Level-1 router receives a Level-1 LSP with the ATT bit set, it generates a default route destined for the Level-1-2 router.
· The Level-1-2 router does not set the ATT bit in Level-1 LSPs if it can reach only one area.
To edit the default ATT bit setting rule for a Level-1-2 router, perform the following tasks as needed:
· To enable ATT bit setting for all Level-1 LSPs, execute the set-att always command on the Level-1-2 router.
· To disable a Level-1 router from generating a default route upon receiving an ATT-bit-set Level-1 LSP from the Level-1-2 router, you can perform one of the following tasks:
¡ Execute the ignore-att command on the Level-1 router.
¡ Execute the set-att never command on the Level-1-2 router.
Configuring IS-IS not to calculate the default route through the ATT bit
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure IS-IS not to calculate the default route through the ATT bit.
ignore-att
By default, IS-IS uses the ATT bit to calculate the default route.
Setting the IPv4 ATT bit of Level-1 LSPs
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the ATT bit of Level-1 LSPs.
set-att { always | never }
By default, the Level-1-2 router sets the ATT bit for IPv4 Level-1 LSPs in accordance with the default ATT bit setting rule.
Setting the IPv6 ATT bit of Level-1 LSPs
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Set the IPv6 ATT bit of Level-1 LSPs.
set-att { always | never }
By default, the Level-1-2 router sets the ATT bit for IPv6 Level-1 LSPs in accordance with the default ATT bit setting rule.
Configuring system ID to host name mappings
About this task
A 6-byte system ID in hexadecimal notation uniquely identifies a router or host in an IS-IS network. To make a system ID easy to read, the system allows you to use host names to identify devices. It also provides mappings between system IDs and host names.
The mappings can be configured manually or dynamically.
· Static system ID to host name mapping—You must manually configure a mapping for each router in the network. When a new router is added to the network or a mapping must be modified, you must configure all routers manually.
· Dynamic system ID to host name mapping—You only need to configure a host name for each router in the network. Each router advertises the host name in a dynamic host name CLV to other routers so all routers in the network can have all mappings. To help check the origin of LSPs in the LSDB, you can configure a name for the DIS in a broadcast network.
Restrictions and guidelines
Follow these guidelines when you configure the mappings:
· To view host names rather than system IDs by using the display isis lsdb command, you must enable dynamic system ID to host name mapping.
· If you configure both dynamic mapping and static mapping on a router, the host name specified for dynamic mapping applies.
Configuring a static system ID to host name mapping
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Configure a system ID to host name mapping for a remote IS.
is-name map sys-id map-sys-name
By default, no system ID to host name mapping is configured for a remote IS.
A system ID can correspond to only one host name.
Configuring dynamic system ID to host name mapping
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify a host name for the IS and enable dynamic system ID to host name mapping.
is-name sys-name
By default, dynamic system ID to host name mapping is disabled and no host name is specified for the router.
4. Return to system view.
quit
5. Enter interface view.
interface interface-type interface-number
6. Configure a DIS name.
isis dis-name symbolic-name
By default, no DIS name is configured.
This command takes effect only on a router enabled with dynamic system ID to host name mapping.
This command is not available on P2P interfaces.
Enabling BIER for an IS-IS process
About this task
A node cannot generate a BFR ID-based forwarding table for multicast packet forwarding unless you enable IS-IS Bit Index Explicit Replication (BIER) on the node. For more information about BIER, see BIER configuration in BIER Configuration Guide.
With BIER enabled, IS-IS floods the BFR IDs of BIER edge devices and other information (for example, IP address of the node) in LSPs. After receiving the LSP, each node generates a bit index forwarding table to forward BIER packets by their bit strings.
Restrictions and guidelines
You can enable BIER only for IS-IS instances running on the public network.
You can enable BIER only for one IS-IS instance on the same device.
The bier enable command takes effect only after you enable BIER by using the bier command.
Procedure
1. Enter system view.
system-view
2. Enable BIER and enter its view.
bier
By default, BIER is disabled.
For more information about this command, see BIER commands in BIER Command Reference.
3. Return to system view
quit
4. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
5. Specify an IS-IS cost style.
cost-style { compatible | wide | wide-compatible }
6. Enable BIER for the IS-IS process.
bier enable
By default, BIER is disabled for the IS-IS process.
7. (Optional.) Enable IS-IS to redistribute BIER information from other protocols.
a. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
b. Enable IS-IS to redistribute BIER information from other protocols.
import-bier bgp4+ [ as-number ]
By default, IS-IS does not redistribute BIER information from other protocols.
This command is applicable to inter-AS BIER traffic forwarding.
Configuring IS-IS logging and SNMP notifications
Enabling the logging of neighbor state changes
About this task
Neighbor flappings cause a series of issues, such as network instability, unnecessary resource consumption, and even data loss. You can enable the logging of neighbor state changes for fast issue location and troubleshooting.
With this feature enabled, the device delivers logs about neighbor state changes to its information center. The information center processes the logs according to user-defined output rules (whether to output logs and where to output). For more information about the information center, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable the logging of neighbor state changes.
log-peer-change
By default, the logging of neighbor state changes is enabled.
Setting the maximum number of log entries that can be recorded
About this task
Perform this task to set the maximum number of log entries that IS-IS can record for each log type.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the maximum number of log entries that IS-IS can record.
event-log { hello { peer-change | received-abnormal | received-dropped | sent-abnormal | sent-failed } | lsp | peer | spf } size count
By default, IS-IS can record 100 log entries for each log type.
Setting the maximum number of advertisement sources that trigger LSP update logging
About task
After the device starts running, it records LSP-update log information every 15 minutes. By default, it can record LSP-update log information for up to 200 advertisement sources. LSP update logging consumes memory resources. To control the memory usage by LSP update logging, you can perform this task.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Set the maximum number of advertisement sources that trigger LSP update logging.
event-log updated-lsp size count
By default, a maximum of 200 advertisement sources can trigger LSP update logging.
Setting the maximum number of IS-IS neighbor relationship troubleshooting entries
1. Enter system view.
system-view
2. Set the maximum number of IS-IS neighbor relationship troubleshooting entries.
isis troubleshooting max-number number
By default, IS-IS can record a maximum of 100 neighbor relationship troubleshooting entries.
Configuring IS-IS network management
About this task
This task includes the following configurations:
· Bind an IS-IS process to MIB so that you can use network management software to manage the specified IS-IS process.
· Enable IS-IS notifications to report important events.
To report critical IS-IS events to an NMS, enable SNMP notifications for IS-IS. For SNMP notifications to be sent correctly, you must also configure SNMP on the device. For more information about SNMP configuration, see the network management and monitoring configuration guide for the device.
Procedure
1. Enter system view.
system-view
2. Bind MIB to an IS-IS process.
isis mib-binding process-id
By default, MIB is bound to the IS-IS process with the smallest process ID.
3. Enable IS-IS notification sending.
snmp-agent trap enable isis [ adjacency-state-change | area-mismatch | authentication | authentication-type | buffsize-mismatch | id-length-mismatch | lsdboverload-state-change | lsp-corrupt | lsp-parse-error | lsp-size-exceeded | manual-address-drop | max-seq-exceeded | maxarea-mismatch | own-lsp-purge | protocol-support | rejected-adjacency | skip-sequence-number | system-id-conflict | version-skew ] *
By default, IS-IS notification sending is enabled.
4. (Optional.) Extend the format of SNMP notifications for neighbor state changes.
snmp-agent trap isis adjacency-state-change extended
By default, IS-IS does not extend the format of SNMP notifications for neighbor state changes.
5. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
6. Configure the context name for the SNMP object for managing IS-IS.
snmp context-name context-name
By default, no context name is set for the SNMP object for managing IS-IS.
Configuring IS-IS fast convergence
Enabling ISPF
About this task
When the network topology changes, Incremental Shortest Path First (ISPF) computes only the affected part of the SPT, instead of the entire SPT.
Enabling IPv4 IS-IS ISPF
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable IPv4 IS-IS ISPF.
ispf enable
By default, IPv4 IS-IS ISPF is enabled.
Enabling IPv6 IS-IS ISPF
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable IPv6 IS-IS ISPF.
ispf enable
By default, IPv6 IS-IS ISPF is enabled.
Enabling prefix suppression
About this task
Perform this task to disable an interface from advertising its prefix in LSPs. This enhances network security by preventing IP routing to the interval nodes and speeds up network convergence.
Enabling IPv4 IS-IS prefix suppression
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable IPv4 IS-IS prefix suppression on the interface.
isis prefix-suppression
By default, IPv4 IS-IS prefix suppression is disabled on the interface.
This command is also applicable to the secondary IP address of the interface.
Enabling IPv6 IS-IS prefix suppression
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable IPv6 IS-IS prefix suppression on the interface.
isis ipv6 prefix-suppression
By default, IPv6 IS-IS prefix suppression is disabled on the interface.
Configuring IS-IS PIC
About this task
Prefix Independent Convergence (PIC) enables the device to speed up network convergence by ignoring the number of prefixes.
Restrictions and guidelines for IS-IS PIC
Follow these restrictions and guidelines when you configure IS-IS PIC:
· When both IS-IS PIC and IS-IS FRR are configured, IS-IS FRR takes effect.
· IS-IS PIC applies only to LSPs sent by neighbors.
Enabling IS-IS PIC
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable PIC for IS-IS.
pic [ additional-path-always ]
By default, IS-IS PIC is disabled.
Enabling BFD control packet mode for IS-IS PIC
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable BFD control packet mode for IS-IS PIC.
isis primary-path-detect bfd ctrl
By default, BFD control packet mode is disabled for IS-IS PIC.
To use BFD (control packet mode) to detect primary link failures, you must enable BFD control packet mode on both ends of the link.
Enabling BFD echo packet mode for IS-IS PIC
1. Enter system view.
system-view
2. (Optional) Configure the source IP address of BFD echo packets.
bfd echo-source-ip ip-address
By default, the source IP address of BFD echo packets is not configured.
As a best practice to avoid network congestion caused by massive ICMP redirect packets from the remote end, execute this command and specify a source IP address that is not on the same network segment as any local interface's IP address.
For more information, see High Availability Command Reference.
3. Enter interface view.
interface interface-type interface-number
4. Enable BFD echo packet mode for IS-IS PIC.
isis primary-path-detect bfd echo
By default, BFD echo packet mode is disabled for IS-IS PIC.
To use BFD (echo packet mode) to detect primary link failures, you only need to enable BFD echo packet mode on one end of the link.
Enhancing IS-IS network security
To enhance the security of an IS-IS network, you can configure IS-IS authentication. IS-IS authentication involves neighbor relationship authentication, area authentication, and routing domain authentication.
Configuring neighbor relationship authentication
About this task
With neighbor relationship authentication configured, an interface adds the key in the specified mode into hello packets to the peer and checks the key in the received hello packets. If the authentication succeeds, it forms the neighbor relationship with the peer.
The authentication mode and key at both ends must be identical.
To prevent packet exchange failure in case of an authentication key change, configure the interface not to check the authentication information in the received packets.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Specify the authentication mode and key.
isis [ process-id process-id ] authentication-mode { { gca key-id { hmac-sha-1 | hmac-sha-224 | hmac-sha-256 | hmac-sha-384 | hmac-sha-512 } [ nonstandard ] | md5 | simple } { cipher | plain } string | keychain keychain-name } [ level-1 | level-2 ] [ ip | osi ]
By default, the authentication mode and key are not configured.
4. (Optional.) Configure the interface not to check the authentication information in the received hello packets.
isis authentication send-only [ level-1 | level-2 ]
When the authentication mode and key are configured, the interface checks the authentication information in the received packets by default.
Configuring area authentication
About this task
Area authentication prevents the router from installing routing information from untrusted routers into the Level-1 LSDB. The router encapsulates the authentication key in the specified mode in Level-1 packets (LSP, CSNP, and PSNP). It also checks the key in received Level-1 packets.
Routers in a common area must have the same authentication mode and key.
To prevent packet exchange failure in case of an authentication key change, configure IS-IS not to check the authentication information in the received packets.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify the area authentication mode and key.
area-authentication-mode { { gca key-id { hmac-sha-1 | hmac-sha-224 | hmac-sha-256 | hmac-sha-384 | hmac-sha-512 } [ nonstandard ] | md5 | simple } { cipher | plain } string | keychain keychain-name } [ ip | osi ]
By default, the area authentication mode and key are not configured.
4. (Optional.) Configure the interface not to check the authentication information in the received Level-1 packets, including LSPs, CSNPs, and PSNPs.
area-authentication send-only
When the authentication mode and key are configured, the interface checks the authentication information in the received packets by default.
Configuring routing domain authentication
About this task
Routing domain authentication prevents untrusted routing information from entering into a routing domain. A router with the authentication configured encapsulates the key in the specified mode into Level-2 packets (LSP, CSNP, and PSNP) and check the key in received Level-2 packets.
To prevent packet exchange failure in case of an authentication key change, configure IS-IS not to check the authentication information in the received packets.
Restrictions and guidelines
A router configured with routing domain authentication can establish neighbor relationships with routers not configured with routing domain authentication, but it will discard LSPs not carrying the authentication information. In this situation, IS-IS might fail to learn the expected routes. To resolve this issue, configure the same authentication mode and key on all routers in the backbone area.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Specify the routing domain authentication mode and key.
domain-authentication-mode { { gca key-id { hmac-sha-1 | hmac-sha-224 | hmac-sha-256 | hmac-sha-384 | hmac-sha-512 } [ nonstandard ] | md5 | simple } { cipher | plain } string | keychain keychain-name } [ ip | osi ]
By default, the routing domain authentication mode and key are not configured.
4. (Optional.) Configure the interface not to check the authentication information in the received Level-2 packets, including LSPs, CSNPs, and PSNPs.
domain-authentication send-only
When the authentication mode and key are configured, the interface checks the authentication information in the received packets by default.
Configuring IS-IS GR
About this task
GR ensures forwarding continuity when a routing protocol restarts or an active/standby switchover occurs.
Two routers are required to complete a GR process. The following are router roles in a GR process.
· GR restarter—Graceful restarting router. It must have GR capability.
· GR helper—A neighbor of the GR restarter. It assists the GR restarter to complete the GR process. By default, the device acts as the GR helper.
Configure IS-IS GR on the GR restarter.
GR restarter uses the following timers:
· T1 timer—Specifies the times that GR restarter can send a Restart TLV with the RR bit set. When rebooted, the GR restarter sends a Restart TLV with the RR bit set to its neighbor. If the GR restarter receives a Restart TLV with the RA set from its neighbor before the T1 timer expires, the GR process starts. Otherwise, the GR process fails.
· T2 timer—Specifies the LSDB synchronization interval. Each LSDB has a T2 timer. The Level-1-2 router has a Level-1 timer and a Level-2 timer. If the LSDBs have not synchronized before the two timers expire, the GR process fails.
· T3 timer—Specifies the GR interval. The GR interval is set as the holdtime in hello PDUs. Within the interval, the neighbors maintain their adjacency with the GR restarter. If the GR process has not completed within the holdtime, the neighbors tear down the neighbor relationship and the GR process fails.
Restrictions and guidelines
Follow these restrictions and guidelines when you configure IS-IS GR:
· The product of the T1 timer and the number of times that the T1 timer can expire must be smaller than the T2 timer.
· The T2 timer must be smaller than the T3 timer.
Procedure
1. Enter system view.
system-view
2. Enable IS-IS and enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enable IS-IS GR.
graceful-restart
By default, the GR capability for IS-IS is disabled.
4. (Optional.) Suppress the SA bit during restart.
graceful-restart suppress-sa
By default, the SA bit is not suppressed.
By enabling the GR restarter to suppress the Suppress-Advertisement (SA) bit in the hello PDUs, the neighbors will still advertise their adjacency with the GR restarter.
5. (Optional.) Configure the T1 timer.
graceful-restart t1 seconds count count
By default, the T1 timer is 3 seconds and can expire 10 times.
6. (Optional.) Configure the T2 timer.
graceful-restart t2 seconds
By default, the T2 timer is 60 seconds.
7. (Optional.) Configure the T3 timer.
graceful-restart t3 seconds
By default, the T2 timer is 300 seconds.
Configuring BFD for IS-IS
Enabling BFD for IS-IS
About this task
IS-IS exchanges hello packets at specific intervals with its neighbors to detect neighbor state changes. If IS-IS does not receive any hello packets from a neighbor within the advertised neighbor relationship hold time, it considers the neighbor down and recalculates the routes. The hold time is the hello multiplier multiplied by the hello interval and the default hold time is 30 seconds. This mechanism is not efficient at neighbor state change detection. Serious packet loss might occur when a neighbor goes down.
To resolve this issue, perform this task to enable BFD for IS-IS. BFD provides a single mechanism to quickly detect and monitor the connectivity of links between IS-IS neighbors, reducing network convergence time. For more information about BFD, see High Availability Configuration Guide.
Restrictions and guidelines
You can use the bfd all-interfaces enable, isis bfd enable, or isis ipv6 bfd enable command to enable IS-IS BFD. These commands are different as follows:
· The bfd all-interfaces enable command takes effect on all interfaces in an IPv4 or IPv6 IS-IS process. To disable BFD on an interface in the IS-IS process, use the isis bfd exclude or isis ipv6 bfd exclude command on the interface.
· The isis bfd enable and isis ipv6 bfd enable commands take effect only on one IS-IS interface. To enable BFD on an IS-IS interface, perform the following tasks:
a. Make sure the IS-IS process to which the interface belongs is not enabled with BFD session state-based interface cost adjustment.
You can use the undo bfd all-interfaces enable command to disable BFD for an IS-IS process.
b. Use the isis bfd enable or isis ipv6 bfd enable command to enable BFD on the IS-IS interface.
Configuring BFD for an IS-IS process
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv4 address family view or IPv6 address family view.
¡ Enter IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable BFD for the IS-IS process.
bfd all-interfaces enable
By default, BFD is disabled for an IS-IS process.
5. (Optional.) Suppress the BFD capacity of an IPv4 IS-IS interface.
a. Return to IS-IS view.
quit
b. Return to system view.
quit
c. Enter interface view.
interface interface-type interface-number
d. Suppress the BFD capacity of the IS-IS interface.
IPv4:
isis bfd exclude
IPv6:
isis ipv6 bfd exclude
By default, the BFD capacity of an IS-IS interface is not suppressed.
Configuring BFD on an IS-IS interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable BFD on an IPv4 IS-IS interface.
IPv4:
isis bfd enable
By default, the IPv4 IS-IS interface inherits the configuration of the bfd all-interfaces enable command in IS-IS IPv4 unicast address family view.
IPv6:
isis ipv6 bfd enable
By default, the IPv6 IS-IS interface inherits the configuration of the bfd all-interfaces enable command in IS-IS IPv6 unicast address family view.
Enabling IS-IS to adjust the interface cost according to the BFD session state
About this task
After you enable BFD for IS-IS link failure detection, IS-IS neighbor relationship flapping will occur upon frequent BFD session state changes. The running of services (such as BGP) that rely on IPv4 IS-IS might be interrupted. To resolve this issue, enable IS-IS to adjust the interface cost according to the BFD session state. IS-IS will adjust the cost value for an interface as follows to ensure fast route convergence against link state changes:
· When the BFD session on the interface goes down, IS-IS increases the cost value for the interface.
· When the BFD session on the interface comes up again, IS-IS restores the cost value for the interface to the original value.
Restrictions and guidelines
This task can take effect on an IS-IS interface only when BFD is enabled on the interface.
· bfd all-interfaces adjust-cost
· isis bfd adjust-cost
· isis ipv6 bfd adjust-cost
These commands are different as follows:
· The bfd all-interfaces adjust-cost command takes effect on all interfaces in an IPv4 or IPv6 IS-IS process. To disable this feature on an interface in that IS-IS process, use the isis bfd adjust-cost exclude or isis ipv6 bfd adjust-cost exclude command on the interface.
· The isis bfd adjust-cost and isis ipv6 bfd adjust-cost commands take effect only on one IS-IS interface. For IS-IS to adjust the cost value for a single interface according to the BFD session state, perform the following tasks:
a. Make sure the IS-IS process to which the interface belongs is not enabled with BFD session state-based interface cost adjustment.
You can use the undo bfd all-interfaces adjust-cost command to disable this feature for an IS-IS process.
b. Use the isis bfd adjust-cost or isis ipv6 bfd adjust-cost command to enable this feature on the interface.
· For an IS-IS interface, the isis bfd adjust-cost or isis ipv6 bfd adjust-cost command takes precedence over the bfd all-interfaces adjust-cost command. The interface uses the configuration of the bfd all-interfaces adjust-cost command only when you do not execute the isis bfd adjust-cost or isis ipv6 bfd adjust-cost command on that interface.
Enabling BFD session state-based interface cost adjustment for an IS-IS process
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv4 address family view or IPv6 address family view.
¡ Enter IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable BFD session state-based interface cost adjustment for the IS-IS process and set the interface cost adjustment value.
bfd all-interfaces adjust-cost { cost-offset | max }
By default, BFD session state-based interface cost adjustment is disabled for an IS-IS process.
5. (Optional.) Suppress BFD session state-based interface cost adjustment on an IS-IS interface.
a. Return to IS-IS view.
quit
b. Return to system view.
quit
c. Enter interface view.
interface interface-type interface-number
d. Suppress BFD session state-based interface cost adjustment on the IS-IS interface.
IPv4:
isis bfd adjust-cost exclude
By default, IPv4 IS-IS can adjust the cost value for an interface according to the BFD session state.
IPv6:
isis ipv6 bfd adjust-cost exclude
By default, IPv6 IS-IS can adjust the cost value for an interface according to the BFD session state.
Enabling BFD session state-based interface cost adjustment on an IS-IS interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable BFD session state-based interface cost adjustment on the IS-IS interface and set the interface cost adjustment value.
¡ IPv4:
isis bfd adjust-cost { cost-offset | max }
By default, the IPv4 IS-IS interface inherits the configuration of the bfd all-interfaces adjust-cost command in IS-IS IPv4 unicast address family view.
¡ IPv6:
isis ipv6 bfd adjust-cost { cost-offset | max }
By default, the IPv6 IS-IS interface inherits the configuration of the bfd all-interfaces adjust-cost command in IS-IS IPv6 unicast address family view.
Suppressing BFD session state-based interface cost adjustment upon BFD session flapping
About this task
After you enable BFD session state-based interface cost adjustment for IS-IS, the following issues might occur as the BFD session flaps frequently:
· The IS-IS interface cost changes frequently, resulting in repeated route calculations that greatly consume device resources.
· When the BFD session state changes from down to up, IS-IS immediately restores the original interface cost. If the link becomes unavailable again in a short time, packet loss will occur on this link before route convergence is complete.
To resolve the previous issues, configure this feature. When the BFD session state changes, IS-IS performs the following tasks instead of immediately adjusting the interface cost:
· When the BFD session state changes from up to down, IS-IS starts a BFD session state detection timer, and records one BFD session down event.
¡ If the number of BFD session down events reaches the threshold before the detection timer expires, IS-IS adjusts the interface cost based on the configuration of one of the following commands:
¡ If the number of BFD session down events does not reach the threshold before the detection timer expires, IS-IS does not adjust the interface cost.
|
|
NOTE: The detection timer, threshold, and resume timer are respectively specified with the detect-interval, threshold, and resume-interval arguments in the isis bfd adjust-cost suppress-flapping command or the isis ipv6 bfd adjust-cost suppress-flapping command. |
· After an interface cost adjustment based on the configuration of the isis bfd adjust-cost or isis ipv6 bfd adjust-cost command, IS-IS starts a resume timer when the BFD session state changes from down to up. When the resume timer expires, the following rules apply:
¡ If the BFD session state remains up before the resume timer expires, IS-IS restores the interface cost to the original.
¡ If the BFD session state changes from up to down before the resume timer expires, IS-IS deletes the resume timer and does not restore the interface cost to the original.
Restrictions and guidelines
This feature takes effect only after you configure the isis bfd adjust-cost command or the isis ipv6 bfd adjust-cost command.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Suppress BFD session state-based interface cost adjustment upon BFD session flapping.
¡ IPv4:
isis bfd adjust-cost suppress-flapping { detect-interval detect-interval | resume-interval resume-interval | threshold threshold } *
By default, IPv4 IS-IS does not suppress BFD session state-based interface cost adjustment upon BFD session flapping.
¡ IPv6:
isis ipv6 bfd adjust-cost suppress-flapping { detect-interval detect-interval | resume-interval resume-interval | threshold threshold } *
By default, IPv6 IS-IS does not suppress BFD session state-based interface cost adjustment upon BFD session flapping.
Controlling adjacency establishment and maintenance based on BFD session state
About this task
When BFD detects a Layer 3 forwarding failure between two routers, the BFD session goes down, which causes the IS-IS adjacency to go down. If Layer 2 forwarding is still available, the routers can exchange IS-IS packets and re-establish the adjacency, which might cause traffic loss.
To avoid the issue, enable this feature on the BFD-enabled interfaces of the local and remote routers, enabling the interfaces to carry BFD-enabled TLVs in hello packets. After the BFD session goes down, the routers do not establish an adjacency if the exchanged BFD-enabled TLVs are identical.
If two IS-IS routers establish both IPv4 and IPv6 adjacency relationships, the following rules apply:
· If route calculation is not performed separately for the IPv4 and IPv6 topologies, the IPv4 or IPv6 adjacency relationship is up only when both the IPv4 and IPv6 BFD sessions are up.
· If route calculation is performed separately for the IPv4 and IPv6 topologies, the IPv4 or IPv6 adjacency relationship is up when the corresponding IPv4 or IPv6 BFD session is up.
If two IS-IS routers establish only an IPv4 or IPv6 adjacency relationship, the adjacency relationship is up when the corresponding IPv4 or IPv6 BFD session is up.
For more information about BFD, see BFD configuration in High Availability Configuration Guide.
Restrictions and guidelines
This task can take effect on an IS-IS interface only when BFD is enabled on the interface.
You can use one of the following commands to enable BFD session state-based control of IS-IS adjacency establishment and maintenance:
· bfd all-interfaces session-restrict-adj
· isis bfd session-restrict-adj
· isis ipv6 bfd session-restrict-adj
These commands are different as follows:
· The bfd all-interfaces session-restrict-adj command takes effect on all interfaces in an IPv4 or IPv6 IS-IS process. To disable this feature on an interface in that IS-IS process, use the isis bfd session-restrict-adj exclude or isis ipv6 bfd session-restrict-adj exclude command on the interface.
· The isis bfd session-restrict-adj and isis ipv6 bfd session-restrict-adj commands take effect only on one IS-IS interface. To enable BFD session state-based control of IS-IS adjacency establishment and maintenance on a single IS-IS interface, perform the following tasks:
a. Make sure the IS-IS process to which the IS-IS interface belongs is not enabled with BFD session state-based control of adjacency establishment and maintenance.
You can use the undo bfd all-interfaces session-restrict-adj command to disable this feature for an IS-IS process.
b. Use the isis bfd session-restrict-adj or isis ipv6 bfd session-restrict-adj command to enable this feature on the IS-IS interface.
Enabling BFD session state-based control of IS-IS adjacency establishment and maintenance for an IS-IS process
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv4 address family view or IPv6 address family view.
¡ Enter IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable BFD session state-based control of IS-IS adjacency establishment and maintenance for the IS-IS process.
bfd all-interfaces session-restrict-adj
By default, BFD session state-based control of IS-IS adjacency establishment and maintenance is disabled for an IS-IS process.
5. (Optional.) Suppress BFD session state-based control of IS-IS adjacency establishment and maintenance on an IS-IS interface.
a. Return to IS-IS view.
quit
b. Return to system view.
quit
c. Enter interface view.
interface interface-type interface-number
d. Suppress BFD session state-based control of IS-IS adjacency establishment and maintenance on the IS-IS interface.
IPv4:
isis bfd session-restrict-adj exclude
By default, BFD session state-based control of IS-IS adjacency establishment and maintenance is not suppressed on an IPv4 IS-IS interface.
IPv6:
isis ipv6 bfd session-restrict-adj exclude
By default, BFD session state-based control of IS-IS adjacency establishment and maintenance is not suppressed on an IPv6 IS-IS interface.
Enabling BFD session state-based control of IS-IS adjacency establishment and maintenance on an IS-IS interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Enable IS-IS BFD on the interface.
¡ IPv4:
isis bfd enable
By default, the IPv4 IS-IS interface inherits the configuration of the bfd all-interfaces enable command in IS-IS IPv4 unicast address family view.
¡ IPv6:
isis ipv6 bfd enable
By default, the IPv6 IS-IS interface inherits the configuration of the bfd all-interfaces enable command in IS-IS IPv6 unicast address family view.
4. Enable BFD session state-based control of IS-IS adjacency establishment and maintenance on the IS-IS interface.
¡ IPv4:
isis bfd session-restrict-adj
By default, the IPv4 IS-IS interface inherits the configuration of the bfd all-interfaces session-restrict-adj command in IS-IS IPv4 unicast address family view.
¡ IPv6:
isis ipv6 bfd session-restrict-adj
By default, the IPv6 IS-IS interface inherits the configuration of the bfd all-interfaces session-restrict-adj command in IS-IS IPv6 unicast address family view.
Configuring IS-IS FRR
About IS-IS FRR
IS-IS Fast Reroute (FRR) calculates a backup path based on the LSDB and saves the backup path information to the FIB. When the primary path fails, the system immediately switches traffic to the backup path to prevent traffic loss and reduce the route convergence time.
IS-IS supports Loop Free Alternate (LFA) FRR and remote LFA FRR.
The following IS-IS FRR traffic protection types are available:
· Link protection—Protects traffic that traverses a specific link.
· Node protection—Protects traffic that traverses a specific node.
Node protection takes precedence over link protection.
IS-IS FRR tasks at a glance
¡ Configuring IPv4 IS-IS LFA FRR to calculate a backup next hop through LFA calculation
¡ Configuring IPv4 IS-IS LFA FRR using a routing policy
¡ Configuring IPv6 IS-IS LFA FRR to calculate a backup next hop through LFA calculation
¡ Configuring IPv6 IS-IS LFA FRR using a routing policy
¡ Enabling BFD-powered primary link failure detection for an IS-IS process
¡ Enabling BFD-powered primary link failure detection on an IS-IS interface
2. Configuring IS-IS remote LFA FRR
3. (Optional.) Setting the priority for FRR backup path selection policies
Configuring IS-IS LFA FRR
About this task
A link or router failure on a path can cause packet loss. IS-IS LFA FRR enables fast rerouting to minimize the failover time.
Figure 26 Network diagram for IS-IS LFA FRR
In Figure 26, after you enable LFA FRR on Router B, IS-IS automatically calculates or designates a backup next hop when a link failure is detected. In this way, packets are directed to the backup next hop to reduce traffic recovery time. Meanwhile, IS-IS calculates the shortest path based on the new network topology, and forwards packets over the path after network convergence.
When a primary link failure occurs, BFD can detect and report the link failure to IS-IS for a primary-backup path switchover. This can shorten the duration of service interruption.
You can assign a backup next hop for IS-IS FRR through the following ways:
· Enable IS-IS LFA FRR to calculate a backup next hop through LFA calculation.
· Designate a backup next hop with a routing policy for routes matching specific criteria.
Restrictions and guidelines
The LFA calculation of FRR and that of TE are mutually exclusive.
To enable BFD-powered primary link failure detection for IS-IS FRR, you can use the fast-reroute primary-path-detect bfd , isis primary-path-detect bfd, or isis ipv6 primary-path-detect bfd command.
These commands are different as follows:
· The fast-reroute primary-path-detect bfd command takes effect on all interfaces in an IPv4 or IPv6 IS-IS process. To disable this feature on an interface in that IS-IS process, use the isis primary-path-detect bfd exclude or isis ipv6 primary-path-detect bfd exclude command on the interface.
· The isis primary-path-detect bfd and isis ipv6 primary-path-detect bfd commands take effect only on one IS-IS interface. To enable BFD-powered primary link failure detection on a single IS-IS interface, perform the following tasks:
a. Make sure the IS-IS process to which the IS-IS interface belongs is not enabled with BFD-powered primary link failure detection.
You can use the undo fast-reroute primary-path-detect bfd command to disable this feature for an IS-IS process.
b. Use the isis primary-path-detect bfd or isis ipv6 primary-path-detect bfd command to enable this feature on the IS-IS interface.
Configuring IPv4 IS-IS LFA FRR to calculate a backup next hop through LFA calculation
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Disable LFA calculation on the interface.
isis fast-reroute lfa-backup exclude [ level-1 | level-2 ]
By default, the interface participates in LFA calculation, and can be elected as a backup interface.
4. Return to system view.
quit
5. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
6. Enable IS-IS LFA FRR to calculate a backup next hop through LFA calculation.
fast-reroute lfa [ ecmp-shared | level-1 | level-2 ]
By default, IS-IS FRR is disabled.
Configuring IPv4 IS-IS LFA FRR using a routing policy
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Disable LFA calculation on the interface.
isis fast-reroute lfa-backup exclude [ level-1 | level-2 ]
By default, the interface participates in LFA calculation, and can be elected as a backup interface.
4. Return to system view.
quit
5. Enter IS-IS IPv4 unicast address family view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
address-family ipv4 [ unicast ]
6. Enable IPv4 IS-IS LFA FRR using a routing policy.
¡ Create a routing policy and specify a backup next hop.
apply fast-reroute backup-interface
For more information about the apply fast-reroute backup-interface command and routing policy, see Layer 3—IP Routing Configuration Guide.
¡ Configure IPv4 IS-IS LFA FRR.
fast-reroute route-policy route-policy-name
By default, IPv4 IS-IS LFA FRR is disabled.
Configuring IPv6 IS-IS LFA FRR to calculate a backup next hop through LFA calculation
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Disable LFA calculation on the interface.
isis ipv6 fast-reroute lfa-backup exclude
By default, the interface participates in LFA calculation, and can be elected as a backup interface.
4. Return to system view.
quit
5. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
6. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
7. Enable IPv6 IS-IS LFA FRR to calculate a backup next hop through LFA calculation.
fast-reroute lfa [ ecmp-shared | level-1 | level-2 ]
By default, IPv6 IS-IS LFA FRR is disabled.
Configuring IPv6 IS-IS LFA FRR using a routing policy
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. (Optional.) Disable LFA calculation on the interface.
isis ipv6 fast-reroute lfa-backup exclude [ level-1 | level-2 ]
By default, the interface participates in LFA calculation, and can be elected as a backup interface.
4. Return to system view.
quit
5. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
6. Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
7. Enable IPv6 IS-IS LFA FRR using a routing policy.
¡ Create a routing policy and specify a backup next hop.
apply ipv6 fast-reroute backup-interface
For more information about the apply ipv6 fast-reroute backup-interface command and routing policy, see Layer 3—IP Routing Configuration Guide.
¡ Configure IPv6 IS-IS LFA FRR.
fast-reroute route-policy route-policy-name
By default, IPv6 IS-IS LFA FRR is disabled.
Enabling BFD-powered primary link failure detection for an IS-IS process
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IPv4 address family view or IPv6 address family view.
¡ Enter IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IPv6 address family view.
address-family ipv6 [ unicast ]
4. Enable BFD-powered primary link failure detection for the IS-IS process.
fast-reroute primary-path-detect bfd { ctrl | echo }
By default, BFD-powered primary link failure detection is disabled for an IS-IS process.
To use BFD (echo packet mode) to detect primary link failures, configure the source IP address of BFD echo packets by using the bfd echo-source-ip or bfd echo-source-ipv6 command.
5. (Optional.) Suppress BFD-powered primary link failure detection on an IS-IS interface.
a. Return to IS-IS view.
quit
b. Return to system view.
quit
c. Enter interface view.
interface interface-type interface-number
d. Suppress BFD-powered primary link failure detection on the IS-IS interface.
IPv4:
isis primary-path-detect bfd exclude
By default, BFD-powered primary link failure detection is not suppressed on an IPv4 IS-IS interface.
IPv6:
isis ipv6 primary-path-detect bfd exclude
By default, BFD-powered primary link failure detection is not suppressed on an IPv6 IS-IS interface.
Enabling BFD-powered primary link failure detection on an IS-IS interface
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable BFD-powered primary link failure detection on the IS-IS interface.
¡ IPv4:
isis primary-path-detect bfd { ctrl | echo }
By default, the IPv4 IS-IS interface inherits the configuration of the fast-reroute primary-path-detect bfd command in IS-IS IPv4 unicast address family view.
¡ IPv6:
isis ipv6 primary-path-detect bfd { ctrl | echo }
By default, the IPv6 IS-IS interface inherits the configuration of the fast-reroute primary-path-detect bfd command in IS-IS IPv6 unicast address family view.
To use BFD (echo packet mode) to detect primary link failures, configure the source IP address of BFD echo packets by using the bfd echo-source-ip or bfd echo-source-ipv6 command.
To use BFD (control packet mode) to detect primary link failures, you must enable BFD control packet mode on both ends of the link.
Configuring IS-IS remote LFA FRR
About this task
In a ring topology where IS-IS LFA FRR cannot calculate the backup path, configure remote LFA FRR to ensure network reliability.
Remote LFA uses the following concepts:
· P space—Use the source node of the protected link as the root to establish a shortest path tree. All nodes that are reachable from the source node without passing the protected link form the P space. Nodes in the P space are called P nodes.
· Extended P space—Use the source node of the protected link and its neighbors as the roots to establish shortest path trees. All nodes that are reachable from the source node or one of its neighbors without passing the protected link form the extended P space. The P space is a subset of the extended P space.
· Q space—Use the destination node of the protected link as the root to establish a reverse shortest path tree. All nodes that are reachable from the root node without passing the protected link form the Q space. Nodes in the Q space are called Q nodes.
· PQ node—A PQ node refers to a node that resides in both the extended P space and the Q space. Remote LFA uses a PQ node as the destination node of a protected link.
As shown in Figure 27, the traffic forwarding path is PE 1—P 1—P 2—PE 2. To avoid traffic loss caused by link failures between P 1 and P 2, the system establishes an LDP tunnel between P 1 and P 4, which is the PQ node. When the link between P 1 and P 2 fails, P 1 encapsulates IP packets in MPLS packets and sends the MPLS packets to P 4 through the LDP tunnel. After receiving the MPLS packets, P 4 removes the MPLS labels of the packets and then forwards the packets to the next hop based on the IP routing table.
The system determines P 4 as the PQ node as follows:
1. Uses P 1 (source node of the protected link) and its neighbors except P 2 (which passes the protected link) as the roots to establish shortest path trees.
2. Finds out all nodes that are reachable from P 1 or one of its neighbors without passing the protected link, which are PE 1, P 1, P 3, and P 4.
These nodes form the extended P space.
3. Uses P 2 (destination node of the protected link) as the root to establish a reverse shortest path tree.
4. Finds out all nodes that are reachable from P 2 without passing the protected link, which are PE 2 and P 4.
These nodes form the Q space.
5. Finds out all nodes that reside in both the extended P space and the Q space.
Only P 4 resides in both the extended P space and the Q space, so P 4 is the PQ node of the protected link.
Figure 27 Network diagram for IS-IS remote LFA FRR
Restrictions and guidelines
To implement remote LFA FRR at a specific IS-IS level, you must enable LFA FRR for that IS-IS level.
Prerequisites
Enable MPLS and MPLS LDP on all nodes and interfaces participating in MPLS forwarding. For more information, see basic MPLS configuration and LDP configuration in MPLS Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 unicast address family view.
address-family ipv4 [ unicast ]
4. Enable IS-IS remote LFA FRR.
fast-reroute remote-lfa tunnel ldp [ level-1 | level-2 ]
By default, IS-IS remote LFA FRR is disabled.
5. (Optional.) Set the maximum cost from the source node of a protected link to a PQ node.
fast-reroute remote-lfa maximum-cost cost [ level-1 | level-2 ]
By default, the maximum cost from the source node of a protected link to a PQ node is 16777215.
6. (Optional.) Specify a prefix list to filter PQ nodes.
fast-reroute remote-lfa prefix-list prefix-list-name [ level-1 | level-2 ]
By default, no prefix list is specified to filter PQ nodes. Any PQ node can be selected as the backup next hop.
Multiple PQ nodes might reach the source node of a specific protected link. You can use this command to specify a prefix list to filter PQ nodes.
7. (Optional.) Disable remote LFA calculation on an interface.
a. Return to system view.
quit
b. Enter interface view.
interface interface-type interface-number
c. Disable remote LFA calculation on the interface.
isis fast-reroute remote-lfa disable [ level-1 | level-2 ]
By default, remote LFA calculation is enabled on the interface.
Setting the priority for FRR backup path selection policies
About this task
IS-IS FRR uses specific policies for backup path calculation. The fast-reroute tiebreaker command defines the priority for the backup path selection policy. The higher the value, the higher the priority of the associated backup path selection policy. Changing the backup path selection policy priority can affect the backup path calculation result for IS-IS FRR. The backup paths can provide node protection or link protection for traffic, or provide both node protection and link protection.
IS-IS FRR supports the following backup path selection policies that are used to generate different topologies for backup path calculation:
· Node protection—IS-IS FRR performs backup path calculation after excluding the primary next hop node.
· Lowest cost—IS-IS FRR performs backup path calculation after excluding the direct primary link.
· SRLG disjoint—When one link in the SRLG fails, the other links in the SRLG might also fail. If you use a link in this SRLG as the backup link for the failed link, protection does not take effect. To avoid this issue, IS-IS FRR excludes the local links in the same SRLG as the direct primary link and then performs backup path calculation.
For IS-IS FRR, the SRLG disjoint policy depends on the node protection and lowest cost policies.
If multiple backup path selection policies exist in an IS-IS process, the policy with the highest priority is used to calculate the backup path. If the policy fails to calculate the backup path, another policy with higher priority is used. IS-IS performs backup path calculation by using the node protection and lowest cost policies as follows:
· If the node protection policy has higher priority and fails to calculate the backup path, IS-IS uses the lowest cost policy to calculate the backup path. If the lowest cost policy still fails to calculate the backup path, reliability cannot be ensured upon primary link failure.
· If the lowest cost policy has higher priority and fails to calculate the backup path, IS-IS does not perform further backup path calculation with the node protection policy. Reliability cannot be ensured upon primary link failure.
Table 4 shows the backup path selection mechanism for IS-IS FRR based on priorities of backup path selection policies.
Table 4 Backup path selection mechanism for IS-IS FRR
|
Priorities of link selection policies |
Backup path selection mechanism for IS-IS FRR |
|
Node protection > lowest cost > SRLG-disjoint |
IS-IS FRR performs calculations based on the node protection and lowest cost policies in descending order of priority. IS-IS FRR performs a maximum of two calculations. If IS-IS FRR obtains a backup path with a link selection policy, it does not perform further calculation. |
|
Node protection > SRLG-disjoint > lowest cost |
IS-IS FRR performs calculations based on the node protection, node protection + SRLG-disjoint, lowest cost + SRLG-disjoint, and lowest cost policies in descending order of priority. IS-IS FRR performs a maximum of four calculations. If IS-IS FRR obtains a backup path with a link selection policy, it does not perform further calculation. |
|
SRLG-disjoint > node protection > lowest cost |
IS-IS FRR performs calculations based on the node protection + SRLG-disjoint, lowest cost + SRLG-disjoint, node protection, and lowest cost policies in descending order of priority. IS-IS FRR performs a maximum of four calculations. If IS-IS FRR obtains a backup path with a link selection policy, it does not perform further calculation. |
|
Lowest cost > node protection > SRLG-disjoint |
IS-IS FRR performs calculations based on the lowest cost policy. IS-IS FRR performs only one calculation. |
|
Lowest cost > SRLG-disjoint > node protection |
IS-IS FRR performs calculations based on the lowest cost policy. IS-IS FRR performs only one calculation. |
|
SRLG-disjoint > lowest cost > node protection |
IS-IS FRR performs calculations based on the node protection + SRLG-disjoint, lowest cost + SRLG-disjoint, and lowest cost policies in descending order of priority. IS-IS FRR performs a maximum of three calculations. If IS-IS FRR obtains a backup path with a link selection policy, it does not perform further calculation. |
Procedure
1. Enter system view.
system-view
2. Enter IS-IS view.
isis [ process-id ] [ vpn-instance vpn-instance-name ]
3. Enter IS-IS IPv4 address family view or IS-IS IPv6 address family view.
¡ Enter IS-IS IPv4 address family view.
address-family ipv4 [ unicast ]
¡ Enter IS-IS IPv6 address family view.
address-family ipv6 [ unicast ]
4. Set the priority value for a backup path selection policy.
fast-reroute tiebreaker { lowest-cost | node-protecting | srlg-disjoint } preference preference [ level-1 | level-2 ]
By default, the priority values of the node-protection, lowest-cost, and shared risk link group (SRLG)-disjoint backup path selection policies are 40, 20, and 10, respectively.
Enabling IS-IS to adjust the interface cost according to the link quality
About this task
Error codes, which refer to bit differences between the received and source signals, cannot be avoided because of inevitable link aging and optical path jitter problems. A high error code ratio might cause service degradation or interruption.
To reduce the impact of error codes on an IS-IS network, you can enable IS-IS to adjust the interface cost according to the link quality.
After you configure this feature on an interface, IS-IS adjusts the interface cost as follows:
· When the link quality of the interface becomes LOW, IS-IS increases the cost value for the interface.
· When the link quality of the interface restores to GOOD, IS-IS restores the cost value for the interface to the original value.
For more information about error code detection, see error code detection configuration in High Availability Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Enable IS-IS to adjust the link cost according to the link quality.
isis link-quality adjust-cost { cost-offset | max }
By default, IS-IS does not adjust the link cost according to the link quality.
Configuring IS-IS neighbor flapping suppression
About this task
When the state of an IS-IS neighbor flaps frequently, IS-IS also frequently performs neighbor relationship re-establishment, LSDB synchronization, and route calculation. Such tasks interrupt IS-IS services and other services that depend on IS-IS, because performing these tasks requires a large number of packet exchanges. To resolve this issue, configure IS-IS neighbor flapping suppression. This feature enables IS-IS to suppress neighbor flapping on an interface by increasing the cost value for the interface. Traffic then does not pass through the interface during neighbor flapping suppression. When the resume timer for neighbor flapping suppression expires, IS-IS restores the cost value to the original for the interface.
IS-IS supports the conservative and non-conservative modes for neighbor flapping suppression.
The conservative mode functions as follows:
1. After you enable neighbor flapping suppression on an interface, the interface starts a flapping event counter to collect statistics about neighbor flapping events. When the time gap between two neighbor down events in a row is shorter than the detection timer, IS-IS increases the number of neighbor flapping events by one.
IS-IS resets and restarts the flapping event counter when the following conditions exist:
¡ The number of neighbor flapping events is less than the threshold that triggers neighbor flapping suppression.
¡ The time gap between two neighbor down events in a row is longer than the resume timer.
2. IS-IS compares the number of neighbor flapping events with the threshold that triggers neighbor flapping suppression:
¡ If the number of neighbor flapping events is less than the threshold, IS-IS does not suppress neighbor flapping.
¡ If the number of neighbor flapping events is not less than the threshold, IS-IS starts neighbor flapping suppression. It increases the cost value for the interface and resets the flapping event counter.
3. The resume timer starts as IS-IS starts neighbor flapping suppression. The suppression duration equals the resume timer.
If a neighbor down event occurs on the interface during neighbor flapping suppression, IS-IS restarts the resume timer.
4. After the resume timer expires, IS-IS restores the cost value to the original for the interface if no neighbor flapping events occur on the interface before the resume timer expires.
The non-conservative mode functions as follows:
1. After you enable neighbor flapping suppression on an interface, the interface starts a flapping event counter to collect statistics about neighbor flapping events. IS-IS increases the number of neighbor flapping events by one each time a neighbor down event occurs on the interface.
When a neighbor down event occurs on the interface, IS-IS performs the following tasks:
a. Record the timestamp of the neighbor down event.
|
|
NOTE: For brief description, the following arguments are introduced: · The T argument represents the timestamp that equals the neighbor down event timestamp minus the detection timer. · The flapping-count argument represents the number of neighbor flapping events that occur later than T and not later than the neighbor down event timestamp. |
b. Compare flapping-count with the threshold that triggers neighbor flapping suppression:
- If flapping-count is less than the threshold, IS-IS does not suppress neighbor flapping or reset the flapping event counter.
- If flapping-count is not less than the threshold, IS-IS starts neighbor flapping suppression. It increases the cost value for the interface and resets the flapping event counter.
2. The resume timer starts as IS-IS starts neighbor flapping suppression. The suppression duration equals the resume timer.
If a neighbor down event occurs on the interface during neighbor flapping suppression, IS-IS restarts the resume timer.
3. After the resume timer expires, IS-IS restores the cost value to the original for the interface if no neighbor flapping events occur on the interface before the resume timer expires.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Configure the detection parameters for IS-IS neighbor flapping suppression.
¡ IPv4 IS-IS:
isis peer suppress-flapping { [ detect-interval detect-interval | threshold threshold | resume-interval resume-interval ] * | non-conservative }
By default, the detection timer is 60 seconds, the threshold is 10, and the resume timer is 120 seconds.
¡ IPv6 IS-IS:
isis ipv6 peer suppress-flapping { [ detect-interval detect-interval | threshold threshold | resume-interval resume-interval ] * | non-conservative }
By default, the detection timer is 60 seconds, the threshold is 10, and the resume timer is 120 seconds.
4. Enable neighbor flapping suppression on the interface and specify the cost adjustment value for the interface.
¡ IPv4 IS-IS:
isis peer suppress-flapping adjust-cost { cost-offset | max }
By default, neighbor flapping suppression is disabled on an IPv4 IS-IS interface.
¡ IPv6 IS-IS:
isis ipv6 peer suppress-flapping adjust-cost { cost-offset | max }
By default, neighbor flapping suppression is disabled on an IPv6 IS-IS interface.
Configuring IS-IS member port flapping suppression
About this task
When two IS-IS neighbors are connected by Layer 3 aggregate links and the links between member ports flap frequently, the neighbors perform link switchover frequently for traffic forwarding. To resolve this issue, enable member port flapping suppression on the aggregate interfaces.
This feature enables IS-IS to suppress member port flapping on an aggregate interface by increasing the cost value for the aggregate interface. Traffic then does not pass through the aggregate interface during member port flapping suppression. When the resume timer for member port flapping suppression expires, IS-IS restores the cost value to the original for the aggregate interface.
IS-IS supports the conservative and non-conservative modes for member port flapping suppression.
The conservative mode functions as follows:
1. After you enable member port flapping suppression on an aggregate interface, the aggregate interface starts a flapping event counter to collect statistics about the flapping events that occur on its member ports. When the time gap between two link failures in a row is shorter than the detection timer, IS-IS increases the number of member port flapping events by one.
IS-IS resets and restarts the flapping event counter when the following conditions exist:
¡ The number of member port flapping events is less than the threshold that triggers member port flapping suppression.
¡ The time gap between two link failures in a row is longer than the resume timer.
2. IS-IS compares the number of member port flapping events with the threshold that triggers member port flapping suppression:
¡ If the number of member port flapping events is less than the threshold, IS-IS does not suppress member port flapping.
¡ If the number of member port flapping events is not less than the threshold, IS-IS starts member port flapping suppression. It increases the cost value for the aggregate interface and resets the flapping event counter.
3. The resume timer starts as IS-IS starts member port flapping suppression. The suppression duration equals the resume timer.
If a link failure occurs on a member port during member port flapping suppression, IS-IS restarts the resume timer.
4. After the resume timer expires, IS-IS restores the cost value to the original for the aggregate interface if no link failures occur on member ports before the resume timer expires.
The non-conservative mode functions as follows:
1. After you enable member port flapping suppression on an aggregate interface, the aggregate interface starts a flapping event counter to collect statistics about the flapping events that occur on its member ports. IS-IS increases the number of member port flapping events by one each time a link failure occurs on a member port.
When a link failure occurs on a member port, IS-IS performs the following tasks:
a. Record the timestamp of the link failure.
|
|
NOTE: For brief description, the following arguments are introduced: · The T argument represents the timestamp that equals the link failure timestamp minus the detection timer. · The flapping-count argument represents the number of member port flapping events that occur later than T and not later than the link failure timestamp. |
b. Compare flapping-count with the threshold that triggers neighbor flapping suppression:
- If flapping-count is less than the threshold, IS-IS does not suppress member port flapping or reset the flapping event counter.
- If flapping-count is not less than the threshold, IS-IS starts member port flapping suppression. It increases the cost value for the aggregate interface and resets the flapping event counter.
2. The resume timer starts as IS-IS starts member port flapping suppression. The suppression duration equals the resume timer.
If a link failure occurs on a member port during member port flapping suppression, IS-IS restarts the resume timer.
3. After the resume timer expires, IS-IS restores the cost value to the original for the aggregate interface if no link failures occur on member ports before the resume timer expires.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 3 aggregate interface view.
interface route-aggregation interface-number [ pex ]
¡ Enter Layer 3 aggregate subinterface view.
interface route-aggregation interface-number.subnumber
3. Configure the detection parameters for IS-IS member port flapping suppression.
¡ IPv4 IS-IS:
isis member-port suppress-flapping { [ detect-interval detect-interval | threshold threshold | resume-interval resume-interval ] * | non-conservative }
By default, the detection timer is 60 seconds, the threshold is 10, and the resume timer is 120 seconds.
¡ IPv6 IS-IS:
isis ipv6 member-port suppress-flapping { [ detect-interval detect-interval | threshold threshold | resume-interval resume-interval ] * | non-conservative }
By default, the detection timer is 60 seconds, the threshold is 10, and the resume timer is 120 seconds.
4. Enable member port flapping suppression on the interface and specify the cost adjustment value for the interface.
¡ IPv4 IS-IS:
isis member-port suppress-flapping adjust-cost { cost-offset | max }
By default, member port flapping suppression is disabled on an IPv4 IS-IS aggregate interface.
¡ IPv6 IS-IS:
isis ipv6 member-port suppress-flapping adjust-cost { cost-offset | max }
By default, member port flapping suppression is disabled on an IPv6 IS-IS aggregate interface.
Display and maintenance commands for IS-IS
Execute display commands in any view and the reset command in user view.
Displaying and maintaining IPv4 IS-IS
|
Task |
Command |
|
|
Display IS-IS process information. |
display isis [ process-id ] |
|
|
Display IS-IS GR log information. |
In standalone mode: display isis event-log graceful-restart slot slot-number [ cpu cpu-number ] In IRF mode: display isis event-log graceful-restart chassis chassis-number slot slot-number [ cpu cpu-number ] |
|
|
Display IS-IS log information about received or sent hello packets. |
display isis event-log hello { peer-change | received-abnormal | received-dropped | sent-abnormal | sent-failed } [ process-id ] |
|
|
Display neighbor state change log information. |
display isis event-log peer [ process-id ] |
|
|
Display information about hello packets sent by an interface. |
display isis interface [ interface-type interface-number ] hello-sent [ process-id ] |
|
|
Display the IS-IS GR status. |
display isis graceful-restart status [ level-1 | level-2 ] [ process-id ] |
|
|
Display IS-IS interface information. |
display isis interface [ [ interface-type interface-number ] [ verbose ] | statistics ] [ process-id ] |
|
|
Display IS-IS LSDB information. |
display isis lsdb [ [ level-1 | level-2 ] | local | lsp-id lspid | [ lsp-name lspname ] | verbose ] * [ process-id ] |
|
|
Display IS-IS LSDB statistics. |
display isis lsdb statistics [ level-1 | level-2 ] [ process-id ] |
|
|
Display IS-IS mesh group information. |
display isis mesh-group [ process-id ] |
|
|
Display the host name to system ID mapping table. |
display isis name-table [ process-id ] |
|
|
Display IS-IS NSR log information. |
In standalone mode: display isis event-log slot non-stop-routing slot-number [ cpu cpu-number ] In IRF mode: display isis event-log non-stop-routing chassis chassis-number slot slot-number [ cpu cpu-number ] |
|
|
Display the IS-IS NSR status. |
display isis non-stop-routing status |
|
|
Display IS-IS packet statistics. |
display isis packet { csnp | hello | lsp | psnp } by-interface [ verbose ] [ interface-type interface-number ] [ process-id ] display isis packet { csnp | hello | lsp | psnp } [ verbose ] [ process-id ] |
|
|
Display IS-IS neighbor information. |
display isis peer [ statistics | verbose ] [ process-id ] |
|
|
Display information about hello packets received from neighbors. |
display isis peer hello-received [ process-id ] |
|
|
Display IS-IS redistributed IPv4 route information. |
display isis redistribute [ ipv4 [ ip-address mask-length ] ] [ level-1 | level-2 ] [ process-id ] |
|
|
Display IS-IS IPv4 routing information. |
display isis route [ ipv4 [ ip-address mask-length | priority { critical | high | low | medium } ] ] [ [ level-1 | level-2 ] | [ source-id source-id | verbose ] ] * [ process-id ] |
|
|
Display IS-IS IPv4 topology information. |
display isis spf-tree [ ipv4 [ topology topo-name ] ] [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
|
Display IS-IS statistics. |
display isis statistics [ ipv4 ] [ level-1 | level-1-2 | level-2 ] [ process-id ] |
|
|
Display IS-IS neighbor relationship troubleshooting information. |
display isis troubleshooting |
|
|
Display IS-IS IPv4 route calculation log information. |
display isis event-log spf [ ipv4 ] [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
|
Display IS-IS LSP update log information. |
display isis event-log updated-lsp [ history [ hour-range hour-range1 to hour-range2 ] ] [ system-id system-id ] [ level-1 | level-2 ] [ process-id ] |
|
|
Display IS-IS LSP log information. |
display isis event-log lsp { purged [ generated | received ] | refreshed } [ level-1 | level-2 ] [ process-id ] |
|
|
Display information about routes calculated by a flexible algorithm. |
display isis flex-algo flex-algo-id route [ level-1 | level-2 ] [ process-id ] [ verbose ] |
|
|
Display SPF tree information calculated by a flexible algorithm. |
display isis flex-algo flex-algo-id spf-tree ipv4 [ level-1 | level-2 ] [ source-id source-id ] [ verbose ] |
|
|
Display information about the FADs received and advertised by a node. |
display isis global-flex-algo [ algorithm-id flex-algo-id ] [ level-1 | level-2 ] [ process-id ] [ system-id system-id ] |
|
|
Display the configuration for a flexible algorithm on a node. |
display isis local-flex-algo [ algorithm-id flex-algo-id ] [ process-id ] |
|
|
Display OSI connection information. |
In standalone mode: display osi [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display osi [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
|
Display OSI connection statistics. |
In standalone mode: display osi statistics [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display osi statistics [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
|
Display global IS-IS statistics. |
display isis global-statistics [ public | vpn-instance vpn-instance-name ] |
|
|
Clear IS-IS process data structure information. |
reset isis all [ process-id ] [ graceful-restart ] |
|
|
Clear IS-IS log information. |
reset isis event-log { hello { peer-change | received-abnormal | received-dropped | sent-abnormal | sent-failed } | peer } [ process-id ] |
|
|
Clear IS-IS GR log information. |
In standalone mode: reset isis event-log graceful-restart slot slot-number [ cpu cpu-number ] In IRF mode: reset isis event-log graceful-restart chassis chassis-number slot slot-number [ cpu cpu-number ] |
|
|
Clear IS-IS NSR log information. |
In standalone mode: reset isis event-log non-stop-routing slot slot-number [ cpu cpu-number ] In IRF mode: reset isis event-log non-stop-routing chassis chassis-number slot slot-number [ cpu cpu-number ] |
|
|
Clear IS-IS route calculation log information. |
reset isis event-log spf [ process-id ] |
|
|
Clear IS-IS LSP update log information. |
reset isis event-log updated-lsp |
|
|
Clear IS-IS LSP log information. |
reset isis event-log lsp { purged [ generated | received ] | refreshed } [ process-id ] |
|
|
Clear IS-IS packet statistics. |
reset isis packet [ csnp | hello | lsp | psnp ] by-interface [ interface-type interface-number ] [ process-id ] |
|
|
Clear the data structure information of an IS-IS neighbor. |
reset isis peer system-id [ process-id ] |
|
|
Clear OSI connection statistics. |
reset osi statistics |
|
|
Clear IS-IS neighbor relationship troubleshooting information. |
reset isis troubleshooting |
|
Displaying and maintaining IPv6 IS-IS
|
Task |
Command |
|
Display IS-IS process information. |
display isis [ process-id ] |
|
Display IS-IS log information about received or sent hello packets. |
display isis event-log hello { peer-change | received-abnormal | received-dropped | sent-abnormal | sent-failed } [ process-id ] |
|
Display neighbor state change log information. |
display isis event-log peer [ process-id ] |
|
Display information about routes calculated by a flexible algorithm. |
display isis flex-algo flex-algo-id route [ level-1 | level-2 ] [ process-id ] [ verbose ] |
|
Display SPF tree information calculated by a flexible algorithm. |
display isis flex-algo flex-algo-id spf-tree ipv6 [ level-1 | level-2 ] [ source-id source-id ] [ verbose ] |
|
Display information about the FADs received and advertised by a node. |
display isis global-flex-algo [ algorithm-id flex-algo-id ] [ level-1 | level-2 ] [ process-id ] [ system-id system-id ] |
|
Display the configuration for a flexible algorithm on a node. |
display isis local-flex-algo [ algorithm-id flex-algo-id ] [ process-id ] |
|
Display information about hello packets sent by an interface. |
display isis interface [ interface-type interface-number ] hello-sent [ process-id ] |
|
Display IS-IS interface information. |
display isis interface [ [ interface-type interface-number ] [ verbose ] | statistics ] [ process-id ] |
|
Display IS-IS LSDB information. |
display isis lsdb [ [ level-1 | level-2 ] | local | lsp-id lspid | [ lsp-name lspname ] | verbose ] * [ process-id ] |
|
Display IS-IS LSDB statistics. |
display isis lsdb statistics [ level-1 | level-2 ] [ process-id ] |
|
Display IS-IS mesh group information. |
display isis mesh-group [ process-id ] |
|
Display the host name to system ID mapping table. |
display isis name-table [ process-id ] |
|
Display IS-IS packet statistics. |
display isis packet { csnp | hello | lsp | psnp } [ verbose ] [ interface-type interface-number ] [ process-id ] |
|
Display IS-IS neighbor information. |
display isis peer [ statistics | verbose ] [ process-id ] |
|
Display information about hello packets received from neighbors. |
display isis peer hello-received [ process-id ] |
|
Display IPv6 IS-IS redistributed route information. |
display isis redistribute ipv6 [ ipv6-address mask-length ] [ level-1 | level-2 ] [ process-id ] |
|
Display IPv6 IS-IS routing information. |
display isis route ipv6 [ ipv6-address | priority { critical | high | low | medium } ] [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
Display IS-IS BIER route information. |
display isis route bier sub-domain sub-domain-id ipv6 [ ipv6-address prefix-length ] [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
Display IPv6 IS-IS topology information. |
display isis spf-tree ipv6 [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
Display IS-IS BIER SPF tree information. |
display isis spf-tree bier sub-domain sub-domain-id ipv6 [ [ level-1 | level-2 ] | [ source-id source-id | verbose ] ] * [ process-id ] |
|
Display IPv6 IS-IS statistics. |
display isis statistics ipv6 [ level-1 | level-1-2 | level-2 ] [ process-id ] |
|
Display IS-IS neighbor relationship troubleshooting information. |
display isis troubleshooting |
|
Display trust level mapping information. |
display isis trust-level-mapping |
|
Display IPv6 IS-IS route calculation log information. |
display isis event-log spf ipv6 [ [ level-1 | level-2 ] | verbose ] * [ process-id ] |
|
Display IPv6 IS-IS LSP update log information. |
display isis event-log updated-lsp [ history [ hour-range hour-range1 to hour-range2 ] ] [ system-id system-id ] [ level-1 | level-2 ] [ process-id ] |
|
Display IPv6 IS-IS LSP log information. |
display isis event-log lsp { purged [ generated | received ] | refreshed } [ level-1 | level-2 ] [ process-id ] |
|
Display OSI connection information. |
In standalone mode: display osi [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display osi [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display OSI connection statistics. |
In standalone mode: display osi statistics [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display osi statistics [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display global IS-IS statistics. |
display isis global-statistics [ public | vpn-instance vpn-instance-name ] |
|
Clear IS-IS process data structure information. |
reset isis all [ process-id ] [ graceful-restart ] |
|
Clear IS-IS log information. |
reset isis event-log { hello { peer-change | received-abnormal | received-dropped | sent-abnormal | sent-failed } | peer } [ process-id ] |
|
Clear IS-IS route calculation log information. |
reset isis event-log spf [ process-id ] |
|
Clear IS-IS LSP update log information. |
reset isis event-log updated-lsp |
|
Clear IS-IS LSP log information. |
reset isis event-log lsp { purged [ generated | received ] | refreshed } [ process-id ] |
|
Clear IS-IS packet statistics. |
reset isis packet [ csnp | hello | lsp | psnp ] by-interface [ interface-type interface-number ] [ process-id ] |
|
Clear the data structure information of an IS-IS neighbor. |
reset isis peer system-id [ process-id ] |
|
Clear OSI connection statistics. |
reset osi statistics |
|
Clear IS-IS neighbor relationship troubleshooting information. |
reset isis troubleshooting |
IS-IS configuration examples
Example: Configuring basic IS-IS
Network configuration
As shown in Figure 28, Router A, Router B, Router C, and Router D reside in an AS.
Router A and Router B are Level-1 routers, Router D is a Level-2 router, and Router C is a Level-1-2 router connecting two areas. Router A, Router B, and Router C are in area 10, and Router D is in area 20.
Procedure
1. Configure IP addresses for interfaces. (Details not shown.)
2. Configure IS-IS:
# Configure Router A
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] is-level level-1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] is-level level-1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/3
[RouterC-Ten-GigabitEthernet3/1/3] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/3] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/2] quit
# Configure Router D
<RouterD> system-view
[RouterD] isis 1
[RouterD-isis-1] is-level level-2
[RouterD-isis-1] network-entity 20.0000.0000.0004.00
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/1] quit
[RouterD] interface ten-gigabitethernet 3/1/2
[RouterD-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/2] quit
Verifying the configuration
# Display the IS-IS LSDB information.
[RouterA] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
---------------------------
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00* 0x00000004 0xdf5e 1096 68 0/0/0
0000.0000.0002.00-00 0x00000004 0xee4d 1102 68 0/0/0
0000.0000.0002.01-00 0x00000001 0xdaaf 1102 55 0/0/0
0000.0000.0003.00-00 0x00000009 0xcaa3 1161 111 1/0/0
0000.0000.0003.01-00 0x00000001 0xadda 1112 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[RouterB] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
---------------------------
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00 0x00000006 0xdb60 988 68 0/0/0
0000.0000.0002.00-00* 0x00000008 0xe651 1189 68 0/0/0
0000.0000.0002.01-00* 0x00000005 0xd2b3 1188 55 0/0/0
0000.0000.0003.00-00 0x00000014 0x194a 1190 111 1/0/0
0000.0000.0003.01-00 0x00000002 0xabdb 995 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[RouterC] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-1 Link State Database
---------------------------
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0001.00-00 0x00000006 0xdb60 847 68 0/0/0
0000.0000.0002.00-00 0x00000008 0xe651 1053 68 0/0/0
0000.0000.0002.01-00 0x00000005 0xd2b3 1052 55 0/0/0
0000.0000.0003.00-00* 0x00000014 0x194a 1051 111 1/0/0
0000.0000.0003.01-00* 0x00000002 0xabdb 854 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
Level-2 Link State Database
---------------------------
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0003.00-00* 0x00000012 0xc93c 842 100 0/0/0
0000.0000.0004.00-00 0x00000026 0x331 1173 84 0/0/0
0000.0000.0004.01-00 0x00000001 0xee95 668 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
[RouterD] display isis lsdb
Database information for ISIS(1)
--------------------------------
Level-2 Link State Database
---------------------------
LSPID Seq Num Checksum Holdtime Length ATT/P/OL
--------------------------------------------------------------------------
0000.0000.0003.00-00 0x00000013 0xc73d 1003 100 0/0/0
0000.0000.0004.00-00* 0x0000003c 0xd647 1194 84 0/0/0
0000.0000.0004.01-00* 0x00000002 0xec96 1007 55 0/0/0
*-Self LSP, +-Self LSP(Extended), ATT-Attached, P-Partition, OL-Overload
# Display the IS-IS routing information on each router.
[RouterA] display isis route
Route information for IS-IS(1)
------------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL XGE3/1/1 Direct D/L/-
10.1.2.0/24 20 NULL XGE3/1/1 10.1.1.1 R/-/-
192.168.0.0/24 20 NULL XGE3/1/1 10.1.1.1 R/-/-
0.0.0.0/0 10 NULL XGE3/1/1 10.1.1.1 R/-/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
[RouterC] display isis route
Route information for IS-IS(1)
-----------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL XGE3/1/1 Direct D/L/-
10.1.2.0/24 10 NULL XGE3/1/3 Direct D/L/-
192.168.0.0/24 10 NULL XGE3/1/2 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL D/L/-
10.1.2.0/24 10 NULL D/L/-
192.168.0.0/24 10 NULL D/L/-
172.16.0.0/16 20 NULL XGE3/1/2 192.168.0.2 R/-/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
[RouterD] display isis route
Route information for IS-IS(1)
-----------------------------
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
192.168.0.0/24 10 NULL XGE3/1/2 Direct D/L/-
10.1.1.0/24 20 NULL XGE3/1/2 192.168.0.1 R/-/-
10.1.2.0/24 20 NULL XGE3/1/2 192.168.0.1 R/-/-
172.16.0.0/16 10 NULL XGE3/1/1 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
The output shows that the routing table of Level-1 routers contains a default route with the next hop as the Level-1-2 router. The routing table of Level-2 router contains all Level-1 and Level-2 routes.
Example: Configuring DIS election
Network configuration
As shown in Figure 29, on a broadcast network (Ethernet), Router A, Router B, Router C, and Router D reside in IS-IS Area 10. Router A and Router B are Level-1-2 routers, Router C is a Level-1 router, and Router D is a Level-2 router.
Change the DIS priority of Router A to make it elected as the Level-1-2 DIS router.
Procedure
1. Configure IP addresses for interfaces. (Details not shown.)
2. Enable IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] is-level level-1
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/1] quit
# Configure Router D.
<RouterD> system-view
[RouterD] isis 1
[RouterD-isis-1] network-entity 10.0000.0000.0004.00
[RouterD-isis-1] is-level level-2
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/1] quit
# Display information about IS-IS neighbors of Router A.
[RouterA] display isis peer
Peer information for IS-IS(1)
----------------------------
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0003.01
State: Up HoldTime: 21s Type: L1(L1L2) PRI: 64
System ID: 0000.0000.0003
Interface: XGE3/1/1 Circuit Id: 0000.0000.0003.01
State: Up HoldTime: 6s Type: L1 PRI: 64
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0004.01
State: Up HoldTime: 23s Type: L2(L1L2) PRI: 64
System ID: 0000.0000.0004
Interface: XGE3/1/1 Circuit Id: 0000.0000.0004.01
State: Up HoldTime: 23s Type: L2 PRI: 64
# Display information about IS-IS interfaces of Router A.
[RouterA] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00001 Up Down 1 1497 L1/L2 No/No
# Display IS-IS interfaces of Router C.
[RouterC] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00001 Up Down 1 1497 L1/L2 Yes/No
# Display information about IS-IS interfaces of Router D.
[RouterD] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00001 Up Down 1 1497 L1/L2 No/Yes
The output shows that when the default DIS priority is used, Router C is the DIS for Level-1, and Router D is the DIS for Level-2. The pseudonodes of Level-1 and Level-2 are 0000.0000.0003.01 and 0000.0000.0004.01.
# Configure the DIS priority of Router A.
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis dis-priority 100
# Display information about IS-IS neighbors of Router A.
[RouterA] display isis peer
Peer information for IS-IS(1)
----------------------------
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 29s Type: L1(L1L2) PRI: 64
System ID: 0000.0000.0003
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 22s Type: L1 PRI: 64
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 22s Type: L2(L1L2) PRI: 64
System ID: 0000.0000.0004
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 22s Type: L2 PRI: 64
# Display information about IS-IS interfaces of Router A.
[RouterA] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00001 Up Down 1 1497 L1/L2 Yes/Yes
The output shows that after the DIS priority configuration, Router A becomes the DIS for Level-1-2, and the pseudonode is 0000.0000.0001.01.
# Display information about IS-IS neighbors and interfaces of Router C.
[RouterC] display isis peer
Peer information for IS-IS(1)
----------------------------
System ID: 0000.0000.0001
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 7s Type: L1 PRI: 100
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 23s Type: L1 PRI: 64
[RouterC] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00 1 Up Down 1 1497 L1/L2 No/No
# Display information about IS-IS neighbors and interfaces of Router D.
[RouterD] display isis peer
Peer information for IS-IS(1)
----------------------------
System ID: 0000.0000.0001
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 7s Type: L2 PRI: 100
System ID: 0000.0000.0002
Interface: XGE3/1/1 Circuit Id: 0000.0000.0001.01
State: Up HoldTime: 26s Type: L2 PRI: 64
[RouterD] display isis interface
Interface information for IS-IS(1)
---------------------------------
Interface: Ten-GigabitEthernet3/1/1
Index IPv4 state IPv6 state Circuit ID MTU Type DIS
00001 Up Down 1 1497 L1/L2 No/No
Example: Configuring IS-IS route redistribution
Network configuration
As shown in Figure 30, Router A, Router B, Router C, and Router D reside in the same AS. They use IS-IS to interconnect. Router A and Router B are Level-1 routers, Router D is a Level-2 router, and Router C is a Level-1-2 router.
Redistribute RIP routes into IS-IS on Router D.
Procedure
1. Configure IP addresses for interfaces. (Details not shown.)
2. Configure basic IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] is-level level-1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] is-level level-1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/2] quit
[RouterC] interface ten-gigabitethernet 3/1/3
[RouterC-Ten-GigabitEthernet3/1/3] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/3] quit
# Configure Router D.
<RouterD> system-view
[RouterD] isis 1
[RouterD-isis-1] is-level level-2
[RouterD-isis-1] network-entity 20.0000.0000.0004.00
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/1] quit
[RouterD] interface ten-gigabitethernet 3/1/2
[RouterD-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/2] quit
# Display IS-IS routing information on each router.
[RouterA] display isis route
Route information for IS-IS(1)
------------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL XGE3/1/1 Direct D/L/-
10.1.2.0/24 20 NULL XGE3/1/1 10.1.1.1 R/-/-
192.168.0.0/24 20 NULL XGE3/1/1 10.1.1.1 R/-/-
0.0.0.0/0 10 NULL XGE3/1/1 10.1.1.1 R/-/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
[RouterC] display isis route
Route information for IS-IS(1)
-----------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL XGE3/1/1 Direct D/L/-
10.1.2.0/24 10 NULL XGE3/1/3 Direct D/L/-
192.168.0.0/24 10 NULL XGE3/1/2 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL D/L/-
10.1.2.0/24 10 NULL D/L/-
10.1.4.0/24 10 NULL D/L/-
192.168.0.0/24 10 NULL D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
[RouterD] display isis route
Route information for IS-IS(1)
-----------------------------
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 20 NULL XGE3/1/2 192.168.0.1 R/-/-
10.1.2.0/24 20 NULL XGE3/1/2 192.168.0.1 R/-/-
10.1.4.0/24 10 NULL XGE3/1/1 Direct D/L/-
192.168.0.0/24 10 NULL XGE3/1/2 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
3. Configure RIPv2 on Router D and Router E, and configure IS-IS to redistribute RIP routes on Router D:
# Configure RIPv2 on Router D.
[RouterD] rip 1
[RouterD-rip-1] network 10.0.0.0
[RouterD-rip-1] version 2
[RouterD-rip-1] undo summary
# Configure RIPv2 on Router E.
[RouterE] rip 1
[RouterE-rip-1] network 10.0.0.0
[RouterE-rip-1] version 2
[RouterE-rip-1] undo summary
# On Router D, configure IS-IS to redistribute routes from RIP.
[RouterD-rip-1] quit
[RouterD] isis 1
[RouterD–isis-1] address-family ipv4
[RouterD–isis-1-ipv4] import-route rip level-2
# Display IS-IS routing information on Router C.
[RouterC] display isis route
Route information for IS-IS(1)
-----------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL XGE3/1/1 Direct D/L/-
10.1.2.0/24 10 NULL XGE3/1/3 Direct D/L/-
192.168.0.0/24 10 NULL XGE3/1/2 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
10.1.1.0/24 10 NULL D/L/-
10.1.2.0/24 10 NULL D/L/-
192.168.0.0/24 10 NULL D/L/-
10.1.4.0/24 20 NULL XGE3/1/2 192.168.0.2 R/L/-
10.1.5.0/24 10 0 XGE3/1/2 192.168.0.2 R/L/-
10.1.6.0/24 10 0 XGE3/1/2 192.168.0.2 R/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Example: Configuring IS-IS authentication
Network configuration
As shown in Figure 31, Router A, Router B, Router C, and Router D reside in the same IS-IS routing domain.
Router A, Router B, and Router C belong to Area 10, and Router D belongs to Area 20.
· Configure neighbor relationship authentication between neighbors.
· Configure area authentication in Area 10 to prevent untrusted routes from entering into the area.
· Configure routing domain authentication on Router C and Router D to prevent untrusted routes from entering the routing domain.
Procedure
1. Configure IP addresses for interfaces. (Details not shown.)
2. Configure basic IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] is-level level-1
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] is-level level-1
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/2] quit
[RouterC] interface ten-gigabitethernet 3/1/3
[RouterC-Ten-GigabitEthernet3/1/3] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/3] quit
# Configure Router D.
<RouterD> system-view
[RouterD] isis 1
[RouterD-isis-1] network-entity 20.0000.0000.0001.00
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/1] quit
3. Configure neighbor relationship authentication between neighbors:
# Set the authentication mode to MD5 and set the plaintext key to eRq on Ten-GigabitEthernet 3/1/1 of Router A and on Ten-GigabitEthernet 3/1/3 of Router C.
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis authentication-mode md5 plain eRg
[RouterA-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/3
[RouterC-Ten-GigabitEthernet3/1/3] isis authentication-mode md5 plain eRg
[RouterC-Ten-GigabitEthernet3/1/3] quit
# Set the authentication mode to MD5 and set the plaintext key to t5Hr on Ten-GigabitEthernet 3/1/1 of Router B and on Ten-GigabitEthernet 3/1/1 of Router C.
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis authentication-mode md5 plain t5Hr
[RouterB-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis authentication-mode md5 plain t5Hr
[RouterC-Ten-GigabitEthernet3/1/1] quit
# Set the authentication mode to MD5 and set the plaintext key to hSec on Ten-GigabitEthernet 3/1/1 of Router D and on Ten-GigabitEthernet 3/1/2 of Router C.
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis authentication-mode md5 plain hSec
[RouterC-Ten-GigabitEthernet3/1/2] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis authentication-mode md5 plain hSec
[RouterD-Ten-GigabitEthernet3/1/1] quit
4. Set the area authentication mode to MD5 and set the plaintext key to 10Sec on Router A, Router B, and Router C.
[RouterA] isis 1
[RouterA-isis-1] area-authentication-mode md5 plain 10Sec
[RouterA-isis-1] quit
[RouterB] isis 1
[RouterB-isis-1] area-authentication-mode md5 plain 10Sec
[RouterB-isis-1] quit
[RouterC] isis 1
[RouterC-isis-1] area-authentication-mode md5 plain 10Sec
[RouterC-isis-1] quit
5. Set routing domain authentication mode to MD5 and set the plaintext key to 1020Sec on Router C and Router D.
[RouterC] isis 1
[RouterC-isis-1] domain-authentication-mode md5 plain 1020Sec
[RouterC-isis-1] quit
[RouterD] isis 1
[RouterD-isis-1] domain-authentication-mode md5 plain 1020Sec
[RouterD-isis-1] quit
Example: Configuring IS-IS GR
Network configuration
As shown in Figure 32, Router A, Router B, and Router C belong to the same IS-IS routing domain. Run IS-IS on all the routers to interconnect them with each other.
Procedure
1. Configure the IP addresses and subnet masks for interfaces on the routers. (Details not shown.)
2. Configure IS-IS on the routers to make sure Router A, Router B, and Router C can communicate with each other at Layer 3 and dynamic route update can be implemented among them with IS-IS. (Details not shown.)
3. Enable IS-IS GR on Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] graceful-restart
[RouterA-isis-1] quit
[RouterA] quit
Verifying the configuration
# Restart the IS-IS process on Router A.
<RouterA> reset isis all 1 graceful-restart
Reset IS-IS process? [Y/N]:y
# Check the GR state of the IS-IS process on Router A.
<RouterA> display isis graceful-restart status
Restart information for IS-IS(1)
--------------------------------
Restart status: COMPLETE
Restart phase: Finish
Restart t1: 3, count 10; Restart t2: 60; Restart t3: 300
SA Bit: supported
Level-1 restart information
---------------------------
Total number of interfaces: 1
Number of waiting LSPs: 0
Level-2 restart information
---------------------------
Total number of interfaces: 1
Number of waiting LSPs: 0
Example: Configuring BFD for IS-IS
Network configuration
· As shown in Figure 33, run IS-IS on Router A, Router B and Router C so that they can reach each other at the network layer.
· After the link over which Router A and Router B communicate through the Layer 2 switch fails, BFD can quickly detect the failure and notify IS-IS of the failure. Router A and Router B then communicate through Router C.
Table 5 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Router A |
XGE3/1/1 |
192.168.0.102/24 |
Router B |
XGE3/1/1 |
192.168.0.100/24 |
|
|
XGE3/1/2 |
10.1.1.102/24 |
|
XGE3/1/2 |
13.1.1.1/24 |
|
|
Loop0 |
121.1.1.1/32 |
|
Loop0 |
120.1.1.1/32 |
|
Router C |
XGE3/1/1 |
10.1.1.100/24 |
|
|
|
|
|
XGE3/1/2 |
13.1.1.2/24 |
|
|
|
Procedure
1. Configure IP addresses for interfaces. (Details not shown.)
2. Configure basic IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface loopback 0
[RouterA-LoopBack0] isis enable
[RouterA-LoopBack0] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable
[RouterA-Ten-GigabitEthernet3/1/1] quit
[RouterA] interface ten-gigabitethernet 3/1/2
[RouterA-Ten-GigabitEthernet3/1/2] isis enable
[RouterA-Ten-GigabitEthernet3/1/2] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface loopback 0
[RouterB-LoopBack0] isis enable
[RouterB-LoopBack0] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable
[RouterB-Ten-GigabitEthernet3/1/1] quit
[RouterB] interface ten-gigabitethernet 3/1/2
[RouterB-Ten-GigabitEthernet3/1/2] isis enable
[RouterB-Ten-GigabitEthernet3/1/2] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis enable
[RouterC-Ten-GigabitEthernet3/1/2] quit
3. Configure BFD functions:
# Enable BFD and configure BFD parameters on Router A.
[RouterA] bfd session init-mode active
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis bfd enable
[RouterA-Ten-GigabitEthernet3/1/1] bfd min-receive-interval 500
[RouterA-Ten-GigabitEthernet3/1/1] bfd min-transmit-interval 500
[RouterA-Ten-GigabitEthernet3/1/1] bfd detect-multiplier 7
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Enable BFD and configure BFD parameters on Router B.
[RouterB] bfd session init-mode active
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis bfd enable
[RouterB-Ten-GigabitEthernet3/1/1] bfd min-receive-interval 500
[RouterB-Ten-GigabitEthernet3/1/1] bfd min-transmit-interval 500
[RouterB-Ten-GigabitEthernet3/1/1] bfd detect-multiplier 8
[RouterB-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Display the BFD session information on Router A.
[RouterA] display bfd session
Total sessions: 1 Up sessions: 1 Init mode: Active
IPv4 session working in control packet mode:
LD/RD SourceAddr DestAddr State Holdtime Interface
3/1 192.168.0.102 192.168.0.100 Up 1700ms XGE3/1/1
# Display routes destined for 120.1.1.1/32 on Router A.
[RouterA] display ip routing-table 120.1.1.1 verbose
Summary count : 1
Destination: 120.1.1.1/32
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
FlushedAge: 15h28m49s
Cost: 10 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 192.168.0.100
Label: NULL RealNextHop: 192.168.0.100
BkLabel: NULL BkNextHop: N/A
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/1
BkSRLabel: NULL BkInterface: N/A
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/1
BkTunnel ID: Invalid BkIPInterface: N/A
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
The output shows that Router A and Router B communicate through Ethernet 1/1. Then the link over Ethernet 1/1 fails.
# Display routes destined for 120.1.1.1/32 on Router A.
[RouterA] display ip routing-table 120.1.1.1 verbose
Summary count : 1
Destination: 120.1.1.1/32
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
FlushedAge: 15h28m49s
Cost: 20 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 10.1.1.100
Label: NULL RealNextHop: 10.1.1.100
BkLabel: NULL BkNextHop: N/A
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/2
BkSRLabel: NULL BkInterface: N/A
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/2
BkTunnel ID: Invalid BkIPInterface: N/A
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
The output shows that Router A and Router B communicate through Ethernet 1/2.
Example: Configuring IS-IS LFA FRR
Network configuration
As shown in Figure 34, Router A, Router B, and Router C reside in the same IS-IS routing domain.
· Run IS-IS on all the routers to interconnect them with each other.
· Configure IS-IS FRR so that when Link A fails, traffic can be switched to Link B immediately.
Table 6 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Router A |
XGE3/1/1 |
12.12.12.1/24 |
Router B |
XGE3/1/1 |
24.24.24.4/24 |
|
|
XGE3/1/2 |
13.13.13.1/24 |
|
XGE3/1/2 |
13.13.13.2/24 |
|
|
Loop0 |
1.1.1.1/32 |
|
Loop0 |
4.4.4.4/32 |
|
Router C |
XGE3/1/1 |
12.12.12.2/24 |
|
|
|
|
|
XGE3/1/2 |
24.24.24.2/24 |
|
|
|
Procedure
1. Configure IP addresses and subnet masks for interfaces on the routers. (Details not shown.)
2. Configure IS-IS on the routers to make sure Router A, Router B, and Router C can communicate with each other at the network layer. (Details not shown.)
3. Configure IS-IS FRR:
Enable IS-IS FRR to calculate a backup next hop through LFA calculation, or designate a backup next hop by using a routing policy.
¡ (Method 1.) Enable IS-IS FRR to calculate a backup next hop through LFA calculation:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] address-family ipv4
[RouterA-isis-1-ipv4] fast-reroute lfa
[RouterA-isis-1-ipv4] quit
[RouterA-isis-1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] address-family ipv4
[RouterB-isis-1-ipv4] fast-reroute lfa
[RouterB-isis-1-ipv4] quit
[RouterB-isis-1] quit
¡ (Method 2.) Enable IS-IS FRR to designate a backup next hop by using a routing policy:
# Configure Router A.
<RouterA> system-view
[RouterA] ip prefix-list abc index 10 permit 4.4.4.4 32
[RouterA] route-policy frr permit node 10
[RouterA-route-policy-frr-10] if-match ip address prefix-list abc
[RouterA-route-policy-frr-10] apply fast-reroute backup-interface ten-gigabitethernet 3/1/1 backup-nexthop 12.12.12.2
[RouterA-route-policy-frr-10] quit
[RouterA] isis 1
[RouterA-isis-1] address-family ipv4
[RouterA-isis-1-ipv4] fast-reroute route-policy frr
[RouterA-isis-1-ipv4] quit
[RouterA-isis-1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] ip prefix-list abc index 10 permit 1.1.1.1 32
[RouterB] route-policy frr permit node 10
[RouterB-route-policy-frr-10] if-match ip address prefix-list abc
[RouterB-route-policy-frr-10] apply fast-reroute backup-interface ten-gigabitethernet 3/1/1 backup-nexthop 24.24.24.2
[RouterB-route-policy-frr-10] quit
[RouterB] isis 1
[RouterB-isis-1] address-family ipv4
[RouterB-isis-1-ipv4] fast-reroute route-policy frr
[RouterB-isis-1-ipv4] quit
[RouterB-isis-1] quit
Verifying the configuration
# Display route 4.4.4.4/32 on Router A to view the backup next hop information.
[RouterA] display ip routing-table 4.4.4.4 verbose
Summary count : 1
Destination: 4.4.4.4/32
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
FlushedAge: 15h28m49s
Cost: 10 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 13.13.13.2
Label: NULL RealNextHop: 13.13.13.2
BkLabel: NULL BkNextHop: 12.12.12.2
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/2
BkSRLabel: NULL BkInterface: Ten-GigabitEthernet3/1/1
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/2
BkTunnel ID: Invalid BkIPInterface: Ten-GigabitEthernet3/1/1
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
# Display route 1.1.1.1/32 on Router B to view the backup next hop information.
[RouterB] display ip routing-table 1.1.1.1 verbose
Summary count : 1
Destination: 1.1.1.1/32
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
FlushedAge: 15h28m49s
Cost: 10 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 13.13.13.1
Label: NULL RealNextHop: 13.13.13.1
BkLabel: NULL BkNextHop: 24.24.24.2
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/2
BkSRLabel: NULL BkInterface: Ten-GigabitEthernet3/1/1
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/2
BkTunnel ID: Invalid BkIPInterface: Ten-GigabitEthernet3/1/1
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
Example: Configuring IS-IS remote LFA FRR
Network configuration
As shown in Figure 34, Router A, Router B, Router C, and Router D reside in the same IS-IS routing domain.
· Run IS-IS on all the routers to interconnect them with each other.
· Configure MPLS LDP on all the routers.
· Configure IS-IS remote LFA FRR so that when Link A fails, traffic can be switched to Link B immediately.
Figure 35 Network diagram
Table 7 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Router A |
XGE3/1/1 |
12.12.12.1/24 |
Router B |
XGE3/1/1 |
12.12.12.2/24 |
|
|
XGE3/1/2 |
13.13.13.1/24 |
|
XGE3/1/2 |
15.15.15.1/24 |
|
|
Loop1 |
1.1.1.1/32 |
|
Loop1 |
2.2.2.2/32 |
|
Router C |
XGE3/1/1 |
13.13.13.2/24 |
Router D |
XGE3/1/1 |
15.15.15.2/24 |
|
|
XGE3/1/2 |
14.14.14.1/24 |
|
XGE3/1/2 |
14.14.14.2/24 |
|
|
Loop1 |
3.3.3.3/32 |
|
Loop1 |
4.4.4.4/32 |
Procedure
1. Configure IP addresses and subnet masks for interfaces on the routers. (Details not shown.)
2. Configure IS-IS and MPLS LDP on all the routers:
# Configure Router A.
<RouterA> system-view
[RouterA] mpls lsr-id 1.1.1.1
[RouterA] mpls ldp
[RouterA-ldp] accept target-hello all
[RouterA-ldp] quit
[RouterA] isis 1
[RouterA-isis-1] network-entity 00.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] isis cost 10
[RouterA-Ten-GigabitEthernet3/1/1] mpls enable
[RouterA-Ten-GigabitEthernet3/1/1] mpls ldp enable
[RouterA-Ten-GigabitEthernet3/1/1] quit
[RouterA] interface ten-gigabitethernet 3/1/2
[RouterA-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/2] isis cost 20
[RouterA-Ten-GigabitEthernet3/1/2] mpls enable
[RouterA-Ten-GigabitEthernet3/1/2] mpls ldp enable
[RouterA-Ten-GigabitEthernet3/1/2] quit
[RouterA] interface loopback 1
[RouterA-LoopBack1] isis enable 1
[RouterA-LoopBack1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] mpls lsr-id 2.2.2.2
[RouterB] mpls ldp
[RouterB-ldp] accept target-hello all
[RouterB-ldp] quit
[RouterB] isis 1
[RouterB-isis-1] network-entity 00.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] isis cost 10
[RouterB-Ten-GigabitEthernet3/1/1] mpls enable
[RouterB-Ten-GigabitEthernet3/1/1] mpls ldp enable
[RouterB-Ten-GigabitEthernet3/1/1] quit
[RouterB] interface ten-gigabitethernet 3/1/2
[RouterB-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/2] isis cost 20
[RouterB-Ten-GigabitEthernet3/1/2] mpls enable
[RouterB-Ten-GigabitEthernet3/1/2] mpls ldp enable
[RouterB-Ten-GigabitEthernet3/1/2] quit
[RouterB] interface loopback 1
[RouterB-LoopBack1] isis enable 1
[RouterB-LoopBack1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] mpls lsr-id 3.3.3.3
[RouterC] mpls ldp
[RouterC-ldp] accept target-hello all
[RouterC-ldp] quit
[RouterC] isis 1
[RouterC-isis-1] network-entity 00.0000.0000.0003.00
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/1] isis cost 20
[RouterC-Ten-GigabitEthernet3/1/1] mpls enable
[RouterC-Ten-GigabitEthernet3/1/1] mpls ldp enable
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterC-Ten-GigabitEthernet3/1/2] isis cost 20
[RouterC-Ten-GigabitEthernet3/1/2] mpls enable
[RouterC-Ten-GigabitEthernet3/1/2] mpls ldp enable
[RouterC-Ten-GigabitEthernet3/1/2] quit
[RouterC] interface loopback 1
[RouterC-LoopBack1] isis enable 1
[RouterC-LoopBack1] quit
# Configure Router D.
<RouterD> system-view
[RouterD] mpls lsr-id 4.4.4.4
[RouterD] mpls ldp
[RouterD-ldp] accept target-hello all
[RouterD-ldp] quit
[RouterD] isis 1
[RouterD-isis-1] network-entity 00.0000.0000.0004.00
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/1] isis cost 20
[RouterD-Ten-GigabitEthernet3/1/1] mpls enable
[RouterD-Ten-GigabitEthernet3/1/1] mpls ldp enable
[RouterD-Ten-GigabitEthernet3/1/1] quit
[RouterD] interface ten-gigabitethernet 3/1/2
[RouterD-Ten-GigabitEthernet3/1/2] isis enable 1
[RouterD-Ten-GigabitEthernet3/1/2] isis cost 20
[RouterD-Ten-GigabitEthernet3/1/2] mpls enable
[RouterD-Ten-GigabitEthernet3/1/2] mpls ldp enable
[RouterD-Ten-GigabitEthernet3/1/2] quit
[RouterD] interface loopback 1
[RouterD-LoopBack1] isis enable 1
[RouterD-LoopBack1] quit
3. Configure IS-IS remote LFA FRR.
[RouterA] isis 1
[RouterA-isis-1] address-family ipv4
[RouterA-isis-1-ipv4] fast-reroute lfa
[RouterA-isis-1-ipv4] fast-reroute remote-lfa tunnel ldp
[RouterA-isis-1-ipv4] quit
[RouterA-isis-1] quit
Verifying the configuration
# Display route 2.2.2.2/32 on Router A to view the backup next hop information.
[RouterA] display isis route ipv4 2.2.2.2 32 verbose
Route information for IS-IS(1)
------------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Dest : 2.2.2.2/32 Int. Cost : 10 Ext. Cost : NULL
Admin Tag : - Src Count : 1 Flag : R/L/-
InLabel : 4294967295 InLabel Flag: -/-/-/-/-/-
NextHop : Interface : ExitIndex :
12.12.12.2 XGE3/1/1 0x00000002
Nib ID : 0x14000008 OutLabel : 4294967295 OutLabelFlag: -
LabelSrc : N/A Delay Flag : N/A
Remote-LFA:
Interface : XGE3/1/2
BkNextHop : 13.13.13.2 LsIndex : 0x01000002
Tunnel destination address: 4.4.4.4
Backup label: {1149}
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
InLabel flags: R-Readvertisement, N-Node SID, P-no PHP
E-Explicit null, V-Value, L-Local
OutLabelFlags: E-Explicit null, I-Implicit null, N-Nomal, P-SR label prefer
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Dest : 2.2.2.2/32 Int. Cost : 10 Ext. Cost : NULL
Admin Tag : - Src Count : 3 Flag : -/-/-
InLabel : 4294967295 InLabel Flag: -/-/-/-/-/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
InLabel flags: R-Readvertisement, N-Node SID, P-no PHP
E-Explicit null, V-Value, L-Local
OutLabelFlags: E-Explicit null, I-Implicit null, N-Nomal, P-SR label prefer
Example: Configuring IS-IS multi-instance processes
Network configuration
As shown in Figure 36, the IPv4 and IPv6 costs are different on an interface. Configure IS-IS multi-instance processes to isolate the IPv4 and IPv6 network and avoid IPv6 route calculation errors.
Table 8 Interface and IP address assignment
|
Device |
Interface |
IPv4 address |
IPv6 address |
|
Router A |
XGE3/1/1 |
10.1.1.1/24 |
2001::1/64 |
|
|
Loop0 |
1.1.1.1/32 |
10::1/128 |
|
Router C |
XGE3/1/1 |
10.1.1.2/24 |
2001::2/64 |
|
|
Loop0 |
2.2.2.2/32 |
20::1/128 |
Prerequisites
Configure IPv4 and IPv6 addresses for the interfaces. (Details not shown.)
Procedure
1. Configure traditional IPv4 IS-IS processes:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] quit
[RouterA] interface loopback 0
[RouterA-LoopBack0] isis enable
[RouterA-LoopBack0] quit
[RouterA] interface loopback 0
[RouterA-LoopBack0] isis ipv6 enable 2
[RouterA-LoopBack0] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] quit
[RouterB] interface loopback 0
[RouterB-LoopBack0] isis enable
[RouterB-LoopBack0] quit
[RouterB] interface loopback 0
[RouterB-LoopBack0] isis ipv6 enable 2
[RouterB-LoopBack0] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
2. Configure IPv6 IS-IS multi-instance processes:
# Configure Router A.
[RouterA] isis 2
[RouterA-isis-2] network-entity 20.0000.0000.0010.00
[RouterA-isis-2] multi-instance enable iid 1
[RouterA-isis-2] address-family ipv6
[RouterA-isis-2-ipv6] quit
[RouterA-isis-2] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis ipv6 enable 2
[RouterA-Ten-GigabitEthernet3/1/1] isis process-id 2 cost 63
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
[RouterB] isis 2
[RouterB-isis-2] network-entity 20.0000.0000.0020.00
[RouterB-isis-2] multi-instance enable iid 1
[RouterB-isis-2] address-family ipv6
[RouterB-isis-2-ipv6] quit
[RouterB-isis-2] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis ipv6 enable 2
[RouterB-Ten-GigabitEthernet3/1/1] isis process-id 2 cost 63
[RouterB-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# View information about the IPv4 IS-IS routing table of Router A.
[RouterA] display isis route ipv4
Route information for IS-IS(1)
------------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
1.1.1.1/32 0 NULL Loop0 Direct D/L/-
10.1.1.0/24 10 NULL GE1/0/1 Direct D/L/-
2.2.2.2/32 10 NULL GE1/0/1 10.1.1.2 R/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
1.1.1.1/32 0 NULL Loop0 Direct D/L/-
10.1.1.0/24 10 NULL ULL Direct D/L/-
2.2.2.2/32 10 NULL
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
The output shows that route calculation results are correct.
# View information about the IPv4 IS-IS routing table of Router B.
[RouterB] display isis route ipv4
Route information for IS-IS(1)
------------------------------
Level-1 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
1.1.1.1/32 10 NULL GE1/0/1 10.1.1.1 R/L/-
10.1.1.0/24 10 NULL GE1/0/1 Direct D/L/-
2.2.2.2/32 0 NULL Loop0 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv4 Forwarding Table
-----------------------------
IPv4 Destination IntCost ExtCost ExitInterface NextHop Flags
-------------------------------------------------------------------------------
1.1.1.1/32 10 NULL
10.1.1.0/24 10 NULL GE1/0/1 Direct D/L/-
2.2.2.2/32 0 NULL Loop0 Direct D/L/-
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
The output shows that route calculation results are correct.
# View information about the IPv6 IS-IS routing table of Router A.
[RouterA] display isis route ipv6
Route information for IS-IS(2)
------------------------------
Level-1 IPv6 forwarding table
-----------------------------
Destination : 10::1 PrefixLen: 128
Flag : D/L/- Cost : 0
Next hop : Direct Interface: Loop0
Destination : 2001:: PrefixLen: 64
Flag : D/L/- Cost : 63
Next hop : Direct Interface: GE1/0/1
Destination : 20::1 PrefixLen: 128
Flag : R/L/- Cost : 63
Next hop : FE80::861F:31FF:FE6D:201 Interface: GE1/0/1
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv6 forwarding table
-----------------------------
Destination : 10::1 PrefixLen: 128
Flag : D/L/- Cost : 0
Next hop : Direct Interface: Loop0
Destination : 2001:: PrefixLen: 64
Flag : D/L/- Cost : 63
Next hop : Direct Interface: GE1/0/1
Destination : 20::1 PrefixLen: 128
Flag : -/-/- Cost : 63
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
The output shows that route calculation results are correct.
# View information about the IPv6 IS-IS routing table of Router B.
[RouterB] display isis route ipv6
Route information for IS-IS(2)
------------------------------
Level-1 IPv6 forwarding table
-----------------------------
Destination : 10::1 PrefixLen: 128
Flag : R/L/- Cost : 63
Next hop : FE80::861F:29FF:FE93:101 Interface: GE1/0/1
Destination : 2001:: PrefixLen: 64
Flag : D/L/- Cost : 63
Next hop : Direct Interface: GE1/0/1
Destination : 20::1 PrefixLen: 128
Flag : D/L/- Cost : 0
Next hop : Direct Interface: Loop0
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv6 forwarding table
-----------------------------
Destination : 10::1 PrefixLen: 128
Flag : -/-/- Cost : 63
Destination : 2001:: PrefixLen: 64
Flag : D/L/- Cost : 63
Next hop : Direct Interface: GE1/0/1
Destination : 20::1 PrefixLen: 128
Flag : D/L/- Cost : 0
Next hop : Direct Interface: Loop0
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
The output shows that route calculation results are correct.
IPv6 IS-IS configuration examples
Example: Configuring IPv6 IS-IS basics
Network configuration
As shown in Figure 37, Router A, Router B, Router C, and Router D, all enabled with IPv6, reside in the same AS. Configure IPv6 IS-IS on the routers so that they can reach each other.
Router A and Router B are Level-1 routers, Router D is a Level-2 router, and Router C is a Level-1-2 router.
Procedure
1. Configure IPv6 addresses for interfaces. (Details not shown.)
2. Configure IPv6 IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] is-level level-1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] address-family ipv6
[RouterA-isis-1-ipv6] quit
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] is-level level-1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] address-family ipv6
[RouterB-isis-1-ipv6] quit
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] address-family ipv6
[RouterC-isis-1-ipv6] quit
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterC-Ten-GigabitEthernet3/1/1] quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[RouterC-Ten-GigabitEthernet3/1/2] quit
[RouterC] interface ten-gigabitethernet 3/1/3
[RouterC-Ten-GigabitEthernet3/1/3] isis ipv6 enable 1
[RouterC-Ten-GigabitEthernet3/1/3] quit
# Configure Router D.
<RouterD> system-view
[RouterD] isis 1
[RouterD-isis-1] is-level level-2
[RouterD-isis-1] network-entity 20.0000.0000.0004.00
[RouterD-isis-1] address-family ipv6
[RouterD-isis-1-ipv6] quit
[RouterD-isis-1] quit
[RouterD] interface ten-gigabitethernet 3/1/1
[RouterD-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterD-Ten-GigabitEthernet3/1/1] quit
[RouterD] interface ten-gigabitethernet 3/1/2
[RouterD-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[RouterD-Ten-GigabitEthernet3/1/2] quit
Verifying the configuration
# Display the IPv6 IS-IS routing table on Router A.
[RouterA] display isis route ipv6
Route information for IS-IS(1)
------------------------------
Level-1 IPv6 forwarding table
-----------------------------
Destination : :: PrefixLen: 0
Flag : R/-/- Cost : 10
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:1:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : Direct Interface: XGE3/1/1
Destination : 2001:2:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:3:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
# Display the IPv6 IS-IS routing table on Router B.
[RouterB] display isis route ipv6
Route information for IS-IS(1)
------------------------------
Level-1 IPv6 forwarding table
-----------------------------
Destination : :: PrefixLen: 0
Flag : R/-/- Cost : 10
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:1:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:2:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : Direct Interface: XGE3/1/1
Destination : 2001:3:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
# Display the IPv6 IS-IS routing table on Router C.
[RouterC] display isis route ipv6
Route information for IS-IS(1)
------------------------------
Level-1 IPv6 forwarding table
-----------------------------
Destination : 2001:1:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : Direct Interface: XGE3/1/2
Destination : 2001:2:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : Direct Interface: XGE3/1/1
Destination : 2001:3:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : Direct Interface: XGE3/1/3
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Level-2 IPv6 forwarding table
-----------------------------
Destination : 2001:1:: PrefixLen: 64
Flag : D/L/- Cost : 10
Destination : 2001:2:: PrefixLen: 64
Flag : D/L/- Cost : 10
Destination : 2001:3:: PrefixLen: 64
Flag : D/L/- Cost : 10
Destination : 2001:4:: PrefixLen: 64
Flag : R/-/- Cost : 10
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
# Display the IPv6 IS-IS routing table on Router D.
[RouterD] display isis route ipv6
Route information for IS-IS(1)
------------------------------
Level-2 IPv6 forwarding table
-----------------------------
Destination : 2001:1:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:2:: PrefixLen: 64
Flag : R/-/- Cost : 20
Next hop : FE80::200:FF:FE0F:4 Interface: XGE3/1/1
Destination : 2001:3:: PrefixLen: 64
Flag : D/L/- Cost : 10
Next hop : Direct Interface: XGE3/1/1
Destination : 2001:4:: PrefixLen: 64
Flag : D/L/- Cost : 0
Next hop : Direct Interface: XGE3/1/2
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
Example: Configuring BFD for IPv6 IS-IS
Network configuration
As shown in Figure 38:
· Configure IPv6 IS-IS on Router A, Router B, and Router C so that they can reach each other.
· Enable BFD on Ten-GigabitEthernet 3/1/1 of Router A and Router B.
When the link between Router B and the Layer 2 switch fails, BFD can quickly detect the failure and notify IPv6 IS-IS of the failure. Then Router A and Router B communicate through Router C.
Table 9 Interface and IP address assignment
|
Device |
Interface |
IPv6 address |
Device |
Interface |
IPv6 address |
|
Router A |
XGE3/1/1 |
2001::1/64 |
Router B |
XGE3/1/1 |
2001::2/64 |
|
|
XGE3/1/2 |
2001:2::1/64 |
|
XGE3/1/2 |
2001:3::2/64 |
|
Router C |
XGE3/1/1 |
2001:2::2/64 |
|
|
|
|
|
XGE3/1/2 |
2001:3::1/64 |
|
|
|
Procedure
1. Configure IPv6 addresses for interfaces. (Details not shown.)
2. Configure IPv6 IS-IS:
# Configure Router A.
<RouterA> system-view
[RouterA] isis 1
[RouterA-isis-1] is-level level-1
[RouterA-isis-1] network-entity 10.0000.0000.0001.00
[RouterA-isis-1] address-family ipv6
[RouterA-isis-1-ipv6] quit
[RouterA-isis-1] quit
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterA-Ten-GigabitEthernet3/1/1] quit
[RouterA] interface ten-gigabitethernet 3/1/2
[RouterA-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[RouterA-Ten-GigabitEthernet3/1/2] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] is-level level-1
[RouterB-isis-1] network-entity 10.0000.0000.0002.00
[RouterB-isis-1] address-family ipv6
[RouterB-isis-1-ipv6] quit
[RouterB-isis-1] quit
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterB-Ten-GigabitEthernet3/1/1] quit
[RouterB] interface ten-gigabitethernet 3/1/2
[RouterB-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[RouterB-Ten-GigabitEthernet3/1/2] quit
# Configure Router C.
<RouterC> system-view
[RouterC] isis 1
[RouterC-isis-1] network-entity 10.0000.0000.0003.00
[RouterC-isis-1] address-family ipv6
[RouterC-isis-1-ipv6] quit
[RouterC-isis-1] quit
[RouterC] interface ten-gigabitethernet 3/1/1
[RouterC-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[RouterC-Ten-GigabitEthernet3/1/1 quit
[RouterC] interface ten-gigabitethernet 3/1/2
[RouterC-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[RouterC-Ten-GigabitEthernet3/1/2] quit
3. Configure BFD functions:
# Enable BFD and configure BFD parameters on Router A.
[RouterA] bfd session init-mode active
[RouterA] interface ten-gigabitethernet 3/1/1
[RouterA-Ten-GigabitEthernet3/1/1] isis ipv6 bfd enable
[RouterA-Ten-GigabitEthernet3/1/1] bfd min-transmit-interval 500
[RouterA-Ten-GigabitEthernet3/1/1] bfd min-receive-interval 500
[RouterA-Ten-GigabitEthernet3/1/1] bfd detect-multiplier 7
[RouterA-Ten-GigabitEthernet3/1/1] quit
# Enable BFD and configure BFD parameters on Router B.
[RouterB] bfd session init-mode active
[RouterB] interface ten-gigabitethernet 3/1/1
[RouterB-Ten-GigabitEthernet3/1/1] isis ipv6 bfd enable
[RouterB-Ten-GigabitEthernet3/1/1] bfd min-transmit-interval 500
[RouterB-Ten-GigabitEthernet3/1/1] bfd min-receive-interval 500
[RouterB-Ten-GigabitEthernet3/1/1] bfd detect-multiplier 6
[RouterB-Ten-GigabitEthernet3/1/1] quit
Verifying the configuration
# Display BFD session information on Router A.
[RouterA] display bfd session
Total sessions: 1 Up sessions: 1 Init mode: Active
IPv6 session working in control packet mode:
Local discr: 1441 Remote discr: 1450
Source IP: FE80::20F:FF:FE00:1202 (link-local address of Ten-GigabitEthernet3/1/1 on Router A)
Destination IP: FE80::20F:FF:FE00:1200 (link-local address of Ten-GigabitEthernet3/1/1 on Router B)
Session state: Up Interface: XGE3/1/1
Hold time: 2319ms
# Display routes destined for 2001:4::0/64 on Router A.
[RouterA] display ipv6 routing-table 2001:4::0 64
Summary count : 2
Destination: 2001:4::/64 Protocol : IS_L1
NextHop : FE80::20F:FF:FE00:1200 Preference: 15
Interface : XGE3/1/1 Cost : 10
The output shows that Router A and Router B communicate through Ten-GigabitEthernet 3/1/1. Then the link over Ten-GigabitEthernet 3/1/1 fails.
# Display routes destined for 2001:4::0/64 on Router A.
[RouterA] display ipv6 routing-table 2001:4::0 64
Summary count : 1
Destination: 2001:4::/64 Protocol : IS_L1
NextHop : FE80::BAAF:67FF:FE27:DCD0 Preference: 15
Interface : XGE3/1/2 Cost : 20
The output shows that Router A and Router B communicate through Ten-GigabitEthernet 3/1/2.
Example: Configuring IPv6 IS-IS FRR
Network configuration
As shown in Figure 39, Router A, Router B, and Router C reside in the same IS-IS routing domain.
· Run IPv6 IS-IS on all the routers to interconnect them with each other.
· Configure IPv6 IS-IS FRR so that when Link A fails, traffic can be switched to Link B immediately.
Table 10 Interface and IP address assignment
|
Device |
Interface |
IPv6 address |
Device |
Interface |
IP address |
|
Router A |
XGE3/1/1 |
1::1/64 |
Router B |
XGE3/1/1 |
3::1/64 |
|
|
XGE3/1/2 |
2::1/64 |
|
XGE3/1/2 |
2::2/64 |
|
|
Loop0 |
10::1/128 |
|
Loop0 |
20::1/128 |
|
Router C |
XGE3/1/1 |
1::2/64 |
|
|
|
|
|
XGE3/1/2 |
3::2/64 |
|
|
|
Procedure
1. Configure IPv6 addresses for interfaces on the routers and enable IPv6 IS-IS. (Details not shown.)
2. Configure IPv6 IS-IS FRR:
Enable IPv6 IS-IS FRR to calculate a backup next hop through LFA calculation, or designate a backup next hop by using a routing policy.
¡ (Method 1.) Enable IPv6 IS-IS FRR to calculate a backup next hop through LFA calculation:
# Configure Router A.
<RouterA>system-view
[RouterA] isis 1
[RouterA-isis-1] address-family ipv6
[RouterA-isis-1-ipv6] fast-reroute lfa
[RouterA-isis-1-ipv6] quit
[RouterA-isis-1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] isis 1
[RouterB-isis-1] address-family ipv6
[RouterB-isis-1-ipv6] fast-reroute lfa
[RouterB-isis-1-ipv6] quit
[RouterB-isis-1] quit
¡ (Method 2.) Enable IPv6 IS-IS FRR to designate a backup next hop by using a routing policy:
# Configure Router A.
<RouterA> system-view
[RouterA] ipv6 prefix-list abc index 10 permit 20::1 128
[RouterA] route-policy frr permit node 10
[RouterA-route-policy-frr-10] if-match ipv6 address prefix-list abc
[RouterA-route-policy-frr-10] apply ipv6 fast-reroute backup-interface ten-gigabitethernet 3/1/1 backup-nexthop 1::2
[RouterA-route-policy-frr-10] quit
[RouterA] isis 1
[RouterA-isis-1] address-family ipv6
[RouterA-isis-1-ipv6] fast-reroute route-policy frr
[RouterA-isis-1-ipv6] quit
[RouterA-isis-1] quit
# Configure Router B.
<RouterB> system-view
[RouterB] ipv6 prefix-list abc index 10 permit 10::1 128
[RouterB] route-policy frr permit node 10
[RouterB-route-policy-frr-10] if-match ipv6 address prefix-list abc
[RouterB-route-policy-frr-10] apply ipv6 fast-reroute backup-interface ten-gigabitethernet 3/1/1 backup-nexthop 3::2
[RouterB-route-policy-frr-10] quit
[RouterB] isis 1
[RouterB-isis-1] address-family ipv6
[RouterB-isis-1-ipv6] fast-reroute route-policy frr
[RouterB-isis-1-ipv6] quit
[RouterB-isis-1] quit
Verifying the configuration
# Display route 20::1/128 on Router A to view the backup next hop information.
[RouterA] display ipv6 routing-table 20::1 128 verbose
Summary count : 1
Destination: 20::1/128
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 00h27m45s
FlushedAge: 15h28m49s
Cost: 10 Preference: 15
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0xa OrigVrf: default-vrf
TableID: 0xa OrigAs: 0
NibID: 0x24000005 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: ::
Flags: 0x10041 OrigNextHop: FE80::34CD:9FF:FE2F:D02
Label: NULL RealNextHop: FE80::34CD:9FF:FE2F:D02
BkLabel: NULL BkNextHop: FE80::7685:45FF:FEAD:102
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/2
BkSRLabel: NULL BkInterface: Ten-GigabitEthernet3/1/1
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/2
BkTunnel ID: Invalid BkIPInterface: Ten-GigabitEthernet3/1/1
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
# Display route 10::1/128 on Router B to view the backup next hop information.
[RouterB] display ipv6 routing-table 10::1 128 verbose
Summary count : 1
Destination: 10::1/128
Protocol: IS_L1
Process ID: 1
SubProtID: 0x1 Age: 00h33m23s
FlushedAge: 15h28m49s
Cost: 10 Preference: 15
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0xa OrigVrf: default-vrf
TableID: 0xa OrigAs: 0
NibID: 0x24000006 LastAs: 0
AttrID: 0xffffffff
BkAttrID: 0xffffffff Neighbor: ::
Flags: 0x10041 OrigNextHop: FE80::34CC:E8FF:FE5B:C02
Label: NULL RealNextHop: FE80::34CC:E8FF:FE5B:C02
BkLabel: NULL BkNextHop: FE80::7685:45FF:FEAD:102
SRLabel: NULL Interface: Ten-GigabitEthernet3/1/2
BkSRLabel: NULL BkInterface: Ten-GigabitEthernet3/1/1
Tunnel ID: Invalid IPInterface: Ten-GigabitEthernet3/1/2
BkTunnel ID: Invalid BkIPInterface: Ten-GigabitEthernet3/1/1
InLabel: NULL ColorInterface: N/A
SIDIndex: NULL BkColorInterface: N/A
FtnIndex: 0x0 TunnelInterface: N/A
TrafficIndex: N/A BkTunnelInterface: N/A
Connector: N/A PathID: 0x0
UserID: 0x0 SRTunnelID: Invalid
SID Type: N/A NID: Invalid
FlushNID: Invalid BkNID: Invalid
BkFlushNID: Invalid StatFlags: 0x0
SID: N/A
BkSID: N/A
CommBlockLen: 0 Priority: Critical
MemberPort: N/A
Applying a flexible algorithm to IS-IS SRv6
Network configuration
As shown in Figure 40, complete the following tasks:
· Configure IPv6 IS-IS on Device A, Device B, Device C, Device D, Device E, and Device F to achieve network level connectivity.
· Enable IS-IS SRv6 on Device A, Device B, Device C, Device D, Device E, and Device F.
· Configure flexible algorithm 130 for each device. The FAD of flexible algorithm 130 is as follows:
¡ Calculation type—SPF algorithm.
¡ Metric type—Link delay. In this example, the link delay on each interface is configured manually.
¡ Constraint—Exclude affinity attribute red.
· Configure TI-LFA FRR to avoid microloops. When Link A fails, Device B will determine Device A as the next hop to Device D before completing route convergence. As a result, a loop will occur because Device B will return the traffic from Device A to Device A.
Figure 40 IS-IS SRv6 network with a flexible algorithm
Table 11 Interface and IP address assignment
|
Device |
Interface |
IPv6 address |
Device |
Interface |
IPv6 address |
|
Device A |
XGE3/1/1 |
1001::1/64 |
Device D |
XGE3/1/1 |
3003::2/64 |
|
|
XGE3/1/2 |
6001::2/64 |
|
XGE3/1/2 |
4004::1/64 |
|
Device B |
XGE3/1/1 |
1001::2/64 |
Device E |
XGE3/1/1 |
4004::2/64 |
|
|
XGE3/1/2 |
2002::1/64 |
|
XGE3/1/2 |
5001::1/64 |
|
Device C |
XGE3/1/1 |
2002::2/64 |
|
XGE3/1/3 |
3002::2/64 |
|
|
XGE3/1/2 |
3003::1/64 |
Device F |
XGE3/1/1 |
5001::2/64 |
|
|
XGE3/1/3 |
3002::1/64 |
|
XGE3/1/2 |
6001::1/64 |
Procedure
1. Configure IPv6 addresses and prefix lengths for interfaces on each device. (Details not shown.)
2. Configure Device A.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceA> system-view
[DeviceA] isis 1
[DeviceA-isis-1] network-entity 00.0000.0000.0001.00
[DeviceA-isis-1] cost-style wide
[DeviceA-isis-1] address-family ipv6
[DeviceA-isis-1-ipv6] quit
[DeviceA-isis-1] quit
[DeviceA] interface ten-gigabitethernet 3/1/1
[DeviceA-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceA-Ten-GigabitEthernet3/1/1] quit
[DeviceA] interface ten-gigabitethernet 3/1/2
[DeviceA-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceA-Ten-GigabitEthernet3/1/2] quit
# Enable SRv6 and configure a locator.
[DeviceA] segment-routing ipv6
[DeviceA-segment-routing-ipv6] locator 10 ipv6-prefix 1000:: 64 static 32
[DeviceA-segment-routing-ipv6-locator-10] quit
[DeviceA-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceA] isis 1
[DeviceA-isis 1] address-family ipv6 unicast
[DeviceA-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceA-isis-1-ipv6] quit
[DeviceA-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 50 microseconds and 100 microseconds, respectively.
[DeviceA] interface ten-gigabitethernet 3/1/1
[DeviceA-Ten-GigabitEthernet3/1/1] isis link-delay min 50 max 100
[DeviceA-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 10 microseconds and 100 microseconds, respectively.
[DeviceA] interface ten-gigabitethernet 3/1/2
[DeviceA-Ten-GigabitEthernet3/1/2] isis link-delay min 10 max 100
[DeviceA-Ten-GigabitEthernet3/1/2] quit
# Enable IS-IS link delay advertisement.
[DeviceA] isis 1
[DeviceA-isis 1] address-family ipv6 unicast
[DeviceA-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceA-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceA-isis-1-ipv6] advertise application link-attributes te
[DeviceA-isis-1-ipv6] quit
[DeviceA-isis-1] quit
# Configure flexible algorithm 130.
[DeviceA] isis 1
[DeviceA-isis-1] affinity-map red bit-position 130
[DeviceA-isis-1] flex-algo 130
[DeviceA-isis-1-flex-algo-130] advertise-definition enable
[DeviceA-isis-1-flex-algo-130] metric-type delay
[DeviceA-isis-1-flex-algo-130] priority 255
[DeviceA-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceA-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceA-isis-1-flex-algo-130] quit
[DeviceA-isis-1] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceA] segment-routing ipv6
[DeviceA-segment-routing-ipv6] locator 10
[DeviceA-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceA-segment-routing-ipv6-locator-10] quit
[DeviceA-segment-routing-ipv6] quit
3. Configure Device B.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceB> system-view
[DeviceB] isis 1
[DeviceB-isis-1] network-entity 00.0000.0000.0002.00
[DeviceB-isis-1] cost-style wide
[DeviceB-isis-1] address-family ipv6
[DeviceB-isis-1-ipv6] quit
[DeviceB-isis-1] quit
[DeviceB] interface ten-gigabitethernet 3/1/1
[DeviceB-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceB-Ten-GigabitEthernet3/1/1] quit
[DeviceB] interface ten-gigabitethernet 3/1/2
[DeviceB-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceB-Ten-GigabitEthernet3/1/2] quit
# Enable SRv6 and configure a locator.
[DeviceB] segment-routing ipv6
[DeviceB-segment-routing-ipv6] locator 10 ipv6-prefix 2000:: 64 static 32
[DeviceB-segment-routing-ipv6-locator-10] quit
[DeviceB-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceB] isis 1
[DeviceB-isis 1] address-family ipv6 unicast
[DeviceB-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceB-isis-1-ipv6] quit
[DeviceB-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 50 microseconds and 100 microseconds, respectively.
[DeviceB] interface ten-gigabitethernet 3/1/1
[DeviceB-Ten-GigabitEthernet3/1/1] isis link-delay min 50 max 100
[DeviceB-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 50 microseconds and 100 microseconds, respectively.
[DeviceB] interface ten-gigabitethernet 3/1/2
[DeviceB-Ten-GigabitEthernet3/1/2] isis link-delay min 50 max 100
[DeviceB-Ten-GigabitEthernet3/1/2] quit
# Enable IS-IS link delay advertisement.
[DeviceB] isis 1
[DeviceB-isis 1] address-family ipv6 unicast
[DeviceB-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceB-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceB-isis-1-ipv6] advertise application link-attributes te
[DeviceB-isis-1-ipv6] quit
[DeviceB-isis-1] quit
# Configure flexible algorithm 130.
[DeviceB] isis 1
[DeviceB-isis-1] affinity-map red bit-position 130
[DeviceB-isis-1] flex-algo 130
[DeviceB-isis-1-flex-algo-130] advertise-definition enable
[DeviceB-isis-1-flex-algo-130] metric-type delay
[DeviceB-isis-1-flex-algo-130] priority 255
[DeviceB-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceB-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceB-isis-1-flex-algo-130] quit
[DeviceB-isis-1] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceB] segment-routing ipv6
[DeviceB-segment-routing-ipv6] locator 10
[DeviceB-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceB-segment-routing-ipv6-locator-10] quit
[DeviceB-segment-routing-ipv6] quit
4. Configure Device C.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceC> system-view
[DeviceC] isis 1
[DeviceC-isis-1] network-entity 00.0000.0000.0003.00
[DeviceC-isis-1] cost-style wide
[DeviceC-isis-1] address-family ipv6
[DeviceC-isis-1-ipv6] quit
[DeviceC-isis-1] quit
[DeviceC] interface ten-gigabitethernet 3/1/1
[DeviceC-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceC-Ten-GigabitEthernet3/1/1] quit
[DeviceC] interface ten-gigabitethernet 3/1/2
[DeviceC-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceC-Ten-GigabitEthernet3/1/2] quit
[DeviceC] interface ten-gigabitethernet 3/1/3
[DeviceC-Ten-GigabitEthernet3/1/3] isis ipv6 enable 1
[DeviceC-Ten-GigabitEthernet3/1/3] quit
# Enable SRv6 and configure a locator.
[DeviceC] segment-routing ipv6
[DeviceC-segment-routing-ipv6] locator 10 ipv6-prefix 3000:: 64 static 32
[DeviceC-segment-routing-ipv6-locator-10] quit
[DeviceC-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceC] isis 1
[DeviceC-isis 1] address-family ipv6 unicast
[DeviceC-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceC-isis-1-ipv6] quit
[DeviceC-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 50 microseconds and 100 microseconds, respectively.
[DeviceC] interface ten-gigabitethernet 3/1/1
[DeviceC-Ten-GigabitEthernet3/1/1] isis link-delay min 50 max 100
[DeviceC-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 50 microseconds and 100 microseconds, respectively.
[DeviceC] interface ten-gigabitethernet 3/1/2
[DeviceC-Ten-GigabitEthernet3/1/2] isis link-delay min 50 max 100
[DeviceC-Ten-GigabitEthernet3/1/2] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/3 to 20 microseconds and 100 microseconds, respectively.
[DeviceC] interface ten-gigabitethernet 3/1/3
[DeviceC-Ten-GigabitEthernet3/1/3] isis link-delay min 20 max 100
[DeviceC-Ten-GigabitEthernet3/1/3] quit
# Enable IS-IS link delay advertisement.
[DeviceC] isis 1
[DeviceC-isis 1] address-family ipv6 unicast
[DeviceC-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceC-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceC-isis-1-ipv6] advertise application link-attributes te
[DeviceC-isis-1-ipv6] quit
[DeviceC-isis-1] quit
# Configure flexible algorithm 130.
[DeviceC] isis 1
[DeviceC-isis-1] affinity-map red bit-position 130
[DeviceC-isis-1] flex-algo 130
[DeviceC-isis-1-flex-algo-130] advertise-definition enable
[DeviceC-isis-1-flex-algo-130] metric-type delay
[DeviceC-isis-1-flex-algo-130] priority 255
[DeviceC-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceC-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceC-isis-1-flex-algo-130] quit
[DeviceC-isis-1] quit
# Assign affinity attribute red to Ten-GigabitEthernet 3/1/3.
[DeviceC] interface ten-gigabitethernet 3/1/3
[DeviceC-Ten-GigabitEthernet3/1/3] isis 1 affinity flex-algo red
[DeviceC-Ten-GigabitEthernet3/1/3] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceC] segment-routing ipv6
[DeviceC-segment-routing-ipv6] locator 10
[DeviceC-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceC-segment-routing-ipv6-locator-10] quit
[DeviceC-segment-routing-ipv6] quit
5. Configure Device D.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceD> system-view
[DeviceD] isis 1
[DeviceD-isis-1] network-entity 00.0000.0000.0004.00
[DeviceD-isis-1] cost-style wide
[DeviceD-isis-1] address-family ipv6
[DeviceD-isis-1-ipv6] quit
[DeviceD-isis-1] quit
[DeviceD] interface ten-gigabitethernet 3/1/1
[DeviceD-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceD-Ten-GigabitEthernet3/1/1] quit
[DeviceD] interface ten-gigabitethernet 3/1/2
[DeviceD-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceD-Ten-GigabitEthernet3/1/2] quit
# Enable SRv6 and configure a locator.
[DeviceD] segment-routing ipv6
[DeviceD-segment-routing-ipv6] locator 10 ipv6-prefix 4000:: 64 static 32
[DeviceD-segment-routing-ipv6-locator-10] quit
[DeviceD-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceD] isis 1
[DeviceD-isis 1] address-family ipv6 unicast
[DeviceD-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceD-isis-1-ipv6] quit
[DeviceD-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 50 microseconds and 100 microseconds, respectively.
[DeviceD] interface ten-gigabitethernet 3/1/1
[DeviceD-Ten-GigabitEthernet3/1/1] isis link-delay min 50 max 100
[DeviceD-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 10 microseconds and 100 microseconds, respectively.
[DeviceD] interface ten-gigabitethernet 3/1/2
[DeviceD-Ten-GigabitEthernet3/1/2] isis link-delay min 10 max 100
[DeviceD-Ten-GigabitEthernet3/1/2] quit
# Enable IS-IS link delay advertisement.
[DeviceD] isis 1
[DeviceD-isis 1] address-family ipv6 unicast
[DeviceD-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceD-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceD-isis-1-ipv6] advertise application link-attributes te
[DeviceD-isis-1-ipv6] quit
[DeviceD-isis-1] quit
# Configure flexible algorithm 130.
[DeviceD] isis 1
[DeviceD-isis-1] affinity-map red bit-position 130
[DeviceD-isis-1] flex-algo 130
[DeviceD-isis-1-flex-algo-130] advertise-definition enable
[DeviceD-isis-1-flex-algo-130] metric-type delay
[DeviceD-isis-1-flex-algo-130] priority 255
[DeviceD-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceD-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceD-isis-1-flex-algo-130] quit
[DeviceD-isis-1] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceD] segment-routing ipv6
[DeviceD-segment-routing-ipv6] locator 10
[DeviceD-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceD-segment-routing-ipv6-locator-10] quit
[DeviceD-segment-routing-ipv6] quit
6. Configure Device E.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceE> system-view
[DeviceE] isis 1
[DeviceE-isis-1] network-entity 00.0000.0000.0005.00
[DeviceE-isis-1] cost-style wide
[DeviceE-isis-1] address-family ipv6
[DeviceE-isis-1-ipv6] quit
[DeviceE-isis-1] quit
[DeviceE] interface ten-gigabitethernet 3/1/1
[DeviceE-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceE-Ten-GigabitEthernet3/1/1] quit
[DeviceE] interface ten-gigabitethernet 3/1/2
[DeviceE-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceE-Ten-GigabitEthernet3/1/2] quit
[DeviceE] interface ten-gigabitethernet 3/1/3
[DeviceE-Ten-GigabitEthernet3/1/3] isis ipv6 enable 1
[DeviceE-Ten-GigabitEthernet3/1/3] quit
# Enable SRv6 and configure a locator.
[DeviceE] segment-routing ipv6
[DeviceE-segment-routing-ipv6] locator 10 ipv6-prefix 5000:: 64 static 32
[DeviceE-segment-routing-ipv6-locator-10] quit
[DeviceE-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceE] isis 1
[DeviceE-isis 1] address-family ipv6 unicast
[DeviceE-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceE-isis-1-ipv6] quit
[DeviceE-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 10 microseconds and 100 microseconds, respectively.
[DeviceE] interface ten-gigabitethernet 3/1/1
[DeviceE-Ten-GigabitEthernet3/1/1] isis link-delay min 10 max 100
[DeviceE-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 10 microseconds and 100 microseconds, respectively.
[DeviceE] interface ten-gigabitethernet 3/1/2
[DeviceE-Ten-GigabitEthernet3/1/2] isis link-delay min 10 max 100
[DeviceE-Ten-GigabitEthernet3/1/2] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/3 to 20 microseconds and 100 microseconds, respectively.
[DeviceE] interface ten-gigabitethernet 3/1/3
[DeviceE-Ten-GigabitEthernet3/1/3] isis link-delay min 20 max 100
[DeviceE-Ten-GigabitEthernet3/1/3] quit
# Enable IS-IS link delay advertisement.
[DeviceE] isis 1
[DeviceE-isis 1] address-family ipv6 unicast
[DeviceE-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceE-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceE-isis-1-ipv6] advertise application link-attributes te
[DeviceE-isis-1-ipv6] quit
[DeviceE-isis-1] quit
# Configure flexible algorithm 130.
[DeviceE] isis 1
[DeviceE-isis-1] affinity-map red bit-position 130
[DeviceE-isis-1] flex-algo 130
[DeviceE-isis-1-flex-algo-130] advertise-definition enable
[DeviceE-isis-1-flex-algo-130] metric-type delay
[DeviceE-isis-1-flex-algo-130] priority 255
[DeviceE-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceE-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceE-isis-1-flex-algo-130] quit
[DeviceE-isis-1] quit
# Assign affinity attribute red to Ten-GigabitEthernet 3/1/3.
[DeviceE] interface ten-gigabitethernet 3/1/3
[DeviceE-Ten-GigabitEthernet3/1/3] isis 1 affinity flex-algo red
[DeviceE-Ten-GigabitEthernet3/1/3] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceE] segment-routing ipv6
[DeviceE-segment-routing-ipv6] locator 10
[DeviceE-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceE-segment-routing-ipv6-locator-10] quit
[DeviceE-segment-routing-ipv6] quit
7. Configure Device F.
# Configure IPv6 IS-IS to achieve network level connectivity and set the IS-IS cost style to wide.
<DeviceF> system-view
[DeviceF] isis 1
[DeviceF-isis-1] network-entity 00.0000.0000.0006.00
[DeviceF-isis-1] cost-style wide
[DeviceF-isis-1] address-family ipv6
[DeviceF-isis-1-ipv6] quit
[DeviceF-isis-1] quit
[DeviceF] interface ten-gigabitethernet 3/1/1
[DeviceF-Ten-GigabitEthernet3/1/1] isis ipv6 enable 1
[DeviceF-Ten-GigabitEthernet3/1/1] quit
[DeviceF] interface ten-gigabitethernet 3/1/2
[DeviceF-Ten-GigabitEthernet3/1/2] isis ipv6 enable 1
[DeviceF-Ten-GigabitEthernet3/1/2] quit
# Enable SRv6 and configure a locator.
[DeviceF] segment-routing ipv6
[DeviceF-segment-routing-ipv6] locator 10 ipv6-prefix 6000:: 64 static 32
[DeviceF-segment-routing-ipv6-locator-10] quit
[DeviceF-segment-routing-ipv6] quit
# Apply the locator to the IPv6 IS-IS process.
[DeviceF] isis 1
[DeviceF-isis 1] address-family ipv6 unicast
[DeviceF-isis-1-ipv6] segment-routing ipv6 locator 10
[DeviceF-isis-1-ipv6] quit
[DeviceF-isis-1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/1 to 10 microseconds and 100 microseconds, respectively.
[DeviceF] interface ten-gigabitethernet 3/1/1
[DeviceF-Ten-GigabitEthernet3/1/1] isis link-delay min 10 max 100
[DeviceF-Ten-GigabitEthernet3/1/1] quit
# Set the minimum link delay and the maximum link delay on Ten-GigabitEthernet 3/1/2 to 10 microseconds and 100 microseconds, respectively.
[DeviceF] interface ten-gigabitethernet 3/1/2
[DeviceF-Ten-GigabitEthernet3/1/2] isis link-delay min 10 max 100
[DeviceF-Ten-GigabitEthernet3/1/2] quit
# Enable IS-IS link delay advertisement.
[DeviceF] isis 1
[DeviceF-isis 1] address-family ipv6 unicast
[DeviceF-isis-1-ipv6] metric-delay advertisement enable
# Enable IS-IS to advertise link attributes in LSPs.
[DeviceF-isis-1-ipv6] advertise link-attributes
# Enable IS-IS to advertise link attributes for use by flexible algorithms.
[DeviceF-isis-1-ipv6] advertise application link-attributes te
[DeviceF-isis-1-ipv6] quit
[DeviceF-isis-1] quit
# Configure flexible algorithm 130.
[DeviceF] isis 1
[DeviceF-isis-1] affinity-map red bit-position 130
[DeviceF-isis-1] flex-algo 130
[DeviceF-isis-1-flex-algo-130] advertise-definition enable
[DeviceF-isis-1-flex-algo-130] metric-type delay
[DeviceF-isis-1-flex-algo-130] priority 255
[DeviceF-isis-1-flex-algo-130] affinity exclude-any red
# Enable TI-LFA FRR for flexible algorithm 130.
[DeviceF-isis-1-flex-algo-130] fast-reroute ti-lfa enable
[DeviceF-isis-1-flex-algo-130] quit
[DeviceF-isis-1] quit
# Associate SRv6 locator 10 to flexible algorithm 130.
[DeviceF] segment-routing ipv6
[DeviceF-segment-routing-ipv6] locator 10
[DeviceF-segment-routing-ipv6-locator-10] flex-algo algorithm 130
[DeviceF-segment-routing-ipv6-locator-10] quit
[DeviceF-segment-routing-ipv6] quit
Verifying the configuration
# Display routes calculated by flexible algorithm 130 on Device A. Device A uses Device F as the next hop to forward traffic to Device D, and the backup next hop calculated by TI-LFA is Device B.
[DeviceA] display isis flex-algo 130 route level-1 verbose
Flex Algo Route Information for IS-IS(1)
-----------------------------------------
Level-1 Flex Algo Route
-----------------------
IPv6 dest : 1000::/64
Flag : D/-/- Cost : 0
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : Direct
NexthopFlag : -
Interface : NULL0 Delay Flag : N/A
Nib ID : 0x0
IPv6 dest : 2000::/64
Flag : R/-/- Cost : 50
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C5:D9FF:FE06:206
NexthopFlag : -
Interface : XGE3/1/1 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/2
BkNextHop : FE80::80C7:7DFF:FE43:607
LsIndex : 0x80000003
Backup label stack(top->bottom): {3000::1:0:0}
Nib ID : 0x2400000c
IPv6 dest : 3000::/64
Flag : R/-/- Cost : 80
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:7DFF:FE43:607
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:206
LsIndex : N/A
Backup label stack(top->bottom): N/A
Nib ID : 0x24000008
IPv6 dest : 4000::/64
Flag : R/-/- Cost : 30
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:7DFF:FE43:607
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:206
LsIndex : 0x80000002
Backup label stack(top->bottom): {3000::1:0:0}
Nib ID : 0x2400000a
IPv6 dest : 5000::/64
Flag : R/-/- Cost : 20
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:7DFF:FE43:607
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:206
LsIndex : 0x80000002
Backup label stack(top->bottom): {3000::1:0:0}
Nib ID : 0x2400000a
IPv6 dest : 6000::/64
Flag : R/-/- Cost : 10
Admin tag : - Src count : 1
Algorithm : 130
Nexthop : FE80::80C7:7DFF:FE43:607
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:206
LsIndex : 0x80000003
Backup label stack(top->bottom): {3000::1:0:0}
Nib ID : 0x2400000c
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set
# Display routes calculated by flexible algorithm 130 on Device C. The backup path to Device D does not include the link whose affinity attribute is red.
[Device C] display isis flex-algo 130 route level-1 verbose
Flex Algo Route Information for IS-IS(1)
-----------------------------------------
Level-1 Flex Algo Route
-----------------------
IPv6 dest : 1000::/64
Flag : R/-/- Cost : 80
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:42FF:FEF4:406
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:207
LsIndex : N/A
Backup label stack(top->bottom): N/A
Nib ID : 0x2400000a
IPv6 dest : 2000::/64
Flag : R/-/- Cost : 50
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C5:D9FF:FE06:207
NexthopFlag : -
Interface : XGE3/1/1 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/2
BkNextHop : FE80::80C7:42FF:FEF4:406
LsIndex : 0x80000002
Backup label stack(top->bottom): {1000::1:0:0}
Nib ID : 0x24000009
IPv6 dest : 3000::/64
Flag : D/-/- Cost : 0
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : Direct
NexthopFlag : -
Interface : NULL0 Delay Flag : N/A
Nib ID : 0x0
IPv6 dest : 4000::/64
Flag : R/-/- Cost : 50
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:42FF:FEF4:406
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:207
LsIndex : N/A
Backup label stack(top->bottom): N/A
Nib ID : 0x2400000a
IPv6 dest : 5000::/64
Flag : R/-/- Cost : 60
Admin tag : - Src count : 1
Algorithm : 130
Priority : Low
Nexthop : FE80::80C7:42FF:FEF4:406
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:207
LsIndex : N/A
Backup label stack(top->bottom): N/A
Nib ID : 0x2400000a
IPv6 dest : 6000::/64
Flag : R/-/- Cost : 70
Admin tag : - Src count : 1
Algorithm : 130
Nexthop : FE80::80C7:42FF:FEF4:406
NexthopFlag : -
Interface : XGE3/1/2 Delay Flag : N/A
TI-LFA:
Interface : XGE3/1/1
BkNextHop : FE80::80C5:D9FF:FE06:207
LsIndex : N/A
Backup label stack(top->bottom): N/A
Nib ID : 0x2400000e
Flags: D-Direct, R-Added to Rib, L-Advertised in LSPs, U-Up/Down Bit Set