- Table of Contents
-
- 07-Layer 3—IP Routing Configuration Guide
- 00-Preface
- 01-Basic IP routing configuration
- 02-Static routing configuration
- 03-RIP configuration
- 04-OSPF configuration
- 05-IS-IS configuration
- 06-EIGRP configuration
- 07-BGP configuration
- 08-Policy-based routing configuration
- 09-IPv6 static routing configuration
- 10-RIPng configuration
- 11-OSPFv3 configuration
- 12-IPv6 policy-based routing configuration
- 13-Routing policy configuration
- 14-DCN configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Basic IP routing configuration | 275.16 KB |
Contents
Extension attribute redistribution
Setting the maximum lifetime for routes and labels in the RIB
Setting the maximum lifetime for routes in the FIB
Enabling the RIB to flush route attribute information to the FIB
Configuring inter-protocol FRR
Enabling routes from different protocols to form ECMP routes
About using BFD to detect the next hop availability of the primary route
Restrictions and guidelines for using BFD to detect the next hop availability of the primary route
Configuring BFD control packet mode
Configuring BFD echo packet mode
Configuring direct route-Track-VRRP collaboration
Configuring routing policy-based recursive lookup
Configuring route recursion suppression
Configuring next hop recursion loop suppression
About next hop recursion loop suppression
Restrictions and guidelines for configuring next hop recursion loop suppression
Disabling suppression for IPv4 next hop recursion loop
Setting the interval for clearing the recursion loop counter (IPv4)
Disabling suppression for IPv6 next hop recursion loop
Setting the interval for clearing the recursion loop counter (IPv6)
Setting the maximum number of active routes supported by the device
Setting the maximum number of RIB next hop records or route entry records
Enabling notifications for RIB
Display and maintenance commands for basic IP routing
Configuring basic IP routing
This chapter focuses on unicast routing protocols. For more information about multicast routing protocols, see IP Multicast Configuration Guide.
About IP routing
IP routing directs IP packet forwarding on routers. Based on the destination IP address in the packet, a router looks up a route for the packet in a routing table and forwards the packet to the next hop. Routes are path information used to direct IP packets.
Routing table
A RIB contains the global routing information and related information, including route recursion, route redistribution, and route extension information. The router selects optimal routes from the routing table and puts them into the FIB table. It uses the FIB table to forward packets. For more information about the FIB table, see Layer 3—IP Services Configuration Guide.
Route categories
Table 1 categorizes routes by different criteria.
|
Criterion |
Categories |
|
Origin |
· Direct route—A direct route is discovered by the data link protocol on an interface, and is also called an interface route. · Static route—A static route is manually configured by an administrator. · Dynamic route—A dynamic route is dynamically discovered by a routing protocol. |
|
Destination |
· Network route—The destination is a network. The subnet mask is less than 32 bits. · Host route—The destination is a host. The subnet mask is 32 bits. |
|
Whether the destination is directly connected |
· Direct route—The destination is directly connected. · Indirect route—The destination is indirectly connected. |
Dynamic routing protocols
Static routes work well in small, stable networks. They are easy to configure and require fewer system resources. However, in networks where topology changes occur frequently, a typical practice is to configure a dynamic routing protocol. Compared with static routing, a dynamic routing protocol is complicated to configure, requires more router resources, and consumes more network resources.
Dynamic routing protocols dynamically collect and report reachability information to adapt to topology changes. They are suitable for large networks.
Dynamic routing protocols can be classified by different criteria, as shown in Table 2.
Table 2 Categories of dynamic routing protocols
|
Criterion |
Categories |
|
Operation scope |
· IGPs—Work within an AS. Examples include RIP, OSPF, and IS-IS. · EGPs—Work between ASs. The most popular EGP is BGP. |
|
Routing algorithm |
· Distance-vector protocols—Examples include RIP and BGP. BGP is also considered a path-vector protocol. · Link-state protocols—Examples include OSPF and IS-IS. |
|
Destination address type |
· Unicast routing protocols—Examples include RIP, OSPF, BGP, and IS-IS. · Multicast routing protocols—Examples include PIM-SM and PIM-DM. |
|
IP version |
· IPv4 routing protocols—Examples include RIP, OSPF, BGP, and IS-IS. · IPv6 routing protocols—Examples include RIPng, OSPFv3, IPv6 BGP, and IPv6 IS-IS. |
An AS refers to a group of routers that use the same routing policy and work under the same administration.
Route preference
Routing protocols, including static and direct routing, each by default have a preference. If they find multiple routes to the same destination, the router selects the route with the highest preference as the optimal route.
The preference of a direct route is always 0 and cannot be changed. You can configure a preference for each static route and each dynamic routing protocol. The following table lists the route types and default preferences. The smaller the value, the higher the preference.
Table 3 Route types and default route preferences
|
Route type |
Preference |
|
Direct route |
0 |
|
Multicast static route |
1 |
|
OSPF |
10 |
|
IS-IS |
15 |
|
Unicast static route |
60 |
|
RIP |
100 |
|
OSPF ASE |
150 |
|
OSPF NSSA |
150 |
|
IBGP |
255 |
|
EBGP |
255 |
|
Unknown (route from an untrusted source) |
256 |
Load sharing
A routing protocol might find multiple optimal equal-cost routes to the same destination. You can use these routes to implement equal-cost multi-path (ECMP) load sharing.
Static routing, IPv6 static routing, RIP, RIPng, OSPF, OSPFv3, BGP, IPv6 BGP, IS-IS, and IPv6 IS-IS support ECMP load sharing.
Route backup
Route backup can improve network availability. Among multiple routes to the same destination, the route with the highest priority is the primary route and others are secondary routes.
The router forwards matching packets through the primary route. When the primary route fails, the route with the highest preference among the secondary routes is selected to forward packets. When the primary route recovers, the router uses it to forward packets.
Route recursion
To use a BGP, static, or RIP route that has an indirectly connected next hop, a router must perform route recursion to find the output interface to reach the next hop.
Link-state routing protocols, such as OSPF and IS-IS, do not need route recursion, because they obtain directly connected next hops through route calculation.
The RIB records and saves route recursion information, including brief information about related routes, recursive paths, and recursion depth.
Route redistribution
Route redistribution enables routing protocols to learn routing information from each other. A dynamic routing protocol can redistribute routes from other routing protocols, including direct and static routing. For more information, see the respective chapters on those routing protocols in this configuration guide.
The RIB records redistribution relationships of routing protocols.
Extension attribute redistribution
Extension attribute redistribution enables routing protocols to learn route extension attributes from each other, including BGP extended community attributes, OSPF area IDs, route types, and router IDs.
The RIB records extended attributes of each routing protocol and redistribution relationships of different routing protocol extended attributes.
Setting the maximum lifetime for routes and labels in the RIB
About this task
Perform this task to prevent routes of a certain protocol from being aged out due to slow protocol convergence resulting from a large number of route entries or long GR period.
Restrictions and guidelines
The configuration takes effect at the next protocol or RIB process switchover.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Set the maximum lifetime for IPv4 routes and labels in the RIB.
protocol protocol [ instance instance-name ] lifetime seconds
By default, the maximum lifetime for routes and labels in the RIB is 900 seconds.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Set the maximum lifetime for IPv6 routes and labels in the RIB.
protocol protocol [ instance instance-name ] lifetime seconds
By default, the maximum lifetime for routes and labels in the RIB is 900 seconds.
Setting the maximum lifetime for routes in the FIB
About this task
When GR is disabled, FIB entries must be retained for some time after a protocol process switchover or RIB process switchover. When GR is enabled, FIB entries must be removed immediately after a protocol or RIB process switchover to avoid routing issues. Perform this task to meet such requirements.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Set the maximum lifetime for IPv4 routes in the FIB.
fib lifetime seconds
By default, the maximum lifetime for routes in the FIB is 600 seconds.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Set the maximum lifetime for IPv6 routes in the FIB.
fib lifetime seconds
By default, the maximum lifetime for routes in the FIB is 600 seconds.
Enabling the RIB to flush route attribute information to the FIB
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Enable the RIB to flush route attribute information to the FIB.
flush route-attribute protocol
By default, the RIB does not flush route attribute information to the FIB.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Enable the RIB to flush route attribute information to the FIB.
flush route-attribute protocol
By default, the RIB does not flush route attribute information to the FIB.
Configuring inter-protocol FRR
About this task
This feature is applicable to services that are sensitive to packet loss and latency. Inter-protocol fast reroute (FRR) enables fast rerouting between routes of different protocols. A backup next hop is automatically selected to reduce the service interruption time caused by unreachable next hops. When the next hop of the primary link fails, the traffic is redirected to the backup next hop.
Among the routes to the same destination in the RIB, a router adds the route with the highest preference to the FIB table. After you configure this feature, the device will select a route of another routing protocol as the backup route. When the next hop of the primary route is unreachable, the device forwards packets through the backup route.
Restrictions and guidelines
This feature uses the next hop of a route from a different protocol as the backup next hop, which might cause loops.
If you configure both inter-protocol FRR and protocol-specific FRR, protocol-specific FRR takes effect.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Enable IPv4 RIB inter-protocol FRR.
inter-protocol fast-reroute [ ecmp-shared ] [ vpn-instance vpn-instance-name ]
By default, inter-protocol FRR is disabled.
If you do not specify a VPN instance, inter-protocol FRR is enabled for the public network.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Enable IPv6 RIB inter-protocol FRR.
inter-protocol fast-reroute [ ecmp-shared ] [ vpn-instance vpn-instance-name ]
By default, inter-protocol FRR is disabled.
If you do not specify a VPN instance, inter-protocol FRR is enabled for the public network.
Enabling routes from different protocols to form ECMP routes
About this task
By default, routes from different protocols have different preferences, and the route costs are calculated in different ways. Such routes cannot form ECMP routes. Perform this task to ignore the costs for routes from different protocols, so that they can form ECMP routes.
For routes from multiple protocols with the same destination to form ECMP routes, follow these restrictions and guidelines:
· If you do not specify the ignore-preference keyword, routes with the highest priority will form ECMP routes. You can edit the preferences for routes from different protocols to the same value, so that they can form ECMP routes.
· If you specify the ignore-preference keyword, multiple routes will form ECMP routes.
Restrictions and guidelines
If you configure both this feature and inter-protocol FRR, only this feature takes effect.
Routes with different next hop types (such as IP or MPLS) cannot form ECMP routes.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Enabling IPv4 routes from different protocols to form ECMP route.
inter-protocol ecmp [ ignore-preference ] [ vpn-instance vpn-instance-name ]
By default, IPv4 routes from different protocols cannot form ECMP route.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Enabling IPv6 routes from different protocols to form ECMP route.
inter-protocol ecmp [ ignore-preference ] [ vpn-instance vpn-instance-name ]
By default, IPv6 routes from different protocols cannot form ECMP route.
Using BFD to detect the next hop availability of the primary route for inter-protocol FRR or ECMP routes
About using BFD to detect the next hop availability of the primary route
This feature uses BFD to detect the next hop availability of the primary route for inter-protocol FRR or ECMP routes. When the next hop of the primary route fails, this feature enables the upper layer routing protocol to reallocate service traffic to the backup next hops or to the remaining ECMP next hops.
For inter-protocol FRR, the primary route is the route with the highest preference among the routes to the same destination. If BFD detects that the next hop of the primary route is invalid, it notifies the FIB of the invalid next hop. The FIB will use the backup next hops to guide traffic forwarding.
For ECMP routes of a routing protocol, the primary route is each ECMP route. If BFD detects that the next hop of an ECMP route is invalid, it notifies the routing protocol of the invalid next hop. The routing protocol will reallocate the service traffic to the remaining ECMP next hops. When BFD detects that the next hops of all ECMP routes are invalid, BFD notifies the routing protocol to withdraw the routes. In addition, the device reselects optimal routes for the service traffic.
For more information about BFD, see High Availability Configuration Guide.
Restrictions and guidelines for using BFD to detect the next hop availability of the primary route
This feature can take effect and automatically establish a BFD session only when a primary route exists and the primary route has backup next hops.
If you specify the ecmp-shared keyword when configuring FRR for a routing protocol, the device will use the LFA algorithm to calculate backup next hops for each ECMP route. The routes destined for the backup next hops are also added to the routing table as ECMP routes and the state of these routes is backup. BFD does not detect these backup ECMP routes.
Configuring BFD control packet mode
About this task
This mode uses BFD control packets to detect the status of a link bidirectionally at a millisecond level.
Restrictions and guidelines for BFD control packet mode
When you use a BFD session in control packet mode to detect the next hop availability of the primary route, you must manually create a static BFD session on the next hop device. The reason is that the BFD session in control packet mode requires negotiation of both ends for successful establishment. The local device can use the BFD session in control packet mode to detect the next hop availability of the primary route only when the static BFD session created on the next hop device of the primary route meets the following requirements:
· The static BFD session is a single-hop BFD session in control packet mode.
· The source IP address of the static BFD session is the destination IP address of the local automatically created BFD session.
· The destination IP address of the static BFD session is the source IP address of the local automatically created BFD session.
· The remote discriminator of the static BFD session is the local discriminator of the local automatically created BFD session.
Procedure
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create RIB IPv4 or IPv6 address family view and enter the view.
IPv4:
address-family ipv4
IPv6:
address-family ipv6
4. Use BFD to detect the next hop availability of the primary route for inter-protocol FRR or ECMP routes.
primary-path-detect bfd ctrl [ inter-protocol-frr | protocol-ecmp protocol ]
By default, BFD is not used for detecting the next hop availability of the primary route for inter-protocol FRR or ECMP routes.
Configuring BFD echo packet mode
About this task
With BFD echo packet mode enabled, the output interface sends BFD echo packets to the destination device, and the device sends the packets back to test the link reachability.
Restrictions and guidelines
You do not need to configure BFD echo packet mode at the peer end.
Procedure
1. Enter system view.
system-view
2. (Optional.) Configure the source IP address of echo packets.
IPv4:
bfd echo-source-ip ip-address
By default, the source IPv4 address of echo packets is not configured.
As a best practice to avoid network congestion caused by excessive ICMP redirect packets from the peer, use this command. Make sure the source IPv4 address is not on the subnet of any interfaces on the device.
For more information about this command, see BFD in High Availability Command Reference.
IPv6:
bfd echo-source-ipv6 ipv6-address
By default, the source IPv6 address of echo packets is not configured.
As a best practice to avoid network congestion caused by excessive ICMPv6 redirect packets from the peer, use this command. Make sure the source IPv6 address is not on the subnet of any interfaces on the device.
You must specify a global unicast address as the source IPv6 address of BFD echo packets.
For more information about this command, see BFD in High Availability Command Reference.
3. Enter RIB view.
rib
4. Create RIB IPv4 or IPv6 address family view and enter the view.
IPv4:
address-family ipv4
IPv6:
address-family ipv6
5. Use BFD to detect the next hop availability of the primary route for inter-protocol FRR or ECMP routes.
primary-path-detect bfd echo [ inter-protocol-frr | protocol-ecmp protocol ]
By default, BFD is not used for detecting the next hop availability of the primary route for inter-protocol FRR or ECMP routes.
Configuring direct route-Track-VRRP collaboration
About this task
On a network where a VRRP group is used as the default gateway, upstream traffic is always forwarded through the master device in the VRRP group. The corresponding downstream traffic might take a different path because the route selection is determined by the configured dynamic routing protocol. The mismatching forwarding paths might cause the traffic to be blocked by firewalls (if configured), and increase the complexity and overhead for traffic monitoring and statistics collection operations.
You can resolve the issue by configuring direct route-Track-VRRP collaboration. The collaboration ensures that the upstream traffic and the corresponding downstream traffic are forwarded through matching paths (both through the master device in the VRRP group).
To configure direct route-Track-VRRP collaboration, perform the following tasks on each member device of the VRRP group:
1. Create a track entry associated with the VRRP group member device so the track entry state changes according to the status of the device in the VRRP group.
¡ If the device state is Backup or Initialize, the track entry state changes to Negative.
¡ If the device state is Master, the track entry state changes to Positive.
¡ If the device state is Inactive or the VRRP group does not exist, the track entry state changes to NotReady.
2. Associate the track entry with the direct route on the interface connected to the downstream device. The cost value of the direct route on the interface changes according to the status of the track entry.
¡ If the track entry does not exist or the track entry is in NotReady or Positive state, the cost of the direct route changes to 0.
¡ If the track entry is in Negative state, the cost of the direct route changes to the value configured by using the route-direct track command.
|
IMPORTANT: The direct route that has a lower cost value is preferentially used. |
3. Enable direct route redistribution on the VRRP group member device for the dynamic routing protocol.
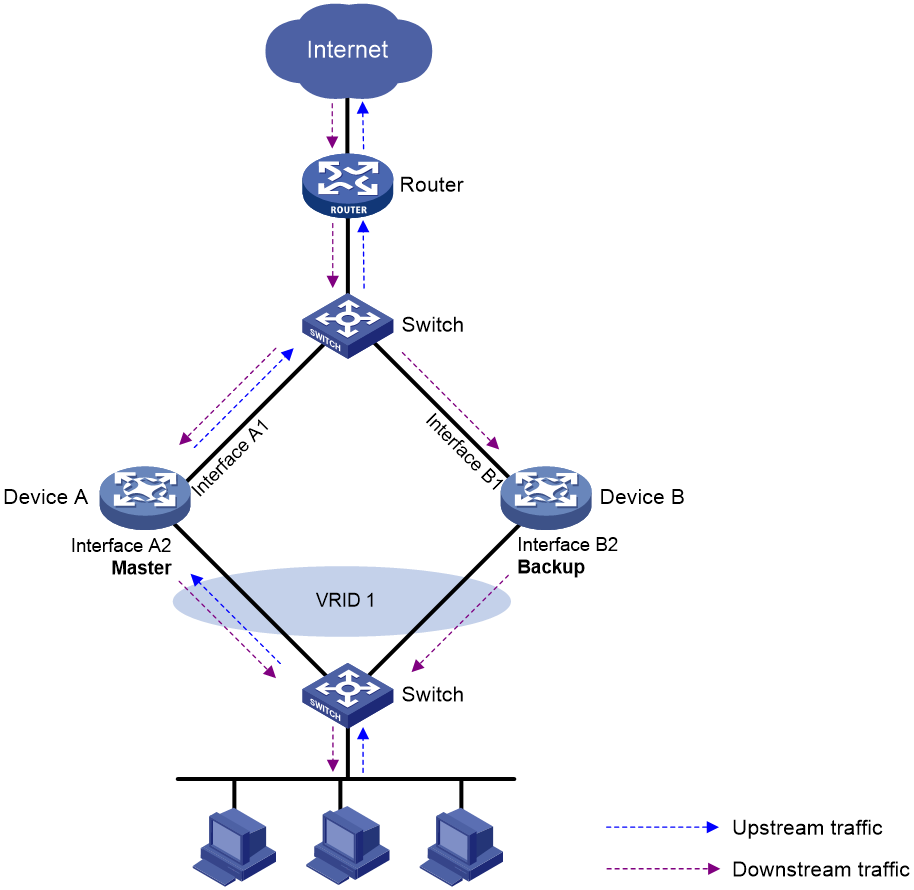
As shown in Figure 1, OSPF is configured on all devices. Device A and Device B belong to VRRP group 1 and Device A is the master device. The router has two ECMP routes to reach the hosts, one through Device A and the other through Device B. The upstream traffic of hosts is always forwarded through Device A, and the corresponding downstream traffic will be load balanced through the ECMP routes.
Figure 1 VRRP gateway network diagram
To ensure that the upstream traffic and downstream traffic of a host are forwarded through matching paths (both through Device A), perform the following tasks on Device A and Device B:
1. Create a track entry and associate the track entry with VRRP group 1 on each device.
2. Associate the track entry with the direct route on Interface A2 of Device A, and associate the track entry with the direct route on Interface B2 of Device B.
3. Enable direct route redistribution for OSPF on each device, and use the original cost of redistributed direct routes.
Device B is in Backup state, so the track entry changes to Negative state. In Negative state, the cost value of Interface B2 on Device B changes from 0 to a user-defined value. The router performs route calculation, and it forwards the downstream traffic to the host through Device A.
For more information about associating Track with a VRRP group, see Track configuration in High Availability Configuration Guide.
Procedure (IPv4)
1. Enter system view.
system-view
2. Create a track entry, associate the track entry with an IPv4 VRRP group, and enter track entry view.
track track-entry-number vrrp interface interface-type interface-number vrid virtual-router-id
For more information about associating a track entry with an IPv4 VRRP group, see Track configuration in High Availability Configuration Guide.
3. Return to system view.
quit
4. Enter interface view.
interface interface-type interface-number
5. Associate the track entry with the IPv4 direct route on the interface and apply the specified cost value to the IPv4 direct route after the track entry changes to Negative state.
route-direct track track-entry-number degrade-cost cost-value
By default, no track entry is associated with the IPv4 direct route on an interface.
To change the track entry associated with the IPv4 direct route on an interface, you must first execute the undo route-direct track command to remove the original association.
Procedure (IPv6)
1. Enter system view.
system-view
2. Create a track entry, associate the track entry with an IPv6 VRRP group, and enter track entry view.
track track-entry-number vrrp ipv6 interface interface-type interface-number vrid virtual-router-id
For more information about associating a track entry with an IPv6 VRRP group, see Track configuration in High Availability Configuration Guide.
3. Return to system view.
quit
4. Enter interface view.
interface interface-type interface-number
5. Associate the track entry with the IPv6 direct route on the interface and apply the specified cost value to the IPv6 direct route after the track entry changes to Negative state.
ipv6 route-direct track track-entry-number degrade-cost cost-value
By default, no track entry is associated with the IPv6 direct route on an interface.
To change the track entry associated with the IPv6 direct route on an interface, you must first execute the undo ipv6 route-direct track command to remove the original association.
Configuring routing policy-based recursive lookup
About this task
Configure routing policy-based recursive lookup to control route recursion results. For example, when a route changes, the routing protocol has to perform a route recursion if the next hop is indirectly connected. The routing protocol might select an incorrect path, which can cause traffic loss. To prevent this problem, you can use a routing policy to filter out incorrect routes. The routes that pass the filtering of the routing policy will be used for route recursion.
Restrictions and guidelines
The apply clauses in the specified routing policy cannot take effect.
Make sure a minimum of one related route can match the routing policy for correct traffic forwarding.
The routing policy does not apply to routes received from directly connected BGP neighbors.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Configure routing policy-based recursive lookup.
protocol protocol nexthop recursive-lookup route-policy route-policy-name
By default, routing policy-based recursive lookup is not configured.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Configure routing policy-based recursive lookup.
protocol protocol nexthop recursive-lookup route-policy route-policy-name
By default, routing policy-based recursive lookup is not configured.
Configuring route recursion suppression
About this task
A change of a related route or tunnel obtained through nexthop recursion triggers another recursion for the recursive route. When the network changes frequently, the route recursion is performed repeatedly, which causes high CPU usage. To solve this issue, configure this feature for the RIB to wait for the suppression timer to expire before obtaining the recursion result. In this way, the route recursion is performed less often and the CPU usage can be reduced. However, this feature can result in lower route recursion efficiency and slow route convergence. Configure this feature as needed make sure the parameters are appropriate.
After you configure this feature, no matter how the route recursion results change within the suppression timer, the RIB always obtains the most recent results after the suppression timer expires.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Configure route recursion suppression.
nexthop recursive-lookup restrain { maximum-interval [ minimum-interval [ incremental-interval ] ] | millisecond interval }
By default, route recursion suppression is disabled.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Configure route recursion suppression.
nexthop recursive-lookup restrain { maximum-interval [ minimum-interval [ incremental-interval ] ] | millisecond interval }
By default, route recursion suppression is disabled.
Configuring next hop recursion loop suppression
About next hop recursion loop suppression
A recursion loop occurs when a route recurses to a related route that recurses back to the route. It causes a route recursion failure and further lookup for a related route. If recursion loop persists, continuous route flapping will cause high system resource consumption and CPU utilization.
This feature enables the system to use a counter to record the number of route recursion failures. When the counter reaches 20, the system suppresses route recursion for a specified period of time to save system resources on the device.
Restrictions and guidelines for configuring next hop recursion loop suppression
The configuration of disabling next hop recursion loop suppression takes effect immediately.
The setting of clearing the recursion loop counter takes effect for the next recursion loop suppression.
Disabling suppression for IPv4 next hop recursion loop
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Disable IPv4 next hop recursion loop suppression.
nexthop recursive-lookup restrain disable
By default, IPv4 next hop recursion loop suppression is enabled.
Setting the interval for clearing the recursion loop counter (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Set the interval for clearing the recursion loop counter.
nexthop recursive-lookup restrain clear-interval interval
By default, the interval for clearing the recursion loop counter is 600 seconds.
Disabling suppression for IPv6 next hop recursion loop
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Disable IPv6 next hop recursion loop suppression.
nexthop recursive-lookup restrain disable
By default, IPv6 next hop recursion loop suppression is enabled.
Setting the interval for clearing the recursion loop counter (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Set the interval for clearing the recursion loop counter.
nexthop recursive-lookup restrain clear-interval interval
By default, the interval for clearing the recursion loop counter is 600 seconds.
Setting the maximum number of active routes supported by the device
About this task
The feature allows you to set the maximum number of active IPv4/IPv6 routes supported by the device. When the maximum number of active IPv4/IPv6 routes is exceeded, the device still accepts new active routes but generates a system log message. You can take relevant actions based on the message to save system resources.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Set the maximum number of active IPv4 routes supported by the device.
routing-table limit number simply-alert
By default, the maximum number of active IPv4 routes is not set for the device.
Configuration in RIB IPv4 address family view limits the number of active IPv4 routes for the public network and all VPN instances.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Set the maximum number of active IPv6 routes supported by the device.
routing-table limit number simply-alert
By default, the maximum number of active IPv6 routes is not set for the device.
Configuration in RIB IPv6 address family view limits the number of active IPv6 routes for the public network and all VPN instances.
Setting the maximum number of RIB next hop records or route entry records
About this task
When adding, modifying, or deleting RIP next hops or route entries, the device records associated information to facilitate troubleshooting. To view the recorded information, execute the display rib nib record command.
As a best practice to avoid excessive system resource usage, set the maximum number of RIB next hop records or route entry records properly. When the maximum number is reached, the device can continue to record new information. The new records will overwrite the earliest records.
Procedure (IPv4)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv4 address family and enter its view.
address-family ipv4
4. Set the maximum number of RIB next hop records or route entry records.
record-limit limit [ rib nib [ flush [ delete | update ] | receive [ add | delete | update ] ] ]
record-limit limit [ routing-table [ flush [ delete | update ] | notify [ delete | update ] | receive [ add | delete | update ] ] ]
By default, the maximum number of RIB next hop records or route entry records is 1000.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enter RIB view.
rib
3. Create the RIB IPv6 address family and enter its view.
address-family ipv6
4. Set the maximum number of IPv6 RIB next hop records or route entry records.
record-limit limit [ rib nib [ flush [ delete | update ] | receive [ add | delete | update ] ] ]
record-limit limit [ routing-table [ flush [ delete | update ] | notify [ delete | update ] | receive [ add | delete | update ] ] ]
By default, the maximum number of IPv6 RIB next hop records or route entry records is 1000.
Enabling MTP
About this task
Use maintenance probe (MTP) to locate faults for routing protocols depending on your network maintenance requirements. MTP enables the device to automatically perform the following operations upon expiration of a neighbor's hold timer:
1. Ping the neighbor or trace the route to the neighbor.
2. Record the ping or tracert results.
To view fault information, use the display commands of routing protocols, for example, the display ospf troubleshooting command. To view detailed MTP information, use the display logbuffer command.
Procedure
1. Enter system view.
system-view
2. Enable MTP.
maintenance-probe enable
By default, MTP is disabled.
Enabling notifications for RIB
About this task
Use this feature to report critical RIB events to an NMS. For RIB event notifications to be sent correctly, you must also configure SNMP on the device. For more information about SNMP configuration, see the network management and monitoring configuration guide for the device.
Procedure (IPv6)
1. Enter system view.
system-view
2. Enable SNMP notifications for IPv6 RIB.
snmp-agent trap enable ipv6 rib
By default, SNMP notifications are enabled for IPv6 RIB.
Display and maintenance commands for basic IP routing
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display routing table information. |
display ip routing-table [ all-vpn-instance | vpn-instance vpn-instance-name ] [ priority { critical | high | low | medium } ] [ verbose ] display ip routing-table all-routes display ip routing-table [ vpn-instance vpn-instance-name ] fast-reroute |
|
Display information about routes permitted by an IPv4 basic ACL. |
display ip routing-table [ vpn-instance vpn-instance-name ] acl ipv4-acl-number [ verbose ] |
|
Display information about routes to a specific destination address. |
display ip routing-table [ vpn-instance vpn-instance-name ] ip-address [ mask-length | mask ] [ longer-match ] [ verbose ] display ip routing-table [ vpn-instance vpn-instance-name ] fast-reroute ip-address [ mask-length | mask ] |
|
Display information about routes to a range of destination addresses. |
display ip routing-table [ vpn-instance vpn-instance-name ] ip-address1 to ip-address2 [ verbose ] |
|
Display information about routes permitted by an IP prefix list. |
display ip routing-table [ vpn-instance vpn-instance-name ] prefix-list prefix-list-name [ verbose ] |
|
Display information about routes installed by a protocol. |
display ip routing-table [ vpn-instance vpn-instance-name ] protocol protocol [ fast-reroute | inactive | verbose ] |
|
Display IPv4 route entry records. |
display ip routing-table record flush [ delete | update ] [ verbose ] display ip routing-table record notify [ delete | update ] [ verbose ] display ip routing-table record receive [ add | delete | update ] [ verbose ] |
|
Display IPv4 route or route prefix statistics. |
display ip routing-table [ all-routes | all-vpn-instance | vpn-instance vpn-instance-name ] [ prefix ] statistics |
|
Display brief IPv4 routing table information. |
display ip routing-table [ vpn-instance vpn-instance-name ] summary |
|
Display route attribute information in the IPv6 RIB. |
display ipv6 rib attribute [ attribute-id ] |
|
Display IPv6 RIB GR state information. |
display ipv6 rib graceful-restart |
|
Display next hop information in the IPv6 RIB. |
display ipv6 rib nib [ self-originated ] [ nib-id ] [ verbose ] display ipv6 rib nib [ sub-nib nib-id ] [ verbose ] display ipv6 rib nib protocol protocol [ fast-reroute ] [ verbose ] |
|
Display next hop records in the IPv6 RIB. |
display ipv6 rib nib record flush [ delete | update ] [ verbose ] display ipv6 rib nib record receive [ add | delete | update ] [ verbose ] |
|
Display next hop information for IPv6 direct routes. |
display ipv6 route-direct nib [ nib-id ] [ verbose ] |
|
Display IPv6 routing table information. |
display ipv6 routing-table [ all-vpn-instance | vpn-instance vpn-instance-name ] [ priority { critical | high | low | medium } ] [ verbose ] display ipv6 routing-table all-routes display ipv6 routing-table [ all-vpn-instance | vpn-instance vpn-instance-name ] fast-reroute |
|
Display information about routes permitted by an IPv6 basic ACL. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] acl ipv6-acl-number [ verbose ] |
|
Display information about routes to an IPv6 destination address. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] ipv6-address [ prefix-length ] [ longer-match ] [ verbose ] display ipv6 routing-table [ vpn-instance vpn-instance-name ] fast-reroute ipv6-address [ prefix-length ] |
|
Display information about routes to a range of IPv6 destination addresses. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] ipv6-address1 to ipv6-address2 [ verbose ] |
|
Display information about routes permitted by an IPv6 prefix list. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] prefix-list prefix-list-name [ verbose ] |
|
Display information about routes installed by an IPv6 protocol. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] protocol protocol [ fast-reroute | inactive | verbose ] |
|
Display IPv6 route entry records. |
display ipv6 routing-table record flush [ delete | update ] [ verbose ] display ipv6 routing-table record notify [ delete | update ] [ verbose ] display ipv6 routing-table record receive [ add | delete | update ] [ verbose ] |
|
Display IPv6 route or route prefix statistics. |
display ipv6 routing-table [ all-routes | all-vpn-instance | vpn-instance vpn-instance-name ] [ prefix ] statistics |
|
Display brief IPv6 routing table information. |
display ipv6 routing-table [ vpn-instance vpn-instance-name ] summary |
|
Display route attribute information in the RIB. |
display rib attribute [ attribute-id ] |
|
Display RIB GR state information. |
display rib graceful-restart |
|
Display next hop information in the RIB. |
display rib nib [ self-originated ] [ nib-id ] [ verbose ] display rib nib [ sub-nib nib-id ] [ verbose ] display rib nib protocol protocol [ fast-reroute ] [ verbose ] |
|
Display next hop records in the RIB. |
display rib nib record flush [ delete | update ] [ verbose ] display rib nib record receive [ add | delete | update ] [ verbose ] |
|
Display next hop information for direct routes. |
display route-direct nib [ nib-id ] [ verbose ] |
|
Clear IPv4 routing entry records. |
reset ip routing-table record |
|
Clear IPv4 route statistics. |
reset ip routing-table statistics protocol [ vpn-instance vpn-instance-name ] { protocol | all } reset ip routing-table [ all-routes | all-vpn-instance ] statistics protocol { protocol | all } |
|
Clear next hop records in the IPv6 RIB. |
reset ipv6 rib nib record |
|
Clear IPv6 routing entry records. |
reset ipv6 routing-table record |
|
Clear IPv6 route statistics. |
reset ipv6 routing-table statistics protocol [ vpn-instance vpn-instance-name ] { protocol | all } reset ipv6 routing-table [ all-routes | all-vpn-instance ] statistics protocol { protocol | all } |
|
Clear next hop records in the IPv4 RIB. |
reset rib nib record |