- Table of Contents
-
- 01-Fundamentals Configuration Guide
- 00-Preface
- 01-CLI configuration
- 02-RBAC configuration
- 03-Login management configuration
- 04-FTP and TFTP configuration
- 05-File system management configuration
- 06-Configuration file management configuration
- 07-Software upgrade configuration
- 08-ISSU configuration
- 09-Device management configuration
- 10-Tcl configuration
- 11-Python configuration
- 12-License management
- 13-Preprovisioning feature configuration
- 14-Automatic configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 08-ISSU configuration | 247.82 KB |
Restrictions and guidelines: ISSU
Logging in to the device through the console port
Identifying availability of ISSU and licensing requirements
Verifying the device operating status
Verifying the device configuration
Determining the upgrade procedure
Adjusting and saving the running configuration
Performing an ISSU in one step
Performing an ISSU step by step by using issu commands
Performing a compatible upgrade on an IRF fabric
Performing an incompatible upgrade on an IRF fabric
Performing an incremental upgrade on a single-chassis IRF fabric
Performing a reboot or incompatible upgrade on a single-chassis IRF fabric
Performing an ISSU by using install commands
Rolling back the running software images
Aborting a software activate or deactivate operation
Deleting inactive software images
Display and maintenance commands for ISSU
Examples of using issu commands for ISSU
Example: Upgrading the system software to a compatible version
Example: Upgrading the system software to an incompatible version
Example: Rolling back the system software
Examples of using install commands for ISSU
Example: Rolling back a feature
Performing an ISSU
About ISSU
The In-Service Software Upgrade (ISSU) feature upgrades the Comware software with a minimum amount of downtime.
Unless otherwise stated, the term "upgrade" refers to both software upgrade and downgrade in ISSU.
ISSU advantages
The Comware software includes the boot image, the system image, and feature images. ISSU supports upgrading the images individually.
When you use ISSU to upgrade a feature, only the related feature images are affected. Other features can continue to provide services.
ISSU supports installing patch images to fix system bugs without a system reboot.
ISSU methods
ISSU methods are determined at software release depending on the compatibility between software versions.
ISSU supports the following upgrade types:
· Compatible upgrade—The new software version is compatible with the running software version. This upgrade type supports the ISSU methods in Table 1.
· Incompatible upgrade—The new software version is incompatible with the running software version. The two versions cannot run concurrently.
This upgrade type supports only one upgrade method (also called incompatible upgrade). This method requires a cold reboot to upgrade both control and data planes. Incompatible upgrade disrupts service if hardware redundancy is not available.
For information about identifying the ISSU method, see "Identifying the ISSU method."
Table 1 ISSU methods for compatible upgrade
|
ISSU method |
Description |
|
Incremental upgrade: · Service Upgrade · File Upgrade |
Upgrades only user mode processes that have differences between the new and old software versions. Backup processes and a main/backup process switchover are required for service continuity. · Service upgrade—Upgrades service features. The upgrade does not affect the operation of the features that are not being upgraded. · File upgrade—Upgrades hidden system program files. The system can provide services during the upgrade. |
|
Reboot |
The Reboot method disrupts service if hardware redundancy is not available. As a best practice, schedule the downtime carefully to minimize the upgrade impact on the services. Reboots member devices to complete the software upgrade. While one member device is rebooting, the other member devices can provide services. |
ISSU commands
ISSU includes the install and issu command sets. After you identify the recommended ISSU method, use Table 2 to choose the command set you want to use.
You can use the issu one-step command to perform an ISSU in one step, or use other ISSU commands to perform an ISSU step by step.
· During a one-step ISSU, you cannot perform a rollback.
· During a multi-step ISSU, you can display the device status, abort the ISSU, or perform a rollback.
Table 2 Command set comparison
|
Item |
issu commands |
install commands |
|
Upgrade types |
· Compatible. · Incompatible. |
Compatible. |
|
Patch installation and uninstallation |
Not supported. |
Supported. |
|
Impact on the system |
Large. |
Small. |
|
Technical skill requirements |
Low. As a best practice, use this command set. |
High. Administrators must have extensive system knowledge and understand the impact of each upgrade task on the network. |
|
One-step ISSU |
Supported. |
Not supported. |
|
Step-by-step ISSU |
Supported. |
Supported. |
Restrictions and guidelines: ISSU
During an ISSU, follow these restrictions and guidelines:
· Do not perform any of the following tasks:
¡ Reboot member devices.
¡ Execute commands that are irrelevant to the ISSU.
¡ Modify, delete, or rename image files.
· You cannot use both install and issu commands for the same ISSU. However, you can use display issu commands with both command sets. For more information, see "Display and maintenance commands for ISSU."
· For better service continuity, strictly follow the recommended ISSU procedure unless you are performing an ISSU in one step. Make sure a step is completed before you proceed to the next step.
· Before executing the issu load command the first time for an ISSU, use the display issu state command to verify that the ISSU status is Init. You can start an ISSU only if the ISSU status is Init.
· Before executing the following commands, use the display system stable state command to verify that the system is stable:
¡ issu commands—issu one-step, issu load, issu run switchover, and issu commit.
¡ install commands—install activate and install deactivate.
If the System State field displays Stable, the system is stable.
· You may use issu commands to upgrade all or some of the software images. If you are upgrading only some of the images, make sure the new images are compatible with the images that are not to be upgraded. The upgrade will fail if a conflict exists.
· To perform a compatible upgrade in advanced operating mode, do not configure an FCoE mode if the current or new version does not support port security in a VSAN. For more information about operating modes, see "Managing the device." For more information about FC port security and FCoE mode, see FC and FCoE Configuration Guide.
After an ISSU, follow these restrictions and guidelines:
· You must log in to the device again before you can use the changed or added commands.
· Use the display boot-loader command to display the startup image files. For the device to start up correctly, make sure the files are not deleted.
Prerequisites for ISSU
To perform a successful ISSU, make sure all the preparation requirements are met.
Logging in to the device through the console port
Log in to the device through the console port. If you use Telnet or SSH, you might be disconnected from the device before the ISSU is completed.
In a multiuser environment, make sure no other administrators access the device while you are performing the ISSU.
Identifying availability of ISSU and licensing requirements
Read the software release notes to identify the following items:
· Support of the device for ISSU between the current software version and the new software version.
· Licensing requirements for the upgrade software images. If the upgrade software images require licenses, make sure the device has the required licenses. For more information about license installation, see "Managing licenses."
Verifying the device operating status
Verify the following items:
· Use the display device command to verify that all installed components are in Master, Standby, or Normal state.
· Use the display irf command to verify that all IRF member devices are operating correctly.
· Use the display cpu-usage command to display the CPU usage statistics. The CPU usage must be lower than the minor alarm threshold. As a best practice, make sure the CPU usage is lower than the recovery threshold.
· Use the display memory and display memory-threshold commands to display the free memory information. The amount of free memory must be lower than the early-warning threshold. As a best practice, make sure the amount of free memory is greater than the sufficient-memory threshold.
· Use the display fan command to verify that all fans are in Normal state.
· Use the display power command to verify that all power supplies are in Normal state.
· Use the display environment command to verify that the temperature readings of all sensors are lower than the warning temperature thresholds.
· Use the display counters rate inbound interface and display interface | include CRC commands to verify that all ports are forwarding traffic correctly.
Preparing the upgrade images
1. Use the dir command to verify that every file system has sufficient free storage space for the upgrade images. If the storage space is not sufficient, delete unused files by using the delete /unreserved file-url command. If the files to be deleted will be used, back up the files before deleting them. You will be unable to restore a deleted file if the /unreserved keyword is used. For more information, see "Managing file systems."
2. Use FTP or TFTP to transfer upgrade image files (in .bin or .ipe) to the root directory of a file system on the master device.
Identifying the ISSU method
1. Execute the display version comp-matrix file command to display the recommended ISSU methods.
¡ If a compatible upgrade is required, check the Upgrade Way field to identify the recommended ISSU method.
¡ If an incompatible upgrade is required, check the end of command output for the Incompatible upgrade string.
For more information about ISSU methods, see Table 1.
Verifying the device configuration
For a successful incompatible upgrade and the IRF fabric integrity during the ISSU, a set of features must have the same configuration as expected after the upgrade. The following are the features and the commands for you to change and verify feature settings:
· System operating mode.
system-working-mode
display system-working-mode
· IPv4 enhanced ECMP mode.
display ecmp mode
· VXLAN hardware resource mode.
hardware-resource vxlan
display hardware-resource vxlan
For more information about system operating mode, see device management in Fundamentals Configuration Guide.
For more information about IPv4 enhanced ECMP mode, see basic IP routing configuration in Layer 3—IP Routing Configuration Guide.
For more information about VXLAN hardware resource mode, see VXLAN Configuration Guide.
Verifying feature status
For service continuity during an ISSU, configure the following feature settings:
|
Feature |
Setting requirements |
|
GR and NSR |
Enable GR or NSR for protocols including LDP, RSVP, OSPF, ISIS, BGP, and FSPF. |
|
BFD |
Disable BFD for protocols including LDP, RSVP, OSPF, ISIS, RIP, BGP, VRRP, and NQA. |
|
Ethernet link aggregation |
Use the long LACP timeout interval (the lacp period short command is not configured) on all member ports in dynamic aggregation groups. Make sure all member ports are Selected ports. |
|
IRF |
Before performing an incompatible upgrade for the IRF fabric, verify that IRF MAD is disabled. To use IRF MAD, enable IRF MAD after finishing the upgrade. Configure IRF bridge MAC persistence as follows: · Compatible upgrade—Configure the irf mac-address persistent timer or irf mac-address persistent always command. · Incompatible upgrade—Configure the irf mac-address persistent always command if the bridge MAC address is the MAC address of the device for which you want to execute the issu load command. |
Determining the upgrade procedure
1. Use Table 2 to choose an upgrade command set, depending on the ISSU method.
2. Identify the hardware redundancy condition.
ISSU can maintain service continuity only when the following conditions are met:
¡ The IRF fabric has multiple members and uses the ring topology.
|
IMPORTANT: If hardware redundancy is not available, service discontinuity is not avoidable during a reboot upgrade or an incompatible upgrade. Make sure you understand the impact of the upgrade on the network. |
3. Perform one of the following tasks:
¡ Choose one-step ISSU to start and finish an ISSU by using a single command, as described in "Performing an ISSU in one step."
¡ Choose the correct procedure from the procedures described in "Performing an ISSU step by step by using issu commands" or "Performing an ISSU by using install commands."
Adjusting and saving the running configuration
1. Remove the configured commands that the new software version does not support.
2. Use the save command to save the running configuration.
Performing an ISSU in one step
Restrictions and guidelines
During a one-step upgrade, you cannot perform a rollback or any other tasks.
If the IRF fabric has multiple member devices, follow these guidelines:
· Make sure both the current software version and the new software version support one-step ISSU.
· For a compatible upgrade, specify one subordinate member for the command. The member device will become the master device after the ISSU.
Procedure
To perform an ISSU in one step, execute one of the following commands in user view:
· Use .bin files:
issu one-step file { boot filename | system filename | feature filename&<1-30> } * [ slot slot-number ] [ reboot ]
· Use an .ipe file:
issu one-step file ipe ipe-filename slot slot-number [ reboot ]
Specify the slot number of the subordinate member for the command.
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it sets and loads that image as a main startup image. If the digital signature verification fails, the system will not set or load the image as a main startup image and you will receive a digital signature verification failure message. |
Performing an ISSU step by step by using issu commands
Performing a compatible upgrade on an IRF fabric
Restrictions and guidelines
Upgrade the subordinate member device first. Then, upgrade the original master.
Procedure
1. (Optional.) Configure automatic rollback:
a. Enter system view.
system-view
b. Set the automatic rollback timer.
issu rollback-timer minutes
By default, the automatic rollback timer is set to 45 minutes.
The automatic rollback timer starts when you execute the issu run switchover command.
c. Return to user view.
quit
2. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step.
3. Load the upgrade images as startup images on a subordinate member.
¡ Use .bin files:
issu load file { boot filename | system filename | feature filename&<1-30> } * slot slot-number [ reboot ]
¡ Use an .ipe file:
issu load file ipe ipe-filename slot slot-number [ reboot ]
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it sets and loads that image as a main startup image. If the digital signature verification fails, the system will not set or load the image as a main startup image and you will receive a digital signature verification failure message. |
4. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step. If the system reported an error in the previous step, verify that the system is stable and then use the issu rollback command to roll back the upgrade.
5. Perform an ISSU switchover.
issu run switchover
This command also starts the automatic rollback timer. When the timer expires, the system automatically rolls back to the original software images.
6. (Optional.) Accept the upgrade and delete the automatic rollback timer.
issu accept
Execute this command before the automatic rollback timer expires.
7. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step. If the system reported an error in the previous two steps, verify that the system is stable and then use the issu rollback command to roll back the upgrade.
8. Upgrade the original master to complete the ISSU.
issu commit slot slot-number
Execute this command before the automatic rollback timer expires.
|
CAUTION: The ISSU process cannot be rolled back automatically or manually after you execute this command. When the ISSU commit operation is completed, the ISSU status changes to Init. |
9. Verify that the ISSU is finished.
display issu state
If the ISSU state field displays Init, the ISSU is finished.
Performing an incompatible upgrade on an IRF fabric
Restrictions and guidelines
Upgrade the subordinate member device first. Then, upgrade the original master.
Procedure
To perform an incompatible upgrade on an IRF fabric, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step.
2. Load the upgrade images as startup images on subordinate members.
¡ Use .bin files:
issu load file { boot filename | system filename | feature filename&<1-30> } * slot slot-number [ reboot ]
¡ Use an .ipe file:
issu load file ipe ipe-filename slot slot-number [ reboot ]
As a best practice on a ring-topology IRF fabric, specify half of the subordinate members for this command to reduce service interruption. Make sure the specified subordinate members are physically connected.
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it sets and loads that image as a main startup image. If the digital signature verification fails, the system will not set or load the image as a main startup image and you will receive a digital signature verification failure message. |
3. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step. If the system reported an error in the previous step, verify that the system is stable and then use the issu rollback command to roll back the upgrade.
4. Perform an ISSU switchover to complete the ISSU process.
issu run switchover
This command upgrades the remaining members.
5. Verify that the ISSU is finished.
display issu state
If the ISSU state field displays Init, the ISSU is finished.
Performing an incremental upgrade on a single-chassis IRF fabric
To perform an incremental upgrade on a single-chassis IRF fabric, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step.
2. Load the upgrade images as startup images.
¡ Use .bin files:
issu load file { boot filename | system filename | feature filename&<1-30> } * slot slot-number [ reboot ]
¡ Use an .ipe file:
issu load file ipe ipe-filename slot slot-number [ reboot ]
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it sets and loads that image as a main startup image. If the digital signature verification fails, the system will not set or load the image as a main startup image and you will receive a digital signature verification failure message. |
3. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step. If the system reported an error in the previous step, verify that the system is stable and then use the issu rollback command to roll back the upgrade.
4. Complete the ISSU process.
issu commit slot slot-number
|
CAUTION: The ISSU process cannot be rolled back automatically or manually after you execute this command. When the ISSU commit operation is completed, the ISSU status changes to Init. |
5. Verify that the ISSU is finished.
display issu state
If the ISSU state field displays Init, the ISSU is finished.
Performing a reboot or incompatible upgrade on a single-chassis IRF fabric
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step.
2. Load the parent device's upgrade images as startup images on subordinate members.
¡ Use .bin files:
issu load file { boot filename | system filename | feature filename&<1-30> } * slot slot-number [ reboot ]
¡ Use an .ipe file:
issu load file ipe ipe-filename slot slot-number [ reboot ]
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it sets and loads that image as a main startup image. If the digital signature verification fails, the system will not set or load the image as a main startup image and you will receive a digital signature verification failure message. |
3. Verify that the ISSU is finished.
display issu state
If the ISSU state field displays Init, the ISSU is finished.
Performing an ISSU by using install commands
ISSU tasks at a glance
1. (Optional.) Decompressing an .ipe file
3. (Optional.) Deactivating software images
4. (Optional.) Rolling back the running software images
5. (Optional.) Aborting a software activate or deactivate operation
6. (Optional.) Verifying software images
7. Committing software changes
8. (Optional.) Deleting inactive software images
Decompressing an .ipe file
1. (Optional.) Identify images that are included in the .ipe file.
display install ipe-info
2. Decompress the .ipe file.
install add ipe-filename filesystem
Activating software images
About software image activation
Use this task to install new features or upgrade the boot, system, or feature images.
Software image activation methods
Use one of the following methods to activate software images:
· Slot by slot—Activate all the images on one slot, and then move to the next slot.
· Image by image—Activate one image on all slots before activating another image.
Restrictions and guidelines
To install an image, you must begin with the master device. To upgrade an image, you must begin with a subordinate device.
The activate operation for an incremental upgrade or patch images only updates the current software image list. For the image changes to take effect after a reboot, you must perform a commit operation to update the main startup image list.
You can install up to 32 .bin files on the device, including one boot image file, one system image file, and up to 30 feature or patch image files.
Prerequisites
Before activating patch images, check whether the device is already running patch images.
· If not, activate patch images.
· If yes, read the release notes to identify the functionality differences between the running patch images and the new patch images.
¡ If the new patch images cover all functions provided by the old patch images, activating the new patch images overwrites the old patch images. After activating the new patch images, deactivate and delete the old patch images to remove them from software image lists and release the storage space.
¡ If the new patch images do not cover one or more functions provided by the old patch images, activating the patch images does not affect the old patch images. The device uses both the new patch images and the old patch images. Do not deactivate or delete the old patch images.
Activating boot, system, and feature images
To activate boot, system, and feature images, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful ISSU, you must make sure the system is stable before you proceed to the next step.
2. (Optional.) Identify the recommended ISSU method and the possible impact of the upgrade.
install activate { boot filename | system filename | feature filename&<1-30> } * slot slot-number test
3. Activate images.
install activate { boot filename | system filename | feature filename&<1-30> } * slot slot-number
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a software image for authenticity and integrity before it activates it. If the digital signature verification fails, the system will not activate the image and you will receive a digital signature verification failure message. |
Activating patch images
To activate patch images, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful installation, you must make sure the system is stable before you proceed to the next step.
2. Activate patch images.
install activate patch filename { all | slot slot-number }
|
|
NOTE: The software images for the device are digitally signed. The system verifies the digital signature of a patch image for authenticity and integrity before it activates it. If the digital signature verification fails, the system will not activate the image and you will receive a digital signature verification failure message. |
Deactivating software images
Restrictions and guidelines
You can deactivate only feature and patch images.
The deactivate operation only removes images from the current software image list. For the image changes to take effect after a reboot, you must perform a commit operation to remove the images from the main startup image list.
Deactivated images are still stored on the storage medium. To permanently delete the images, execute the install remove command. For more information, see "Deleting inactive software images."
Deactivating feature images
To deactivate feature images, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful deactivate operation, you must make sure the system is stable before you proceed to the next step.
2. Deactivate feature images.
install deactivate feature filename&<1-30> slot slot-number
Deactivating patch images
To deactivate patch images, execute the following commands in user view:
1. Verify that the system is stable.
display system stable state
The system is stable if the System State field displays Stable. For a successful deactivate operation, you must make sure the system is stable before you proceed to the next step.
2. Deactivate patch images.
install deactivate patch filename { all | slot slot-number }
Rolling back the running software images
About software image rollback
During an incremental upgrade, the system creates a rollback point for each activate or deactivate operation of a boot, system, or feature image. The system can maintain a maximum of 50 rollback points. If this limit has been reached when a rollback point is created, the system removes the earliest rollback point. You can roll back the software to any of the rollback points.
During a reboot upgrade, the system does not create rollback points. After a reboot upgrade, you can roll back the software only to the status before any activate or deactivate operations were performed.
Restrictions and guidelines
During an incremental upgrade, you can perform this task only before committing software changes. A commit operation deletes all rollback points..
For an incremental upgrade rollback to take effect after a reboot, you must perform a commit operation to update the main startup image list.
Procedure
To roll back the running software images, execute the following commands in user view:
1. (Optional.) Display available rollback points.
display install rollback
2. Roll back the software.
install rollback to { point-id | original }
Aborting a software activate or deactivate operation
About aborting a software activate or deactivate operation
While the system is activating or deactivating a software image for a service upgrade or file upgrade, you can abort the activate or deactivate operation. After an operation is aborted, the system runs with the software images that it was running with before the operation.
Procedure
To abort a software activate or deactivate operation, use one of the following methods:
· Execute the install abort [ job-id ] command in user view.
· Press Ctrl+C.
Committing software changes
About committing software changes
When you activate or deactivate images for an incremental upgrade, or activate or deactivate patch images, the main startup image list does not update with the changes. The software changes are lost at reboot. For the changes to take effect after a reboot, you must commit the changes.
Procedure
To commit software changes, execute the following command in user view:
install commit
Verifying software images
About software image verification
Perform this task to verify the following items:
· Integrity—Verify that the boot, system, and feature images are integral.
· Consistency—Verify that the same active images are running across the entire system.
· Software commit status—Verify that the active images are committed as needed.
Procedure
To verify software images, execute the following commands in user view:
1. Verify software images.
install verify
2. Activate or deactivate images as required.
install { activate | deactivate }
3. Commit the software changes.
install commit
Deleting inactive software images
About deleting inactive software images
After completing an ISSU, you can use this task to delete old image files permanently.
Restrictions and guidelines
This task delete image files permanently. You cannot use the install rollback to command to revert the operation, or use the install abort command to abort the operation.
Procedure
To delete inactive software image files, execute the following command in user view:
install remove [ slot slot-number ] { filename | inactive }
Display and maintenance commands for ISSU
|
CAUTION: The reset install rollback oldest command clears the specified rollback point and all rollback points earlier than the specified rollback point. You will be unable to roll back the configuration to the status when any of these rollback points was created. |
Unless otherwise stated, the display and reset commands can be used during an ISSU, regardless of whether the install or issu commands are used.
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
Remarks |
|
Display active software images. |
display install active [ slot slot-number ] [ verbose ] |
N/A |
|
Display backup startup software images. |
display install backup [ slot slot-number ] [ verbose ] |
N/A |
|
Display main startup software images. |
display install committed [ slot slot-number ] [ verbose ] |
N/A |
|
Display inactive software images in the root directories of file systems. |
display install inactive [ slot slot-number ] [ verbose ] |
N/A |
|
Display the software images included in an .ipe file. |
display install ipe-info ipe-filename |
N/A |
|
Display ongoing ISSU activate, deactivate, and rollback operations. |
display install job |
N/A |
|
Display ISSU log entries. |
display install log [ log-id ] [ verbose ] |
N/A |
|
Display software image file information. |
display install package { filename | all } [ verbose ] |
N/A |
|
Display rollback point information. |
display install rollback [ point-id ] |
The system does not record rollback points during an ISSU that uses issu commands. |
|
Display the software image file that includes a specific component or file. |
display install which { component name | file filename } [ slot slot-number ] |
N/A |
|
Display automatic rollback timer information. |
N/A |
|
|
Display ISSU status information. |
display issu state |
This command applies only to an ISSU that uses issu commands. |
|
Display the recommended ISSU methods. |
display version comp-matrix file { boot filename | system filename | feature filename&<1-30> } * display version comp-matrix file ipe ipe-filename |
N/A |
|
Clear ISSU log entries. |
reset install log-history oldest log-number |
N/A |
|
Clear ISSU rollback points. |
reset install rollback oldest point-id |
N/A |
Examples of using issu commands for ISSU
Example: Upgrading the system software to a compatible version
Network configuration
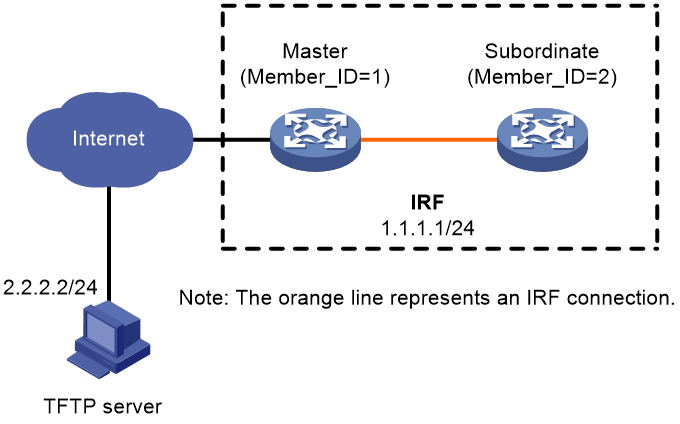
As shown in Figure 1, the IRF fabric has two members.
Upgrade the boot, system, and feature images from T0001015 to T0001016. The two versions are compatible.
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
# Download the upgrade image files from the TFTP server.
<Sysname> tftp 2.2.2.2 get boot-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6078464 100 6078464 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get system-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 97750016 100 97750016 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get feature-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1008640 100 1008640 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
# Identify the recommended ISSU methods.
<Sysname> display version comp-matrix file boot flash:/boot-t0001016.bin system flash:/system-t0001016.bin feature flash:/feature-t0001016.bin
Verifying the file flash:/boot-t0001016.bin on slot 1.......................Done.
Verifying the file flash:/system-t0001016.bin on slot 1................. .................Done.
Verifying the file flash:/feature-t0001016.bin on slot 1.................Done.
Identifying the upgrade methods....Done.
Slot Upgrade Way
1 Reboot
2 Reboot
The output shows that reboot upgrades are recommended.
# Save the running configuration.
<Sysname> save
# Upgrade the system software on the subordinate member.
<Sysname> issu load file boot flash:/boot-t0001016.bin system flash:/system-t0001016.bin feature flash:/feature-t0001016.bin slot 2
This operation will delete the rollback point information for the previous upgrade and maybe get unsaved configuration lost. Continue? [Y/N]:y
Copying file flash:/boot-t0001016.bin to slot2#flash:/boot-t0001016.bin......Done.
Copying file flash:/system-t0001016.bin to slot2#flash:/system-t0001016.bin........................Done.
Copying file flash:/feature-t0001016.bin to slot2#flash:/feature-t0001016.bin......Done.
Verifying the file flash:/boot-t0001016.bin on slot 2...Done.
Verifying the file flash:/system-t0001016.bin on slot 2............Done.
Verifying the file flash:/feature-t0001016.bin on slot 2...Done.
Identifying the upgrade methods….Done.
Upgrade summary according to following table:
flash:/boot-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/system-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/feature-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
2 Reboot
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
# Verify that the ISSU is in a stable state.
<Sysname> display issu state
ISSU state: Loaded
Compatibility: Compatible
Work state: Normal
Upgrade method: Card by card
Upgraded slot:
slot 2
Current upgrading slot: None
Previous version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Previous software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Upgrade version list:
boot: 7.1.070, Test 0001016
system: 7.1.070, Test 0001016
feature: 7.1.070, Test 0001016
Upgrade software images:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
The Loaded state is a stable state, which indicates that the system is waiting for a master/subordinate switchover. Slot 2 has completed the upgrade, and slot 1 has not.
# Perform a master/subordinate switchover.
<Sysname> issu run switchover
Upgrade summary according to following table:
flash:/boot-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/system-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/feature-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Switchover Way
1 Master subordinate switchover
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait.........
# Verify that the ISSU is in a stable state.
<Sysname> display issu state
ISSU state: Switchover
Compatibility: Compatible
Work state: Normal
Upgrade method: Card by card
Upgraded slot:
slot 2
Current upgrading slot: None
Previous version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Previous software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Upgrade version list:
boot: 7.1.070, Test 0001016
system: 7.1.070, Test 0001016
feature: 7.1.070, Test 0001016
Upgrade software images:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
The Switchover state is a stable state, which indicates that the system has completed the master/subordinate switchover and is waiting for a commit operation to upgrade slot 1.
# Upgrade the system software on the original master.
<Sysname> issu commit slot 1
Upgrade summary according to following table:
flash:/boot-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/system-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/feature-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
1 Reboot
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
Verifying the upgrade
# Verify that the ISSU is finished.
<Sysname> display issu state
ISSU state: Init
Compatibility: Unknown
Work state: Normal
Upgrade method: Card by card
Upgraded slot: None
Current upgrading slot: None
Current version list:
boot: 7.1.070, Test 0001016
system: 7.1.070, Test 0001016
feature: 7.1.070, Test 0001016
Current software images:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
The ISSU state field displays Init, which indicates that the ISSU is finished.
# Verify that both members are running the new software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
Active packages on slot 2:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
Example: Upgrading the system software to an incompatible version
Network configuration
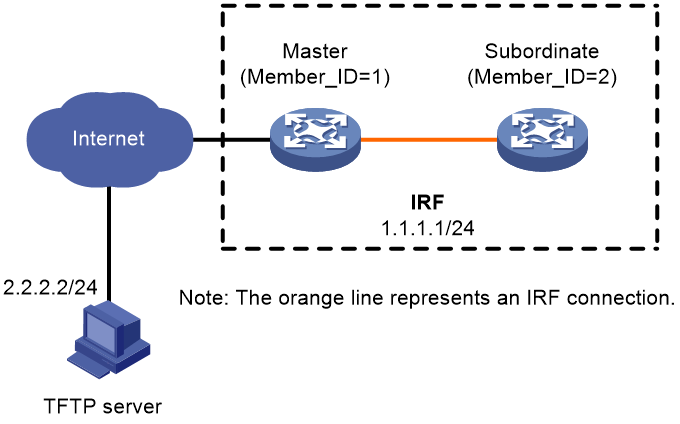
As shown in Figure 2, the IRF fabric has two members.
Upgrade the boot, system, and feature images from T0001015 to T0001017, which is an incompatible version.
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
# Download the upgrade image files from the TFTP server.
<Sysname> tftp 2.2.2.2 get boot-t0001017.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6078464 100 6078464 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get system-t0001017.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 97750016 100 97750016 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get feature-t0001017.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1008640 100 1008640 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
# Identify the recommended ISSU methods.
<Sysname> display version comp-matrix file boot flash:/boot-t0001017.bin system flash:/system-t0001017.bin feature flash:/feature-t0001017.bin
Verifying the file flash:/boot-t0001017.bin on slot 1.......................Done.
Verifying the file flash:/system-t0001017.bin on slot 1................. .................Done.
Verifying the file flash:/feature-t0001017.bin on slot 1.................Done.
Identifying the upgrade methods....Done.
Incompatible upgrade.
The output shows that an incompatible upgrade is recommended.
# Save the running configuration.
<Sysname> save
# Upgrade the system software on the subordinate member.
<Sysname> issu load file boot flash:/boot-t0001017.bin system flash:/system-t0001017.bin feature flash:/feature-t0001017.bin slot 2
This operation will delete the rollback point information for the previous upgrade and maybe get unsaved configuration lost. Continue? [Y/N]:y
Copying file flash:/boot-t0001017.bin to slot2#flash:/boot-t0001017.bin......Done.
Copying file flash:/system-t0001017.bin to slot2#flash:/system-t0001017.bin........................Done.
Copying file flash:/feature-t0001017.bin to slot2#flash:/feature-t0001017.bin......Done.
Verifying the file flash:/boot-t0001017.bin on slot 2...Done.
Verifying the file flash:/system-t0001017.bin on slot 2............Done.
Verifying the file flash:/feature-t0001017.bin on slot 2...Done.
Identifying the upgrade methods….Done.
Upgrade summary according to following table:
flash:/boot-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
flash:/system-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
flash:/feature-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
Slot Upgrade Way
2 Reboot
Upgrading software images to incompatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
# Verify that the ISSU is in a stable state.
<Sysname> display issu state
ISSU state: Loaded
Compatibility: Incompatible
Work state: Normal
Upgrade method: Card by card
Upgraded slot:
slot 2
Current upgrading slot: None
Previous version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Previous software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Upgrade version list:
boot: 7.1.070, Test 0001017
system: 7.1.070, Test 0001017
feature: 7.1.070, Test 0001017
Upgrade software images:
flash:/boot-t0001017.bin
flash:/system-t0001017.bin
flash:/feature-t0001017.bin
The Loaded state is a stable state, which indicates that the system is waiting for a master/subordinate switchover. Slot 2 has completed the upgrade, and slot 1 has not.
# Perform a master/subordinate switchover.
<Sysname> issu run switchover
Upgrade summary according to following table:
flash:/boot-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
flash:/system-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
flash:/feature-t0001017.bin
Running Version New Version
Test 0001015 Test 0001017
Slot Switchover Way
1 Master subordinate switchover
Verifying the upgrade
# Verify that the ISSU is finished.
<Sysname> display issu state
ISSU state: Init
Compatibility: Unknown
Work state: Normal
Upgrade method: Card by card
Upgraded slot: None
Current upgrading slot: None
Current version list:
boot: 7.1.070, Test 0001017
system: 7.1.070, Test 0001017
feature: 7.1.070, Test 0001017
Current software images:
flash:/boot-t0001017.bin
flash:/system-t0001017.bin
flash:/feature-t0001017.bin
The ISSU state field displays Init, which indicates that the ISSU is finished.
# Verify that both members are running the new software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001017.bin
flash:/system-t0001017.bin
flash:/feature-t0001017.bin
Active packages on slot 2:
flash:/boot-t0001017.bin
flash:/system-t0001017.bin
flash:/feature-t0001017.bin
Example: Rolling back the system software
Network configuration
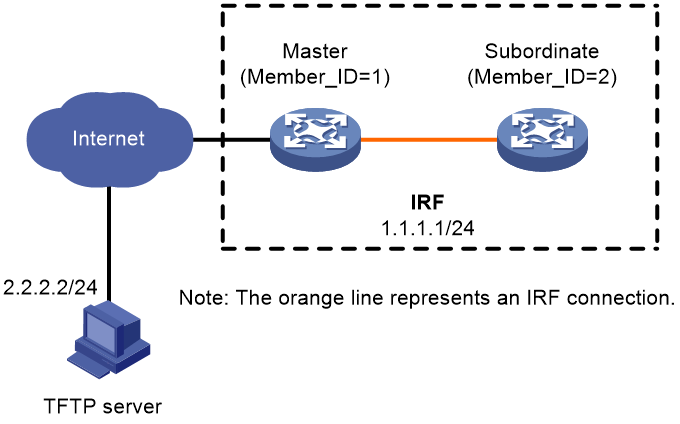
As shown in Figure 3, the IRF fabric has two members.
Roll back the boot, system, and feature images from T0001016 to T0001015 after upgrading them from T0001015 to T0001016. T0001016 and T0001015 are compatible.
Procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
# Download the upgrade image files from the TFTP server.
<Sysname> tftp 2.2.2.2 get boot-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6078464 100 6078464 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get system-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 97750016 100 97750016 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
<Sysname> tftp 2.2.2.2 get feature-t0001016.bin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1008640 100 1008640 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
# Identify the recommended ISSU methods.
<Sysname> display version comp-matrix file boot flash:/boot-t0001016.bin system flash:/system-t0001016.bin feature flash:/feature-t0001016.bin
Verifying the file flash:/all.ipe on slot 1................. .................Done.
Identifying the upgrade methods....Done.
Slot Upgrade Way
1 Reboot
2 Reboot
The output shows that reboot upgrades are recommended.
# Save the running configuration.
<Sysname> save
# Upgrade the system software on the subordinate member.
<Sysname> issu load file boot flash:/boot-t0001016.bin system flash:/system-t0001016.bin feature flash:/feature-t0001016.bin slot 2
This operation will delete the rollback point information for the previous upgrade and maybe get unsaved configuration lost. Continue? [Y/N]:y
Copying file flash:/boot-t0001016.bin to slot2#flash:/boot-t0001016.bin......Done.
Copying file flash:/system-t0001016.bin to slot2#flash:/system-t0001016.bin........................Done.
Copying file flash:/feature-t0001016.bin to slot2#flash:/feature-t0001016.bin......Done.
Verifying the file flash:/boot-t0001016.bin on slot 2...Done.
Verifying the file flash:/system-t0001016.bin on slot 2............Done.
Verifying the file flash:/feature-t0001016.bin on slot 2...Done.
Identifying the upgrade methods….Done.
Upgrade summary according to following table:
flash:/boot-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/system-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/feature-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
2 Reboot
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
# Verify that the ISSU is in a stable state.
<Sysname> display issu state
ISSU state: Loaded
Compatibility: Compatible
Work state: Normal
Upgrade method: Card by card
Upgraded slot:
slot 2
Current upgrading slot: None
Previous version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Previous software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Upgrade version list:
boot: 7.1.070, Test 0001016
system: 7.1.070, Test 0001016
feature: 7.1.070, Test 0001016
Upgrade software images:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
The Loaded state is a stable state, which indicates that the system is waiting for a master/subordinate switchover. Slot 2 has completed the upgrade, and slot 1 has not.
# Perform a master/subordinate switchover.
<Sysname> issu run switchover
Upgrade summary according to following table:
flash:/boot-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/system-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
flash:/feature-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Switchover Way
1 Master subordinate switchover
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait.........
# Verify that the ISSU is in a stable state.
<Sysname> display issu state
ISSU state: Switchover
Compatibility: Compatible
Work state: Normal
Upgrade method: Card by card
Upgraded slot:
slot 2
Current upgrading slot: None
Previous version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Previous software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Upgrade version list:
boot: 7.1.070, Test 0001016
system: 7.1.070, Test 0001016
feature: 7.1.070, Test 0001016
Upgrade software images:
flash:/boot-t0001016.bin
flash:/system-t0001016.bin
flash:/feature-t0001016.bin
The Switchover state is a stable state, which indicates that the system has completed the master/subordinate switchover and is waiting for a commit operation to upgrade slot 1.
# Roll back the software images to T0001015.
<Sysname> issu rollback
This command will quit the ISSU process and roll back to the previous version. Continue? [Y/N]:Y
# Verify that the rollback is finished.
<Sysname> display issu state
ISSU state: Init
Compatibility: Unknown
Work state: Normal
Upgrade method: Card by card
Upgraded slot: None
Current upgrading slot: None
Current version list:
boot: 7.1.070, Test 0001015
system: 7.1.070, Test 0001015
feature: 7.1.070, Test 0001015
Current software images:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
The ISSU state field displays Init, which indicates that the rollback is finished.
# Verify that both members are running the old software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature-t0001015.bin
Examples of using install commands for ISSU
Example: Upgrading a feature
Upgrade requirements
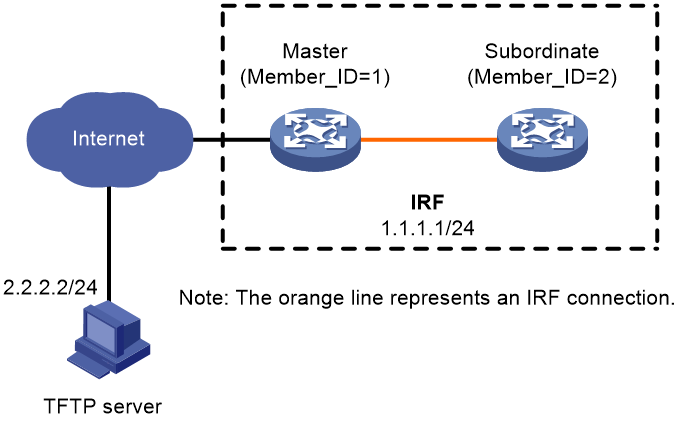
As shown in Figure 4, the IRF fabric has two members.
Upgrade the Feature1 feature from T0001015 to T0001016. The two versions are compatible.
Upgrade procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
# Download the .ipe file that contains the T0001016 Feature1 feature image from the TFTP server.
<Sysname> tftp 2.2.2.2 get feature1-t0001016.ipe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 256 100 256 0 0 764 0 --:--:-- --:--:-- --:--:-- 810
Writing file...Done.
# Decompress the .ipe file.
<Sysname> install add flash:/feature1-t0001016.ipe flash:
Verifying the file flash:/feature1-t0001016.ipe on slot 1...Done.
Decompressing file feature1-t0001016.bin to flash:/feature1-t0001016.bin.......................Done.
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin
# Identify the recommended ISSU methods.
<Sysname> install activate feature flash:/feature1-t0001016.bin slot 2 test
Copying file flash:/feature1-t0001016.bin to slot2#flash:/feature1-t0001016.bin......Done.
Verifying the file flash:/feature1-t0001016.bin on slot 2...Done.
Upgrade summary according to following table:
flash:/feature1-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
2 Service Upgrade
Influenced service according to following table on slot 2:
flash:/feature1-t0001016.bin
Feature1
<Sysname> install activate feature flash:/feature1-t0001016.bin slot 1 test
Verifying the file flash:/feature1-t0001016.bin on slot 1...Done.
Upgrade summary according to following table:
flash:/feature1-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
1 Service Upgrade
Influenced service according to following table on slot 1:
flash:/feature1-t0001016.bin
Feature1
The output shows that both members need a service upgrade and the Feature1 module will be rebooted during the upgrade.
# Activate the new Feature1 image to upgrade the Feature1 feature.
<Sysname> install activate feature flash:/feature1-t0001016.bin slot 2
Verifying the file flash:/feature1-t0001016.bin on slot 1...Done.
flash:/feature1-t0001016.bin already exists on slot 2.
Overwrite it?[Y/N]:y
Copying file flash:/feature1-t0001016.bin to slot2#flash:/feature1-t0001016.bin......Done.
Verifying the file flash:/feature1-t0001016.bin on slot 2...Done.
Upgrade summary according to following table:
flash:/feature1-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
2 Service Upgrade
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
<Sysname> install activate feature flash:/feature1-t0001016.bin slot 1
Verifying the file flash:/feature1-t0001016.bin on slot 1...Done.
Upgrade summary according to following table:
flash:/feature1-t0001016.bin
Running Version New Version
Test 0001015 Test 0001016
Slot Upgrade Way
1 Service Upgrade
Upgrading software images to compatible versions. Continue? [Y/N]:y
This operation might take several minutes, please wait...Done.
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
# Commit the software changes.
<Sysname> install commit
This operation will take several minutes, please wait...........................Done.
The current software images have been saved as the startup software images.
Current software images on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
Current software images on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
Example: Rolling back a feature
Rollback requirement
As shown in Figure 4, the IRF fabric has two members. The Feature1 feature has been upgraded from T0001015 to T0001016. However, the software change has not been committed.
Roll back the Feature1 feature from T0001016 to T0001015.
Rollback procedure
|
IMPORTANT: By default, interfaces on the device are disabled (in ADM or Administratively Down state). To have an interface operate, you must use the undo shutdown command to enable that interface. |
# Display active software images.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001016.bin
# Display available rollback points.
<Sysname> display install rollback
Install rollback information 1 on slot 1:
Updating from flash:/feature1-t0001015.bin
to flash:/feature1-t0001016.bin.
Install rollback information 2 on slot 2:
Updating from flash:/feature1-t0001015.bin
to flash:/feature1-t0001016.bin.
# Roll back the Feature1 feature to T0001015.
<Sysname> install rollback to original
This operation might take several minutes, please wait...Done.
# Verify that the IRF members are running the old Feature1 image.
<Sysname> display install active
Active packages on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin
Active packages on slot 2:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin
# Commit the software changes.
<Sysname> install commit
This operation will take several minutes, please wait...........................Done.
The current software images have been saved as the startup software images.
Current software images on slot 0:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin
Current software images on slot 1:
flash:/boot-t0001015.bin
flash:/system-t0001015.bin
flash:/feature1-t0001015.bin