- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-H3C Access Points Login Management Configuration | 227.75 KB |
|
H3C Access Points |
|
Login Management Configuration |
New H3C Technologies Co., Ltd.
http://www.h3c.com
Document version: 6W100-20220830
Contents
Supported device access methods
Supported initial access methods and default login settings
Logging to the device through console login for the first time
Restrictions and guidelines: CLI login configuration
Display and maintenance commands for CLI login
Restrictions and guidelines: Web login configuration
Web login configuration tasks at a glance
Configuring a Web login local user
Enabling Web operation logging
Display and maintenance commands for Web login
Accessing the device through SNMP
Configuring an SNMPv1 or SNMPv2c community
Login overview
Supported device access methods
The following are methods available for you to access the device:
· CLI login—At the CLI, you can enter text commands to configure and manage the device.
To log in to the CLI, use one of the following methods:
¡ Access the Console user line, as follows:
¡ Use Telnet.
¡ Use SSH.
· Web login—Through the Web interface, you can configure and manage the device visually.
· SNMP access—You can run SNMP on an NMS to access the device MIB, and perform Get and Set operations to configure and manage the device.
Supported initial access methods and default login settings
The first time you access the device, use the login methods and settings in Table 1.
Table 1 Default login settings
|
Login method |
Default username/password |
Default management IP address |
|
Console login through the physical console port |
No username or password is required. |
N/A |
|
Telnet |
admin/h3capadmin |
192.168.0.50/24 |
|
Web interface |
admin/h3capadmin |
192.168.0.50/24 |
Prerequisites
This document describes the login procedures on the basis that automatic configuration is not used.
Logging to the device through console login for the first time
Prerequisites
To log in through the console port, prepare a console terminal, for example, a PC. Make sure the console terminal has a terminal emulation program, such as HyperTerminal or PuTTY. For information about how to use terminal emulation programs, see the programs' user guides.
Procedure
1. Turn off the PC.
The serial ports on PCs do not support hot swapping. Before connecting a cable to or disconnecting a cable from a serial port on a PC, you must turn off the PC.
2. Find the console cable shipped with the device and connect the DB-9 female connector of the console cable to the serial port of the PC.
3. Identify the console port of the device carefully and connect the RJ-45 connector of the console cable to the console port.
|
IMPORTANT: To connect a PC to an operating device, first connect the PC end. To disconnect a PC from an operating device, first disconnect the device end. |
Figure 1 Connecting a terminal to the console port
4. Turn on the PC.
5. On the PC, launch the terminal emulation program, and create a connection that uses the serial port connected to the device. Set the port properties so the port properties match the following console port default settings:
¡ Bits per second—9600 bps.
¡ Flow control—None.
¡ Parity—None.
¡ Stop bits—1.
¡ Data bits—8.
6. Power on the device and press Enter as prompted.
The user view prompt appears. Enter commands to configure or manage the device. To get help, enter a question mark (?).
Configuring CLI login
About CLI login
The device uses user lines (also called user interfaces) to manage CLI sessions and monitor user behavior. For a user line, you can configure access control settings, including the login authentication method and user roles.
User lines
User line types
The device supports the types of user lines listed in Table 2. Different user lines require different login methods.
Table 2 CLI login method and user line matrix
|
User line |
Login method |
|
Console line |
Console port Virtual console port |
|
Virtual type terminal (VTY) line |
Telnet SSH |
User line numbering
A user line has an absolute number and a relative number.
An absolute number uniquely identifies a user line among all user lines. The user lines are numbered starting from 0 and incrementing by 1, in the sequence of console and VTY USB lines. You can use the display line command without any parameters to view supported user lines and their absolute numbers.
A relative number uniquely identifies a user line among all user lines of the same type. The number format is user line type + number. User lines are numbered starting from 0 and incrementing by 1.
User line assignment
The device assigns user lines to CLI login users depending on their login methods, as shown in Table 2. When a user logs in, the device checks the idle user lines for the login method, and assigns the lowest numbered user line to the user. For example, if VTY 0 and VTY 3 are idle when a user Telnets to the device, the device assigns VTY 0 to the user.
Each user line can be assigned only to one user at a time. If no user line is available, a CLI login attempt will be rejected.
Login authentication modes
You can configure login authentication to prevent illegal access to the device CLI.
The device supports the following login authentication modes:
· None—Disables authentication. This mode allows access without authentication and is insecure.
· Password—Requires password authentication. A user must provide the correct password at login.
· Scheme—Uses the AAA module to provide local or remote login authentication. A user must provide the correct username and password at login.
Different login authentication modes require different user line configurations, as shown in Table 3.
Table 3 Configuration required for different login authentication modes
|
Authentication mode |
Configuration tasks |
|
|
None |
Set the authentication mode to none. |
|
|
Password |
1. Set the authentication mode to password. 2. Set a password. |
|
|
Scheme |
1. Set the authentication mode to scheme. 2. Configure login authentication methods in ISP domain view. |
|
User roles
A user is assigned user roles at login. The user roles control the commands and resources available for the user.
The device assigns user roles based on the login authentication mode and user type.
· In none or password authentication mode, the device assigns the user roles specified for the user line.
· In scheme authentication mode, the device uses the following rules to assign user roles:
¡ For an SSH user who uses publickey or password-publickey authentication, the device assigns the user roles specified in the local device management user account for that user.
¡ For non-SSH or SSH password authentication users, the device assigns user roles depending on the authorization settings in the AAA module. If the AAA server does not assign any user roles and the default user role feature is disabled, a remote AAA authentication user cannot log in.
Restrictions and guidelines: CLI login configuration
If a command is available in both user line view and user line class view, the following rules apply:
· The setting in user line view applies only to the user line. The setting in user line class view applies to all user lines of the class.
· The non-default setting in one view takes precedence over the default setting in the other view. A non-default setting in user line view takes precedence over the non-default setting in user line class view.
· The setting in user line class view takes effect only on users who log in after the setting is made. It does not affect users who are already online when the setting is made.
Configuring console login
About console login
You can use the console port or virtual console port of the device to log in and manage the device. For information about the login procedure, see "Logging to the device through console login for the first time."
After logging in to the device, you can use the application on the mobile terminal to manage the device.
Restrictions and guidelines
By default, console login is enabled and does not require authentication. The user role is network-admin for a console user. To improve device security, configure password or scheme authentication for console login immediately after you log in to the device for the first time.
A console login configuration change takes effect only on users who log in after the change is made. It does not affect users who are already online when the change is made.
Console login configuration tasks at a glance
To configure console login, perform the following tasks:
1. Configuring console login authentication
¡ Disabling authentication for console login
¡ Configuring password authentication for console login
¡ Configuring scheme authentication for console login
2. (Optional.) Configuring common console login settings
Configuring console login authentication
Disabling authentication for console login
1. Enter system view.
system-view
2. Enter console line view or class view.
¡ Enter console line view.
line console first-number [ last-number ]
¡ Enter console line class view.
line class console
3. Disable authentication.
authentication-mode none
By default, authentication is disabled for console login.
4. Assign a user role.
user-role role-name
By default, a console user is assigned the network-admin user role.
Configuring password authentication for console login
1. Enter system view.
system-view
2. Enter console line view or class view.
¡ Enter console line view.
line console first-number [ last-number ]
¡ Enter console class view.
line class console
3. Enable password authentication.
authentication-mode password
By default, authentication is disabled for console login.
4. Set a password.
set authentication password { hash | simple } string
By default, no password is set.
5. Assign a user role.
user-role role-name
By default, a console user is assigned the network-admin user role.
Configuring scheme authentication for console login
1. Enter system view.
system-view
2. Enter console line view or class view.
¡ Enter console line view.
line console first-number [ last-number ]
¡ Enter console line class view.
line class console
3. Enable scheme authentication.
authentication-mode scheme
By default, authentication is disabled for console login.
4. Configure user authentication parameters in ISP domain view.
To use local authentication, configure a local user and set the relevant attributes. To use remote authentication, configure a RADIUS, LDAP, or HWTACACS scheme.
Configuring common console login settings
Restrictions and guidelines
Some common console login settings take effect immediately and can interrupt the current session. Use a login method different from console login to log in to the device before you change console login settings.
After you change console login settings, adjust the settings on the configuration terminal accordingly for a successful login.
Procedure
1. Enter system view.
system-view
2. Enter console line view or class view.
¡ Enter console line view.
line console first-number [ last-number ]
¡ Enter console line class view.
line class console
3. Configure terminal attributes.
¡ Enable the terminal service.
shell
Be default, the terminal service is enabled on all user lines.
The undo shell command is not available in console line view.
¡ Specify the terminal display type.
terminal type { ansi | vt100 }
By default, the terminal display type is ANSI.
The device supports ANSI and VT100 terminal display types. As a best practice, specify VT100 type on both the device and the configuration terminal. You can also specify the ANSI type for both sides, but a display problem might occur if a command line has more than 80 characters.
¡ Set the maximum number of lines of command output to send to the terminal at a time.
screen-length screen-length
By default, the device sends a maximum of 24 lines to the terminal at a time.
To disable pausing between screens of output, set the value to 0.
¡ Set the size for the command history buffer.
history-command max-size value
By default, the buffer size is 10. The buffer for a user line can save a maximum of 10 history commands.
¡ Set the CLI connection idle-timeout timer.
idle-timeout minutes [ seconds ]
By default, the CLI connection idle-timeout timer is 10 minutes.
If no interaction occurs between the device and the user within the idle-timeout interval, the system automatically terminates the user connection on the user line.
If you set the timeout timer to 0, the connection will not be aged out.
4. Configure shortcut keys.
¡ Specify the terminal session activation key.
activation-key character
By default, pressing Enter starts the terminal session.
¡ Specify the escape key.
escape-key { key-string | default }
By default, pressing Ctrl+C terminates a command.
¡ Set the user line locking key.
lock-key key-string
By default, no user line locking key is set.
Configuring Telnet login
About Telnet login
The device can act as a Telnet server to allow Telnet login, or as a Telnet client to Telnet to other devices.
Restrictions and guidelines
A Telnet login configuration change takes effect only on users who log in after the change is made. It does not affect users who are already online when the change is made.
A VTY line uses the line class settings for the authentication-mode and protocol inbound commands if the line specific settings for both of them are the default settings. If the line setting for either command is not the default, the VTY line uses the line specific settings for both of the commands.
Configuring the device as a Telnet server
Telnet server configuration tasks at a glance
To configure the device as a Telnet server, perform the following tasks:
2. Configuring Telnet login authentication
¡ Disabling authentication for Telnet login
¡ Configuring password authentication for Telnet login
¡ Configuring scheme authentication for Telnet login
3. (Optional.) Configuring common Telnet server settings
4. (Optional.) Configuring common VTY line settings
Enabling the Telnet server
1. Enter system view.
system-view
2. Enable the Telnet server.
telnet server enable
By default, the Telnet server is disabled.
Disabling authentication for Telnet login
1. Enter system view.
system-view
2. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
3. Disable authentication.
authentication-mode none
When the device starts up with initial settings, password authentication is enabled by default.
When the device starts up with factory defaults, scheme authentication is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
4. (Optional.) Assign a user role.
user-role role-name
By default, a Telnet user is assigned the network-operator user role.
Configuring password authentication for Telnet login
1. Enter system view.
system-view
2. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
3. Enable password authentication.
authentication-mode password
When the device starts up with initial settings, password authentication is enabled by default.
When the device starts up with factory defaults, scheme authentication is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
The VTY line will use the authentication mode setting configured in VTY line class view if the setting for the protocol inbound command on the VTY line is the default setting.
4. Set a password.
set authentication password { hash | simple } password
By default, no password is set.
5. (Optional.) Assign a user role.
user-role role-name
By default, a Telnet user is assigned the network-operator user role.
Configuring scheme authentication for Telnet login
1. Enter system view.
system-view
2. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
3. Enable scheme authentication.
authentication-mode scheme
When the device starts up with initial settings, password authentication is enabled by default.
When the device starts up with factory defaults, scheme authentication is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
4. Configure user authentication parameters in ISP domain view.
To use local authentication, configure a local user and set the relevant attributes.
To use remote authentication, configure a RADIUS, LDAP, or HWTACACS scheme.
Configuring common Telnet server settings
1. Enter system view.
system-view
2. Set the DSCP value for outgoing Telnet packets.
IPv4:
telnet server dscp dscp-value
IPv6:
telnet server ipv6 dscp dscp-value
By default, the DSCP value is 48.
3. Specify the Telnet service port number.
IPv4:
telnet server port port-number
IPv6:
telnet server ipv6 port port-number
By default, the Telnet service port number is 23.
4. Set the maximum number of concurrent Telnet users.
aaa session-limit telnet max-sessions
By default, the maximum number of concurrent Telnet users is 32.
Changing this setting does not affect users who are currently online. If the new limit is less than the number of online Telnet users, no additional users can Telnet in until the number drops below the new limit.
Configuring common VTY line settings
1. Enter system view.
system-view
2. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
3. Configure VTY terminal attributes.
¡ Enable the terminal service.
shell
By default, the terminal service is enabled on all user lines.
¡ Specify the terminal display type.
terminal type { ansi | vt100 }
By default, the terminal display type is ANSI.
¡ Set the maximum number of lines of command output to send to the terminal at a time.
screen-length screen-length
By default, the device sends a maximum of 24 lines to the terminal at a time.
To disable pausing between screens of output, set the value to 0.
¡ Set the size for the command history buffer.
history-command max-size value
By default, the buffer size is 10. The buffer for a user line can save a maximum of 10 history commands.
¡ Set the CLI connection idle-timeout timer.
idle-timeout minutes [ seconds ]
By default, the CLI connection idle-timeout timer is 10 minutes.
If no interaction occurs between the device and the user within the idle-timeout interval, the system automatically terminates the user connection on the user line.
If you set the timeout timer to 0, the connection will not be aged out.
4. Specify the supported protocols.
protocol inbound { all | ssh | telnet }
By default, Telnet and SSH are supported. The VTY line will use the protocol setting configured in VTY line class view if the protocol and authentication mode settings on the VTY line are both the default settings.
A protocol change takes effect only on users who log in after the setting is made. It does not affect users who are already online when the setting is made.
5. Specify the command to be automatically executed for login users on the user lines.
auto-execute command command
By default, no command is specified for auto execution.
|
IMPORTANT: Before you configure this command and save the configuration, make sure you can access the CLI to modify the configuration through other VTY lines. |
For a VTY line, you can specify a command that is to be automatically executed when a user logs in. After executing the specified command, the system automatically disconnects the Telnet session.
6. Configure shortcut keys.
¡ Specify the shortcut key for terminating a task.
escape-key { key-string | default }
The default setting is Ctrl+C.
¡ Set the user line locking key.
lock-key key-string
By default, no user line locking key is set.
Using the device to log in to a Telnet server
About this task
You can use the device as a Telnet client to log in to a Telnet server.
Figure 2 Telnetting from the device to a Telnet server
Prerequisites
Assign an IP address to the device and obtain the IP address of the Telnet server. If the device resides on a different subnet than the Telnet server, make sure the device and the Telnet server can reach each other.
Procedure
1. Enter system view.
system-view
2. (Optional.) Specify the source IPv4 address or source interface for outgoing Telnet packets.
telnet client source { interface interface-type interface-number | ip ip-address }
By default, no source IPv4 address or source interface is specified. The device uses the primary IPv4 address of the output interface as the source address for outgoing Telnet packets.
3. Exit to user view.
quit
4. Use the device to log in to a Telnet server.
IPv4:
telnet remote-host [ service-port ] [ source { interface interface-type interface-number | ip ip-address } ] [ dscp dscp-value ] [ escape character ]
IPv6:
telnet ipv6 remote-host [ -i interface-type interface-number ] [ port-number ] [ source { interface interface-type interface-number | ipv6 ipv6-address } ] [ dscp dscp-value ] [ escape character ]
Configuring SSH login
About SSH login
SSH offers a secure remote login method. By providing encryption and strong authentication, it protects devices against attacks such as IP spoofing and plaintext password interception.
The device can act as an SSH server to provide secure Telnet (Stelnet) service or act as an SSH client to log in to an SSH server.
Configuring the device as an SSH server
About this task
The following information provides the SSH server configuration procedure used when the SSH client authentication method is password.
Procedure
1. Enter system view.
system-view
2. Enable the SSH server.
ssh server enable
By default, the SSH server is disabled.
3. (Optional.) Create an SSH user and specify the authentication mode.
ssh user username service-type stelnet authentication-type password
4. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
5. Enable scheme authentication.
authentication-mode scheme
When the device starts up with initial settings, password authentication is enabled by default.
When the device starts up with factory defaults, scheme authentication is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
6. (Optional.) Specify the protocols for the user lines to support.
protocol inbound { all | ssh | telnet }
By default, Telnet and SSH are supported.
A protocol change takes effect only on users who log in after the setting is made. It does not affect users who are already online when the setting is made.
7. (Optional.) Set the maximum number of concurrent SSH users.
aaa session-limit ssh max-sessions
By default, the maximum number of concurrent SSH users is 32.
Changing this setting does not affect users who are currently online. If the new limit is less than the number of online SSH users, no additional SSH users can log in until the number drops below the new limit.
8. (Optional.) Configure common settings for VTY lines:
a. Return to system view.
quit
b. Configure common settings for VTY lines.
See "Configuring common VTY line settings."
Configuring the device as an SSH server
About this task
The following information provides the SSH server configuration procedure used when the SSH client authentication method is public key.
Procedure
1. Enter system view.
system-view
2. Create local key pairs.
public-key local create { dsa | ecdsa secp256r1 | secp384r1 } | rsa }
3. Enable the SSH server.
ssh server enable
By default, the SSH server is disabled.
4. (Optional.) Create an SSH user and specify the authentication mode.
ssh user username service-type stelnet authentication-type publickey
5. Enter VTY line view or class view.
¡ Enter VTY line view.
line vty first-number [ last-number ]
¡ Enter VTY line class view.
line class vty
6. Enable scheme authentication.
authentication-mode scheme
When the device starts up with initial settings, password authentication is enabled by default.
When the device starts up with factory defaults, scheme authentication is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
7. (Optional.) Specify the protocols for the user lines to support.
protocol inbound { all | ssh | telnet }
By default, Telnet and SSH are supported.
A protocol change takes effect only on users who log in after the setting is made. It does not affect users who are already online when the setting is made.
8. (Optional.) Set the maximum number of concurrent SSH users.
aaa session-limit ssh max-sessions
By default, the maximum number of concurrent SSH users is 32.
Changing this setting does not affect users who are currently online. If the new limit is less than the number of online SSH users, no additional SSH users can log in until the number drops below the new limit.
9. (Optional.) Configure common settings for VTY lines:
a. Return to system view.
quit
b. Configure common settings for VTY lines.
See "Configuring common VTY line settings."
Using the device to log in to an SSH server
About this task
You can use the device as an SSH client to log in to an SSH server.
Figure 3 Logging in to an SSH server from the device
Prerequisites
Assign an IP address to the device and obtain the IP address of the SSH server. If the device resides on a different subnet than the SSH server, make sure the device and the SSH server can reach each other.
Procedure
1. Enter system view.
system-view
2. Create local key pairs.
public-key local create { dsa | ecdsa { secp256r1 | secp384r1 } | rsa }
3. (Optional.) Configure the source IPv4 address for SSH packets that are sent by the SSH client.
IPv4:
ssh client source { interface interface-type interface-number | ip ip-address }
By default, the SSH client uses the primary IPv4 address of the output interface in the matching route as the source address of outgoing SSH packets.
IPv6:
ssh client ipv6 source { interface interface-type interface-number | ipv6 ipv6-address }
By default, the SSH client automatically selects an IPv6 address for outgoing SSH packets in compliance with RFC 3484.
4. Return to user view.
quit
5. Establish a connection to an SSH server.
IPv4:
ssh2 server
IPv6:
ssh2 ipv6 server
Display and maintenance commands for CLI login
Execute display commands in any view.
|
Task |
Command |
Remarks |
|
Display user line information. |
display line [ num1 | { console | vty } num2 ] [ summary ] |
N/A |
|
Display the packet source setting for the Telnet client. |
display telnet client |
N/A |
|
Display online CLI users. |
display users [ all ] |
N/A |
|
Release a user line. |
free line { num1 | { console | vty } num2 } |
Multiple users can log in to the device to simultaneously configure the device. When necessary, you can execute this command to release some connections. You cannot use this command to release the connection you are using. This command is available in user view. |
|
Lock the current user line and set the password for unlocking the line. |
lock |
By default, the system does not lock any user lines. This command is available in user view. |
|
Lock the current user line and enable unlocking authentication. |
lock reauthentication |
By default, the system does not lock any user lines or initiate reauthentication. To unlock the locked user line, you must press Enter and provide the login password to pass reauthentication. This command is available in any view. |
|
Send messages to user lines. |
send { all | num1 | { console | vty } num2 } |
This command is available in user view. |
Configuring Web login
About Web login
The device provides a built-in Web server that supports HTTP 1.0, HTTP 1.1, and HTTPS. You can use a Web browser to log in to and configure the device.
HTTPS uses SSL to ensure the integrity and security of data exchanged between the client and the server, and is more secure than HTTP. You can define a certificate-based access control policy to allow only legal clients to access the Web interface.
Restrictions and guidelines: Web login configuration
To improve device security, the system automatically enables the HTTPS service when you enable the HTTP service. When the HTTP service is enabled, you cannot disable the HTTPS service.
Web login configuration tasks at a glance
To configure Web login, perform the following tasks:
1. Configuring Web login
2. Configuring a Web login local user
4. Enabling Web operation logging
Prerequisites for Web login
Make sure the configuration terminal and the device can communicate over the IP network.
Configuring HTTP login
1. (Optional.) Specify a fixed verification code for Web login.
web captcha verification-code
By default, no fixed verification code is specified. A Web user must enter the verification code displayed on the login page at login.
Execute this command in user view.
2. Enter system view.
system-view
3. Enable the HTTP service.
ip http enable
When the device starts up with initial settings, HTTP is enabled by default.
When the device starts up with factory defaults, HTTP is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
4. (Optional.) Specify the HTTP service port number.
ip http port port-number
The default HTTP service port number is 80.
5. (Optional.) Specify the HTTP methods to be added to the reply to an OPTIONS request.
http method { delete | get | head | options | post | put } *
By default, no HTTP methods are specified.
Configuring HTTPS login
About this task
The device supports the following HTTPS login modes:
· Simplified mode—The device uses a self-signed certificate (a certificate that is generated and signed by the device itself) and the default SSL settings. The device operates in simplified mode after you enable HTTPS service on the device.
· Secure mode—The device uses a certificate signed by a CA and a set of user-defined security protection settings to ensure security. For the device to operate in secure mode, you must perform the following tasks:
¡ Enable HTTPS service on the device.
¡ Specify an SSL server policy for the service.
¡ Configure PKI domain-related parameters.
Simplified mode is easy to configure but it is insecure. Secure mode is secure but it is complicated to configure.
Restrictions and guidelines
· To associate a different SSL server policy with the HTTPS service, you must perform the following tasks:
a. Disable the HTTP service and HTTPS service before you associate the new SSL server policy.
b. Enable the HTTP service and HTTPS service again after the association.
If you fail to complete the required tasks, the new SSL server policy does not take effect.
· For the HTTP service to use its self-signed certificate after you associate an SSL server policy with the HTTPS service, you must follow these steps:
a. Disable the HTTP service and HTTPS service.
b. Execute the undo ip https ssl-server-policy command to remove the existing SSL server policy association.
c. Enable the HTTP service and HTTPS service again.
· Enabling the HTTPS service triggers the SSL handshake negotiation process.
¡ If the device has a local certificate, the SSL handshake negotiation succeeds and the HTTPS service starts up.
¡ If the device does not have a local certificate, the certificate application process starts. Because the certificate application process takes a long time, the SSL handshake negotiation might fail and the HTTPS service might not be started. To solve the problem, execute the ip https enable command again until the HTTPS service is enabled.
· To use a certificate-based access control policy to control HTTPS access, you must perform the following tasks:
¡ Configure the client-verify enable command in the SSL server policy that is associated with the HTTPS service.
¡ Configure a minimum of one permit rule in the certificate-based access control policy.
If you fail to complete the required tasks, HTTPS clients cannot log in.
Procedure
1. (Optional.) Specify a fixed verification code for Web login.
web captcha verification-code
By default, no fixed verification code is configured. A Web user must enter the verification code displayed on the login page at login.
2. Enter system view.
system-view
3. (Optional.) Apply policies to the HTTPS service.
¡ Apply an SSL server policy.
ip https ssl-server-policy policy-name
By default, no SSL server policy is associated. The HTTP service uses a self-signed certificate.
¡ Apply a certificate-based access control policy to control HTTPS access.
ip https certificate access-control-policy policy-name
By default, no certificate-based access control policy is applied.
4. Enable the HTTPS service.
ip https enable
When the device starts up with initial settings, HTTP is enabled by default.
When the device starts up with factory defaults, HTTP is enabled by default.
For more information about the initial settings and factory defaults, see Fundamentals Configuration Guide for the device.
5. (Optional.) Specify the HTTPS service port number.
ip https port port-number
The default HTTPS service port number is 443.
6. (Optional.) Set the HTTPS login authentication mode.
web https-authorization mode { auto | manual }
By default, manual authentication mode is used for HTTPS login.
Configuring a Web login local user
1. Enter system view.
system-view
2. Create a local user and enter local user view.
local-user user-name [ class manage ]
3. (Optional.) Configure a password for the local user.
password [ { hash | simple } password ]
By default, no password is configured for a local user. The local user can pass authentication after entering the correct username and passing attribute checks.
4. Configure user attributes.
¡ Assign a user role to the local user.
authorization-attribute user-role user-role
The default user role is network-operator for a Web user.
¡ Specify the service type for the local user.
service-type { http | https }
By default, no service type is specified for a local user.
Managing Web connections
Setting the Web connection idle-timeout timer
1. Enter system view.
system-view
2. Set the Web connection idle-timeout timer.
web idle-timeout minutes
By default, the Web connection idle-timeout timer is 10 minutes.
Specifying the maximum number of online HTTP or HTTPS users
1. Enter system view.
system-view
2. Specify the maximum number of online HTTP or HTTPS users.
aaa session-limit { http | https } max-sessions
By default, the device supports a maximum number of 32 online HTTP users and 32 online HTTPS users.
Changing this setting does not affect users who are currently online. If the new setting is less than the number of online HTTP or HTTPS users, no additional HTTP or HTTPS users can log in until the number drops below the new limit.
Logging off Web users
To log off Web users, execute the following command in user view:
free web users { all | user-id user-id | user-name user-name }
Enabling Web operation logging
1. Enter system view.
system-view
2. Enable Web operation logging.
webui log enable
By default, Web operation logging is disabled.
Display and maintenance commands for Web login
Execute display commands in any view and the free web users command in user view.
|
Task |
Command |
|
Display HTTP service configuration and status information. |
display ip http |
|
Display HTTPS service configuration and status information. |
display ip https |
|
Display Web interface navigation tree information. |
display web menu [ chinese ] |
|
Display online Web users. |
display web users |
|
Log off online Web users. |
free web users { all | user-id user-id | user-name user-name } |
Accessing the device through SNMP
About SNMP
A network management station (NMS) can use the Simple Network Management Protocol (SNMP) to access and operate the devices on a network, regardless of their vendors, physical characteristics, and interconnect technologies.
SNMP enables network administrators to read and set the variables on managed devices for state monitoring, troubleshooting, statistics collection, and other management purposes.
SNMP framework
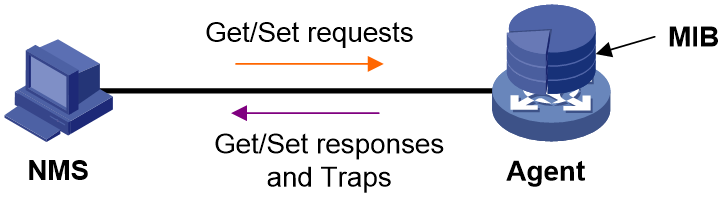
The SNMP framework contains the following elements:
· SNMP manager—Works on an NMS to monitor and manage the SNMP-capable devices in the network.
· SNMP agent—Works on a managed device to receive and handle requests from the NMS, and sends notifications to the NMS when events, such as an interface state change, occur.
· Management Information Base (MIB)—Specifies the variables (for example, interface status and CPU usage) maintained by the SNMP agent for the SNMP manager to read and set.
Figure 4 Relationship between NMS, agent, and MIB
SNMP tasks at a glance
To configure SNMP, perform the following tasks:
3. Configuring an SNMPv1 or SNMPv2c community
4. Configuring an SNMPv3 group and user
Enabling the SNMP agent
Restrictions and guidelines
The SNMP agent is enabled when you use any command that begins with snmp-agent except for the snmp-agent calculate-password command.
Procedure
1. Enter system view.
system-view
2. Enable the SNMP agent.
snmp-agent
By default, the SNMP agent is disabled.
Enabling SNMP versions
Restrictions and guidelines
SNMPv1, SNMPv2c, and SNMPv3 are supported. An NMS and an SNMP agent must use the same SNMP version to communicate with each other.
Procedure
1. Enter system view.
system-view
2. Enable SNMP versions.
snmp-agent sys-info version { all | { v1 | v2c | v3 } * }
By default, SNMPv3 is enabled.
If you execute the command multiple times with different options, all the configurations take effect, but only one SNMP version is used by the agent and NMS for communication.
Configuring an SNMPv1 or SNMPv2c community
About configuring an SNMPv1 or SNMPv2c community
You can create an SNMPv1 or SNMPv2c community by using a community name or by creating an SNMPv1 or SNMPv2c user. After you create an SNMPv1 or SNMPv2c user, the system automatically creates a community by using the username as the community name.
Restrictions and guidelines for configuring an SNMPv1 or SNMPv2c community
Make sure the NMS and agent use the same SNMP community name.
Only users with the network-admin or level-15 user role can create SNMPv1 or SNMPv2c communities, users, or groups. Users with other user roles cannot create SNMPv1 or SNMPv2c communities, users, or groups even if these roles are granted access to related commands or commands of the SNMPv1 or SNMPv2c feature.
Configuring an SNMPv1/v2c community by a community name
1. Enter system view.
system-view
2. Create an SNMPv1/v2c community. Choose one option as needed.
¡ In VACM mode:
snmp-agent community { read | write } [ simple | cipher ] community-name [ mib-view view-name ] [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
¡ In RBAC mode:
snmp-agent community [ simple | cipher ] community-name user-role role-name [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
3. (Optional.) Map the SNMP community name to an SNMP context.
snmp-agent community-map community-name context context-name
Configuring an SNMPv1/v2c community by creating an SNMPv1/v2c user
1. Enter system view.
system-view
2. Create an SNMPv1/v2c group.
snmp-agent group { v1 | v2c } group-name [ read-view view-name ] [ write-view view-name ] [ notify-view view-name ] [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
3. Add an SNMPv1/v2c user to the group.
snmp-agent usm-user { v1 | v2c } user-name group-name [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
The system automatically creates an SNMP community by using the username as the community name.
4. (Optional.) Map the SNMP community name to an SNMP context.
snmp-agent community-map community-name context context-name
Configuring an SNMPv3 group and user
Restrictions and guidelines for configuring an SNMPv3 group and user
Only users with the network-admin or level-15 user role can create SNMPv3 users or groups. Users with other user roles cannot create SNMPv3 users or groups even if these roles are granted access to related commands or commands of the SNMPv3 feature.
SNMPv3 users are managed in groups. All SNMPv3 users in a group share the same security model, but can use different authentication and encryption algorithms and keys. Table 4 describes the basic configuration requirements for different security models.
Table 4 Basic configuration requirements for different security models
|
Security model |
Keyword for the group |
Parameters for the user |
Remarks |
|
Authentication with privacy |
privacy |
Authentication and encryption algorithms and keys |
For an NMS to access the agent, make sure the NMS and agent use the same authentication and encryption keys. |
|
Authentication without privacy |
authentication |
Authentication algorithm and key |
For an NMS to access the agent, make sure the NMS and agent use the same authentication key. |
|
No authentication, no privacy |
N/A |
N/A |
The authentication and encryption keys, if configured, do not take effect. |
Configuring an SNMPv3 group and user
1. Enter system view.
system-view
2. Create an SNMPv3 group.
snmp-agent group v3 group-name [ authentication | privacy ] [ read-view view-name ] [ write-view view-name ] [ notify-view view-name ] [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
3. (Optional.) Calculate the encrypted form for the key in plaintext form.
snmp-agent calculate-password plain-password mode { 3desmd5 | 3dessha | md5 | sha } { local-engineid | specified-engineid engineid }
4. Create an SNMPv3 user. Choose one option as needed.
¡ In VACM mode:
snmp-agent usm-user v3 user-name group-name [ remote { ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] ] [ { cipher | simple } authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
¡ In RBAC mode:
snmp-agent usm-user v3 user-name user-role role-name [ remote { ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] ] [ { cipher | simple } authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl { ipv4-acl-number | name ipv4-acl-name } | acl ipv6 { ipv6-acl-number | name ipv6-acl-name } ] *
To send notifications to an SNMPv3 NMS, you must specify the remote keyword.
If the cipher keyword is specified, the auth-password and priv-password arguments are used as encrypted keys.
5. (Optional.) Assign a user role to the SNMPv3 user created in RBAC mode.
snmp-agent usm-user v3 user-name user-role role-name
By default, an SNMPv3 user has the user role assigned to it at its creation.
Display and maintenance commands for SNMP
Execute display commands in any view.
|
Task |
Command |
|
Display SNMPv1 or SNMPv2c community information. |
display snmp-agent community [ read | write ] |
|
Display SNMP group information. |
display snmp-agent group [ group-name ] |
|
Display SNMPv3 user information. |
display snmp-agent usm-user [ engineid engineid | username user-name | group group-name ] * |