- Table of Contents
-
- 13-Layer 3—IP Services Configuration Guide
- 00-Preface
- 01-IP addressing configuration
- 02-IP forwarding basics configuration
- 03-Fast forwarding configuration
- 04-ARP configuration
- 05-IPv6 basics configuration
- 06-IPv6 fast forwarding configuration
- 07-DHCP configuration
- 08-DHCPv6 configuration
- 09-DNS configuration
- 10-IP performance optimization configuration
- 11-Multi-CPU packet distribution configuration
- 12-Adjacency table configuration
- 13-Web caching configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 09-DNS configuration | 171.44 KB |
Contents
DNS server-based domain name resolution
About domain name resolution on the DNS client
Configuring static domain name resolution
Configuring DNS server-based domain name resolution
Specifying DNS server addresses
Configuring the DNS transparent proxy
Configuring a DNS packet rate limit
Configuring the DNS trusted interface
Specifying the source interface for DNS packets
Setting the DSCP value for outgoing DNS packets
Display and maintenance commands for DNS
Troubleshooting DNS configuration
Configuring DNS
About DNS
Domain Name System (DNS) is a distributed database used by TCP/IP applications to translate domain names into IP addresses. The domain name-to-IP address mapping is called a DNS entry.
Types of DNS services
DNS services can be static or dynamic. After a user specifies a name, the device checks the static name resolution table for an IP address. If no IP address is available, it uses a DNS server group or a DNS server for dynamic name resolution, which takes more time than static name resolution. To improve efficiency, you can put frequently queried name-to-IP address mappings in the local static name resolution table.
Static domain name resolution
Static domain name resolution means manually creating mappings between domain names and IP addresses. For example, you can create a static DNS mapping for a device so that you can Telnet to the device by using the domain name.
DNS server-based domain name resolution
Architecture
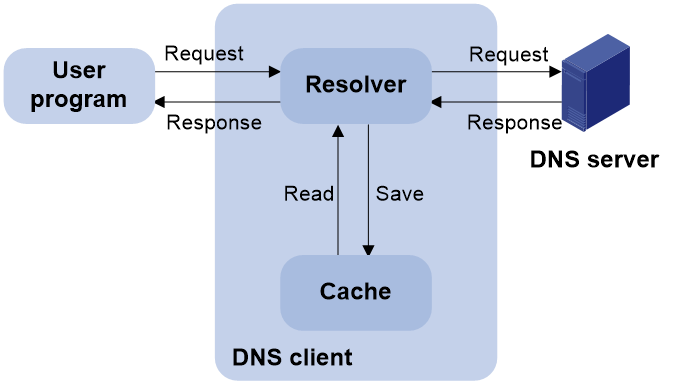
Figure 1 shows the relationship between the user program, DNS client, and DNS server. The DNS client includes the resolver and cache. The user program and DNS client can run on the same device or different devices. The DNS server and the DNS client usually run on different devices.
Figure 1 DNS server-based dynamic domain name resolution
The device can function as a DNS client, but not a DNS server.
If an alias is configured for a domain name on the DNS server, the device can resolve the alias into the IP address of the host.
Resolution process
The DNS server-based dynamic domain name resolution process is as follows:
1. A user program sends a name query to the resolver of the DNS client.
2. The DNS resolver looks up the local domain name cache for a match. If the resolver finds a match, it sends the corresponding IP address back. If not, it sends a query to the DNS server.
3. The DNS server looks up the corresponding IP address of the domain name in its DNS database. If no match is found, the server sends a query to other DNS servers. This process continues until a result, whether successful or not, is returned.
4. After receiving a response from the DNS server, the DNS client returns the resolution result to the user program.
Caching
DNS server-based dynamic domain name resolution allows the DNS client to store latest DNS entries in the DNS cache. The DNS client does not need to send a request to the DNS server for a repeated query within the aging time. To make sure the entries from the DNS server are up to date, a DNS entry is removed when its aging timer expires. The DNS server determines how long a mapping is valid, and the DNS client obtains the aging information from DNS responses.
DNS suffixes
You can configure a domain name suffix list so that the resolver can use the list to supply the missing part of an incomplete name.
For example, you can configure com as the suffix for aabbcc.com. The user only needs to enter aabbcc to obtain the IP address of aabbcc.com. The resolver adds the suffix and delimiter before passing the name to the DNS server.
The name resolver handles the queries based on the domain names that the user enters:
· If the user enters a domain name without a dot (.) (for example, aabbcc), the resolver considers the domain name to be a host name. It adds a DNS suffix to the host name before performing the query operation. If no match is found for any host name and suffix combination, the resolver uses the user-entered domain name (for example, aabbcc) for the IP address query.
· If the user enters a domain name with a dot (.) among the letters (for example, www.aabbcc), the resolver directly uses this domain name for the query operation. If the query fails, the resolver adds a DNS suffix for another query operation.
· If the user enters a domain name with a dot (.) at the end (for example, aabbcc.com.), the resolver considers the domain name an FQDN and returns the successful or failed query result. The dot at the end of the domain name is considered a terminating symbol.
DNS proxy
The DNS proxy performs the following functions:
· Forwards the request from the DNS client to the designated DNS server.
· Conveys the reply from the DNS server to the client.
The DNS proxy simplifies network management. When the DNS server address is changed, you can change the configuration only on the DNS proxy instead of on each DNS client.
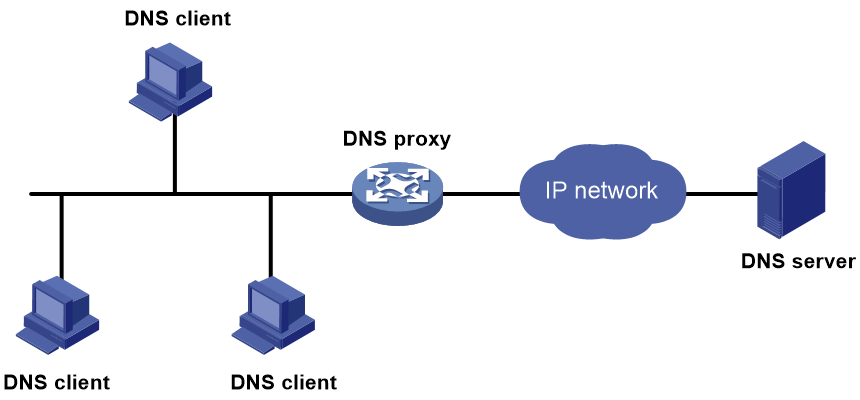
Figure 2 shows the typical DNS proxy application.
Figure 2 DNS proxy application
A DNS proxy operates as follows:
1. A DNS client considers the DNS proxy as the DNS server, and sends a DNS request to the DNS proxy. The destination address of the request is the IP address of the DNS proxy.
2. The DNS proxy searches the local static domain name resolution table and dynamic domain name resolution cache after receiving the request. If the requested information is found, the DNS proxy returns a DNS reply to the client.
3. If the requested information is not found, the DNS proxy forwards the request as follows:
a. If a matching domain name rule exists, the proxy forwards the request to DNS servers in the DNS server group bound to the rule.
b. If no matching DNS server group exists but a DNS server is specified, the DNS proxy sends the request to the DNS server for domain name resolution.
4. After receiving a reply from the DNS server, the DNS proxy records the DNS mapping and forwards the reply to the DNS client.
If no DNS server is designated or no route is available to the designated DNS server, the DNS proxy does not forward DNS requests.
DNS spoofing
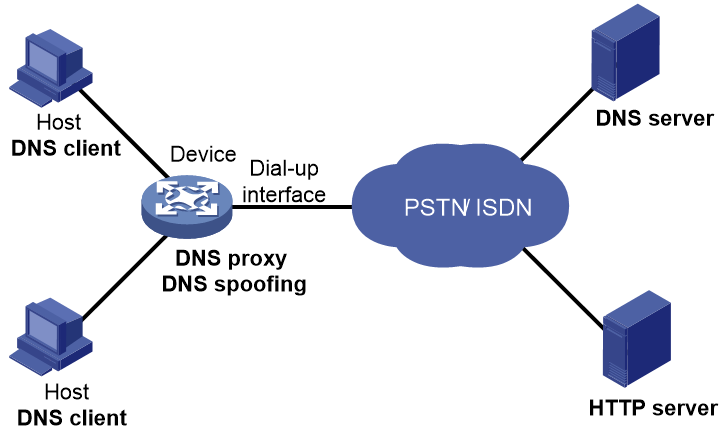
As shown in Figure 3, DNS spoofing is applied to the dial-up network.
· The device connects to a PSTN network through a dial-up interface. The device triggers the establishment of a dial-up connection only when packets are to be forwarded through the dial-up interface.
· The device acts as a DNS proxy and is specified as a DNS server on the hosts. After the dial-up connection is established, the device dynamically obtains the DNS server address through DHCP or another autoconfiguration mechanism.
Figure 3 DNS spoofing application
The DNS proxy does not have the DNS server address or cannot reach the DNS server after startup. A host accesses the HTTP server in the following steps:
1. The host sends a DNS request to the device to resolve the domain name of the HTTP server into an IP address.
2. Upon receiving the request, the device searches the local static and dynamic DNS entries for a match. Because no match is found, the device spoofs the host by replying a configured IP address. The device must have a route to the IP address with the dial-up interface as the output interface.
The IP address configured for DNS spoofing is not the actual IP address of the requested domain name. Therefore, the TTL field is set to 0 in the DNS reply. When the DNS client receives the reply, it creates a DNS entry and ages it out immediately.
3. Upon receiving the reply, the host sends an HTTP request to the replied IP address.
4. When forwarding the HTTP request through the dial-up interface, the device performs the following operations:
¡ Establishes a dial-up connection with the network.
¡ Dynamically obtains the DNS server address through DHCP or another autoconfiguration mechanism.
5. Because the DNS entry ages out immediately upon creation, the host sends another DNS request to the device to resolve the HTTP server domain name.
6. The device operates the same as a DNS proxy. For more information, see "DNS proxy."
7. After obtaining the IP address of the HTTP server, the host can access the HTTP server.
Without DNS spoofing, the device forwards the DNS requests from the host to the DNS server if it cannot find a matching local DNS entry. However, the device cannot obtain the DNS server address, because no dial-up connection is established. Therefore, the device cannot forward or answer the requests from the client. DNS resolution fails, and the client cannot access the HTTP server.
DNS tasks at a glance
To configure DNS, perform the following tasks:
Choose the following tasks as needed:
¡ Configuring static domain name resolution
¡ Configuring DNS server-based domain name resolution
2. (Optional.) Configuring the DNS proxy
¡ Configuring the DNS transparent proxy
3. (Optional.) Configuring DNS spoofing
This feature is applied to the dial-up network.
4. (Optional.) Configuring DNS security features
¡ Enabling DNS snooping logging
¡ Configuring a DNS packet rate limit
¡ Configuring the DNS trusted interface
5. (Optional.) Configuring DNS packet parameters
¡ Specifying the source interface for DNS packets
¡ Setting the DSCP value for outgoing DNS packets
6. (Optional.) Configuring DNS filtering
Configuring the DNS client
About domain name resolution on the DNS client
A DNS client resolves a domain name in the following order:
1. Locally saved DNS mappings that have been resolved.
2. DNS server group-based domain name resolution.
3. Static domain name resolution.
4. DNS server-based domain name resolution.
The resolution fails if domain name cannot be resolved after all these methods are used.
Configuring static domain name resolution
Restrictions and guidelines
For the public network or a VPN instance, each host name maps to only one IPv4 address and one IPv6 address.
A maximum of 2048 DNS entries can be configured for the public network or each VPN instance. You can configure DNS entries for both public network and VPN instances.
Procedure
1. Enter system view.
system-view
2. Configure a host name-to-address mapping.
IPv4:
ip host host-name ip-address [ vpn-instance vpn-instance-name ]
IPv6:
ipv6 host host-name ipv6-address [ vpn-instance vpn-instance-name ]
Configuring DNS server-based domain name resolution
Restrictions and guidelines
· The limit on the number of DNS servers on the device is as follows:
¡ In system view, you can specify a maximum of six DNS server IPv4 addresses for the public network or each VPN instance. You can specify DNS server IPv4 addresses for both public network and VPN instances.
¡ In system view, you can specify a maximum of six DNS server IPv6 addresses for the public network or each VPN instance. You can specify DNS server IPv6 addresses for both public network and VPN instances.
¡ In interface view, you can specify a maximum of six DNS server IPv4 addresses for the public network or each VPN instance. You can specify DNS server IPv4 addresses for both public network and VPN instances.
· A DNS server address is required so that DNS queries can be sent to a correct server for resolution. If you specify both an IPv4 address and an IPv6 address, the device performs the following operations:
¡ Sends an IPv4 DNS query first to the DNS server IPv4 addresses. If the query fails, the device turns to the DNS server IPv6 addresses.
¡ Sends an IPv6 DNS query first to the DNS server IPv6 addresses. If the query fails, the device turns to the DNS server IPv4 addresses.
· A DNS server address specified in system view takes priority over a DNS server address specified in interface view. A DNS server address specified earlier has a higher priority. A DNS server address manually specified takes priority over a DNS server address dynamically obtained, for example, through DHCP. The device first sends a DNS query to the DNS server address of the highest priority. If the first query fails, it sends the DNS query to the DNS server address of the second highest priority, and so on.
· You can configure a DNS suffix that the system automatically adds to the incomplete domain name that a user enters.
¡ You can configure a maximum of 16 DNS suffixes for the public network or each VPN instance. You can configure DNS suffixes for both public network and VPN instances.
¡ A DNS suffix manually configured takes priority over a DNS suffix dynamically obtained, for example, through DHCP. A DNS suffix configured earlier has a higher priority. The device first uses the suffix that has the highest priority. If the query fails, the device uses the suffix that has the second highest priority, and so on.
Procedure
1. Enter system view.
system-view
2. (Optional.) Set the TTL value for DNS entries.
dns cache ttl { maximum max-value | minimum min-value } *
By default, the TTL value for DNS entries is the TTL value in the DNS reply.
3. (Optional.) Configure a DNS suffix.
dns domain domain-name [ vpn-instance vpn-instance-name ]
By default, no DNS suffix is configured and only the domain name that a user enters is resolved.
4. Specify a DNS server address.
¡ Specify a DNS server address in system view.
IPv4:
dns server ip-address [ vpn-instance vpn-instance-name ]
IPv6:
ipv6 dns server ipv6-address [ interface-type interface-number ] [ vpn-instance vpn-instance-name ]
¡ Execute the following commands in sequence to specify a DNS server IPv4 address in interface view.
interface interface-type interface-number
dns server ip-address [ vpn-instance vpn-instance-name ]
By default, no DNS server address is specified.
Configuring the DNS proxy
Enabling DNS proxy
1. Enter system view.
system-view
2. Enable DNS proxy.
dns proxy enable
By default, DNS proxy is disabled.
Specifying DNS server addresses
Restrictions and guidelines
You can specify multiple DNS servers. The DNS proxy forwards a request to the DNS server that has the highest priority. If it does not receive a reply, the proxy forwards the request to a DNS server that has the second highest priority, and so on.
You can specify both an IPv4 address and an IPv6 address.
· A DNS proxy forwards an IPv4 name query first to IPv4 DNS servers. If no reply is received, it forwards the request to IPv6 DNS servers.
· A DNS proxy forwards an IPv6 name query first to IPv6 DNS servers. If no reply is received, it forwards the request to IPv4 DNS servers.
Procedure
1. Enter system view.
system-view
2. Specify a DNS server address.
¡ Specify a DNS server address in system view.
IPv4:
dns server ip-address [ vpn-instance vpn-instance-name ]
IPv6:
ipv6 dns server ipv6-address [ interface-type interface-number ] [ vpn-instance vpn-instance-name ]
¡ Execute the following commands in sequence to specify a DNS server IPv4 address in interface view.
interface interface-type interface-number
dns server ip-address [ vpn-instance vpn-instance-name ]
By default, no DNS server address is specified.
Configuring the DNS transparent proxy
About this task
DNS transparent proxy modifies the source address in the DNS request so that the DNS client seems to receive a DNS reply directly from the DNS server. This feature is applicable to domain name-based policies, such as security policies and bandwidth policies.
The DNS client does not configure the DNS server address as the DNS transparent proxy address, which simplifies DNS client configurations. As a best practice, enable DNS transparent proxy in some load balancing scenarios.
The device enabled with DNS transparent proxy monitors received DNS requests and replies and records the DNS mapping as follows:
1. The DNS transparent proxy monitors all received DNS packets. After receiving a DNS request, the DNS transparent proxy specifies a local IP address that can reach the DNS server as the source IP address in the request.
2. After receiving the DNS reply, the DNS transparent proxy records the DNS mapping and forwards the reply to the DNS client.
3. The DNS transparent proxy searches the local entries after receiving another request. If the requested information is found, the DNS transparent proxy returns a DNS reply to the client. If the requested information is not found, the DNS proxy forwards the query to the DNS server for domain name resolution.
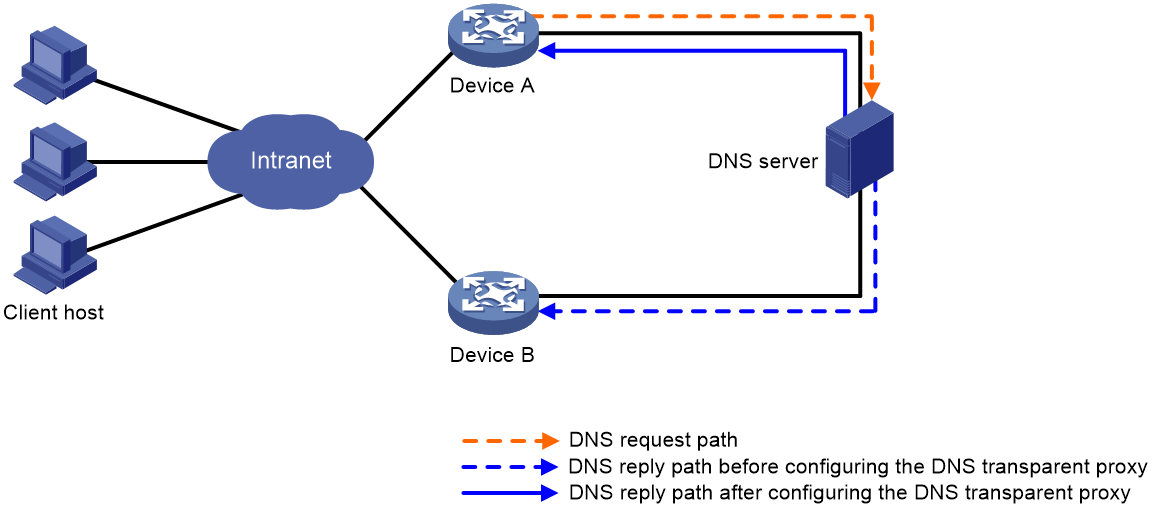
Figure 4 shows the DNS transparent proxy conceptual diagram.
Figure 4 DNS transparent proxy conceptual diagram
A DNS transparency proxy operates as follows:
1. Device A is enabled with DNS transparency proxy. After receiving a DNS request, Device A changes the source address in the request to its own address and forwards the query to the DNS server.
2. After receiving the DNS reply, Device A records the DNS mapping and forwards the reply to the DNS client.
Restrictions and guidelines
The DNS transparent proxy and DNS snooping features cannot be both configured.
The DNS transparent proxy is not VPN-aware. The input interface and output interface of DNS packets must belong to the same VPN.
Procedure
1. Enter system view.
system-view
2. (Optional.) Set the TTL value for DNS entries.
dns cache ttl { maximum max-value | minimum min-value } *
By default, the TTL value for DNS entries is the TTL value in the DNS reply.
3. Enable DNS transparent proxy.
dns transparent-proxy enable
By default, DNS transparent proxy is disabled.
Configuring DNS spoofing
Restrictions and guidelines
· You can configure DNS spoofing for both public network and VPN instances.
· After DNS spoofing takes effect, the device spoofs a DNS request even though a matching static DNS entry exists.
Prerequisites
The DNS proxy is enabled on the device.
No DNS server or route to any DNS server is specified on the device.
Procedure
1. Enter system view.
system-view
2. Enable DNS proxy.
dns proxy enable
By default, DNS proxy is disabled.
3. Enable DNS spoofing and specify the IP address used to spoof DNS requests. Choose one option as needed:
IPv4:
dns spoofing ip-address [ vpn-instance vpn-instance-name ]
IPv6:
ipv6 dns spoofing ipv6-address [ vpn-instance vpn-instance-name ]
By default, DNS spoofing is disabled.
Configuring DNS snooping
About this task
DNS snooping is applicable to domain name-based policies, such as security policies and bandwidth policies. To filter traffic based on domain names, the DNS mapping is required. The device enabled with DNS snooping monitors received DNS requests and replies. If the domain name in a DNS request matches a policy, the device records the DNS mapping after receiving a DNS reply and reports the mapping to the policy for traffic filtering. If the domain name does not match a policy, the device does not record the DNS mapping.
Restrictions and guidelines
DNS snooping only works between the DNS client and DNS server, or the DNS client and DNS proxy.
The DNS snooping and DNS transparent proxy features cannot be both configured.
The DNS snooping feature is not VPN-aware. The input interface and output interface of DNS packets must belong to the same VPN.
Procedure
1. Enter system view.
system-view
2. (Optional.) Set the TTL value for DNS entries.
dns cache ttl { maximum max-value | minimum min-value } *
By default, the TTL value for DNS entries is the TTL value in the DNS reply.
3. Enable DNS snooping.
dns snooping enable
By default, DNS snooping is disabled.
Enabling DNS snooping logging
About this task
The DNS proxy searches the static domain name resolution table and dynamic domain name resolution cache after receiving a request.
· If the requested information is found, the DNS proxy returns a DNS reply to the client.
· If the requested information is not found, the DNS proxy sends the request to the designated DNS server.
Too many requests received at the same time will increase network load and affect the performance of the DNS proxy and DNS server. To avoid this issue, you can configure DNS snooping logging on the device between the DNS client and DNS proxy, or the DNS client and DNS server.
The device configured with DNS snooping monitors and records for received DNS queries and responses. Also, you can configure the device to generate and send DNS snooping logs to the fast log module. The administrator can locate and troubleshoot issues based on the logs. For information about the fast log output configuration, see Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable DNS snooping logging.
dns snooping log enable
By default, DNS snooping logging is enabled.
Configuring a DNS packet rate limit
About this task
Perform this task to limit the rate of incoming DNS packets on interfaces. An interface will discard DNS packets exceeding the specified rate limit.
Restrictions and guidelines
This feature takes effect only when the DNS transparent proxy or DNS snooping logging feature is enabled.
Procedure
1. Enter system view.
system-view
2. Set the DNS packet rate limit.
dns snooping rate-limit rate
By default, the rate of incoming DNS packets is not limited.
Configuring the DNS trusted interface
About this task
This task enables the device to use only the DNS suffix and domain name server information obtained through the trusted interface. The device can then obtain the correct resolved IP address. This feature protects the device against attackers that act as the DHCP server to assign incorrect DNS suffix and domain name server address.
Restrictions and guidelines
You can configure a maximum of 128 DNS trusted interfaces.
Procedure
1. Enter system view.
system-view
2. Specify the DNS trusted interface.
dns trust-interface interface-type interface-number
By default, no DNS trusted interface is specified.
Specifying the source interface for DNS packets
About this task
This task enables the device to always use the primary IP address of the specified source interface as the source IP address of outgoing DNS packets. This feature applies to scenarios in which the DNS server responds only to DNS requests sourced from a specific IP address. If no IP address is configured on the source interface, no DNS packets can be sent out.
Restrictions and guidelines
When sending an IPv6 DNS request, the device follows the method defined in RFC 3484 to select an IPv6 address of the source interface.
You can configure only one source interface on the public network or a VPN instance. You can configure source interfaces for both public network and VPN instances.
Make sure the source interface belongs to the specified VPN instance if you specify the vpn-instance vpn-instance-name option.
Procedure
1. Enter system view.
system-view
2. Specify the source interface for DNS packets.
dns source-interface interface-type interface-number [ vpn-instance vpn-instance-name ]
By default, no source interface for DNS packets is specified.
Setting the DSCP value for outgoing DNS packets
About this task
The DSCP value of a packet specifies the priority level of the packet and affects the transmission priority of the packet. A bigger DSCP value represents a higher priority.
Procedure
1. Enter system view.
system-view
2. Set the DSCP value for DNS packets sent by a DNS client or a DNS proxy.
IPv4:
dns dscp dscp-value
By default, the DSCP value is 0 in IPv4 DNS packets sent by a DNS client or a DNS proxy.
IPv6:
ipv6 dns dscp dscp-value
By default, the DSCP value is 0 in IPv6 DNS packets sent by a DNS client or a DNS proxy.
Configuring DNS filtering
About this task
Enabled with DNS filtering, the DNS proxy matches the domain names in DNS requests with the host names on the allowlist or denylist to filter in or discard DNS requests.
The DNS proxy uses DNS filtering to filter DNS requests as follows:
· If the allowlist has a matching host name or the denylist has no matching host name with the domain name in the received DNS request, the DNS proxy filters in the request. After receiving a DNS reply, the DNS proxy records the DNS mapping and forwards the reply to the DNS client.
· If the denylist has a matching host name or the allowlist has no matching host name with the domain name in the received DNS request, the DNS proxy discards the DNS request.
To implement a strict access control, use an allowlist to filter DNS requests. To implement a loose access control, use a denylist to filter DNS requests.
Restrictions and guidelines
To add multiple host names to the allowlist or denylist, repeat this command. However, a host name cannot be added to both the denylist and allowlist.
Procedure
1. Enter system view.
system-view
2. Enable DNS filtering and add a host name to the allowlist or denylist.
dns filter { allowlist | denylist } hostname
By default, DNS filtering is disabled.
Display and maintenance commands for DNS
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display DNS suffixes. |
display dns domain [ dynamic ] [ vpn-instance vpn-instance-name ] |
|
Display the domain name resolution table. |
display dns host [ ip | ipv6 ] [ vpn-instance vpn-instance-name ] |
|
Display IPv4 DNS server information. |
display dns server [ dynamic ] [ vpn-instance vpn-instance-name ] |
|
Display IPv6 DNS server information. |
display ipv6 dns server [ dynamic ] [ vpn-instance vpn-instance-name ] |
|
Clear dynamic DNS entries. |
reset dns host [ ip | ipv6 ] [ vpn-instance vpn-instance-name ] |
|
Clear log statistics for incoming DNS packets. |
reset dns snooping log statistics |
Troubleshooting DNS configuration
Failure to resolve IPv4 addresses
Symptom
After enabling dynamic domain name resolution, the user cannot get the correct IP address.
Solution
To resolve the problem:
1. Use the display dns host ip command to verify that the specified domain name is in the cache.
2. If the specified domain name does not exist, check that the DNS client can communicate with the DNS server.
3. If the specified domain name is in the cache, but the IP address is incorrect, check that the DNS client has the correct IP address of the DNS server.
4. Verify that the mapping between the domain name and IP address is correct on the DNS server.
Failure to resolve IPv6 addresses
Symptom
After enabling dynamic domain name resolution, the user cannot get the correct IPv6 address.
Solution
To resolve the problem:
1. Use the display dns host ipv6 command to verify that the specified domain name is in the cache.
2. If the specified domain name does not exist, check that dynamic domain name resolution is enabled, and that the DNS client can communicate with the DNS server.
3. If the specified domain name is in the cache, but the IPv6 address is incorrect, check that the DNS client has the correct IPv6 address of the DNS server.
4. Verify that the mapping between the domain name and IPv6 address is correct on the DNS server.