- Table of Contents
-
- 16-High Availability Configuration Guide
- 00-Preface
- 01-Interface backup configuration
- 02-CFD configuration
- 03-DLDP configuration
- 04-VRRP configuration
- 05-Layer 3 connection keepalive configuration
- 06-Error code detection configuration
- 07-High availability group configuration
- 08-BFD configuration
- 09-Process placement configuration
- 10-Track configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-High availability group configuration | 913.55 KB |
Contents
Operating modes of the HA group
HA group member switchover mechanisms
Associating the HA group with VRRP
Associating the HA group with routing protocols
Transparent in-path deployment of the HA group
Restrictions: Hardware compatibility with the HA group
Restrictions and guidelines: HA group configuration
Member device restrictions and guidelines
Interface restrictions and guidelines
HA channel restrictions and guidelines
HA group deployment restrictions and guidelines
Feature compatibility restrictions
Hardware environment consistency
Software environment consistency
Network interconnection restrictions
Configuring the HA control channel
Configuring the HA data channel
Enabling service entry hot backup
Configuring HA configuration synchronization
Enabling traffic switchover upon failure recovery
Configuring the active/standby mode
Configuring the dual-active mode
Associating the HA group with VRRP
Associating the HA group with routing protocols
Configuring HA group transparent in-path deployment
Enabling the HA group to monitor interfaces
Enabling the HA group to monitor VLANs
Associating the HA group with Track
Performing an active/standby switchover
Configuring service features on the HA group
HA group support for DPI services
Routed in-path deployment in active/standby mode
Routed in-path deployment in dual-active mode
Transparent in-path deployment in active/standby mode
Transparent in-path deployment in dual-active mode
Display and maintenance commands for the HA group
HA group configuration examples (IPv4)
Example: Configuring the HA group in active/standby mode in collaboration with VRRP
Example: Configuring the HA group in dual-active mode in collaboration with VRRP
Example: Configuring the HA group in active/standby mode in collaboration with a routing protocol
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol
Example: Configuring a transparent in-path HA group in active/standby mode
Example: Configuring a transparent in-path HA group in dual-active mode
Example: Configuring NAT on the HA group in active/standby mode in collaboration with VRRP
Example: Configuring NAT on the HA group in dual-active mode in collaboration with VRRP
HA group configuration examples (IPv6)
Example: Configuring the HA group in active/standby mode in collaboration with VRRP
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol
Configuring the HA group
About the HA group
The high availability (HA) group is a device-level HA solution. It enables two devices to back up each other dynamically to ensure user service continuity upon failure of one of the devices.
The HA group works with Remote Backup Management (RBM) to manage multiple VRRP groups or adjust the link costs for routing protocols on two member devices to ensure that the devices have consistent roles and states. The HA group can synchronize important configuration and service entries between the devices to ensure service continuity. Two devices must have the same software and hardware environments to join the HA group.
Application scenario
As shown in Figure 1, typically redundant egress devices are deployed at the border between the external and internal networks to prevent a single point of failure from interrupting traffic forwarding. When one egress device fails, traffic is switched to a different path.
Figure 1 HA group network model
Basic HA group concepts
Basic HA group concepts are as follows:
· Primary and secondary roles—The primary and secondary roles are assigned to the two devices in the HA group to control the configuration synchronization between the devices.
· Active and standby states—Determine which device forwards and processes traffic in the data plane. The active device forwards traffic of services and backs up service entries to the standby device in real time. When the active device fails, the standby device takes over the active role to ensure service continuity.
· HA channels—Transmit status information, important configuration, and service entries between the HA group members.
· HA group modes—Include active/standby mode and dual-active mode. In active/standby mode, the active device processes all services. In dual-active mode, both devices process services to increase the capability of the HA group and load share traffic.
· HA packets—RBM packets transmitted through TCP over the HA channels between the HA group members.
Operating modes of the HA group
The HA group supports the active/standby and dual-active modes.
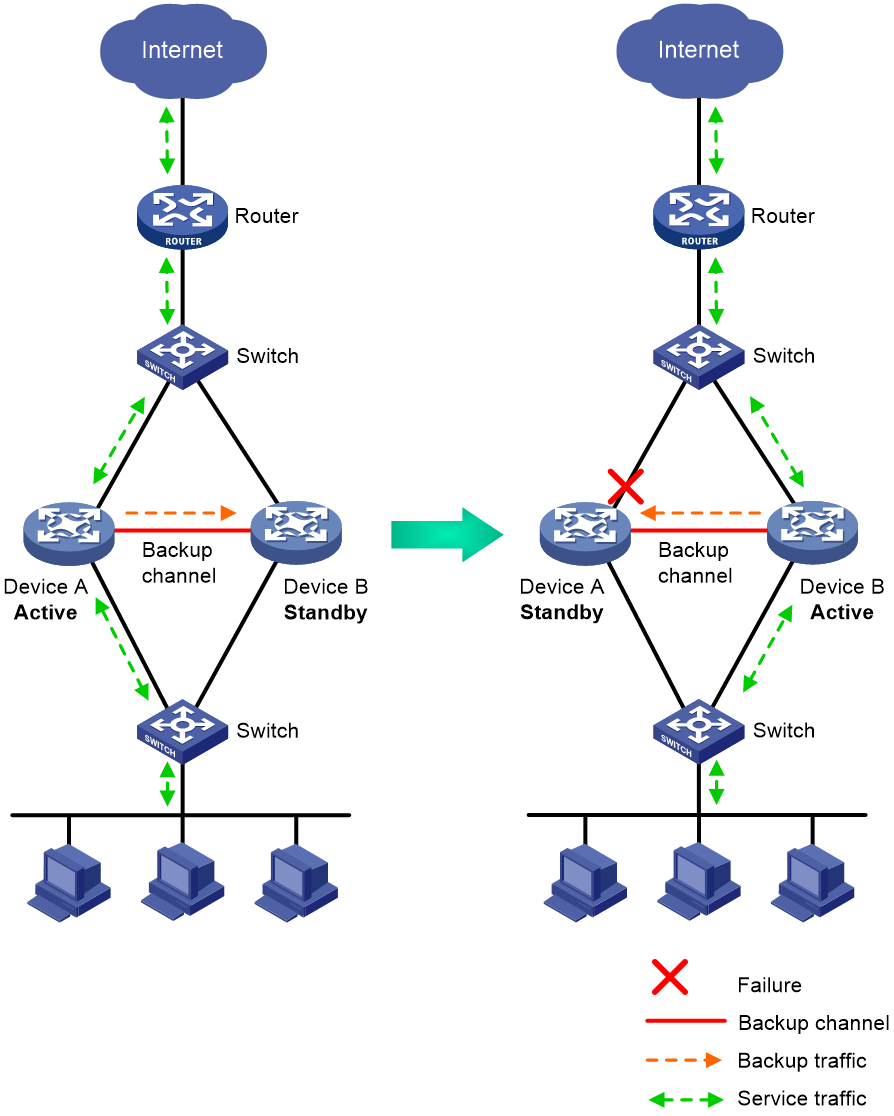
Active/standby mode
In active/standby mode, one device is active to process services, and the other device stands by, as shown in Figure 2. When an interface or link on the active device fails or when the active device fails, the standby device becomes active to process services.
Figure 2 Active/standby mode of the HA group
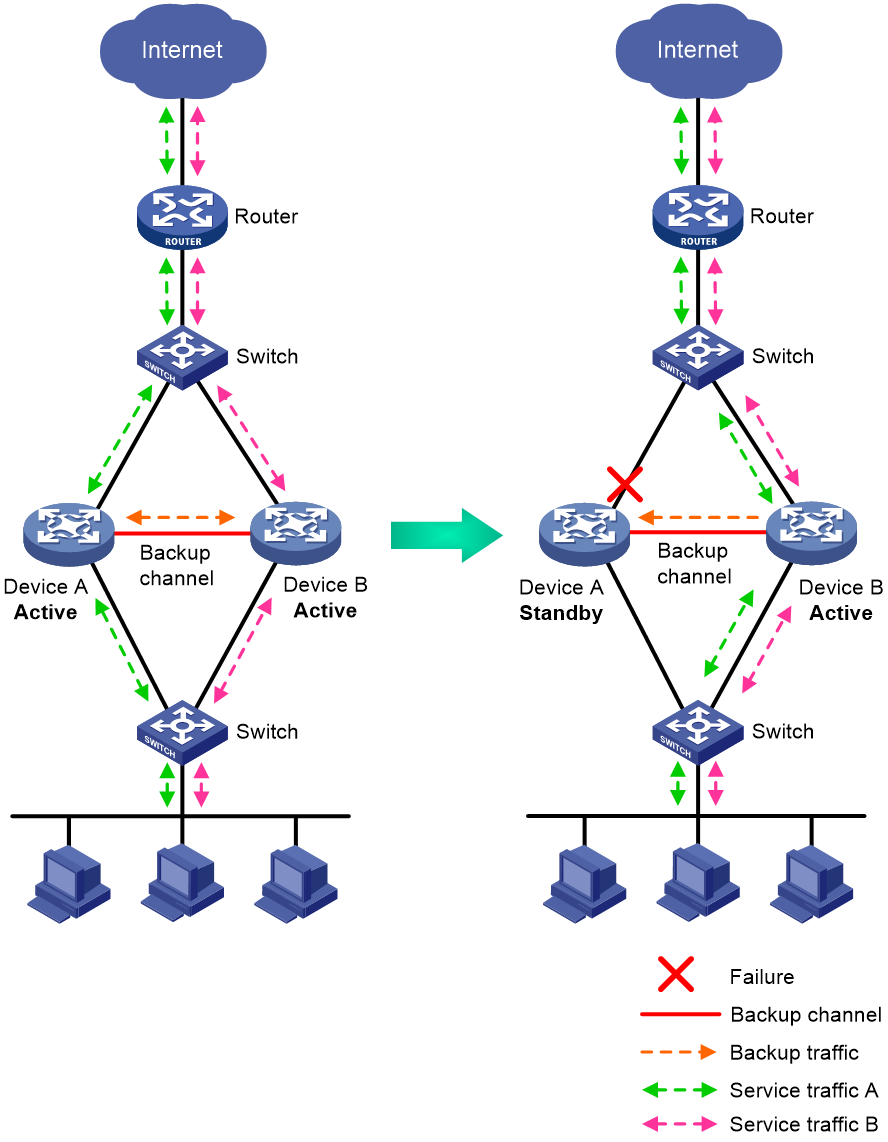
Dual-active mode
In dual-active mode, both devices process services to increase capability of the HA group, as shown in Figure 3. When one device fails, its traffic is switched to the other device for forwarding.
Figure 3 Dual-active mode of the HA group
HA data synchronization
HA packets
HA packets include the following:
· Keepalive packets—Transmitted periodically between the HA group members for peer availability detection.
· Control packets—Control active/standby switchovers based on the running status.
· Backup packets—Back up configuration and service entries between the HA group members.
· Configuration consistency check packets—Check whether the HA group members have consistent configuration.
· Transparent transmission packets—Transmit or replicate asymmetric-path traffic between the HA group members.
HA channels
The HA group transmits HA group status, important configuration, and service entries between the HA group members through the following channels:
· Control channel—Transmits data by using packets, including HA group status packets, configuration consistency check packets, and packets used for configuration synchronization.
· Data channel—Transmits backup packets and packets that require transparent transmission. The data channel uses the hardware driver for data transmission and supports only Layer 2 forwarding.
The control channel uses the keepalive mechanism of TCP for reachability detection. Each member device periodically sends HA keepalive packets to the HA peer over the HA control channel. If a device has not received any responses from the peer when the maximum number of HA keepalive attempts is reached, the HA control channel is disconnected.
Service entry backup
The HA group backs up the service entries generated on the active device to the standby device to prevent service interruption when an active/standby switchover occurs.
Security devices generate a session entry for each dynamic connection. In the HA group, only the active device processes traffic and generates session entries. To ensure service continuity, the active device backs up its session entries to the standby device in real time. After an active/standby switchover, the new active device can forward the packets of the existing services based on the session entries without interruption.
The HA group can perform hot backup for the following service entries:
· NAT port blocks.
· Session entries.
· Session relation entries.
· Entries generated by security service modules.
Configuration backup
The HA group backs up important configuration from the primary device to the secondary device to prevent service interruption when an active/standby switchover occurs.
· When both devices are operating correctly, the primary device synchronizes configuration to the secondary device. The configuration on the secondary device is overwritten. As a best practice to ensure correct operation of the HA group, enable configuration backup on the primary device.
· When one of the devices reboots, the device that completes reboot obtains configuration from the device that is not rebooted. The configuration on the rebooted device is overwritten.
The HA group supports both automatic backup and manual backup.
The HA group can perform configuration backup for the following services:
· Resources—VPN instance, ACL (excluding the acl copy command), object group, time range, security zone, session management, APR, and AAA.
· DPI—Application layer inspection engine, IPS, and URL filter.
· Polices—Security policy, ASPF, attack detection and prevention (excluding the blacklist ip command), connection limit, NAT, AFT, and bandwidth management.
· Logs—Flow log (excluding the userlog flow export source-ip command).
· VPN—SSL VPN.
· Any other services—VLAN and information center (excluding the info-center loghost source command).
Configuration consistency check
The HA group verifies configuration consistency between the HA group members by using configuration consistency check packets. If a device detects configuration inconsistency, it generates a log for you to manually synchronize configuration.
Configuration consistency check operates as follows:
1. The primary device sends configuration consistency check packets to the secondary device and collects configuration digests of related modules at the same time.
2. The secondary device receives the packets, encapsulates its configuration digests into configuration consistency check packets, and sends these packets to the primary device.
3. The primary device compares its configuration digests with those of the secondary device. If inconsistency is detected, the primary device generates a log.
HA group member switchover mechanisms
In the HA group, an active/standby switchover occurs if one device fails or its links fail. The other device that operates correctly will take over to process all traffic that traverse the HA group to ensure service continuity. The following events can trigger an active/standby switchover.
· Disconnection of the HA control channel.
If the HA control channel is disconnected when both member devices are operating correctly, both devices become active devices. However, the devices will leave the HA group in this situation, and forwarding of asymmetric-path traffic will be interrupted.
· Failure of the active device.
· Failure of the interface monitored by the HA group on the active device.
· State change to Negative of any track entry monitored by the HA group on the active device.
When an active/standby switchover occurs, the HA group collaborates with other modules to direct traffic to the new active device.
· When working with VRRP, the HA group places all VRRP groups on the failed device to backup state.
· When working with a routing protocol, the HA group increases the link costs of routes on the failed device.
Associating the HA group with VRRP
About HA group and VRRP association
You can use the HA group and VRRP in combination to control master/backup switchover for device role consistency (master or backup) in multiple VRRP groups. This ensures that both inbound and outbound traffic can be switched to the new master for symmetric forwarding upon device failure.
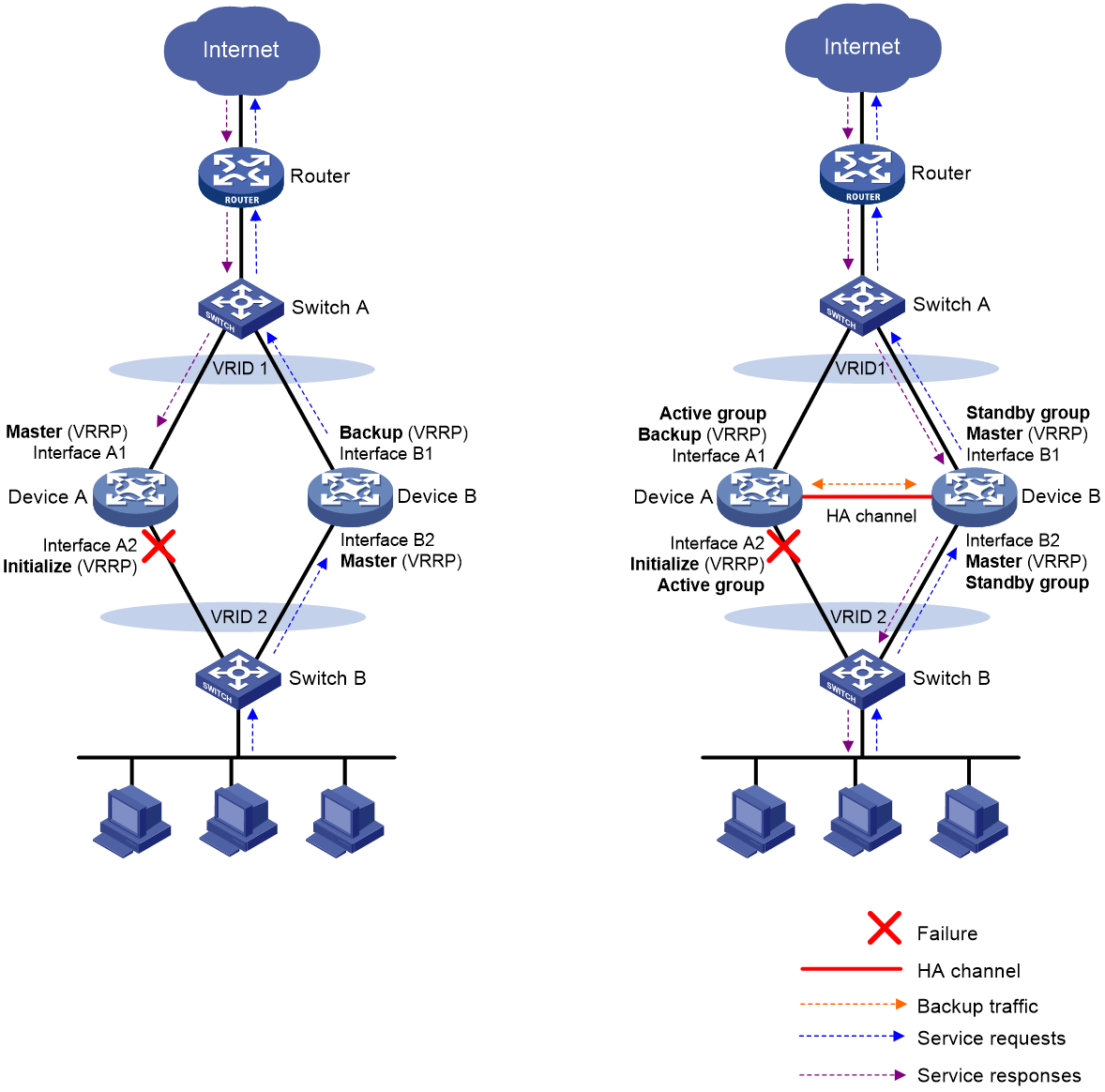
Figure 4 illustrates VRRP association with the HA group in active/standby mode.
· As shown in the left, VRRP cannot ensure symmetric forwarding upon failure on a device, which causes traffic interruption.
· As shown in the right, after the HA control channel is established, the HA group determines the roles of the devices in all VRRP groups. The master election mechanism of VRRP no longer takes effect. If the HA control channel is disconnected, the master election mechanism of VRRP takes effect again.
Figure 4 VRRP and HA group association
VRRP active/standby group
The HA group is associated with VRRP by VRRP active and standby groups.
A VRRP active/standby group can be in master or backup state, which determines the state of devices in the associated VRRP groups. For example, if a VRRP active group is in master state, all devices in the associated VRRP groups are masters.
The initial state of a VRRP active/standby group is depends on the HA group mode.
· Active/Standby mode—On the primary device, the initial state is master for the VRRP active and standby groups. On the secondary device, the initial state is backup for the VRRP active and standby groups.
· Dual-active mode—The state of a VRRP active/standby group is not affected by the HA roles. The initial state is master for the VRRP active group and is backup for the VRRP standby group.
VRRP master election in the HA group environment
After the HA group is associated with VRRP, the HA group determines the roles of the devices in the VRRP groups. As shown in Figure 4, Device A is the master in VRRP group 1 and VRRP group 2, and Device B is the backup in VRRP group 1 and VRRP group 2. When Interface A2 on Device A fails, the following events occur:
1. The HA group receives an interface failure event and sends the status change information of the VRRP active and standby groups to Device B.
2. Device B sets its role to master in the VRRP standby group and then becomes the master in VRRP group 1 and VRRP group 2.
3. Device B sends a response to Device A after the master/backup switchover.
4. Device A sets its role to backup in the VRRP active group and then becomes the backup in VRRP group 1 and VRRP group 2.
When Interface A2 recovers, the HA group performs another master/backup switchover following the same procedure. Traffic is switched back to Device A after the switchover.
ARP and MAC learning in VRRP
When the members of a VRRP group receive an ARP request for the group's virtual IP address, the master replies with the group's virtual MAC address. This allows the upstream and downstream Layer 2 devices and hosts to learn the virtual MAC address.
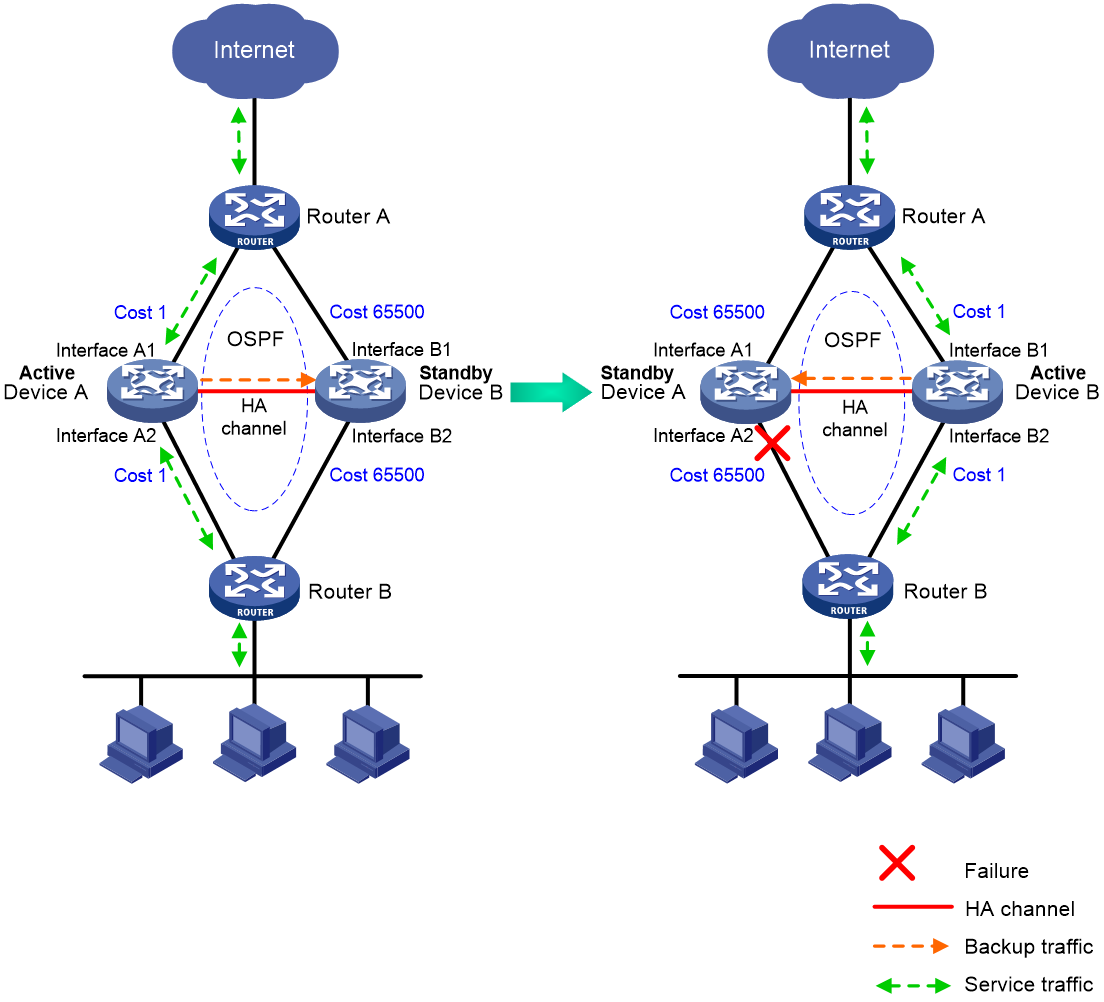
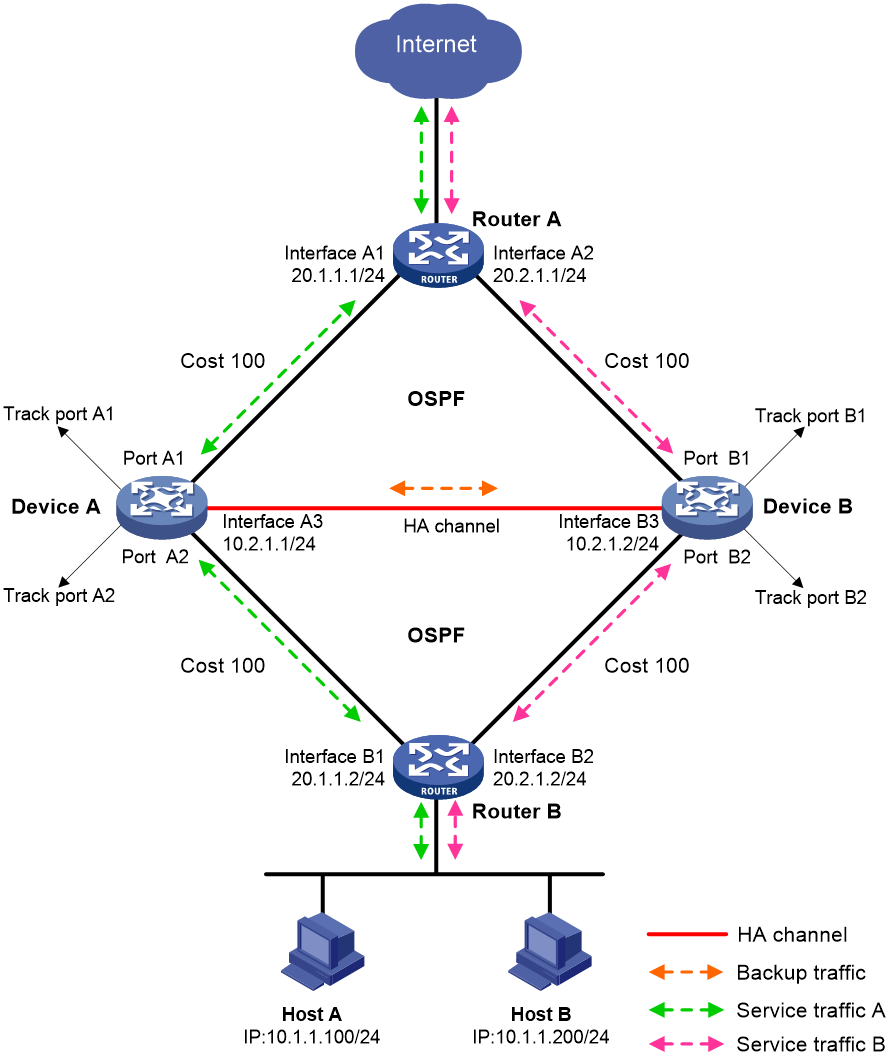
Associating the HA group with routing protocols
You can use the HA group to enable the routing protocols on the standby device to advertise modified link cost. The feature ensures that both inbound and outbound traffic can be switched to the new active device for symmetric forwarding.
This feature requires associating the HA group with Track to perform active/standby switchover upon link or interface failures.
Figure 5 illustrates OSPF association with the HA group in active/standby mode.
· As shown in the left, Device A (active device) advertises link cost 1 based on OSPF configuration. Device B (standby device) advertises link cost 65500 modified by the HA group. Both inbound and outbound traffic are forwarded through Device A.
· As shown in the right, when interface A2 fails, Device A and Device B perform an active/standby switchover. After the switchover is complete, Device B (active device) advertises link cost 1 based on OSPF configuration. Device A (standby device) advertises link cost 65500 modified by the HA group. Both inbound and outbound traffic are forwarded through Device B.
Figure 5 OSPF and HA group association
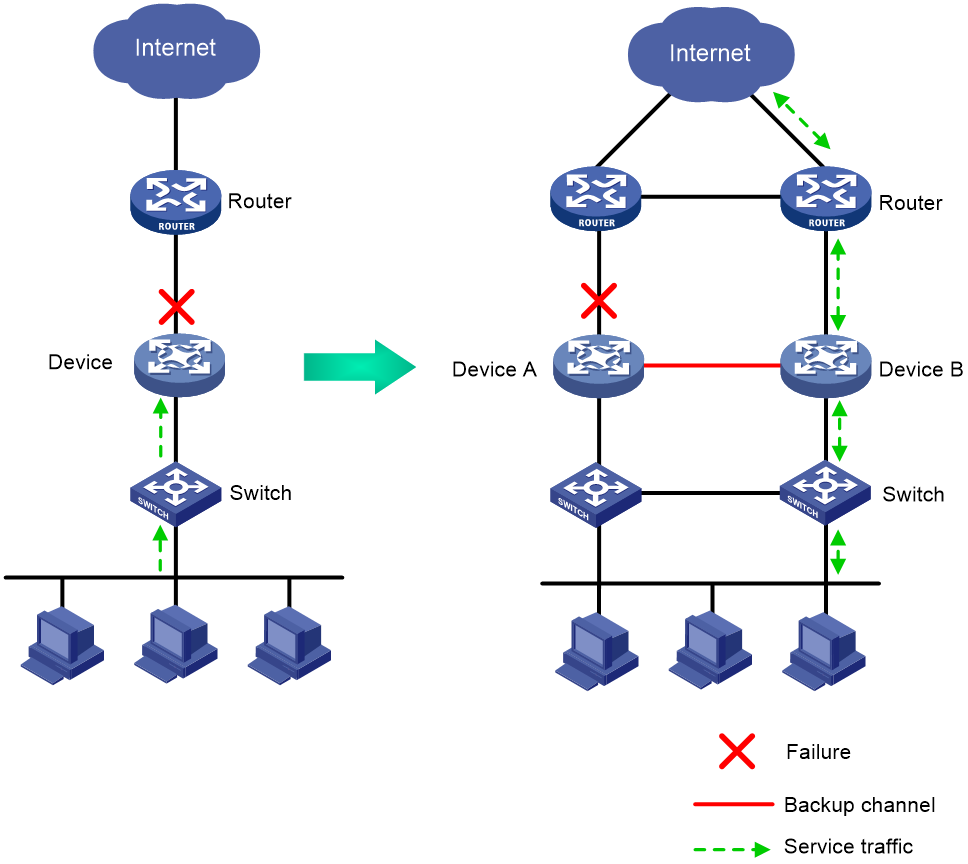
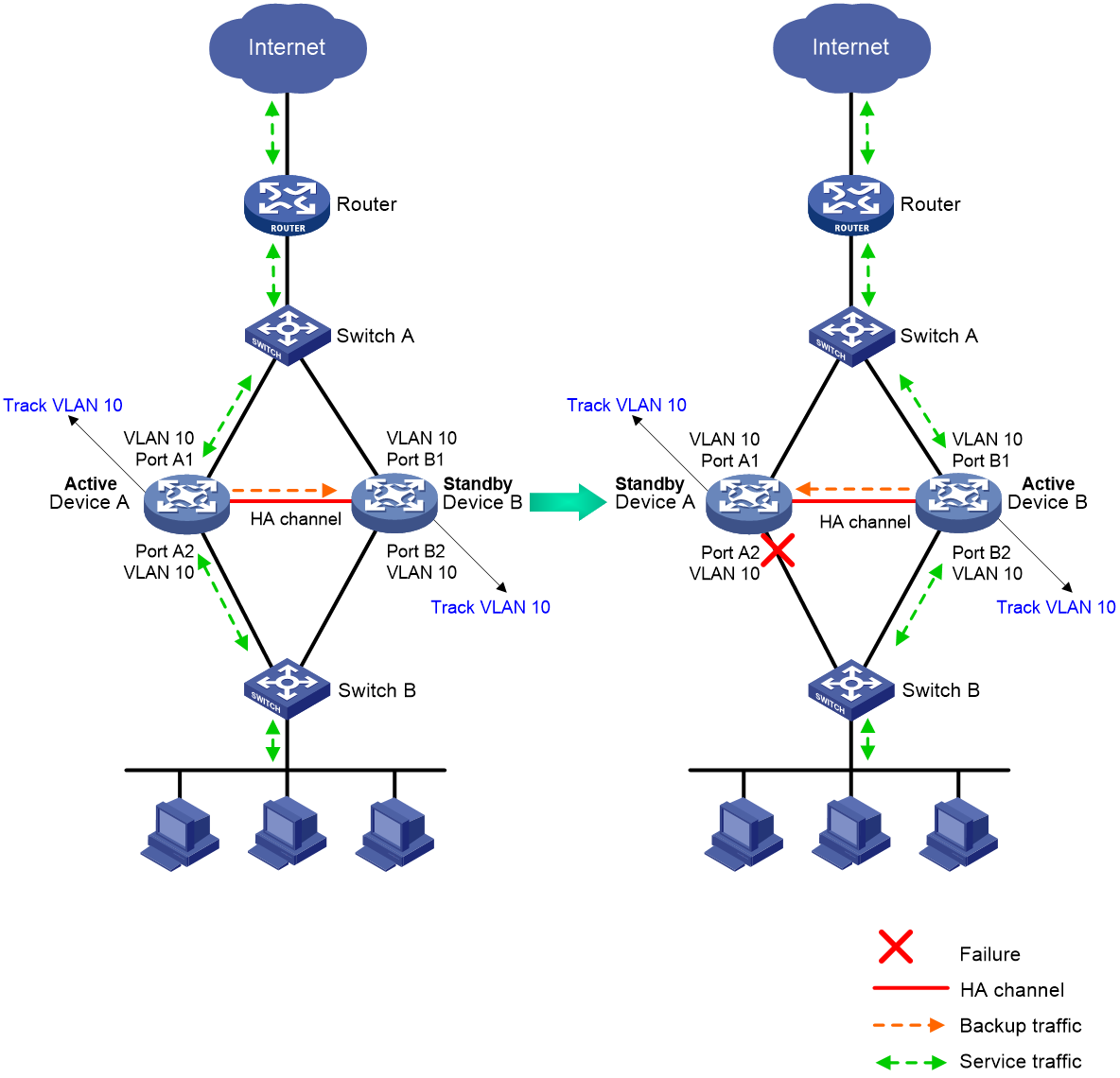
Transparent in-path deployment of the HA group
When you use this networking scheme, you can use the track vlan or track interface command to enable collaboration between uplink and downlink interfaces. The Track configuration ensures that a group of interfaces have the same status, and uplink and downlink traffic can be switched simultaneously between the member devices.
The following information uses the track vlan setting as an example to describe how interfaces collaborate:
· As shown in Figure 6, when both Device A (active) and Device B (standby) are operating correctly, tracked VLAN 10 is in active state on Device A and in inactive state on Device B. As a result, Device A forwards all traffic that traverses the HA group.
· As shown in Figure 6, when downlink Port A2 of Device A fails, Device A and Device B switch their roles. Then, the HA group places VLAN 10 in inactive state on Device A (standby) and in active state on Device B (active). As a result, Device B forwards all traffic that traverses the HA group.
Figure 6 Transparent in-path deployment of the HA group
Restrictions: Hardware compatibility with the HA group
|
Hardware |
HA group compatibility |
|
MSR810, MSR810-W, MSR810-W-DB, MSR810-LM, MSR810-W-LM, MSR810-LM-HK, MSR810-W-LM-HK, MSR810-LM-CNDE-SJK, MSR810-CNDE-SJK |
Yes |
|
MSR810-10-PoE |
No |
|
MSR810-LMS, MSR810-LUS |
No |
|
MSR810-LMS-EA, MSR810-LME |
No |
|
MSR1004S-5G |
No |
|
MSR2600-6-X1, MSR2600-15-X1 |
Yes |
|
MSR2600-10-X1 |
No |
|
MSR 2630 |
No |
|
MSR3600-28, MSR3600-51 |
No |
|
MSR3600-28-SI, MSR3600-51-SI |
No |
|
MSR3600-28-X1, MSR3600-28-X1-DP, MSR3600-51-X1, MSR3600-51-X1-DP |
No |
|
MSR3610-I-DP, MSR3610-IE-DP, MSR3610-IE-ES, MSR3610-IE-EAD, MSR-EAD-AK770, MSR3610-I-IG, MSR3610-IE-IG |
No |
|
MSR3610-X1, MSR3610-X1-DP, MSR3610-X1-DC, MSR3610-X1-DP-DC, MSR3620-X1, MSR3640-X1 |
Yes |
|
MSR3610, MSR3620, MSR3620-DP, MSR3640, MSR3660 |
No |
|
MSR3610-G, MSR3620-G |
No |
|
MSR3640-X1-HI |
No |
|
Hardware |
HA group compatibility |
|
MSR810-W-WiNet, MSR810-LM-WiNet |
No |
|
MSR830-4LM-WiNet |
No |
|
MSR830-5BEI-WiNet, MSR830-6EI-WiNet, MSR830-10BEI-WiNet |
No |
|
MSR830-6BHI-WiNet, MSR830-10BHI-WiNet |
No |
|
MSR2600-6-WiNet, MSR2600-10-X1-WiNet |
No |
|
MSR2630-WiNet |
No |
|
MSR3600-28-WiNet |
No |
|
MSR3610-X1-WiNet |
No |
|
MSR3610-WiNet, MSR3620-10-WiNet, MSR3620-DP-WiNet, MSR3620-WiNet, MSR3660-WiNet |
No |
|
Hardware |
HA group compatibility |
|
MSR2630-XS |
No |
|
MSR3600-28-XS |
No |
|
MSR3610-XS |
No |
|
MSR3620-XS |
No |
|
MSR3610-I-XS |
No |
|
MSR3610-IE-XS |
No |
|
MSR3620-X1-XS |
Yes |
|
MSR3640-XS |
Yes |
|
MSR3660-XS |
No |
|
Hardware |
HA group compatibility |
|
MSR810-LM-GL |
No |
|
MSR810-W-LM-GL |
No |
|
MSR830-6EI-GL |
No |
|
MSR830-10EI-GL |
No |
|
MSR830-6HI-GL |
No |
|
MSR830-10HI-GL |
No |
|
MSR1004S-5G-GL |
No |
|
MSR2600-6-X1-GL |
No |
|
MSR3600-28-SI-GL |
No |
Restrictions and guidelines: HA group configuration
Member device restrictions and guidelines
The HA group can contain a maximum of two devices.
To ensure that the traffic size is within the processing capability of one device upon failure of the other device, make sure the throughput of each device does not exceed 50% of its capability.
For the features or signature libraries that require licenses, purchase separate licenses and activate them on the HA group member devices.
Interface restrictions and guidelines
Do not use the HA group in combination with the features that obtain IP addresses automatically, DHCP client for example. The interfaces on the HA group must use static IP addresses.
If service interfaces work in Layer 2 mode, assign uplink and downlink service interfaces to the same VLAN.
HA channel restrictions and guidelines
The HA channels are set up over the keepalive link that is a direct link or traverses only Layer 2 switches.
When you select interfaces for HA channel setup, follow these restrictions and guidelines:
· To ensure correct transmission over the HA channels, set the MTUs of the interfaces to 1500 bytes or larger.
· Use physical interfaces or aggregate interfaces. Do not use subinterfaces or aggregation member ports.
· As a best practice, use the same physical or logical link to convey the HA data and control channels.
When configuration backup is in progress, do not perform active/standby switchovers or remove or install service modules. To view the backup progress, execute the display remote-backup-group status command.
If the HA group performs asymmetric forwarding, use the session aging-time state fin command to set the aging time for TCP sessions in FIN_WAIT state to 15 seconds. This configuration speeds up session entry aging when TCP connections disconnect and thus saves system resources. For more information about the session aging-time state command, see session management commands in Security Command Reference.
HA group deployment restrictions and guidelines
When you deploy the HA group, follow the restrictions and guidelines for the network scheme you have chosen.
Routed in-path HA group deployment between upstream and downstream routers
You can use either active/standby or dual-active mode.
If you use the HA group with a routing protocol, use the adjust-cost enable command to enable the HA group to adjust the link costs for the routing protocol. In addition, associate the HA group with track entries to monitor the status of uplink and downlink interfaces.
Routed in-path HA group deployment between upstream and downstream switches
You can use either active/standby or dual-active mode.
You must use the HA group with VRRP. You do not configure additional link monitoring settings.
Transparent in-path HA group deployment between upstream and downstream routers
You can use either active/standby or dual-active mode.
You must use the track interface command to enable the HA group to monitor the status of uplink and downlink interfaces.
Transparent in-path HA group deployment between upstream and downstream switches
You can use only active/standby mode.
You must use the track vlan command to enable the HA group to monitor the status of uplink and downlink VLANs.
Feature compatibility restrictions
Compatibility with virtual systems
You cannot use the HA group together with contexts.
Compatibility with NAT
When you use NAT on the HA group, follow these restrictions:
· The HA group does not support detecting reachability of NAT address group members or Easy IP.
· NAT address groups cannot contain the IP addresses of any interfaces on the HA group member devices. If you violate this restriction, both HA group member devices will respond to the ARP packets that an upstream device sends to request the IP addresses in the NAT address groups. As a result, ARP conflicts occur.
· The source or destination IP address in a NAT policy does not belong to the interface used for setting up the HA control or data channel. Violation of this restriction causes keepalive link faults.
· If you cannot ensure that a flow identified by a five-tuple is processed by the same device in one direction, you must use the nat remote-backup port-alloc { primary | secondary } command to specify NAT port ranges for the HA group member devices.
When you use NAT on the HA group operating in dual-active mode, follow these restrictions:
· NAT address groups do not support EIM.
· If NAT operates in PAT mode, you must execute the following commands on the NAT group members, one command on one device:
¡ nat remote-backup port-alloc primary
¡ nat remote-backup port-alloc secondary
These commands divide an address group into two halves to avoid conflicts.
· If NAT operates in NO-PAT mode, you must configure two address groups to avoid resource assignment conflicts.
Hardware environment consistency
Before you configure the HA group, verify that the following hardware settings are the same on the devices to be assigned to the HA group:
· Device model.
· Number and type of management interfaces, service interfaces, interfaces for setting up the control channel, and interfaces for setting up the data channel. Do not use one interface for multiple purposes.
· Location, number, and type of disks. A device not with disks installed has small log storage and do not support some types of logs or reports.
Software environment consistency
Before you configure the HA group, verify that the following software settings are the same on the devices to be assigned to the HA group:
· Software environment and version, including boot packages, system packages, feature packages, and patches.
· Licensed signature libraries and features, such as signature library types, signature library version, validation time, and number of licensed resources.
· Interface numbers.
· Type, speed, and number of the interfaces for setting up the control channel. As a best practice, use aggregate interfaces.
· Type, speed, and number of the interfaces for setting up the data channel. As a best practice, use aggregate interfaces.
· Aggregate interface numbers and aggregation member port numbers.
· Multi-CPU packet distribution policy (configurable with the forwarding policy command).
Network interconnection restrictions
The device by default permits the HA packets transmitted over the HA channels. You do not need to configure security policies for the HA packets.
Configure a feature prior to HA group deployment if the HA group cannot back up configuration of the feature. For more information about the features that can be backed up by the HA group, see "Configuration backup."
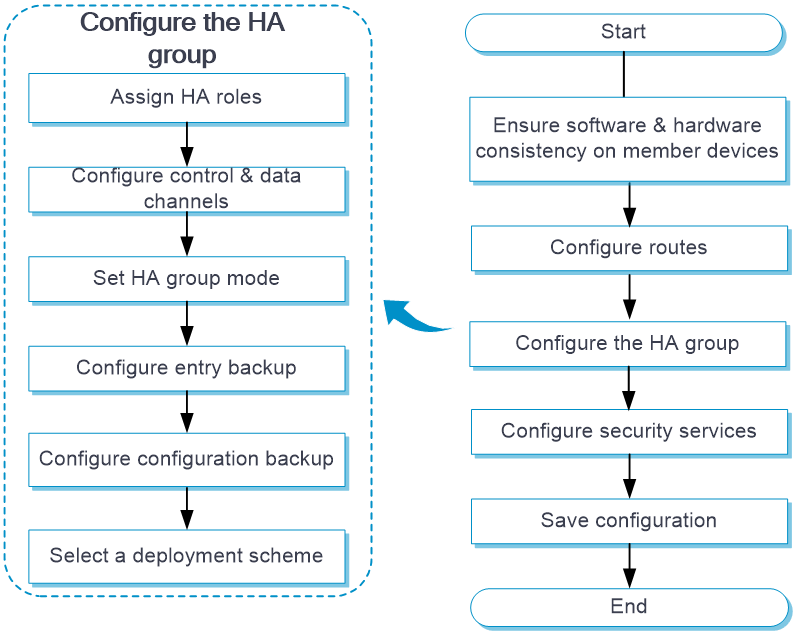
HA group configuration flow
Figure 7 shows the configuration flow for the HA group.
Figure 7 HA group configuration flow chart
HA group tasks at a glance
To configure the HA group, perform the following tasks:
2. Configuring HA data synchronization settings
a. Configuring the HA control channel
b. Configuring the HA data channel
c. Enabling service entry hot backup
d. Configuring HA configuration synchronization
3. Enabling traffic switchover upon failure recovery
4. Setting the HA group mode
Choose one of the following tasks:
¡ Configuring the active/standby mode
¡ Configuring the dual-active mode
5. Configuring HA group associations
Choose one of the following tasks:
¡ Associating the HA group with VRRP
¡ Associating the HA group with routing protocols
¡ Configuring HA group transparent in-path deployment
6. (Optional.) Associating the HA group with Track
7. (Optional.) Performing an active/standby switchover
8. (Optional.) Configuring service features on the HA group
Configuring the HA role
About this task
The HA group backs up important configuration from the primary device to the secondary device to prevent service interruption when an active/standby switchover occurs. The configuration on the secondary device is overwritten. The unidirectional backup mechanism avoids configuration conflicts, especially in dual-active mode. The HA roles can only be manually assigned to devices.
Restrictions and guidelines
You must assign the primary and secondary roles to the two member devices in the HA group, respectively.
As a best practice to ensure correct operation of the HA group, enable configuration backup on the primary device.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Configure the HA role.
device-role { primary | secondary }
By default, the HA role is not configured.
Configuring the HA control channel
About this task
The HA group compares the specified local and peer IP address to determine the device role for setting up the control channel. The device with higher IP address acts as the server, and the other device acts as the client to initiate the TCP connection.
If the port number is configured on the server, the port provides services for the client. If the port number is configured on the client, the port serves as the destination port to establish TCP connection to the server. The source port is randomly generated on the client.
Restrictions and guidelines
You can specify only one peer IP address with the same port number on the HA group member devices. The specified port cannot be the same as the TCP listening port in use.
You can set up an IPv4 control channel or IPv6 control channel, but not both.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Set up an HA control channel. Choose one of the following options:
¡ Set up an IPv4 control channel.
- Configure the peer IPv4 address for setting up the HA control channel.
remote-ip ipv4-address [ port port-number ]
By default, the peer IPv4 address is not configured.
- Configure the local IPv4 address for setting up the HA control channel.
local-ip ipv4-address
By default, the local IPv4 address is not configured.
¡ Set up an IPv6 control channel.
- Configure the peer IPv6 address for setting up the HA control channel.
remote-ipv6 ipv6-address [ port port-number ]
By default, the peer IPv6 address is not configured.
- Configure the local IPv6 address for setting up the HA control channel.
local-ipv6 ipv6-address
By default, the local IPv6 address is not configured.
Configuring the HA data channel
About this task
The HA group can use the same physical interface or different physical interfaces for setting up the HA data channel and control channel.
Perform this task to set up a dedicated data channel that transmits only hot backup packets and the packets that require transparent transmission. This ensures that the packets are not interrupted by other packets transmitted between the HA group member devices and saves link bandwidth.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Configure an HA data channel.
data-channel interface interface-type interface-number
By default, no HA data channel is configured.
Enabling service entry hot backup
About this task
Service entry hot backup enables the active device to back up service entries to the standby device in real time.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable service entry hot backup.
hot-backup enable
By default, service entry hot backup is enabled.
Configuring HA configuration synchronization
About this task
The HA group member devices can synchronize configuration changes in real time and synchronize all configuration in bulk.
· Real-time synchronization—The primary device copies added, deleted, or modified configuration to the secondary device in real time to maintain configuration consistency.
· Bulk synchronization—The primary device backs up important configuration in bulk to the secondary device. The secondary device will delete the settings that are inconsistent with those on the primary device.
After you enable automatic configuration synchronization, the primary device performs a bulk synchronization. Consequent synchronization for configuration changes will be performed in real time.
With automatic configuration synchronization enabled, a bulk synchronization is triggered by the following events:
· The HA control channel is set up for the first time.
· An HA group member device reboots.
· A process restarts.
Restrictions and guidelines
If the amount of configuration to be synchronized is large, bulk synchronization might take one to two hours. To avoid the issue, you can perform one of the following operations:
· Enable automatic configuration synchronization first when you configure the HA group.
· Copy the configuration file to the secondary device during initial network deployment and then enable configuration consistency check.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable automatic configuration synchronization.
configuration auto-sync enable
By default, automatic configuration synchronization is disabled.
4. Enable configuration consistency check.
configuration sync-check [ interval interval ]
By default, configuration consistency check is disabled.
5. (Optional.) Manually synchronize the configuration of the primary device to the secondary device.
configuration manual-sync
This command applies only to the primary device.
Enabling traffic switchover upon failure recovery
About this task
After an active/standby switchover occurs, if the original active device recovers, traffic will not be switched back by default. Perform this task to enable traffic switchover to the original active device upon failure recovery. You can set a delay timer to ensure smooth service switchover.
Restrictions and guidelines
In dual-active mode, you must enable this feature to ensure that both devices can operate after the failure is recovered.
This feature does not take effect on ongoing traffic switchovers. It applies only to subsequent traffic switchovers.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable traffic switchover upon failure recovery.
delay-time delay-time
By default, traffic switchover upon failure recovery is disabled.
Configuring the active/standby mode
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Configure the active/standby mode.
undo backup-mode dual-active
By default, the HA group mode is active/standby.
Configuring the dual-active mode
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Configure the dual-active mode.
backup-mode dual-active
By default, the HA group mode is active/standby.
Associating the HA group with VRRP
Restrictions and guidelines
You can associate only VRRP groups operating in standard mode with the HA group.
Use the HA group in combination with VRRP groups only for in-path HA group deployment between upstream and downstream switches. As a best practice, assign the primary device to the VRRP active group, and assign the secondary device to the VRRP standby group.
You can assign multiple virtual IP addresses to a VRRP group associated with the HA group. Make sure the interfaces in the VRRP group do not own the virtual IP addresses.
You cannot associate a VRRP group with both the HA group and Track.
For an IPv6 VRRP group to work correctly, you must assign it a link-local address and a global unicast address as virtual IPv6 addresses.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
interface interface-type interface-number
3. Associate the HA group with VRRP. Choose one of the following options:
¡ Create an IPv4 VRRP group and associate it with the HA group.
vrrp vrid virtual-router-id virtual-ip virtual-address { active | standby }
By default, no IPv4 VRRP groups exist.
¡ Create an IPv6 VRRP group and associate it with the HA group. Assign a link-local address and a global unicast address as virtual IPv6 addresses to the VRRP group.
vrrp ipv6 vrid virtual-router-id virtual-ip virtual-address link-local { active | standby }
vrrp ipv6 vrid virtual-router-id virtual-ip virtual-address
By default, no IPv6 VRRP groups exist.
Associating the HA group with routing protocols
About this task
The HA group can adjust link cost on the standby device to advertise the following costs for the specified routing protocol:
· Absolute cost—The device advertises an absolute link cost for the routing protocol.
· Calculated cost—The device advertises the original link cost plus the configured increment cost for the specified routing protocol.
Restrictions and guidelines
The feature takes effect on only the standby device.
To ensure switchover of both uplink and downlink traffic to the new active device, configure this feature with the same parameters on both HA group member devices.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable the HA group to adjust the link cost for the specified routing protocol on the standby device.
adjust-cost { bgp | isis | ospf | ospfv3 } enable { absolute [ absolute-cost ] | increment [ increment-cost ] }
By default, the HA group does not adjust the link cost for the specified routing protocol on the standby device.
Configuring HA group transparent in-path deployment
Enabling the HA group to monitor interfaces
About this task
Perform this task to enable the HA group to monitor the interfaces connecting the uplink and downlink devices in HA group transparent in-path deployment. The monitored interfaces can forward packets only when they are all up. If any of the monitored interfaces goes down, none of them will be able to forward packets.
Restrictions and guidelines
The track vlan, track interface, and track commands are mutually exclusive.
The HA group supports monitoring Layer 2 Ethernet interfaces only.
The HA group does not support monitoring member ports of aggregate interfaces.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable the HA group to monitor an interface.
track interface interface-type interface-number
By default, the HA group does not monitor any interfaces.
Enabling the HA group to monitor VLANs
About this task
Perform this task to enable the HA group to monitor the VLANs of the uplink and downlink devices in HA group transparent in-path deployment. The monitored VLANs are active and the member ports can forward packets only when the member ports are all up. If any of the member ports goes down, none of them will be able to forward packets, and all the monitored VLANs will become inactive.
In active/standby mode, the state of monitored VLANs is active on the primary device and inactive on the secondary device.
In dual-active mode, the state of monitored VLANs is active on both HA group member devices.
Restrictions and guidelines
The track vlan, track interface, and track commands are mutually exclusive.
Do not enable the HA group to monitor VLAN 1 (to which all access ports belong by default). This restriction prevents an unused interface in down state from interrupting operation of other interfaces in VLAN 1.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Enable the HA group to monitor a VLAN.
track vlan vlan-id
By default, the HA group does not monitor any VLANs.
Associating the HA group with Track
About this task
Perform this task to associate the HA group with Track to monitor links. If one of the monitored track entries becomes Negative, the HA group performs an active/standby switchover and switches traffic to the new active device to ensure service continuity. For more information about Track, see "Configuring Track."
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Associate the HA group with Track.
track track-entry-number
By default, the HA group is not associated with Track.
Performing an active/standby switchover
About this task
If you want to replace components or upgrade software on the current active device, you can perform this task to switch services to the standby device.
Restrictions and guidelines
This feature applies only when the HA group operates in active/standby mode, and it takes effect on only the active device.
In an HA group and VRRP associated network, performing this task might cause temporary virtual IP address conflict in the VRRP group, which is considered a normal condition.
Procedure
1. Enter system view.
system-view
2. Enter HA group view.
remote-backup group
3. Perform an active/standby switchover.
switchover request
Configuring service features on the HA group
NAT on the HA group
For NAT to operate correctly on the HA group, you must associate NAT features with the VRRP groups. For example, when you use dynamic NAT, static NAT, NAT server, or NAT444, you must associate the feature with the VRRP groups. For more information about NAT features, see Layer 3—IP Services Configuration Guide.
NAT features have similar mechanisms, and the operating mode of the HA group does not change the IP address translation process. This section uses dynamic NAT on the HA group in active/standby mode to explain how NAT works on the HA group.
About NAT on the HA group
When receiving an ARP request with a target IP address that belongs to the subnet of the IP address of a NAT interface, a NAT device replies with the MAC address of the NAT interface.
As shown in Figure 8, dynamic NAT is configured on the HA group that is operating in active/standby mode. If dynamic NAT is not associated with any VRRP group, the devices process the traffic as follows when the host accesses the Internet:
1. When receiving the packets sent by the host, Device A translates the source IP address into a public IP address in the NAT address group and forwards the packets to the router. In this example, the public IP address is in the same subnet as the virtual IP address of uplink VRRP group 1.
2. The router receives the return packets and broadcasts an ARP request for the destination public IP address.
3. Device A and Device B receive the ARP request and reply with the MAC address of their respective uplink interface because they have the same NAT address group configuration.
4. The router might send the return packets to the uplink interface of Device A or Device B, which affects service continuity.
For the router to learn the virtual MAC address of the uplink VRRP group, you must associate NAT features with the VRRP group.
Figure 8 NAT not associated with a VRRP group
Traffic forwarding process
The master in a VRRP group relies with the virtual MAC address of the VRRP group to an ARP request if the following requirements are met:
· NAT features are associated with the VRRP group.
· The target IP address belongs to the subnet that contains the IP address of a NAT interface.
As shown in Figure 9, dynamic NAT is configured on the HA group that is operating in active/standby mode. If NAT is associated with the uplink VRRP group, the devices process the traffic as follows when the host accesses the Internet:
1. When receiving the packets sent by the host, Device A translates the source IP address into a public IP address in the NAT address group and forwards the packets to the router. In this example, the public IP address is in the same subnet as the virtual IP address of uplink VRRP group 1.
2. The router receives the return packets and broadcasts an ARP request for the destination public IP address.
3. Device A and Device B receive the ARP request, and Device A (master) replies with the virtual MAC addresses of the uplink VRRP group.
4. Router A sends the return packets to Device A.
Figure 9 NAT on the HA group
For more information about VRRP group association with dynamic NAT, static NAT, NAT server, and NAT444, see Layer 3—IP Services Configuration Guide.
HA group support for SSL VPN
To back up SSL VPN data, you must use the sslvpn rbm-port command to establish a data backup channel for SSL VPN on the HA group. For more information about the data backup channel and SSL VPN configuration, see Security Configuration Guide.
The HA group supports SSL VPN only when it is operating in active/standby mode.
HA group support for DPI services
When you use DPI services on the transparently deployed HA group operating in dual-active mode, you must enable HA group support for DPI services if asymmetric-path traffic exists. If you do not enable this feature, DPI services might fail to correctly identify and process packets. For more information about DPI services and HA group support for DPI services, see DPI engine configuration in DPI Configuration Guide.
HA group deployment schemes
The HA group supports the following deployment schemes:
· Routed in-path deployment in active/standby mode.
· Routed in-path deployment in dual-active mode.
· Transparent in-path deployment in active/standby mode.
· Transparent in-path deployment in dual-active mode.
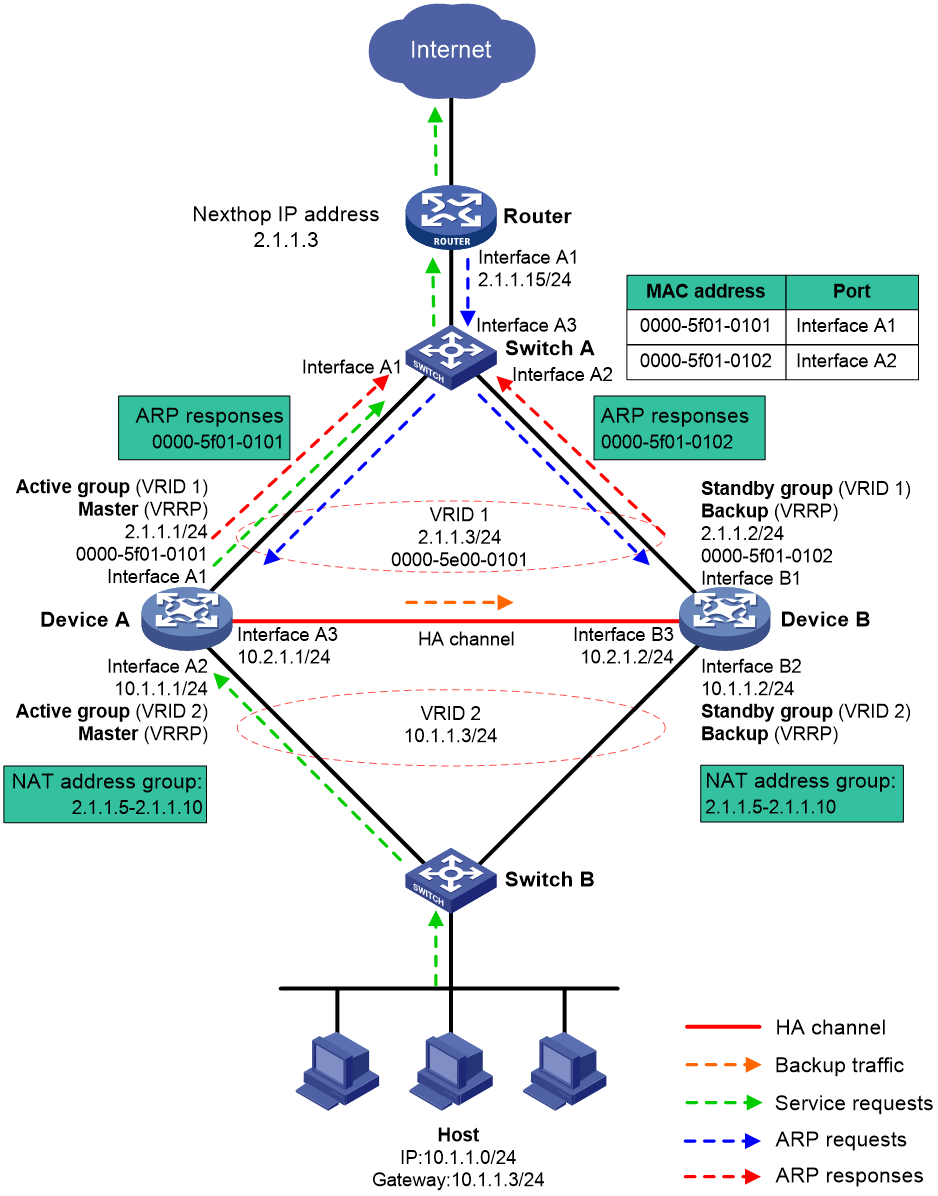
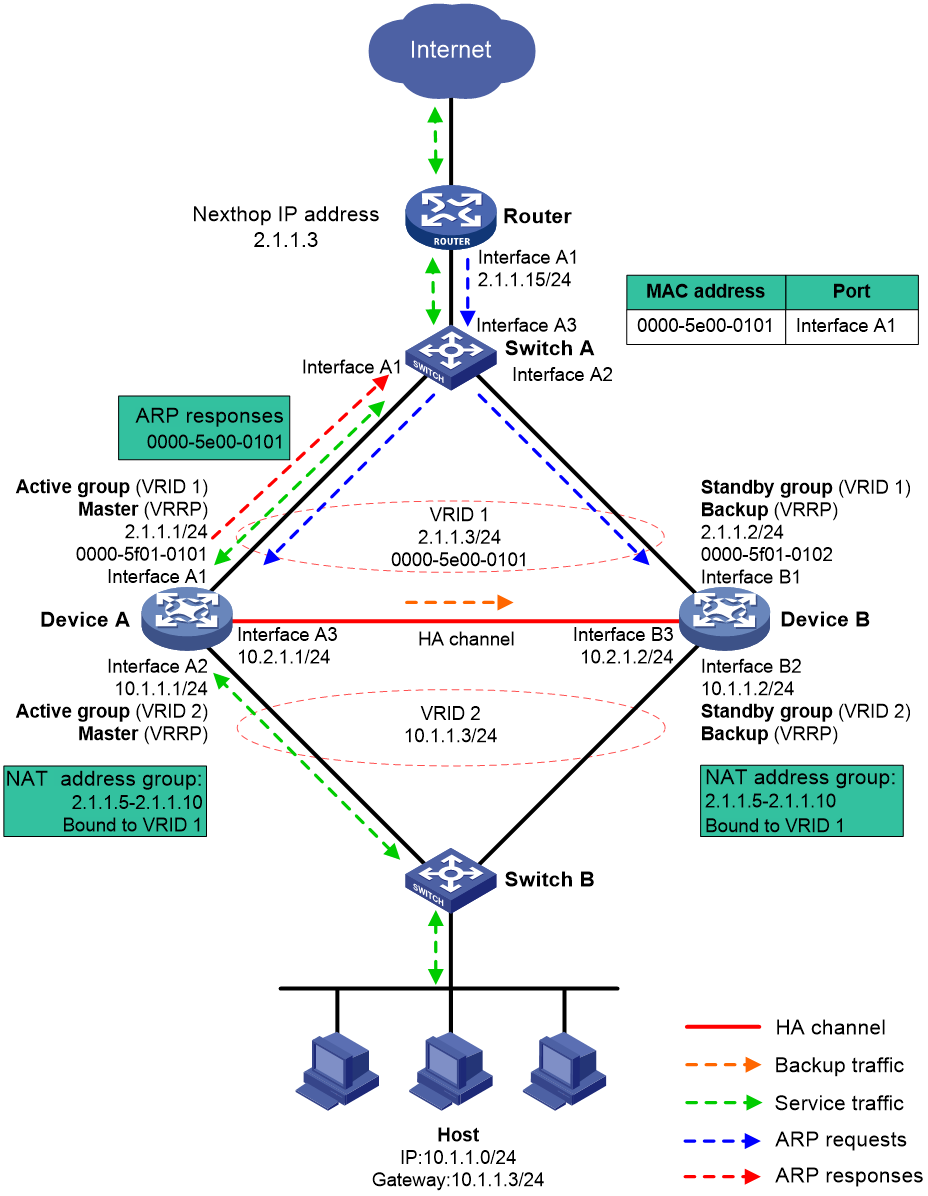
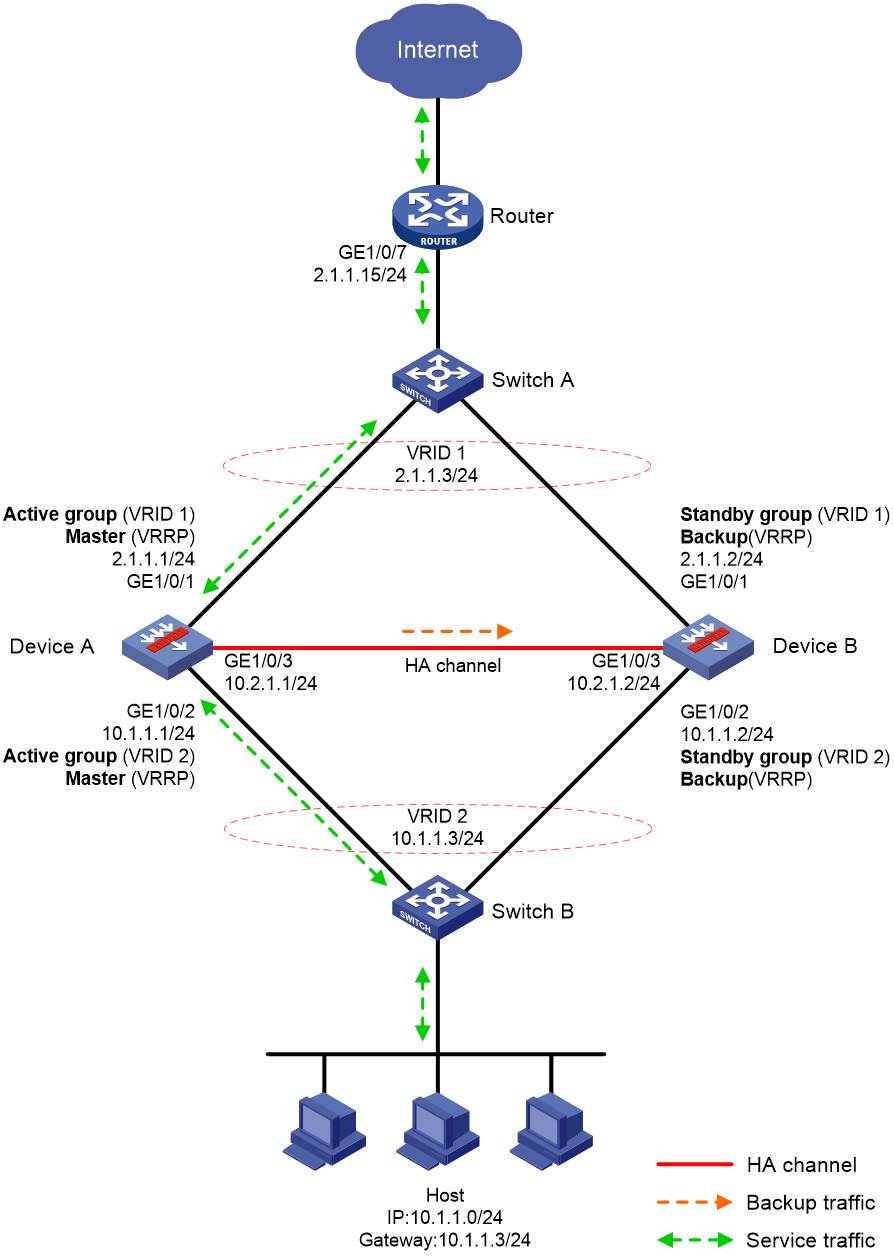
Routed in-path deployment in active/standby mode
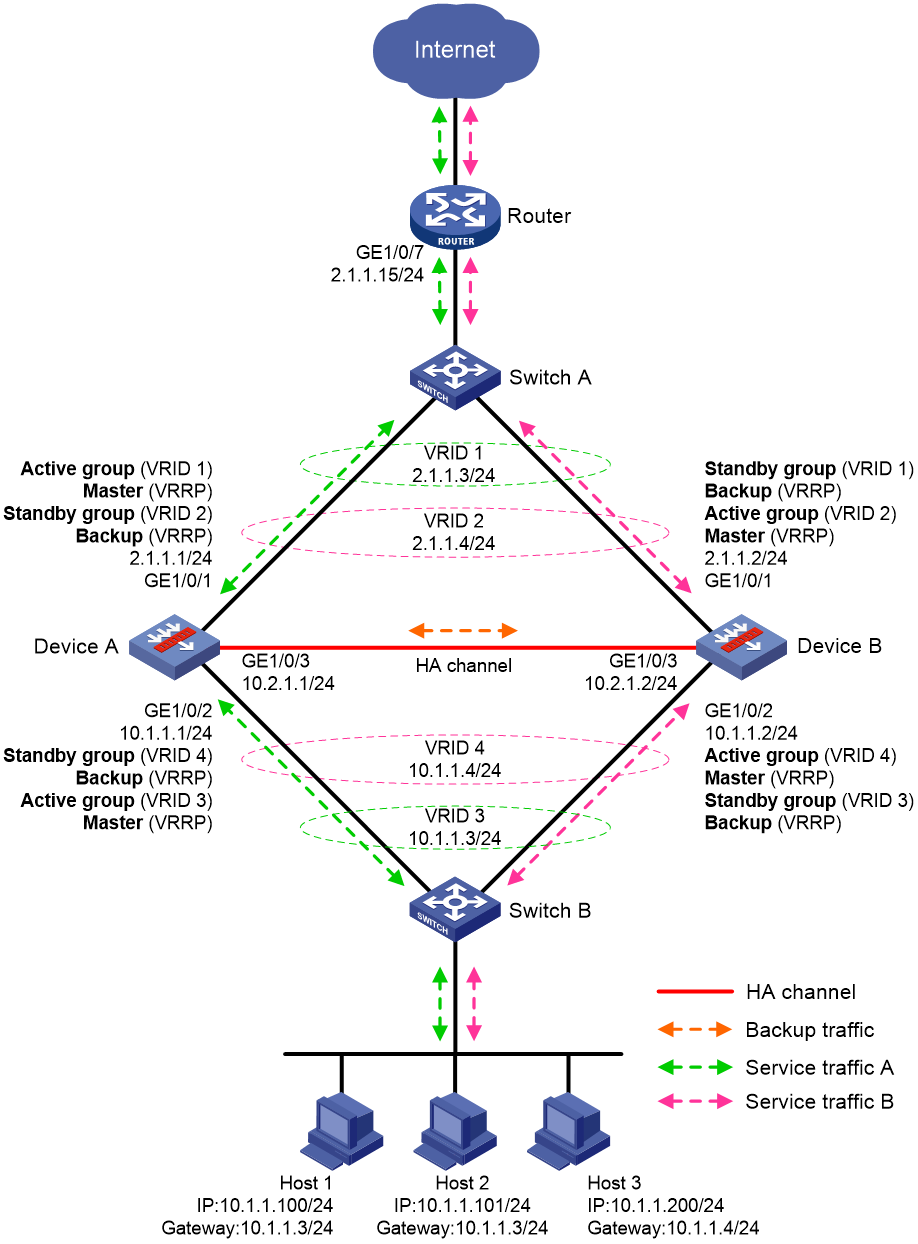
Figure 10 shows a typical model of routed in-path deployment in active/standby mode. The HA group is directly connected to the upstream and downstream Layer 2 switches by Layer 3 interfaces. To use this scheme in collaboration with VRRP, perform the following tasks:
· Establish HA channels between Device A and Device B.
· On Device A and Device B, create uplink VRRP group 1 and downlink VRRP group 2 and associate them with the HA group.
· On Device A, associate VRRP group 1 and VRRP group 2 with the VRRP active group. On Device B, associate VRRP group 1 and VRRP group 2 with the VRRP standby group.
· On Device A and Device B, specify the IP address of Interface A1 on the router (2.1.1.15) as the next hop of the route to the Internet.
· On the router, specify the virtual IP address of VRRP group 1 (2.1.1.3) as the next hop of the route to the host's subnet.
· On the host, specify the virtual IP address of VRRP group 2 (10.1.1.3) as the default gateway.
· On Switch A, assign the interfaces attached to the router, Device A, and Device B to the same VLAN.
· On Switch B, assign the interfaces attached to the host, Device A, and Device B to the same VLAN.
Figure 10 Routed in-path deployment in active/standby mode
The following shows how traffic is forwarded when the host accesses the Internet in Figure 10:
1. The host identifies that the destination IP address is on a different subnet and sends an ARP request to obtain the MAC address of the default gateway. In this example, the host does not have the ARP entry for the default gateway.
2. Switch B broadcasts the ARP request and learns the MAC address of the host.
3. Device A and Device B receives the ARP request, and Device A (master) replies with the virtual MAC address of VRRP group 2.
4. Switch B learns the MAC address entry for the virtual MAC address of VRRP group 2 and forwards the ARP reply to the host.
5. The host learns the virtual MAC address and sends the packets destined for the Internet to the default gateway.
6. Switch B forwards the packets to Device A (master). The traffic of the host will be processed and forwarded by Device A as long as it is the master.
7. Device A does not have the ARP entry for the next hop of the route to the Internet and sends an ARP request to obtain the MAC address of the next hop. In the ARP request, the source MAC address is the virtual MAC address of VRRP group 1.
8. Switch A and the router then perform typical forwarding and ARP and MAC address learning.
The forwarding process for the traffic sent from the Internet to the host is similar to the above process.
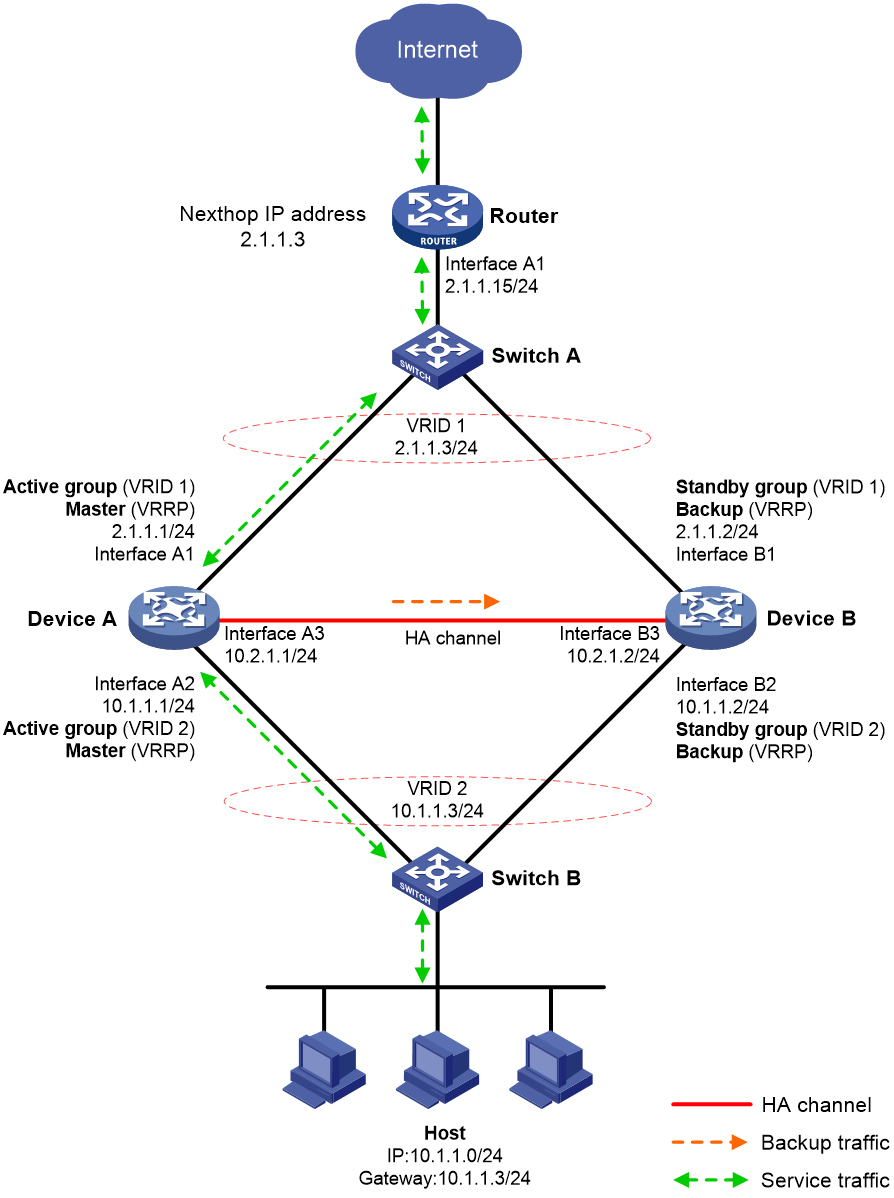
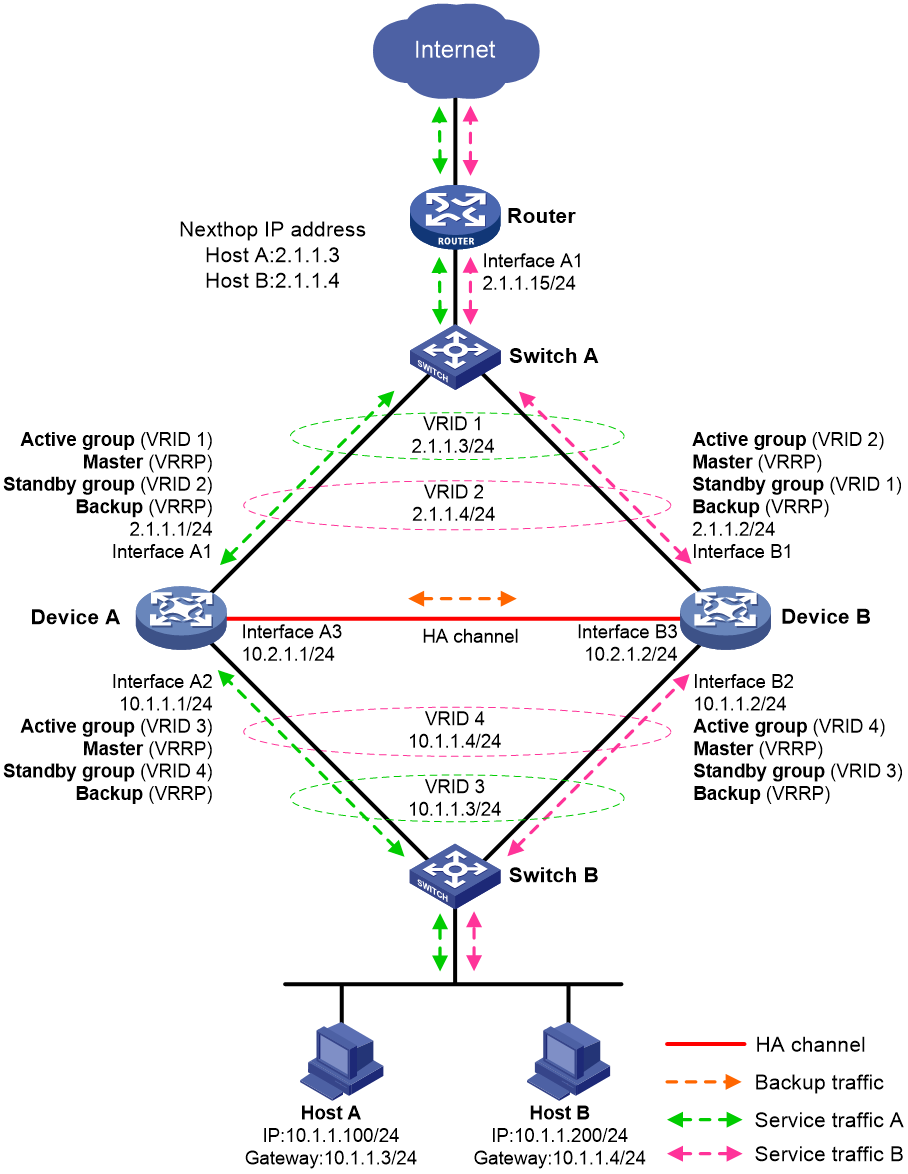
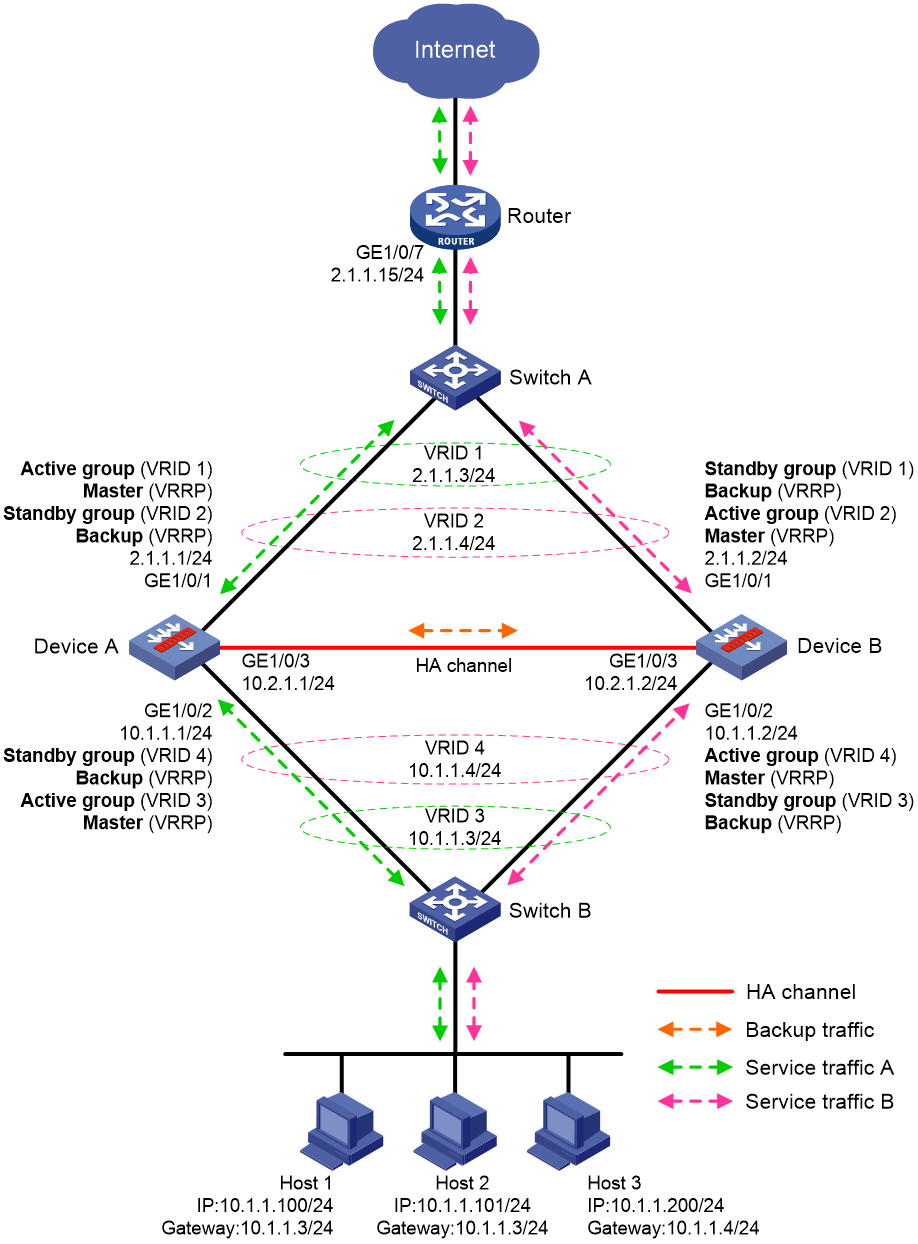
Routed in-path deployment in dual-active mode
Figure 11 shows a typical model of routed in-path deployment in dual-active mode. The HA group is directly connected to the upstream and downstream Layer 2 switches by Layer 3 interfaces. To use this scheme in collaboration with VRRP, perform the following tasks:
· Establish HA channels between Device A and Device B.
· On Device A and Device B, create two uplink VRRP groups and two downlink VRRP groups.
· Create VRRP group 3 and VRRP group 4 on the downlink interfaces of Device A and Device B.
· On Device A, associate VRRP group 1 and VRRP group 3 with the VRRP active group, and associate VRRP group 2 and VRRP group 4 with the VRRP standby group.
· On Device B, associate VRRP group 1 and VRRP group 3 with the VRRP standby group, and associate VRRP group 2 and VRRP group 4 with the VRRP active group.
· On Device A and Device B, specify the IP address of Interface A1 on the router (2.1.1.15) as the next hop of the route to the Internet.
· On the router, configure routes as follows:
¡ Specify the virtual IP address of VRRP group 1 (2.1.1.3) as the next hop of the route to Host A's subnet.
¡ Specify the virtual IP address of VRRP group 2 (2.1.1.4) as the next hop of the route to Host B's subnet.
· On Host A, specify the virtual IP address of VRRP group 3 (10.1.1.3) as the default gateway.
· On Host B, specify the virtual IP address of VRRP group 4 (10.1.1.4) as the default gateway.
· On Switch A, assign the interfaces attached to the router, Device A, and Device B to the same VLAN.
· On Switch B, assign the interfaces attached to the hosts, Device A, and Device B to the same VLAN.
Figure 11 Routed in-path deployment in dual-active mode
As shown in Figure 11, the traffic of Host A and Host B is distributed to Device A and Device B, respectively. The traffic forwarding process is similar to that in active/standby mode.
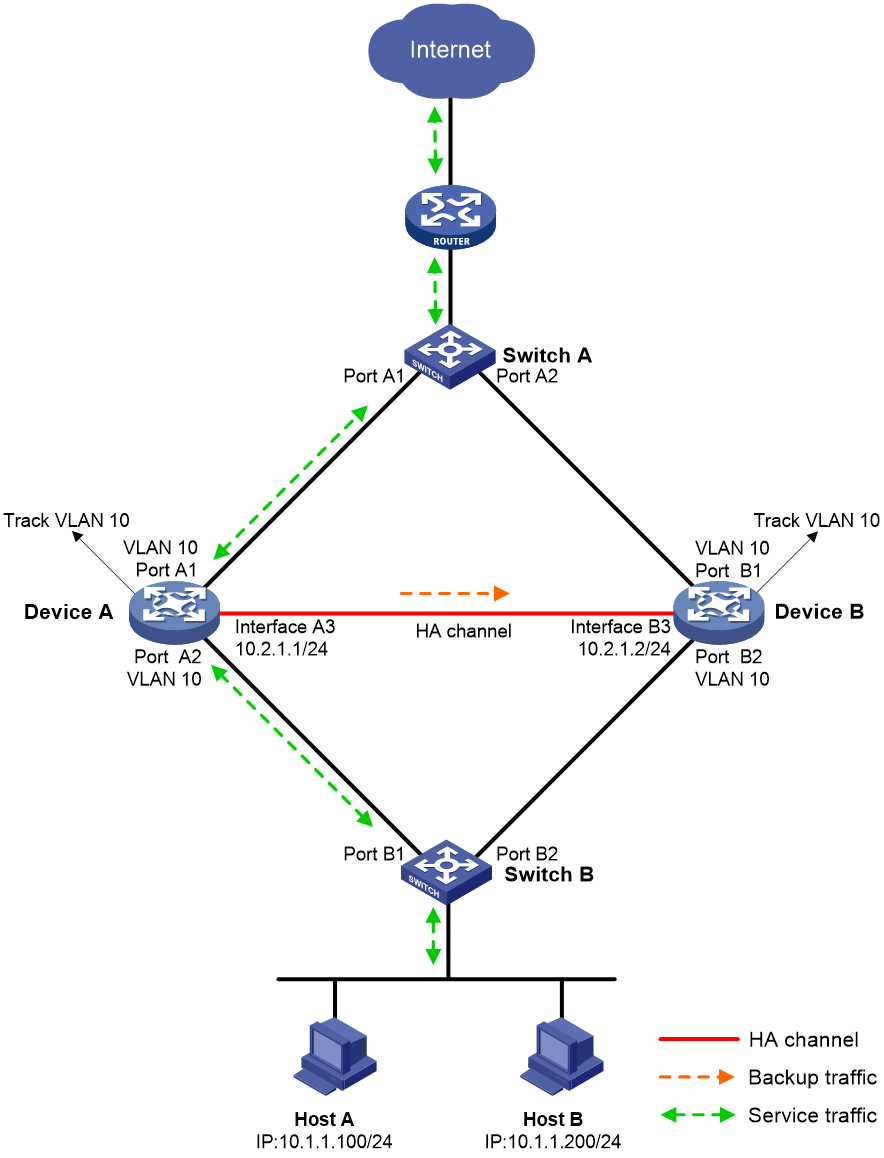
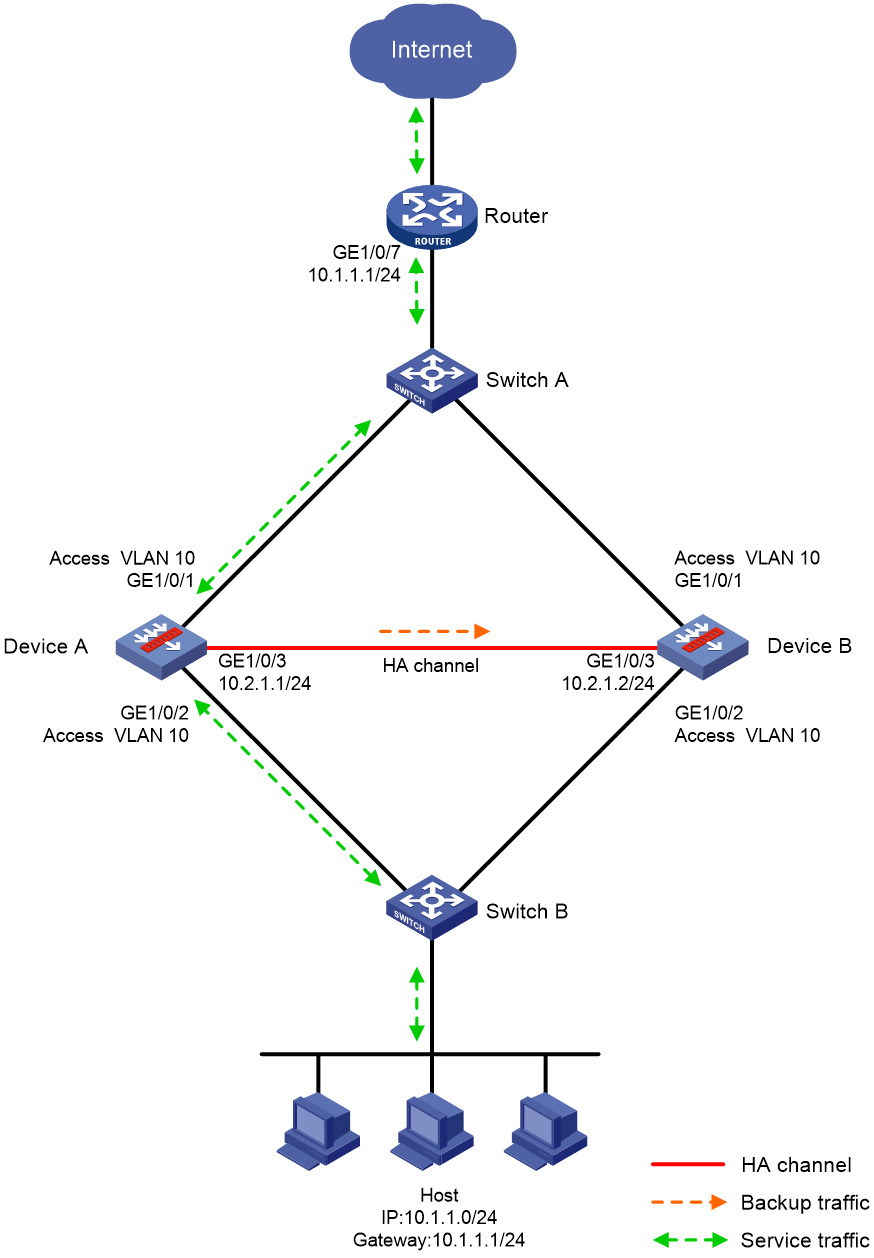
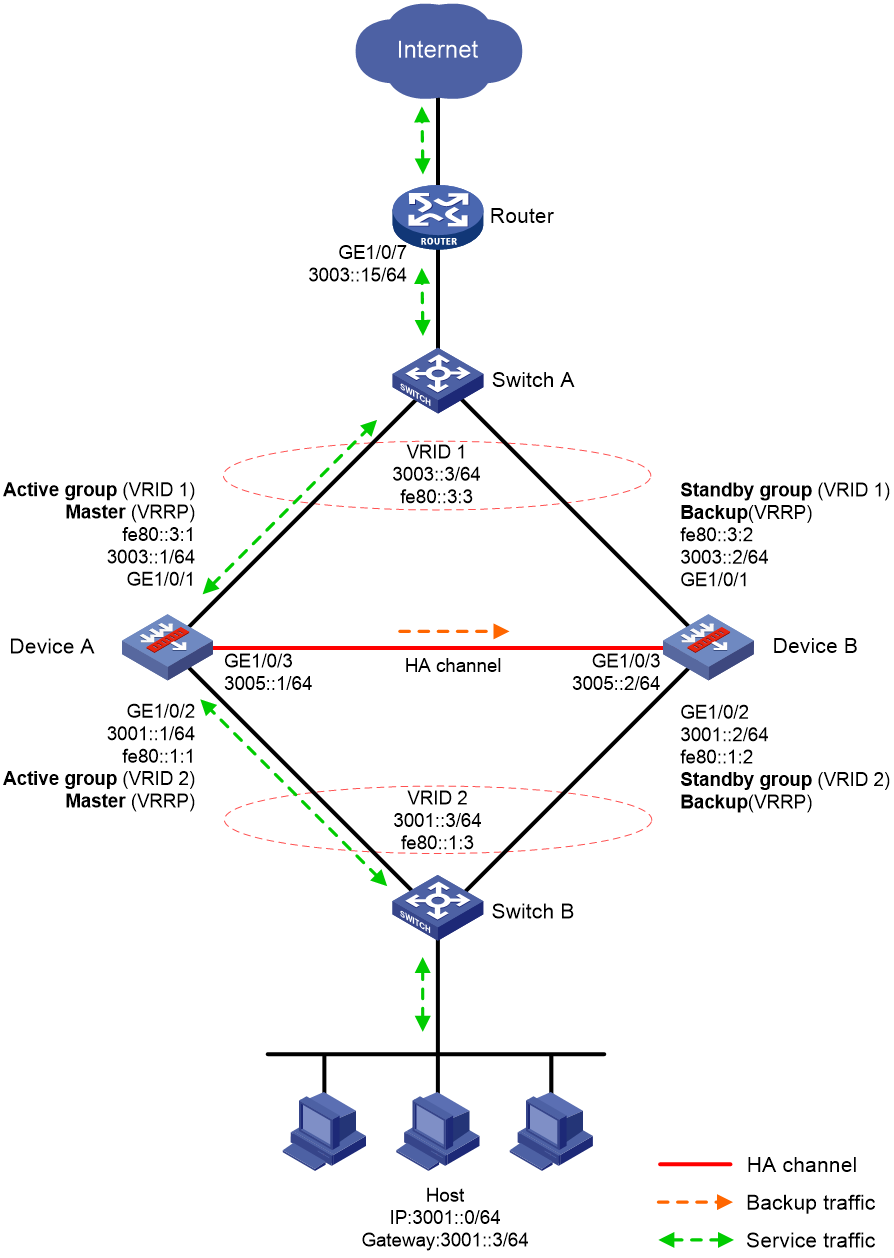
Transparent in-path deployment in active/standby mode
Figure 12 shows a typical model of transparent in-path deployment in active/standby mode. The Layer 2 HA group is directly connected to the upstream and downstream Layer 2 switches by Layer 2 interfaces. To use this scheme, perform the following tasks:
· Establish HA channels between Device A and Device B.
· On Device A and Device B, assign uplink and downlink interfaces to the same VLAN.
· Configure the HA group to monitor one of the following objects:
¡ The VLAN where Device A and Device B reside.
You do not need to enable spanning tree on the upstream and downstream switches.
¡ Uplink and downlink interfaces of Device A and Device B.
You must enable spanning tree on the upstream and downstream switches.
· On Switch A, assign the interfaces attached to the upstream router, Device A, and Device B to the same VLAN.
· On Switch B, assign the interfaces attached to the hosts, Device A, and Device B to the same VLAN.
Figure 12 Transparent in-path deployment in active/standby mode
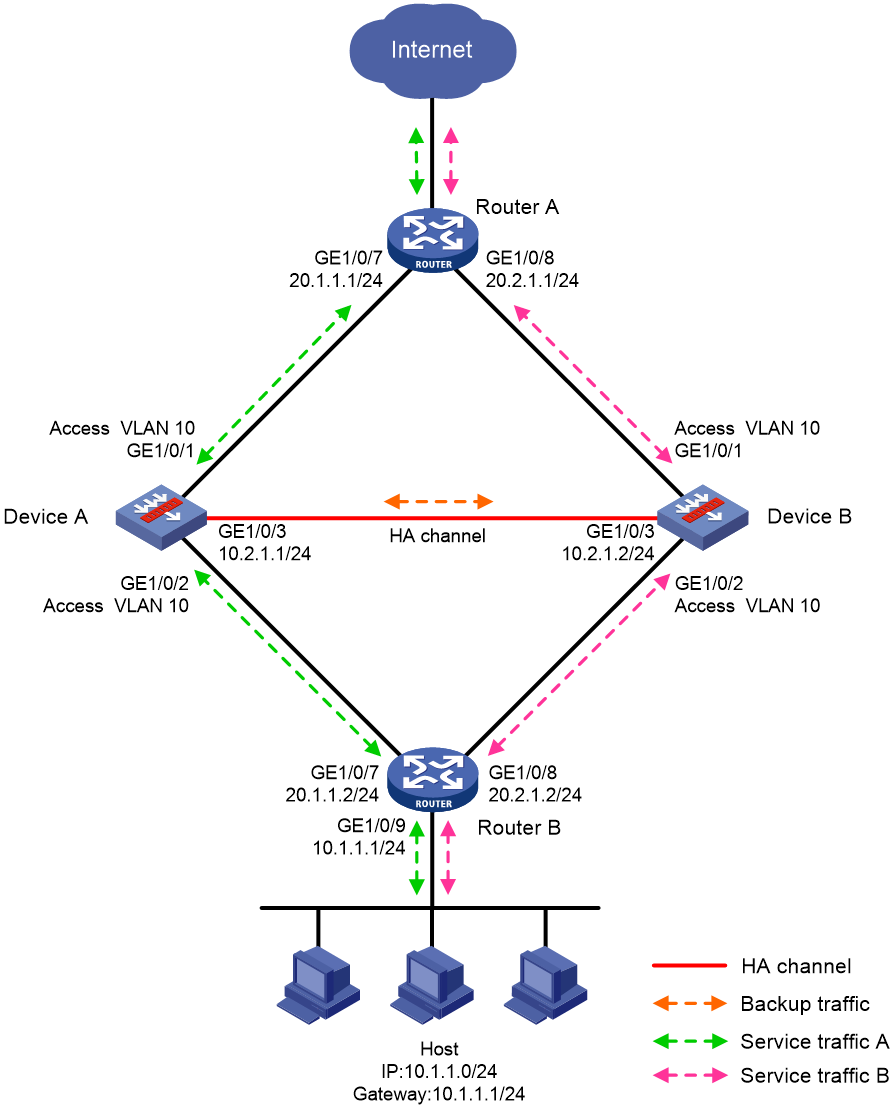
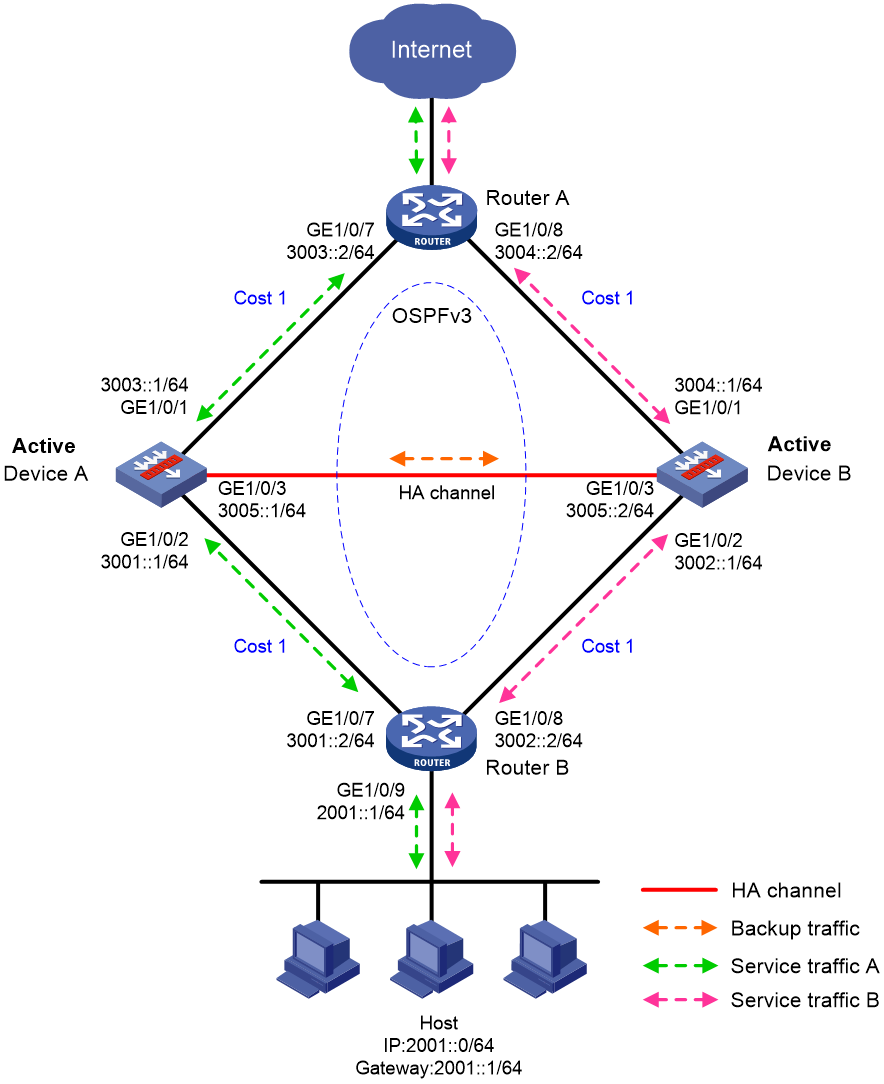
Transparent in-path deployment in dual-active mode
Figure 13 shows a typical model of transparent in-path deployment in dual-active mode. The Layer 2 HA group is directly connected to the upstream and downstream routers by Layer 2 interfaces. To use this scheme, perform the following tasks:
· Establish HA channels between Device A and Device B.
· On Device A and Device B, assign uplink and downlink interfaces to the same VLAN.
· On Device A and Device B, configure the HA group to monitor the status of the uplink and downlink interfaces.
· On Router A and Router B, configure the same cost for OSPF routes and enable per-flow load sharing among ECMP routes.
Figure 13 Transparent in-path deployment in dual-active mode
Display and maintenance commands for the HA group
Execute display commands in any view.
|
Task |
Command |
|
Display HA group status information. |
display remote-backup-group status |
|
Display the configuration consistency check result for the HA group. |
display remote-backup-group sync-check |
HA group configuration examples (IPv4)
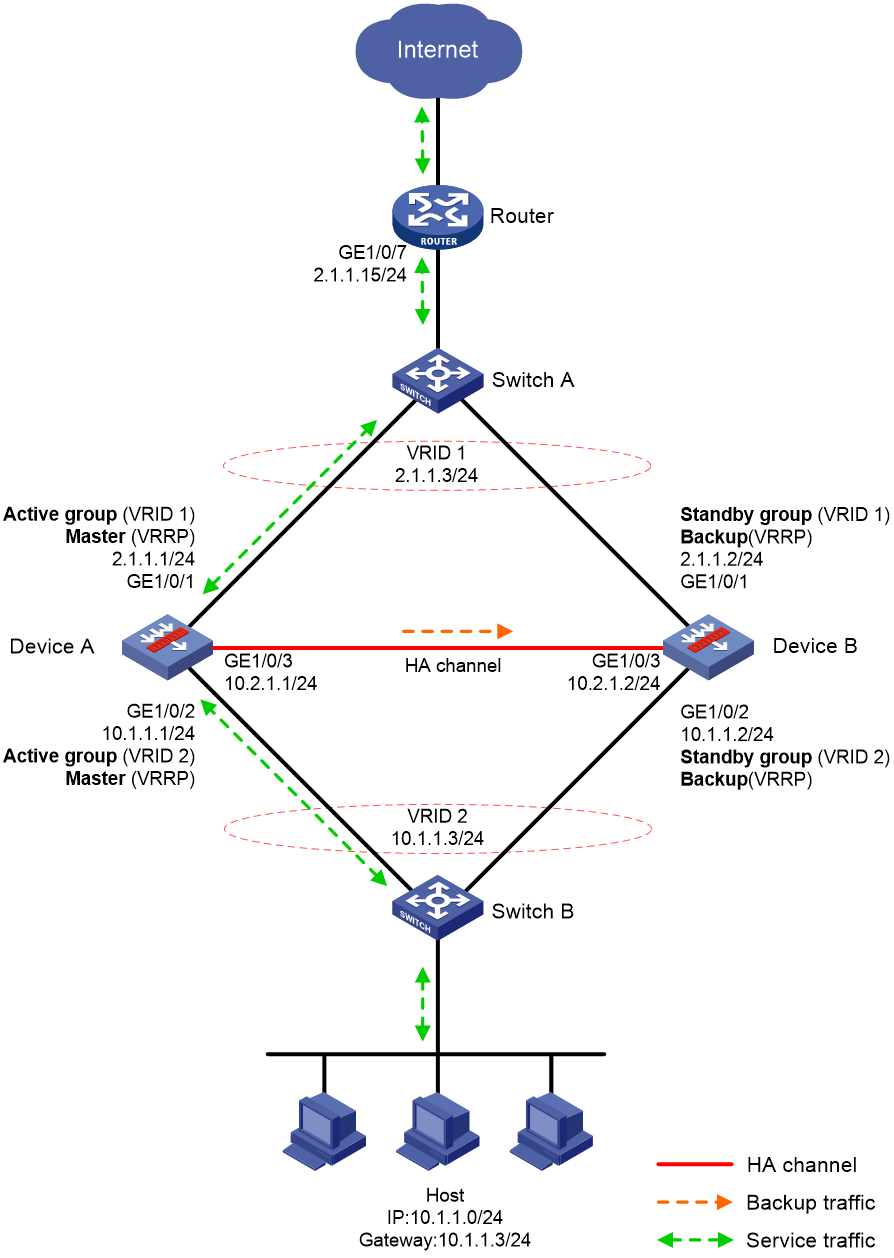
Example: Configuring the HA group in active/standby mode in collaboration with VRRP
Network configuration
As shown in Figure 14, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Switch A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
3. Configure Switch B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
4. Configure the router:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 2.1.1.15/24 to GigabitEthernet 1/0/7.
# Configure routes as follows:
¡ Specify 2.1.1.3 (virtual IP address of VRRP group 1) as the next hop of the routes to the internal network.
¡ Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
5. Configure Device A:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 2.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 2.1.1.15.
[DeviceA] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
c. Configure HA group settings.
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] undo backup-mode
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 active
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] vrrp vrid 2 virtual-ip 10.1.1.3 active
[DeviceA-GigabitEthernet1/0/2] quit
d. Configure security services on Device A. (Details not shown.)
6. Configure Device B:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.1.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 2.1.1.15.
[DeviceB] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
c. Configure HA group settings.
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] undo backup-mode
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
[DeviceB-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 standby
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] vrrp vrid 2 virtual-ip 10.1.1.3 standby
[DeviceB-GigabitEthernet1/0/2] quit
7. On the host, specify 10.1.1.3 (virtual IP address of VRRP group 2) as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that Device A is the master in all VRRP groups.
[DeviceA] display vrrp
IPv4 Virtual Router Information:
Running mode : Standard
RBM control channel is established
VRRP active group status : Master
VRRP standby group status: Master
Total number of virtual routers : 2
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Master 100 100 None 2.1.1.3
GE1/0/2 2 Master 100 100 None 10.1.1.3
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device A generates log messages when the host communicates with the Internet. (Details not shown.)
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that Device A is the backup in all VRRP groups.
[DeviceB] display vrrp
IPv4 Virtual Router Information:
Running mode : Standard
RBM control channel is established
VRRP active group status : Backup
VRRP standby group status: Backup
Total number of virtual routers : 2
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Backup 100 100 None 2.1.1.3
GE1/0/2 2 Backup 100 100 None 10.1.1.3
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device B does not generate log messages when the host communicates with the Internet. (Details not shown.)
Example: Configuring the HA group in dual-active mode in collaboration with VRRP
Network configuration
As shown in Figure 15, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Switch A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
3. Configure Switch B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
4. Configure the router:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 2.1.1.15/24 to GigabitEthernet 1/0/7.
# Configure routes as follows:
¡ Specify 2.1.1.3 (virtual IP address of VRRP group 1) as the next hop of the routes to some subnets of the internal network. Specify 2.1.1.4 (virtual IP address of VRRP group 2) as the next hop of the routes to the other subnets of the internal network.
¡ Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
5. Configure Device A:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 2.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 2.1.1.15.
[DeviceA] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
c. Configure HA group settings.
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] backup-mode dual-active
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] delay-time 1
[DeviceA-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 active
[DeviceA-GigabitEthernet1/0/1] vrrp vrid 2 virtual-ip 2.1.1.4 standby
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] vrrp vrid 3 virtual-ip 10.1.1.3 active
[DeviceA-GigabitEthernet1/0/2] vrrp vrid 4 virtual-ip 10.1.1.4 standby
[DeviceA-GigabitEthernet1/0/2] quit
d. Configure security services on Device A. (Details not shown.)
6. Configure Device B:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.1.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 2.1.1.15.
[DeviceB] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
c. Configure HA group settings.
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] backup-mode dual-active
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
[DeviceB-remote-backup-group] delay-time 1
[DeviceB-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 standby
[DeviceB-GigabitEthernet1/0/1] vrrp vrid 2 virtual-ip 2.1.1.4 active
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] vrrp vrid 3 virtual-ip 10.1.1.3 standby
[DeviceB-GigabitEthernet1/0/2] vrrp vrid 4 virtual-ip 10.1.1.4 active
[DeviceB-GigabitEthernet1/0/2] quit
7. On some hosts, specify 10.1.1.3 (virtual IP address of VRRP group 3) as the default gateway. On the other hosts, specify 10.1.1.4 (virtual IP address of VRRP group 4) as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that Device A is the master in VRRP groups 1 and 3 and the backup in VRRP groups 2 and 4.
[DeviceA] display vrrp
IPv4 Virtual Router Information:
Running mode : Standard
RBM control channel is established
VRRP active group status : Master
VRRP standby group status: Backup
Total number of virtual routers : 4
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Master 100 100 None 2.1.1.3
GE1/0/1 2 Backup 100 100 None 2.1.1.4
GE1/0/2 3 Master 100 100 None 10.1.1.3
GE1/0/2 4 Backup 100 100 None 10.1.1.4
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device A generates log messages when a host for which Device A forwards traffic communicates with the Internet. Verity that Device A does not generate log messages when a host for which Device B forwards traffic communicates with the Internet. (Details not shown.)
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that Device B is the master in VRRP groups 2 and 4 and the backup in VRRP groups 1 and 3.
[DeviceB] display vrrp
IPv4 Virtual Router Information:
Running mode : Standard
RBM control channel is established
VRRP active group status : Master
VRRP standby group status: Backup
Total number of virtual routers : 4
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Backup 100 100 None 2.1.1.3
GE1/0/1 2 Master 100 100 None 2.1.1.4
GE1/0/2 3 Backup 100 100 None 10.1.1.3
GE1/0/2 4 Master 100 100 None 10.1.1.4
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device B generates log messages when a host for which Device B forwards traffic communicates with the Internet. Verity that Device B does not generate log messages when a host for which Device A forwards traffic communicates with the Internet. (Details not shown.)
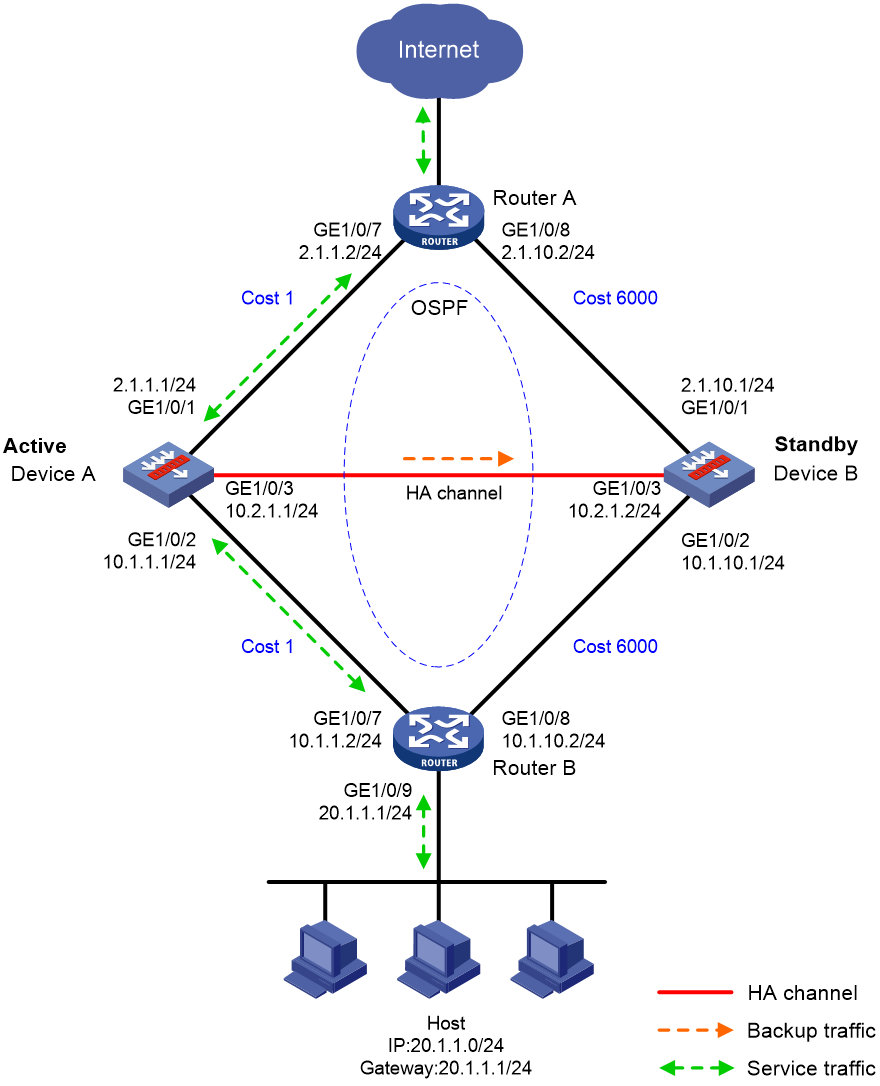
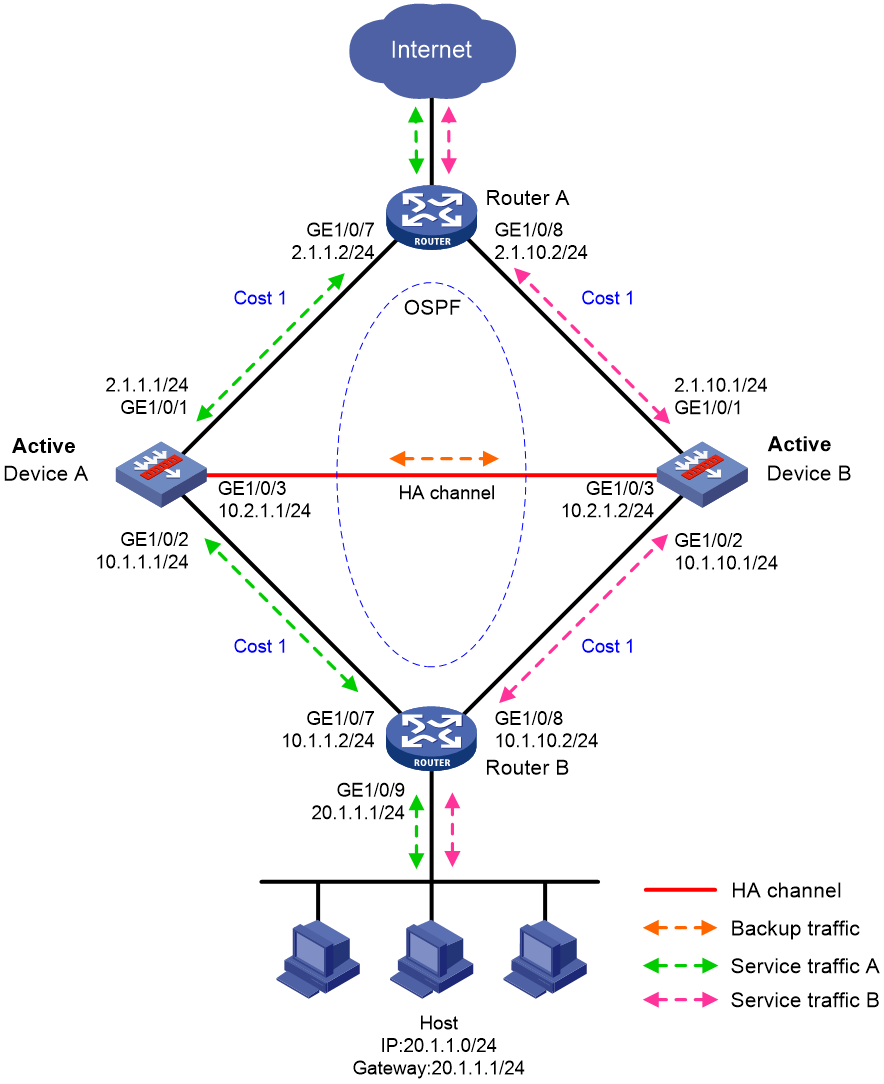
Example: Configuring the HA group in active/standby mode in collaboration with a routing protocol
Network configuration
As shown in Figure 16, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPF.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Router A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 2.1.1.2/24 to GigabitEthernet 1/0/7.
# Assign 2.1.10.2/24 to GigabitEthernet 1/0/8.
# Configure OSPF for Device A, Device B, and the routers to have Layer 3 reachability.
3. Configure Router B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 10.1.1.2/24 to GigabitEthernet 1/0/7.
# Assign 10.1.10.2/24 to GigabitEthernet 1/0/8.
# Configure OSPF for Device A, Device B, and the routers to have Layer 3 reachability.
4. Configure Device A:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 2.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure OSPF. Use the default OSPF link cost configuration.
[DeviceA] router id 2.1.1.1
[DeviceA] ospf
[DeviceA-ospf-1] area 0
[DeviceA-ospf-1-area-0.0.0.0] network 2.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] quit
[DeviceA-ospf-1] quit
c. Configure HA group settings.
# Associate track entries with interfaces.
[DeviceA] track 1 interface gigabitethernet 1/0/1
[DeviceA-track-1] quit
[DeviceA] track 2 interface gigabitethernet 1/0/2
[DeviceA-track-2] quit
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] undo backup-mode
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
# Configure the HA group to change the link costs advertised in OSPF routes to 6000.
[DeviceA-remote-backup-group] adjust-cost ospf enable absolute 6000
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceA-remote-backup-group] track 1
[DeviceA-remote-backup-group] track 2
[DeviceA-remote-backup-group] quit
d. Configure security services on Device A. (Details not shown.)
5. Configure Device B:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.1.10.1 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure OSPF. Use the default OSPF link cost configuration.
[DeviceB] router id 2.1.10.1
[DeviceB] ospf
[DeviceB-ospf-1] area 0
[DeviceB-ospf-1-area-0.0.0.0] network 2.1.10.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] network 10.1.10.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] quit
[DeviceB-ospf-1] quit
# Associate track entries with interfaces.
[DeviceB] track 1 interface gigabitethernet 1/0/1
[DeviceB-track-1] quit
[DeviceB] track 2 interface gigabitethernet 1/0/2
[DeviceB-track-2] quit
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] undo backup-mode
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
# Configure the HA group to change the link costs advertised in OSPF routes to 6000.
[DeviceB-remote-backup-group] adjust-cost ospf enable absolute 6000
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceB-remote-backup-group] track 1
[DeviceB-remote-backup-group] track 2
[DeviceB-remote-backup-group] quit
6. On the host, specify 20.1.1.1 as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that the OSPF routes advertised by Device A include a smaller link cost than that advertised by Device B.
[DeviceA] display ospf interface
OSPF Process 1 with Router ID 2.1.1.1
Interfaces
Area: 0.0.0.0
IP Address Type State Cost Pri DR BDR
2.1.1.1 Broadcast BDR 1 1 2.1.1.2 2.1.1.1
10.1.1.1 Broadcast DR 1 1 10.1.1.1 10.1.1.2
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that the OSPF routes advertised by Device B include a larger link cost than that advertised by Device A.
[DeviceB] display ospf interface
OSPF Process 1 with Router ID 2.1.10.1
Interfaces
Area: 0.0.0.0
IP Address Type State Cost Pri DR BDR
2.1.10.1 Broadcast BDR 6000 1 2.1.10.2 2.1.10.1
10.1.10.1 Broadcast BDR 6000 1 10.1.10.2 10.1.10.1
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol
Network configuration
As shown in Figure 17, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPF.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Router A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 2.1.1.2/24 to GigabitEthernet 1/0/7.
# Assign 2.1.10.2/24 to GigabitEthernet 1/0/8.
# Configure OSPF for Device A, Device B, and the routers to have Layer 3 reachability.
# Configure per-flow load sharing for IP forwarding.
3. Configure Router B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 10.1.1.2/24 to GigabitEthernet 1/0/7.
# Assign 10.1.10.2/24 to GigabitEthernet 1/0/8.
# Configure OSPF for Device A, Device B, and the routers to have Layer 3 reachability.
# Configure per-flow load sharing for IP forwarding.
4. Configure Device A:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 2.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure OSPF. Use the default OSPF link cost configuration.
[DeviceA] router id 2.1.1.1
[DeviceA] ospf
[DeviceA-ospf-1] area 0
[DeviceA-ospf-1-area-0.0.0.0] network 2.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] quit
[DeviceA-ospf-1] quit
c. Configure HA group settings.
# Associate track entries with interfaces.
[DeviceA] track 1 interface gigabitethernet 1/0/1
[DeviceA-track-1] quit
[DeviceA] track 2 interface gigabitethernet 1/0/2
[DeviceA-track-2] quit
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] backup-mode dual-active
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] delay-time 1
# Configure the HA group to change the link costs advertised in OSPF routes to 1.
[DeviceA-remote-backup-group] adjust-cost ospf enable absolute 1
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceA-remote-backup-group] track 1
[DeviceA-remote-backup-group] track 2
[DeviceA-remote-backup-group] quit
d. Configure security services on Device A. (Details not shown.)
5. Configure Device B:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.1.10.1 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure OSPF. Use the default OSPF link cost configuration.
[DeviceB] router id 2.1.10.1
[DeviceB] ospf
[DeviceB-ospf-1] area 0
[DeviceB-ospf-1-area-0.0.0.0] network 2.1.10.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] network 10.1.10.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] quit
[DeviceB-ospf-1] quit
c. Configure HA group settings.
# Associate track entries with interfaces.
[DeviceB] track 1 interface gigabitethernet 1/0/1
[DeviceB-track-1] quit
[DeviceB] track 2 interface gigabitethernet 1/0/2
[DeviceB-track-2] quit
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] backup-mode dual-active
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
[DeviceB-remote-backup-group] delay-time 1
# Configure the HA group to change the link costs advertised in OSPF routes to 1.
[DeviceB-remote-backup-group] adjust-cost ospf enable absolute 1
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceB-remote-backup-group] track 1
[DeviceB-remote-backup-group] track 2
[DeviceB-remote-backup-group] quit
6. On the hosts, specify 20.1.1.1 as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that the OSPF routes advertised by Device A and Device B include the same link cost.
[DeviceA] display ospf interface
OSPF Process 1 with Router ID 2.1.1.1
Interfaces
Area: 0.0.0.0
IP Address Type State Cost Pri DR BDR
2.1.1.1 Broadcast BDR 1 1 2.1.1.2 2.1.1.1
10.1.1.1 Broadcast DR 1 1 10.1.1.1 10.1.1.2
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that the OSPF routes advertised by Device A and Device B include the same link cost.
[DeviceB] display ospf interface
OSPF Process 1 with Router ID 2.1.10.1
Interfaces
Area: 0.0.0.0
IP Address Type State Cost Pri DR BDR
2.1.10.1 Broadcast BDR 1 1 2.1.10.2 2.1.10.1
10.1.10.1 Broadcast BDR 1 1 10.1.10.2 10.1.10.1
Example: Configuring a transparent in-path HA group in active/standby mode
Network configuration
As shown in Figure 18, set up a transparent in-path HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to operate in active/standby mode.
· Connect Switch A and Switch B to Layer 2 interfaces of the HA group.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Switch A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
3. Configure Switch B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
4. Configure Device A:
a. Configure VLANs.
# Configure the uplink and downlink interfaces to operate at Layer 2.
<DeviceA> system-view
[DeviceA] interface range gigabitethernet 1/0/1 to gigabitethernet 1/0/2
[DeviceA-if-range] port link-mode bridge
[DeviceA-if-range] quit
# Assign the uplink and downlink interfaces to VLAN 10.
[DeviceA] vlan 10
[DeviceA-vlan10] port gigabitethernet 1/0/1
[DeviceA-vlan10] port gigabitethernet 1/0/2
[DeviceA-vlan10] quit
b. Assign an IP address to GigabitEthernet 1/0/3.
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] ip address 10.2.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/3] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
c. Configure HA group settings.
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] undo backup-mode
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
# Configure the HA group to monitor the status of VLAN 10.
[DeviceA-remote-backup-group] track vlan 10
[DeviceA-remote-backup-group] quit
d. Configure security services on Device A. (Details not shown.)
5. Configure Device B:
a. Configure VLANs.
# Configure the uplink and downlink interfaces to operate at Layer 2.
<DeviceB> system-view
[DeviceB] interface range gigabitethernet 1/0/1 to gigabitethernet 1/0/2
[DeviceB-if-range] port link-mode bridge
[DeviceB-if-range] quit
# Assign the uplink and downlink interfaces to VLAN 10.
[DeviceB] vlan 10
[DeviceB-vlan10] port gigabitethernet 1/0/1
[DeviceB-vlan10] port gigabitethernet 1/0/2
[DeviceB-vlan10] quit
b. Assign an IP address to GigabitEthernet 1/0/3.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ip address 10.2.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/3] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
c. Configure HA group settings.
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] undo backup-mode
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
# Configure the HA group to monitor the state of VLAN 10.
[DeviceB-remote-backup-group] track vlan 10
[DeviceB-remote-backup-group] quit
6. On the host, specify 10.1.1.1 as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify that the HA channels have been set up and the tracked VLAN is active on Device A.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
2. Verify that the HA channels have been set up and the tracked VLAN is inactive on Device B.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
Example: Configuring a transparent in-path HA group in dual-active mode
Network configuration
As shown in Figure 19, set up a transparent in-path HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to operate in dual-active mode.
· Connect Router A and Router B to Layer 2 interfaces of the HA group.
· Configure Device A and Device B to load share traffic.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure OSPF on Router A for the host to access the Internet and for Device A and Device B to load share the traffic sent to the host.
3. Configure OSPF on Router B for the host to access the Internet and for Device A and Device B to load share the traffic sent to the Internet.
4. Configure Device A:
a. Configure VLANs.
# Configure the uplink and downlink interfaces to operate at Layer 2.
<DeviceA> system-view
[DeviceA] interface range gigabitethernet 1/0/1 to gigabitethernet 1/0/2
[DeviceA-if-range] port link-mode bridge
[DeviceA-if-range] quit
# Assign the uplink and downlink interfaces to VLAN 10.
[DeviceA] vlan 10
[DeviceA-vlan10] port gigabitethernet 1/0/1
[DeviceA-vlan10] port gigabitethernet 1/0/2
[DeviceA-vlan10] quit
b. Assign an IP address to GigabitEthernet 1/0/3.
[DeviceA] interface GigabitEthernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] ip address 10.2.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/3] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
c. Configure HA group settings.
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] backup-mode dual-active
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] delay-time 1
# Configure the HA group to monitor the status of GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2.
[DeviceA-remote-backup-group] track interface gigabitethernet 1/0/1
[DeviceA-remote-backup-group] track interface gigabitethernet 1/0/2
[DeviceA-remote-backup-group] quit
d. Configure security services on Device A. (Details not shown.)
5. Configure Device B:
a. Configure VLANs.
# Configure the uplink and downlink interfaces to operate at Layer 2.
<DeviceB> system-view
[DeviceB] interface range gigabitethernet 1/0/1 to gigabitethernet 1/0/2
[DeviceB-if-range] port link-mode bridge
[DeviceB-if-range] quit
# Assign the uplink and downlink interfaces to VLAN 10.
[DeviceB] vlan 10
[DeviceB-vlan10] port gigabitethernet 1/0/1
[DeviceB-vlan10] port gigabitethernet 1/0/2
[DeviceB-vlan10] quit
b. Assign an IP address to GigabitEthernet 1/0/3.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ip address 10.2.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/3] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
c. Configure HA group settings.
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] backup-mode dual-active
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] delay-time 1
[DeviceB-remote-backup-group] configuration sync-check interval 12
# Configure the HA group to monitor the status of GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2.
[DeviceB-remote-backup-group] track interface gigabitethernet 1/0/1
[DeviceB-remote-backup-group] track interface gigabitethernet 1/0/2
[DeviceB-remote-backup-group] quit
6. On the host, specify 10.1.1.1 as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify that the HA channels have been set up on Device A.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.1
Remote IP: 10.2.1.2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
2. Verify that the HA channels have been set up on Device B.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IP: 10.2.1.2
Remote IP: 10.2.1.1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
Example: Configuring NAT on the HA group in active/standby mode in collaboration with VRRP
Network configuration
As shown in Figure 20, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
· Configure dynamic NAT to translate the private IP addresses in the internal network into public IP addresses 2.1.1.1 through 2.1.1.10.
Procedure
1. Set up the HA group as described in "Example: Configuring the HA group in active/standby mode in collaboration with VRRP."
2. Configure dynamic NAT on Device A (primary):
# Create NAT address group 1 and add address range 2.1.1.5 to 2.1.1.10. Associate NAT address group 1 with VRRP group 1.
<DeviceA> system-view
[DeviceA] nat address-group 1
[DeviceA-address-group-1] address 2.1.1.5 2.1.1.10
[DeviceA-address-group-1] vrrp vrid 1
[DeviceA-address-group-1] quit
# Configure outbound dynamic NAT to use NAT address group 1 for address translation on GigabitEthernet 1/0/1.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] nat outbound address-group 1
[DeviceA-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify that the host can communicate with the Internet. (Details not shown.)
# Verify that Device A has generated a NAT session entry.
[DeviceA] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.10/52082
Destination IP/port: 202.38.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.10/80
Destination IP/port: 2.1.1.5/1036
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2019-1-29 16:16:59 TTL: 9995s
Initiator->Responder: 551 packets 32547 bytes
Responder->Initiator: 956 packets 1385514 bytes
Total sessions found: 1
Example: Configuring NAT on the HA group in dual-active mode in collaboration with VRRP
Network configuration
As shown in Figure 21, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
· Configure dynamic NAT to translate the private IP addresses in the internal network into public IP addresses 2.1.1.1 through 2.1.1.10.
Procedure
1. Set up the HA group as described in "Example: Configuring the HA group in dual-active mode in collaboration with VRRP".
2. Configure dynamic NAT on Device A (primary):
# Create NAT address group 1 and add address range 2.1.1.5 to 2.1.1.7. Associate NAT address group 1 with VRRP group 1.
<DeviceA> system-view
[DeviceA] nat address-group 1
[DeviceA-address-group-1] address 2.1.1.5 2.1.1.7
[DeviceA-address-group-1] vrrp vrid 1
[DeviceA-address-group-1] quit
# Create NAT address group 2 and add address range 2.1.1.8 to 2.1.1.10. Associate NAT address group 2 with VRRP group 2.
[DeviceA] nat address-group 2
[DeviceA-address-group-2] address 2.1.1.8 2.1.1.10
[DeviceA-address-group-2] vrrp vrid 2
[DeviceA-address-group-2] quit
# Configure ACL 3000 to permit packets from 10.1.1.1/25. Configure ACL 3001 to permit packets from 10.1.1.129/25.
[DeviceA] acl advanced 3000
[DeviceA-ipv4-adv-3000] rule permit ip source 10.1.1.1 0.0.0.127
[DeviceA-ipv4-adv-3000] quit
[DeviceA] acl advanced 3001
[DeviceA-ipv4-adv-3001] rule permit ip source 10.1.1.129 0.0.0.127
[DeviceA-ipv4-adv-3001] quit
# Configure outbound dynamic NAT on GigabitEthernet 1/0/1. The source IP addresses of the packets permitted by ACL 3000 are translated into the addresses in NAT address group 1. The source IP addresses of the packets permitted by ACL 3001 are translated into the addresses in NAT address group 2.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] nat outbound 3000 address-group 1
[DeviceA-GigabitEthernet1/0/1] nat outbound 3001 address-group 2
[DeviceA-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify that Host 1 can communicate with the Internet. (Details not shown.)
# Verify that Device A has generated a NAT session entry.
[DeviceA] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.100/52082
Destination IP/port: 202.38.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.10/80
Destination IP/port: 2.1.1.5/1036
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2019-1-29 16:16:59 TTL: 9995s
Initiator->Responder: 551 packets 32547 bytes
Responder->Initiator: 956 packets 1385514 bytes
Total sessions found: 1
# Verify that Host 3 can communicate with the Internet. (Details not shown.)
# Verify that Device B has generated a NAT session entry.
[DeviceB] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.200/52082
Destination IP/port: 202.38.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface:
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.10/80
Destination IP/port: 2.1.1.8/1036
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface:
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2019-1-29 16:17:59 TTL: 9995s
Initiator->Responder: 551 packets 32547 bytes
Responder->Initiator: 956 packets 1385514 bytes
Total sessions found: 1
HA group configuration examples (IPv6)
Example: Configuring the HA group in active/standby mode in collaboration with VRRP
Network configuration
As shown in Figure 22, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with VRRP.
· Configure the HA group to operate in active/standby mode.
· Configure Device A and Device B as the primary device and the secondary device, respectively.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Switch A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the router to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
3. Configure Switch B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Create VLAN 10.
# Configure the interfaces attached to the HA group and the host to operate at Layer 2. Assign them to VLAN 10 as access interfaces.
4. Configure the router:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 3003::15/64 to GigabitEthernet 1/0/7.
# Configure routes as follows:
¡ Specify 3003::3/64 (virtual IP address of VRRP group 1) as the next hop of the routes to the internal network.
¡ Specify the IP address of the peer interface attached to the traffic outgoing interface as the next hop of the route to the Internet.
5. Configure Device A:
a. Assign IP addresses to interfaces.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ipv6 address 3003::1/64
[DeviceA-GigabitEthernet1/0/1] ipv6 address fe80::3:1 link-local
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ipv6 address 3001::1/64
[DeviceA-GigabitEthernet1/0/2] ipv6 address fe80::1:1 link-local
[DeviceA-GigabitEthernet1/0/2] undo ipv6 nd ra halt
[DeviceA-GigabitEthernet1/0/2] quit
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] ipv6 address 3005::1/64
[DeviceA-GigabitEthernet1/0/3] ipv6 address auto link-local
[DeviceA-GigabitEthernet1/0/3] quit
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 3003::15.
[DeviceA] ipv6 route-static 0::0 0 3003::15
c. Configure HA group settings.
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ipv6 3005::2
[DeviceA-remote-backup-group] local-ipv6 3005::1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] undo backup-mode
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] vrrp ipv6 vrid 1 virtual-ip fe80::3:3 link-local active
[DeviceA-GigabitEthernet1/0/1] vrrp ipv6 vrid 1 virtual-ip 3003::3
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] vrrp ipv6 vrid 1 virtual-ip fe80::1:3 link-local active
[DeviceA-GigabitEthernet1/0/2] vrrp ipv6 vrid 1 virtual-ip 3001::3
[DeviceA-GigabitEthernet1/0/2] quit
d. Configure security services on Device A. (Details not shown.)
6. Configure Device B:
a. Assign IP addresses to interfaces.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipv6 address 3003::2/64
[DeviceB-GigabitEthernet1/0/1] ipv6 address fe80::3:2 link-local
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] ipv6 address 3001::2/64
[DeviceB-GigabitEthernet1/0/2] ipv6 address fe80::1:2 link-local
[DeviceB-GigabitEthernet1/0/2] undo ipv6 nd ra halt
[DeviceB-GigabitEthernet1/0/2] quit
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ipv6 address 3005::2/64
[DeviceB-GigabitEthernet1/0/3] ipv6 address auto link-local
[DeviceB-GigabitEthernet1/0/3] quit
b. Configure settings for routing. This example configures a static route, and the next hop in the route is 3003::15.
[DeviceB] ipv6 route-static 0::0 0 3003::15
c. Configure HA group settings.
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ipv6 3005::1
[DeviceB-remote-backup-group] local-ipv6 3005::2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] undo backup-mode
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
[DeviceB-remote-backup-group] quit
# Create VRRP groups and associate them with the HA group.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] vrrp ipv6 vrid 1 virtual-ip fe80::3:3 link-local standby
[DeviceB-GigabitEthernet1/0/1] vrrp ipv6 vrid 1 virtual-ip 3003::3
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] vrrp ipv6 vrid 1 virtual-ip fe80::1:3 link-local standby
[DeviceB-GigabitEthernet1/0/2] vrrp ipv6 vrid 1 virtual-ip 3001::3
[DeviceB-GigabitEthernet1/0/2] quit
7. On the host, specify 3001::3 (virtual IP address of VRRP group 2) as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IPv6: 3005::1
Remote IPv6: 3005::2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that Device A is the master in all VRRP groups.
[DeviceA] display vrrp ipv6
IPv6 Virtual Router Information:
Running mode : Standard
RBM control channel is established
IPv6 VRRP active group status : Master
IPv6 VRRP standby group status: Master
Total number of virtual routers : 2
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Master 100 100 None FE80::3:3
GE1/0/2 1 Master 100 100 None FE80::1:3
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device A generates log messages when the host communicates with the Internet. (Details not shown.)
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Active/standby
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IPv6: 3005::2
Remote IPv6: 3005::1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 0 min
# Verify that Device A is the backup in all VRRP groups.
[DeviceB] display vrrp ipv6
IPv6 Virtual Router Information:
Running mode : Standard
RBM control channel is established
IPv6 VRRP active group status : Backup
IPv6 VRRP standby group status: Backup
Total number of virtual routers : 2
Interface VRID State Running Adver Auth Virtual
Pri Timer Type IP
---------------------------------------------------------------------
GE1/0/1 1 Backup 100 100 None FE80::3:3
GE1/0/2 1 Backup 100 100 None FE80::1:3
# Enable logging for the interzone policy that permits communication between security zones Trust and Untrust. Verity that Device B does not generate log messages when the host communicates with the Internet. (Details not shown.)
Example: Configuring the HA group in dual-active mode in collaboration with a routing protocol
Network configuration
As shown in Figure 23, set up the HA group at the border between the Internet and the internal network of an enterprise to ensure service continuity.
· Configure the HA group to collaborate with OSPFv3.
· Configure the HA group to operate in dual-active mode.
· Configure Device A and Device B to load share traffic.
Procedure
1. Verify that Device A and Device B have software and hardware environment consistency.
2. Configure Router A:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 3003::2/64 to GigabitEthernet 1/0/7.
# Assign 3004::2/64 to GigabitEthernet 1/0/8.
# Configure OSPFv3 for Device A, Device B, and the routers to have Layer 3 reachability.
# Configure per-flow load sharing for IP forwarding.
3. Configure Router B:
|
|
NOTE: This step only provides the brief configuration procedure. |
# Assign 3001::2/64 to GigabitEthernet 1/0/7.
# Assign 3002::2/64 to GigabitEthernet 1/0/8.
# Configure OSPFv3 for Device A, Device B, and the routers to have Layer 3 reachability.
# Configure per-flow load sharing for IP forwarding.
4. Configure Device A:
a. Assign an IP address to GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ipv6 address 3003::1/64
[DeviceA-GigabitEthernet1/0/1] ipv6 address auto link-local
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
b. Configure OSPFv3. Use the default OSPFv3 link cost configuration.
[DeviceA] ospfv3 1
[DeviceA-ospfv3-1] router-id 2.1.1.1
[DeviceA-ospfv3-1] quit
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ospfv3 1 area 0
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface GigabitEthernet1/0/2
[DeviceA-GigabitEthernet1/0/2] ospfv3 1 area 0
[DeviceA-GigabitEthernet1/0/2] quit
c. Configure HA group settings.
# Associate track entries with interfaces.
[DeviceA] track 1 interface gigabitethernet 1/0/1
[DeviceA-track-1] quit
[DeviceA] track 2 interface gigabitethernet 1/0/2
[DeviceA-track-2] quit
# Set up an HA group.
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ipv6 3005::2
[DeviceA-remote-backup-group] local-ipv6 3005::1
[DeviceA-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
[DeviceA-remote-backup-group] backup-mode dual-active
[DeviceA-remote-backup-group] hot-backup enable
[DeviceA-remote-backup-group] configuration auto-sync enable
[DeviceA-remote-backup-group] configuration sync-check interval 12
[DeviceA-remote-backup-group] delay-time 1
# Configure the HA group to change the link costs advertised in OSPFv3 routes to 1.
[DeviceA-remote-backup-group] adjust-cost ospfv3 enable absolute 1
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceA-remote-backup-group] track 1
[DeviceA-remote-backup-group] track 2
[DeviceA-remote-backup-group] quit
d. Configure security services on Device A. (Details not shown.)
5. Configure Device B:
a. Assign IP addresses to interfaces.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipv6 address 3002::1/64
[DeviceB-GigabitEthernet1/0/1] ipv6 address auto link-local
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] ipv6 address 3004::1/64
[DeviceB-GigabitEthernet1/0/2] ipv6 address auto link-local
[DeviceB-GigabitEthernet1/0/2] quit
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ipv6 address 3005::2/64
[DeviceB-GigabitEthernet1/0/3] ipv6 address auto link-local
[DeviceB-GigabitEthernet1/0/3] quit
b. Configure OSPFv3. Use the default OSPFv3 link cost configuration.
[DeviceB] ospfv3 1
[DeviceB-ospfv3-1] router-id 3.1.1.1
[DeviceB-ospfv3-1] quit
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ospfv3 1 area 0
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface GigabitEthernet1/0/2
[DeviceB-GigabitEthernet1/0/2] ospfv3 1 area 0
[DeviceB-GigabitEthernet1/0/2] quit
c. Configure HA group settings.
# Associate track entries with interfaces.
[DeviceB] track 1 interface gigabitethernet 1/0/1
[DeviceB-track-1] quit
[DeviceB] track 2 interface gigabitethernet 1/0/2
[DeviceB-track-2] quit
# Set up an HA group.
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ipv6 3005::1
[DeviceB-remote-backup-group] local-ipv6 3005::2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
[DeviceB-remote-backup-group] backup-mode dual-active
[DeviceB-remote-backup-group] hot-backup enable
[DeviceB-remote-backup-group] configuration auto-sync enable
[DeviceB-remote-backup-group] configuration sync-check interval 12
[DeviceB-remote-backup-group] delay-time 1
# Configure the HA group to change the link costs advertised in OSPFv3 routes to 1.
[DeviceB-remote-backup-group] adjust-cost ospfv3 enable absolute 1
# Configure the HA group to monitor the status of track entry 1 and track entry 2.
[DeviceB-remote-backup-group] track 1
[DeviceB-remote-backup-group] track 2
[DeviceB-remote-backup-group] quit
6. On the hosts, specify 2002::1 as the default gateway. (Details not shown.)
Verifying the configuration
1. Verify the configuration on Device A:
# Verify that the HA channels have been set up.
[DeviceA] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Primary
Data channel interface: GigabitEthernet1/0/3
Local IPv6: 3005::1
Remote IPv6: 3005::2 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that the OSPFv3 routes advertised by Device A and Device B include the same link cost.
[DeviceA] display ospfv3 interface
OSPFv3 Process 1 with Router ID 2.1.1.1
Area: 0.0.0.0
-------------------------------------------------------------------------
ID State Cost Pri DR BDR Ins Name
2 DR 1 1 2.1.1.1 1.1.1.1 0 GE1/0/1
3 BDR 1 1 4.1.1.1 2.1.1.1 0 GE1/0/2
2. Verify the configuration on Device B:
# Verify that the HA channels have been set up.
[DeviceB] display remote-backup-group status
Remote backup group information:
Backup mode: Dual-active
Device role: Secondary
Data channel interface: GigabitEthernet1/0/3
Local IPv6: 3005::2
Remote IPv6: 3005::1 Destination port: 60064
Control channel status: Connected
Hot backup status:Enabled
Auto configuration synchronization: Enable
Configuration consistency check interval: 12 hour
Delay-time: 1 min
# Verify that the OSPFv3 routes advertised by Device A and Device B include the same link cost.
[DeviceB] display ospfv3 interface
OSPFv3 Process 1 with Router ID 3.1.1.1
Area: 0.0.0.0
-------------------------------------------------------------------------
ID State Cost Pri DR BDR Ins Name
2 DR 1 1 3.1.1.1 1.1.1.1 0 GE1/0/1
3 BDR 1 1 4.1.1.1 3.1.1.1 0 GE1/0/2