- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Layer 2 forwarding configuration | 118.18 KB |
Configuring normal Layer 2 forwarding
About normal Layer 2 forwarding
Display and maintenance commands for Layer 2 forwarding
Configuring fast Layer 2 forwarding
Disabling VLAN ID check for fast Layer 2 forwarding
Display and maintenance commands for fast Layer 2 forwarding
Configuring bridging forwarding
Configuring security service bypass
Configuring fast bridge forwarding
Disabling VLAN ID check for fast bridge forwarding
Display and maintenance commands for fast bridge forwarding
Configuring normal Layer 2 forwarding
About normal Layer 2 forwarding
When an incoming frame's destination MAC address does not match any Layer 3 interface's MAC address, normal Layer 2 forwarding forwards the frame through a Layer 2 interface.
The device uses the destination MAC address of the frame to look for a match in the MAC address table.
· The device forwards the frame out of the outgoing interface in the matching entry if a match is found.
· The device floods the frame to all interfaces in the VLAN of the frame if no match is found.
Normal Layer 2 forwarding is enabled by default.
Display and maintenance commands for Layer 2 forwarding
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display Layer 2 forwarding statistics. |
display mac-forwarding statistics [ interface interface-type interface-number ] |
|
Clear Layer 2 forwarding statistics. |
reset mac-forwarding statistics |
Configuring fast Layer 2 forwarding
About fast Layer 2 forwarding
Fast Layer 2 forwarding improves packet forwarding efficiency by using a high-speed cache and flow-based technology. It identifies a flow by using the following items:
· Source IP address.
· Source port number.
· Destination IP address.
· Destination port number.
· Protocol number.
· Input interface.
· Output interface.
· VLAN ID.
Fast Layer 2 forwarding creates an entry in a high-speed cache by obtaining the forwarding information of a flow's first packet. Subsequent packets of the flow are forwarded based on the entry.
Fast Layer 2 forwarding is enabled by default.
Disabling VLAN ID check for fast Layer 2 forwarding
About this task
The VLAN ID of a packet helps the device to determine the TCP session to which the packet belongs. On a hot backup system formed by two firewalls, you must disable VLAN ID check if the traffic incoming interfaces on the primary and secondary devices belong to different VLANs. If you enable VLAN ID check, traffic cannot match session entries correctly when asymmetric-path traffic exists.
Procedure
1. Enter system view.
system-view
2. Disable VLAN ID check for fast Layer 2 forwarding.
undo mac fast-forwarding check-vlan-id
By default, VLAN ID check is enabled for fast Layer 2 forwarding.
Display and maintenance commands for fast Layer 2 forwarding
Execute display commands in any view.
|
Task |
Command |
|
Display IPv4 fast forwarding entries. |
In standalone mode: display mac-forwarding cache ip [ ip-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display mac-forwarding cache ip [ ip-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv4 fast forwarding entries for fragments. |
In standalone mode: display mac-forwarding cache ip fragment [ ip-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display mac-forwarding cache ip fragment [ ip-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv6 fast forwarding entries. |
In standalone mode: display mac-forwarding cache ipv6 [ ipv6-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display mac-forwarding cache ipv6 [ ipv6-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
Configuring bridge forwarding
About bridge forwarding
Bridge forwarding allows users to customize bridge instances to implement VLAN or port based secure packet forwarding.
Bridge forwarding types
Bridge forwarding has the following types:
· Inline forwarding—Inline forwarding has the following types:
¡ Reflect-type bridge forwarding—Forwards a packet through the receiving port of the packet.
¡ Forward-type bridge forwarding—Forwards a packet through a port that is different from the receiving port of the packet.
¡ Blackhole-type bridge forwarding—Drops the received packets.
Inline forwarding
Inline forwarding monitors traffic at the data link layer. It is typically used on security devices. When inline forwarding is configured on the device, Layer 2 traffic arriving at the device is forwarded toward the destination after security service processing.
Inline forwarding can be further classified into the following forwarding types:
· Reflect-type bridge forwarding.
· Blackhole-type bridge forwarding.
· Forward-type bridge forwarding.
Reflect-type/blackhole-type bridge forwarding
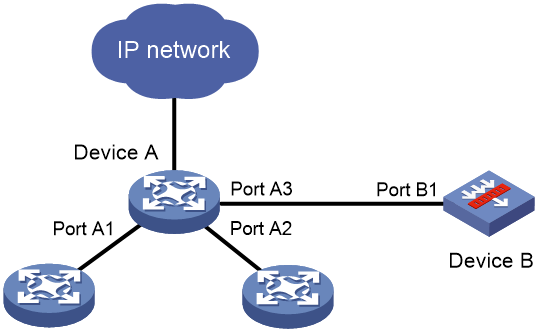
Reflect-type bridge forwarding and blackhole-type bridge forwarding are applicable to the scenario where a device directly accesses the network and is directly connected to a security device.
As shown in Figure 1, Device A is connected to the security device (Device B) through a physical port.
· In reflect-type bridge forwarding mode, packets arriving at Device A are forwarded to Device B for security service processing and then sent back to Device A for forwarding.
· In blackhole-type bridge forwarding mode, packets arriving at Device A are forwarded to Device B. Device B processes the packets and then drops the packets.
Figure 1 Reflect-type/blackhole-type bridge forwarding network
Forward-type bridge forwarding
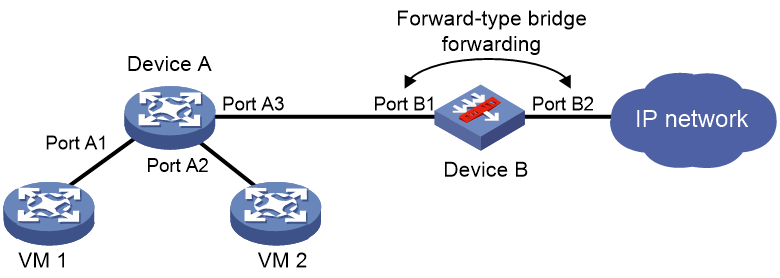
Forward-type bridge forwarding is applicable to the scenario where a device accesses the network through a security device.
As shown in Figure 2, Device A is connected to Device B through two physical ports. Device B uses one port to receive packets from Device A, and it uses the other port to send packets back to Device A.
Figure 2 Forward-type bridge forwarding network
Packet processing example in inline forwarding
As shown in Figure 1 and Figure 2, when VMs 1 and 2 communicate through Device A, inline forwarding processes packets between them as follows:
· Device A forwards the received packets to Device B.
· Device B passes the IP packets to the security modules for processing and sends other types of packets back to Device A.
· Device B creates forwarding entries for IP packets that meet the security requirements and forwards them to Device A. IP packets that do not meet the security requirements are dropped.
Configuring bridging forwarding
Configuring inline forwarding
Restrictions and guidelines
You can manually create reflect-type, forward-type, and blackhole-type bridge instances for inline forwarding and add interfaces to the instances.
The device will automatically create a forward-type bridge instance upon insertion of a hardware bypass subcard.
If you configure inline forwarding on a security device connected to a switch, disable MAC address learning on the switch's interface that is connected to the security device to avoid frequent MAC moves.
Only one interface can be added to a reflect-type or blackhole-type bridge instance.
Only two interfaces can be added to a manually created forward-type bridge instance. The two interfaces must be the same type.
An automatically created forward-type bridge instance uses the pair of interfaces on the bypass subcard by default and you cannot edit the interfaces in the instance.
If you add a Layer 3 Ethernet interface to a forward-type bridge instance, the interface can be used only for Layer 2 forwarding. As a best practice, do not configure Layer 3-related settings such as configuring an IP address, for a Layer 3 Ethernet interface in a forward-type bridge instance. Even if you configure these settings, the settings will not take effect.
Procedure
1. Enter system view.
system-view
2. (Optional.) Configure the device to ignore the tunnel encapsulation when forwarding tunneled packets in inline mode.
bridge tunnel-encapsulation skip
In inline forwarding mode, tunneled packets are forwarded based on information in the tunnel encapsulation by default.
3. Create a bridge instance and enter its view.
¡ Create a reflect-type bridge instance.
bridge bridge-index reflect
¡ Create a forward-type bridge instance.
bridge bridge-index forward
¡ Create a blackhole-type bridge instance.
bridge bridge-index blackhole
4. Add an interface to the bridge instance.
add interface interface-type interface-number
By default, no interfaces exist in a manually created bridge instance.
Configuring security service bypass
About this task
By default, packets are processed by the security service first before being forwarded according to the configured bridge forwarding mode.
The security service bypass feature enables user traffic to bypass security service processing of a security device and be forwarded directly according to the configured bridge forwarding mode.
The device supports only the internal bypass mode. In internal bypass mode, user traffic is sent to the security device but is not processed by it. The security device directly forwards or drops the traffic according to the configured bridge forwarding mode.
Restrictions and guidelines for security service bypass
If you configure the bypass enable command for the same bridge instance multiple times, the most recent configuration takes effect.
Enabling internal security service bypass
1. Enter system view.
system-view
2. Enter bridge instance view.
¡ Enter the view of a reflect-type bridge instance.
bridge bridge-index reflect
¡ Enter the view of an automatically created forward-type bridge instance.
bridge bridge-index forward
¡ Enter the view of a manually created forward-type bridge instance.
bridge bridge-index forward
¡ Enter the view of a blackhole-type bridge instance.
bridge bridge-index blackhole
3. Enable internal security service bypass.
bypass enable
Security service bypass is disabled by default.
Configuring fast bridge forwarding
About fast bridge forwarding
Fast bridge forwarding improves packet forwarding efficiency by using a high-speed cache and flow-based technology. It identifies a flow by using the following items:
· Source IP address.
· Source port number.
· Destination IP address.
· Destination port number.
· Protocol number.
· Input interface.
· Output interface.
· VLAN ID.
Fast bridge forwarding creates an entry in a high-speed cache by obtaining the forwarding information of a flow's first packet. Subsequent packets of the flow are forwarded based on the entry.
Fast bridge forwarding is enabled by default.
Disabling VLAN ID check for fast bridge forwarding
About this task
The VLAN ID of a packet helps the device to determine the TCP session to which the packet belongs. On a hot backup system formed by two firewalls, you must disable VLAN ID check if the traffic incoming interfaces on the primary and secondary devices belong to different VLANs. If you enable VLAN ID check, traffic cannot match session entries correctly when asymmetric-path traffic exists.
Restrictions and guidelines
Only inline forwarding supports VLAN ID check. You do not need to configure this feature for inter-VLAN fast bridge forwarding because the device does not check VLAN IDs for inter-VLAN fast bridge forwarding. That is, this feature does not take effect on inter-VLAN fast bridge forwarding.
On a hot backup system formed by two firewalls, inter-VLAN fast bridge forwarding enables a packet to match the same session after being transmitted between the primary and secondary devices.
Procedure
1. Enter system view.
system-view
2. Disable VLAN ID check for fast bridge forwarding.
undo bridge fast-forwarding check-vlan-id
By default, VLAN ID check is enabled for fast bridge forwarding.
Display and maintenance commands for fast bridge forwarding
Execute display commands in any view.
|
Task |
Command |
|
Display IPv4 fast bridge forwarding entries. |
In standalone mode: display bridge cache ip inline [ ip-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display bridge cache ip inline [ ip-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv4 fast bridge forwarding entries for fragments. |
In standalone mode: display bridge cache ip fragment inline [ ip-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display bridge cache ip fragment inline [ ip-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Display IPv6 fast bridge forwarding entries. |
In standalone mode: display bridge cache ipv6 inline [ ipv6-address ] [ slot slot-number [ cpu cpu-number ] ] In IRF mode: display bridge cache ipv6 inline [ ipv6-address ] [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |