- Table of Contents
-
- 20-Network Management and Monitoring Configuration Guide
- 00-Preface
- 01-System maintenance and debugging configuration
- 02-NQA configuration
- 03-SNMP configuration
- 04-RMON configuration
- 05-NETCONF configuration
- 06-EAA configuration
- 07-Process monitoring and maintenance configuration
- 08-Flow log configuration
- 09-Packet capture configuration
- 10-Mirroring configuration
- 11-Fast log output configuration
- 12-UCC configuration
- 13-SQA configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-EAA configuration | 119.60 KB |
Contents
Restrictions: Command and hardware compatibility
Configuring a user-defined EAA environment variable
Configuring a monitor policy from the CLI
Configuring a monitor policy by using Tcl
Display and maintenance commands for EAA
Example: Configuring a CLI event monitor policy by using Tcl
Example: Configuring a CLI event monitor policy from the CLI
Example: Configuring a CLI event monitor policy with EAA environment variables from the CLI
Configuring EAA
About EAA
Embedded Automation Architecture (EAA) is a monitoring framework that enables you to self-define monitored events and actions to take in response to an event. It allows you to create monitor policies by using the CLI or Tcl scripts.
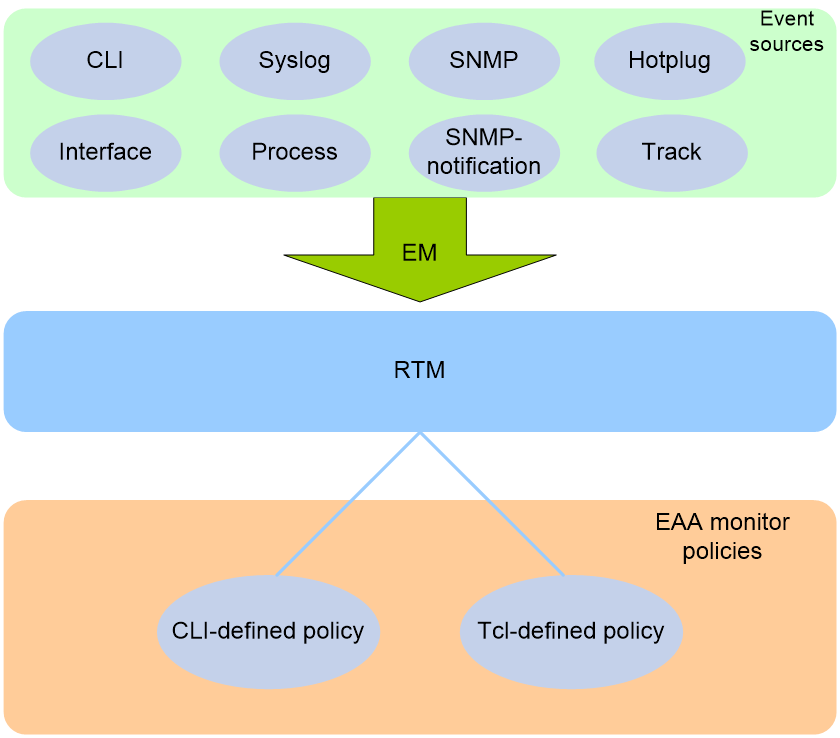
EAA framework
EAA framework includes a set of event sources, a set of event monitors, a real-time event manager (RTM), and a set of user-defined monitor policies, as shown in Figure 1.
Figure 1 EAA framework
Event sources
Event sources are software or hardware modules that trigger events (see Figure 1).
For example, the CLI module triggers an event when you enter a command. The Syslog module (the information center) triggers an event when it receives a log message.
Event monitors
EAA creates one event monitor to monitor the system for the event specified in each monitor policy. An event monitor notifies the RTM to run the monitor policy when the monitored event occurs.
RTM
RTM manages the creation, state machine, and execution of monitor policies.
EAA monitor policies
A monitor policy specifies the event to monitor and actions to take when the event occurs.
You can configure EAA monitor policies by using the CLI or Tcl.
A monitor policy contains the following elements:
· One event.
· A minimum of one action.
· A minimum of one user role.
· One running time setting.
For more information about these elements, see "Elements in a monitor policy."
Elements in a monitor policy
Elements in an EAA monitor policy include event, action, user role, and runtime.
Event
Table 1 shows types of events that EAA can monitor.
|
Event type |
Description |
|
CLI |
CLI event occurs in response to monitored operations performed at the CLI. For example, a command is entered, a question mark (?) is entered, or the Tab key is pressed to complete a command. |
|
Syslog |
Syslog event occurs when the information center receives the monitored log within a specific period. NOTE: The log that is generated by the EAA RTM does not trigger the monitor policy to run. |
|
Process |
Process event occurs in response to a state change of the monitored process (such as an exception, shutdown, start, or restart). Both manual and automatic state changes can cause the event to occur. |
|
Hotplug |
Hot-swapping event occurs when the monitored member device joins or leaves the IRF fabric. |
|
Interface |
Each interface event is associated with two user-defined thresholds: start and restart. An interface event occurs when the monitored interface traffic statistic crosses the start threshold in the following situations: · The statistic crosses the start threshold for the first time. · The statistic crosses the start threshold each time after it crosses the restart threshold. |
|
SNMP |
Each SNMP event is associated with two user-defined thresholds: start and restart. SNMP event occurs when the monitored MIB variable's value crosses the start threshold in the following situations: · The monitored variable's value crosses the start threshold for the first time. · The monitored variable's value crosses the start threshold each time after it crosses the restart threshold. |
|
SNMP-Notification |
SNMP-Notification event occurs when the monitored MIB variable's value in an SNMP notification matches the specified condition. For example, the broadcast traffic rate on an Ethernet interface reaches or exceeds 30%. |
|
Track |
Track event occurs when the state of the track entry changes from Positive to Negative or from Negative to Positive. If you specify multiple track entries for a policy, EAA triggers the policy only when the state of all the track entries changes from Positive (Negative) to Negative (Positive). If you set a suppress time for a policy, the timer starts when the policy is triggered. The system does not process the messages that report the track entry state change from Positive (Negative) to Negative (Positive) until the timer times out. |
Action
You can create a series of order-dependent actions to take in response to the event specified in the monitor policy.
The following are available actions:
· Executing a command.
· Sending a log.
· Enabling an active/standby switchover.
· Executing a reboot without saving the running configuration.
User role
For EAA to execute an action in a monitor policy, you must assign the policy the user role that has access to the action-specific commands and resources. If EAA lacks access to an action-specific command or resource, EAA does not perform the action and all the subsequent actions.
For example, a monitor policy has four actions numbered from 1 to 4. The policy has user roles that are required for performing actions 1, 3, and 4. However, it does not have the user role required for performing action 2. When the policy is triggered, EAA executes only action 1.
For more information about user roles, see RBAC in Fundamentals Configuration Guide.
Runtime
The runtime limits the amount of time that the monitor policy runs its actions from the time it is triggered. This setting prevents a policy from running its actions permanently to occupy resources.
EAA environment variables
EAA environment variables decouple the configuration of action arguments from the monitor policy so you can modify a policy easily.
An EAA environment variable is defined as a <variable_name variable_value> pair and can be used in different policies. When you define an action, you can enter a variable name with a leading dollar sign ($variable_name). EAA will replace the variable name with the variable value when it performs the action.
To change the value for an action argument, modify the value specified in the variable pair instead of editing each affected monitor policy.
EAA environment variables include system-defined variables and user-defined variables.
System-defined variables
System-defined variables are provided by default, and they cannot be created, deleted, or modified by users. System-defined variable names start with an underscore (_) sign. The variable values are set automatically depending on the event setting in the policy that uses the variables.
System-defined variables include the following types:
· Public variable—Available for any events.
· Event-specific variable—Available only for a type of event. The hotplug event-specific variable is _slot. When a member device in slot 1 joins or leaves the IRF fabric, the value of _slot is 1. When a member device in slot 2 joins or leaves the IRF fabric, the value of _slot is 2. (In IRF mode.)
Table 2 shows all system-defined variables.
Table 2 System-defined EAA environment variables by event type
|
Event |
Variable name and description |
|
Any event |
_event_id: Event ID _event_type: Event type _event_type_string: Event type description _event_time: Time when the event occurs _event_severity: Severity level of an event |
|
CLI |
_cmd: Commands that are matched |
|
Syslog |
_syslog_pattern: Log message content |
|
Hotplug |
_slot: The value is 1.(In standalone mode.) |
|
Hotplug |
_slot: ID of the member device that joins or leaves the IRF fabric (In IRF mode.) |
|
Interface |
_ifname: Interface name |
|
SNMP |
_oid: OID of the MIB variable where an SNMP operation is performed _oid_value: Value of the MIB variable |
|
SNMP-Notification |
_oid: OID that is included in the SNMP notification. |
|
Process |
_process_name: Process name |
User-defined variables
You can use user-defined variables for all types of events.
User-defined variable names can contain digits, characters, and the underscore sign (_), except that the underscore sign cannot be the leading character.
Restrictions: Command and hardware compatibility
The WX1800H series, WX2500H series, MAK series, and WX3000H series access controllers do not support parameters or commands that are available only in IRF mode.
Configuring a user-defined EAA environment variable
About this task
Configure user-defined EAA environment variables so that you can use them when creating EAA monitor policies.
Procedure
1. Enter system view.
system-view
2. Configure a user-defined EAA environment variable.
rtm environment var-name var-value
For the system-defined variables, see Table 2.
Configuring a monitor policy
Restrictions and guidelines
Make sure the actions in different policies do not conflict. Policy execution result will be unpredictable if policies that conflict in actions are running concurrently.
You can assign the same policy name to a CLI-defined policy and a Tcl-defined policy. However, you cannot assign the same name to policies that are the same type.
A monitor policy supports only one event and runtime. If you configure multiple events for a policy, the most recent one takes effect.
A monitor policy supports a maximum of 64 valid user roles. User roles added after this limit is reached do not take effect.
Configuring a monitor policy from the CLI
Restrictions and guidelines
You can configure a series of actions to be executed in response to the event specified in a monitor policy. EAA executes the actions in ascending order of action IDs. When you add actions to a policy, you must make sure the execution order is correct. If two actions have the same ID, the most recent one takes effect.
Procedure
1. Enter system view.
system-view
2. Create a CLI-defined policy and enter its view.
rtm cli-policy policy-name
3. Configure an event for the policy.
¡ Configure a CLI event.
event cli { async [ skip ] | sync } mode { execute | help | tab } pattern regular-exp
¡ Configure an IRF fabric join or leave event.
event hotplug [ insert | remove ] slot slot-number
¡ Configure an interface event.
event interface interface-type interface-number monitor-obj monitor-obj start-op start-op start-val start-val restart-op restart-op restart-val restart-val [ interval interval ]
¡ Configure a process event.
event process { exception | restart | shutdown | start } [ name process-name [ instance instance-id ] ] [ slot slot-number ]
¡ Configure an SNMP event.
event snmp oid oid monitor-obj { get | next } start-op start-op start-val start-val restart-op restart-op restart-val restart-val [ interval interval ]
For the command to take effect, enable SNMP before you execute this command. The device automatically deletes this command after you disable SNMP.
¡ Configure an SNMP-Notification event.
event snmp-notification oid oid oid-val oid-val op op [ drop ]
For the command to take effect, enable SNMP before you execute this command. The device automatically deletes this command after you disable SNMP.
¡ Configure a Syslog event.
event syslog priority priority msg msg occurs times period period
¡ Configure a track event.
event track track-list state { negative | positive } [ suppress-time suppress-time ]
By default, a monitor policy does not contain an event.
If you configure multiple events for a policy, the most recent one takes effect.
4. Configure the actions to take when the event occurs.
Choose the following tasks as needed:
¡ Configure a CLI action.
action number cli command-line
¡ Configure a reboot action.
action number reboot [ slot slot-number ]
¡ Configure an active/standby switchover action.
action number switchover
¡ Configure a logging action.
action number syslog priority priority facility local-number msg msg-body
By default, a monitor policy does not contain any actions.
5. (Optional.) Assign a user role to the policy.
user-role role-name
By default, a monitor policy contains user roles that its creator had at the time of policy creation.
An EAA policy cannot have both the security-audit user role and any other user roles. Any previously assigned user roles are automatically removed when you assign the security-audit user role to the policy. The previously assigned security-audit user role is automatically removed when you assign any other user roles to the policy.
6. (Optional.) Configure the policy action runtime.
running-time time
The default policy action runtime is 20 seconds.
If you configure multiple action runtimes for a policy, the most recent one takes effect.
7. Enable the policy.
commit
By default, CLI-defined policies are not enabled.
A CLI-defined policy can take effect only after you perform this step.
Configuring a monitor policy by using Tcl
About this task
A Tcl script contains two parts: Line 1 and the other lines.
· Line 1
Line 1 defines the event, user roles, and policy action runtime. After you create and enable a Tcl monitor policy, the device immediately parses, delivers, and executes Line 1.
Line 1 must use the following format:
::comware::rtm::event_register event-type arg1 arg2 arg3 … user-role role-name1 | [ user-role role-name2 | [ … ] ] [ running-time running-time ]
¡ The arg1 arg2 arg3 … arguments represent event matching rules. If an argument value contains spaces, use double quotation marks ("") to enclose the value. For example, "a b c."
¡ The configuration requirements for the event-type, user-role, and running-time arguments are the same as those for a CLI-defined monitor policy.
· The other lines
From the second line, the Tcl script defines the actions to be executed when the monitor policy is triggered. You can use multiple lines to define multiple actions. The system executes these actions in sequence. The following actions are available:
¡ Standard Tcl commands.
¡ EAA-specific Tcl actions:
- switchover ( ::comware::rtm::action switchover )
- syslog (::comware::rtm::action syslog priority priority facility local-number msg msg-body). For more information about these arguments, see EAA commands in Network Management and Monitoring Command Reference.
¡ Commands supported by the device.
Restrictions and guidelines
To revise the Tcl script of a policy, you must suspend all monitor policies first, and then resume the policies after you finish revising the script. The system cannot execute a Tcl-defined policy if you edit its Tcl script without first suspending these policies.
Procedure
1. Download the Tcl script file to the device by using FTP or TFTP.
For more information about using FTP and TFTP, see Fundamentals Configuration Guide.
2. Create and enable a Tcl monitor policy.
a. Enter system view.
system-view
b. Create a Tcl-defined policy and bind it to the Tcl script file.
rtm tcl-policy policy-name tcl-filename
By default, no Tcl policies exist.
(In IRF mode.) Make sure the script file is saved on all IRF member devices. This practice ensures that the policy can run correctly after a master/subordinate switchover occurs or the member device where the script file resides leaves the IRF.
Suspending monitor policies
About this task
This task suspends all CLI-defined and Tcl-defined monitor policies. If a policy is running when you perform this task, the system suspends the policy after it executes all the actions.
Restrictions and guidelines
To restore the operation of the suspended policies, execute the undo rtm scheduler suspend command.
Procedure
1. Enter system view.
system-view
2. Suspend monitor policies.
rtm scheduler suspend
Display and maintenance commands for EAA
Execute display commands except for the display this command in any view.
|
Task |
Command |
|
Display the running configuration of all CLI-defined monitor policies. |
display current-configuration |
|
Display user-defined EAA environment variables. |
display rtm environment [ var-name ] |
|
Display EAA monitor policies. |
display rtm policy { active | registered [ verbose ] } [ policy-name ] |
|
Display the running configuration of a CLI-defined monitor policy in CLI-defined monitor policy view. |
display this |
EAA configuration examples
Example: Configuring a CLI event monitor policy by using Tcl
Network configuration
As shown in Figure 2, use Tcl to create a monitor policy on the AC. This policy must meet the following requirements:
· EAA sends the log message "rtm_tcl_test is running" when a command that contains the display this string is entered.
· The system executes the command only after it executes the policy successfully.
Procedure
# Edit a Tcl script file (rtm_tcl_test.tcl, in this example) for EAA to send the message "rtm_tcl_test is running" when a command that contains the display this string is executed.
::comware::rtm::event_register cli sync mode execute pattern display this user-role network-admin
::comware::rtm::action syslog priority 1 facility local4 msg rtm_tcl_test is running
# Download the Tcl script file from the TFTP server at 1.2.1.1.
<AC> tftp 1.2.1.1 get rtm_tcl_test.tcl
# Create Tcl-defined policy test and bind it to the Tcl script file.
<AC> system-view
[AC] rtm tcl-policy test rtm_tcl_test.tcl
[AC] quit
Verifying the configuration
# Execute the display rtm policy registered command to verify that a Tcl-defined policy named test is displayed in the command output.
<AC> display rtm policy registered
Total number: 1
Type Event TimeRegistered PolicyName
TCL CLI May 06 09:47:12 2019 test
# Enable the information center to output log messages to the current monitoring terminal.
<AC> terminal monitor
The current terminal is enabled to display logs.
<AC> system-view
[AC] info-center enable
Information center is enabled.
[AC] quit
# Execute the display this command. Verify that the system displays an "rtm_tcl_test is running" message and a message that the policy is being executed successfully.
<AC> display this
%Jan 1 09:50:04:634 2019 AC RTM/1/RTM_ACTION: rtm_tcl_test is running
%Jan 1 09:50:04:634 2019 AC RTM/6/RTM_POLICY: TCL policy test is running successfully.
#
return
Example: Configuring a CLI event monitor policy from the CLI
Network configuration
Configure a policy from the CLI to monitor the event that occurs when a question mark (?) is entered at the command line that contains letters and digits.
When the event occurs, the system executes the command and sends the log message "hello world" to the information center.
Procedure
# Create CLI-defined policy test and enter its view.
<AC> system-view
[AC] rtm cli-policy test
# Add a CLI event that occurs when a question mark (?) is entered at any command line that contains letters and digits.
[AC-rtm-test] event cli async mode help pattern [a-zA-Z0-9]
# Add an action that sends the message "hello world" with a priority of 4 from the logging facility local3 when the event occurs.
[AC-rtm-test] action 0 syslog priority 4 facility local3 msg “hello world”
# Add an action that enters system view when the event occurs.
[AC-rtm-test] action 2 cli system-view
# Add an action that creates VLAN 2 when the event occurs.
[AC-rtm-test] action 3 cli vlan 2
# Set the policy action runtime to 2000 seconds.
[AC-rtm-test] running-time 2000
# Specify the network-admin user role for executing the policy.
[AC-rtm-test] user-role network-admin
# Enable the policy.
[AC-rtm-test] commit
Verifying the configuration
# Execute the display rtm policy registered command to verify that a CLI-defined policy named test is displayed in the command output.
[AC-rtm-test] display rtm policy registered
Total number: 1
Type Event TimeRegistered PolicyName
TCL CLI Jan 1 09:47:12 2019 test
# Enable the information center to output log messages to the current monitoring terminal.
[AC-rtm-test] return
<AC> terminal monitor
The current terminal is enabled to display logs.
<AC> system-view
[AC] info-center enable
Information center is enabled.
[AC] quit
# Enter a question mark (?) at a command line that contains a letter d. Verify that the system displays a "hello world" message and a message that the policy is being executed successfully on the terminal screen.
<AC> d?
debugging
delete
diagnostic-logfile
dir
display
<AC>d%Jan 1 09:50:04:634 2019 AC RTM/4/RTM_ACTION: "hello world"
%Jan 1 09:50:04:634 2019 AC RTM/6/RTM_POLICY: CLI policy test is running successfully.
Example: Configuring a CLI event monitor policy with EAA environment variables from the CLI
Network configuration
Define an environment variable to match the IP address 1.1.1.1.
Configure a policy from the CLI to monitor the event that occurs when a command line that contains loopback0 is executed. In the policy, use the environment variable for IP address assignment.
When the event occurs, the system performs the following tasks:
· Creates the Loopback 0 interface.
· Assigns 1.1.1.1/24 to the interface.
· Sends the matching command line to the information center.
Procedure
# Configure an EAA environment variable for IP address assignment. The variable name is loopback0IP, and the variable value is 1.1.1.1.
<AC> system-view
[AC] rtm environment loopback0IP 1.1.1.1
# Create the CLI-defined policy test and enter its view.
[AC] rtm cli-policy test
# Add a CLI event that occurs when a command line that contains loopback0 is executed.
[AC-rtm-test] event cli async mode execute pattern loopback0
# Add an action that enters system view when the event occurs.
[AC-rtm-test] action 0 cli system-view
# Add an action that creates the interface Loopback 0 and enters loopback interface view.
[AC-rtm-test] action 1 cli interface loopback 0
# Add an action that assigns the IP address 1.1.1.1 to Loopback 0. The loopback0IP variable is used in the action for IP address assignment.
[AC-rtm-test] action 2 cli ip address $loopback0IP 24
# Add an action that sends the matching loopback0 command with a priority of 0 from the logging facility local7 when the event occurs.
[AC-rtm-test] action 3 syslog priority 0 facility local7 msg $_cmd
# Specify the network-admin user role for executing the policy.
[AC-rtm-test] user-role network-admin
# Enable the policy.
[AC-rtm-test] commit
[AC-rtm-test] return
Verifying the configuration
# Enable the information center to output log messages to the current monitoring terminal.
<AC> terminal monitor
The current terminal is enabled to display logs.
<AC> system-view
[AC] info-center enable
Information center is enabled.
# Execute the loopback0 command. Verify that the system displays a "loopback0" message and a message that the policy is being executed successfully on the terminal screen.
<AC> loopback0
<AC>%Jan 1 09:46:10:592 2019 AC RTM/0/RTM_ACTION: loopback0
%Jan 1 09:46:10:613 2019 AC RTM/6/RTM_POLICY: CLI policy test is running successfully.
# Verify that a Loopback 0 interface has been created and its IP address is 1.1.1.1.
<AC> display interface loopback brief
Brief information on interfaces in route mode:
Link: ADM - administratively down; Stby - standby
Protocol: (s) - spoofing
Interface Link Protocol Primary IP Description
Loop0 UP UP(s) 1.1.1.1