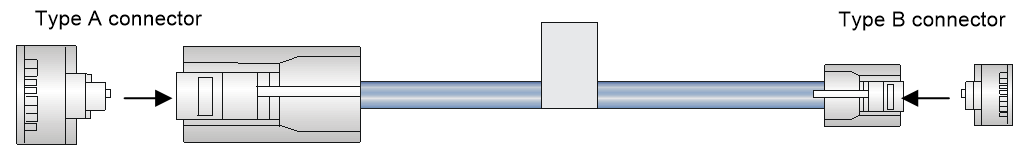- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Text | 4.85 MB |
Contents
General safety recommendations
Examining the installation site
Mounting the firewall on a workbench
Installing the firewall in a standard 19-inch rack
Rack-mounting the firewall by using front and rear mounting brackets
Rack-mounting the firewall by using front mounting brackets
Grounding the firewall with a grounding strip
Grounding the firewall with the grounding terminal on the rack
Installing a power module for an F1070 or F1080 firewall
Installing a power module for an F1090 firewall
Installing an interface module
Connecting a copper Ethernet port
Connecting a high-voltage DC power cord for an F1090 firewall
Check before starting the firewall
Starting the firewall and observing the initial startup conditions
Logging in from the Web interface
Logging in from the serial console port or micro USB console port
Replacing a power module for an F1070 or F1080 firewall
Replacing a power module for an F1090 firewall
Replacing a transceiver module
5 Hardware management and maintenance
Displaying detailed information about the firewall
Displaying the software and hardware version information for the firewall
Displaying the electrical label information for the firewall
Displaying the CPU usage of the firewall
Displaying the memory usage of the firewall
Displaying the operational status of power modules
Displaying the temperature information of the firewall
Displaying the operational statistics of the firewall
Displaying transceiver module information
Configuration terminal display problem
7 Appendix A Chassis views and technical specifications
Network data encryption modules
Network data encryption modules
Network data encryption modules
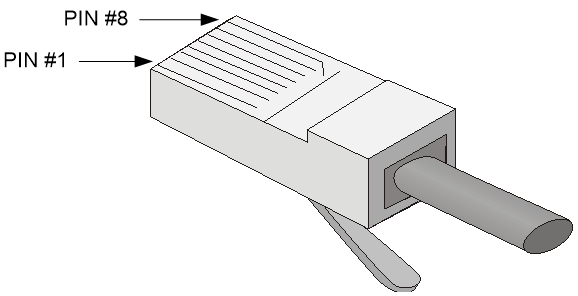
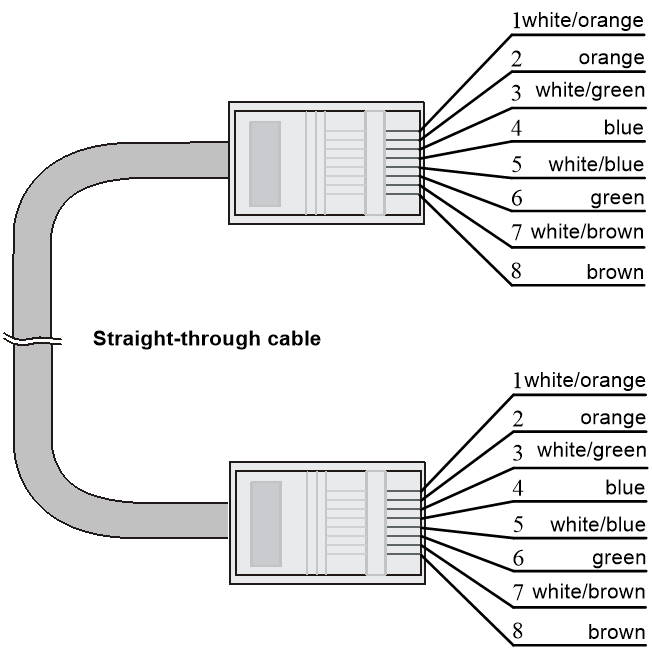
Making an Ethernet twisted pair cable
1 Preparing for installation
The H3C SecPath F10X0 firewall series include the following models:
· F1005
· F1010
· F1020
· F1030
· F1050
· F1060
· F1070
· F1080
Safety recommendations
To avoid any equipment damage or bodily injury, read the following safety recommendations before installation. Note that the recommendations do not cover every possible hazardous condition.
Safety symbols
When reading this document, note the following symbols:
![]() WARNING means an alert that calls attention to important information that if
not understood or followed can result in personal injury.
WARNING means an alert that calls attention to important information that if
not understood or followed can result in personal injury.
![]() CAUTION means an alert that calls attention to important information that if
not understood or followed can result in data loss, data corruption, or damage
to hardware or software.
CAUTION means an alert that calls attention to important information that if
not understood or followed can result in data loss, data corruption, or damage
to hardware or software.
General safety recommendations
· Do not place the firewall on an unstable case or desk. The firewall might be severely damaged in case of a fall.
· Make sure the ground is dry and flat and anti-slip measures are in place.
· Keep the chassis and installation tools away from walk areas.
· Keep the chassis clean and dust-free.
· Do not place the firewall near water or in a damp environment. Prevent water or moisture from entering the firewall chassis.
· Ensure good ventilation of the equipment room and keep the air inlet and outlet vents of the firewall free of obstruction.
· Make sure the operating voltage is in the required range.
· Use a screwdriver, rather than your fingers, to fasten screws.
· Stack devices according to the sizes of and packing symbols on the packages.
Figure1-1 Packing symbols
|
Symbol |
Description |
|
Stored with a maximum stack of n units. |
|
|
Transported and stored with the arrows up. |
|
|
Transported and stored with care. |
|
|
Transported and stored avoiding humidity, rains and wet floor. |
Electrical safety
· Carefully examine your work area for possible hazards such as moist floors, ungrounded power extension cables, and missing safety grounds.
· Locate the emergency power-off switch in the room before installation. Shut the power off at once in case accident occurs.
· Do not work alone when the firewall has power.
· Always verify that the power has been disconnected.
Laser safety
|
WARNING! Disconnected optical fibers or transceiver modules might emit invisible laser light. Do not stare into beams or view directly with optical instruments when the firewall is operating. |
The firewall is a Class 1 laser device.
· Before you disconnect the fiber connector, execute the shutdown command in interface view to disable the optical source.
· Install dust caps to disconnected optical fiber connectors and ports on disconnected transceiver modules to avoid damage caused by built-up dust.
· Insert a dust plug into empty fiber ports.
Handling safety
When you move the firewall, follow these guidelines:
· Move and unpack the firewall carefully to avoid firewall damage.
· Unpack the firewall at least half an hour and power on the firewall at least two hours after you move it from a place below 0°C (32°F) to the equipment room. This prevents condensation and even damage to the firewall.
· Use a safety hand truck when you move multiple firewalls.
· Before you move the firewall, remove all cables and mounting brackets.
· For long-distance transportation, remove all removable components, such as power modules and interface modules, and package them separately, and install the filler panels supplied with the firewall. For short-distance transportation, make sure all removable components are securely seated in the slots and the screws are fastened.
· When you move or lift the firewall chassis, support the bottom of the chassis, rather than holding any removable component. Make sure the accessories of the firewall are not lost or damaged during firewall moving.
Examining the installation site
The firewall can only be used indoors. To make sure the firewall operates correctly and to prolong its service lifetime, the installation site must meet the following requirements.
Weight support
Make sure the floor can support the total weight of the rack, chassis, modules, and all other components. For more information, see "Dimensions and weights."
Temperature and humidity
Maintain appropriate temperature and humidity in the equipment room.
· Lasting high relative humidity can cause poor insulation, electricity leakage, mechanical property change of materials, and metal corrosion.
· Lasting low relative humidity can cause washer contraction and ESD and bring problems including loose captive screws and circuit failure.
· High temperature can accelerate the aging of insulation materials and significantly lower the reliability and lifespan of the firewall.
For the temperature and humidity requirements of the firewall, see Table1-1.
Table1-1 Temperature/humidity requirements
|
Temperature |
Relative humidity |
|
· Operating: ¡ Without drives: 0°C to 45°C (32°F to 113°F) ¡ With hard drives: 5°C to 40°C (41°F to 104°F) · Storage: –40°C to +70°C (–40°F to +158°F) |
· Operating: ¡ Without drives: 5% to 95%, noncondensing ¡ With drives: 10% to 90%, noncondensing · Storage: 5% to 95%, noncondensing |
Cleanliness
Dust buildup on the chassis might result in electrostatic adsorption, which causes poor contact of metal components and contact points, especially when indoor relative humidity is low. In the worst case, electrostatic adsorption can cause communication failure.
Table1-2 Dust concentration limit in the equipment room
|
Substance |
Concentration limit (particles/m3) |
|
Dust particles |
≤ 3 × 104 (No visible dust on desk in three days) |
|
NOTE: Dust particle diameter ≥ 5 µm |
|
The equipment room must also meet strict limits on salts, acids, and sulfides to eliminate corrosion and premature aging of components, as shown in Table1-3.
Table1-3 Harmful gas limits in an equipment room
|
Gas |
Max. (mg/m3) |
|
SO2 |
0.2 |
|
H2S |
0.006 |
|
NH3 |
0.05 |
|
Cl2 |
0.01 |
|
NO2 |
0.04 |
Cooling system
For adequate cooling of the firewall, follow these guidelines:
· Install the firewall at the installation site with its airflow direction meeting the ventilation requirements.
¡ Workbench mounting—Ensure a minimum clearance of 100 mm (3.94 in) around the air inlet and outlet vents of the chassis.
¡ 19-inch rack mounting—Ensure a minimum clearance of 80 mm (3.15 in) around the air inlet and outlet vents of the chassis and a distance of 1U (44.45 mm, or 1.75 in) between the chassis and other devices.
· Make sure the installation site has a good cooling system.
The F1005 and F1010 firewalls use passive cooling for heat dissipation.
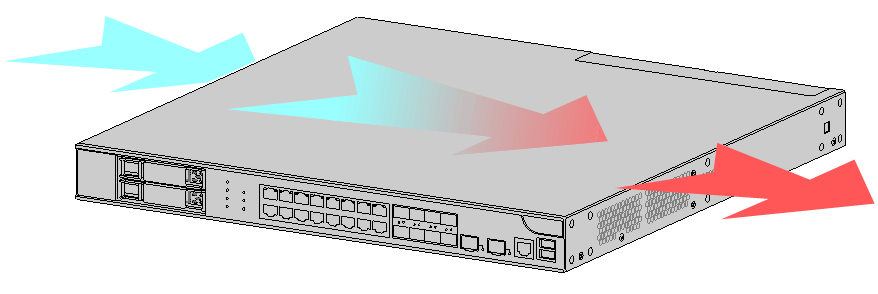
The F1020, F1030, F1050, F1060, F1070, F1080, and F1090 firewalls provide left side-intake and right-side exhaust airflow for heat dissipation.
Figure1-2 Airflow through the F1080 firewall chassis
ESD prevention
To prevent electrostatic discharge (ESD), follow these guidelines:
· Make sure the firewall, the workbench, and the rack are reliably grounded.
· Take dust-proof measures for the equipment room. For more information, see "Cleanliness."
· Maintain the humidity and temperature at an acceptable level. For more information, see "Temperature and humidity."
· Put the removed interface modules away on an ESD workbench, with the PCB upward, or put them in ESD bags for future use.
· Always wear ESD clothing, ESD gloves, and an ESD wrist strap.
EMI
All electromagnetic interference (EMI) sources, from outside or inside of the firewall and application system, adversely affect the firewall in the following ways:
· A conduction pattern of capacitance coupling.
· Inductance coupling.
· Electromagnetic wave radiation.
· Common impedance (including the grounding system) coupling.
To prevent EMI, use the following guidelines:
· If AC power is used, use a single-phase three-wire power receptacle with protection earth (PE) to filter interference from the power grid.
· Keep the firewall far away from radio transmitting stations, radar stations, and high-frequency devices.
· Use electromagnetic shielding, for example, shielded interface cables, when necessary.
· To prevent signal ports from getting damaged by overvoltage or overcurrent caused by lightning strikes, route interface cables only indoors. If part of the network cable of an Ethernet port must be routed outdoors, connect a lightning arrester to the cable before you plug the cable into the port.
Lightning protection
To protect the firewall from lightning better, follow these guidelines:
· Make sure the grounding cable of the chassis is reliably grounded.
· Make sure the grounding terminal of the AC power receptacle is reliably grounded.
· If an AC power cord is routed from outdoors for connecting to the device, connect the power cord first to a power lightning arrester before connecting it to the power receptacle on the device.
· If a network cable is routed from outdoors for connecting to an Ethernet port on the firewall, connect the network cable first to a network port lightning arrester before connecting it to the port.
|
IMPORTANT: No network port lightning arrester or AC power lightning arrester is provided with the device. Prepare them as required. For the technical specifications and installation instructions for the lightning protectors, see the documents shipped with them. |
Power supply
Verify that the power system at the installation site meets the requirements of the power modules, including the input method and rated input voltage. For more information, see "Appendix A Chassis views and technical specifications."
Installation tools
All installation tools are user supplied.
|
Flat-head screwdriver |
Phillips screwdriver |
Needle-nose pliers |
Diagonal pliers |
|
|
|
||
|
ESD wrist strap |
Marker |
|
|
Accessories
|
Mounting bracket for the F1005 and F1010 |
Mounting brackets (including M4 shoulder screw) for other F10X0 models than F1005 and F1010 |
M4 screw |
M6 rack screw and cage nut (shipped with the F1005 and F1010 firewalls and user supplied for other models) |
|
Rubber feet |
Power cord retainer clip |
Power cord |
Grounding cable |
|
|
|
|
|
|
Console cable |
|
|
|
Pre-installation checklist
Table1-4 Checklist before installation
|
Item |
Requirements |
Result |
|
|
Installation site |
Ventilation |
· Workbench mounting—Ensure a minimum clearance of 100 mm (3.94 in) around the air inlet and outlet vents of the chassis. · 19-inch rack mounting—Ensure a minimum clearance of 80 mm (3.15 in) around the air inlet and outlet vents of the chassis and a distance of 1U (44.45 mm, or 1.75 in) between the chassis and other devices. · A good ventilation system is available at the installation site. |
|
|
Temperature |
· Operating: ¡ Without drives: 0°C to 45°C (32°F to 113°F) ¡ With drives: 5°C to 40°C (41°F to 104°F) · Storage: –40°C to +70°C (–40°F to +158°F) |
|
|
|
Relative humidity |
· Operating: ¡ Without drives: 5% RH to 95% RH, noncondensing ¡ With drives: 10% RH to 90% RH, noncondensing · Storage: 5% RH to 95% RH, noncondensing |
|
|
|
Cleanness |
· Dust concentration ≤ 3 × 104 particles/m3 · No dust on desk within three days |
|
|
|
ESD prevention |
· The equipment, workbench, and rack are reliably grounded. · The equipment room is dust-proof. · The humidity and temperature are at an acceptable level. · Wear an ESD wrist strap and make sure it makes good skin contact and is reliably grounded when installing FRUs. · Put the removed interface modules away on an ESD workbench, with the PCB upward, or put them in ESD bags for future use. · Touch only the edges, instead of electronic components when observing or moving a removed interface module. |
|
|
|
EMI prevention |
· Take effective measures to protect the power system from the power grid system. · Separate the protection ground of the firewall from the grounding device or lightning protection grounding device as far as possible. · Keep the firewall far away from radio stations, radar and high-frequency devices working in high current. · Use electromagnetic shielding when necessary. |
|
|
|
Lightning protection |
· The grounding cable of the chassis is reliably grounded. · The grounding terminal of the AC power receptacle is reliably grounded. · (Optional.) A power lightning arrester is installed. |
|
|
|
Electricity safety |
· Equip a UPS. · Locate the power switch in the equipment room. In case of emergency during operation, switch off the power switch. |
|
|
|
Rack-mounting requirements |
· Make sure the cabinet is equipped with a good ventilation system. · The rack is sturdy enough to support the weight of the firewall and installation accessories. · The size of the rack is appropriate for the firewall. · The front and rear of the rack are a minimum of 0.8 m (31.50 in) away from walls or other devices. |
|
|
|
Safety precautions |
· The firewall is far away from any moist area and heat source. · The emergency power switch in the equipment room is located. |
|
|
|
Tools and accessories |
· Installation accessories supplied with the firewall · User-supplied tools |
|
|
|
Reference |
· Documents shipped with the firewall · Online documents |
|
|
2 Installing the firewall
|
WARNING! Keep the tamper-proof seal on a mounting screw on the chassis cover intact, and if you want to open the chassis, contact H3C for permission. Otherwise, H3C shall not be liable for any consequence. |
The firewall view varies by model. The following figures are for illustration only. This document uses an F1080 firewall as an example.
Installation flow
Table2-1 Installation flow for the F10X0 firewalls
|
Step |
Description |
|
Before installation, make sure all requirements on the checklist are met and the firewall is powered off. |
|
|
Verify that the workbench is sturdy and reliably grounded. Ensure a minimum clearance of 100 mm (3.94 in) around the air inlet and outlet vents of the chassis. |
|
|
To avoid bodily injury and device damage, use a minimum of two people to rack-mount the device. |
|
|
Before installation, make sure the firewall and rack are reliably grounded and you wear an ESD wrist strap. |
|
|
Before you install a power module, make sure the power module is not connected to any power source and the grounding cable of the firewall is connected reliably. |
|
|
Install compatible interface modules on the firewall. |
|
|
Install compatible drives on the firewall. |
|
|
The firewall provides various ports. Choose compatible transceiver modules and cables as required. To avoid bodily injury or device damage, read the restrictions and guidelines carefully before connection. |
|
|
Connect compatible power cords to the power modules. |
|
|
Verify that the firewall is installed securely and reliably grounded, and that the power modules are as required. |
Mounting the firewall on a workbench
|
IMPORTANT: · Ensure good ventilation and a minimum clearance of 100 mm (3.94 in) around the chassis for heat dissipation. · Avoid placing heavy objects on the firewall. · To stack firewalls, make sure a minimum vertical distance of 15 mm (0.59 in) is available between two adjacent firewalls. |
If a standard 19-inch rack is not available, you can place the firewall on a workbench.
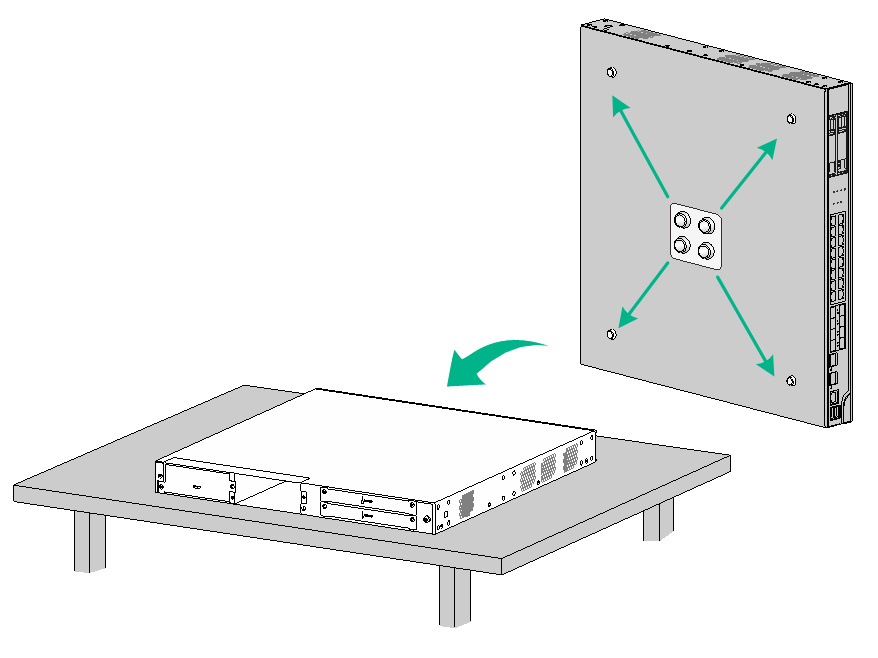
To mount the firewall on a workbench:
1. Verify that the workbench is sturdy and reliably grounded.
2. Place the firewall upside down on the workbench and clean the four round holes in the chassis bottom with a dry cloth.
3. Attach the four rubber feet to the round holes in the chassis bottom.
4. Place the firewall with upside up on the workbench.
Figure2-1 Mounting the firewall on a workbench
Installing the firewall in a standard 19-inch rack
|
WARNING! To avoid bodily injury and device damage, use a minimum of two persons to rack-mount the firewall. |
|
CAUTION: · For adequate heat dissipation, ensure a minimum clearance of 80 mm (3.15 in) around the air inlet and outlet vents of the chassis and a distance of 1U (44.45 mm, or 1.75 in) between the chassis and other devices in the rack. · As a best practice, use a rack shelf together with the mounting brackets to support the weight of the chassis. |
Rack-mounting the firewall by using front and rear mounting brackets
The F1020, F1030, F1050, F1060, F1070, F1080, and F1090 firewalls support this installation method.
To install the firewall in a standard 19-inch rack by using front and rear mounting brackets:
1. Wear an ESD wrist strap and make sure the wrist strap makes good skin contact and is reliably grounded.
2. Unpack the firewall and accessories.
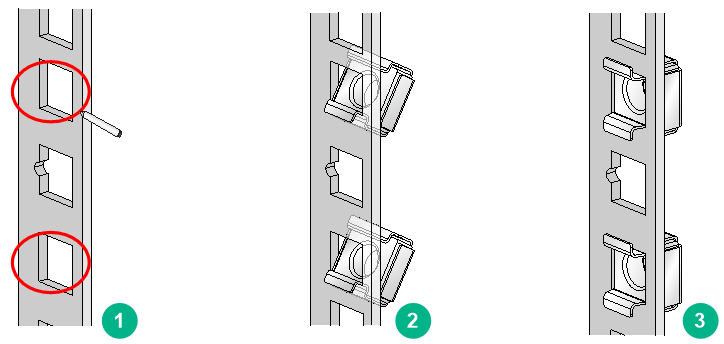
3. Mark the cage nut installation positions on the rack posts by using the mounting brackets.
Use a front mounting bracket to mark the positions on the front rack posts and use a rear mounting bracket to mark the positions on the rear rack posts.
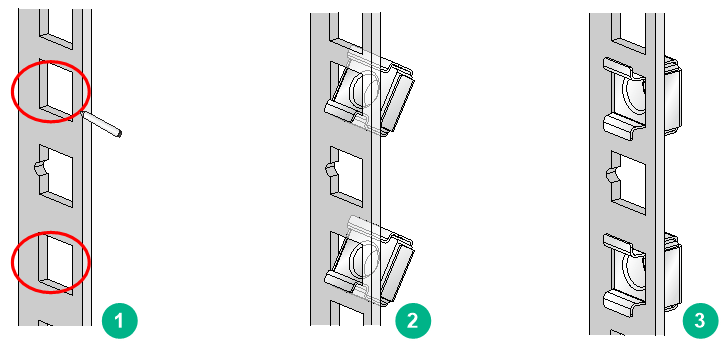
4. Install cage nuts.
Figure2-2 Installing cage nuts
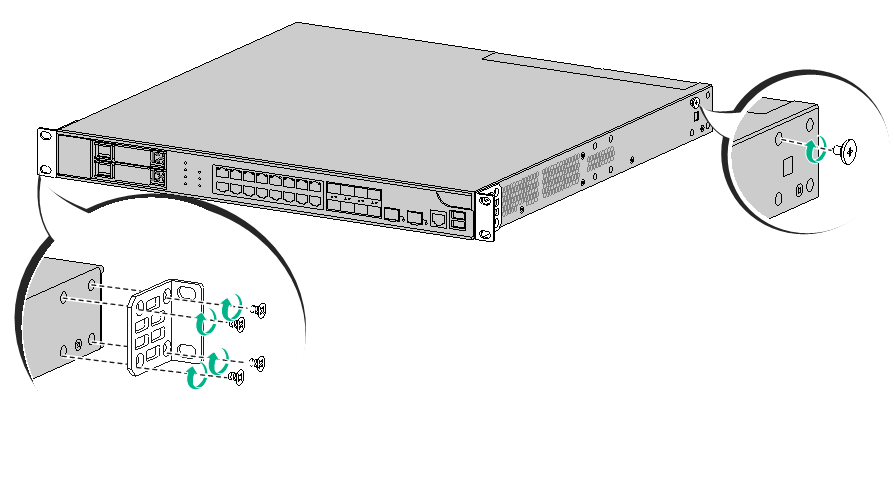
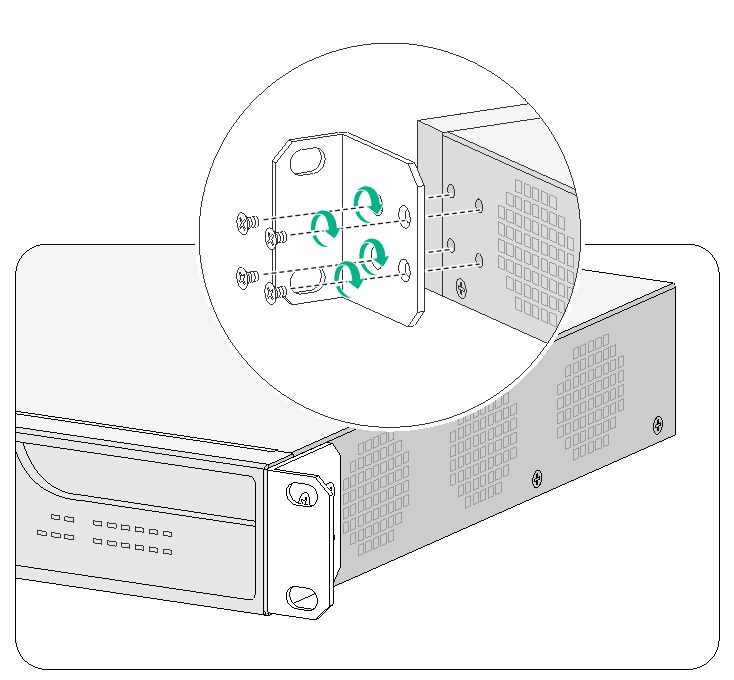
5. Attach the front mounting brackets and shoulder screws to both sides of the firewall with M4 screws provided with the firewall.
Figure2-3 Attaching mounting brackets and shoulder screws to the firewall
6. Attach the rear mounting brackets to the rear rack posts. The rear mounting brackets can be attached to the rear rack posts with the wide flange inside or outside the rack.
Table2-2 Installation methods for rear mounting brackets
|
Distance between the front and rear rack posts |
Rear mounting bracket installation method |
|
405 to 569 mm (15.94 to 22.40 in) |
With the wide flange inside the rack. |
|
247 to 411 mm (9.72 to 16.18 in) |
With the wide flange outside the rack. Caution: To prevent the rear mounting brackets from obstructing the closing of the rack door, ensure a distance greater than 153 mm (6.02 in) between the rear rack posts and the interior side of the rack door. |
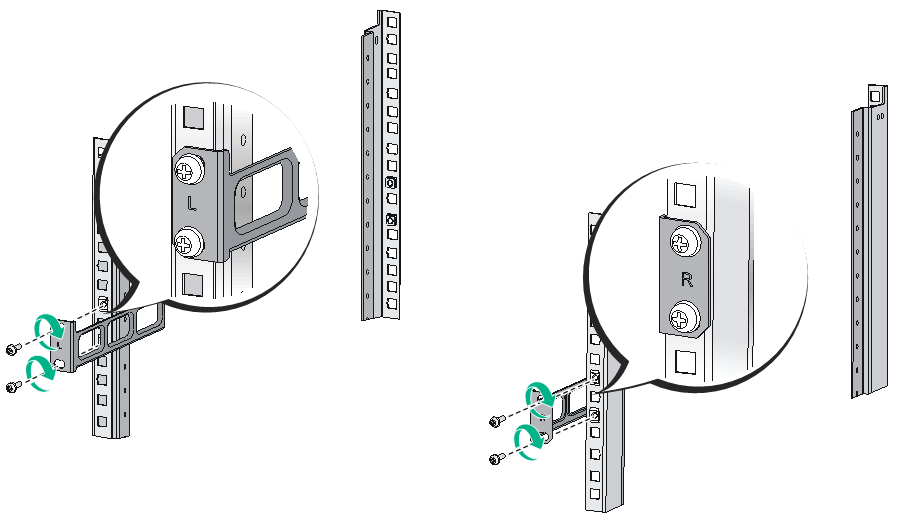
Figure2-4 Attaching the rear mounting brackets (with the wide flange inside the rack)
Figure2-5 Attaching the rear mounting brackets (with the wide flange outside the rack)
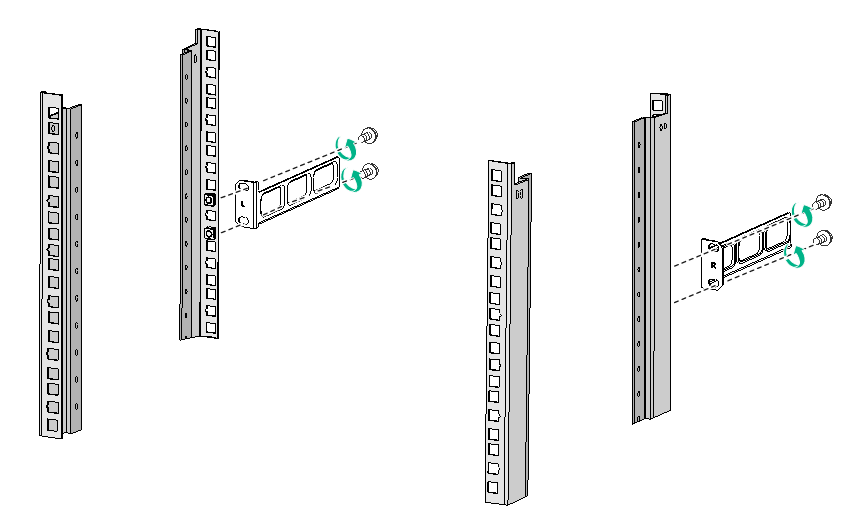
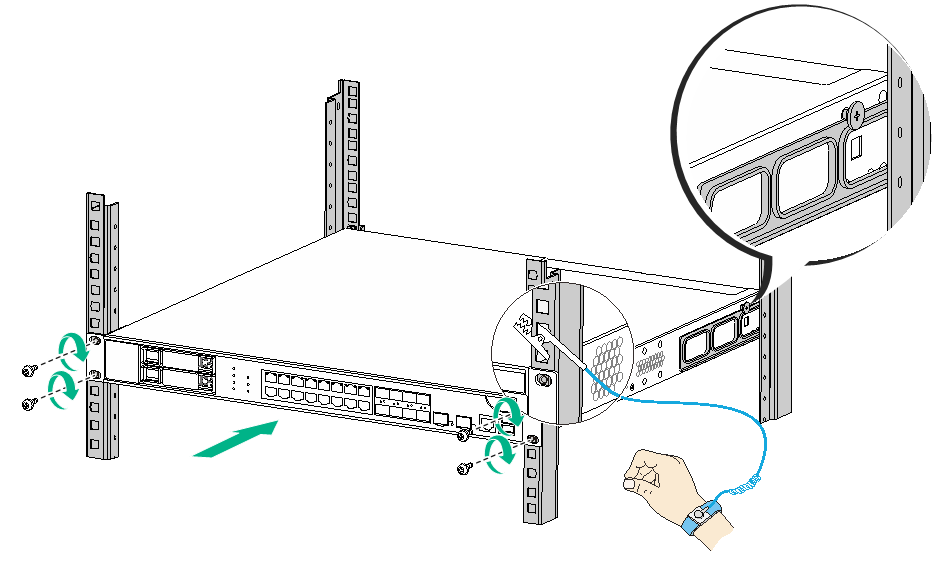
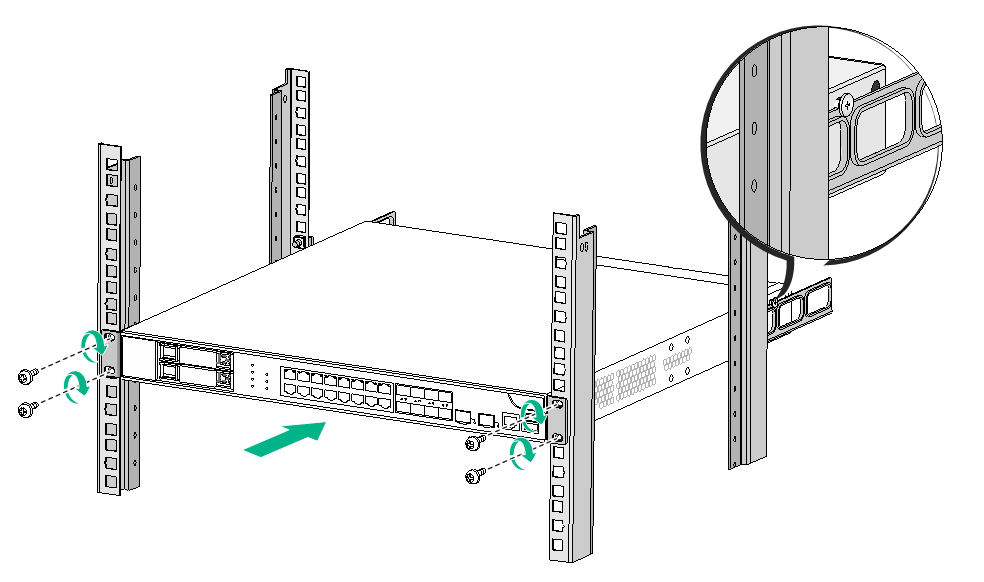
7. Mount the firewall in the rack. Use M6 screws to secure the mounting brackets to the front rack posts and make sure the shoulder screws rest firmly on the upper edge of the rear mounting brackets.
Figure2-6 Mounting the firewall in the rack (with the wide flange of the rear mounting brackets inside the rack)
Figure2-7 Mounting the firewall in the rack (with the wide flange of the rear mounting brackets outside the rack)
Rack-mounting the firewall by using front mounting brackets
The F1005 and F1010 firewalls support this installation method.
To install the firewall in a standard 19-inch rack by using front mounting brackets:
1. Wear an ESD wrist strap and make sure the wrist strap makes good skin contact and is reliably grounded.
2. Unpack the firewall and accessories.
3. Mark the cage nut installation positions on the rack posts by using the mounting brackets.
4. Install cage nuts.
Figure2-8 Installing cage nuts
5. Attach the front mounting brackets to both sides of the firewall with M4 screws provided with the firewall.
Figure2-9 Attaching the front mounting brackets to the firewall
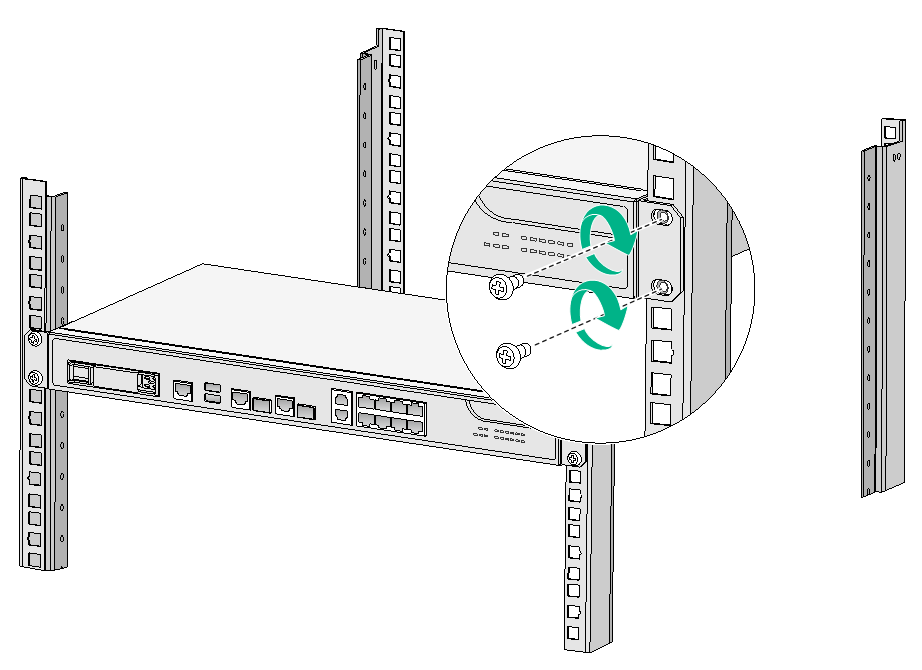
6. Mount the firewall in the rack. Use M6 screws to secure the mounting brackets to the front rack posts.
Figure2-10 Mounting the firewall in the rack
Grounding the firewall
|
WARNING! · Correctly connecting the firewall grounding cable is crucial to lightning protection and EMI protection. · Do not connect the firewall grounding cable to a fire main or lightning rod. |
You can ground the firewall in one of the following ways, depending on the grounding conditions available at the installation site.
Grounding the firewall with a grounding strip
If a grounding strip is available at the installation site, connect the grounding cable through the grounding strip.
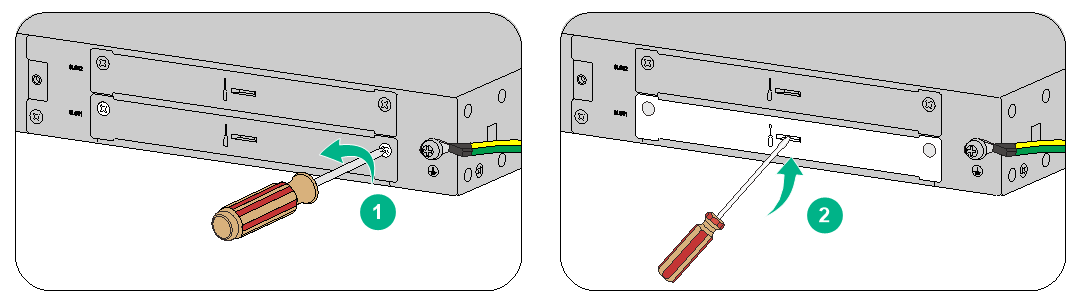
To connect the grounding cable:
1. Remove the grounding screw from the firewall chassis.
2. Attach the grounding screw to the ring terminal of the grounding cable.
3. Use a Phillips screwdriver to fasten the grounding screw into the grounding hole on the firewall.
4. Remove the hex nut from the grounding strip.
5. Use a pair of needle-nose pliers to bend a hook at the other end of the grounding cable. Attach the hook to the grounding point, and secure the hook with a screw.
Figure2-11 Grounding the firewall with a grounding strip
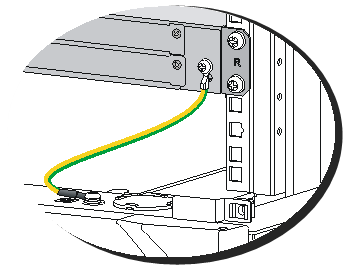
Grounding the firewall with the grounding terminal on the rack
1. Remove the grounding screw from the firewall chassis.
2. Attach the grounding screw to the ring terminal of the grounding cable.
3. Use a Phillips screwdriver to fasten the grounding screw into the grounding hole on the firewall.
4. Remove the grounding screw from the grounding point on the rack.
5. Use a pair of needle-nose pliers to bend a hook at the other end of the grounding cable. Attach the hook to the grounding point, and secure the hook with the screw.
Figure2-12 Grounding the firewall with the grounding terminal on the rack
Installing power modules
|
CAUTION: · Make sure the power module is powered off and the grounding cable is correctly connected before installation. · Do not install both AC and DC power modules on the same firewall. · Only the F1070, F1080, and F1090 firewalls support removable power modules. |
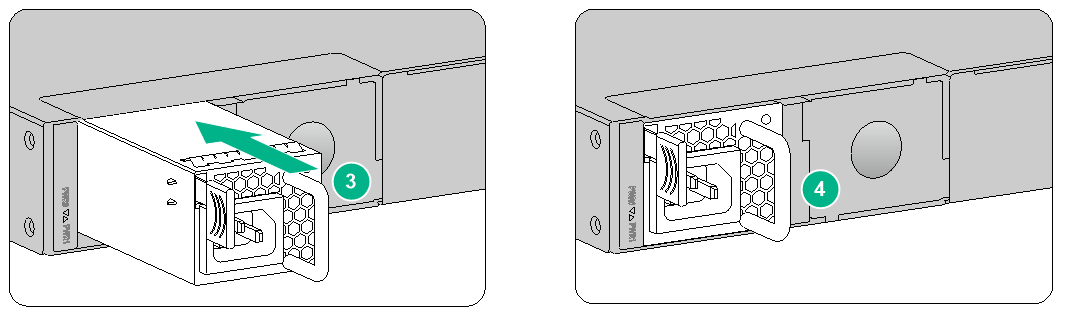
Installing a power module for an F1070 or F1080 firewall
The installation procedures for AC and DC power modules are similar. The following procedure installs an AC power module.
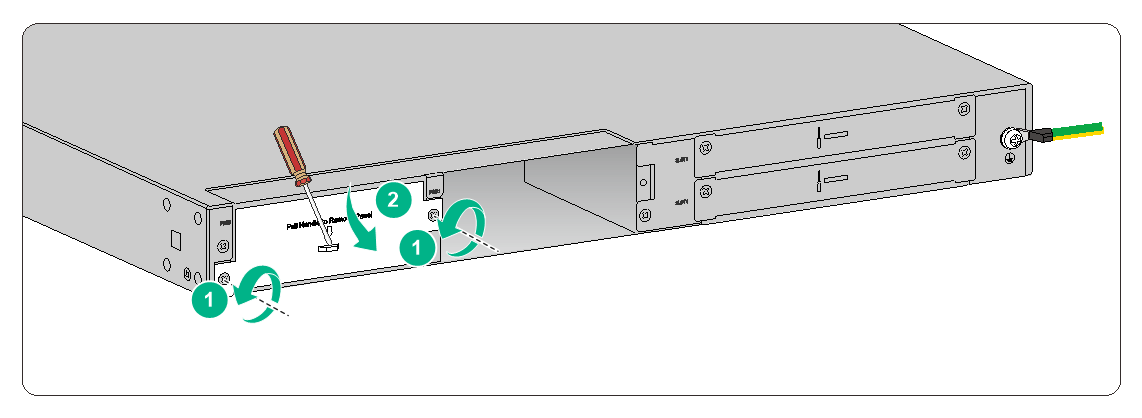
To install a power module for an F1070 or F1080 firewall:
1. Remove the filler panel (if any) from the target power module slot.
Figure2-13 Removing the filler panel from an F1070 or F1080 firewall
The firewall comes with the PWR1 slot empty and the PWR0 slot installed with a filler panel.
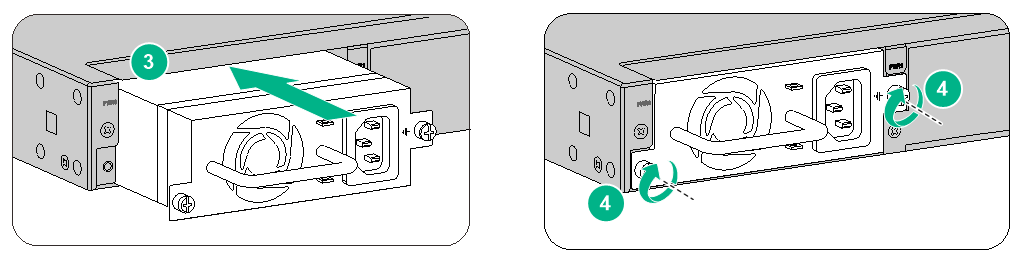
2. Orient the power module with its handle at the left. Holding the handle of the module with one hand and supporting the module bottom with the other, slide the power module slowly into the slot along the guide rails.
3. Use a Phillips screwdriver to fasten the captive screws on the power module to secure the power module in place.
Figure2-14 Installing a power module for an F1070 or F1080 firewall
Installing a power module for an F1090 firewall
The installation procedures for AC and DC power modules are similar. The following procedure installs an AC power module.
To install a power module for an F1090 firewall:
1. Remove the filler panel (if any) from the target power module slot.
Figure2-15 Removing the filler panel from an F1090 firewall
The firewall comes with the PWR1 slot empty and the PWR0 slot installed with a filler panel.
2. Orient the power module with its handle at the right. Holding the handle of the module with one hand and supporting the module bottom with the other, slide the power module slowly into the slot along the guide rails.
Figure2-16 Installing a power module for an F1090 firewall
Installing an interface module
|
CAUTION: · Do not hot swap interface modules. · To install two or more interface modules, use the upper interface module slots as a best practice. If you have installed an interface module in a lower slot, you must press down the ejector levers of the interface module while inserting it into an upper slot. |
The F1005 and F1010 do not support interface modules.
No interface modules are provided with the firewall. Purchase them as needed.
The installation procedure is the same for all interface modules.
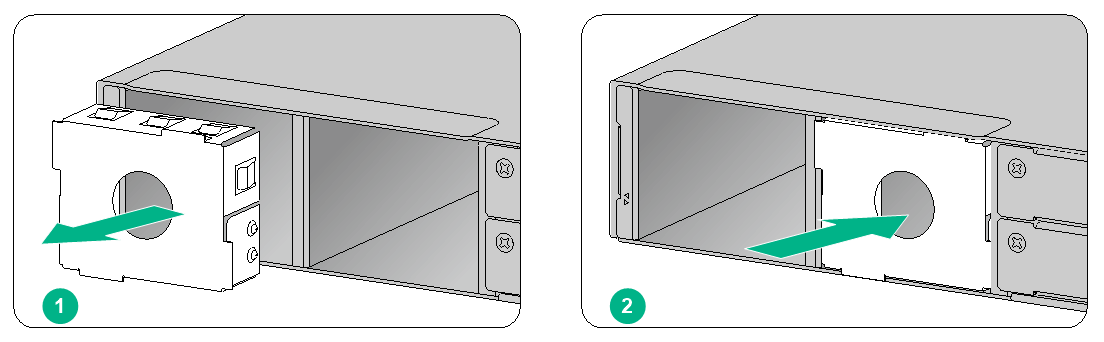
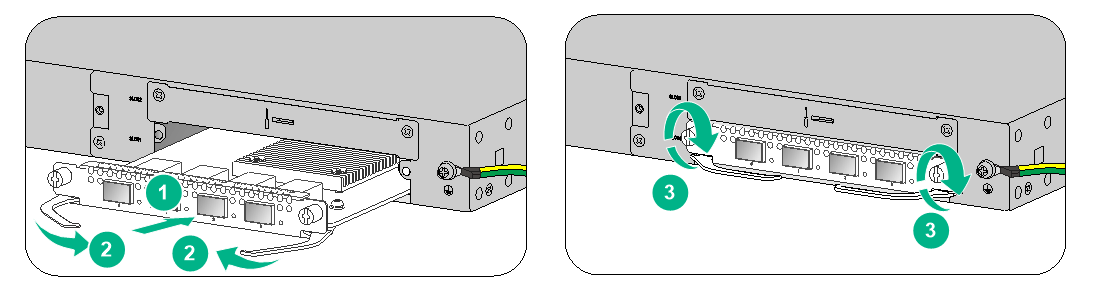
To install an interface module:
1. Face the rear panel of the firewall.
2. Use a Phillips screwdriver to remove the screws on the filler panel and then remove the filler panel.
Keep the filler panel for future use.
Figure2-17 Removing the filler panel
3. Pull the ejector levers on the module outward and slide the module slowly into the slot along the guide rails.
4. Press the ejector levers inward until they touch the panel tightly and the module seats into the slot securely.
5. Use a Phillips screwdriver to fasten the captive screws on the module.
Figure2-18 Installing an interface module
Installing a drive
|
CAUTION: · Do not hot swap drives. · To avoid damage to drives, always hold a drive by its sides. Do not touch any components and do not squeeze, vibrate, or strike a drive. · Install a filler panel in empty drive slots to prevent dust and ESD damage. · Before using a drive, execute the fdisk and format commands from the CLI to partition and format the drive. |
The device does not come with any drives and cannot recognize drives from other vendors. Purchase drives from H3C as needed.
To install a drive:
1. Wear an ESD wrist strap and make sure it makes good skin contact and is reliably grounded.
2. Remove the filler panel from the drive slot.
3. Press the button on the drive panel to release the locking lever.
4. Hold the locking lever and push the drive into the slot slowly along the guide rails. Then close the locking lever.
Figure2-19 Installing a drive
Connecting Ethernet cables
Connecting a copper Ethernet port
You can use either a straight-through or a cross-over network cable. For more information about Ethernet twisted pair cables, see "Ethernet twisted pair cable."
To connect a copper Ethernet port:
1. Connect one end of the Ethernet cable to the copper Ethernet port of the firewall, and the other end to the Ethernet port of the peer device.
2. Examine whether the LEDs of the Ethernet port are normal. For more information about LEDs, see "Appendix B LEDs."
After connecting the firewall to the network, you can use the ping or tracert command to examine network connectivity. For more information, see the related command reference.
Connecting a fiber port
|
WARNING! Disconnected optical fibers or transceiver modules might emit invisible laser light. Do not stare into beams or view directly with optical instruments when the firewall is operating. |
|
CAUTION: · Never bend or curve a fiber excessively. The bend radius of a fiber must be not less than 100 mm (3.94 in). · Keep the fiber end clean. · Make sure the fiber connector matches the transceiver module. · Before connecting a fiber, make sure the optical power at the receiving end does not exceed the transceiver module's upper threshold of the optical receive power. If the optical power at the receiving end exceeds the threshold, the transceiver module might be damaged. · Do not install a transceiver module connected with a fiber into a fiber port. To connect an optical fiber, first install the transceiver module in the fiber port and then connect the fiber. · Insert a dust plug into any open fiber port. · Make sure the Tx and Rx ports on a transceiver module are connected to the Rx and Tx ports on the peer end, respectively. |
The firewall supports GE SFP transceiver modules and 10GE SFP+ transceiver modules. For the transceiver module specifications, see "GE fiber Ethernet port" and "10 GE fiber Ethernet port."
No transceiver module is provided with the firewall. As a best practice, use H3C transceiver modules.
Figure2-20 GE SFP transceiver module
Figure2-21 10GE SFP+ transceiver module
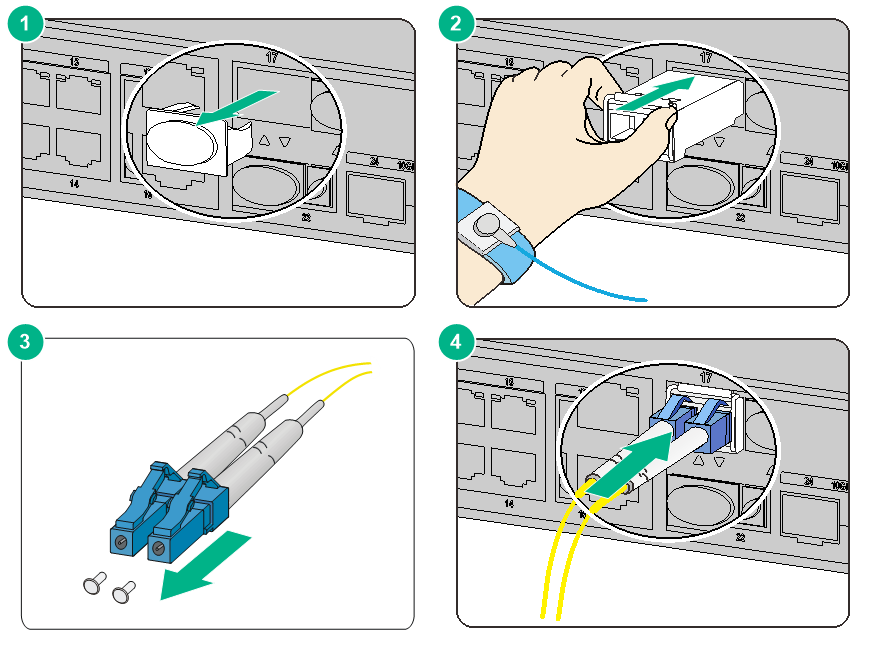
To connect the firewall to the network through an optical fiber:
1. Remove the dust plug from the fiber port.
2. Remove the dust cap from the transceiver module and insert it into the fiber port.
3. Remove the dust cap of the optical fiber connector, and use dust free paper and absolute alcohol clean the end face of the fiber connector.
4. Identify the Rx and Tx ports on the transceiver module. Plug one end of the optical fiber into the transceiver module in the firewall, and plug the other end into the transceiver module in the peer device.
Make sure the Rx port and the Tx port are connected to the Tx port and the Rx port on the peer device, respectively.
Figure2-22 Installing and connecting an optical fiber
Connecting power cords
|
CAUTION: Make sure the grounding cable of the firewall is correctly connected and the power source is powered off before connecting the power cord. |
Connecting an AC power cord
Connecting an AC power cord for an F1005 or F1010 firewall
1. Attach the hooks of the power cord retainer clip into the holes on the top of the AC-input power receptacle, and pull the power cord retainer clip upwards.
2. Connect one end of the AC power cord to the AC-input power receptacle on the firewall.
3. Pull the power cord retainer clip downwards and secure the connector to the power receptacle.
4. Connect the other end of the power cord to an AC power source.
Figure2-23 Connecting an AC power cord for an F1005 or F1010 firewall
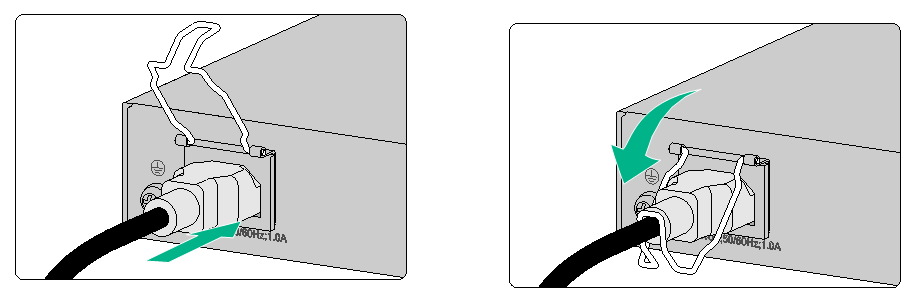
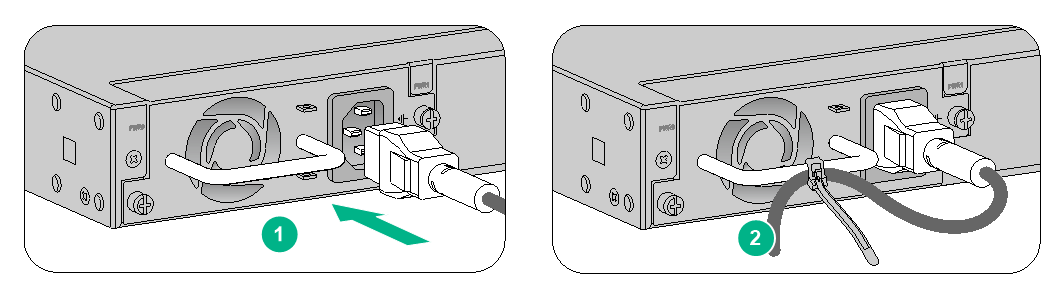
Connecting an AC power cord for an F1020, F1030, F1050, or F1060 firewall
1. Connect the connector of the AC power cord to the target AC power receptacle on the rear panel of the chassis. Then use a power cord retainer clip (see Figure2-24) or a cable tie (see Figure2-25) to secure the power cord.
2. Connect the other end of the power cord to an AC power source.
Figure2-24 Connecting an AC power cord (using a power cord retainer clip to secure the power cord)
Figure2-25 Connecting an AC power cord (using a cable tie to secure the power cord)
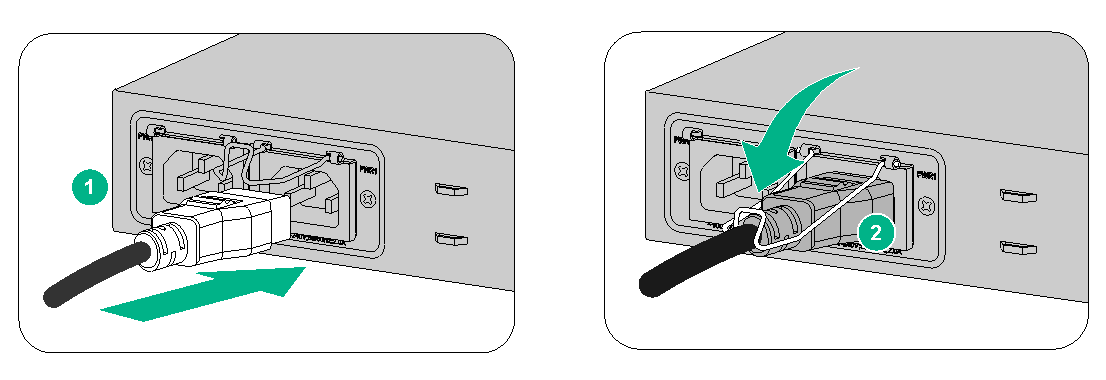
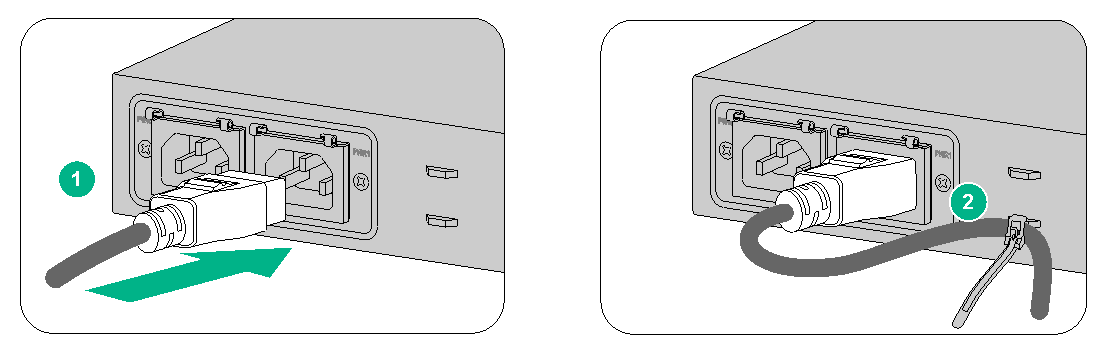
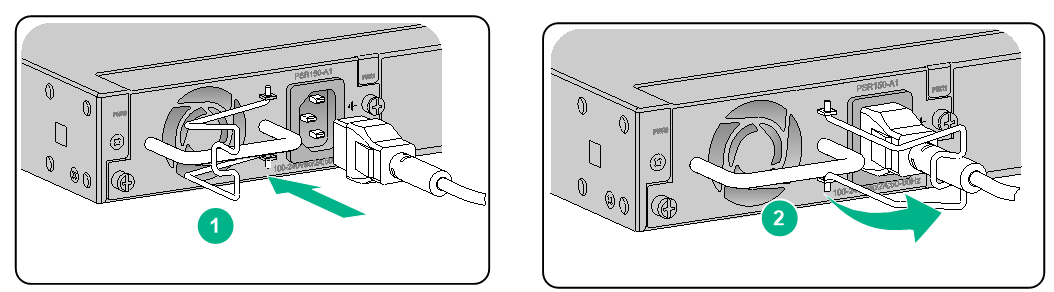
Connecting an AC power cord for an F1070 or F1080 firewall
1. Connect the connector of the AC power cord to the AC power receptacle on the rear panel of the chassis. Then use a power cord retainer clip (see Figure2-26) or a cable tie (see Figure2-27) to secure the power cord.
2. Connect the other end of the power cord to an AC power source.
Figure2-26 Connecting an AC power cord (using a power cord retainer clip to secure the power cord)
Figure2-27 Connecting an AC power cord (using a cable tie to secure the power cord)
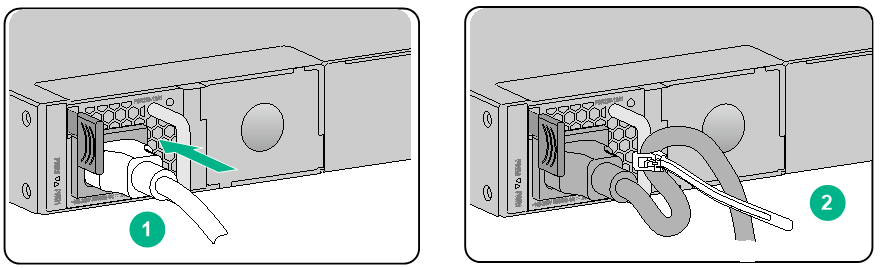
Connecting an AC power cord for an F1090 firewall
1. Connect the female connector of the AC power cord to the AC-input power receptacle on the power module.
2. Use a cable tie to secure the AC power cord to the power module handle.
3. Connect the other end of the power cord to an AC power source.
Figure2-28 Connecting an AC power cord for an F1090 firewall
Connecting a DC power cord
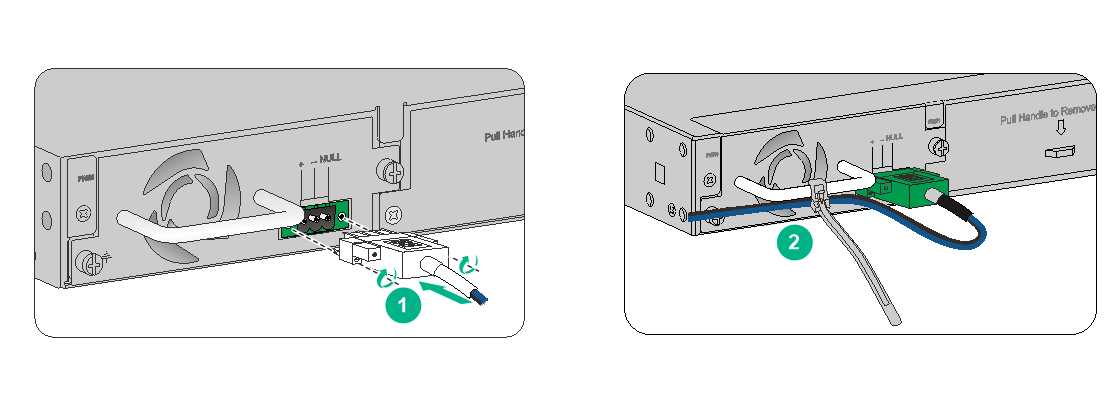
Connecting a DC power cord for an F1070, F1080, or F1090 firewall
1. Correctly orient the DC power cord connector with the power receptacle on the power module, and insert the connector into the receptacle.
The receptacle is foolproof. If you cannot insert the connector into the receptacle, re-orient the connector rather than use excessive force to push it in.
2. Fasten the captive screws on the power cord connector with a flathead screwdriver to secure the power cord connector.
3. Use a cable tie to secure the power cord to the handle.
4. Connect the other end of the power cord to a DC power source.
Figure2-29 Connecting a DC power cord for an F1070, F1080, or F1090 firewall
Connecting a high-voltage DC power cord for an F1090 firewall
Only the F1090 firewall supports high-voltage DC power cords.
The connection procedure is similar for high-voltage DC power cords and AC power cords. For information about connecting a high-voltage DC power cord, see "Connecting an AC power cord for an F1090 firewall."
Verifying the installation
Verify the following items to ensure correct installation:
· There is enough space for heat dissipation around the firewall.
· The firewall and its components are installed securely. The screws are fastened tightly.
· The power source specifications are as required by the firewall.
· The grounding cable and power cords are connected correctly.
3 Accessing the firewall
Starting the firewall
Check before starting the firewall
|
WARNING! Locate the emergency power-off switch in the room before powering on the firewall so you can quickly shut power off when an electrical accident occurs. |
Before powering on the firewall, verify that the following conditions are met:
· The power cord and grounding cable are correctly connected.
· The power source specifications meet the firewall requirements.
· The firewall is connected correctly to a configuration terminal (a PC for example). The configuration terminal has been started and the parameters have been set correctly. For more information, see "Logging in from the serial console port or micro USB console port."
· The interface modules (if any) are installed correctly.
Starting the firewall and observing the initial startup conditions
1. Turn on the circuit breakers to power on the firewall.
2. Observe the initial startup conditions to verify that the firewall starts up correctly.
¡ The LEDs on the front panel indicate that the device is operating correctly. For more information about LEDs, see "Appendix B LEDs."
¡ The fan blades are rotating and air is exhausted from the air outlet vents.
¡ The configuration terminal displays the following information:
System is starting...
Press Ctrl+D to access BASIC-BOOTWARE MENU...
Press Ctrl+T to start heavy memory test
Booting Normal Extended BootWare
The Extended BootWare is self-decompressing......Done.
****************************************************************************
* *
* H3C F1080 BootWare, Version 1.04 *
* *
****************************************************************************
Compiled Date : Sep 10 2014
CPU Type : xxx
CPU Clock Speed : 1000MHz
Memory Type : DDR3 SDRAM
Memory Size : 4096MB
Memory Speed : 1332MHz
BootWare Size : 768KB
Flash Size : 8MB
CPLD_A Version : 2.0
CPLD_B Version : 2.0
PCB Version : Ver.A
BootWare Validating...
Press Ctrl+B to access EXTENDED-BOOTWARE MENU...
Loading the main image files...
Loading file flash:/f1000fw-cmw710-system-E9308.bin.............................
........................Done.
Loading file flash:/f1000fw-cmw710-boot-E9308.bin.... Done.
Image file flash:/f1000fw-cmw710-boot-E9308.bin is self-decompressing.......
......................................................Done.
System image is starting...
Cryptographic Algorithms Known-Answer Tests are running ...
CPU 0 of slot 1 in chassis 0:
Starting Known-Answer tests in the user space.
Known-answer test for SHA1 passed.
Known-answer test for SHA224 passed.
Known-answer test for SHA256 passed.
Known-answer test for SHA384 passed.
Known-answer test for SHA512 passed.
Known-answer test for HMAC-SHA1 passed.
Known-answer test for HMAC-SHA224 passed.
Known-answer test for HMAC-SHA256 passed.
Known-answer test for HMAC-SHA384 passed.
Known-answer test for HMAC-SHA512 passed.
Known-answer test for AES passed.
Known-answer test for RSA(signature/verification) passed.
Known-answer test for RSA(encrypt/decrypt) passed.
Known-answer test for DSA(signature/verification) passed.
Known-answer test for random number generator passed.
Known-Answer tests in the user space passed.
Starting Known-Answer tests in the kernel.
Known-answer test for SHA1 passed.
Known-answer test for HMAC-SHA1 passed.
Known-answer test for AES passed.
Known-answer test for random number generator passed.
Known-Answer tests in the kernel passed.
Starting Known-Answer tests in the engine.
Known-answer test for SHA1 passed.
Known-answer test for HMAC-SHA1 passed.
Known-answer test for AES passed.
Known-answer test for RSA(signature/verification) passed.
Known-answer test for RSA(encrypt/decrypt) passed.
Known-answer test for DSA(signature/verification) passed.
Known-answer test for random number generator passed.
Known-Answer tests in the engine passed.
Cryptographic Algorithms Known-Answer Tests passed.
Line con0 is available.
Press ENTER to get started..
..
Press Enter to access user view of the firewall.
|
|
NOTE: To access the EXTENDED-BOOTWARE menu, press Ctrl + B within four seconds at the prompt "Press Ctrl+B to access EXTENDED-BOOTWARE MENU." If you do not press Ctrl+B at the prompt, the system starts to read and decompress program files. To enter the EXTENDED-BOOT menu afterwards, you need to reboot the device. |
Logging in to the firewall
You can use the following methods to access and manage the firewall. For more information about logging in to the firewall, see the configuration guides and command references for the firewall.
· Logging in from the Web interface
· Logging in from the serial console port or micro USB console port
Logging in from the Web interface
The default Web interface login information is as follows:
· Username—admin
· Password—admin
· IP address of the Ethernet management port GigabitEthernet 1/0/0 (0/MGMT)—192.168.0.1/24
To log in to the firewall from the Web interface by using the default account:
1. Use an Ethernet cable to connect a PC to the Ethernet management interface on the firewall.
2. Configure an IP address in subnet 192.168.0.0/24 for the PC. Make sure the PC and the firewall are reachable to each other.
The PC must use a different IP address than the Ethernet management interface.
3. Start a browser, enter 192.168.0.1 in the address bar, and press Enter.
4. Enter the default username admin and password admin and then click Login.
5. Modify the login information.
At the first login from the Web interface, change the password as required in the pop-up window, and then click OK.
Keep the new password secure.
Logging in from the serial console port or micro USB console port
|
CAUTION: · When you connect the console cable, identify the port marks and make sure you are connecting the correct ports. · The serial ports on PCs do not support hot swapping. To connect a PC to an operating firewall, first connect the PC end. To disconnect a PC from an operating firewall, first disconnect the firewall end. |
To access and manage the firewall locally, connect the serial console port or the micro USB console port on the firewall to a configuration terminal (a PC for example). Only the micro USB console port is available if you connect both the serial console port and micro USB console port.
By default, the firewall uses the scheme access authentication mode. The username and password are both admin.
To configure and manage the firewall through the serial console port or micro USB console port, you must run a terminal emulator program, TeraTermPro or PuTTY, on your configuration terminal and configure the following settings for the terminal. For more information about the terminal emulator programs, see the user guides for these programs.
· Bits per second—9600.
· Data bits—8.
· Stop bits—1.
· Parity—None.
· Flow control—None.
Logging in through Telnet
1. Log in to the firewall through the serial console port or micro USB console port, and enable the Telnet function in system view by using the telnet server enable command.
2. Enter VTY user line view, and configure the authentication mode, user role, and common properties in VTY user line view.
By default, the authentication mode is scheme, and the username and password are admin.
3. Connect a PC to the Ethernet management port GigabitEthernet 1/0/0 (0/MGMT) on the firewall.
4. Specify an IP address for the network port of the PC. The IP address must be in subnet 192.168.0.0/24 and cannot be 192.168.0.1.
5. Run the Telnet client on the PC and enter the default login information.
4 Hardware replacement
|
CAUTION: Wear an ESD wrist strap or ESD gloves for hardware maintenance. They are not provided with the firewall. Prepare them yourself. |
Replacing a power module
|
CAUTION: · Before you replace a power module, turn off the circuit breaker and remove the power cord. · Before hot swapping a power module, make sure another power module is operating correctly on the firewall. |
This section applies only to F1070, F1080, and F1090 firewalls that support removable power modules.
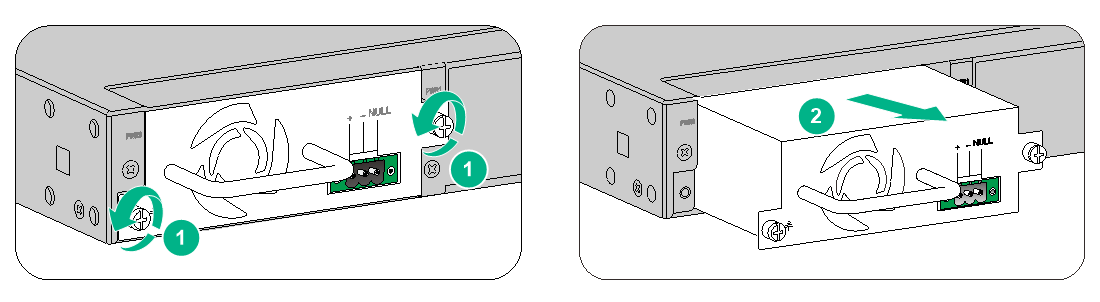
Replacing a power module for an F1070 or F1080 firewall
The replacement procedure is the same for an AC power module and a DC power module. This section takes a DC power module as an example.
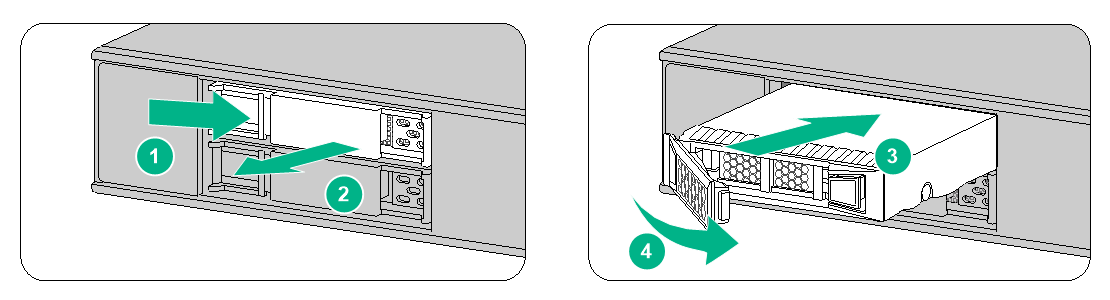
To replace a power module for an F1070 or F1080 firewall:
1. Face the rear panel of the firewall.
2. Use a Phillips screwdriver to loosen the captive screw of the power module.
3. Hold the power module with one hand and pull the power module part way out of the slot.
4. Supporting the bottom of the power module with the other hand, gently pull the power module out of the slot along the slide rails.
Figure4-1 Removing a power module from an F1070 or F1080 firewall
5. Put the removed power module on a workbench or into an antistatic bag.
6. Install a new power module. If you do not install a new power module in the slot, install a filler panel. For the installation procedure, see "Installing power modules."
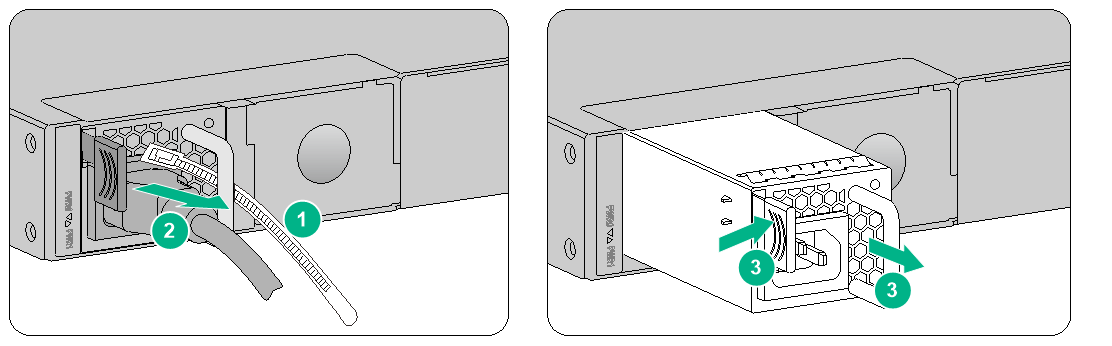
Replacing a power module for an F1090 firewall
The replacement procedure is the same for an AC power module and a DC power module. This section takes an AC power module as an example.
To replace a power module for an F1090 firewall:
1. Face the rear panel of the firewall.
2. Remove the cable tie from the power cord and then remove the power cord connector from the power module.
3. Hold the power module handle with one hand, press the latch towards the handle, and then pull the power module part way out of the slot. Supporting the power module bottom with one hand, slowly pull the power module out of the slot along the guide rails with the other.
4. Put the removed power module in an antistatic bag or on the workbench.
5. Install a new power module. For the installation procedure, see "Installing a power module for an F1090 firewall."
If you are not to install a new power module, install a filler panel in the slot to ensure good ventilation in the firewall.
Figure4-2 Removing a power module from an F1090 firewall
Replacing an interface module
|
CAUTION: · Do not hot swap interface modules. Power off the firewall before you replace an interface module. · To install two or more interface modules, use the upper interface module slots as a best practice. If you have installed an interface module in a lower slot, you must press down the ejector levers of the interface module while inserting it into an upper slot. |
The F1005 and F1010 firewalls do not support interface modules.
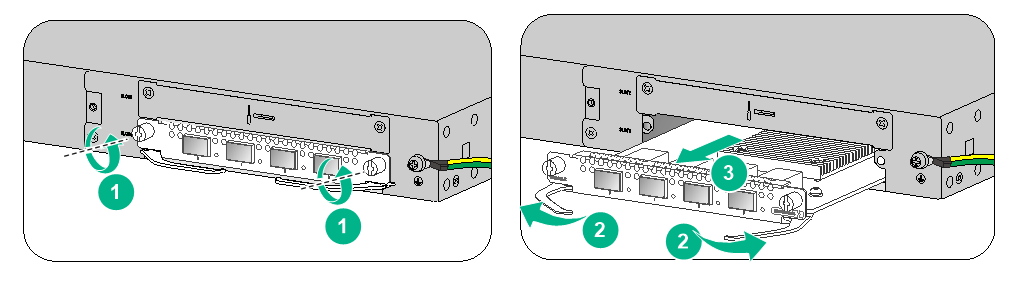
To replace an interface module:
1. Power off the firewall.
2. Use a Phillips screwdriver to loosen the captive screws of the interface module.
3. Holding the ejector levers of the interface module with both hands, pull the ejector levers outward, and pull the interface module part way out of the slot along the slide rails. Supporting the bottom of the interface module with one hand, gently pull the interface module out of the slot with the other.
4. Put the removed interface module (with the circuit board facing upward) on an antistatic workbench or into an antistatic bag.
5. Install a new interface module. For the installation procedure, see "Installing an interface module."
If you are not to install a new interface module, install a filler panel in the slot to ensure good ventilation in the firewall.
Figure4-3 Removing an interface module
Replacing a drive
|
CAUTION: · To avoid storage medium damage, execute the umount command from the CLI to unmount all partitions before removing a drive. · Do not hot swap drives. |
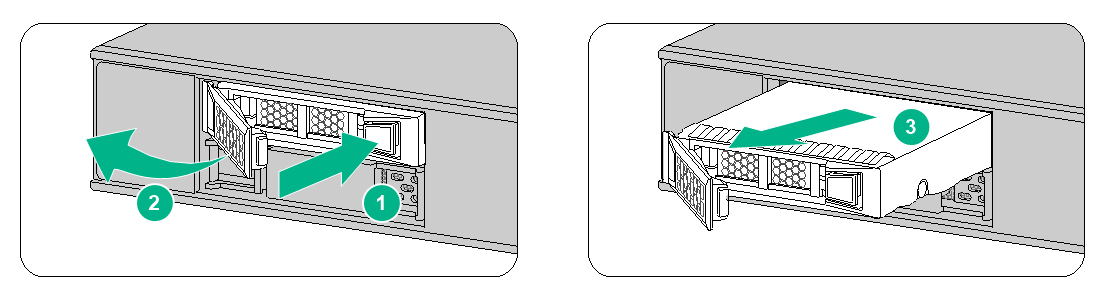
To replace a drive:
1. Log in to the Web interface. Click the Unmount button on the Storage settings page.
2. Wear an ESD wrist strap and make sure it makes good skin contact and is reliably grounded.
3. Press the button at the right side of the drive panel to release the locking lever.
4. Hold the locking lever and pull the drive out of the slot.
5. Install a new drive. For the installation procedure, see "Installing a drive."
Figure4-4 Removing a drive
Replacing a transceiver module
|
WARNING! Disconnected optical fibers or transceiver modules might emit invisible laser light. Do not stare into beams or view directly with optical instruments when the firewall is operating. |
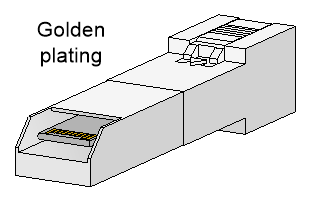
When you replace a transceiver module, make sure the two transceiver modules connected by the same optical fiber are the same type. Do not touch the golden plating of the transceiver module.
Figure4-5 Transceiver module golden plating
To replace a transceiver module:
1. Use the shutdown command in interface view at the CLI to shut down the optical source before you remove the fiber connector.
2. Remove the LC connectors with the optical fiber from the transceiver module, and install dust caps to the LC connectors.
3. Pivot the clasp of the transceiver module down to the horizontal position, and gently pull the transceiver module out.
Figure4-6 Removing the transceiver module
4. Install dust caps to the removed transceiver module, and put it into the package.
5. Install a new transceiver module. If you do not install a new transceiver module in the slot, install a dust cap. For information about installing a transceiver module, see "Connecting a fiber port."
5 Hardware management and maintenance
|
|
NOTE: The output depends on your firewall model. For more information about the commands used in this chapter, see the configuration guides and command references for the firewall. |
Displaying detailed information about the firewall
Use the display device verbose command to display detailed information, including the running status and hardware version, about the firewall and its interface modules.
<Sysname> display device verbose
Status : Normal
Type : F1080
PCB 1 Ver : VER.A
Software Ver : 9313P11
CPU Ver : 1.0
CPLD_A : 1.0
CPLD_B : 1.0
CFCard Num : 0
Displaying the software and hardware version information for the firewall
Use the display version command to display software and hardware version information for the firewall.
H3C Comware Software, Version 7.1.064, Release 9313P11
Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.
H3C SecPath F1080 uptime is 0 weeks, 0 days, 2 hours, 23 minutes
Last reboot reason: User reboot
Boot image: flash:/f1000fw-cmw710-boot- R9313P11.bin
Boot image version: 7.1.064, Release 9313P11
Compiled Nov 29 2016 16:00:00
System image: flash:/f1000fw-cmw710-system-R9313P11.bin
System image version: 7.1.064, Release 9313P11
Compiled Nov 29 2016 16:00:00
SLOT 1
CPU type: Multi-core CPU
DDR3 SDRAM Memory 16382M bytes
Board PCB Version:Ver.A
CPLD_A Version: 1.0
CPLD_B Version: 1.0
Basic BootWare Version: 1.05
Extend BootWare Version: 1.05
Board PFC Version:Ver.A
NandFlash PCB Version:Ver.A
HD PCB Version:Ver.A
[SubSlot 0]16GE+8SFP+2XGE (Hardware)Ver.A, (Driver)1.0, (Cpld)1.0
Displaying the electrical label information for the firewall
Use the display device manuinfo command to display the electrical label information for the firewall.
<Sysname> display device manuinfo
Slot 1 CPU 0:
DEVICE_NAME : SecPath F1080
DEVICE_SERIAL_NUMBER : 210235A1FXH164000026
MAC_ADDRESS : 487A-DA95-91BB
MANUFACTURING_DATE : 2016-04-29
VENDOR_NAME : H3C
Fan 0:
The operation is not supported on the specified fan.
Fan 1:
The operation is not supported on the specified fan.
Fan 2:
The operation is not supported on the specified fan.
Fan 3:
The operation is not supported on the specified fan.
Power 1:
The operation is not supported on the specified power.
Table5-1 Output description
|
Field |
Description |
|
DEVICE_NAME |
Firewall name. |
|
DEVICE_SERIAL_NUMBER |
Firewall serial number. |
|
MAC_ADDRESS |
MAC address of the firewall. |
|
MANUFACTURING_DATE |
Manufacturing date of the firewall. |
|
VENDOR_NAME |
Vendor name. |
Displaying the CPU usage of the firewall
Use the display cpu-usage command to display the CPU usage of the firewall.
<Sysname> display cpu-usage
Slot 1 CPU 0 CPU usage:
3% in last 5 seconds
3% in last 1 minute
3% in last 5 minutes
Table5-2 Output description
|
Field |
Description |
|
Slot 1 CPU 0 CPU usage |
CPU 0 usage information for the interface module in slot 1. |
|
3% in last 5 seconds |
Average CPU usage in the last 5 seconds. (After the firewall boots, the firewall calculates and records the average CPU usage at the interval of 5 seconds.) |
|
3% in last 1 minute |
Average CPU usage in the last minute. (After the firewall boots, the firewall calculates and records the average CPU usage at the interval of 1 minute.) |
|
3% in last 5 minutes |
Average CPU usage in the last 5 minutes. (After the firewall boots, the firewall calculates and records the average CPU usage at the interval of 5 minutes.) |
Displaying the memory usage of the firewall
Use the display memory command to display the memory information of the firewall.
The statistics about memory is measured in KB:
Slot 1:
Total Used Free Shared Buffers Cached FreeRatio
Mem: 1718140 921604 796536 0 1108 187644 46.4%
-/+ Buffers/Cache: 732852 985288
Swap: 0 0 0
Table5-3 Output description
|
Field |
Description |
|
Slot |
Slot number of the interface module |
|
Mem |
Memory usage information. |
|
Total |
Total size of the physical memory space that can be allocated. The memory space is virtually divided into two parts. Part 1 is used for kernel codes, kernel management, and ISSU functions. Part 2 can be allocated and used for such tasks as running service modules and storing files. The size of part 2 equals the total size minus the size of part 1. |
|
Used |
Used physical memory. |
|
Free |
Free physical memory. |
|
Shared |
Physical memory shared by processes. |
|
Buffers |
Physical memory used for buffers. |
|
Cached |
Physical memory used for caches. |
|
FreeRatio |
Free memory ratio. |
|
-/+ Buffers/Cache |
-/+ Buffers/Cache:used = Mem:Used – Mem:Buffers – Mem:Cached, which indicates the physical memory used by applications. -/+ Buffers/Cache:free = Mem:Free + Mem:Buffers + Mem:Cached, which indicates the physical memory available for applications. |
|
Swap |
Swap memory. |
Displaying the operational status of power modules
Use the display power command to display the operational status of power modules.
<Sysname> display power
Power 0 Status: Normal
Power 1 Status: Absent
Table5-4 Output description
|
Field |
Description |
|
Power |
Number of the power module. |
|
Status |
Power module state: · Normal—The power module is operating correctly. · Absent—The power module is not in position. · Abnormal—The power module has failed. |
Displaying the temperature information of the firewall
|
IMPORTANT: Only F1020, F1030, F1050, F1060, F1070, F1080, and F1090 firewalls support the display environment command. |
Use the display environment command to display the temperature information of the firewall.
<Sysname> display environment
System Temperature information (degree centigrade):
--------------------------------------------------------------------------------
---------
Sensor Temperature LowerLimit Warning-UpperLimit Alarm-UpperLimit Shutdown-U
pperLimit
inflow 1 26 -5 48 56 NA
Table5-5 Output description
|
Field |
Description |
|
Sensor |
Temperature sensor: · inflow—Air inlet vent temperature sensor. · outflow—Air outlet vent temperature sensor. · hotspot—Hotspot temperature sensor. |
|
Temperature |
Current temperature. |
|
LowerLimit |
Low temperature alarm threshold. |
|
Warning-UpperLimit |
Warning-level high temperature alarm threshold. |
|
Alarm-UpperLimit |
Alarm-level high temperature alarm threshold. |
|
Shutdown-Upperlimit |
Shutdown-level high temperature alarm threshold. The firewall automatically powers off when the temperature exceeds this threshold. |
Displaying the operational statistics of the firewall
When you perform routine maintenance or the system fails, you might need to view the operational information of each functional module for locating failures. Typically you need to run display commands one by one. To collect more information one time, you can execute the display diagnostic-information command in any view to display or save the operational statistics of multiple functional modules of the firewall.
· Save the operational statistics of each functional module of the firewall:
<Sysname> display diagnostic-information
Save or display diagnostic information (Y=save, N=display)? [Y/N]:y
Please input the file name(*.gz)[flash:/diag.gz]:
Diagnostic information is outputting to flash:/diag.gz.
Please wait...
Save successfully.
To view the diag.gz file:
a. Execute the gunzip diag.gz command in user view to decompress the file.
b. Execute the more diag command.
c. Press Pg Up and Pg Down.
· Display the operational statistics for each functional module of the firewall:
<Sysname> display diagnostic-information
<Sysname>display diagnostic-information
Save or display diagnostic information (Y=save, N=display)? [Y/N]:n
===============================================
===============display cpu===============
Slot 1 CPU 0 CPU usage:
13% in last 5 seconds
13% in last 1 minute
13% in last 5 minutes
...
Displaying transceiver module information
Identifying transceiver modules
To identify transceiver modules, you can use the following command to view the key parameters of the transceiver modules, including transceiver module type, connector type, central wavelength of the laser sent, transmission distance, and vendor name or name of the vendor who customizes the transceiver modules.
To display transceiver module information:
|
Task |
Command |
Remarks |
|
Display key parameters of the transceiver module in a specific interface. |
display transceiver interface [ interface-type interface-number ] |
Available for all transceiver modules. |
Troubleshooting transceiver modules
The system outputs alarm information for you to locate and troubleshoot faults of transceiver modules.
To display the alarming information or fault detection parameters of a transceiver module:
|
Task |
Command |
Remarks |
|
Display the current alarm information of the transceiver module in a specific interface. |
display transceiver alarm interface [ interface-type interface-number ] |
Available for all transceiver modules. |
Rebooting the firewall
|
CAUTION: · If the main system software image file does not exist, do not use the reboot command to reboot the firewall. Specify the main system software image file first, and then reboot the firewall. · The precision of the rebooting timer is 1 minute. 1 minute before the rebooting time, the firewall prompts "REBOOT IN ONE MINUTE" and reboots in one minute. · If you are performing file operations when the firewall is to be rebooted, the system does not execute the reboot command for security. |
To reboot a firewall, use one of the following methods:
· Use the reboot command to reboot the firewall immediately.
· Enable the scheduled reboot function at the CLI. You can set a time at which the firewall can automatically reboot, or set a delay so that the firewall can automatically reboot within the delay.
· Power on the firewall after powering it off, which is also called hard reboot or cold start. H3C does not recommend that you use this method because it might cause data loss and hardware damages.
To reboot the firewall immediately:
|
Task |
Command |
Remarks |
|
Reboot the firewall immediately. |
reboot |
Available in user view. |
To enable the scheduled reboot function:
|
Task |
Command |
Remarks |
|
Enable the scheduled reboot function. |
· Enable the scheduled reboot function and
specify a specific reboot time and date: · Enable the scheduled reboot function and
specify a reboot waiting time: |
Use either approach. The scheduled reboot function is disabled by default. Available in user view. |
6 Troubleshooting
Power module failure
Symptom
The firewall cannot be powered on, and the power LED (PWR0/PWR1) on the front panel is off.
Solution
To solve the issue:
1. Power off the firewall.
2. Verify that the power supply is as required by the firewall.
3. Verify that the power cords of the firewall are firmly connected.
4. Verify that the power cords are not damaged.
5. If the issue persists, contact your local sales agent.
Configuration terminal display problem
Symptom
The configuration terminal displays nothing or garbled text when the firewall is powered on.
Solution
To solve the issue:
1. Verify that the power supply system is operating correctly.
2. Verify that the serial console cable or micro USB console cable is correctly connected.
3. Verify that the serial console cable or micro USB console cable is connected to the serial port configured on the configuration terminal.
4. Verify that the configuration terminal parameters are configured as follows:
¡ Baud rate—9600.
¡ Data bits—8.
¡ Parity—None.
¡ Stop bits—1.
¡ Flow control—None.
¡ Terminal emulation—VT100.
5. Verify that the serial console cable or micro USB console cable is in good condition.
6. If the issue persists, contact your local sales agent.
Password loss
To deal with loss of the password used for accessing the firewall through the serial console port or micro USB console port, see the release notes for the firewall.
Cooling system failure
Symptom
The temperature of the firewall is higher than the normal operating temperature (45°C or 113°F).
Solution
To solve the issue:
1. Verify that the fans are operating correctly.
2. Verify that the operating environment of the firewall has good ventilation.
3. If the following alarm information is generated, the temperature of the firewall has reached the warning-level high temperature alarm threshold,
%Nov 28 20:02:59:085 2019 H3C DEV/4/TEMPERATURE_WARNING: -Context=1; Temperature is greater than the high-temperature warning threshold on slot 1 sensor outflow 1. Current temperature is 58 degrees centigrade.
Use the display environment command to examine whether the temperature of the firewall keeps rising. If the temperature has reached the alarming-level high temperature alarm threshold, back up data immediately, power off the firewall, and contact your local sales agent.
Information about the firewall temperature in the display environment command output varies by firewall model.
Only F1020, F1030, F1050, F1060, F1070, F1080, and F1090 firewalls support the display environment command.
4. If the issue persists, contact your local sales agent.
Software loading failure
Symptom
Software loading fails and the system runs the software of the previous version.
Solution
To solve the issue:
1. Verify that the physical ports are correctly connected.
2. Verify that no parameter is configured incorrectly during the loading process. You can examine the software loading process displayed on the HyperTerminal for configuration errors. The following errors can lead to software loading failure.
¡ When XMODEM is used to load software, a baud rate other than 9600 bps is selected, but the baud rate for the HyperTerminal is not reset.
¡ When TFTP is used to load software, an incorrect IP address, software name, or TFTP serve path is configured.
¡ When FTP is used to load software, an incorrect IP address, software name, username, or password is entered.
3. If the issue persists, contact your local sales agent.
7 Appendix A Chassis views and technical specifications
Chassis views
F1005/F1010
The F1005 or F1010 firewall provides the following ports on the front panel:
· Eight 10/100/1000BASE-T autosensing Ethernet ports.
· Two bypass ports.
· Two combo interfaces.
· Two USB ports.
· One console port.
· One drive slot.
Figure7-1 Front panel
|
(1) Drive slot |
(2) Console port |
|
(3) USB ports (host mode, Type A connector) |
(4) Combo interfaces |
|
(5) Bypass ports |
(6) 10/100/1000BASE-T copper ports |
|
(7) LEDs |
(8) Management Ethernet port (0/MGMT) |
|
(1) Grounding screw |
(2) Power receptacle |
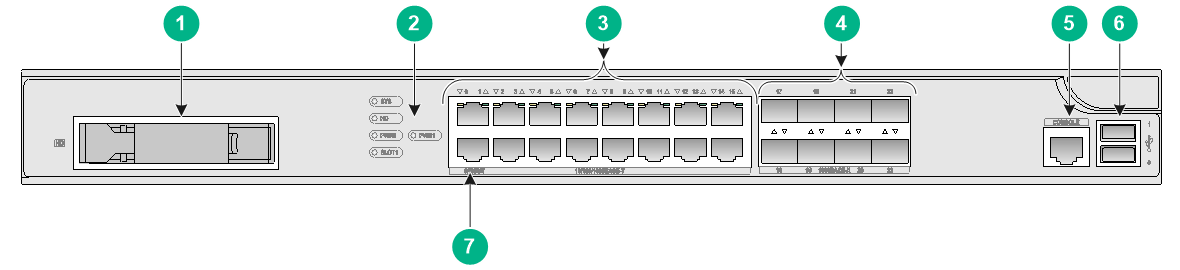
F1020
The F1020 firewall provides the following ports on the front panel:
· Sixteen 10/100/1000BASE-T autosensing Ethernet copper ports.
· Eight 1000BASE-X fiber ports.
· Two USB ports.
· One console port.
· One drive slot.
Figure7-3 Front panel
|
(1) Drive slot |
(2) LEDs |
|
(3) 10/100/1000BASE-T copper ports |
(4) 1000BASE-X fiber ports |
|
(5) Console port |
(6) USB ports (host mode, Type A connector) |
|
(7) Management Ethernet port (0/MGMT) |
|
Figure7-4 Rear panel
|
(1) Power receptacle |
(2) Interface module slot 1 |
|
(3) Interface module slot 2 (not supported) |
(4) Grounding screw |
F1030/F1050/F1060
The F1030, F1050, or F1060 firewall provides the following ports on the front panel:
· Sixteen 10/100/1000BASE-T autosensing Ethernet copper ports.
· Eight 1000BASE-X fiber ports.
· Two USB ports.
· One console port.
· One drive slot.
Figure7-5 Front panel
|
(1) Drive slot |
(2) LEDs |
|
(3) 10/100/1000BASE-T copper ports |
(4) 1000BASE-X fiber ports |
|
(5) Console port |
(6) USB ports (host mode, Type A connector) |
|
(7) Management Ethernet port (0/MGMT) |
|
Figure7-6 Rear panel
|
(1) Power receptacle |
(2) Interface module slot 1 |
|
(3) Interface module slot 2 (not supported) |
(4) Grounding screw |
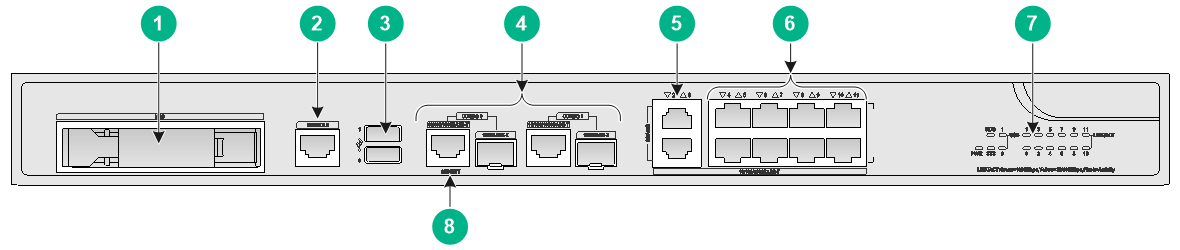
F1070/F1080
The F1070 or F1080 firewall provides the following ports on the front panel:
· Sixteen 10/100/1000BASE-T autosensing Ethernet copper ports.
· Eight 1000BASE-X fiber ports.
· Two 10GBASE-R fiber ports.
· Two USB ports.
· One console port.
· Two drive slots.
Figure7-7 Front panel
|
(1) Drive slots |
(2) LEDs |
|
(3) 10/100/1000BASE-T copper ports |
(4) 1000BASE-X fiber ports |
|
(5) 10GBASE-R fiber ports |
(6) Console port |
|
(7) USB ports (host mode, Type A connector) |
(8) Management Ethernet port (0/MGMT) |
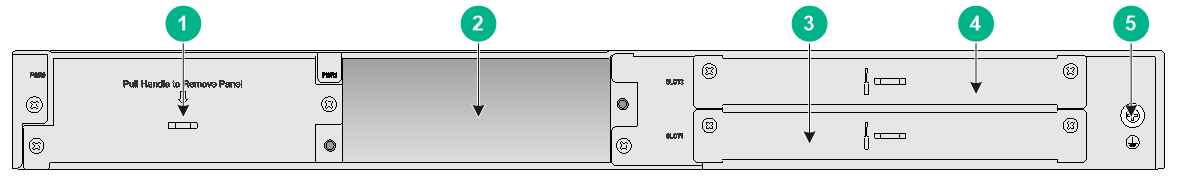
Figure7-8 Rear panel
|
(1) Power module slot 0 |
(2) Power module slot 1 |
|
(3) Interface module slot 1 |
(4) Interface module slot 2 |
|
(5) Grounding screw |
|
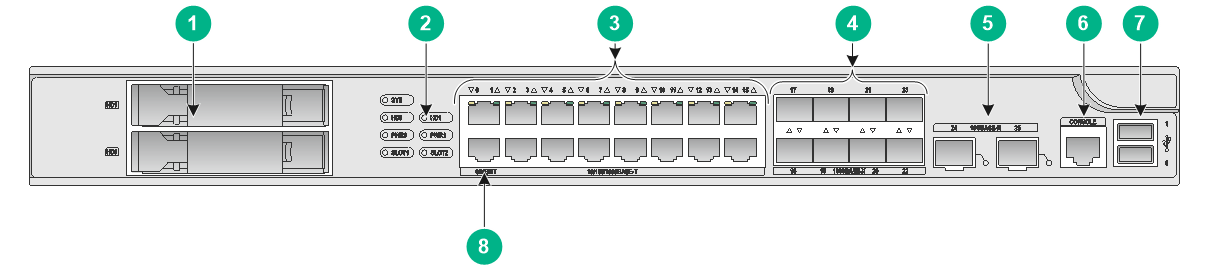
F1090
The F1090 firewall provides the following ports on the front panel:
· Fourteen 10/100/1000BASE-T autosensing Ethernet copper ports.
· Eight 1000BASE-X fiber ports.
· Eight 10GBASE-R fiber ports.
· Two USB ports.
· One console port.
· One micro USB port.
· Two drive slots.
· Two management Ethernet ports.
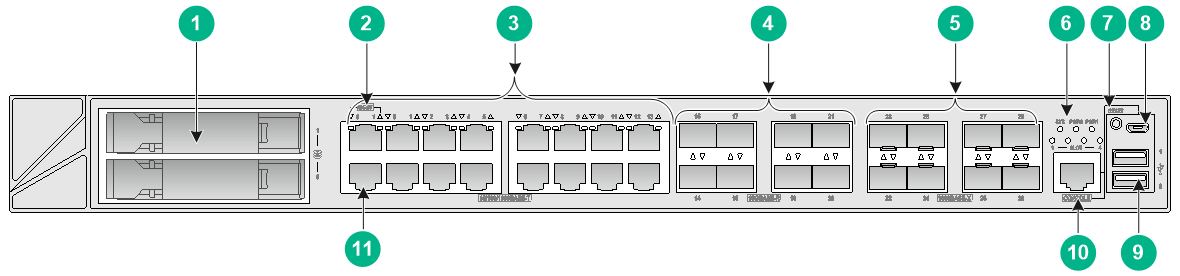
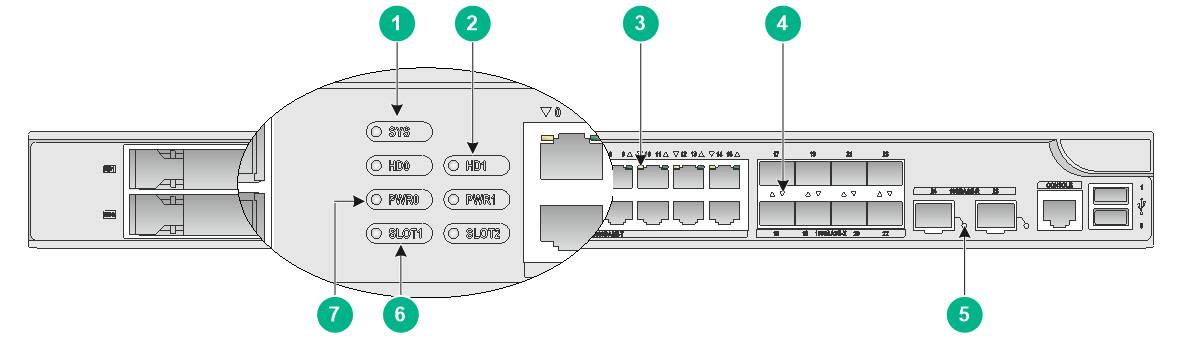
Figure7-9 Front panel
|
(1) Drive slots |
(2) Management Ethernet port (1/MGMT) |
|
(3) 10/100/1000BASE-T copper ports |
(4) 10GBASE-R fiber ports |
|
(5) 1000BASE-X fiber ports |
(6) LEDs |
|
(7) Reset button |
(8) Micro USB port |
|
(9) USB port (host mode, Type A connector) |
(10) Console port |
|
(11) Management Ethernet port (0/MGMT) |
|
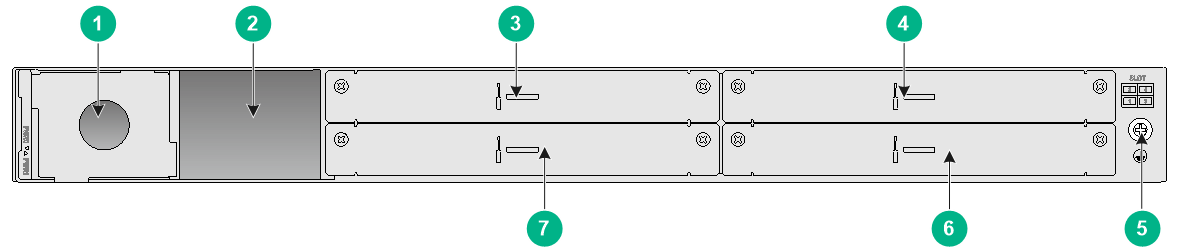
Figure7-10 Rear panel
|
(1) Power module slot 1 |
(2) Power module slot 2 |
|
(3) Interface module slot 1 |
(4) Interface module slot 4 |
|
(5) Grounding screw |
(6) Interface module slot 3 |
|
(7) Interface module slot 1 |
|
Interface modules
|
CAUTION: Do not hot swap interface modules. |
Table7-1 displays the slots available for interface module installation.
Table7-1 Interface module and device slot compatibility
|
Firewall model |
Slot number |
Slot specification |
Available interface modules |
|
F1005/F1010 |
N/A |
N/A |
Not supported |
|
F1020 |
Slot 1 |
Low speed |
· NSQM1GT4PFC · NSQM1GP4FBA |
|
F1030/F1040/F1050/F1060/F1070/F1080 |
Slots 1 and 2 |
Low speed |
· NSQM1GT4PFC · NSQM1GP4FBA |
|
F1090 |
Slots 1 to 3 |
High speed |
NS-NIM-TG6A |
|
Slots 2 to 4 |
Low speed |
· NSQM1GT4PFC · NSQM1GP4FBA |
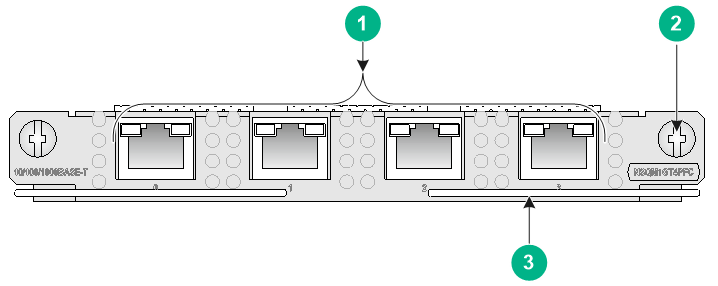
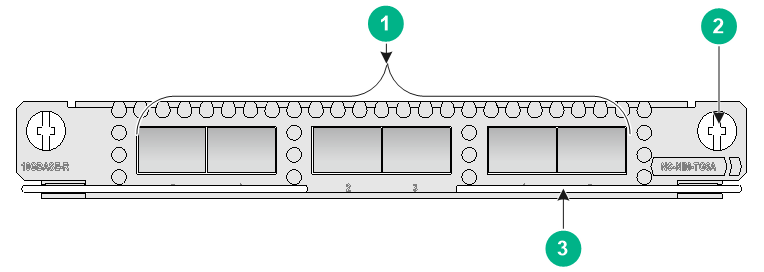
NSQM1GT4PFC
The NSQM1GT4PFC interface module provides four 10/100/1000BASE-T Ethernet copper ports.
· When the firewall is operating correctly, the four ports operate as common data ports.
· When the firewall is powered off, the four ports are divided into two bypass port pairs with ports 0 and 1 in one pair and ports 2 and 3 in another pair. The two ports in a pair can act as the uplink and downlink interfaces for a Layer 2 link and form a bypass link. This enables traffic to be transmitted through the firewall even if the firewall is powered off and ensures service continuity.
Figure7-11 Front panel of the NSQM1GT4PFC interface module
|
(1) 10/100/1000BASE-T copper ports |
(2) Captive screw |
|
(3) Ejector lever |
|
NSQM1GP4FBA
The NSQM1GP4FBA interface module provides four 1000BASE-X fiber ports.
Figure7-12 Front panel of the NSQM1GP4FBA interface module
|
(1) 1000BASE-X fiber ports |
(2) Captive screw |
|
(3) Ejector lever |
|
NS-NIM-TG6A
The NS-NIM-TG6A interface module provides six 10GBASE-R fiber ports.
Figure7-13 Front panel of the NS-NIM-TG6A interface module
|
(1) 10GBASE-R fiber ports |
(2) Captive screw |
|
(3) Ejector lever |
|
Network data encryption modules
|
CAUTION: Do not hot swap network data encryption modules. |
The appearance of network data encryption modules varies by models. For more information, see H3C SecPath Firewall Network Data Encryption Module Guide.
Table7-2 describes the hardware and software compatibility with the network data encryption modules.
Table7-2 Hardware and software compatibility with the network data encryption modules
|
Network data encryption module |
Applicable firewalls |
Applicable slots |
Applicable software version |
|
NSQM1F1KGM0 |
F1005, F1010 |
N/A |
N/A |
|
F1020, F1030, F1050, F1060, F1070, F1080 |
Slot 1 |
R9333 and later |
|
|
F1090 |
Slots 1 and 3 |
R8601P24 and later |
|
|
NSQM1F1KGMB |
F1005, F1010 |
N/A |
N/A |
|
F1020 |
Slot 1 |
R9345 and later |
|
|
F1030, F1050, F1060, F1070, F1080 |
Slots 1 and 2 |
R9345 and later |
|
|
F1090 |
Slots 1 to 4 |
R8601P24 and later |
|
|
NSQM1F1KGMC |
F1005, F1010 |
N/A |
N/A |
|
F1020 |
Slot 1 |
R9345P14 and later |
|
|
F1030, F1050, F1060, F1070, F1080 |
Slots 1 and 2 |
R9345P14 and later |
|
|
F1090 |
Subslots 1 to 4 |
R8601P24 and later |
Drives
|
CAUTION: Do not hot swap drives. |
Table7-3 describes the compatibility between drives and F10X0 firewalls.
Table7-3 Drive compatibility with F10X0 firewalls
|
Drive |
F1005/F1010 |
F1020/F1030/F1050/F1060 |
F1070/F1080 |
F1090 |
|
NS-SSD-480G-SATA-SFF |
Yes |
Yes |
Yes |
Yes |
|
NS-HDD-500G-SATA-SFF |
No |
Yes |
No |
Yes |
|
NS-HDD-1T-SATA-SFF |
No |
Yes |
No |
Yes |
Power modules
The F1070/F1080/F1090 firewall comes with power module slot PWR0 installed with a filler panel and power module slot PWR1 empty. It supports both AC and DC power modules. No power modules are provided with the firewall. Prepare power modules for the firewall yourself as required.
The F1070/F1080/F1090 firewall supports hot swapping of power modules and 1+1 power module redundancy. To install two power modules for the firewall, make sure they are the same model.
Table7-4 Power modules available for the firewall
|
Firewall model |
Available power modules |
|
F1005/F1010 |
One built-in power module |
|
F1020/F1030/F1050/F1060 |
Two built-in power modules |
|
F1070/F1080 |
Two power module slots, supporting the following power modules: · PSR150-A1 · PSR150-D1 |
|
F1090 |
Two power module slots, supporting the following power modules: · PSR250-12A1 · PSR450-12AHD · PSR450-12D |
AC power modules
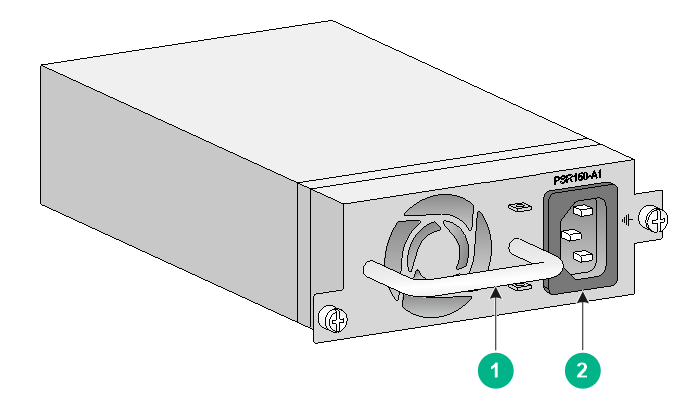
PSR150-A1
The PSR150-A1 power module with a product code of PSR150-A1-B provides a maximum output power of 150 W.
Figure7-14 PSR150-A1 power module
|
(1) Handle |
(2) Power receptacle |
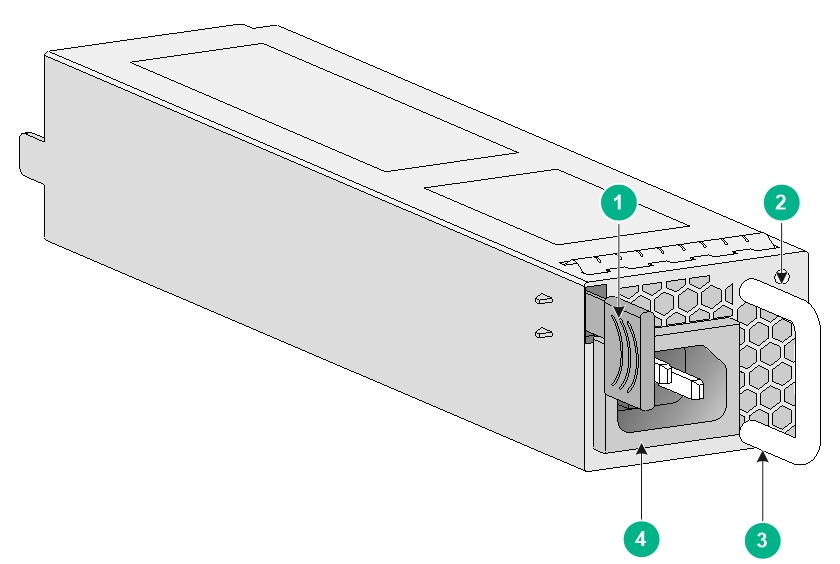
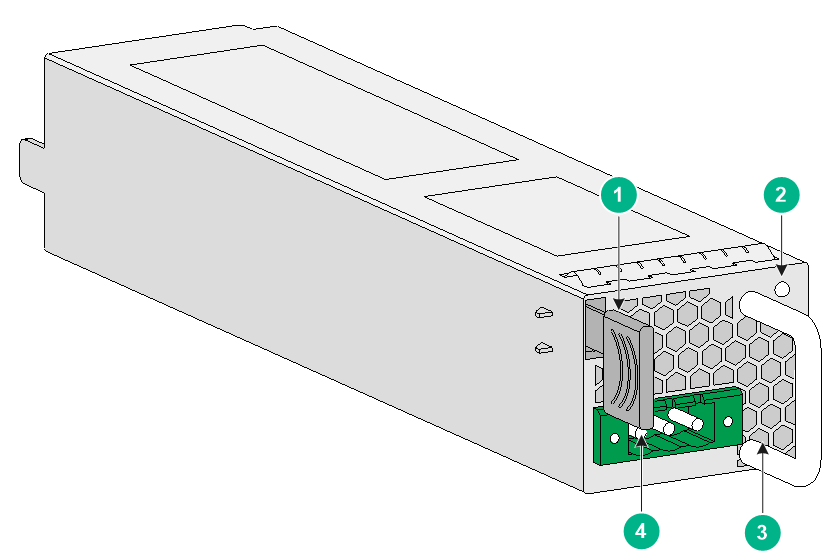
PSR250-12A1
The PSR250-12A1 power module with a product code of PSR250-12A1 provides a maximum output power of 250 W.
Figure7-15 PSR250-12A1 power module
|
(1) Latch |
(2) Status LED |
|
(3) Handle |
(4) Power receptacle |
DC power modules
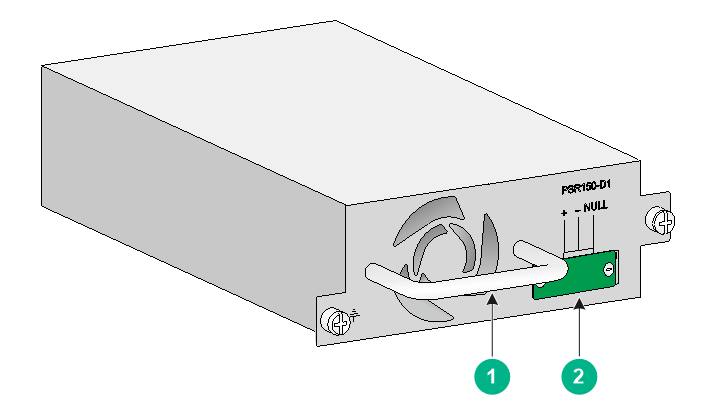
PSR150-D1
The PSR150-D1 power module with a product code of PSR150-D1-B provides a maximum output power of 150 W.
Figure7-16 PSR150-D1 power module
|
(1) Handle |
(2) Power receptacle |
PSR450-12D
The PSR450-12D power module with a product code of PSR450-12D provides a maximum output power of 450 W.
Figure7-17 PSR450-12D power module
|
(1) Latch |
(2) Status LED |
|
(3) Handle |
(4) Power receptacle |
High-voltage DC power modules
|
CAUTION: You can install high-voltage DC power modules only on the F1090 firewall. |
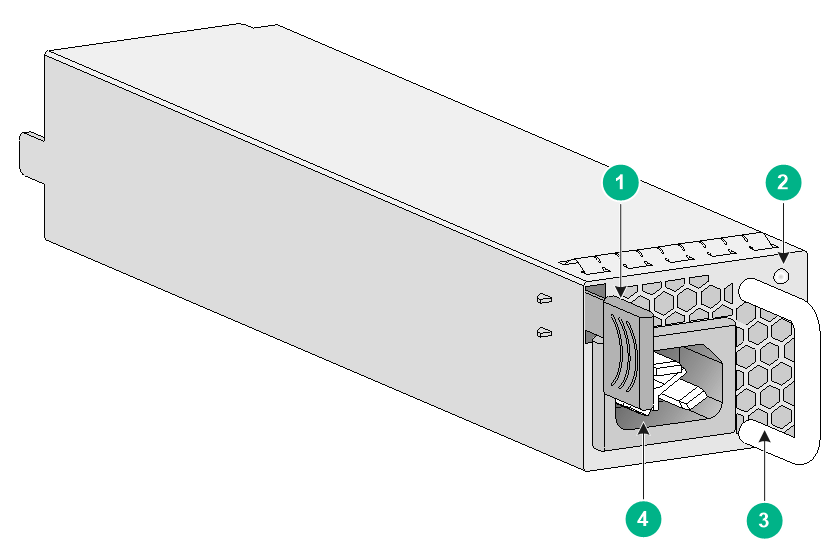
PSR450-12AHD
The PSR450-12AHD power module with a product code of PSR450-12AHD provides a maximum output power of 450 W.
Figure7-18 PSR450-12AHD power module
|
(1) Latch |
(2) Status LED |
|
(3) Handle |
(4) Power receptacle |
Dimensions and weights
The weight of the firewall includes the chassis and its removable components.
Chassis
Table7-5 Chassis dimensions and weights
|
Dimensions (H × W × D), excluding rubber feet and mounting brackets |
Weight |
|
|
F1005/F1010 |
44 × 440 × 230 mm (1.73 × 17.32 × 9.06 in) |
3 kg (6.61 lb) |
|
F1020 |
44.2 × 440 × 435 mm (1.74 × 17.32 × 17.13 in) |
6.75 kg (14.88 lb) |
|
F1030/F1050/F1060 |
44.2 × 440 × 435 mm (1.74 × 17.32 × 17.13 in) |
7.3 kg (16.09 lb) |
|
F1070/F1080 |
44.2 × 440 × 435 mm (1.74 × 17.32 × 17.13 in) |
8.5 kg (18.74 lb) |
|
F1090 |
44 × 440 × 435 mm (1.73 × 17.32 × 17.13 in) |
10 kg (22.05 lb) |
Interface modules
Table7-6 Interface module dimensions and weights
|
Interface module model |
Dimensions (H × W × D) |
Weight |
|
NSQM1GT4PFC |
19 × 150 × 172.9 mm (0.75 × 5.91 × 6.81 in) |
0.45 kg (0.99 lb) |
|
NSQM1GP4FBA |
19 × 150 × 172.9 mm (0.75 × 5.91 × 6.81 in) |
0.42 kg (0.93 lb) |
|
NS-NIM-TG6A |
19 × 150 × 172.9 mm (0.75 × 5.91 × 6.81 in) |
0.4 kg (0.88 lb) |
Network data encryption modules
Table7-7 Network data encryption module dimensions and weights
|
Network data encryption module model |
Dimensions (H × W × D) |
Weight |
|
NSQM1F1KGM0 |
40.1 × 150 × 172.9 mm (1.58 × 5.91 × 6.81 in) |
0.64 kg (1.41 lb) |
|
NSQM1F1KGMB |
19.8 × 150 × 172.9 mm (0.78 × 5.91 × 6.81 in) |
0.36 kg (0.79 lb) |
|
NSQM1F1KGMC |
19.8 × 150 × 172.9 mm (0.78 × 5.91 × 6.81 in) |
0.38 kg (0.84 lb) |
Drives
Table7-8 Drive dimensions and weights
|
Drive model |
Dimensions (H × W × D) |
Weight |
|
NS-SSD-480G-SATA-SFF |
19 × 75.7 × 118.4 mm (0.75 × 2.98 × 4.66 in) |
0.069 kg (0.15 lb) |
|
NS-HDD-500G-SATA-SFF |
19 × 75.7 × 118.4 mm (0.75 × 2.98 × 4.66 in) |
0.12 kg (0.26 lb) |
|
NS-HDD-1T-SATA-SFF |
19 × 75.7 × 118.4 mm (0.75 × 2.98 × 4.66 in) |
0.14 kg (0.31 lb) |
Storage media
Table7-9 Storage media specifications of the device
|
Firewall model |
Memory |
|
F1005/F1010 |
2GB DDR3 |
|
F1020 |
2GB DDR3 |
|
F1030/F1050 |
4GB DDR3 |
|
F1060/F1070 |
8GB DDR3 |
|
F1080 |
16GB DDR3 |
|
F1090 |
16GB DDR4 |
Table7-10 Memory specifications of drives
|
Drive model |
Memory |
|
NS-SSD-480G-SATA-SFF |
480 GB |
|
NS-HDD-500G-SATA-SFF |
500 GB |
|
NS-HDD-1T-SATA-SFF |
1 TB |
Power consumption
The system power consumption includes the power consumptions of the chassis and the removable components.
Chassis
Table7-11 Chassis power consumption
|
Firewall model |
Power consumption |
|
F1005/F1010 |
32 W |
|
F1020/F1030/F1050/F1060 |
79 W |
|
F1070/F1080 |
116 W |
|
F1090 |
180 W |
Interface modules
Table7-12 Interface module power consumption
|
Interface module model |
Power consumption |
|
NSQM1GT4PFC |
11.5 W |
|
NSQM1GP4FBA |
10.4 W |
|
NS-NIM-TG6A |
11 W |
Network data encryption modules
Table7-13 Network data encryption module power consumption
|
Network data encryption module model |
Power consumption |
|
NSQM1F1KGM0 |
4.14 W |
|
NSQM1F1KGMB |
3.7 W |
|
NSQM1F1KGMC |
5.7 W |
Drives
Table7-14 Drive power consumption
|
Drive model |
Power consumption |
|
NS-SSD-480G-SATA-SFF |
3 W |
|
NS-HDD-500G-SATA-SFF |
4.9 W |
|
NS-HDD-1T-SATA-SFF |
5 W |
Power module specifications
Table7-15 AC power module specifications
|
Model |
Rated input voltage range |
Maximum input current |
Maximum power |
|
PSR150-A1 |
100 VAC to 240 VAC @ 50 Hz or 60 Hz |
2 A |
150 W |
|
PSR250-12A1 |
100 VAC to 240 VAC @ 50 Hz or 60 Hz |
5 A |
250 W |
Table7-16 DC power module specifications
|
Model |
Rated input voltage range |
Maximum input current |
Maximum power |
|
PSR150-D1 |
–48 VDC to –60 VDC |
6 A |
150 W |
|
PSR450-12D |
–48 VDC to –60 VDC |
15 A |
450 W |
Table7-17 High-voltage DC power module specifications
|
Model |
Rated input voltage range |
Maximum input current |
Maximum power |
|
|
PSR450-12AHD |
AC input |
100 VAC to 240 VAC @ 50 Hz or 60 Hz |
7 A |
450 W |
|
High-voltage DC input |
240 VDC to 380 VDC |
3.5 A |
450 W |
|
Port specifications
Console port
Table7-18 Console port specifications
|
Item |
Specification |
|
Connector |
RJ-45 |
|
Standard compliant |
RS-232 |
|
Baud rate |
9600 bps (default) to 115200 bps |
|
Cable type |
Common asynchronous serial port cable |
|
Transmission distance |
≤ 15 m (49.21 ft) |
|
Services |
· Connection to an ASCII terminal · Connection to the serial port of a local PC running the terminal emulation program · CLI |
Micro USB console port
Table7-19 Micro USB console port specifications
|
Item |
Specification |
|
Connector |
Micro USB |
|
Standard compliant |
Micro USB |
|
Baud rate |
9600 bps (default) to 115200 bps |
|
Cable type |
USB console cable |
|
Transmission distance |
≤ 10 m (32.81 ft) |
|
Services |
· Connection to an ASCII terminal · Connection to the serial port of a local PC running the terminal emulation program · CLI |
GE copper port
Table7-20 GE copper port specifications
|
Item |
Specification |
|
Connector |
RJ-45 |
|
Standard compliance |
802.3, 802.3u, and 802.3ab |
|
Interface type |
MDI/MDI-X autosensing |
|
Cable type |
Category 5 or higher twisted pair cable |
|
Transmission distance |
100 m (328.08 ft) |
|
Interface speed and duplex mode |
10 Mbps, half/full-duplex 100 Mbps, half/full-duplex 1000 Mbps, full-duplex |
|
|
NOTE: The media dependent interface (MDI) standard is typically used on the Ethernet port of network adapters. The media dependent interface crossover (MDI-X) standard is typically used on hubs or LAN switches. |
GE fiber port
Table7-21 GE fiber port specifications
|
Item |
Specification |
|
Connector type |
LC |
|
Transceiver module type |
SFP |
|
Standard compliance |
1000BASE-X |
|
Interface speed |
1000 Mbps |
|
Duplex mode |
Full duplex |
Table7-22 1000BASE-X SFP transceiver module specifications
|
Transceiver module |
Central wavelength |
Connector |
Fiber |
Max transmission distance |
|
SFP-GE-SX-MM850-A |
850 nm |
LC |
50/125 µm multi-mode optical fiber |
0.55 km (1804.46 ft) |
|
SFP-GE-LX-SM1310-A |
1310 nm |
LC |
9/125 µm single-mode optical fiber |
10 km (6.21 miles) |
|
SFP-GE-LH40-SM1310 |
1310 nm |
LC |
9/125 µm single-mode optical fiber |
40 km (24.86 miles) |
|
SFP-GE-LH40-SM1550 |
1550 nm |
LC |
9/125 µm single-mode optical fiber |
40 km (24.86 miles) |
|
SFP-GE-LH80-SM1550 |
1550 nm |
LC |
9/125 µm single-mode optical fiber |
80 km (49.71 miles) |
|
SFP-GE-LH100-SM1550 |
1550 nm |
LC |
9/125 µm single-mode optical fiber |
100 km (62.14 miles) |
10 GE fiber port
The F1070/F1080 firewall provides two 10GBASE-R fiber ports and the F1090 provides eight 10GBASE-R fiber ports.
Table7-23 10 GE fiber port specifications
|
Item |
Specification |
|
Connector type |
LC |
|
Transceiver module type |
SFP+ |
|
Standard compliance |
10GBASE-R |
|
Interface speed |
LAN PHY: 10.3125 Gbps/1000 Mbps |
Table7-24 10 Gbps SFP+ transceiver module specifications
|
Transceiver module |
Central wavelength |
Connector |
Fiber |
Max transmission distance |
|
SFP-XG-SX-MM850-A |
850 nm |
LC |
50/125 µm multi-mode optical fiber |
300 m (984.25 ft) |
|
82 m (269.03 ft) |
||||
|
66 m (216.54 ft) |
||||
|
62.5/125 µm multi-mode optical fiber |
33 m (108.27 ft) |
|||
|
26 m (85.30 ft) |
||||
|
SFP-XG-LX220-MM1310 |
1310 nm |
LC |
62.5/125 µm multi-mode optical fiber |
220 m (721.78 ft) |
|
50/125 µm multi-mode optical fiber |
220 m (721.78 ft) |
|||
|
100 m (328.08 ft) |
||||
|
SFP-XG-LX-SM1310 |
1310 nm |
LC |
9/125 µm single-mode optical fiber |
10 km (6.21 miles) |
|
SFP-XG-LH40-SM1550 |
1550 nm |
LC |
9/125 µm single-mode optical fiber |
40 km (24.86 miles) |
|
|
NOTE: The 10 GE fiber ports on the F1090 support only SFP-XG-LH40-SM1550 transceiver modules. |
8 Appendix B LEDs
The F10X0 firewalls use similar LEDs. This section uses the LEDs on the F1080 firewall as an example.
Figure8-1 LEDs
|
(1) System status LED |
(2) Drive status LED |
|
(3) 10/100/1000BASE-T copper port LED |
(4) 1000BASE-X fiber port LED |
|
(5) 10GBASE-R fiber port LED |
(6) Interface module LED |
|
(7) Power module LED |
|
Table8-2 LED description
|
LED |
Mark |
Status |
Description |
|
System status LED |
SYS |
Off |
The firewall is not powered on or has failed. |
|
Slow flashing green |
The firewall is operating correctly. |
||
|
Fast flashing green |
The firewall is loading software. |
||
|
Drive status LED |
HD0, HD1 |
Off |
The firewall is not powered on or has failed. |
|
Fast flashing green |
Data is being read from or written to the drive. |
||
|
Steady green |
The drive is present and operating correctly. |
||
|
10/100/1000BASE-T copper port LED |
10/100/1000BASE-T |
Off |
No link is present. |
|
Steady green |
A link is present. |
||
|
Flashing green |
The port is receiving and sending data. |
||
|
1000BASE-X fiber port LED |
1000BASE-X |
Off |
No link is present. |
|
Steady green |
A 1000 Mbps link is present. |
||
|
Flashing green |
The port is receiving and sending data at 1000 Mbps. |
||
|
10GBASE-R fiber port LED |
10GBASE-R |
Off |
No link is present. |
|
Steady green |
A 10 Gbps link is present. |
||
|
Flashing green |
The port is receiving and sending data at 10 Gbps. |
||
|
Interface module LED |
SLOT1, SLOT2 |
Off |
No interface module is present or the interface module has failed. |
|
Steady green |
The interface module is operating correctly. |
||
|
Power module LED |
PWR0, PWR1 |
Off |
No power module is present or the power module has failed. |
|
Steady green |
The power module is operating correctly. |
9 Appendix C Cables
Console cable
RJ-45 to DB9 console cable
An RJ-45 to DB9 console cable is used to connect the console port on the firewall to the serial port on a configuration terminal (a PC for example):
· Connect the DB9 female connector of the cable to the 8-core serial port on the configuration terminal.
· Connect the RJ-45 connector of the cable to the console port on the firewall.
Figure9-1 RJ-45 to DB9 console cable
Table9-1 RJ-45 to DB9 console cable pinouts
|
RJ-45 |
Signal |
Direction |
DB-9 |
|
1 |
RTS |
← |
7 |
|
2 |
DTR |
← |
4 |
|
3 |
TXD |
← |
3 |
|
4 |
CD |
→ |
1 |
|
5 |
GND |
- |
5 |
|
6 |
RXD |
→ |
2 |
|
7 |
DSR |
→ |
6 |
|
8 |
CTS |
→ |
8 |
Micro USB console cable
A micro USB console cable is used to connect the micro USB console port on the firewall to the USB port on a configuration terminal (a PC for example):
· Connect the USB Type A connector of the cable to the USB port on the configuration terminal.
· Connect the USB Type mini-A/B connector to the micro USB console port on the firewall.
Figure9-2 Micro USB console cable
Table9-2 Micro USB console cable pinouts
|
USB Type A connector |
Signal |
USB Type mini-A/B connector |
Signal |
|
1 |
VBUS |
1 |
VBUS |
|
2 |
D- |
2 |
D- |
|
3 |
D+ |
3 |
D+ |
|
|
|
4 |
ID(NC) |
|
4 |
GND |
5 |
GND |
Ethernet twisted pair cable
Introduction
An Ethernet twisted pair cable consists of four pairs of insulated copper wires twisted together. Every wire uses a different color, and has a diameter of about 1 mm (0.04 in). A pair of twisted copper cables can cancel the electromagnetic radiation of each other, and reduce interference of external sources. An Ethernet twisted pair cable mainly transmits analog signals and is advantageous in transmitting data over shorter distances. It is the commonly used transmission media of the Ethernet. The maximum transmission distance of the Ethernet twisted pair cable is 100 m (328.08 ft). To extend the transmission distance, you can connect two twisted pair cable segments with a repeater. At most four repeaters can be added, which means five segments can be joined together to provide a transmission distance of 500 m (1640.42 ft).
Ethernet twisted pair cables can be classified into category 3, category 4, category 5, category 5e, category 6, and category 7 cables based on performance. In LANs, category 5, category 5e, and category 6 are commonly used.
Table9-3 Description for commonly used Ethernet twisted pair cables
|
Type |
Description |
|
Category 5 |
Suitable for data transmission at a maximum speed of 100 Mbps |
|
Category 5e |
Suitable for data transmission at a maximum speed of 1000 Mbps |
|
Category 6 |
Suitable for data transmission at a speed higher than 1 Gbps |
Based on whether a metal shielding is used, Ethernet twisted pair cables can be classified into shielded twisted pair (STP) and unshielded twisted pair (UTP). An STP cable provides a metallic braid between the twisted pairs and the outer jacket. This metallic braid helps reduce radiation, prevent information from being listened, and eliminate external electromagnetic interference (EMI) of external sources. STPs have strict application requirements and are expensive although they provide better EMI prevention performance than UTPs, so in most LANs, UTPs are commonly used.
An Ethernet twisted pair cable connects network devices through the RJ-45 connectors at the two ends. Figure9-3 shows the pinouts of an RJ-45 connector.
Figure9-3 RJ-45 connector pinout
|
|
NOTE: The RJ-45 Ethernet ports of the firewall use category 5 or higher Ethernet twisted pair cables for connection. |
EIA/TIA cabling specifications define two standards, 568A and 568B, for cable pinouts.
· Standard 568A—pin 1: white/green stripe, pin 2: green solid, pin 3: white/orange stripe, pin 4: blue solid, pin 5: white/blue stripe, pin 6: orange solid, pin 7: white/brown stripe, pin 8: brown solid.
· Standard 568B—pin 1: white/orange stripe, pin 2: orange solid, pin 3: white/green stripe, pin 4: blue solid, pin 5: white/blue stripe, pin 6: green solid, pin 7: white/brown stripe, pin 8: brown solid.
Ethernet twisted pair cables can be classified into straight-through and crossover cables based on their pinouts.
· Straight-through—The pinouts at both ends are T568B compliant, as shown in Figure9-4.
· Crossover—The pinouts are T568B compliant at one end and T568A compliant at the other end, as shown in Figure9-5.
Figure9-4 Straight-through cable
Select an Ethernet twisted pair cable according to the RJ-45 Ethernet port type on your device. An RJ-45 Ethernet port can be MDI (for routers and PCs) or MDIX (for switches). Table9-4 and Table9-5 show their pinouts.
Table9-4 RJ-45 MDI port pinouts
|
Pin |
10BASE-T/100BASE-TX |
1000BASE-T |
||
|
Signal |
Function |
Signal |
Function |
|
|
1 |
Tx+ |
Sends data |
BIDA+ |
Bi-directional data cable A+ |
|
2 |
Tx- |
Sends data |
BIDA- |
Bi-directional data cable A- |
|
3 |
Rx+ |
Receives data |
BIDB+ |
Bi-directional data cable B+ |
|
4 |
Reserved |
N/A |
BIDC+ |
Bi-directional data cable C+ |
|
5 |
Reserved |
N/A |
BIDC- |
Bi-directional data cable C- |
|
6 |
Rx- |
Receives data |
BIDB- |
Bi-directional data cable B- |
|
7 |
Reserved |
N/A |
BIDD+ |
Bi-directional data cable D+ |
|
8 |
Reserved |
N/A |
BIDD- |
Bi-directional data cable D- |
Table9-5 RJ-45 MDIX port pinouts
|
Pin |
10BASE-T/100BASE-TX |
1000BASE-T |
||
|
Signal |
Function |
Signal |
Function |
|
|
1 |
Rx+ |
Receives data |
BIDB+ |
Bi-directional data cable B+ |
|
2 |
Rx- |
Receives data |
BIDB- |
Bi-directional data cable B- |
|
3 |
Tx+ |
Sends data |
BIDA+ |
Bi-directional data cable A+ |
|
4 |
Reserved |
N/A |
BIDD+ |
Bi-directional data cable D+ |
|
5 |
Reserved |
N/A |
BIDD- |
Bi-directional data cable D- |
|
6 |
Tx- |
Sends data |
BIDA- |
Bi-directional data cable A- |
|
7 |
Reserved |
N/A |
BIDC+ |
Bi-directional data cable C+ |
|
8 |
Reserved |
N/A |
BIDC- |
Bi-directional data cable C- |
To ensure normal communication, the pins for sending data on one port must correspond to the pins for receiving data on the peer port. When both of the ports on the two devices are MDI or MDIX, use a crossover Ethernet cable; when one port is MDI and the other is MDIX, use a straight-through Ethernet cable. To summarize, straight-through and crossover cables connect the following devices:
· Straight-through cables connect devices of different types—for example, router to PC and router to switch.
· Crossover cables connect devices of the same type—for example, switch to switch, router to router, and PC to PC.
If an RJ-45 Ethernet port is enabled with MDI/MDIX autosensing, it can automatically negotiate pin roles.
|
|
NOTE: The RJ-45 Ethernet ports on the firewall support MDI/MDIX autosensing. |
Making an Ethernet twisted pair cable
1. Cut the cable to a required length with the crimping tool.
2. Strip off an appropriate length of the cable sheath. The length is typically that of the RJ-45 connector.
3. Untwist the pairs so that they can lay flat, and arrange the colored wires based on the wiring specifications.
4. Cut the top of the wires even with one another. Insert the wires into the RJ-45 connector and make sure the wires extend to the front of the RJ-45 connector and make good contact with the metal contacts in the RJ-45 connector and in the correct order.
5. Crimp the RJ-45 connector with the crimping tool until you hear a click.
6. Use a cable tester to verify the connectivity of the cable.
Optical fiber
Optical fibers feature low loss and long transmission distance.
Optical fibers can be classified into single mode fibers and multi-mode fibers. A single mode fiber (with yellow jacket) carries only a single ray of light; a multi-mode fiber (with orange jacket) carries multiple modes of lights.
Table9-6 Characteristics of single mode and multi-mode optical fibers
|
Item |
Single mode fiber |
Multi-mode fiber |
|
Core |
Small core (10 micrometers or less) |
Larger core than single mode fiber (50 micrometers, 62.5 micrometers or greater) |
|
Dispersion |
Less dispersion |
Allows greater dispersion and therefore, signal loss exists. |
|
Light source and transmission distance |
Uses lasers as the light source often within campus backbones for distance of several thousand meters |
Uses LEDs as the light source often within LANs or distances of a couple hundred meters within a campus network |
Table9-7 Allowed maximum tensile force and crush load
|
Period of force |
Tensile load (N) |
Crush load (N/mm) |
|
Short period |
150 |
500 |
|
Long term |
80 |
100 |
Fiber connectors are indispensable passive components in an optical fiber communication system. They allow the removable connection between optical channels, which makes the optical system debugging and maintenance more convenient. There are multiple types of fiber connectors. Figure9-6 shows an LC connector.
Figure9-6 Appearance of an LC connector
Follow these guidelines when you connect an optical fiber:
· Before connecting an optical fiber, make sure the connector and cable type match the interface module.
· The fiber Ethernet port of the firewall supports only the LC connector.
· Fiber connectors are fitted with dust caps. Keep the dust caps secure when the fiber connectors are in use. Install dust caps when the fiber connectors are not in use to avoid damage to their end face. Replace the dust cap if it is loose or polluted.
· Before connecting an optical fiber, use dust free paper and absolute alcohol to clean the end face of the two fiber connectors. You can brush the end faces only in one direction.
· Never bend or curve a fiber when connecting it.
· If the fiber has to pass through a metallic board hole, when passing through a metallic board hole or bending along the acute side of mechanical parts, the fiber must wear jackets or cushions.