- Table of Contents
-
- 14-WLAN Configuration Guide (AC)
- 00-Preface
- 01-Compatibility of hardware and AC functionality
- 02-AP management configuration
- 03-Radio management configuration
- 04-WLAN access configuration
- 05-WLAN security configuration
- 06-WLAN authentication configuration
- 07-WIPS configuration
- 08-WLAN QoS configuration
- 09-WLAN roaming configuration
- 10-WLAN load balancing configuration
- 11-WLAN radio resource measurement configuration
- 12-Channel scanning configuration
- 13-Band navigation configuration
- 14-WLAN multicast optimization configuration
- 15-WLAN RRM configuration
- 16-WLAN IP snooping configuration
- 17-WLAN probe configuration
- 18-Spectrum management configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 05-WLAN security configuration | 408.10 KB |
Contents
802.11w management frame protection
About 802.11w management frame protection
Restrictions: Hardware compatibility with WLAN security
WLAN security tasks at a glance
Setting the security information element
Setting the TKIP MIC failure hold time
Configuring 802.11w management frame protection
Enabling password failure limit
Configuring PPSK authentication
Enabling Oasis PPSK authentication
Enabling SNMP notifications for WLAN security
Display and maintenance commands for WLAN security
WLAN security configuration examples
Example: Configuring shared key authentication
Example: Configuring PSK authentication and bypass authentication
Example: Configuring PSK authentication and MAC authentication
Example: Configuring 802.1X AKM
Example: Configuring management frame protection
Example: Configuring dynamic WEP
Example: Configuring private PSK authentication and MAC authentication
Configuring WLAN security
About WLAN security
WLAN security mechanisms include Pre Robust Security Network Association (Pre-RSNA), 802.11i, and 802.11w.
Pre-RSNA defines the original security mechanism, which is vulnerable to security attacks. To enhance WLAN security, 802.11i was introduced, but it encrypts only WLAN data traffic. Based on the 802.11i framework, 802.11w offers management frame protection to prevent attacks such as forged de-authentication and disassociation frames.
Pre-RSNA mechanism
The pre-RSNA mechanism uses the open system and shared key algorithms for authentication and uses WEP for data encryption. WEP uses the stream cipher RC4 for confidentiality and supports key sizes of 40 bits (WEP40), 104 bits (WEP104), and 128 bits (WEP128).
Open system authentication
Open system authentication is the default and simplest authentication algorithm. Any client that requests authentication by using this algorithm can pass the authentication.
Open system authentication uses the following process:
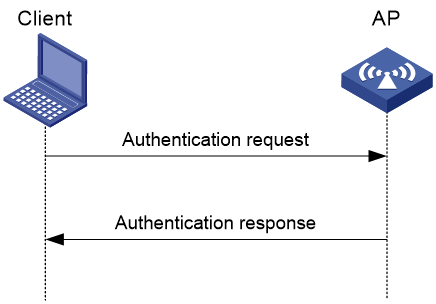
1. The client sends an authentication request to the AP.
2. The AP sends an authentication response to the client after the client passes the authentication.
Figure 1 Open system authentication process
Shared key authentication
Shared key authentication uses a WEP key for the AP and client to complete authentication.
Shared key authentication uses the following process:
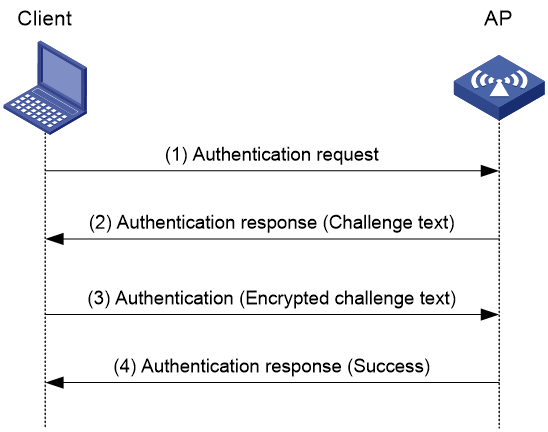
1. The client sends an authentication request to the AP.
2. The AP randomly generates a challenge text and sends it to the client.
3. The client uses the WEP key to encrypt the challenge text and sends it to the AP.
4. The AP uses the WEP key to decrypt the challenge text and compares the decrypted challenge text with the original challenge text. If they are identical, the client passes the authentication. If they are not, the authentication fails.
Figure 2 Shared key authentication process
802.11i mechanism
|
IMPORTANT: 802.11i requires open system authentication for link layer authentication. |
Security modes
The 802.11i mechanism (the RSNA mechanism) provides WPA and RSN security modes. WPA implements a subset of an 802.11i draft to provide enhanced security over WEP and RSN implements the full 802.11i.
AKM
The 802.11i mechanism uses the following authentication and key management (AKM) modes for authenticating user integrity and dynamically generating and updating keys:
· 802.1X—802.1X performs user authentication and generates the pairwise master key (PMK) during authentication. The client and AP use the PMK to generate the pairwise transient key (PTK).
· Private PSK—The MAC address of the client is used as the PSK to generate the PMK. The client and AP use the PMK to generate the PTK.
· PSK—The PSK is used to generate the PMK. The client and AP use the PMK to generate the PTK.
Authentication
802.1X authentication is more secure than PSK authentication. For more information about 802.1X authentication, see "Configuring WLAN user access authentication."
PSK authentication requires the same PSK to be configured for both an AP and a client. PSK integrity is verified during the four-way handshake. If PTK negotiation succeeds, the client passes the authentication.
Key management
Key management defines how to generate and update the PTK and group temporary key (GTK). The PTK is used in unicast and the GTK is used in multicast and broadcast.
PTK and GTK
· PTK structure
¡ EAPOL-Key Confirmation Key (KCK) is used to verify the integrity of an EAPOL-Key frame.
¡ EAPOL-Key Encryption Key (KEK) is used to encrypt the key data in the EAPOL-Key frame.
¡ Temporal Key (TK) is used to encrypt unicast packets.
· The GTK includes the TK and other fields. The TK is used to encrypt multicast and broadcast packets.
EAPOL-Key packet
The IEEE 802.11i protocol uses EAPOL-Key packets during key negotiation.
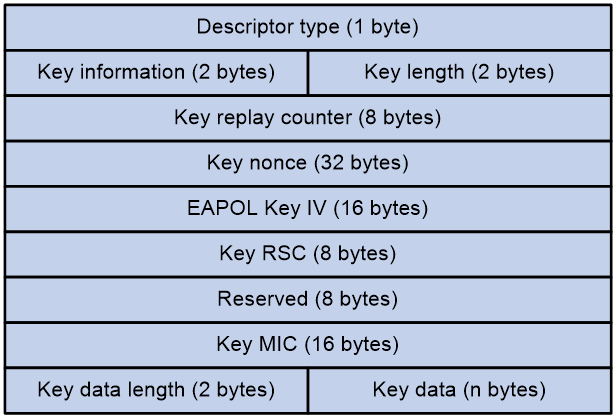
Figure 3 EAPOL-Key structure
Table 1 EAPOL-Key field description
|
Field |
Description |
|
Descriptor type |
Specifies the network type: · WPA network. · RSN network. |
|
Key information |
For more information about this field, see Table 2. |
|
Key length |
Length of the key. |
|
Key replay counter |
Records the total number of GTK updates to prevent replay attacks. The AP sets this field to 0 at the beginning of the negotiation and increments the value on each successive EAPOL-Key frame. The client records this field from the last valid EAPOL-Key frame that it received if this field is greater than the field recorded previously. EAPOL-Key frame retransmission is required in the following situations: · The field received by the client is smaller than or equal to the field recorded by the client. · The field received by the AP is not equal to the field recorded on the AP. If the retransmission attempts exceed the maximum number, the AP disconnects the client. |
|
Key nonce |
Random value used to generate the PTK. |
|
EAPOL Key IV |
Encrypts the TKIP. This field is valid only when the encryption type is not CCMP. |
|
Key RSC |
Records the total number of multicast packets or broadcast packets to prevent replay attacks. The AP increments the value of this field on transmission of each multicast or broadcast packet. |
|
Reserved |
Reserved field. |
|
Key MIC |
Message integrity check. |
|
Key data length |
Length of the key data. |
|
Key data |
Data to be transmitted, such as the GTK and pairwise master key identifier (PMKID). |
Figure 4 Key information structure
Table 2 Key information description
|
Field |
Description |
|
Key Descriptor Version |
3-bit key version: · 1—Non-CCMP key. · 2—CCMP key. |
|
Key Type |
1-bit key type: · 0—Multicast negotiation key. · 1—Unicast negotiation key. |
|
Reserved |
2-bit field reserved. The sender sets this field to 0, and the receiver ignores this field. |
|
Install |
1-bit key installation field. If the Key Type field is 1, this field is 0 or 1. · 0—The AP does not request the client to install the TK. · 1—The AP requests the client to install the TK. If the Key type field is 0, the sender sets this field to 0, and the receiver ignores this field. |
|
Key Ack |
1-bit key acknowledgment field. The value 1 indicates that the AP requests an acknowledgement from the client. |
|
Key MIC |
Message integrity check. If this field is 1, the generated MIC must be included in the Key MIC field of the EAPOL-key frame. |
|
Secure |
1-bit key status. The value 1 indicates that the key has been generated. |
|
Error |
1-bit MIC check status. The value 1 indicates that a MIC failure has occurred. The client sets this field to 1 when the Request field is 1. |
|
Request |
1-bit request used by the client to request the AP to initiate the four-way handshake or multi-cast handshake in a MIC failure report. |
|
Encrypted Key Data |
1-bit key data encryption status. The value 1 indicates that the key data is encrypted. |
|
Reserved |
3-bit reserved field. The sender sets this field to 0, and the receiver ignores this field. |
WPA key negotiation
WPA uses EAPOL-Key packets in the four-way handshake to negotiate the PTK, and in the two-way handshake to negotiate the GTK.
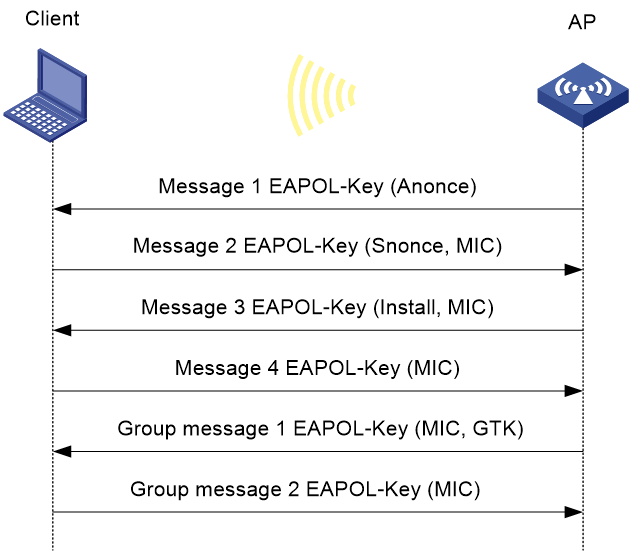
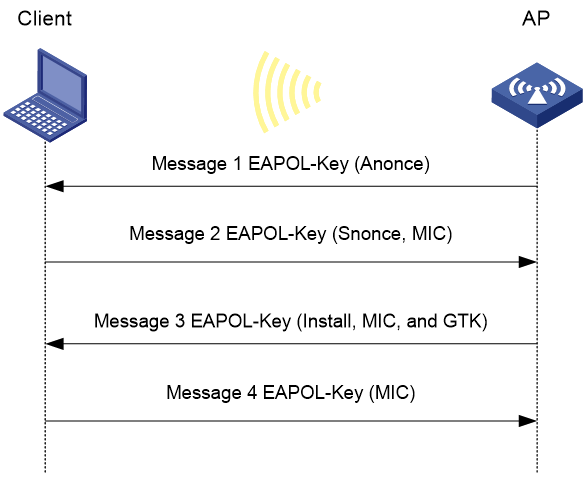
Figure 5 WPA key negotiation process
WPA key negotiation uses the following process:
1. The AP sends the client EAPOL-Key message 1 that contains a random value ANonce.
2. The client performs the following operations:
a. Uses the random value SNonce, ANonce, and PMK to generate a PTK by using the key derivation function (KDF).
b. Uses the KCK in the PTK to generate the MIC.
c. Returns EAPOL-Key message 2 that contains the SNonce and MIC.
3. The AP performs the following operations:
a. Uses the SNonce, ANonce, and PMK to generate a PTK by using the KDF.
b. Uses the KCK in the PTK to generate the MIC.
c. Compares the received MIC with the local MIC.
d. Returns EAPOL-Key message 3 that contains the PTK installation request tag and MIC if the two MICs are the same.
4. The client performs the following operations:
a. Compares the received MIC with the local MIC.
b. Installs the PTK and returns EAPOL-Key message 4 that contains the MIC if the two MICs are the same.
5. The AP performs the following operations:
a. Compares the received MIC with the local MIC.
b. Installs the PTK and generates a GTK with the GMK and MAC address of the AP by using the KDF if the two MICs are the same.
c. Returns EAPOL-Key group message 1 that contains the GTK and MIC.
6. The client performs the following operations:
a. Installs the GTK if the two MICs are the same.
b. Returns EAPOL-Key group message 2 that contains the MIC.
7. The AP performs the following operations:
a. Compares the received MIC with the local MIC.
b. Installs the GTK if the MICs are the same.
RSN key negotiation
RSN uses EAPOL-Key packets in the four-way handshake to negotiate the PTK and the GTK.
Figure 6 RSN key negotiation process
RSN key negotiation uses the following process:
1. The AP sends the client EAPOL-Key message 1 that contains a random value ANonce.
2. The client performs the following operations:
a. Uses the random value SNonce, ANonce, and PMK to generate a PTK by using the KDF.
b. Uses the KCK in the PTK to generate the MIC.
c. Returns EAPOL-Key message 2 that contains the SNonce and MIC.
3. The AP performs the following operations:
a. Uses the SNonce, ANonce, and PMK to generate a PTK by using the KDF.
b. Uses the KCK in the PTK to generate the MIC.
c. Compares the received MIC with the local MIC.
d. Generates a GTK with the random GMK and MAC address of the AP by using the KDF if the two MICs are the same.
e. Returns EAPOL-Key message 3 that contains the key installation request tag, MIC, and GTK.
4. The client performs the following operations:
a. Compares the received MIC with the local MIC.
b. Installs the PTK and GTK if the two MICs are the same.
c. Returns EAPOL-Key message 4 that contains the MIC.
5. The AP performs the following operations:
a. Compares the received MIC with the local MIC.
b. Installs the PTK and GTK if the two MICs are the same.
Key updates
Key updates enhance WLAN security. Key updates include PTK updates and GTK updates.
· PTK updates—Updates for the unicast keys using the four-way handshake negotiation.
· GTK updates—Updates for the multicast keys using the two-way handshake negotiation.
Cipher suites
TKIP
Temporal Key Integrity Protocol (TKIP) and WEP both use the RC4 algorithm. You can change the cipher suite from WEP to TKIP by updating the software without changing the hardware. TKIP has the following advantages over WEP:
· TKIP provides longer initialization vectors (IVs) to enhance encryption security. Compared with WEP encryption, TKIP encryption uses the 128-bit RC4 encryption algorithm, and increases the length of IVs from 24 bits to 48 bits.
· TKIP allows for dynamic key negotiation to avoid static key configuration. TKIP dynamic keys cannot be easily deciphered.
· TKIP offers MIC and countermeasures. If a packet has been tampered with, it will fail the MIC. If two packets fail the MIC in a period, the AP automatically takes countermeasures by stopping providing services in a period to prevent attacks.
CCMP
Counter mode with CBC-MAC Protocol (CCMP) is based on the Counter-Mode/CBC-MAC (CCM) of the Advanced Encryption Standard (AES) encryption algorithm.
CCMP contains a dynamic key negotiation and management method. Each client can dynamically negotiate a key suite, which can be updated periodically to further enhance the security of the CCMP cipher suite. During the encryption process, CCMP uses a 48-bit packet number (PN) to make sure each encrypted packet uses a different PN. This improves WLAN security.
Dynamic WEP mechanism
|
IMPORTANT: The dynamic WEP mechanism uses open system authentication for link layer authentication. |
802.11 provides the dynamic WEP mechanism to ensure that each user uses a private WEP key.
· For unicast communications, the mechanism uses the WEP key negotiated by the client and server during 802.1X authentication.
· For multicast and broadcast communications, the mechanism uses the configured WEP key. If you do not configure a WEP key, the AP randomly generates a WEP key for broadcast and multicast communications.
After the client passes 802.1X authentication, the AP sends the client an RC4-EAPOL packet that contains the unicast WEP key ID, and the multicast and broadcast WEP key and key ID. The unicast WEP key ID is 4.
802.11w management frame protection
About 802.11w management frame protection
The management frame protection service protects a set of robust management frames, such as de-authentication, disassociation, and some robust action frames.
· For unicast management frames, it uses the PTK to encrypt the frames and provides secrecy, integrity, and replay protection.
· For broadcast and multicast management frames, it uses the Broadcast Integrity Protocol (BIP) to provide integrity and replay protection.
The security association (SA) query mechanism is used to enhance security if the AP and client negotiate to use management frame protection. SA queries include active SA queries and passive SA queries.
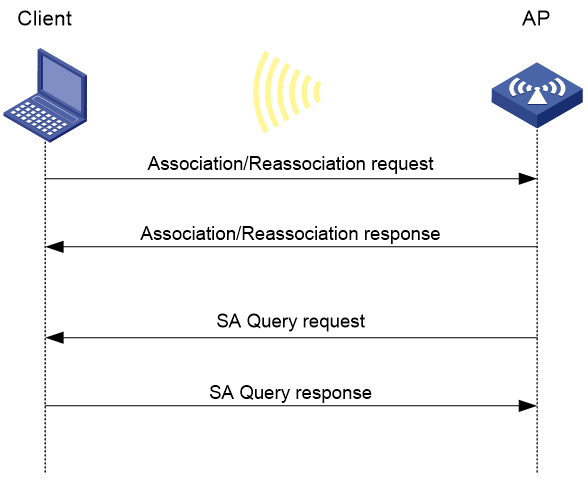
Active SA query
As shown in Figure 7, active SA query uses the following process:
1. The client sends an association or reassociation request to the AP.
2. Upon receiving the request, the AP sends a response to inform the client that the request is denied and the client can associate at a later time. The response contains the association comeback time.
3. The AP sends an SA query request to verify the status of the client:
¡ If the AP receives an SA query response within the timeout time, it considers the client online.
¡ If the AP does not receive an SA query response within the timeout time, it sends another SA query request. If the AP receives an SA query response within the retransmission time, it considers the client online. The AP does not respond to any association or reassociation requests from the client until the association comeback time times out.
¡ If the AP does not receive an SA query response within the retransmission time, it considers the client offline and allows the client to reassociate.
Figure 7 Active SA query process
Passive SA query
As shown in Figure 8, passive SA query uses the following process:
1. The client triggers the SA query process upon receiving an unencrypted disassociation or deauthentication frame.
2. The client sends an SA query request to the AP.
3. The AP sends an SA query response to the client:
¡ If the client receives the response, the client determines that the AP is online and does not process the disassociation or deauthentication frame.
¡ If the client does not receive a response, the client determines that the AP is offline and disassociates with the AP.
Figure 8 Passive SA query process
Restrictions: Hardware compatibility with WLAN security
For information about MSR routers that can function as ACs, see "Compatibility of hardware and AC functionality."
Protocols and standards
· IEEE Standard for Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements—2004
· WI-FI Protected Access—Enhanced Security Implementation Based On IEEE P802.11i Standard-Aug 2004
· Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements—802.11, 1999
· IEEE Standard for Local and metropolitan area networks "Port-Based Network Access Control" 802.1X™-2004
· 802.11i IEEE Standard for Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements
· 802.11w IEEE Standard for Information technology—Telecommunications and information exchange between systems—Local and metropolitan area networks—Specific requirements
WLAN security tasks at a glance
Pre-RSNA tasks at a glance
To configure Pre-RSNA, perform the following tasks:
3. (Optional.) Enabling SNMP notifications for WLAN security
802.11i tasks at a glance
To configure 802.11i, perform the following tasks:
2. Setting the security information element
4. (Optional.) Setting the PSK
5. (Optional.) Setting the KDF
6. (Optional.) Configuring GTK update
7. (Optional.) Configuring PTK update
8. (Optional.) Setting the TKIP MIC failure hold time
9. (Optional.) Setting the WEP key
10. (Optional.) Configuring 802.11w management frame protection
11. (Optional.) Enabling password failure limit
12. (Optional.) Configuring PPSK authentication
13. (Optional.) Enabling SNMP notifications for WLAN security
Dynamic WEP tasks at a glance
To configure dynamic WEP, perform the following tasks:
2. (Optional.) Setting the cipher suite
3. (Optional.) Setting the WEP key
4. (Optional.) Enabling SNMP notifications for WLAN security
Configuring security features
Configuring the AKM mode
About this task
Each of the following AKM modes must be used with a specific authentication mode:
· 802.1X AKM—802.1X authentication mode.
· Private PSK AKM—MAC authentication mode.
· PSK AKM—MAC or bypass authentication mode.
· WiFi alliance anonymous 802.1X AKM—802.1X authentication mode.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Configure the AKM mode.
akm mode { dot1x | private-psk | psk | anonymous-dot1x }
By default, no AKM mode is configured.
Setting the security information element
About this task
Perform this task to enable an AP to set the security information element (security IE) bit in beacon and probe responses to notify clients of its security capabilities.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the security IE.
security-ie { osen | rsn | wpa }
By default, no security IE is set.
Setting the cipher suite
About this task
The following cipher suites are available:
· WEP (WEP40, WEP104, or WEP128).
· CCMP.
· TKIP.
Restrictions and guidelines
When WEP128 is configured, you cannot set CCMP or TKIP.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the cipher suite.
cipher-suite { ccmp | tkip | wep40 | wep104 | wep128 }
By default, no cipher suite is set.
Setting the PSK
Restrictions and guidelines
The PSK must be set if the AKM mode is PSK. If you configure the PSK when the AKM mode is 802.1X, the WLAN service template can be enabled but the PSK configuration does not take effect.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the PSK.
preshared-key { pass-phrase | raw-key } { cipher | simple } string
By default, no PSK is set.
Setting the KDF
About this task
KDFs are used by 802.11i networks to generate PTKs and GTKs. KDFs include HMAC-SHA1 and HMAC-SHA256 algorithms. The HMAC-SHA256 algorithm is more secure than the HMAC-SHA1 algorithm.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the KDF.
key-derivation { sha1 | sha256 | sha1-and-sha256 }
By default, the HMAC-SHA1 algorithm is set.
Configuring GTK update
About this task
The system generates the GTK during key negotiation if the AKM, security IE, and cipher suite are configured. This feature updates the GTK to enhance key security based on the following updating modes:
· Time-based—The GTK is updated at the specified interval.
· Packet-based—The GTK is updated after the specified number of packets is sent.
· Offline-triggered—The GTK is updated when a client in the basic service set (BSS) goes offline.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable GTK update.
gtk-rekey enable
By default, GTK update is enabled.
4. Choose the options to configure as needed:
¡ Configure a GTK update method.
gtk-rekey method { packet-based [ packet ] | time-based [ time ] }
By default, the GTK is updated at intervals of 86400 seconds. The default packet quantity is 10000000 for packet-based GTK update.
¡ Enable offline-triggered GTK update.
gtk-rekey client-offline enable
By default, offline-triggered GTK update is disabled.
Configuring PTK update
About this task
The system generates the PTK during key negotiation when the AKM, security IE, and cipher suite are configured. This feature updates the PTK after the PTK lifetime expires.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable PTK update.
ptk-rekey enable
By default, PTK update is enabled.
4. Set the PTK lifetime.
ptk-lifetime time
By default, the PTK lifetime is 43200 seconds.
Setting the TKIP MIC failure hold time
About this task
After configuring the TKIP, you can configure the TKIP MIC failure hold time. If the AP detects two MIC failures within the MIC failure hold time, it disassociates all clients for 60 seconds.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the TKIP MIC failure hold time.
tkip-cm-time time
By default, the TKIP MIC failure hold time is 0. The AP does not take any countermeasures.
Setting the WEP key
Restrictions and guidelines
The WEP key can be used to encrypt all packets for pre-RSNA networks and encrypt multicast packets for 802.11i networks. If the WEP key is not set, a pre-RSNA network does not encrypt packets and an 802.11i network uses the negotiated GTK to encrypt multicast packets.
Do not apply WEP key 4 if dynamic WEP is enabled.
In the 802.11i mechanism, key 1 is the negotiated key. To apply a WEP key, specify a WEP key whose ID is not 1.
The applied WEP key takes effect only when the key length matches the requirements of the specified cipher suite. For more information, see WLAN Command Reference.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Set the WEP key.
wep key key-id { wep40 | wep104 | wep128 } { pass-phrase | raw-key } { cipher | simple } string
By default, no WEP key is set.
4. (Optional.) Apply the WEP key.
wep key-id { 1 | 2 | 3 | 4 }
By default, WEP key 1 is applied.
Configuring 802.11w management frame protection
About this task
When 802.11w management frame protection is disabled, network access is available for all clients, but management frame protection is not performed. When 802.11w management frame protection is enabled, network access and management frame protection availability varies by management frame protection mode.
· Optional mode—Network access is available for all clients, but management frame protection is performed only for clients that support management frame protection.
· Mandatory mode—Network access and management frame protection are available only for clients that support management frame protection.
Restrictions and guidelines
802.11w management frame protection takes effect only for a network that uses the 802.11i mechanism and is configured with the CCMP cipher suite and RSN security IE.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable management frame protection.
pmf { optional | mandatory }
By default, management frame protection is disabled.
4. Set the interval for sending SA query requests.
pmf saquery retrytimeout timeout
By default, the interval for sending SA query requests is 200 milliseconds.
5. Set the maximum transmission attempts for SA query requests.
pmf saquery retrycount count
By default, the maximum retransmission attempt number is 4 for SA query requests.
6. Set the association comeback time.
pmf association-comeback time
By default, the association comeback time is 1 second.
Enabling dynamic WEP
About this task
If dynamic WEP is enabled, the keys used for packet encryption depend on whether a WEP key is configured.
· If a WEP key is configured, dynamic WEP uses the configured WEP key as the multicast and broadcast WEP key. The negotiated unicast WEP has an ID of 4 and uses the cipher suite length setting.
· If no WEP key is configured, the length for both dynamic WEP keys is 104 bits. The negotiated unicast WEP key has an ID of 4. The generated multicast and broadcast WEP key has an ID of 1.
Restrictions and guidelines
Dynamic WEP must be used with the 802.1X authentication mode.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable dynamic WEP.
wep mode dynamic
By default, dynamic WEP is disabled.
Enabling password failure limit
About this task
This feature enables the system to add a client to the dynamic blacklist if the number of the client's password failures reaches the failure threshold within the specified detection period. For more information about the dynamic blacklist, see "Configuring WLAN access."
Restrictions and guidelines
This feature takes effect only when the AKM mode is PSK or private PSK.
This feature takes effect only on clients coming online after the feature is enabled.
The system restarts failure calculation if the STAMGR process restarts.
Procedure
1. Enter system view.
system-view
2. Enable password failure limit.
wlan password-failure-limit enable [ detection-period detection-period ] [ failure-threshold failure-threshold ]
By default, password failure limit is disabled.
Configuring PPSK authentication
Enabling Oasis PPSK authentication
About this task
This feature enables clients to use private pre-shared keys (PPSKs) configured on the Oasis platform for WLAN access.
With this feature enabled, clients must first pass bypass or MAC authentication, and then enter the PPSK password to access a WLAN. The device will generate binding entries between client MAC addresses and PPSK passwords at client association.
Restrictions and guidelines
Make sure the service template has been disabled before you configure this feature.
Oasis PPSK authentication must be used together with bypass or MAC authentication.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable Oasis PPSK authentication.
private-psk cloud enable
By default, Oasis PPSK authentication is disabled.
Enabling PPSK fail-permit
About this task
With Oasis PPSK authentication enabled, clients and devices must connect to the Oasis platform for authentication. PPSK fail-permit allows clients to bypass the Oasis platform and access the WLAN when the Oasis platform is unavailable.
If the Oasis platform becomes unavailable, PPSK fail-permit provides the following functions:
· Allows online clients to stay online until the MAC-password binding entries expire. When the MAC-password binding entries expire, the device logs all online clients.
· Allows clients whose MAC-password binding entries have not expired to re-access the WLAN.
· Allows clients that have a correct PPSK password but have never come online to access the WLAN.
Restrictions and guidelines
Make sure the service template has been disabled before you configure this feature.
Procedure
1. Enter system view.
system-view
2. Enter WLAN service template view.
wlan service-template service-template-name
3. Enable PPSK fail-permit.
private-psk fail-permit enable
By default, PPSK fail-permit is enabled.
Enabling SNMP notifications for WLAN security
About this task
To report critical WLAN security events to an NMS, enable SNMP notifications for WLAN security. For WLAN security event notifications to be sent correctly, you must also configure SNMP as described in Network Management and Monitoring Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for WLAN security.
snmp-agent trap enable wlan usersec
By default, SNMP notifications are disabled for WLAN security.
Display and maintenance commands for WLAN security
For more information about the following display commands, see "WLAN access commands."
Execute display commands in any view.
|
Task |
Command |
|
Display client information. |
display wlan client [ ap ap-name [ radio radio-id ] | mac-address mac-address | service-template service-template-name ] [ verbose ] |
|
Display WLAN service template information. |
display wlan service-template [ service-template-name ] [ verbose ] |
|
Display private pre-shared key (PPSK) password information. |
display wlan private-psk cloud-password [ password-id ] [ verbose ] |
|
Display MAC-password bindings. |
display wlan private-psk cloud-password mac-binding [ password-id ] |
WLAN security configuration examples
Example: Configuring shared key authentication
Network configuration
As shown in Figure 9, the switch functions as a DHCP server to assign IP addresses to the AP and client. Configure shared key authentication to enable the client to access the network by using WEP key 12345.
Procedure
# Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
# Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
# Configure a WEP40 plaintext key of 12345 as WEP key 2, and apply WEP key 2.
[AC-wlan-st-service1] cipher-suite wep40
[AC-wlan-st-service1] wep key 2 wep40 pass-phrase simple 12345
[AC-wlan-st-service1] wep key-id 2
# Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
# Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
# Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : Not configured
Security IE : Not configured
Cipher suite : WEP40
WEP key ID : 2
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : Bypass
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
Example: Configuring PSK authentication and bypass authentication
Network configuration
As shown in Figure 10, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure open system authentication and bypass authentication.
· Configure the client to use preshared key 12345678 to access the network.
Procedure
1. Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
2. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
3. Configure WLAN security for service template service1:
# Configure the PSK AKM mode and the 12345678 plaintext key.
[AC-wlan-st-service1] akm mode psk
[AC-wlan-st-service1] preshared-key pass-phrase simple 12345678
# Configure CCMP as the cipher suite and WPA as the security IE.
[AC-wlan-st-service1] cipher-suite ccmp
[AC-wlan-st-service1] security-ie wpa
4. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
5. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
6. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : PSK
Security IE : WPA
Cipher suite : CCMP
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : Bypass
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
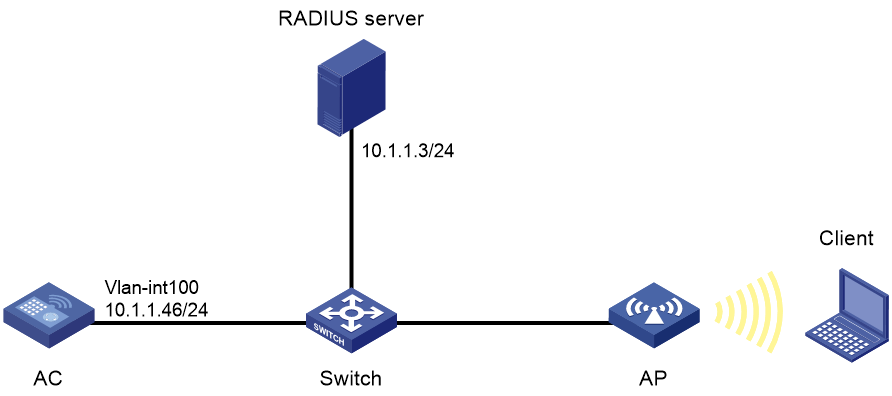
Example: Configuring PSK authentication and MAC authentication
Network configuration
As shown in Figure 11, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure open system authentication and MAC authentication so that the client can access the network by using login username abc and password 123.
· Configure the client to use preshared key 12345678 to access the network.
Procedure
1. Configure a username of abc and a password of 123 on the RADIUS server and make sure the RADIUS server and AC can reach each other. (Details not shown.)
2. Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
3. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
4. Configure WLAN security for service template service1:
# Configure the PSK AKM mode and the 12345678 plaintext key.
[AC-wlan-st-service1] akm mode psk
[AC-wlan-st-service1] preshared-key pass-phrase simple 12345678
# Configure CCMP as the cipher suite and WPA as the security IE.
[AC-wlan-st-service1] cipher-suite ccmp
[AC-wlan-st-service1] security-ie wpa
# Configure MAC authentication.
[AC-wlan-st-service1] client-security authentication-mode mac
5. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
6. Configure a RADIUS scheme:
# Create a RADIUS scheme named radius1 and enter its view.
[AC] radius scheme radius1
# Specify the primary authentication server and accounting server.
[AC-radius-radius1] primary authentication 10.1.1.3 1812
[AC-radius-radius1] primary accounting 10.1.1.3 1813
# Set the shared keys for authentication and accounting to 12345678 in plaintext.
[AC-radius-radius1] key authentication simple 12345678
[AC-radius-radius1] key accounting simple 12345678
# Set the format for the usernames sent to the RADIUS server based on the RADIUS server configuration:
¡ Exclude domain names from the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format without-domain
[Device-radius-rs1] quit
¡ Include domain names in the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format with-domain
[Device-radius-rs1] quit
7. Create an ISP domain named dom1 and configure a RADIUS scheme for the ISP domain.
[AC] domain dom1
[AC-isp-dom1] authentication lan-access radius-scheme radius1
[AC-isp-dom1] authorization lan-access radius-scheme radius1
[AC-isp-dom1] accounting lan-access radius-scheme radius1
[AC-isp-dom1] quit
8. Configure an ISP domain of dom1, a username of abc, and password 123 for the user.
[AC] mac-authentication mac domain dom1
[AC] mac-authentication user-name-format fixed account abc password simple 123
9. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
10. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
|
|
NOTE: For more information about the AAA and RADIUS commands in this section, see Security Command Reference. |
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : PSK
Security IE : WPA
Cipher suite : CCMP
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : MAC
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
Example: Configuring 802.1X AKM
Network configuration
As shown in Figure 12, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure open system authentication and 802.1X authentication so that the client can access the network by using login username abcdef and password 123456.
· Configure 802.1X as the AKM mode.
Procedure
2. Configure the 802.1X client.
<AC> system-view
[AC] dot1x
[AC] dot1x authentication-method eap
3. Create a WLAN service template named service1.
[AC] wlan service-template service1
4. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
5. Configure WLAN security for service template service1:
# Configure 802.1X as the AKM mode.
[AC-wlan-st-service1] akm mode dot1x
# Configure CCMP as the cipher suite and WPA as the security IE.
[AC-wlan-st-service1] cipher-suite ccmp
[AC-wlan-st-service1] security-ie wpa
# Configure the 802.1X authentication mode.
[AC-wlan-st-service1] client-security authentication-mode dot1x
6. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
7. Configure a RADIUS scheme:
# Create a RADIUS scheme named radius1 and enter its view.
[AC] radius scheme radius1
# Specify the primary authentication server and accounting server.
[AC-radius-radius1] primary authentication 10.1.1.3 1812
[AC-radius-radius1] primary accounting 10.1.1.3 1813
# Set the shared keys for authentication and accounting to 12345 in plaintext.
[AC-radius-radius1] key authentication simple 12345
[AC-radius-radius1] key accounting simple 12345
# Set the format for the usernames sent to the RADIUS server based on the RADIUS server configuration:
¡ Exclude domain names from the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format without-domain
[Device-radius-rs1] quit
¡ Include domain names in the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format with-domain
[Device-radius-rs1] quit
8. Create an ISP domain named dom1 and configure a RADIUS scheme for the ISP domain.
[AC] domain dom1
[AC-isp-dom1] authentication lan-access radius-scheme radius1
[AC-isp-dom1] authorization lan-access radius-scheme radius1
[AC-isp-dom1] accounting lan-access radius-scheme radius1
[AC-isp-dom1] quit
9. Configure ISP domain dom1 as the default ISP domain.
[AC] domain default enable dom1
10. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
11. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
|
|
NOTE: For more information about the AAA and RADIUS commands in this section, see Security Command Reference. |
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : dot1x
Security IE : WPA
Cipher suite : CCMP
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : 802.1X
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
Example: Configuring management frame protection
Network configuration
As shown in Figure 13, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure the client to use preshared key 12345678 to access the network.
· Configure the CCMP cipher suite, RSN security IE, and management frame protection.
Procedure
1. Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
2. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
3. Configure management frame protection:
# Enable management frame protection in optional mode.
[AC-wlan-st-service1] pmf optional
# Set the KDF to sha1-and-sha256.
[AC-wlan-st-service1] key-derivation sha1-and-sha256
4. Configure the 802.11i mechanism:
# Configure the PSK AKM mode and the 12345678 plaintext key.
[AC-wlan-st-service1] akm mode psk
[AC-wlan-st-service1] preshared-key pass-phrase simple 12345678
# Configure CCMP as the cipher suite and RSN as the security IE.
[AC-wlan-st-service1] cipher-suite ccmp
[AC-wlan-st-service1] security-ie rsn
5. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
6. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
7. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : PSK
Security IE : RSN
Cipher suite : CCMP
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : Bypass
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : SHA1-AND-SHA256
PMF status : Optional
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
# Use the display wlan client verbose command to verify the management frame protection negotiation results after a client comes online.
<AC> display wlan client verbose
Total number of clients: 1
MAC address : 5250-0012-0411
IPv4 address : 135.3.2.1
IPv6 address : N/A
Username : 11w
AID : 1
AP ID : 1
AP name : ap1
Radio ID : 1
SSID : service
BSSID : 1111-2222-3333
VLAN ID : 1
Sleep count : 147
Wireless mode : 802.11a
Channel bandwidth : 20MHz
SM power save : Disabled
Short GI for 20MHz : Not supported
Short GI for 40MHz : Not supported
Short GI for 80MHz : Supported
Short GI for 160/80+80MHz : Not supported
STBC RX capability : Not supported
STBC TX capability : Not supported
LDPC RX capability : Not supported
Beamformee STS capability : N/A
Number of Sounding Dimensions : N/A
SU beamformee capability : Not supported
MU beamformee capability : Not supported
Block Ack : TID 0 In
Supported VHT-MCS set : NSS1 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
NSS2 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
Support HT-MCS set : 0, 1, 2, 3, 4, 5, 6, 7,
8, 9, 10, 11, 12, 13, 14,
15
Supported rates : 1, 2, 5.5, 6, 9, 11,
12, 18, 24, 36, 48, 54 Mbps
QoS mode : WMM
Listen interval : 10
RSSI : 46
Rx/Tx rate : 39/65
Authentication method : Open system
Security mode : RSN
AKM mode : PSK
Cipher suite : CCMP
User authentication mode : Bypass
WPA3 status : Disabled
Authorization ACL ID : N/A
Authorization user profile : N/A
Authorization CAR : N/A
Roam status : N/A
Key derivation : SHA1
PMF status : Enabled
Forwarding policy name : N/A
Online time : 0days 0hours 2minutes 56seconds
FT status : Inactive
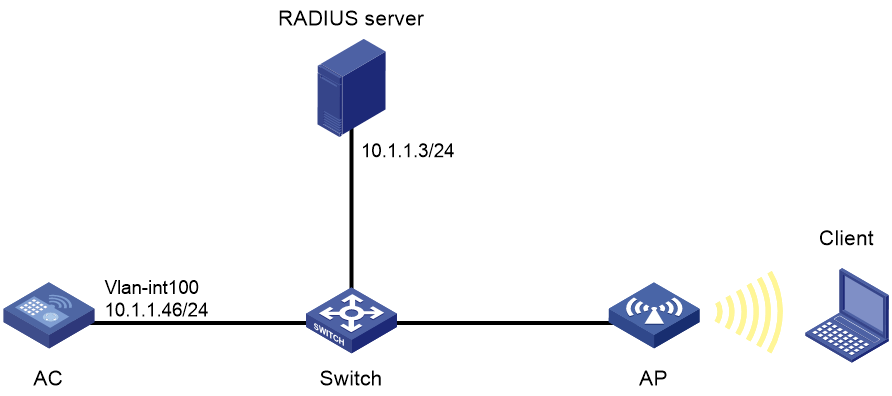
Example: Configuring dynamic WEP
Network configuration
As shown in Figure 14, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure open system authentication and 802.1X authentication so that the client can access the network by using login username abcdef and password 123456.
· Configure dynamic WEP.
Procedure
1. Configure a username of abcdef and a password of 123456 on the RADIUS server and make sure the RADIUS server and AC can reach each other. (Details not shown.)
2. Configure the 802.1X client. (Details not shown.)
3. Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
4. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
5. Enable dynamic WEP.
[AC-wlan-st-service1] wep mode dynamic
6. Configure the 802.1X authentication mode.
[AC-wlan-st-service1] client-security authentication-mode dot1x
7. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
8. Configure a RADIUS scheme:
# Create a RADIUS scheme named radius1 and enter its view.
[AC] radius scheme radius1
# Specify the primary authentication server and accounting server.
[AC-radius-radius1] primary authentication 10.1.1.3 1812
[AC-radius-radius1] primary accounting 10.1.1.3 1813
# Set the shared keys for authentication and accounting to 12345 in plaintext.
[AC-radius-radius1] key authentication simple 12345
[AC-radius-radius1] key accounting simple 12345
# Set the format for the usernames sent to the RADIUS server based on the RADIUS server configuration:
¡ Exclude domain names from the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format without-domain
[Device-radius-rs1] quit
¡ Include domain names in the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format with-domain
[Device-radius-rs1] quit
9. Create an ISP domain named dom1 and configure a RADIUS scheme for the ISP domain.
[AC] domain dom1
[AC-isp-dom1] authentication lan-access radius-scheme radius1
[AC-isp-dom1] authorization lan-access radius-scheme radius1
[AC-isp-dom1] accounting lan-access radius-scheme radius1
[AC-isp-dom1] quit
10. Configure ISP domain dom1 as the default ISP domain.
[AC] domain default enable dom1
11. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
12. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
|
|
NOTE: For more information about the AAA and RADIUS commands in this section, see Security Command Reference. |
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
VLAN ID : 1
AKM mode : Not configured
Security IE : Not configured
Cipher suite : WEP104
WEP key ID : 1
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : 802.1X
Intrusionprotection : Disabled
Intrusionprotection mode : Temporary-block
Temporary block time : 180 sec
Temporaryservicestop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0
Example: Configuring private PSK authentication and MAC authentication
Network configuration
As shown in Figure 15, the switch functions as a DHCP server to assign IP addresses to the AP and client.
· Configure the MAC authentication mode so that the client can access the network by using its MAC address as the login username and password.
· Configure the private PSK AKM mode so that the client can use its MAC address as the PSK.
Procedure
1. Configure a username of 00-23-12-45-67-7a and a password of 00-23-12-45-67-7a on the RADIUS server and make sure the RADIUS server and AC can reach each other. (Details not shown.)
2. Create a WLAN service template named service1.
<AC> system-view
[AC] wlan service-template service1
3. Specify an SSID of service for the service template.
[AC-wlan-st-service1] ssid service
4. Configure WLAN security for service template service1:
# Configure private PSK as the AKM mode.
[AC-wlan-st-service1] akm mode psk
# Configure CCMP as the cipher suite and WPA as the security IE.
[AC-wlan-st-service1] cipher-suite ccmp
[AC-wlan-st-service1] security-ie wpa
# Configure MAC authentication.
[AC-wlan-st-service1] client-security authentication-mode mac
5. Enable service template service1.
[AC-wlan-st-service1] service-template enable
[AC-wlan-st-service1] quit
6. Configure a RADIUS scheme:
# Create a RADIUS scheme named radius1 and enter its view.
[AC] radius scheme radius1
# Specify the primary authentication server and accounting server.
[AC-radius-radius1] primary authentication 10.1.1.3 1812
[AC-radius-radius1] primary accounting 10.1.1.3 1813
# Set the shared keys for authentication and accounting to 12345678 in plaintext.
[AC-radius-radius1] key authentication simple 12345678
[AC-radius-radius1] key accounting simple 12345678
# Set the format for the usernames sent to the RADIUS server based on the RADIUS server configuration:
¡ Exclude domain names from the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format without-domain
[Device-radius-rs1] quit
¡ Include domain names in the usernames sent to the RADIUS server.
[Device-radius-rs1] user-name-format with-domain
[Device-radius-rs1] quit
7. Create an ISP domain named dom1 and configure a RADIUS scheme for the ISP domain.
[AC] domain dom1
[AC-isp-dom1] authentication lan-access radius-scheme radius1
[AC-isp-dom1] authorization lan-access radius-scheme radius1
[AC-isp-dom1] accounting lan-access radius-scheme radius1
[AC-isp-dom1] quit
8. Configure the MAC address as the username and password for ISP domain dom1.
[AC] mac-authentication domain dom1
[AC] mac-authentication user-name-format mac-address with-hyphen lowercase
9. Create an AP named ap1 and specify the model and serial ID.
[AC] wlan ap ap1 model WA4320i-ACN
[AC-wlan-ap-ap1] serial-id 219801A0CNC138011454
10. Bind service template service1 to radio 1 of the AP and enable radio 1.
[AC-wlan-ap-ap1] radio 1
[AC-wlan-ap-ap1-radio-1] service-template service1
[AC-wlan-ap-ap1-radio-1] radio enable
[AC-wlan-ap-ap1-radio-1] return
|
|
NOTE: For more information about the AAA and RADIUS commands in this section, see Security Command Reference. |
Verifying the configuration
# Use the display wlan service-template command to verify that the WLAN service template has been configured correctly.
<AC> display wlan service-template service1 verbose
Service template name : service1
Description : Not configured
SSID : service
SSID-hide : Disabled
User-isolation : Disabled
Service template status : Enabled
Maximum clients per BSS : 64
Frame format : Dot3
Seamless roam status : Disabled
Seamless roam RSSI threshold : 50
Seamless roam RSSI gap : 20
VLAN ID : 1
AKM mode : Private-PSK
Security IE : WPA
Cipher suite : CCMP
TKIP countermeasure time : 0
PTK lifetime : 43200 sec
GTK rekey : Enabled
GTK rekey method : Time-based
GTK rekey time : 86400 sec
GTK rekey client-offline : Enabled
User authentication mode : MAC
Intrusion protection : Disabled
Intrusion protection mode : Temporary-block
Temporary block time : 180 sec
Temporary service stop time : 20 sec
Fail VLAN ID : Not configured
802.1X handshake : Disabled
802.1X handshake secure : Disabled
802.1X domain : Not configured
MAC-auth domain : Not configured
Max 802.1X users per BSS : 4096
Max MAC-auth users per BSS : 4096
802.1X re-authenticate : Disabled
Authorization fail mode : Online
Accounting fail mode : Online
Authorization : Permitted
Key derivation : N/A
PMF status : Disabled
Hotspot policy number : Not configured
Forward policy : Not configured
Forwarder : AC
FT status : Disabled
QoS trust : Port
QoS priority : 0