- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-MAC address table configuration | 134.03 KB |
Contents
Configuring the MAC address table
How a MAC address entry is created
MAC address table tasks at a glance
Configuring MAC address entries
About MAC address entry-based frame forwarding
Restrictions and guidelines for MAC address entry configuration
Prerequisites for MAC address entry configuration
Adding or modifying a static or dynamic MAC address entry
Adding or modifying a blackhole MAC address entry
Adding or modifying a multiport unicast MAC address entry
Setting the aging timer for dynamic MAC address entries
Disabling MAC address learning
About disabling MAC address learning
Disabling global MAC address learning
Disabling MAC address learning on an interface
Disabling MAC address learning on a VLAN
Setting the MAC learning limit
Setting the MAC learning limit on interfaces
Setting the MAC learning limit for a VLAN
Configuring the unknown frame forwarding rule after the MAC learning limit is reached
About unknown frame forwarding rule configuration
Configuring the device to forward unknown frames after the MAC learning limit for a VLAN is reached
Configuring MAC address move notifications and suppression
Enabling SNMP notifications for the MAC address table
Display and maintenance commands for MAC address table
MAC address table configuration examples
Example: Configuring the MAC address table
Configuring the MAC address table
About the MAC address table
An Ethernet device uses a MAC address table to forward frames. A MAC address entry includes a destination MAC address, an outgoing interface, and a VLAN ID. When the device receives a frame, it uses the destination MAC address of the frame to look for a match in the MAC address table.
· The device forwards the frame out of the outgoing interface in the matching entry if a match is found.
· The device floods the frame in the VLAN of the frame if no match is found.
How a MAC address entry is created
The entries in the MAC address table include entries automatically learned by the device and entries manually added.
MAC address learning
The device can automatically populate its MAC address table by learning the source MAC addresses of incoming frames on each interface.
The device performs the following operations to learn the source MAC address of incoming packets:
1. Checks the source MAC address (for example, MAC-SOURCE) of the frame.
2. Looks up the source MAC address in the MAC address table.
¡ The device updates the entry if an entry is found.
¡ The device adds an entry for MAC-SOURCE and the incoming port if no entry is found.
When the device receives a frame destined for MAC-SOURCE after learning this source MAC address, the device performs the following operations:
1. Finds the MAC-SOURCE entry in the MAC address table.
2. Forwards the frame out of the port in the entry.
The device performs the learning process for each incoming frame with an unknown source MAC address until the table is fully populated.
Manually configuring MAC address entries
Dynamic MAC address learning does not distinguish between illegitimate and legitimate frames, which can invite security hazards. When Host A is connected to Port A, a MAC address entry will be learned for the MAC address of Host A (for example, MAC A). When an illegal user sends frames with MAC A as the source MAC address to Port B, the device performs the following operations:
1. Learns a new MAC address entry with Port B as the outgoing interface and overwrites the old entry for MAC A.
2. Forwards frames destined for MAC A out of Port B to the illegal user.
As a result, the illegal user obtains the data of Host A. To improve the security for Host A, manually configure a static entry to bind Host A to Port A. Then, the frames destined for Host A are always sent out of Port A. Other hosts using the forged MAC address of Host A cannot obtain the frames destined for Host A.
Types of MAC address entries
A MAC address table can contain the following types of entries:
· Static entries—A static entry is manually added to forward frames with a specific destination MAC address out of the associated interface, and it never ages out. A static entry has higher priority than a dynamically learned one.
· Dynamic entries—A dynamic entry can be manually configured or dynamically learned to forward frames with a specific destination MAC address out of the associated interface. A dynamic entry might age out. A manually configured dynamic entry has the same priority as a dynamically learned one.
· Blackhole entries—A blackhole entry is manually configured and never ages out. A blackhole entry is configured for filtering out frames with a specific source or destination MAC address. For example, to block all frames destined for or sourced from a user, you can configure the MAC address of the user as a blackhole MAC address entry. A blackhole entry has higher priority than a dynamically learned one.
· Multiport unicast entries—A multiport unicast entry is manually added to send frames with a specific unicast destination MAC address out of multiple ports, and it never ages out. A multiport unicast entry has higher priority than a dynamically learned one.
A static, blackhole, or multiport unicast MAC address entry can overwrite a dynamic MAC address entry, but not vice versa. A static entry, a blackhole entry, and a multiport unicast entry cannot overwrite one another.
MAC address table tasks at a glance
All MAC address table configuration tasks are optional.
To configure the MAC address table, perform the following tasks:
· Configuring MAC address entries
¡ Adding or modifying a static or dynamic MAC address entry
¡ Adding or modifying a blackhole MAC address entry
¡ Adding or modifying a multiport unicast MAC address entry
· Setting the aging timer for dynamic MAC address entries
· Configuring MAC address learning
¡ Disabling MAC address learning
¡ Setting the MAC learning limit
¡ Configuring the unknown frame forwarding rule after the MAC learning limit is reached
· Configuring MAC address move notifications and suppression
· Enabling SNMP notifications for the MAC address table
Configuring MAC address entries
About MAC address entry-based frame forwarding
A frame whose source MAC address matches different types of MAC address entries is processed differently.
|
Type |
Description |
|
Static MAC address entry |
Forwards the frame according to the destination MAC address regardless of whether the frame's ingress interface is the same as that in the entry. |
|
Multiport unicast MAC address entry |
Forwards the frame out of the outgoing interfaces in the matching multiport unicast MAC address entry. |
|
Blackhole MAC address entry |
Drops the frame. |
|
Dynamic MAC address entry |
· Learns the MAC address of the frames received on a different interface from that in the entry and overwrites the original entry. · Forwards the frame received on the same interface as that in the entry and updates the aging timer for the entry. |
Restrictions and guidelines for MAC address entry configuration
You cannot add a dynamic MAC address entry if a learned entry already exists with a different outgoing interface for the MAC address.
The manually configured static, blackhole, and multiport unicast MAC address entries cannot survive a reboot if you do not save the configuration. The manually configured dynamic MAC address entries are lost upon reboot whether or not you save the configuration.
Prerequisites for MAC address entry configuration
Before manually configuring a MAC address entry for an interface, make sure the VLAN in the entry has been created.
Adding or modifying a static or dynamic MAC address entry
Adding or modifying a static or dynamic MAC address entry globally
1. Enter system view.
system-view
2. Add or modify a static or dynamic MAC address entry.
mac-address { dynamic | static } mac-address interface interface-type interface-number vlan vlan-id
By default, no MAC address entry is configured globally.
Make sure you have assigned the interface to the VLAN.
Adding or modifying a static or dynamic MAC address entry on an interface
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Add or modify a static or dynamic MAC address entry.
mac-address { dynamic | static } mac-address vlan vlan-id
By default, no MAC address entry is configured on an interface.
Make sure you have assigned the interface to the VLAN.
Adding or modifying a blackhole MAC address entry
1. Enter system view.
system-view
2. Add or modify a blackhole MAC address entry.
mac-address blackhole mac-address vlan vlan-id
By default, no blackhole MAC address entry is configured.
Adding or modifying a multiport unicast MAC address entry
About this task
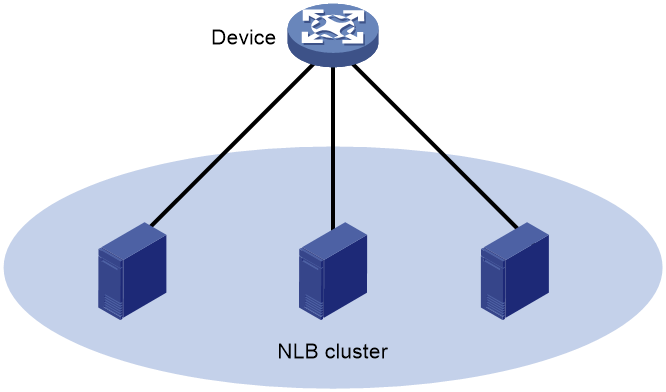
You can configure a multiport unicast MAC address entry to associate a unicast destination MAC address with multiple ports. The frame with a destination MAC address matching the entry is sent out of multiple ports.
For example, in NLB unicast mode (see Figure 1):
· All servers within a cluster uses the cluster's MAC address as their own address.
· Frames destined for the cluster are forwarded to every server in the group.
In this case, you can configure a multiport unicast MAC address entry on the device connected to the server group. Then, the device forwards the frame destined for the server group to every server through all ports connected to the servers within the cluster.
You can configure a multiport unicast MAC address entry globally or on an interface.
Configuring a multiport unicast MAC address entry globally
1. Enter system view.
system-view
2. Add or modify a multiport unicast MAC address entry.
mac-address multiport mac-address interface interface-list vlan vlan-id
By default, no multiport unicast MAC address entry is configured globally.
Make sure you have assigned the interface to the VLAN.
Configuring a multiport unicast MAC address entry on an interface
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Add the interface to a multiport unicast MAC address entry.
mac-address multiport mac-address vlan vlan-id
By default, no multiport unicast MAC address entry is configured on an interface.
Make sure you have assigned the interface to the VLAN.
Setting the aging timer for dynamic MAC address entries
About this task
For security and efficient use of table space, the MAC address table uses an aging timer for each dynamic MAC address entry. If a dynamic MAC address entry is not updated before the aging timer expires, the device deletes the entry. This aging mechanism ensures that the MAC address table can promptly update to accommodate latest network topology changes.
A stable network requires a longer aging interval, and an unstable network requires a shorter aging interval.
An aging interval that is too long might cause the MAC address table to retain outdated entries. As a result, the MAC address table resources might be exhausted, and the MAC address table might fail to update its entries to accommodate the latest network changes.
An interval that is too short might result in removal of valid entries, which would cause unnecessary floods and possibly affect the device performance.
To reduce floods on a stable network, set a long aging timer or disable the timer to prevent dynamic entries from unnecessarily aging out. Reducing floods improves the network performance. Reducing flooding also improves the security because it reduces the chances for a data frame to reach unintended destinations.
Procedure
1. Enter system view.
system-view
2. Set the aging timer for dynamic MAC address entries.
mac-address timer { aging seconds | no-aging }
The default setting is 300 seconds.
Disabling MAC address learning
About disabling MAC address learning
MAC address learning is enabled by default. To prevent the MAC address table from being saturated when the device is experiencing attacks, disable MAC address learning. For example, you can disable MAC address learning to prevent the device from being attacked by a large amount of frames with different source MAC addresses.
After MAC address learning is disabled, existing dynamic MAC address entries can age out.
Disabling global MAC address learning
Restrictions and guidelines
After you disable global MAC address learning, the device cannot learn MAC addresses on any interfaces.
Procedure
1. Enter system view.
system-view
2. Disable global MAC address learning.
undo mac-address mac-learning enable
By default, global MAC address learning is enabled.
Disabling MAC address learning on an interface
About this task
When global MAC address learning is enabled, you can disable MAC address learning on a single interface.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Disable MAC address learning on the interface.
undo mac-address mac-learning enable
By default, MAC address learning is enabled on an interface.
Disabling MAC address learning on a VLAN
About this task
When global MAC address learning is enabled, you can disable MAC address learning on a per-VLAN basis.
Procedure
1. Enter system view.
system-view
2. Enter VLAN view.
vlan vlan-id
3. Disable MAC address learning on the VLAN.
undo mac-address mac-learning enable
By default, MAC address learning on the VLAN is enabled.
Setting the MAC learning limit
Setting the MAC learning limit on interfaces
About this task
This feature limits the MAC address table size. A large MAC address table will degrade forwarding performance.
Restrictions and guidelines
The MAC learning limit does not control the number of MAC addresses learned in voice VLANs. For more information, see "Configuring voice VLANs."
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Set the MAC learning limit on the interface.
mac-address max-mac-count count
By default, the MAC learning limit on an interface is 1024.
Setting the MAC learning limit for a VLAN
About this task
You can limit the number of MAC addresses that can be learned for a VLAN. A large MAC address table will degrade forwarding performance.
Procedure
1. Enter system view.
system-view
2. Enter VLAN view.
vlan vlan-id
3. Set the MAC leaning limit for the VLAN.
mac-address max-mac-count count
By default, the MAC learning limit for a VLAN is 2048.
Configuring the unknown frame forwarding rule after the MAC learning limit is reached
In this document, unknown frames refer to frames whose source MAC addresses are not in the MAC address table.
About unknown frame forwarding rule configuration
You can enable or disable forwarding of unknown frames after the MAC learning limit is reached.
Configuring the device to forward unknown frames after the MAC learning limit on an interface is reached
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Configure the device to forward unknown frames received on the interface after the MAC learning limit on the interface is reached.
mac-address max-mac-count enable-forwarding
By default, the device can forward unknown frames received on an interface after the MAC learning limit on the interface is reached.
Configuring the device to forward unknown frames after the MAC learning limit for a VLAN is reached
1. Enter system view.
system-view
2. Enter VLAN view.
vlan vlan-id
3. Configure the device to forward unknown frames received on interfaces in the VLAN after the MAC learning limit for the VLAN is reached.
mac-address max-mac-count enable-forwarding
By default, the device can forward unknown frames received on interfaces in a VLAN after the MAC learning limit for the VLAN is reached.
Configuring MAC address move notifications and suppression
About this task
The outgoing interface for a MAC address entry learned on interface A is changed to interface B when the following conditions exist:
· Interface B receives a packet with the MAC address as the source MAC address.
· Interface B belongs to the same VLAN as interface A.
In this case, the MAC address is moved from interface A to interface B, and a MAC address move occurs.
The MAC address move notifications feature enables the device to output MAC address move logs when MAC address moves are detected.
If a MAC address is continuously moved between the two interfaces, Layer 2 loops might occur. To detect and locate loops, you can view the MAC address move information. To display the MAC address move records after the device is started, use the display mac-address mac-move command.
If the system detects that MAC address moves occur frequently on an interface, you can configure MAC address move suppression to shut the interface down. The interface automatically goes up after a suppression interval. Or, you can manually bring up the interface.
Restrictions and guidelines
After you configure MAC address move notifications, the system sends only log messages to the information center module. If the device is also configured with the snmp-agent trap enable mac-address command, the system also sends SNMP notifications to the SNMP module.
Procedure
1. Enter system view.
system-view
2. Enable MAC address move notifications and optionally specify a MAC move detection interval.
mac-address notification mac-move [ interval interval ]
By default, MAC address move notifications are disabled.
3. (Optional.) Set MAC address move suppression parameters.
mac-address notification mac-move suppression { interval interval | threshold threshold }
By default, the suppression interval is 30 seconds, and the suppression threshold is 3.
For the MAC address move suppression parameters to take effect, enable the MAC address move suppression on a port.
4. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
5. Enable MAC address move suppression.
mac-address notification mac-move suppression
By default, MAC address move suppression is disabled.
Enabling SNMP notifications for the MAC address table
About this task
To report critical MAC address move events to an NMS, enable SNMP notifications for the MAC address table. For MAC address move event notifications to be sent correctly, you must also configure SNMP on the device.
When SNMP notifications are disabled for the MAC address table, the device sends the generated logs to the information center. To display the logs, configure the log destination and output rule configuration in the information center.
For more information about SNMP and information center configuration, see the network management and monitoring configuration guide for the device.
Procedure
1. Enter system view.
system-view
2. Enable SNMP notifications for the MAC address table.
snmp-agent trap enable mac-address [ mac-move ]
By default, SNMP notifications are enabled for the MAC address table.
When SNMP notifications are disabled for the MAC address table, syslog messages are sent to notify important events on the MAC address table module.
Display and maintenance commands for MAC address table
Execute display commands in any view.
|
Task |
Command |
|
Display MAC address table information. |
display mac-address [ mac-address [ vlan vlan-id ] | [ [ dynamic | static ] [ interface interface-type interface-number ] | blackhole | multiport ] [ vlan vlan-id ] [ count ] | nickname nickname ] |
|
Display the aging timer for dynamic MAC address entries. |
display mac-address aging-time |
|
Display the system or interface MAC address learning state. |
display mac-address mac-learning [ interface interface-type interface-number ] |
|
Display the MAC address move records. |
In standalone mode: display mac-address mac-move display mac-address mac-move [ slot slot-number ] |
|
Display MAC address statistics. |
display mac-address statistics |
MAC address table configuration examples
Example: Configuring the MAC address table
Network configuration
As shown in Figure 2:
· Host A at MAC address 000f-e235-dc71 is connected to GigabitEthernet 1/0 of Device and belongs to VLAN 1.
· Host B at MAC address 000f-e235-abcd, which behaved suspiciously on the network, also belongs to VLAN 1.
Configure the MAC address table as follows:
· To prevent MAC address spoofing, add a static entry for Host A in the MAC address table of Device.
· To drop all frames destined for Host B, add a blackhole MAC address entry for Host B.
· Set the aging timer to 500 seconds for dynamic MAC address entries.
Procedure
# Add a static MAC address entry for MAC address 000f-e235-dc71 on GigabitEthernet 1/0 that belongs to VLAN 1.
<Device> system-view
[Device] mac-address static 000f-e235-dc71 interface gigabitethernet 1/0 vlan 1
# Add a blackhole MAC address entry for MAC address 000f-e235-abcd that belongs to VLAN 1.
[Device] mac-address blackhole 000f-e235-abcd vlan 1
# Set the aging timer to 500 seconds for dynamic MAC address entries.
[Device] mac-address timer aging 500
Verifying the configuration
# Display the static MAC address entries for GigabitEthernet 1/0.
[Device] display mac-address static interface gigabitethernet 1/0
MAC Address VLAN ID State Port/Nickname Aging
000f-e235-dc71 1 Static GE1/0 N
# Display the blackhole MAC address entries.
[Device] display mac-address blackhole
MAC Address VLAN ID State Port/Nickname Aging
000f-e235-abcd 1 Blackhole N/A N
# Display the aging time of dynamic MAC address entries.
[Device] display mac-address aging-time
MAC address aging time: 500s.