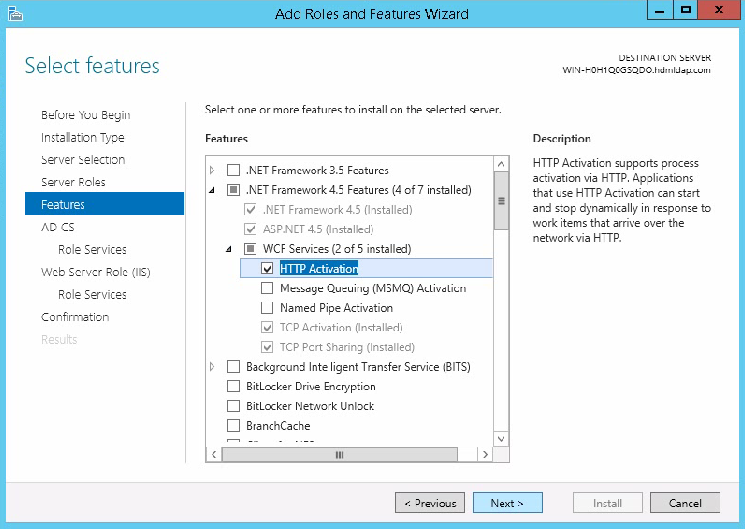
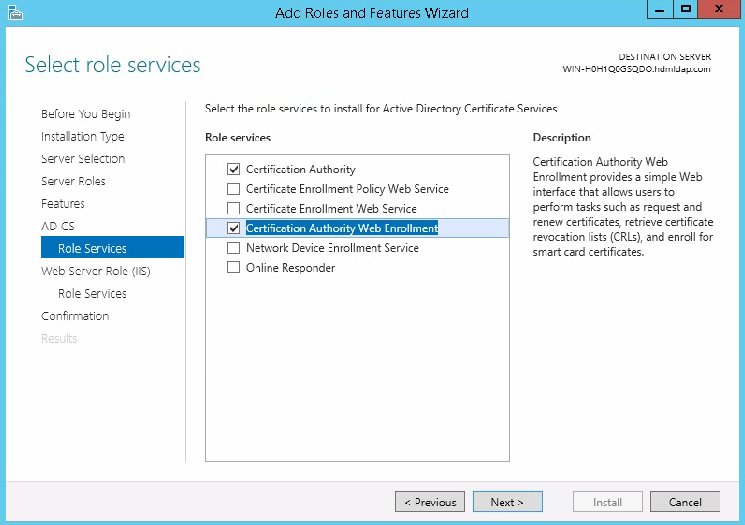
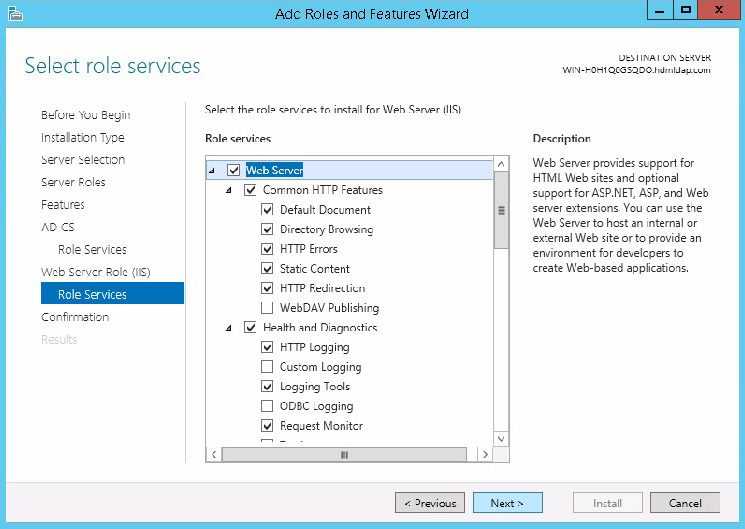
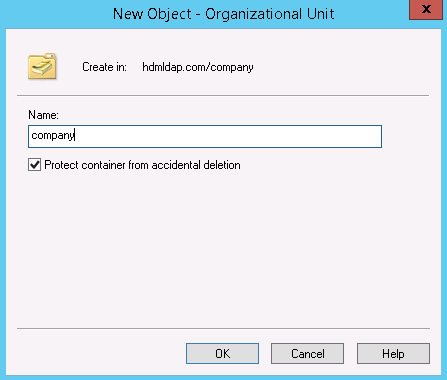
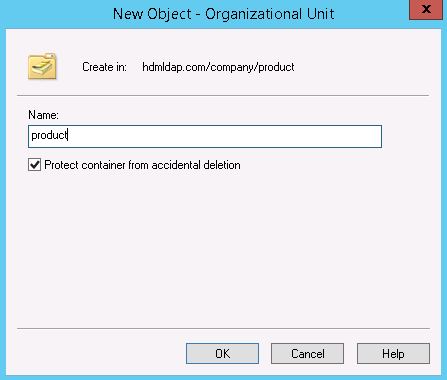
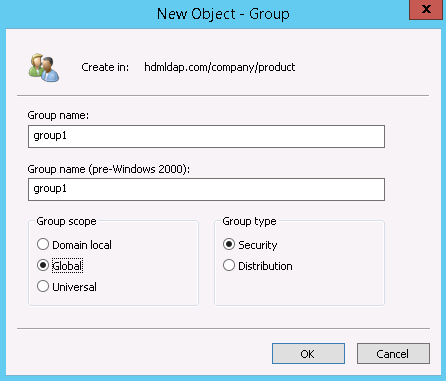
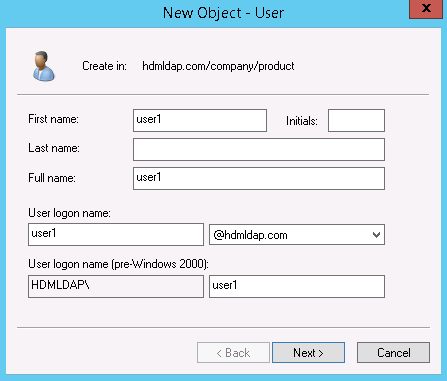
- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Text | 11.27 MB |
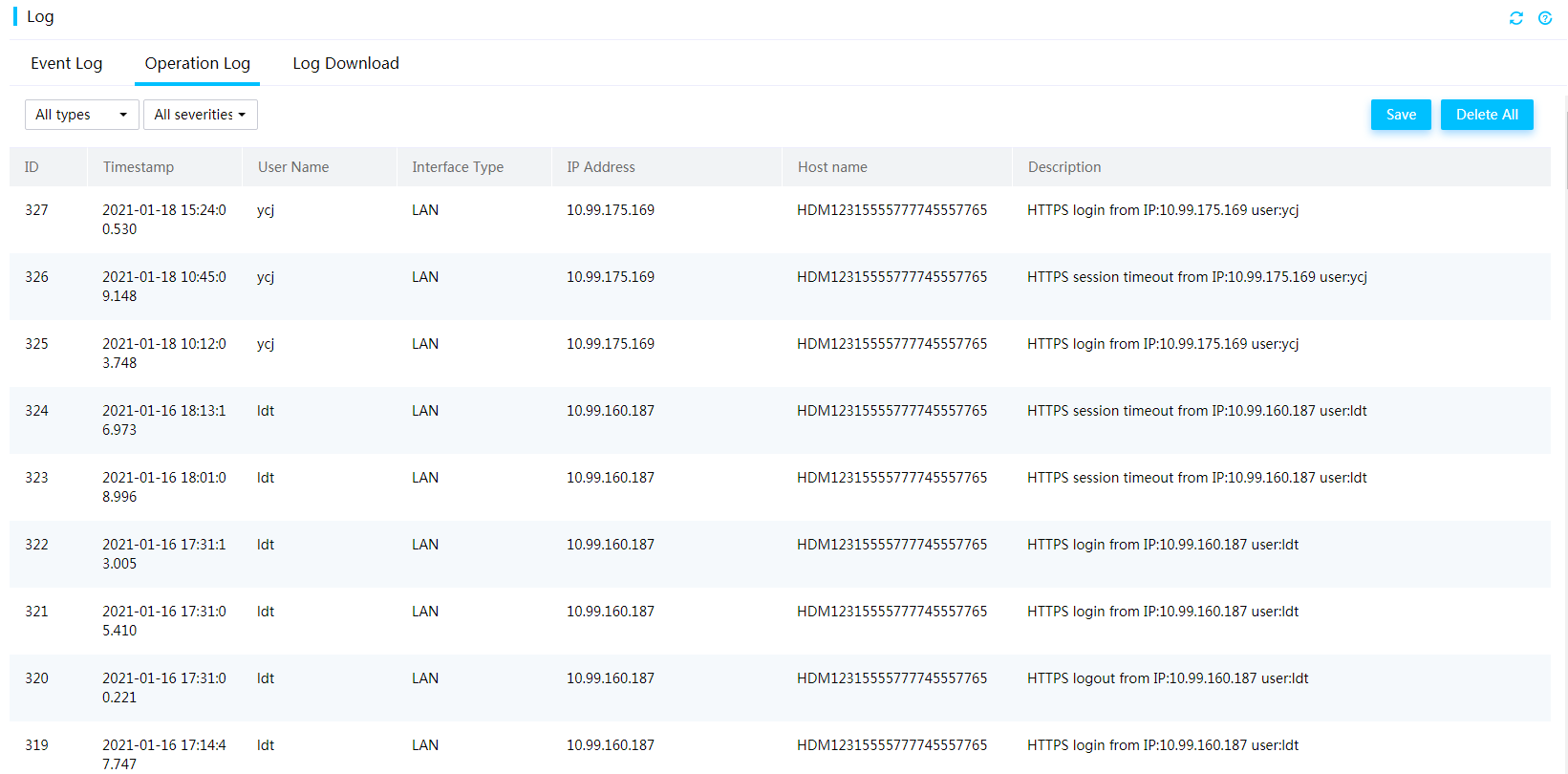
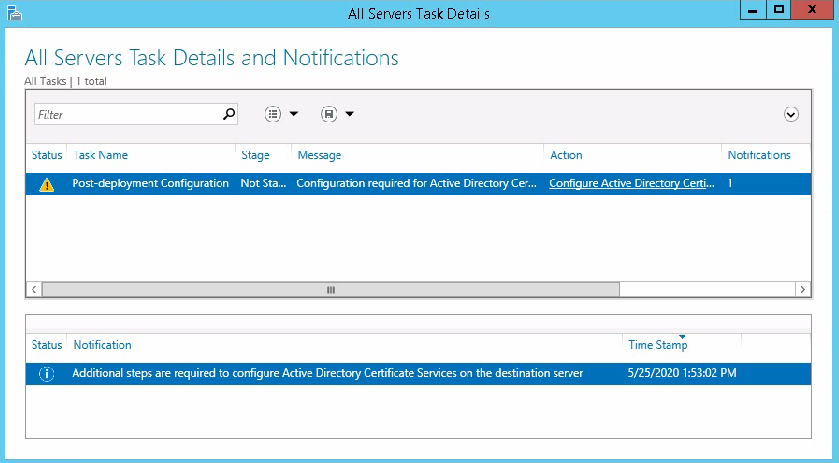
HDM Web interface access failures
Sign in to HDM for rack servers
Sign in to HDM for blade servers and AE modules
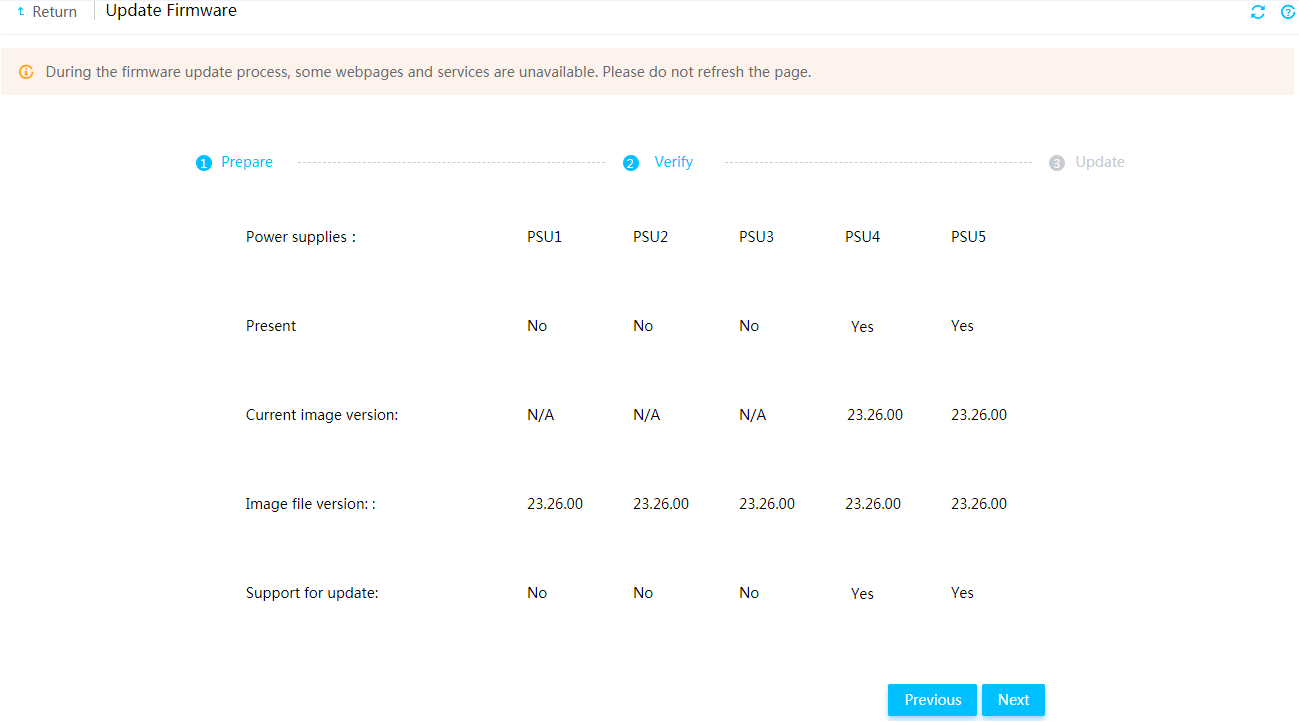
View summary information about the device
View information about other components
View storage summary information
View storage controller information
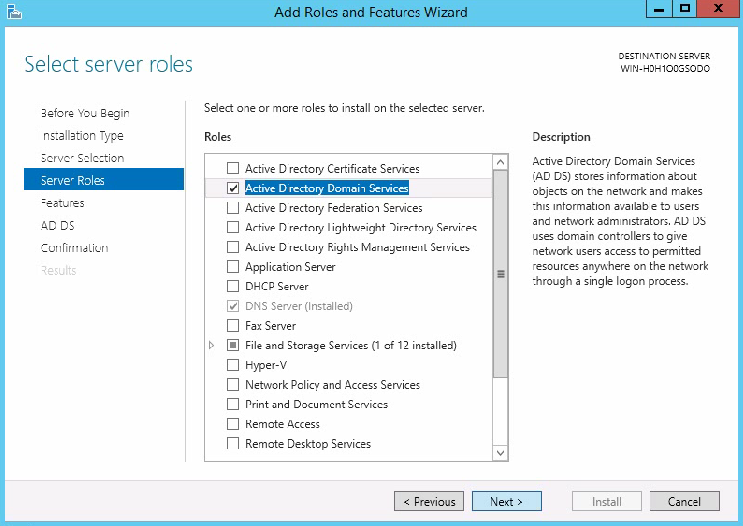
Power on or power off the server
Set the power supply operating mode
View power consumption information
Configure processor power states
View status and readings of temperature sensors
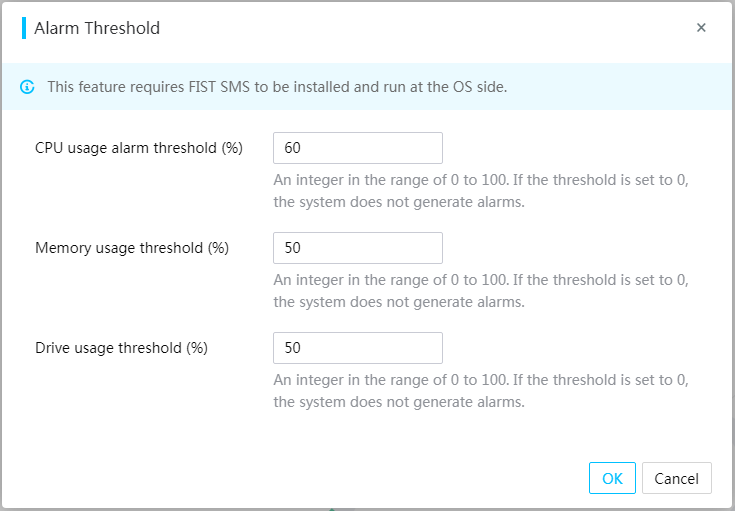
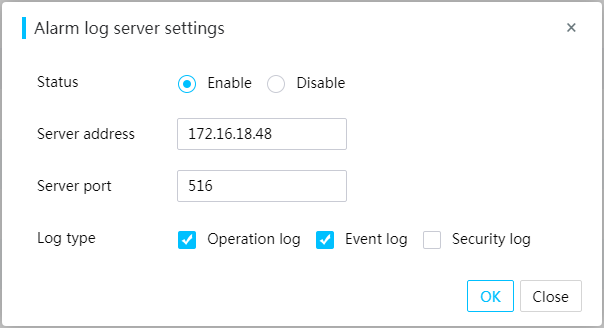
Set resource usage alarm thresholds
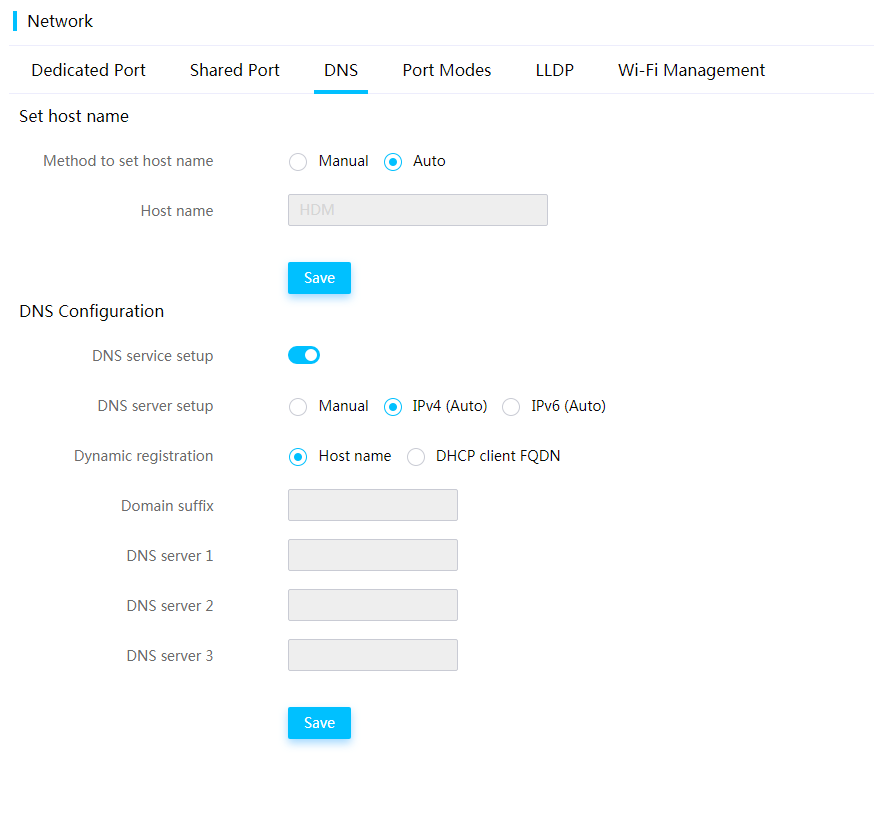
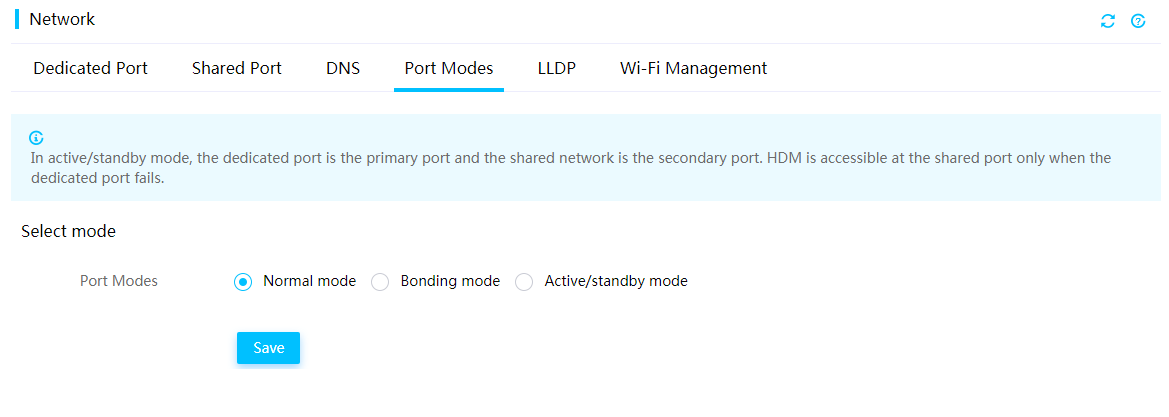
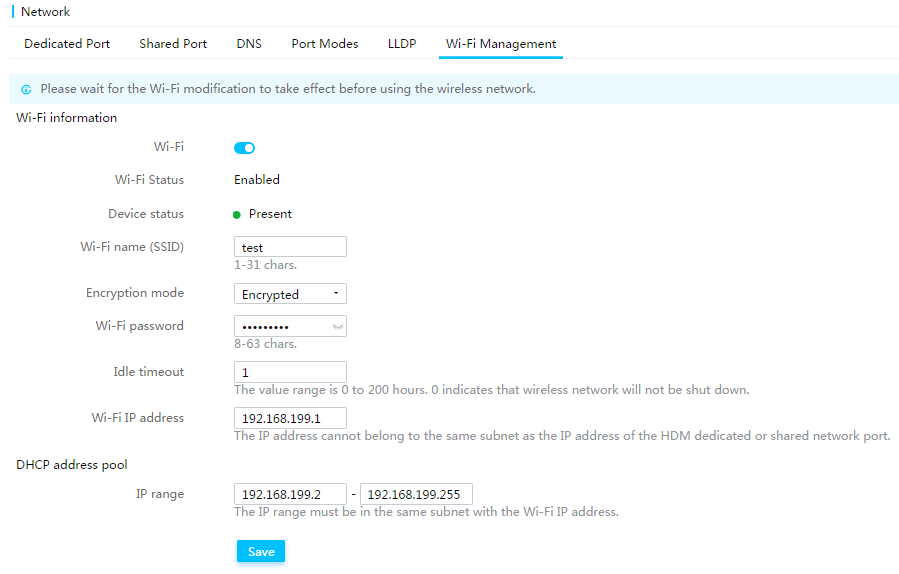
General restrictions and guidelines for network configuration
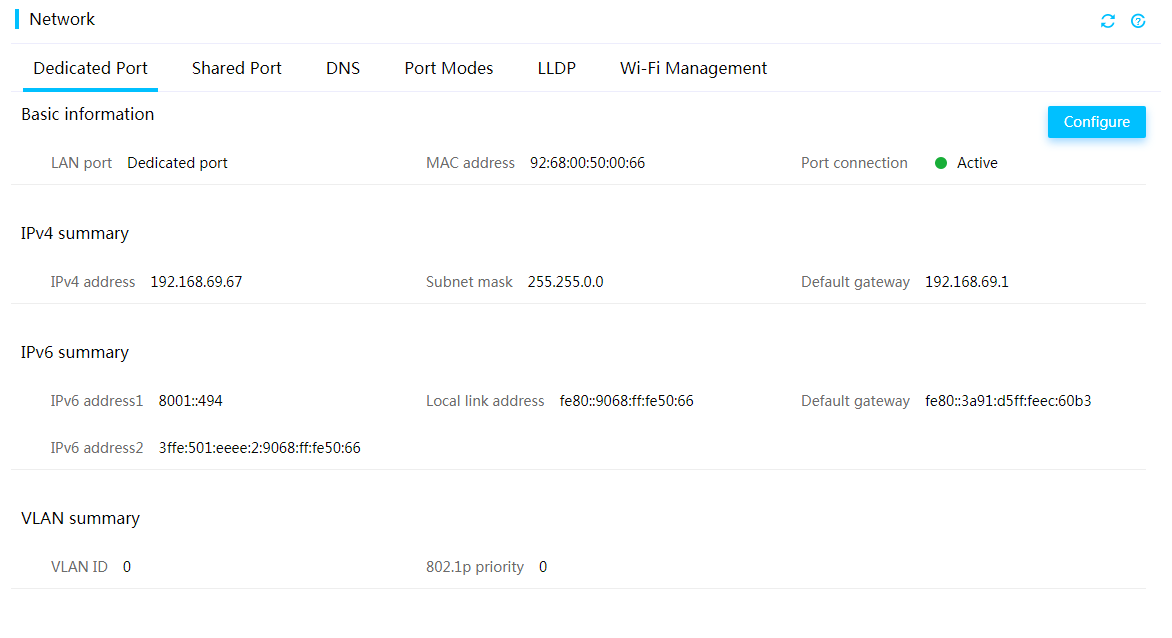
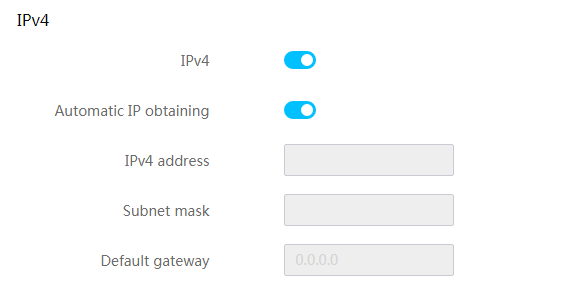
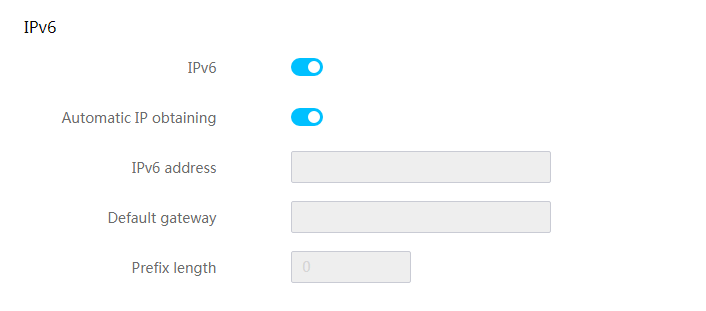
View dedicated network port information
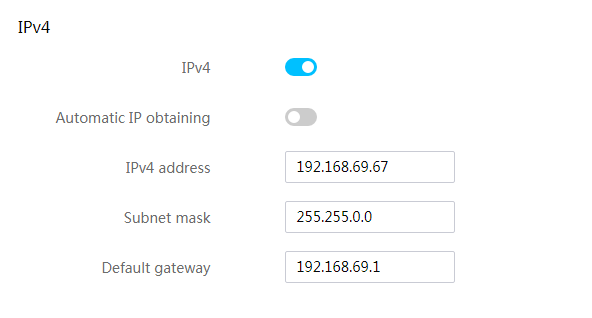
Configure the dedicated network port
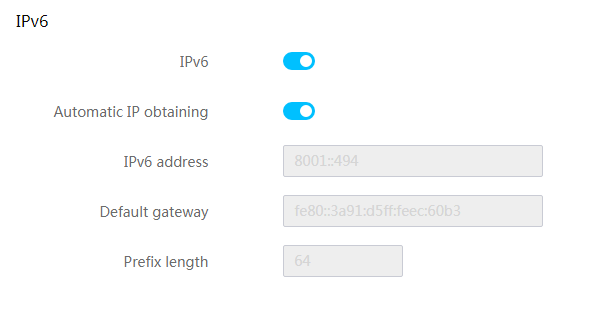
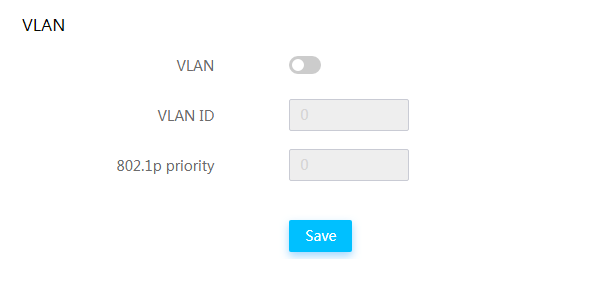
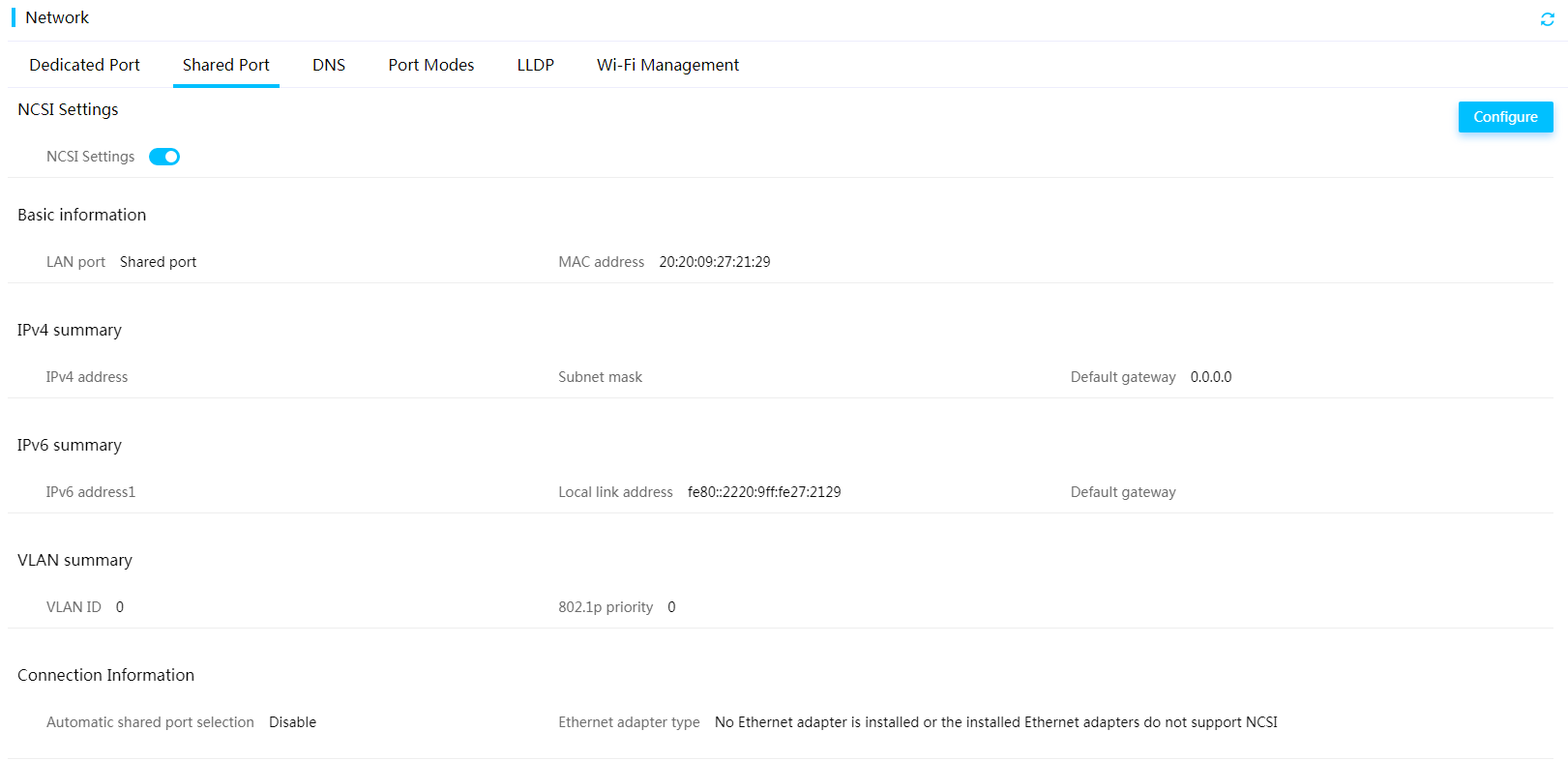
View shared network port information
Configure the shared network port
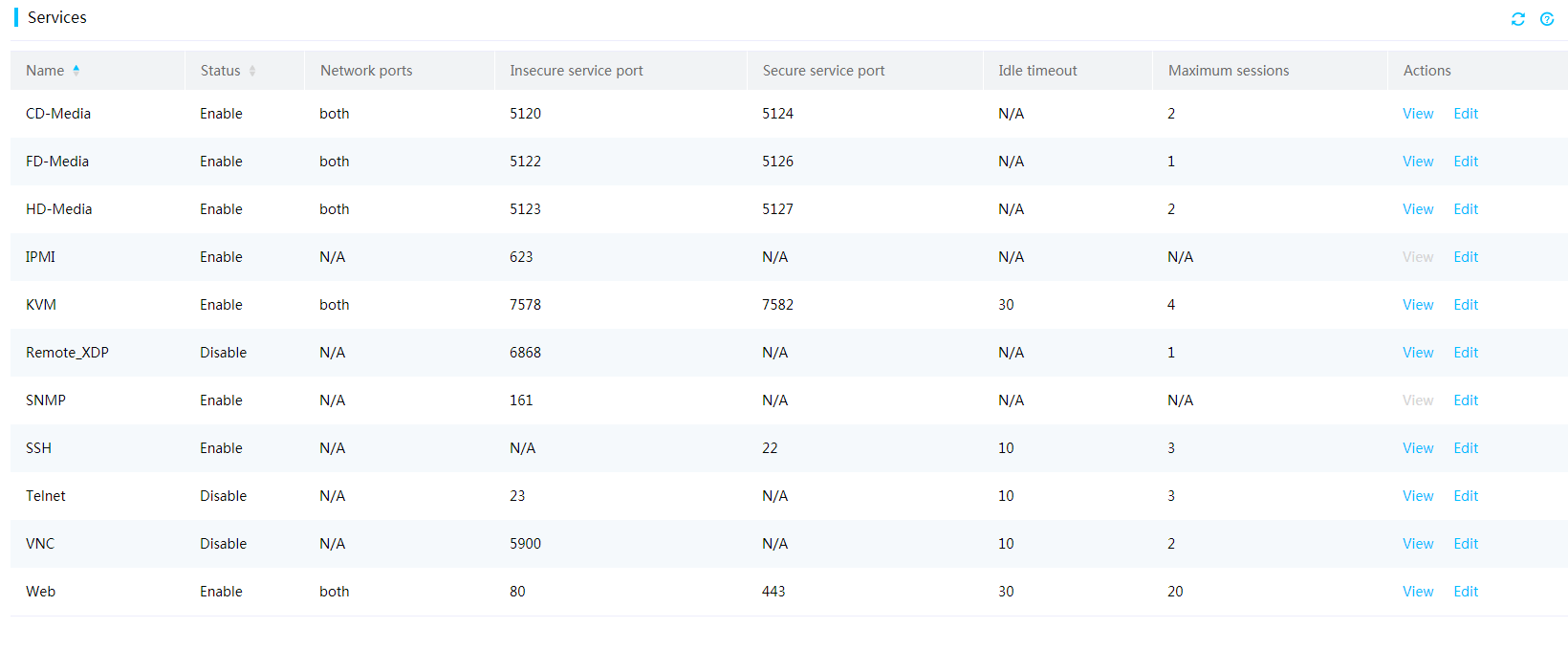
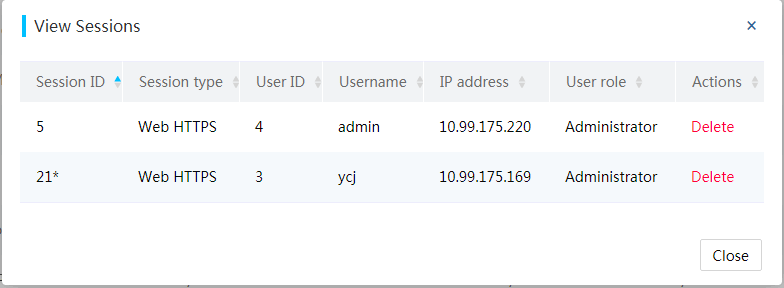
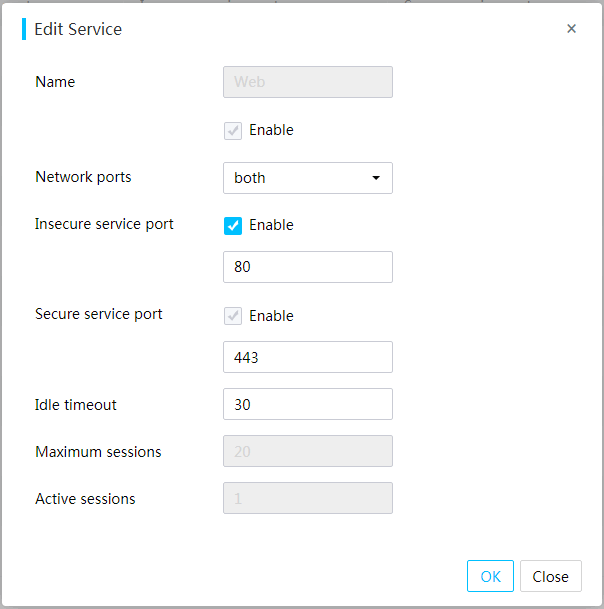
View services and user sessions
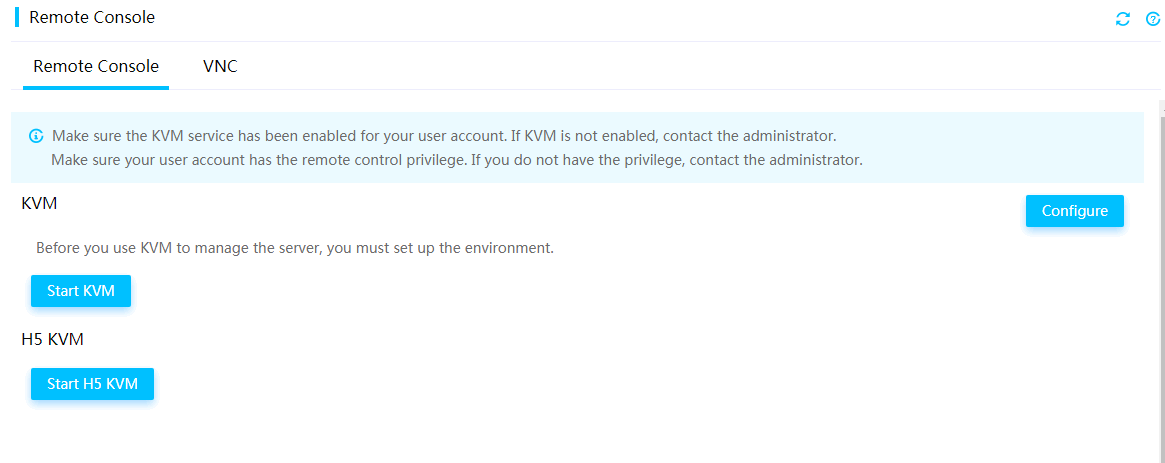
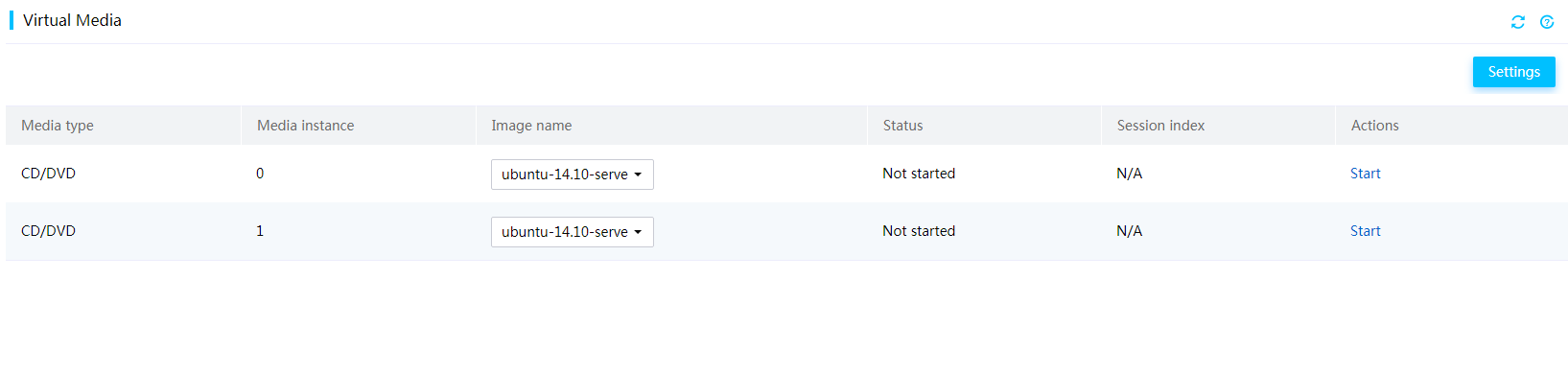
Launch a KVM or H5 KVM remote console
Operate the server from H5 KVM
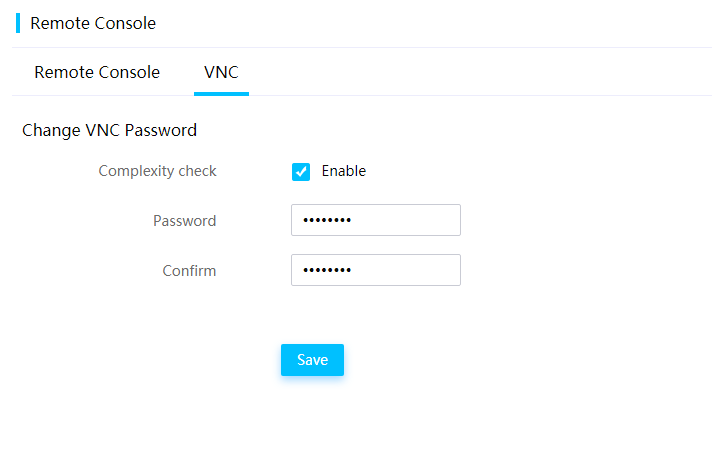
Configure the VNC login password
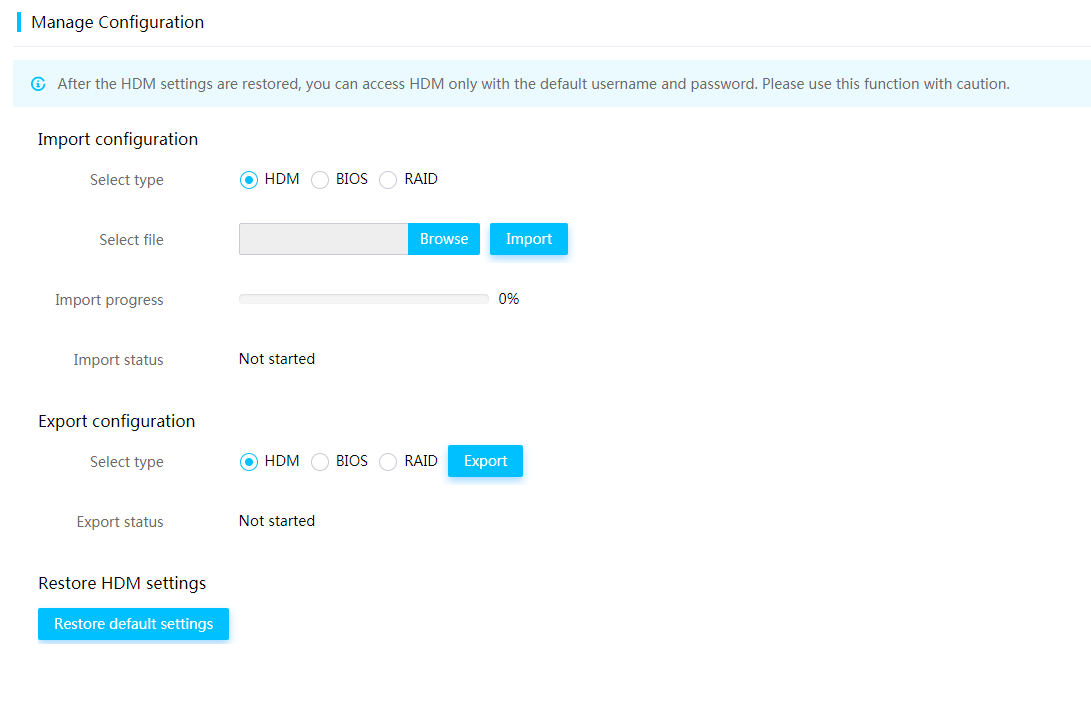
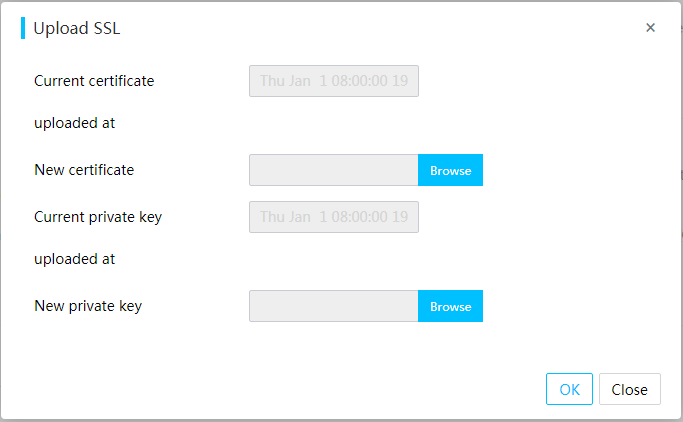
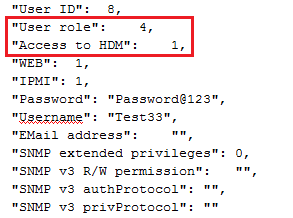
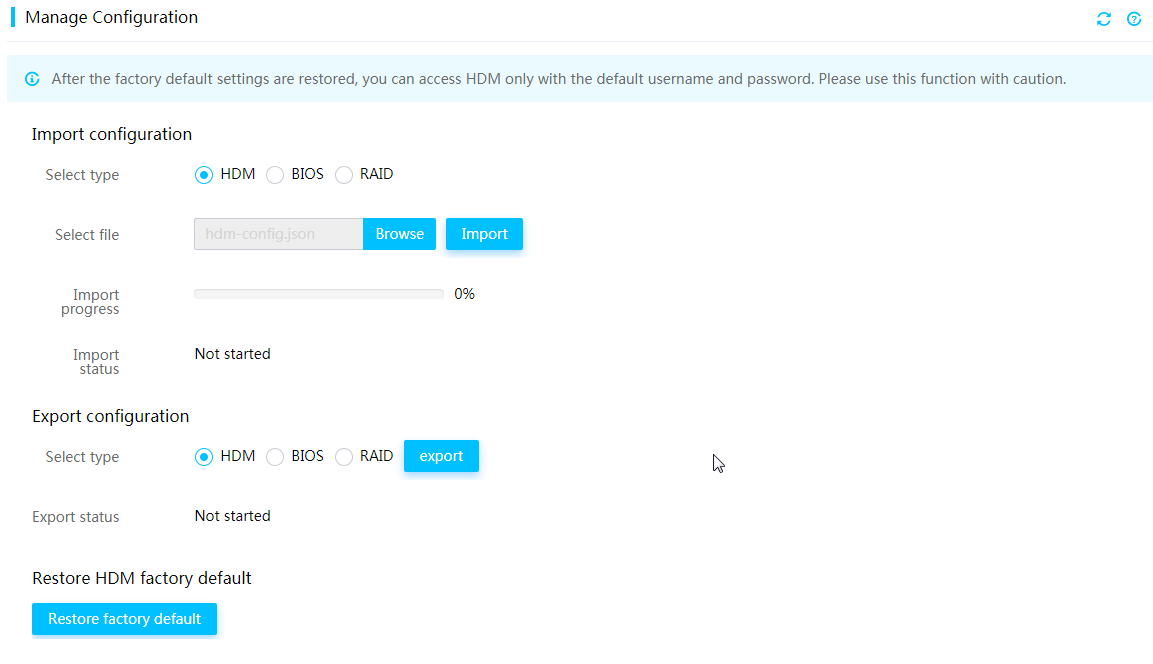
Export HDM, BIOS, or RAID configuration
Import HDM, BIOS, or RAID configuration
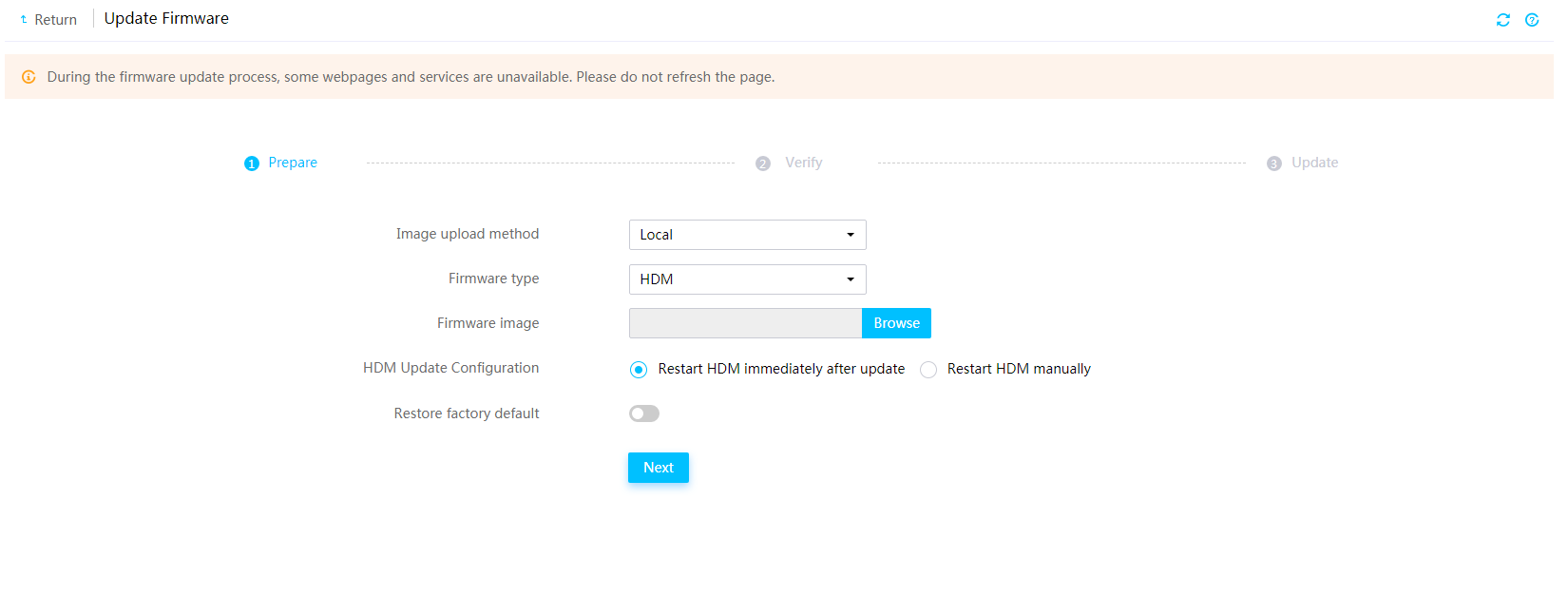
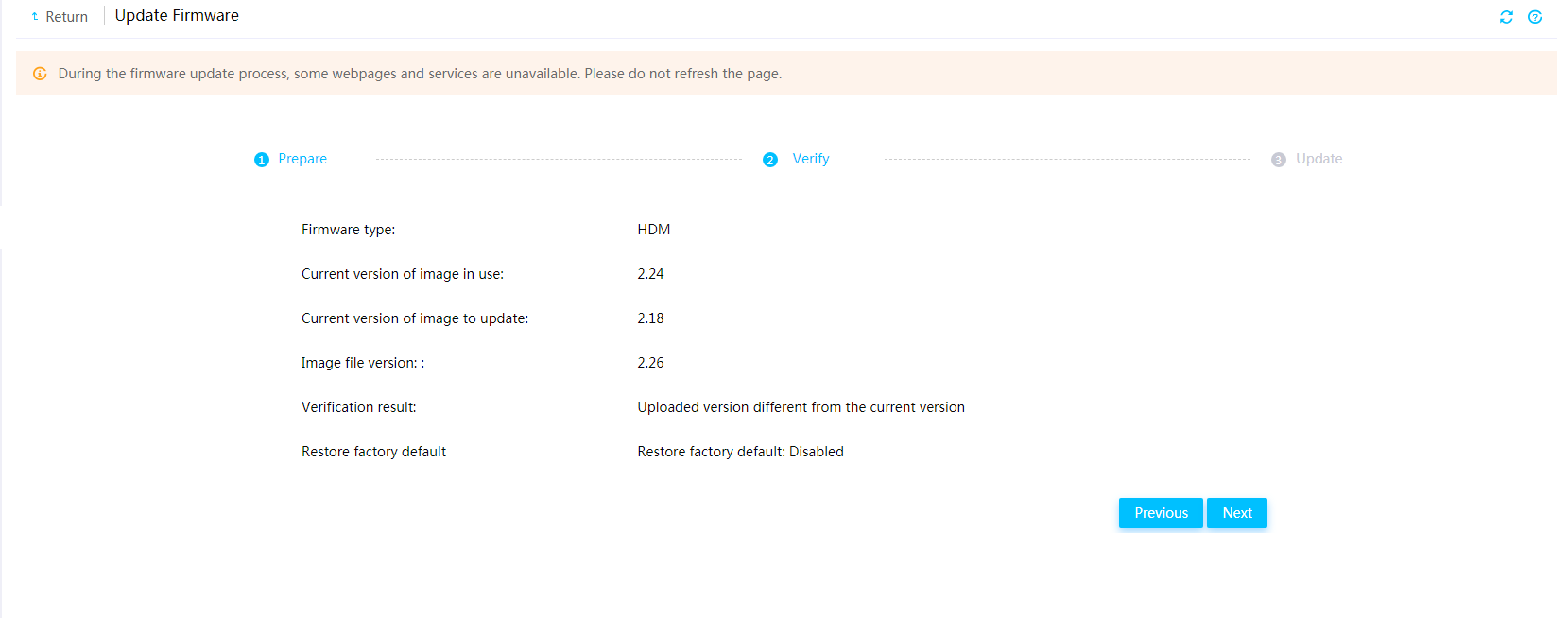
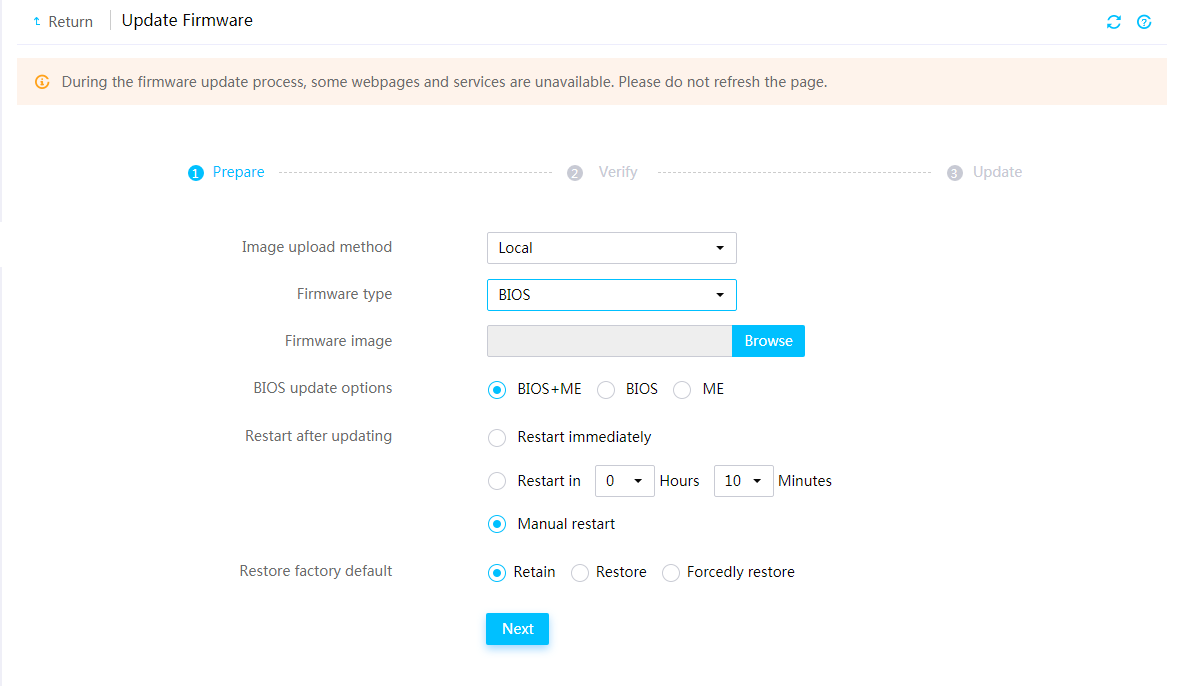
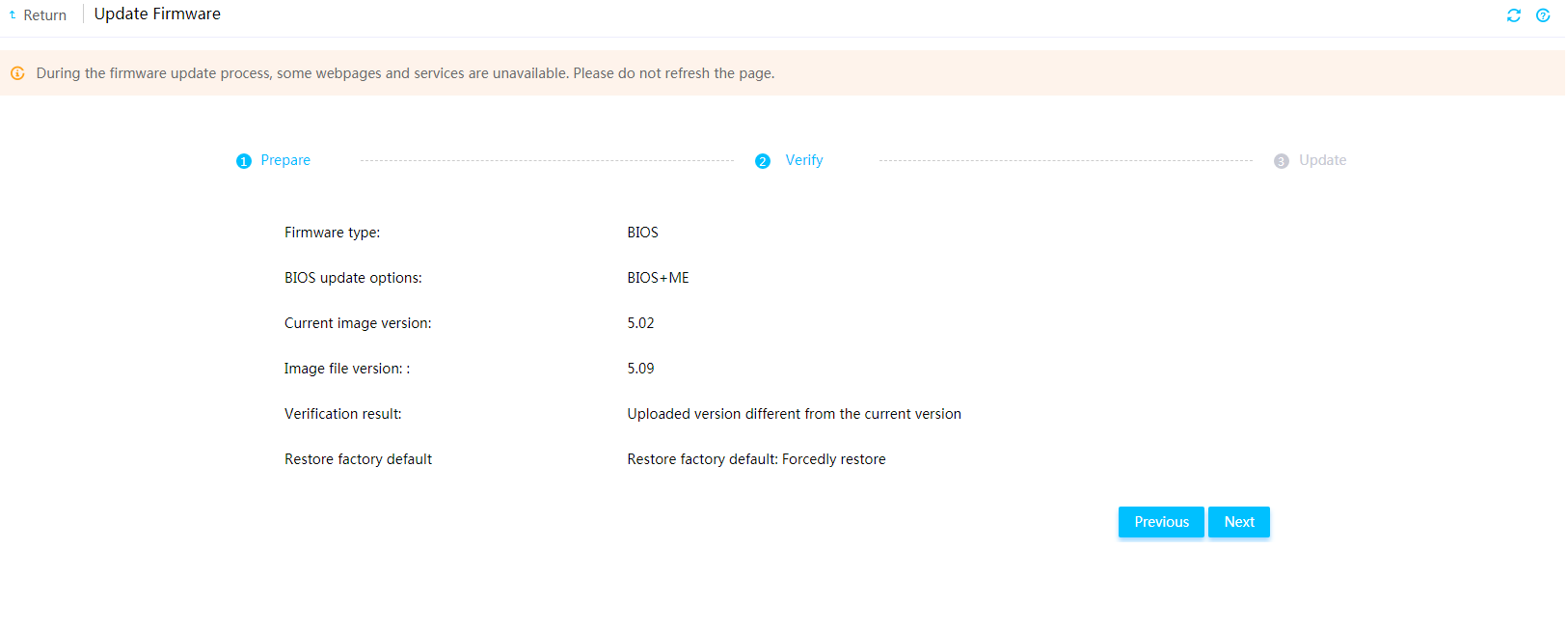
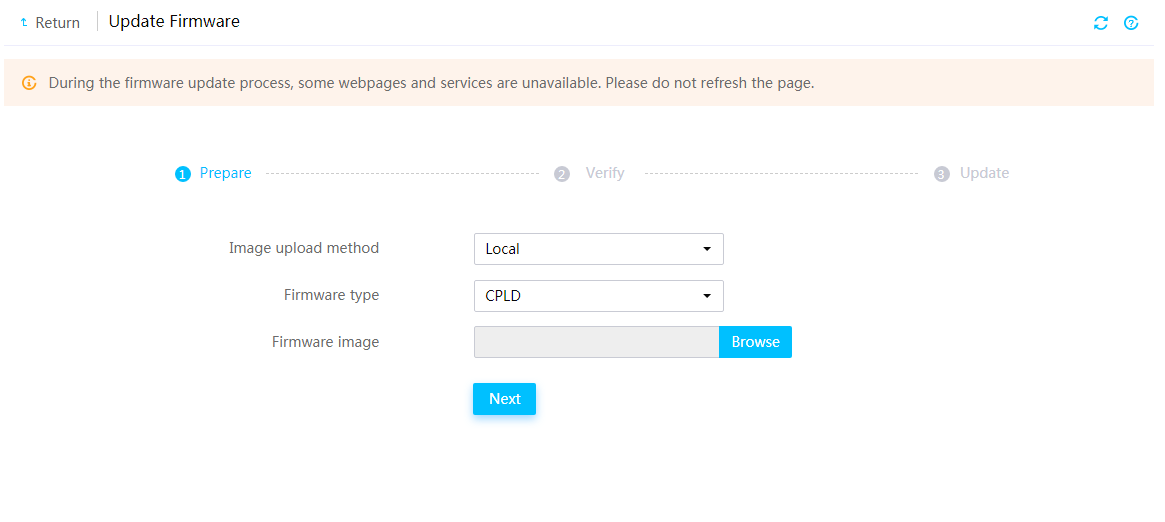
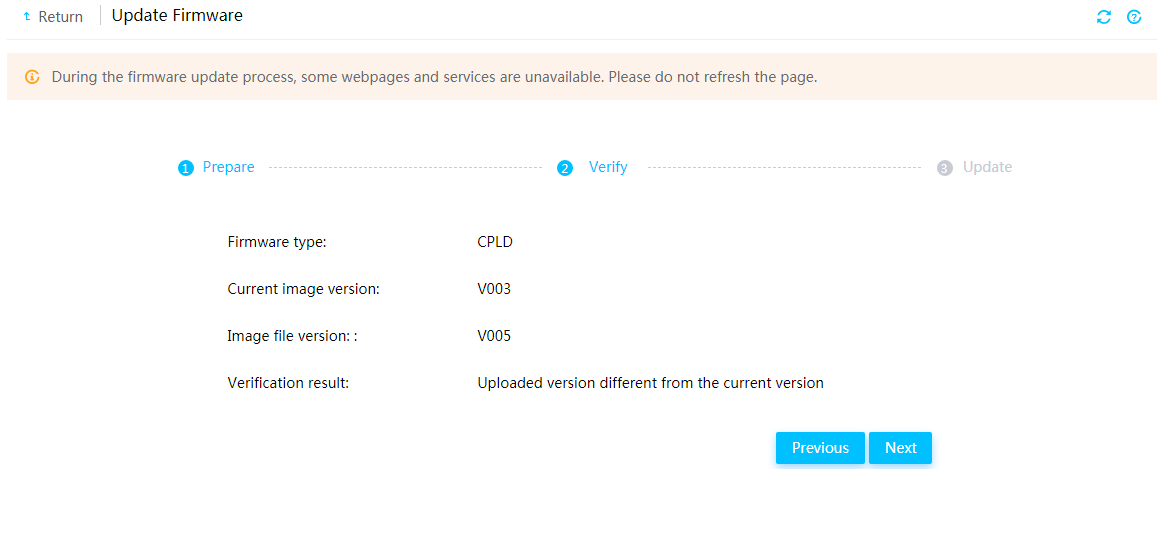
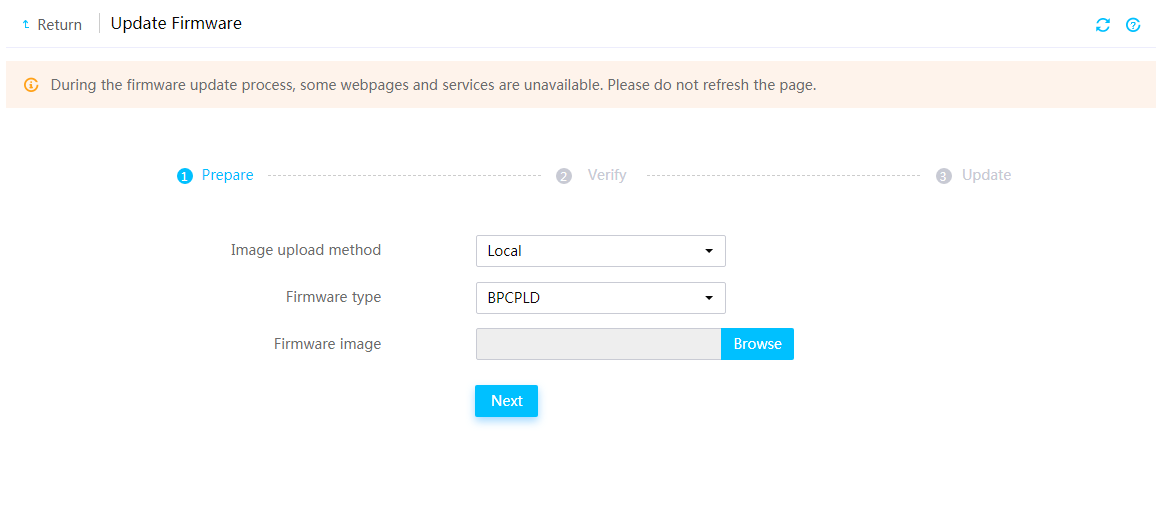
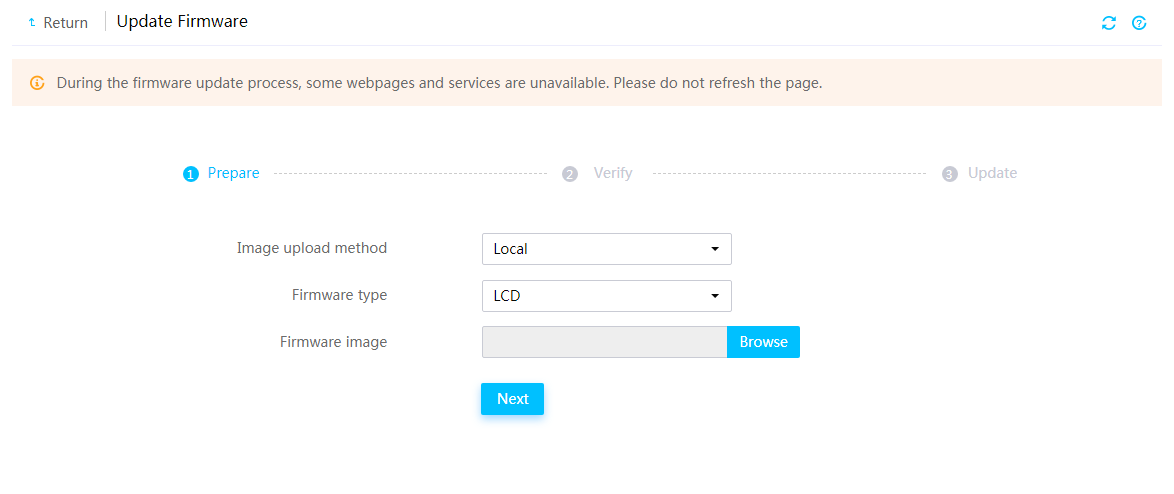
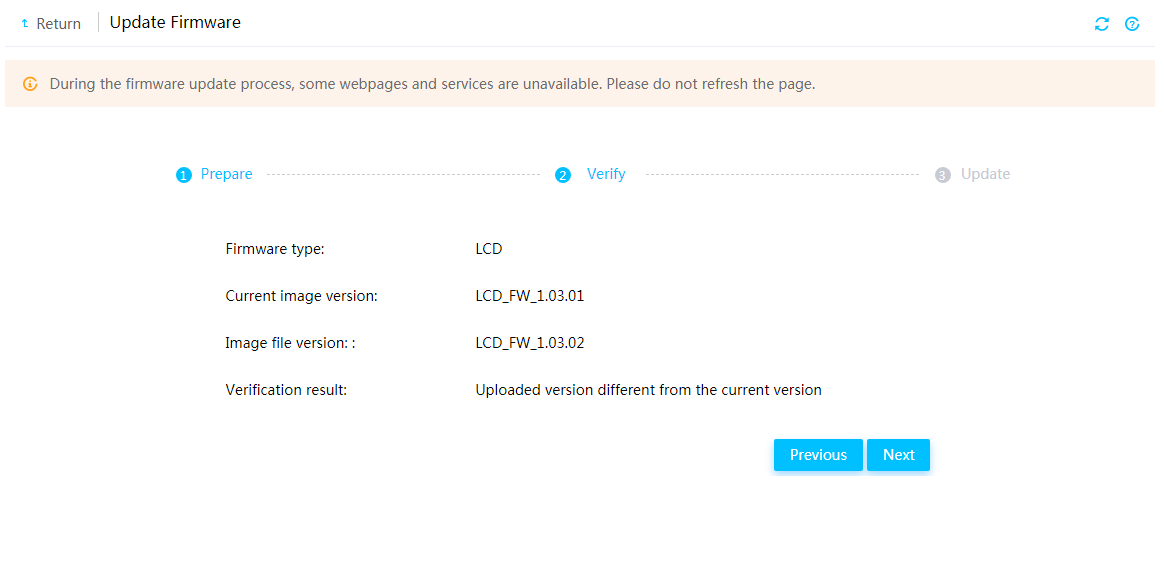
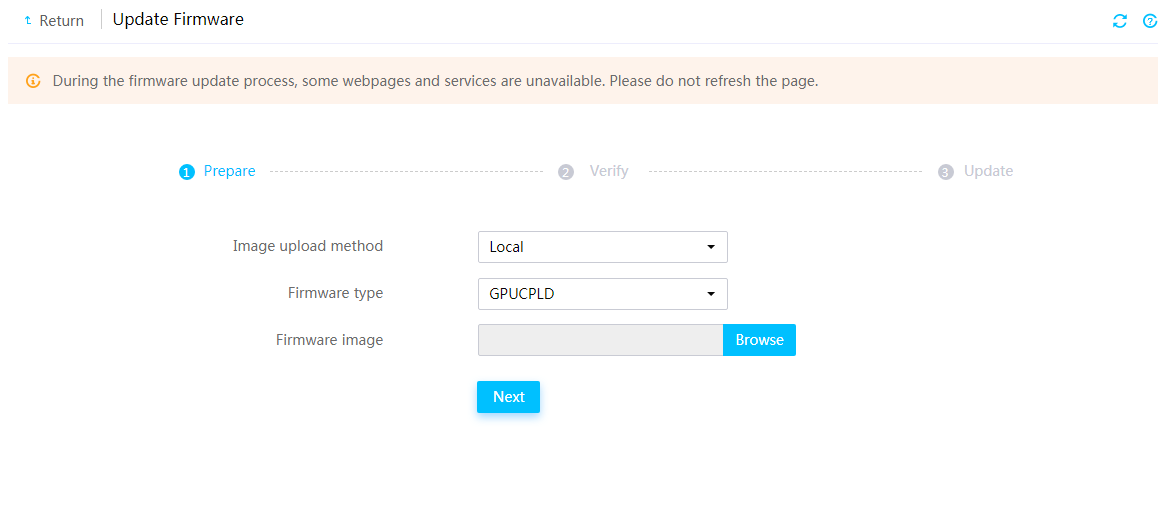
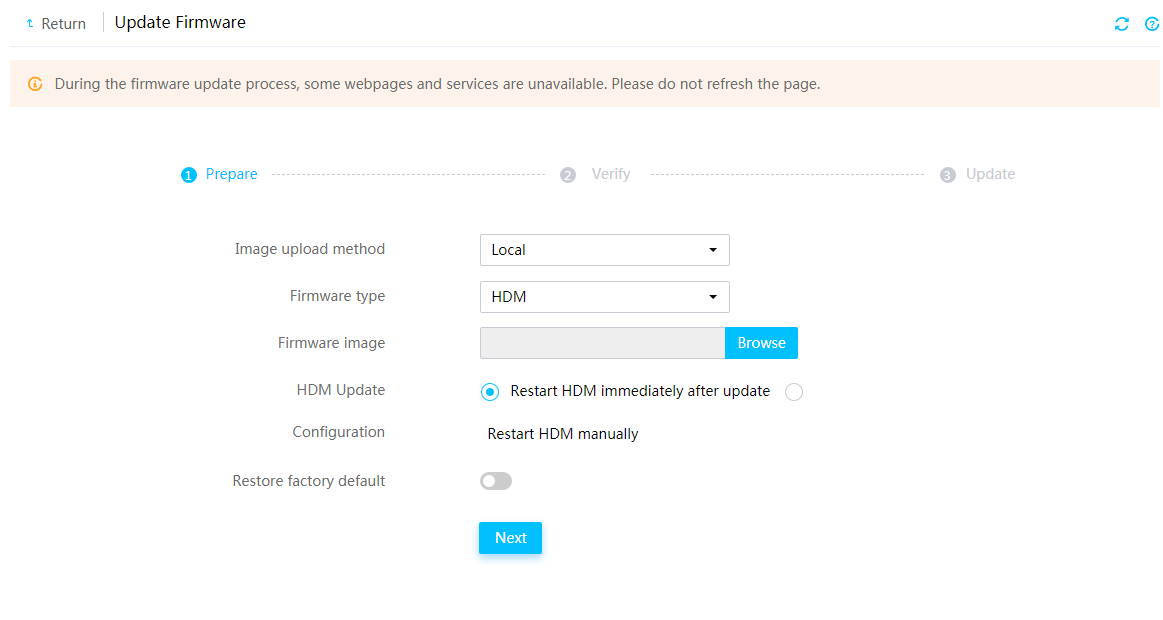
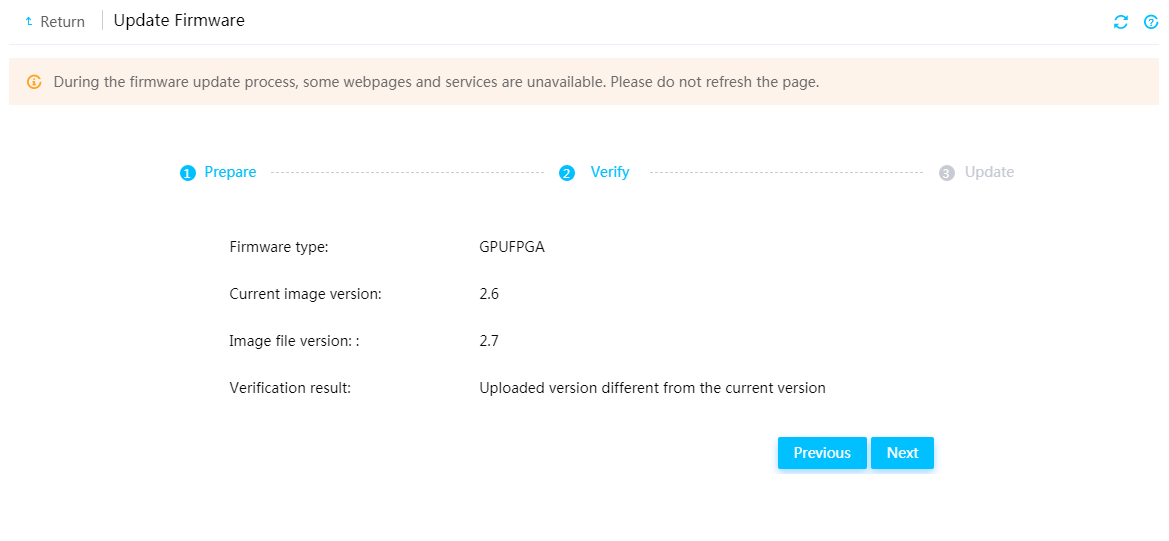
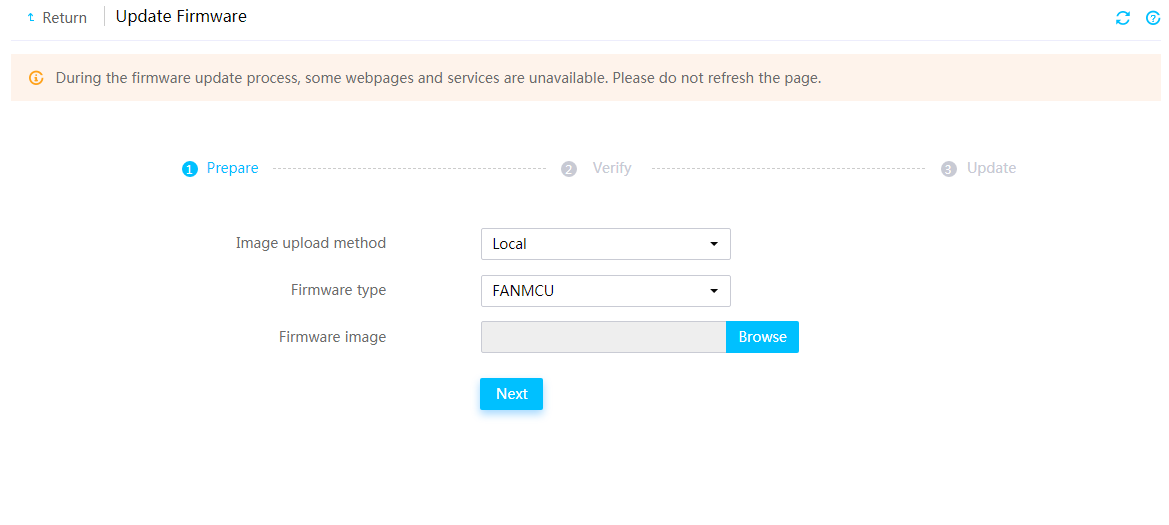
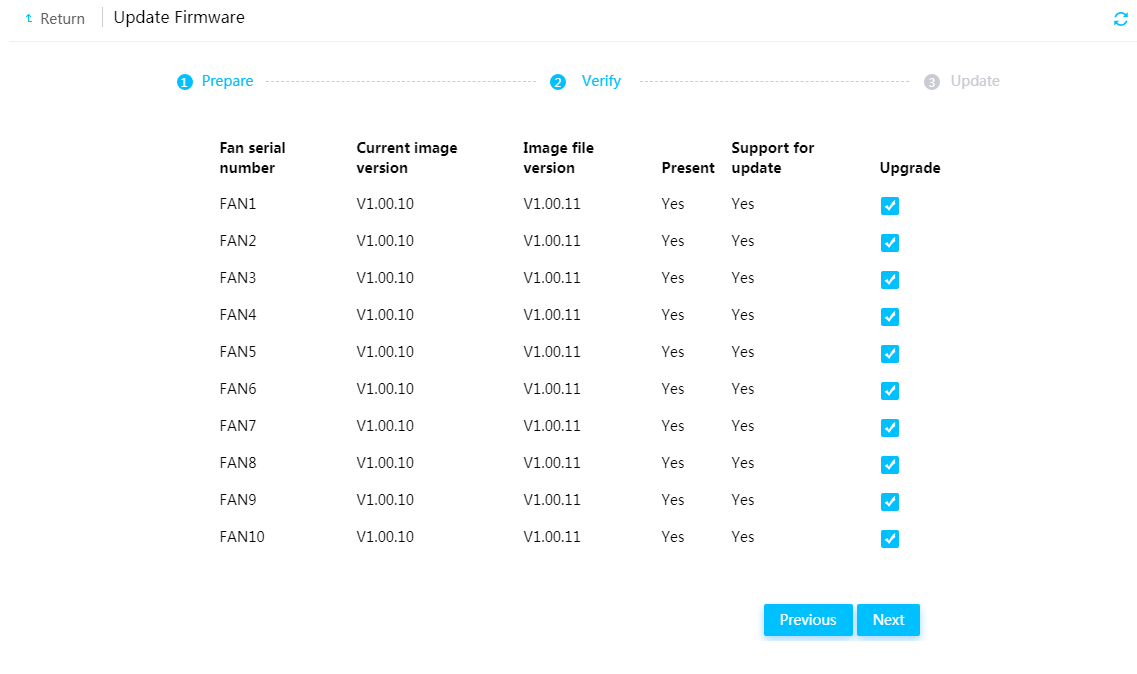
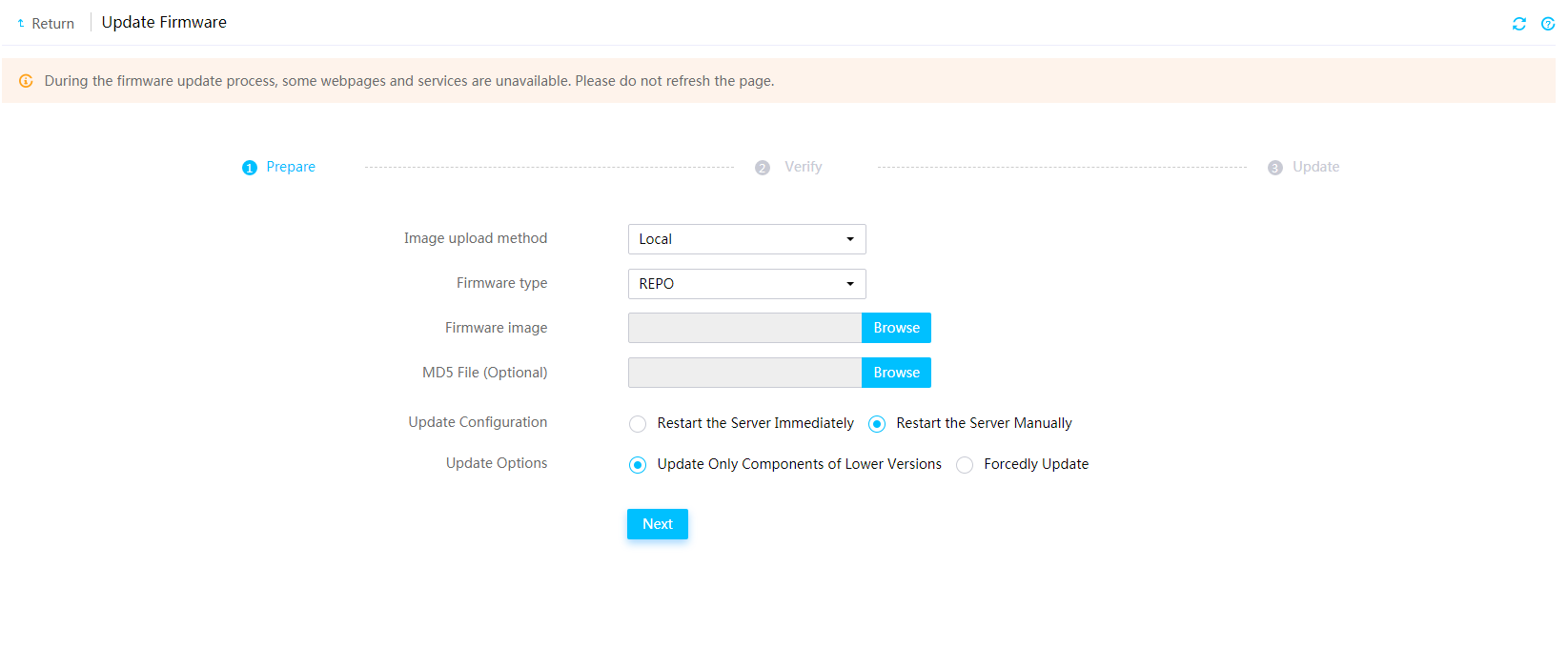
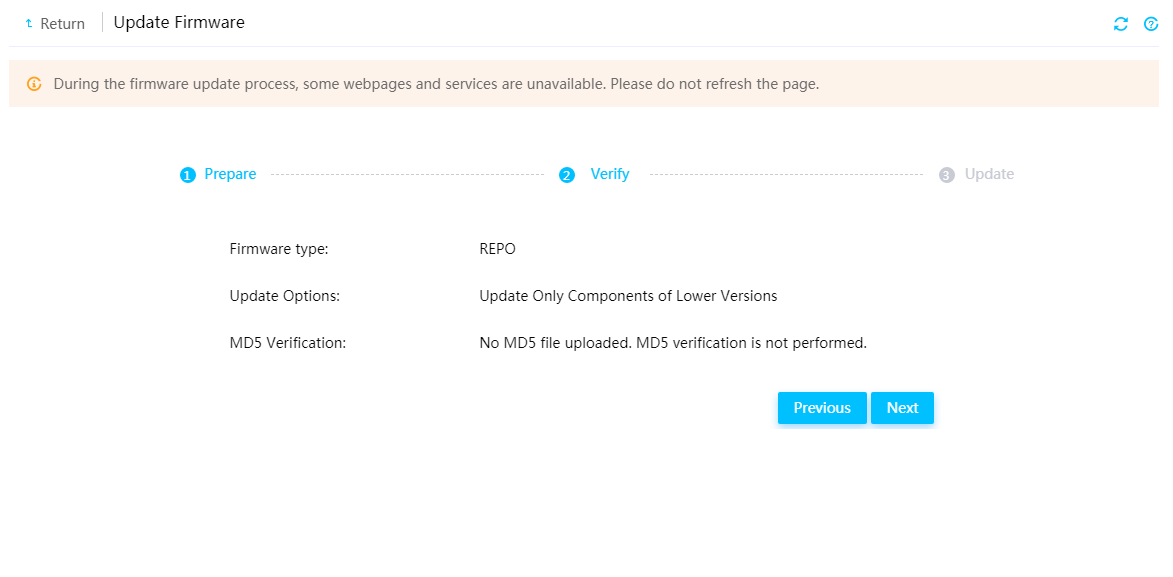
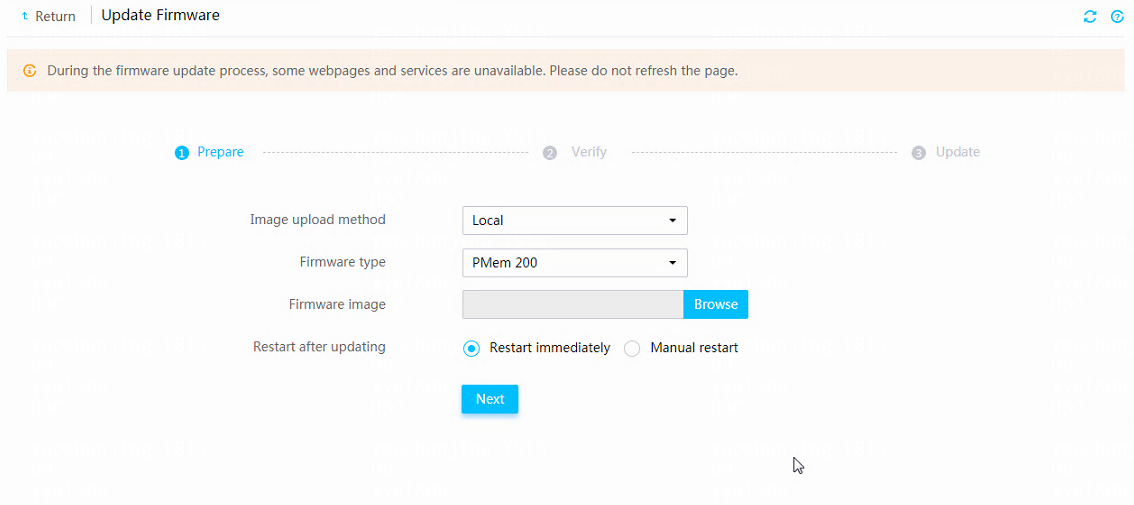
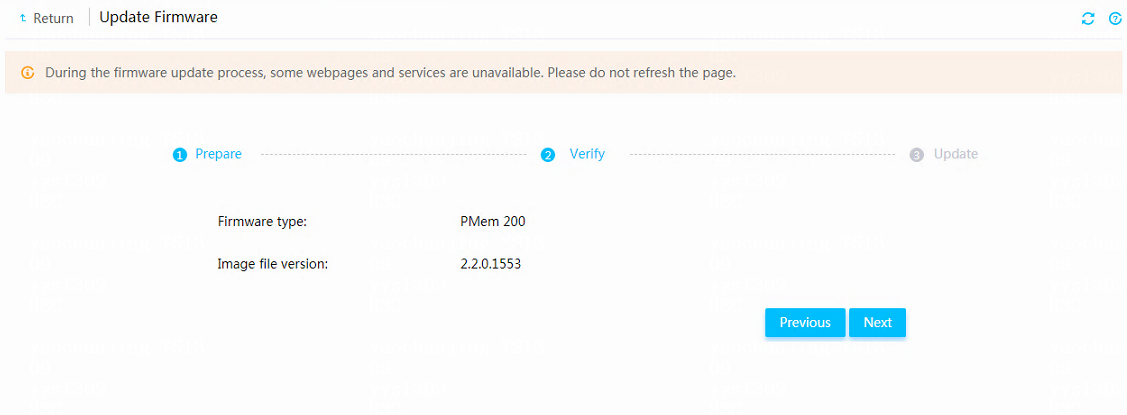
Firmware update restrictions and guidelines
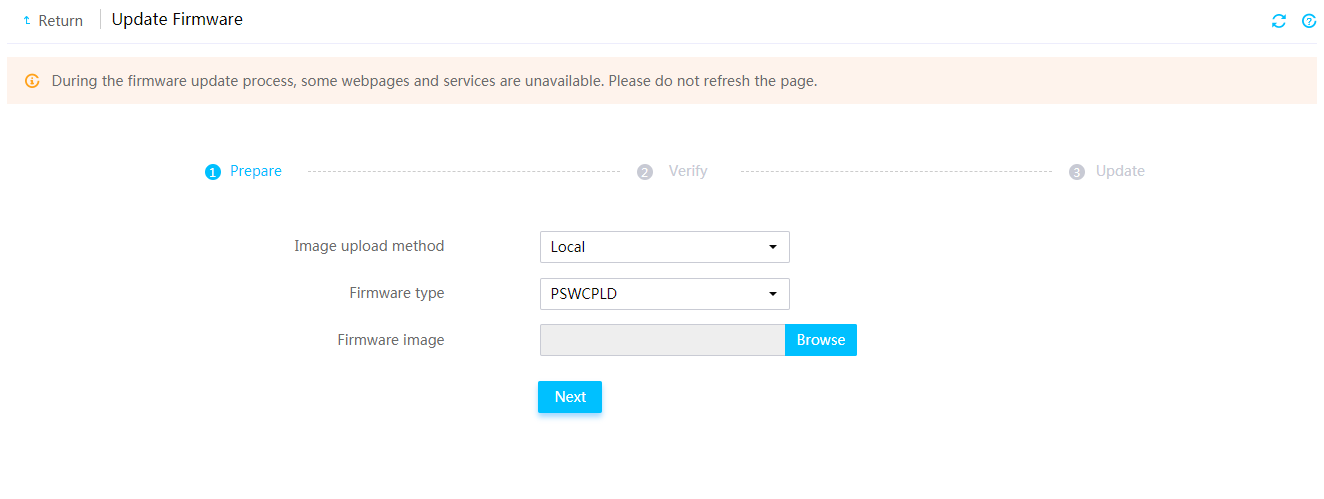
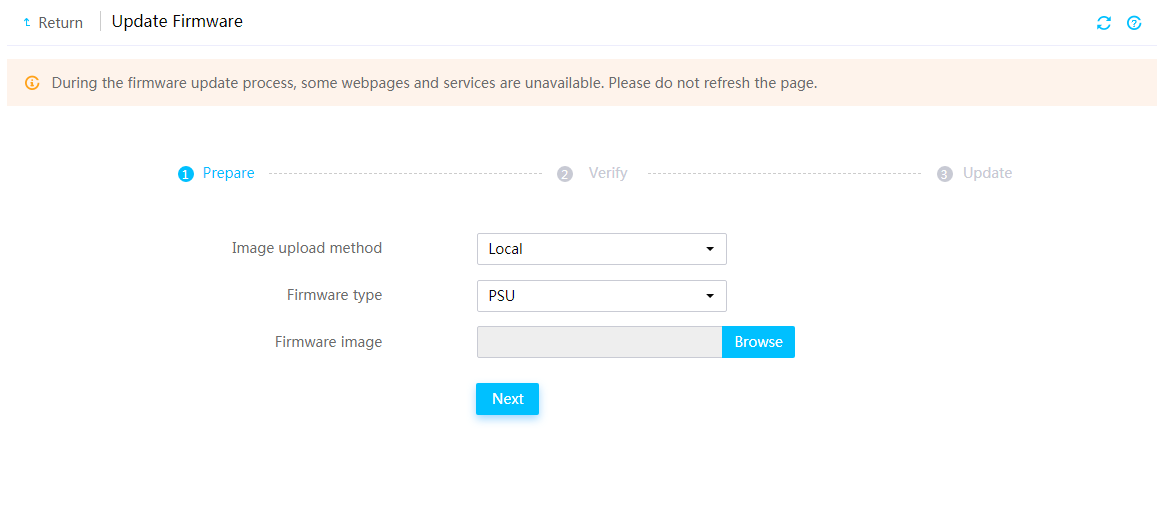
Prerequisites for firmware update
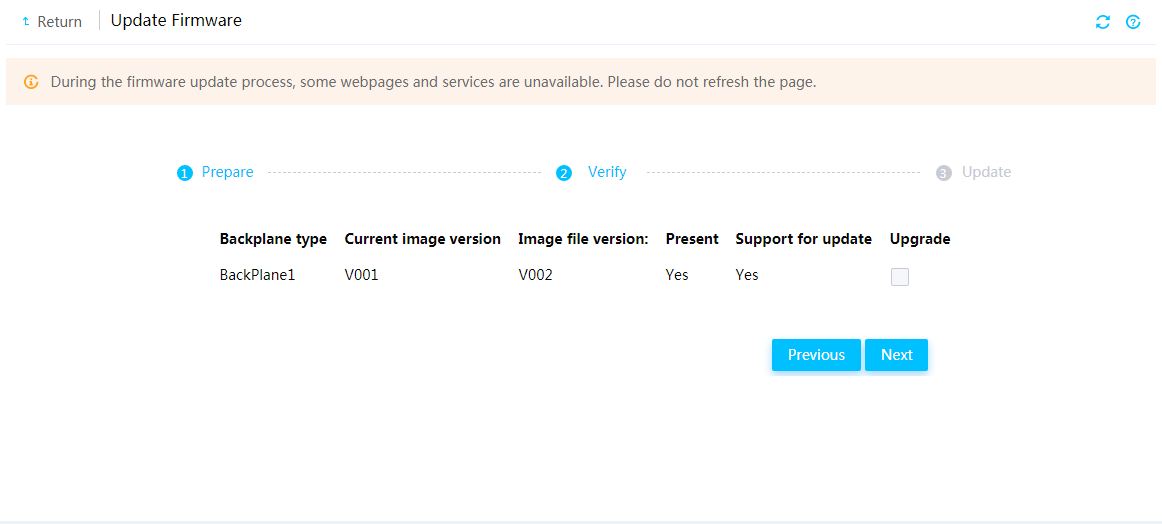
Update drive backplane firmware
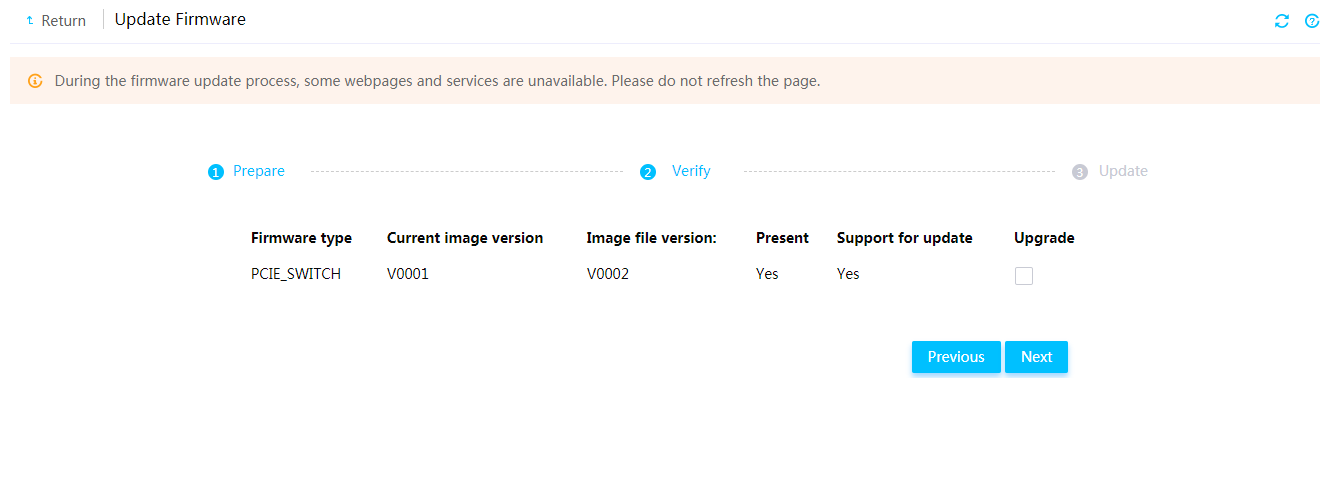
Update PCIe switch board firmware
Update the REPO for firmware update
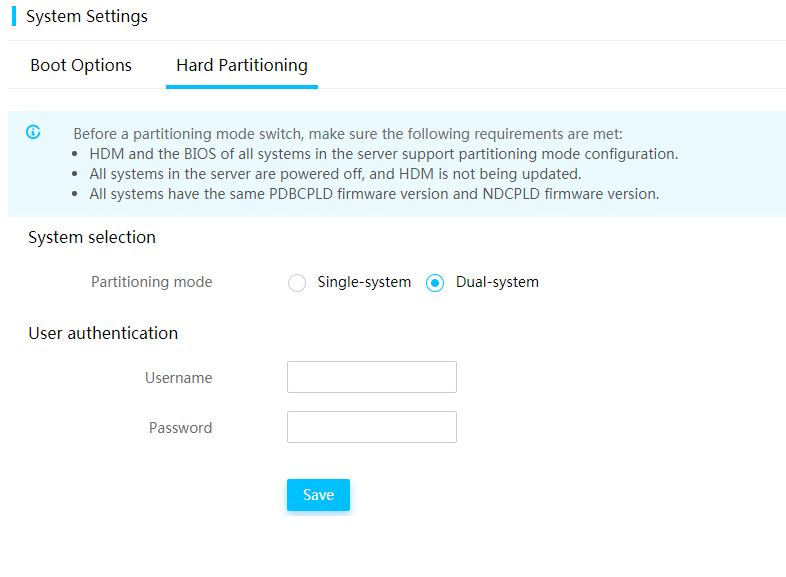
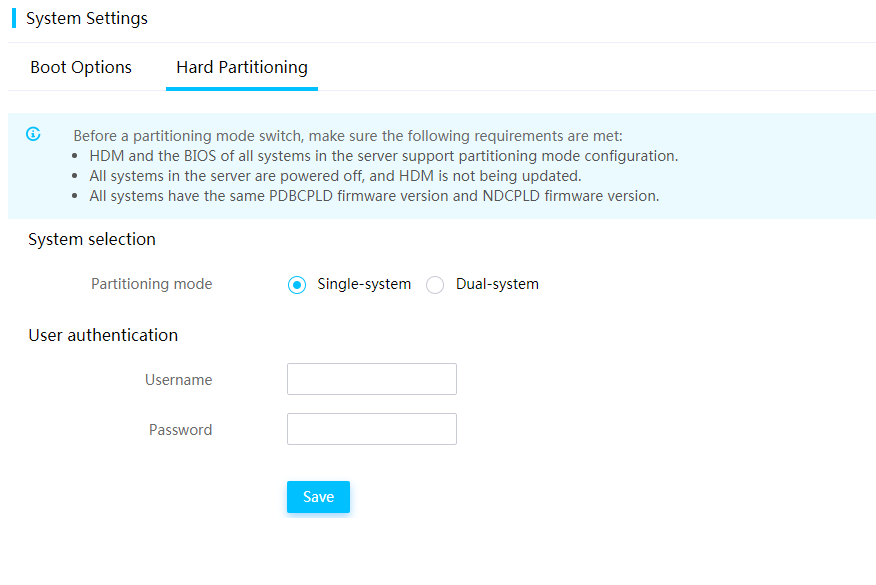
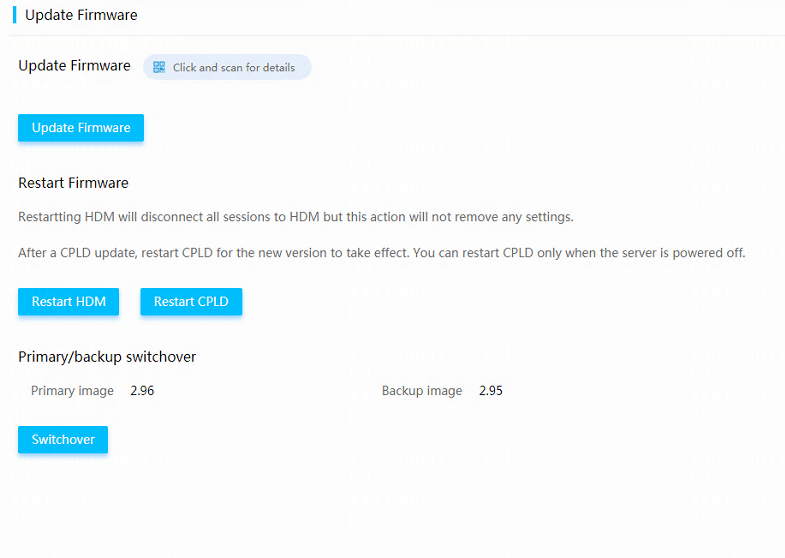
Switch over between primary and backup HDM firmware images
Manage the intelligent security bezel
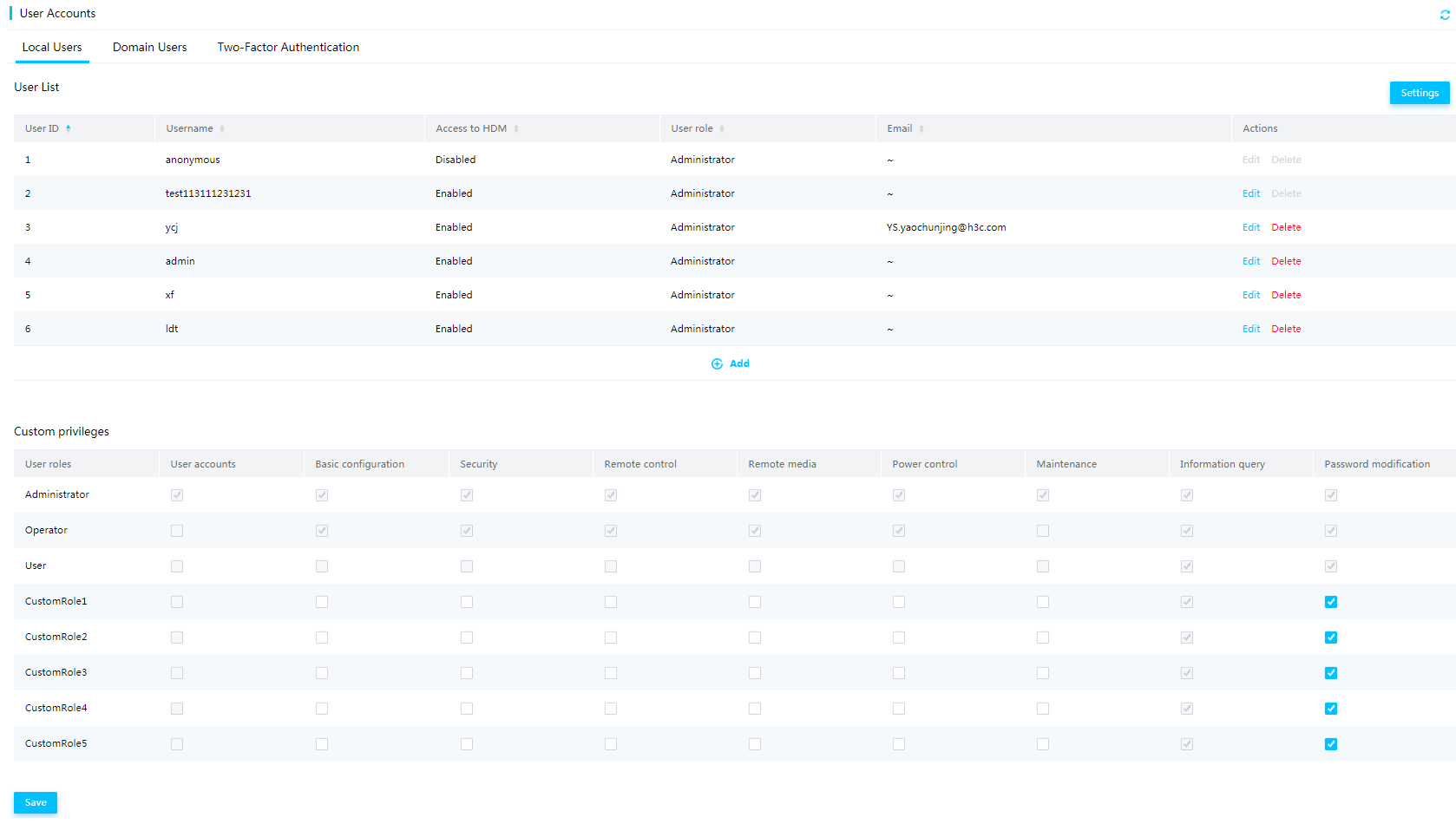
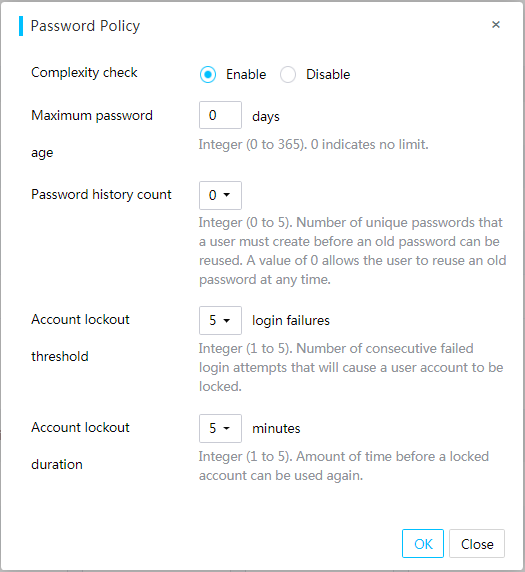
Configure the password policy for local users
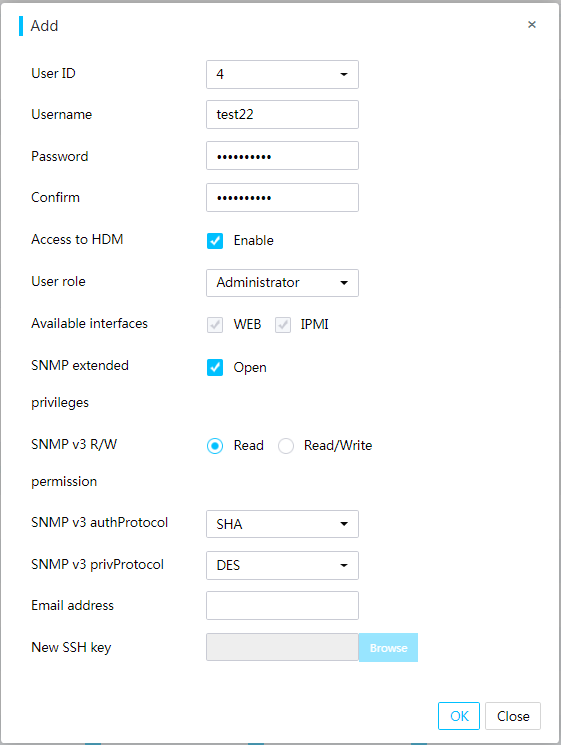
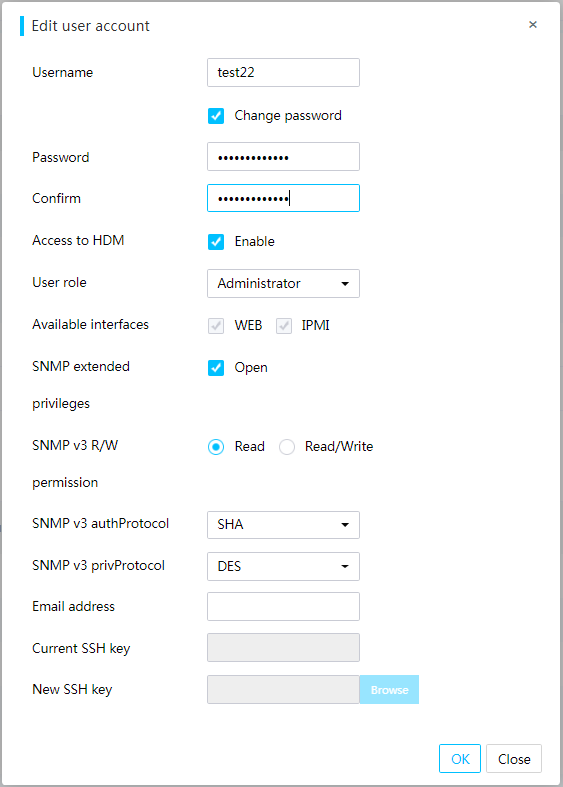
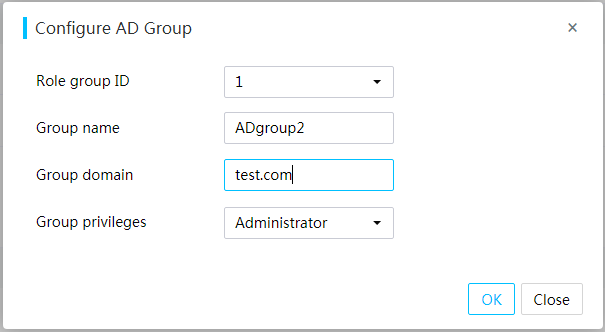
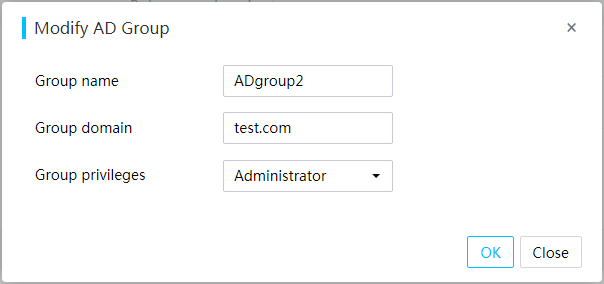
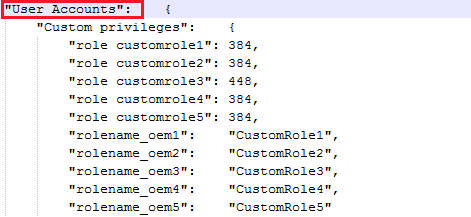
Configure privileges for custom users
User roles and privileges matrix
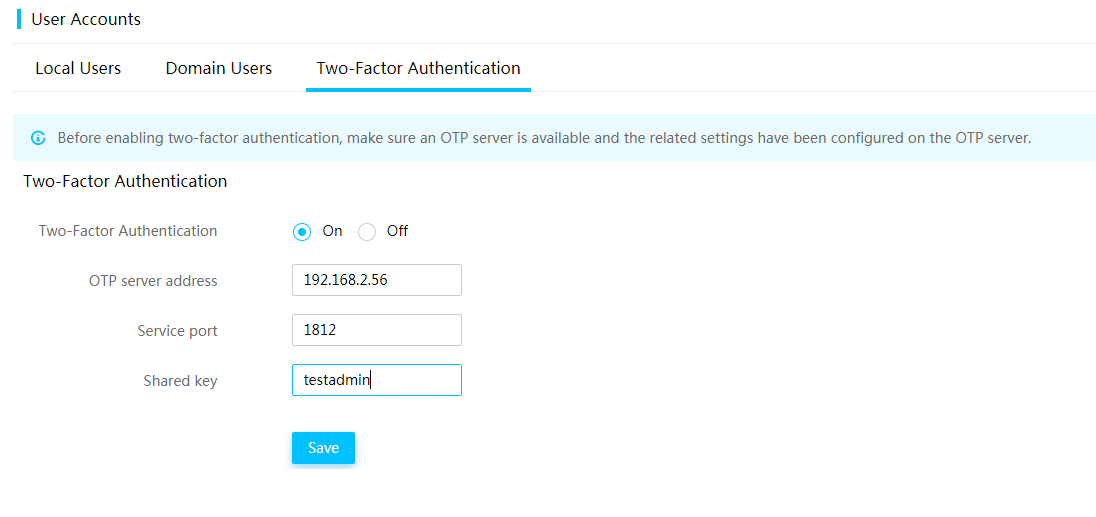
Configure two-factor authentication
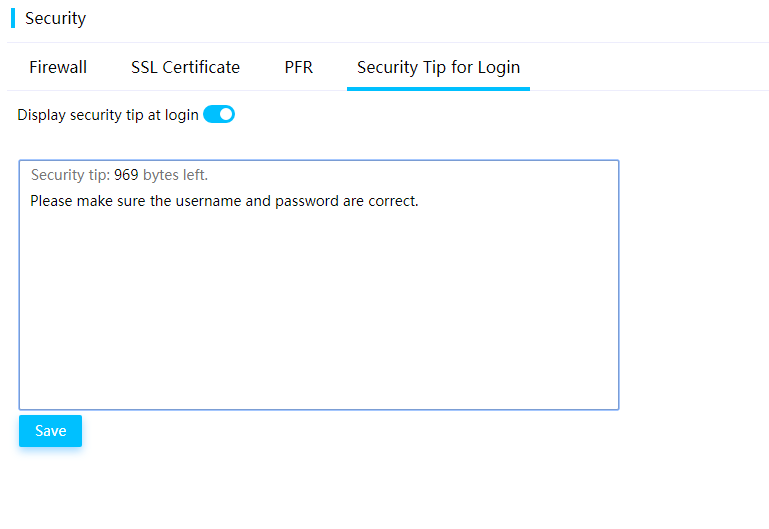
Configure the security tip for login
Launch an H5 KVM remote console
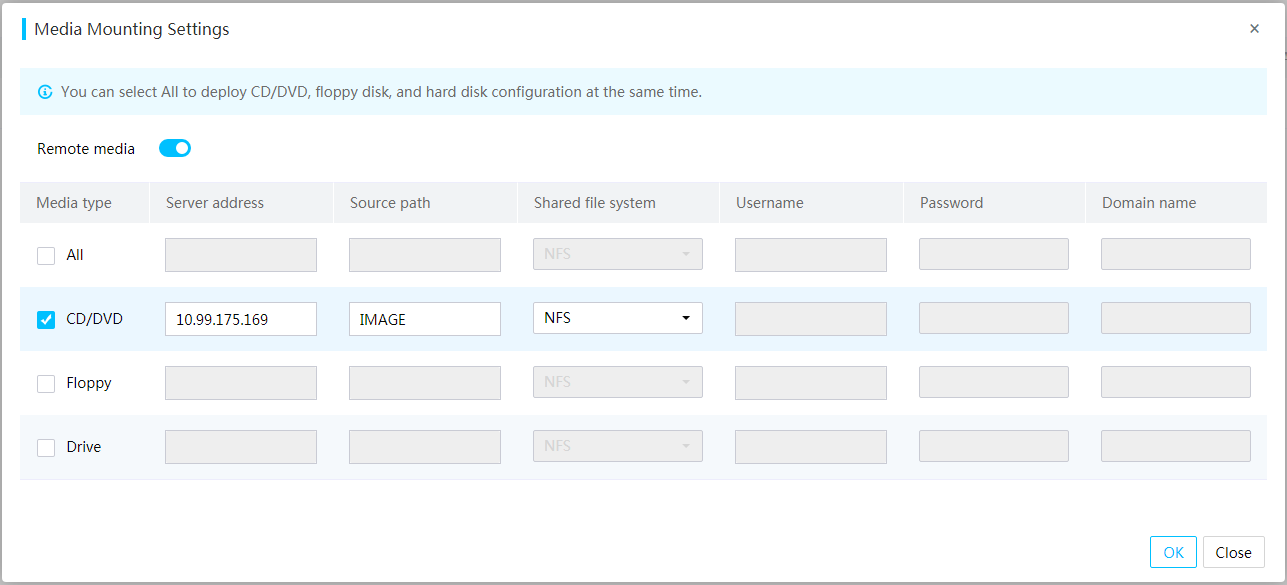
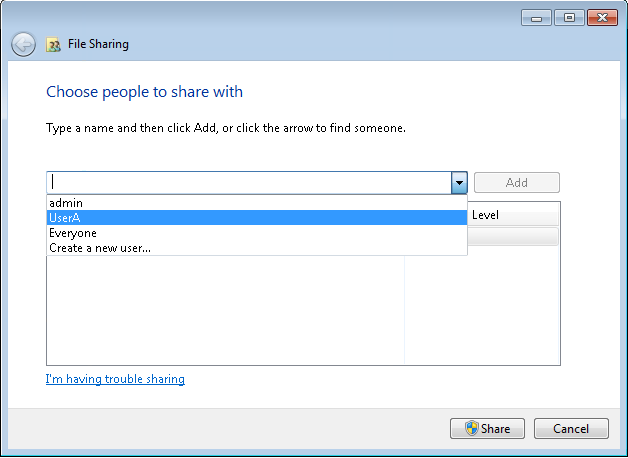
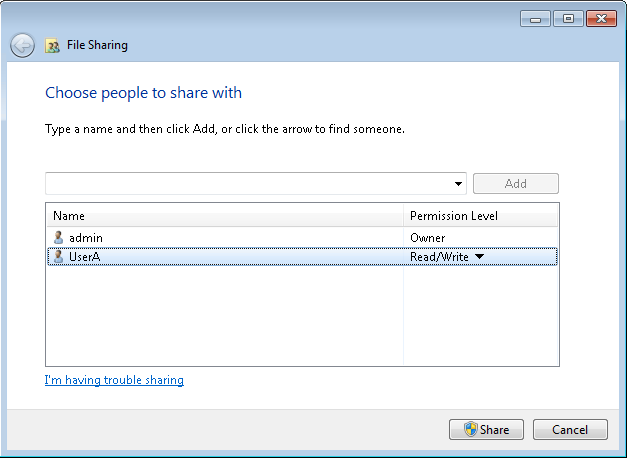
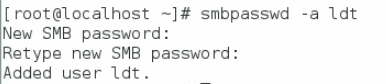
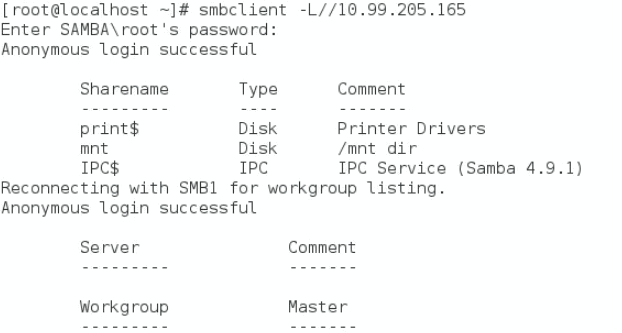
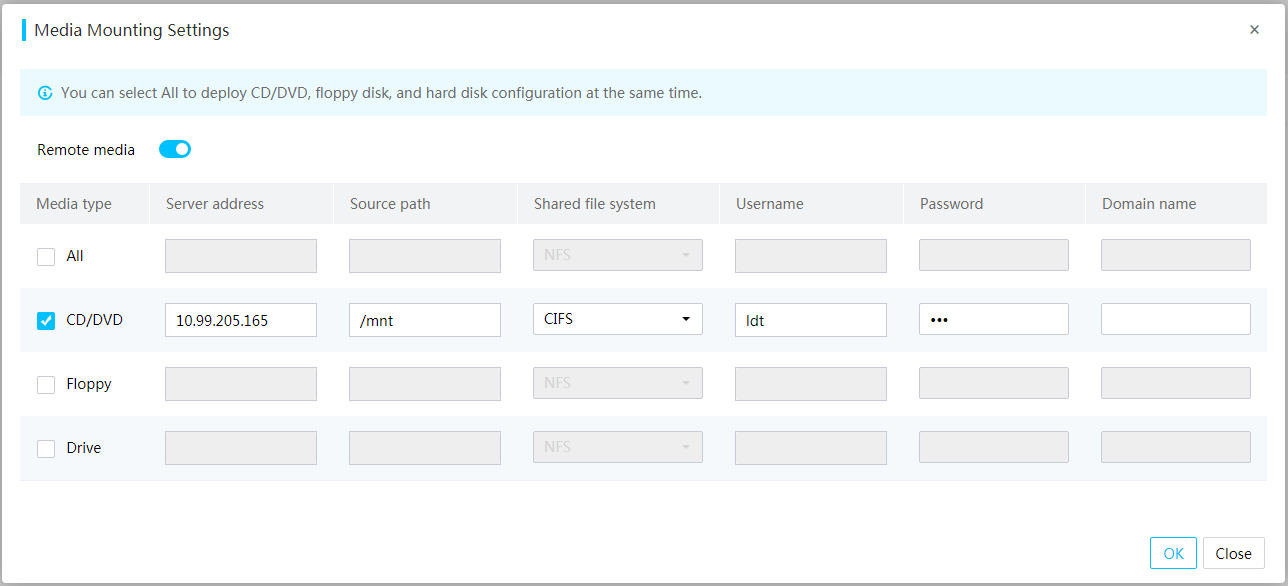
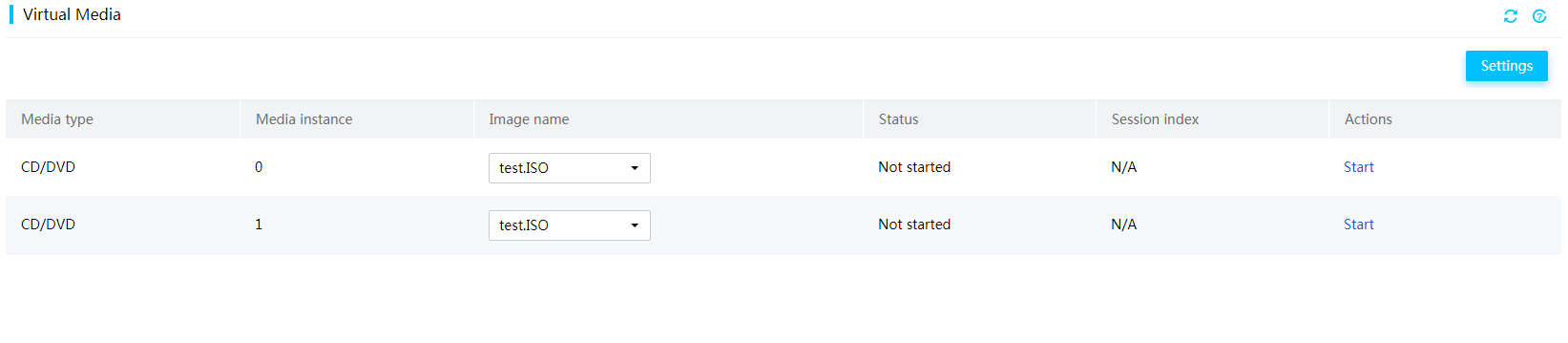
Mount images through a Windows CIFS server
Mount images through a Linux CIFS server
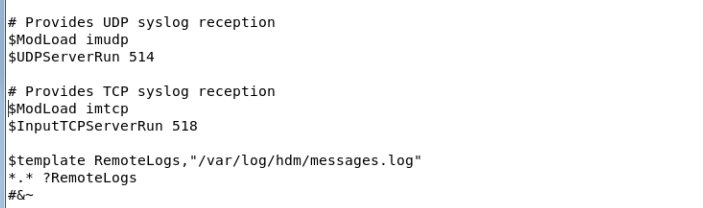
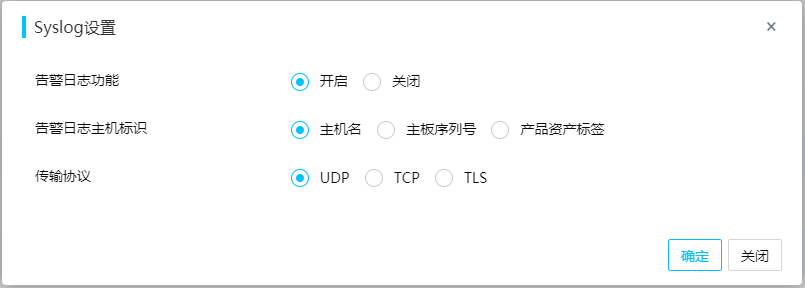
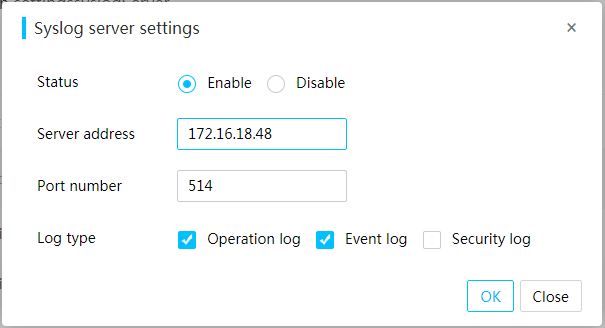
Set up a Linux syslog server based on UDP or TCP
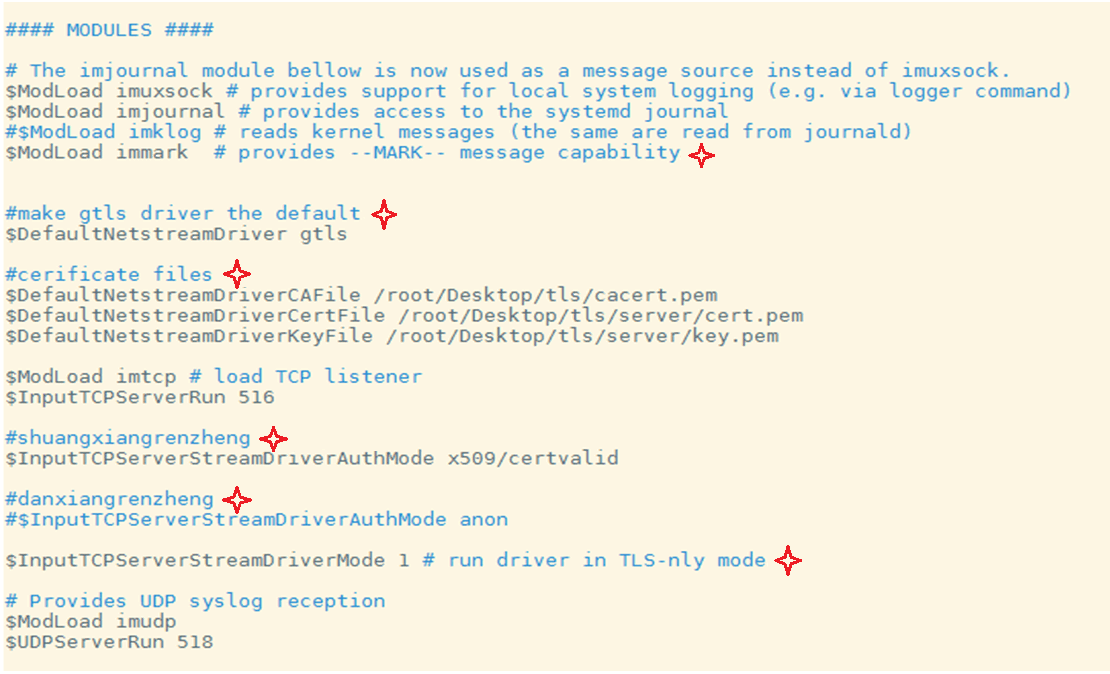
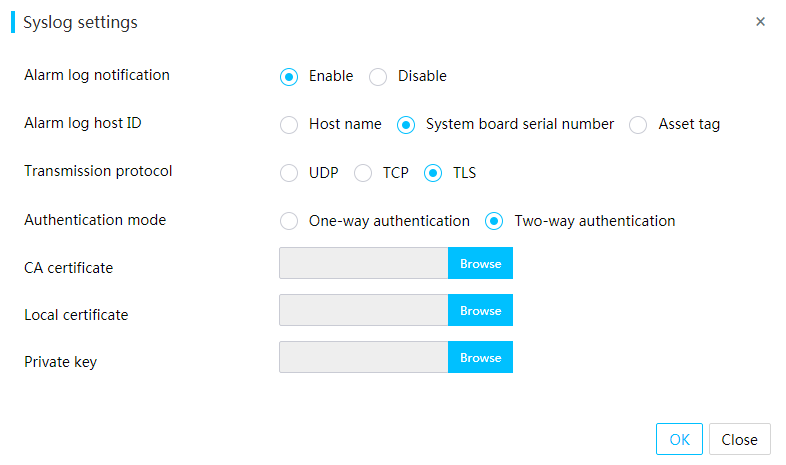
Set up a Linux syslog server based on TLS
About HDM
Introduction
Hardware Device Management (HDM) is a remote server management system that provides the following abundant features:
· Various management interfaces
¡ HDM provides IPMI, HTTPS, SNMP, and Redfish, to meet various system integration requirements.
¡ HDM is compatible with IPMI v1.5 and IPMI v2.0 and provides a standard management interface for standard management system integration.
· Remote maintenance
¡ HDM provides remote access to the server through KVM (keyboard, video, and mouse) and virtual media, enabling convenient server monitoring and management.
¡ HDM supports out-of-band RAID monitoring and configuration to improve RAID configuration efficiency and management capability.
¡ HDM supports importing and exporting HDM, BIOS, or RAID configuration to improve remote server management efficiency.
· Fault monitoring and diagnosis
¡ HDM supports taking a screenshot or records a video upon a system crash for future troubleshooting.
¡ HDM supports using syslog messages, traps and emails to report alarms for troubleshooting.
¡ HDM provides all-round server monitoring, alarming, and event logging. It monitors server operation, for example, CPU core temperature, voltage, and fan speed, and generates alarms and logs if any event occurs, such as memory failure, drive failure, or power supply failure.
¡ HDM supports Smart Hardware Diagnosis (SHD) for component fault diagnosis, bringing ease to fault location and faulty component replacement.
· Networking
¡ HDM supports VLANs and the sideband technology that allows for flexible network management.
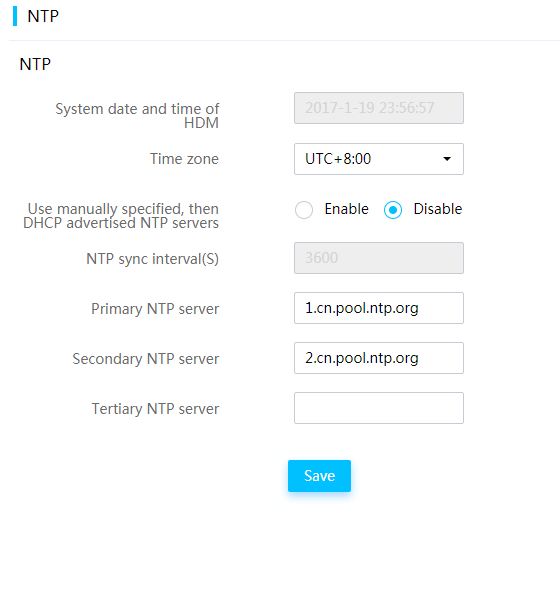
¡ NTP is available for time synchronization to improve time precision on the server.
¡ HDM supports domain servers and directory servers to simplify user management and improve security of user management.
· Security management
¡ HDM supports primary/backup image switchover. The switchover enables startup by using the backup image if the system crashes, which enhances system availability.
¡ HDM provides various user interfaces to ensure user login security.
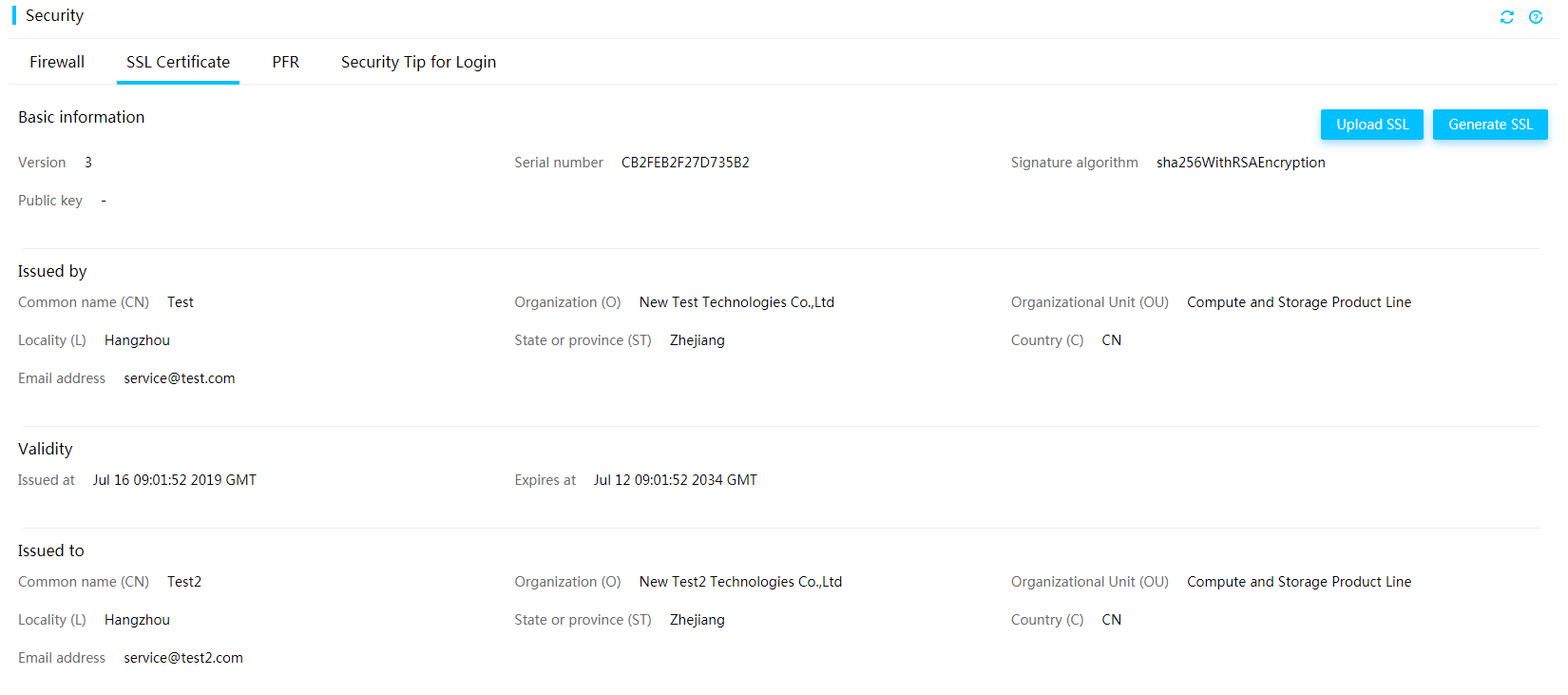
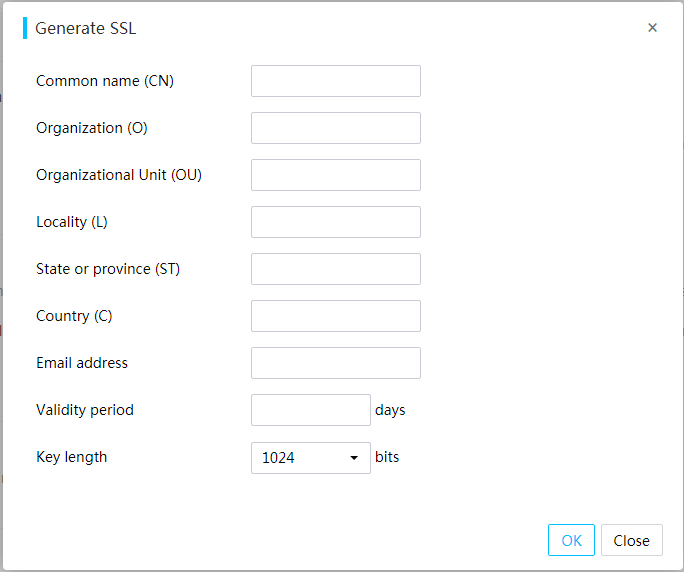
¡ HDM supports uploading and replacing certificates to enhance data transmission security.
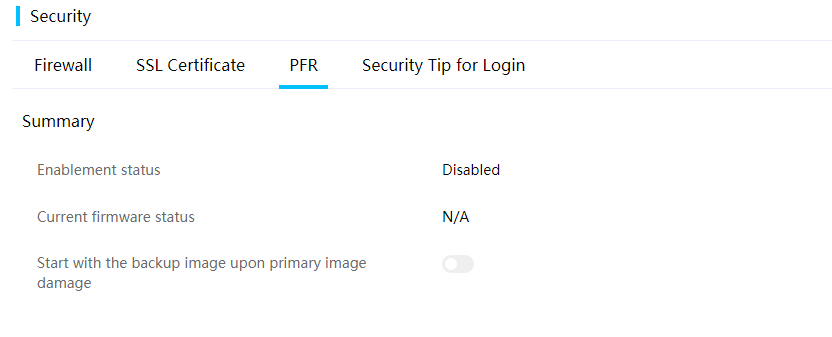
¡ Platform Firmware Resiliency (PFR) is used to protect HDM from attacks.
· Smart power supply management
¡ HDM provides power capping to precisely control the power consumption of each server, helping arranging energy supply.
¡ HDM supports configuring processor power states and the power supply operating mode to achieve power saving.
· Unified control
HDM supports managing servers in bulk to improve efficiency.
· LCD display
¡ A touchable 3.5-inch LCD display is optional for some H3C rack servers for the ease of local maintenance.
¡ The LCD display obtains server information from HDM to quickly obtain the health state of the server.
Various management interfaces
HDM supports management through Web, Redfish, IPMI, and SNMP interfaces.
HDM Web interface
HDM Web interface provides a convenient configuration query interface. Multiple modules are integrated on the HDM Web interface based on feature implementation, including Dashboard, System, Configuration, Remote Services, Remote O&M, Users & Security, and Unified Control.
HDM supports both Chinese and English. You
click the ![]() or
or ![]() button to change
the language to Chinese and English, respectively.
button to change
the language to Chinese and English, respectively.
To access the online help, you can click the ![]() button.
button.
Redfish management interface
HDM supports the standard Redfish management interface. The Redfish client as a Redfish interface tool such as Postman, sends HTTPS requests to the server, and performs information query, configuration, and monitoring through the GET, PATCH, POST, or DELETE command.
For more information about Redfish, see H3C HDM Redfish API Reference.
IPMI management interface
HDM supports IPMI 1.5 and IPMI 2.0. IPMI is a server management system standard that provides server management on different types of hardware. It enables multiple platform-integrated management.
Baseboard Management Controller (BMC) is the core controller in IPMI that enables system management software to exchange information for server management.
IPMI provides the following out-of-band management and monitoring features:
· Asset management.
· Fault monitoring.
· Logging.
· Recovery control.
For information about supported IPMI commands, see H3C HDM IPMI Basics Command Reference.
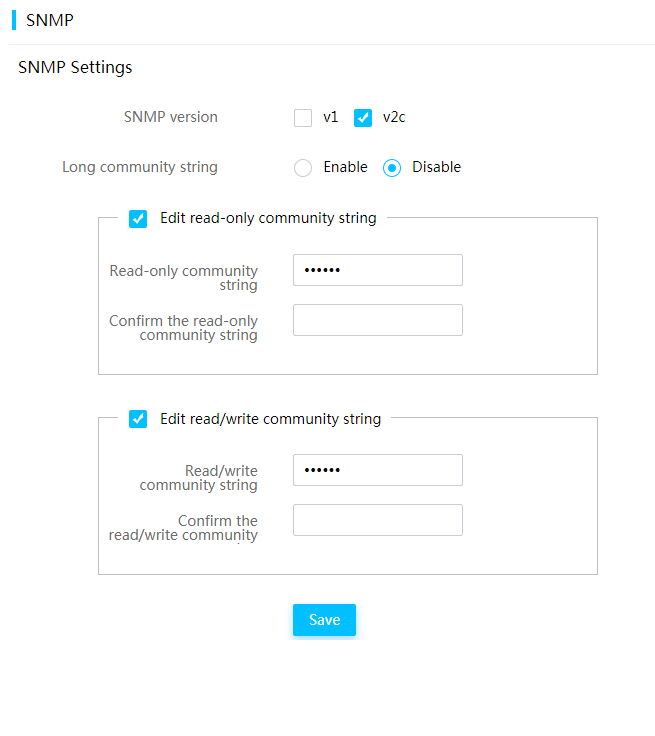
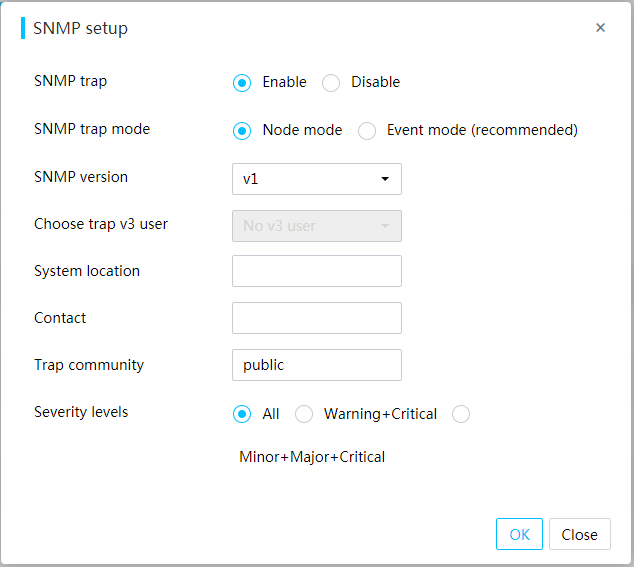
SNMP management interface
Simple Network Management Protocol (SNMP) defines the standard management framework, common communication languages, and security and access control mechanisms for device monitoring and management in a network. It is widely used for remote management and operation on network devices.
HDM provides SNMP-based programming interfaces. SNMP supports GET and SET operations, and trap sending. Third-party management software can manage servers in a centralized manner by using SNMP interfaces. The SNMP agents support SNMPv1, SNMPv2c, and SNMPv3.
An SNMP agent supports displaying the following information: system health status, hardware status, memory and processor models, alarm reporting configuration, power statistics, asset information, heat dissipation management, firmware version, and network management.
Applicable products
This document is applicable to the following products:
· AE100.
· H3C UniServer B5700 G3.
· H3C UniServer B5800 G3.
· H3C UniServer B7800 G3.
· H3C UniServer E3200 G3.
· H3C UniServer R2700 G3.
· H3C UniServer R2900 G3.
· H3C UniServer R4100 G3.
· H3C UniServer R4300 G3.
· H3C UniServer R4400 G3.
· H3C UniServer R4700 G3.
· H3C UniServer R4900 G3.
· H3C UniServer R4950 G3.
· H3C UniServer R5300 G3.
· H3C UniServer R6700 G3.
· H3C UniServer R6900 G3.
· H3C UniServer R8900 G3.
· H3C UniServer R4300 G5.
· H3C UniServer R4330 G5.
· H3C UniServer B5700 G5.
· H3C UniServer R4700 G5.
· H3C UniServer R4900 G5.
· H3C UniServer R4930 G5
· H3C UniServer R4950 G5.
· H3C UniServer R5300 G5.
· H3C UniServer R5500 G5.
· H3C UniServer R6900 G5.
Using this document
The figures of hardware options used in this document are for illustration only and might differ from your product.
The screenshots in this document are subject to change over time.
Some data in this document is used as an example and might differ from your product.
Before you start
Guidelines for using HDM
· As a best practice, use a dedicated network port to manage and configure HDM.
· Do not connect HDM to the Internet.
· Do not use insecure protocols or ports.
· Audit the operation logs periodically.
Default parameter settings
Table 1 describes the default parameter settings. As a best practice, change the default parameter values at your first access to HDM and update the default parameter values periodically.
Table 1 Default parameter settings
|
Parameter |
Default value |
|
Username |
admin |
|
Password |
Password@_ |
|
IPv4 address of the dedicated network port |
192.168.1.2/24 |
|
SNMP read-only community name |
rocommstr |
|
SNMP read-write community name |
N/A |
|
Trap community name |
public |
HDM users
HDM supports the following types of users:
· Local users—HDM supports a maximum of 16 local users. The local access mode is suitable for small-size scenarios such as laboratories and small- and medium-sized enterprises.
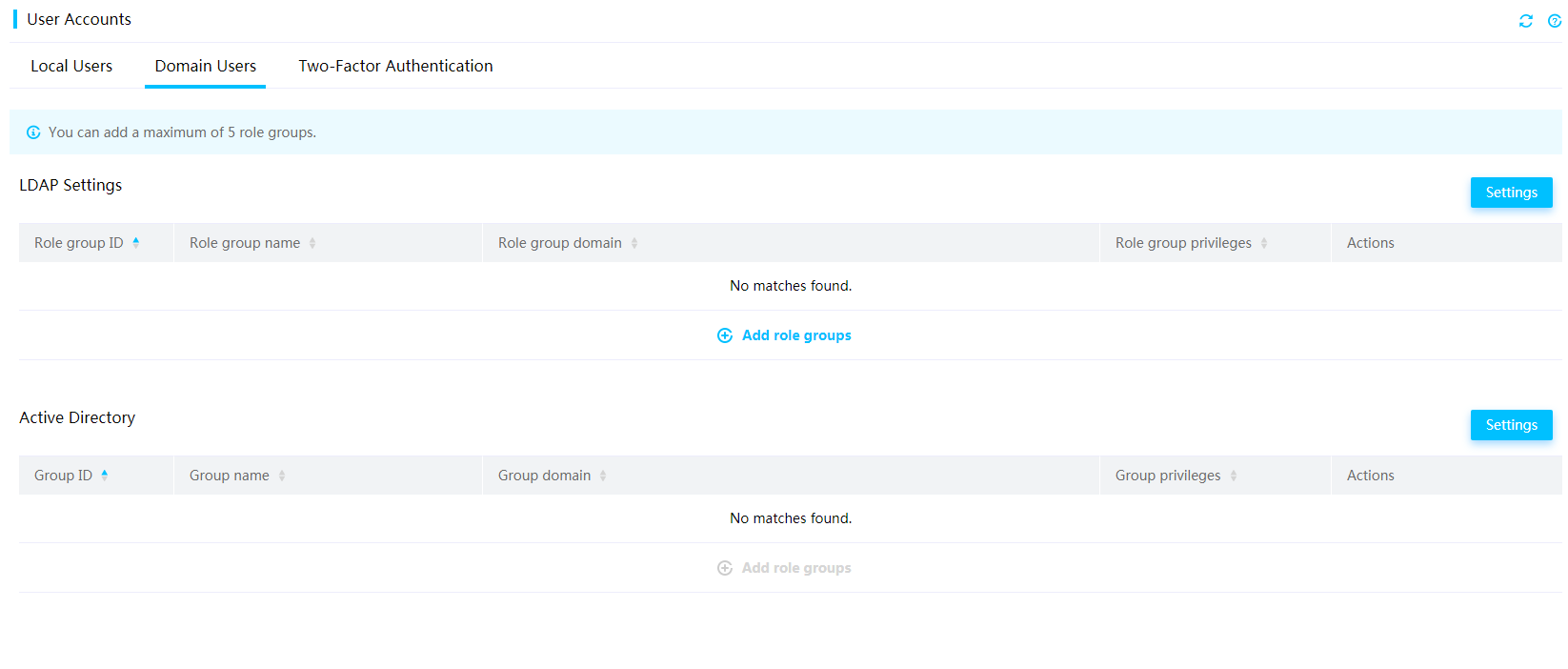
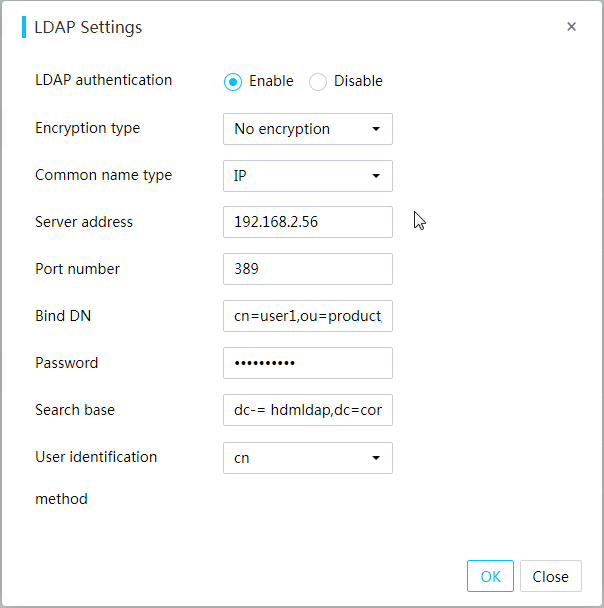
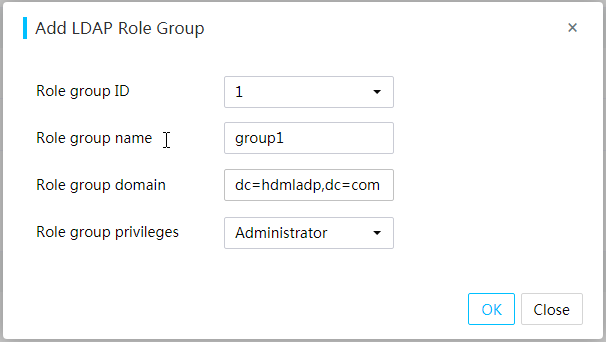
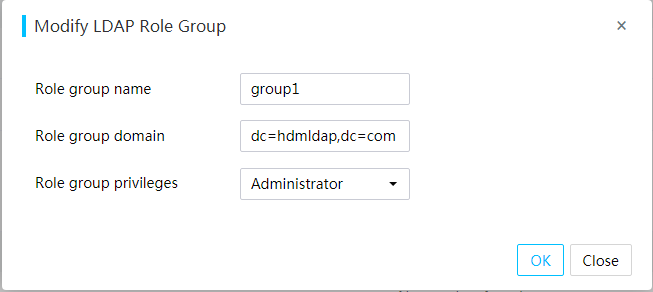
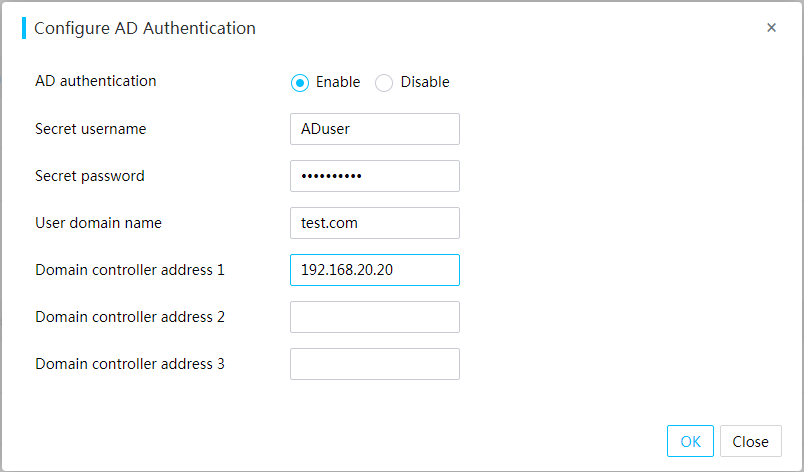
· Domain users (LDAP users and AD users)—The number of users and user permissions are configured and managed on the domain server. This access mode is suitable for environments with a large number of users.
FAQs
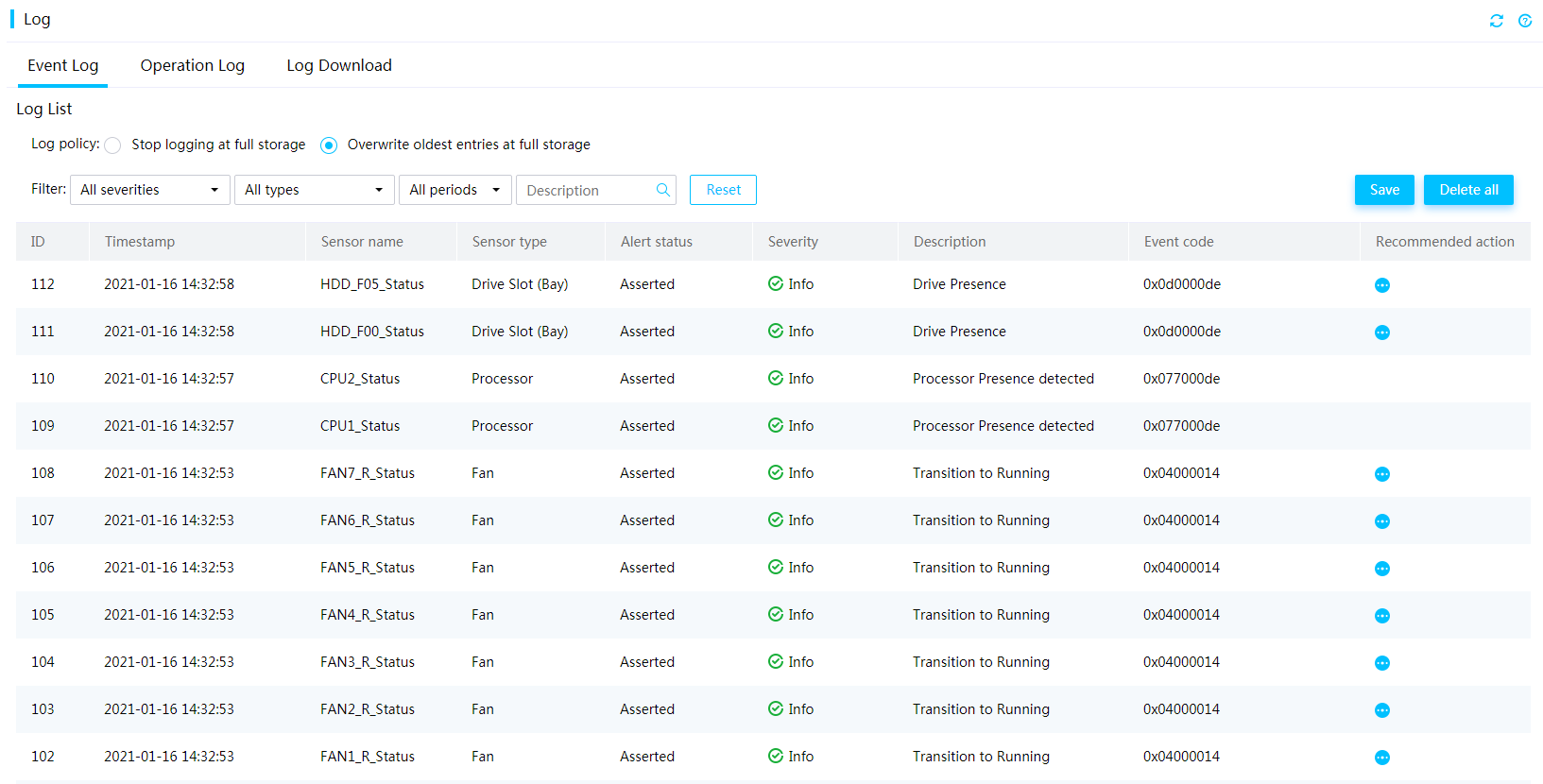
Fault diagnosis and location
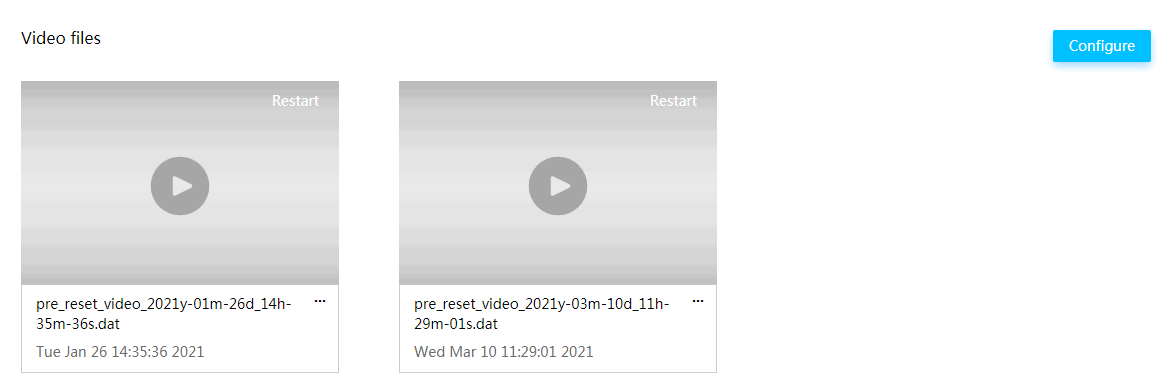
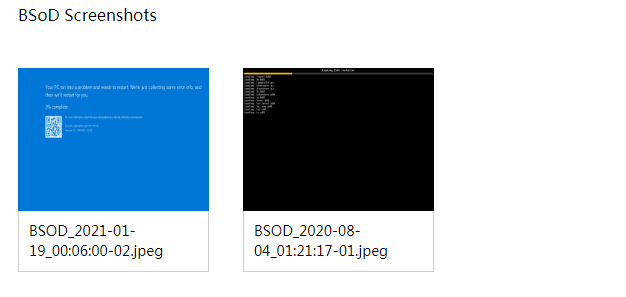
HDM takes a bluescreen of death (BSoD) screenshot and video recording upon a system crash. When the system fails and restarts, you can view the BSoD screenshot or the video for troubleshooting.
HDM Web interface access failures
Table 2 describes the possible causes and solutions for HDM Web interface access failures.
Table 2 Causes and solutions for HDM Web interface access failures
|
HDM Web interface access failure reason |
Solution |
|
|
Network connection issue |
The HDM network port is disconnected. |
Connect the network cable for the HDM network port correctly. |
|
An incorrect HDM management IP address is used. |
Use the IP address of the HDM management interface for access. |
|
|
The local PC and HDM network port are not on the same network segment. |
Make sure the local PC and HDM network port are on the same network segment. |
|
|
The access to HDM is unauthorized. |
Make sure the local PC and HDM network port are on the same network segment. |
|
|
Browser cache not cleared |
The firmware of HDM has been upgraded recently, but the browser cache is not cleared. |
Clear the browser cache and then re-log in to HDM. |
|
Incorrect access information |
The username does not exist. |
Use a username that has been created. At the first login, use the default username and password. |
|
The password is not correct. |
Use the correct password. The password is case sensitive. |
|
|
Username or password forgotten |
A new username or password has been configured to replace the default username or password. However, the new username or password is forgotten. |
Use the system maintenance switches. For more information about system maintenance switches, see the server user guide. |
|
Maximum number of sessions is exceeded at login. |
Press and hold the UID button and restart HDM to initialize HDM configurations. |
|
Sign in to HDM
The following information describes the prerequisites for a successful sign-in to HDM, the default sign-in parameters, the sign-in procedure, and global operations for all pages.
Sign in to HDM for rack servers
Prepare for an HDM sign-in
Before you sign in to the HDM Web interface, make sure all preparation requirements are met.
Set up the HDM client
HDM does not require installation of client software. You can use a Web browser to access HDM.
Make sure the browser and resolution setting of the configuration terminal meet the requirements in Table 3.
Table 3 Browser and resolution requirements
|
Browsers |
Resolution |
|
Google Chrome 48.0 (or higher) Internet Explorer 11 (or higher) Mozilla Firefox 50.0 (or higher) |
Minimum: 1366*768 Recommended: 1600*900 (or higher) |
Connect the server to the network
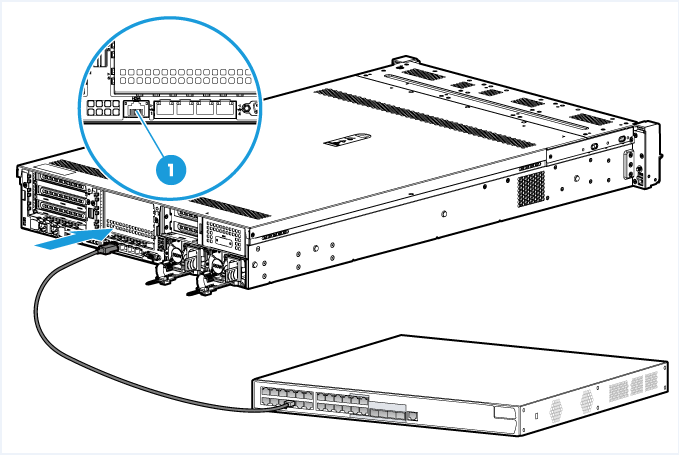
Connect either of the following network ports on the server to the network:
· HDM shared network port—Transmits HDM management traffic and server data traffic simultaneously. This port is available on all servers.
· HDM dedicated network port—Transmits only HDM management traffic. This port is not available on blade servers and AE modules.
For network port configuration on rack or storage servers, see "Network." For network port configuration on blade servers and AE modules, see "Configure the shared network port."
Figure 1 Connecting the server to the network (HDM dedicated network port on the R4900 G3)
Obtain the HDM sign-in settings
To sign in to HDM, you must obtain its management IP address and user account information.
On the first sign-in, use the default settings in Table 4. To change the management IP address after login, see "Network."
Table 4 Default HDM sign-in settings
|
Item |
Default setting |
|
IP address |
HDM shared network port: DHCP HDM dedicated network port: 192.168.1.2/24 |
|
Username |
admin |
|
Password (case-sensitive) |
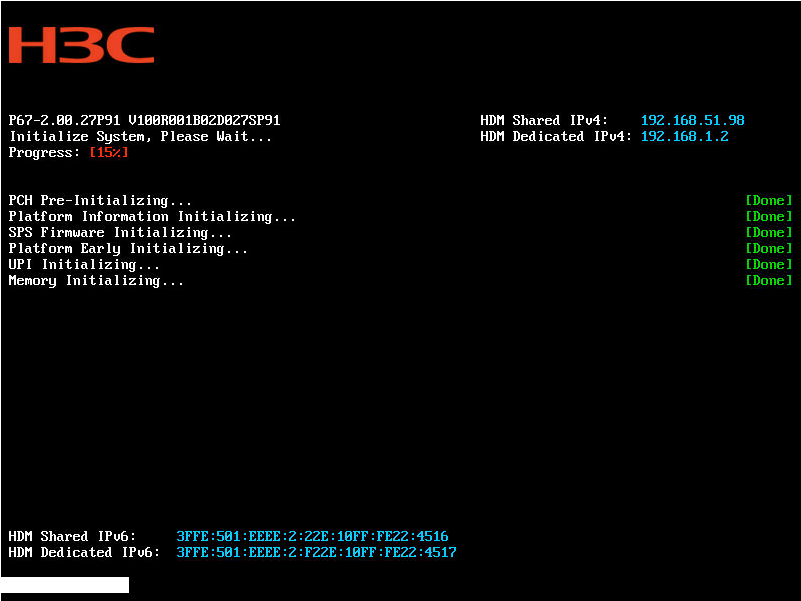
You can obtain the HDM management IP address from the POST screen of the BIOS. As shown in Figure 2, the POST screen displays the IPv4 addresses of the shared and dedicated network ports at the upper right corner, and the IPv6 addresses at the lower left corner.
Figure 2 Obtaining the HDM management IP address (BIOS version 2.00.27)
Sign in to HDM
Restrictions and guidelines
By default, the session timeout is 30 minutes. If no operation is performed within 30 minutes, the system logs you out.
After five consecutive password check failures, your account will be locked for five minutes.
For security purposes, change the default username and password at the first login, and update your password periodically.
Procedure
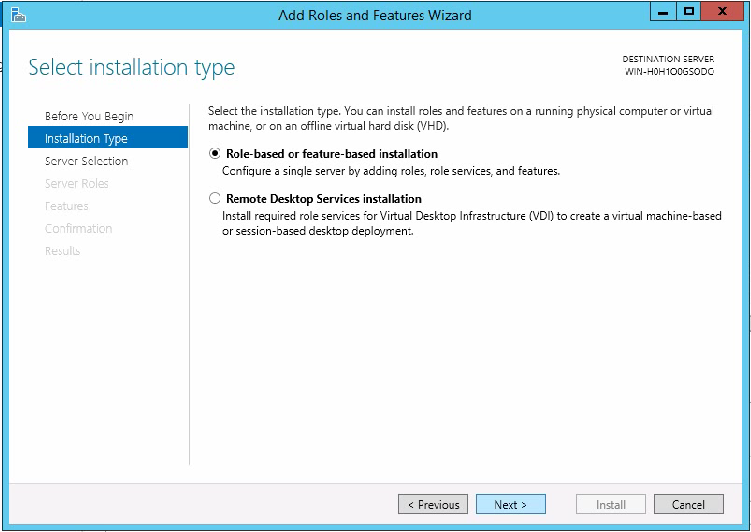
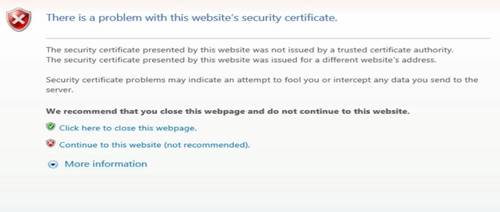
2. On the security certificate page that opens, click Continue to this website (not recommended).
Figure 3 Security certificate confirmation page
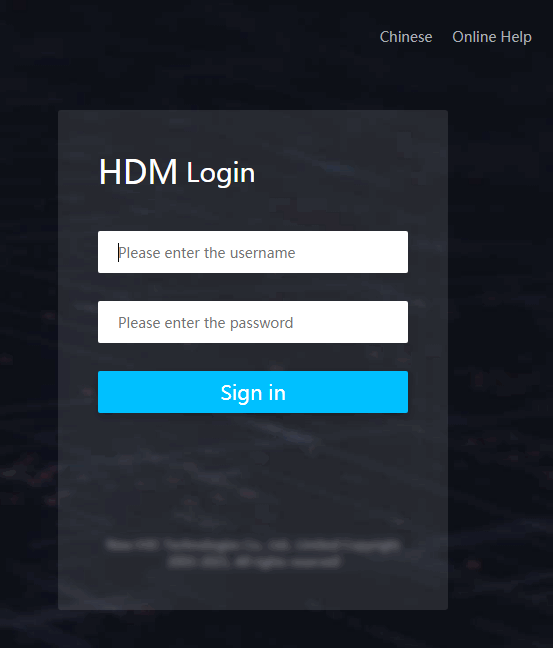
3. On the sign-in page, enter the username and password, and then click Sign in.
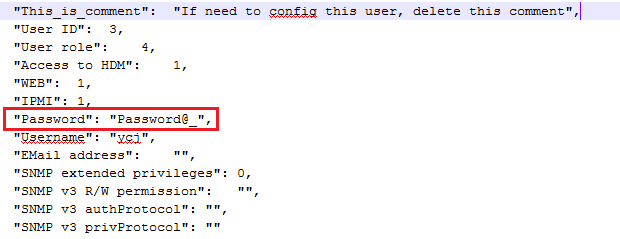
If this is the first sign-in, enter the default username (admin) and password (Password@_). The password is case sensitive.
Figure 4 HDM sign-in page
4. Click Chinese or English to change the language if needed.
5. If this is the first sign-in, change the username and password for security purposes as described in "User accounts."
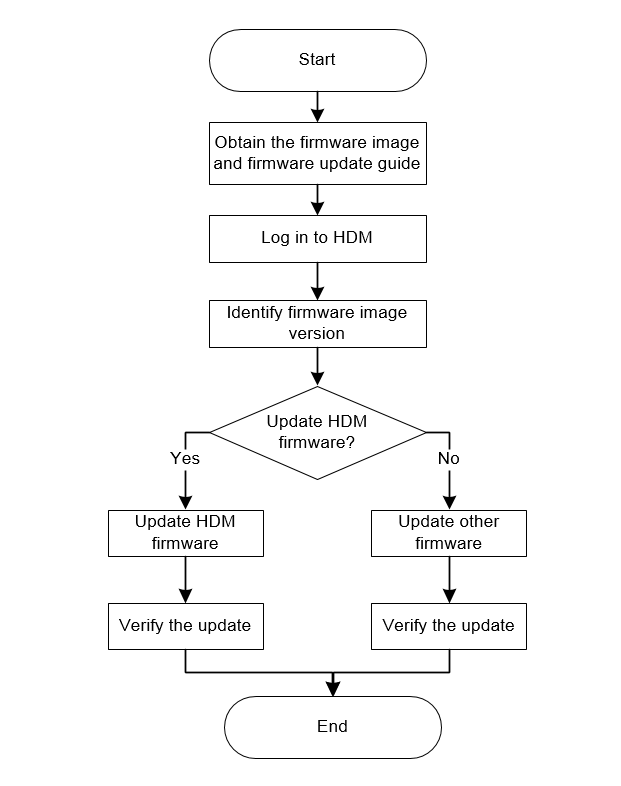
Sign in to HDM for blade servers and AE modules
For blade servers and AE modules, HDM is accessible only from OM. You can access HDM from the Remote Consoles page without being authenticated or by clicking the HDM network IP address from the blade server information page.
Only OM administrator users and operator users that have the HDM access privilege can access HDM from OM.
The HDM sign-in procedure is the same for blade servers and AE modules. This section uses the procedure for blade servers as an example.
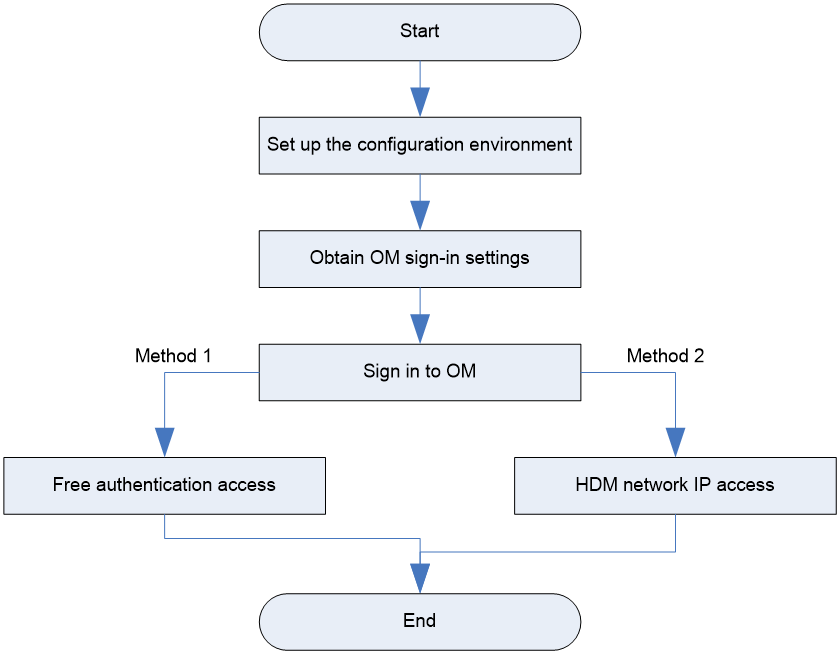
HDM sign-in flowchart
Prepare for an HDM sign-in
Setting up the configuration environment
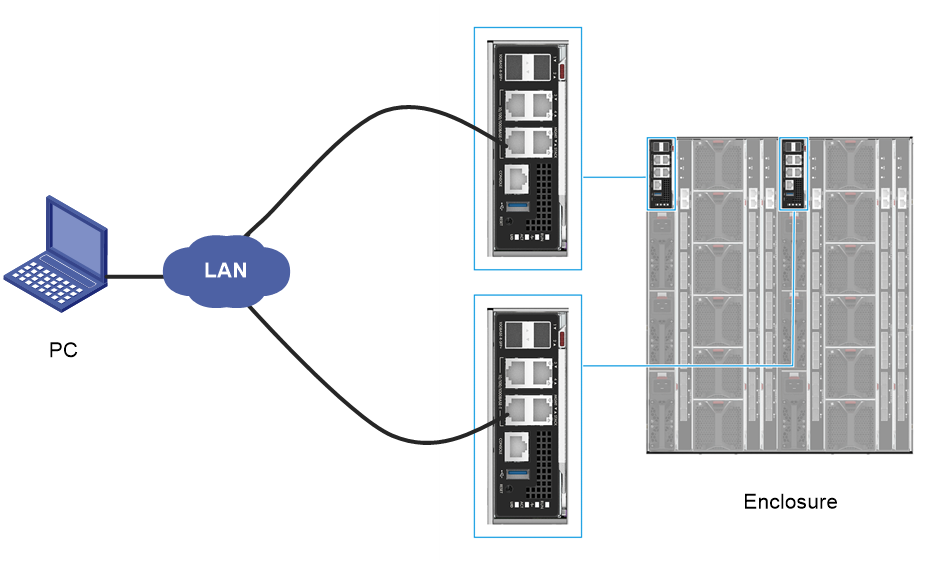
As shown in Figure 5, use a local PC as the HDM client and connect the PC to the management (MGMT) ports on the active and standby OM modules. For more information about port locations, see the labels on the front panel of the OM modules.
Figure 5 Setting up the configuration environment
Obtain OM sign-in settings
To sign in to the OM Web interface, you must obtain its management IP address and user account information. On the first sign-in, use the default settings in Table 5.
Table 5 Default OM sign-in settings
|
Item |
Default setting |
|
IP address |
192.168.100.100/24 |
|
Username |
admin |
|
Password (case-sensitive) |
Password@_ |
Set up the HDM client
HDM does not require installation of client software. You can use a Web browser to access HDM. To ensure login success, follow these restrictions:
· Make sure the IP address of the HDM client is in the same network segment with the management IP addresses of OM modules and HDM. You can obtain the HDM management IP address from the OM Web interface. For more information, see OM online help.
· Make sure the browser and resolution setting of the configuration terminal meet the requirements in Table 6.
Table 6 Browser and resolution requirements
|
Browsers |
Resolution |
|
Google Chrome 58.0 (or higher) |
Recommended: 1600*900 (or higher) |
Sign in to OM
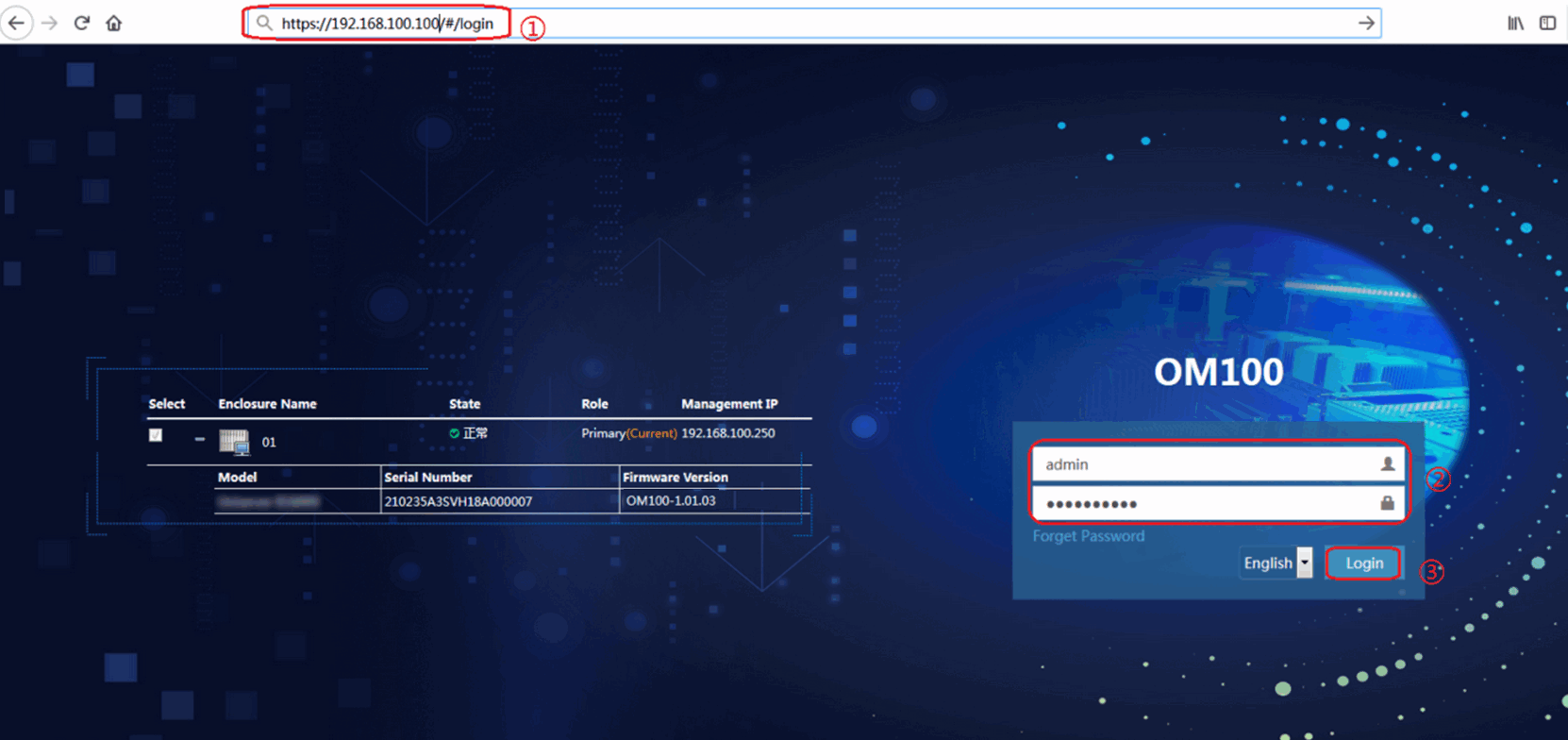
1. Open the browser, and enter the OM management IP address in the format of https://OM_ip_address.
2. On the sign-in page, enter the username and password, and then click Login.
If this is the first sign-in, enter the default username (admin) and password (Password@_). The password is case sensitive.
Figure 6 Signing in to OM
Sign in to HDM
Authentication-free access
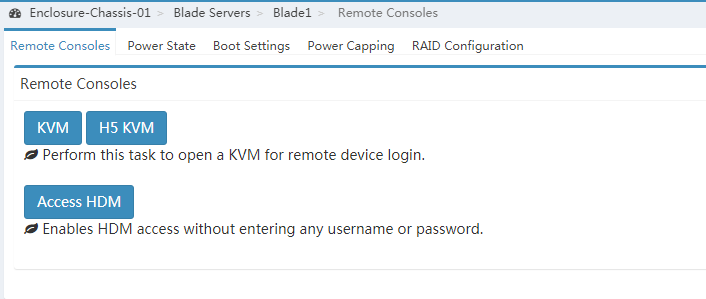
1. In the navigation pane of the OM Web interface, click Blade Servers, select the target server, and then click Remote Consoles.
2. On the Remote Consoles tab, click the Access HDM button to sign in to HDM, as shown in Figure 7.
If this is the first sign-in, click the Proceed to link as shown in Figure 8 to trust the webpage that opens.
Figure 7 Authentication-free access
Figure 8 Confirming the connection
The HDM Web interface opens.
HDM network IP access
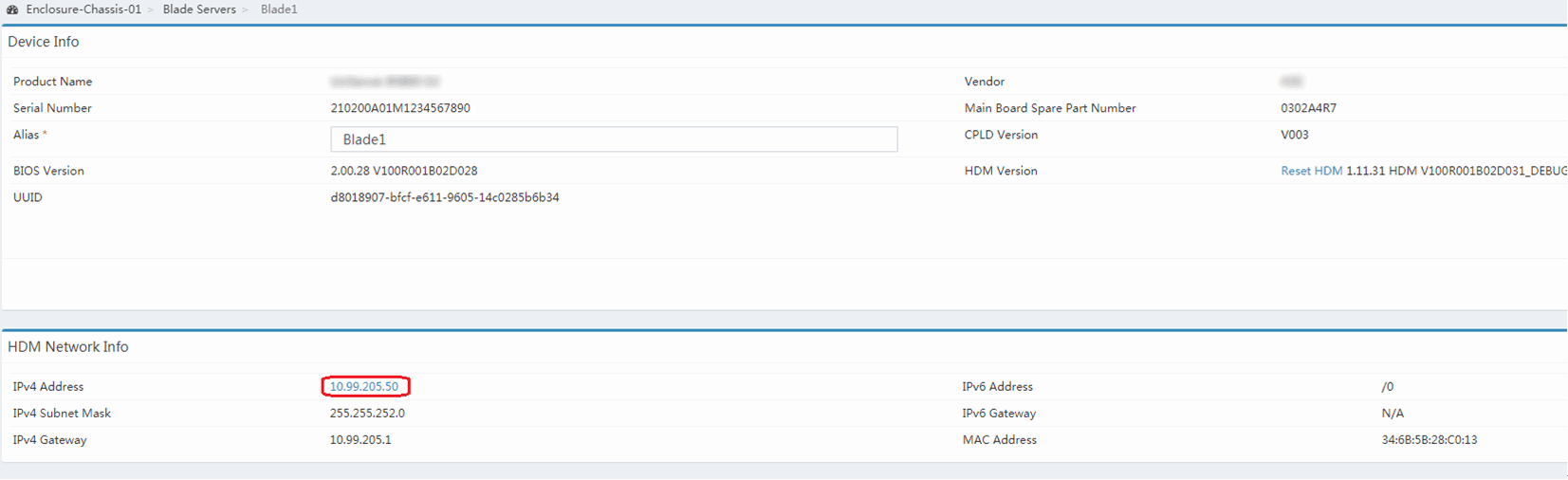
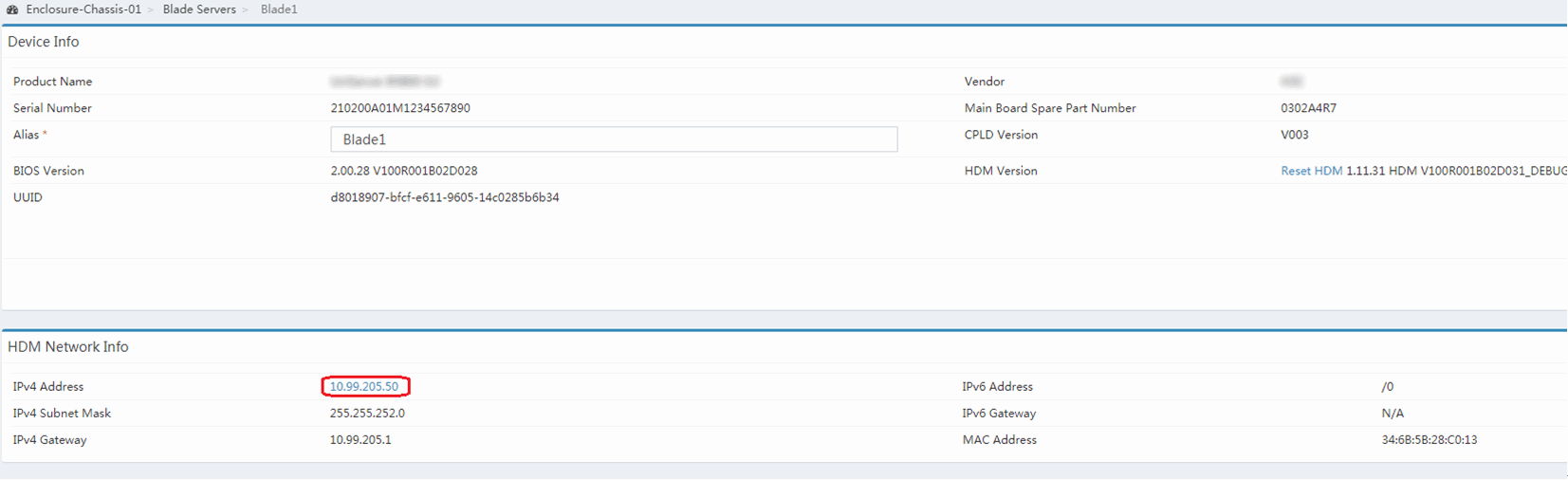
1. In the navigation pane of the OM Web interface, click Blade Servers, and then select the target server.
2. In the HDM Network Info section, click the IP address link from the IPv4 Address field, as shown in Figure 10.
If this is the first sign-in, click the Proceed to link as shown in Figure 8 to trust the webpage that opens.
Figure 10 HDM network IP access
The HDM Web interface opens.
Figure 11 HDM Web interface
Global operations
You can perform the following operations on any HDM page:
· To change the language, click ![]() for English and
for English and ![]() for
Chinese.
for
Chinese.
View device information
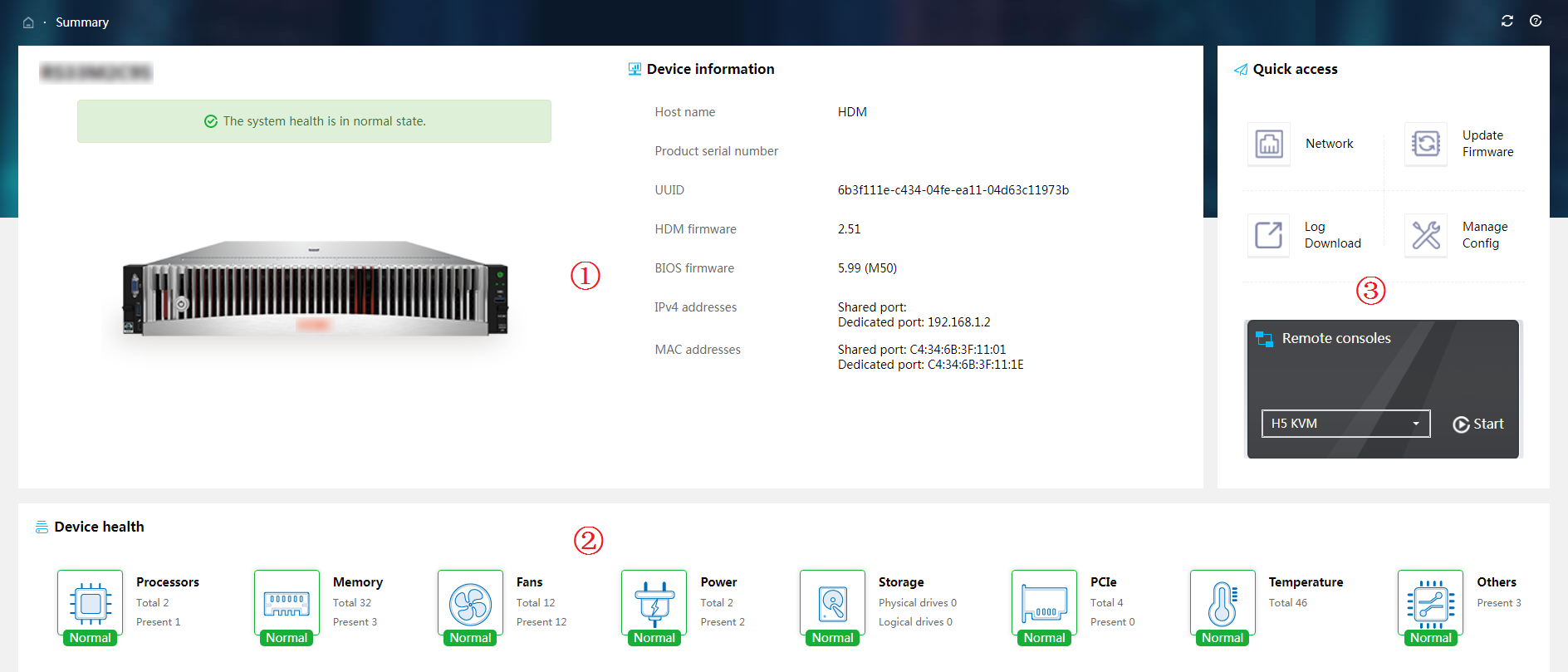
View summary information about the device
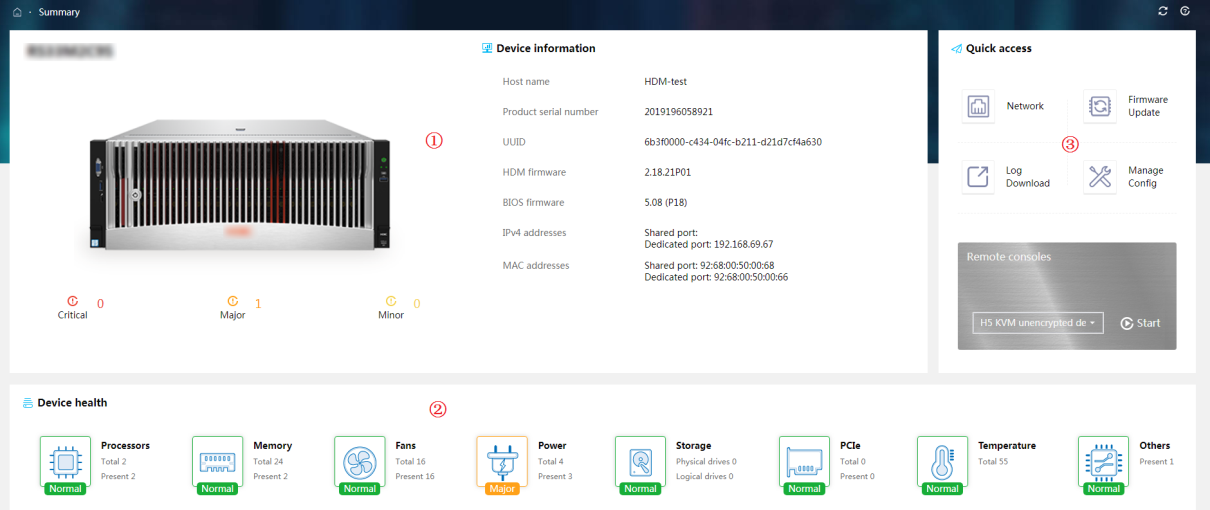
The Dashboard presents summary information about the device, including basic information about the device, system alarm status, device health information, and shortcuts for you to quickly access the desirable function or feature menus.
|
|
NOTE: The Dashboard pages on G3 and G5 servers are slightly different. |
Procedure
Select Dashboard on the top navigation bar. Summary information about the device is displayed.
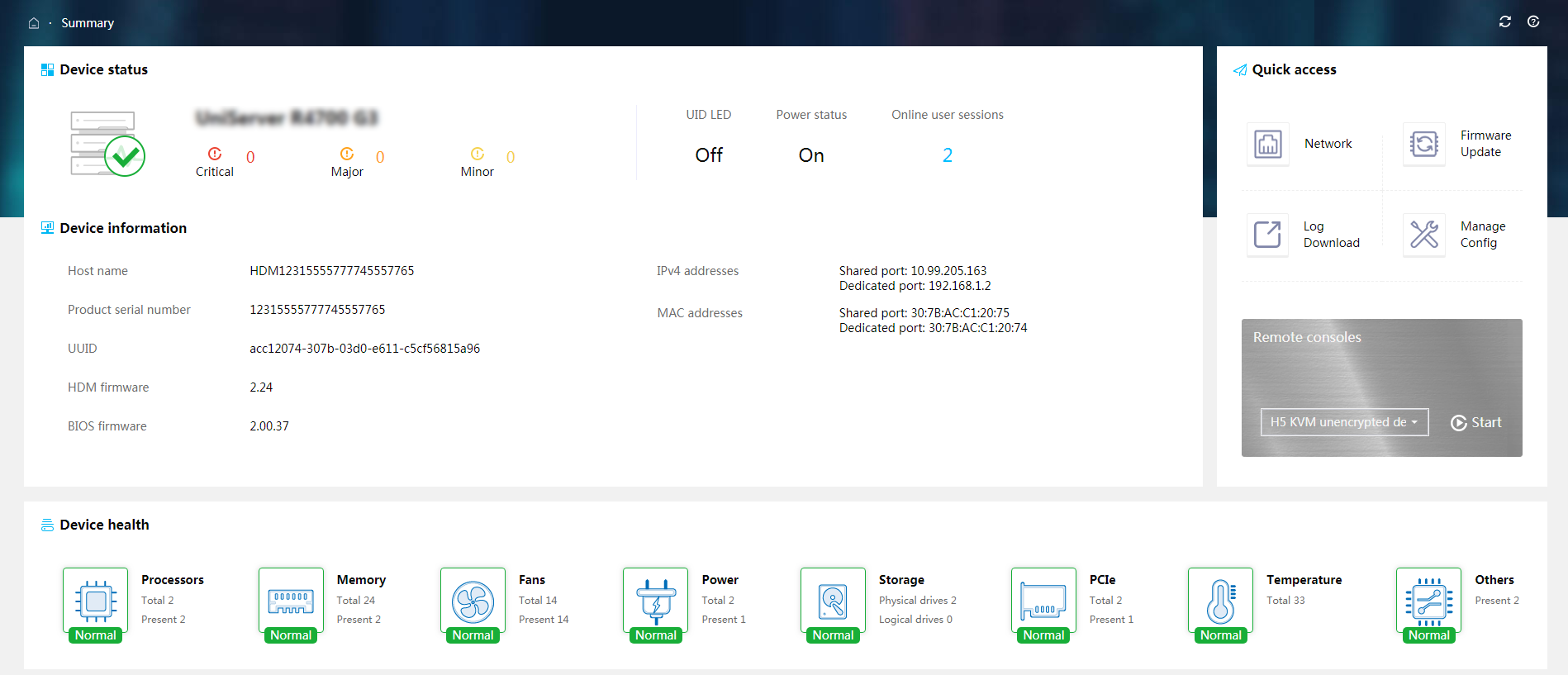
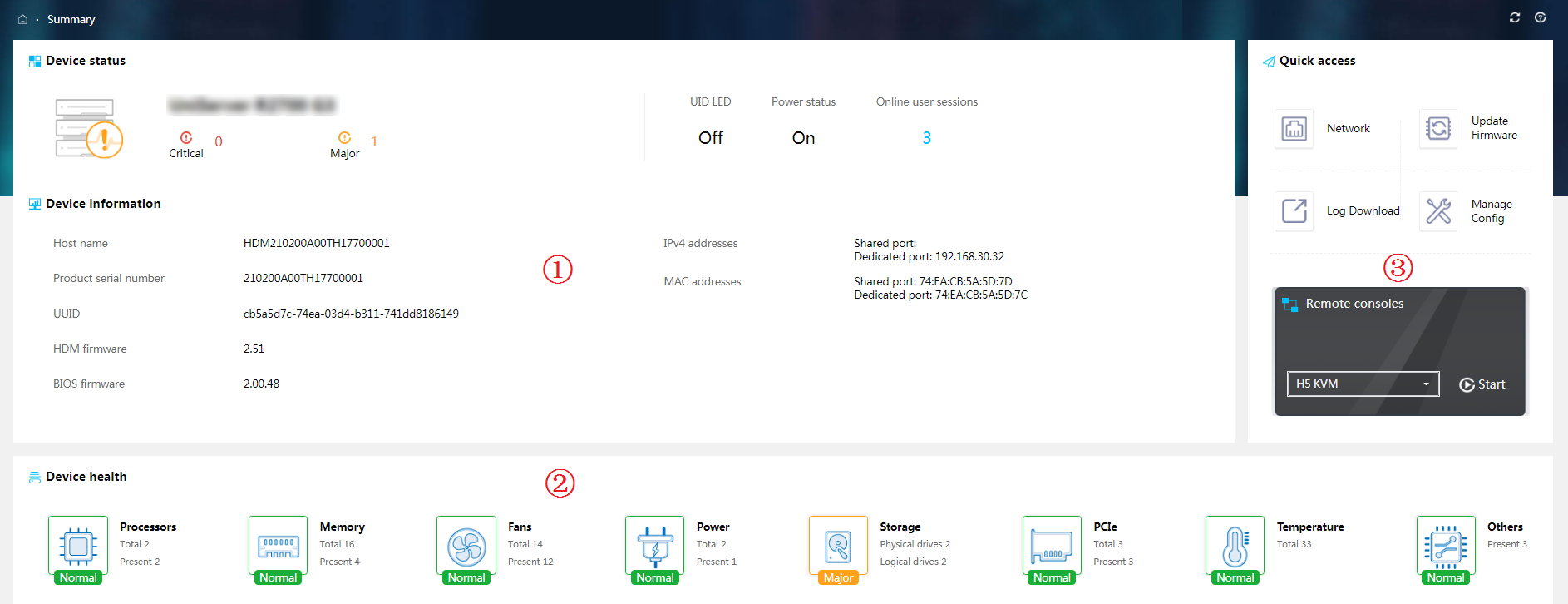
Figure 12 shows summary information for a G3 server. Figure 13 shows summary information for a G5 server.
Figure 12 Summary information (G3 server)
Figure 13 Summary information (G5 server)
Parameters
The work pane provides the following sections:
· Section 1—Displays the server status and basic information about the server.
¡ Health status: Displays health status of the server.
- ![]() Normal—All
server components are operating correctly.
Normal—All
server components are operating correctly.
- ![]() Critical,
Critical, ![]() Major—A minimum
of one component is experiencing issues.
Major—A minimum
of one component is experiencing issues.
¡ UID LED: Displays the status of the UID LED on the server.
- On—The UID LED on the server is steady blue.
- Flashing—The UID LED on the server is flashing blue, indicating that the server is upgrading firmware or the remote console for the server is launched.
- Off—The UID LED on the server is off.
¡ Power status: Displays power status of the server.
- On—The server is powered on.
- Off—The server is powered off.
¡ Number of alarms for each severity level
- Major—The event has serious impact on some subsystems and might result in service interruption. Immediate action is required.
- Critical—The event might result in system crash or shutdown. Immediate action is required.
¡ Basic information about the server, including the following:
- Host name of the server.
- Product serial number of the server.
- Universally Unique Identifier (UUID) of the server.
- Current HDM firmware version
- Current BIOS firmware version.
- Server name. Only blade servers and AE modules support this field. By default, no value is displayed.
- IPv4 addresses of the HDM network ports. This field displays the IPv4 addresses of HDM dedicated and shared network ports if the network port mode is normal or active/standby. If the network port mode is bonding, this field displays the IPv4 address of bond port Bond0.
- MAC address of the HDM network port.
· Section 2—Displays the health status of the device components.
¡ ![]() Normal: The component is operating correctly.
Normal: The component is operating correctly.
¡ ![]() Major: The component performance is degraded
significantly.
Major: The component performance is degraded
significantly.
¡ ![]() Critical: The server might shut down to prevent component
damage.
Critical: The server might shut down to prevent component
damage.
Table 7 Component health status
|
Component |
Health status |
Description |
|
Processors |
The processors are operating correctly. |
|
|
One of the following conditions exists: · An overtemperature condition has occurred. · The processor configuration is incorrect. |
||
|
One of the following conditions exists: · The temperature of a processor has exceeded the critical threshold. · An unrecoverable processor error has occurred. · The primary processor is absent. · BIOS halt has occurred during POST because of a processor error. |
||
|
Memory |
The memory is operating correctly. |
|
|
One of the following conditions exists: · All memory modules are absent or isolated. · An unrecoverable memory error has occurred. · A DIMM is not correctly installed or a DIMM compatibility error occurred. |
||
|
BIOS halt has occurred during POST because of a memory error. |
||
|
Fans |
The fans are operating correctly in redundancy. None of the fans at critical locations has failed. |
|
|
Fan redundancy issue is present because fans at two or more critical locations have failed. |
||
|
Power supplies |
The power supplies are operating correctly. |
|
|
A severe power supply error has occurred. |
||
|
Storage |
All logical drives, physical drives, and storage controllers are operating correctly. |
|
|
One of the following conditions exists: · A logical drive error has occurred. · A major physical drive error has occurred. · A storage controller error has occurred. |
||
|
PCIe modules |
The PCIe modules (network adapters, GPUs, FC HBAs, QAT cards, and FPGA cards) are operating correctly. |
|
|
A bus uncorrectable error, bus fatal error, or PCIe module (network adapter, GPU, FC HBA, QAT card, or FPGA card) error has occurred. |
||
|
Temperature |
All component temperatures are within the normal range. No action is required. |
|
|
A component temperature has crossed a major threshold, but it has not reached a critical threshold. Immediate action is required. |
||
|
A component temperature has crossed a critical threshold. Immediate action is required. |
||
|
Others |
All components are operating correctly. |
|
|
A major error has occurred on a minimum of one component. |
||
|
A critical error has occurred on a minimum of one component. |
· Section 3—Provides shortcuts for you to quickly access the desirable function or feature menus.
To access a remote console, you must first select a remote console type (KVM or H5 KVM). For information about the KVM and H5 KVM launch modes, see "Launch a KVM or H5 KVM remote console."
Buttons
The HDM Web interface provides buttons on the top right corner. Table 8 provides information about the buttons.
|
Button name |
Icon |
Description |
|
UID LED |
The UID LED on the server is steady blue. |
|
|
The UID LED on the server is flashing blue, indicating that the server is upgrading firmware or the remote console for the server is launched. |
||
|
The UID LED on the server is off. |
||
|
Server power |
The server is powered on. When you click this button, the following power options are displayed for you to change the power status of the server. · Force system reset—Warm reboots the server without power cycling the server. · Force power-off—Shuts down the server immediately by force. This action is equivalent to pressing the power button on the server for five seconds. · Graceful power-off—Shuts down the operating system first, and then removes power from the server. · Power on—Starts up the server. · Force power-cycle—Powers off and then powers on the server. |
|
|
The server is powered off. |
||
|
Language |
Changes the language to Chinese. |
|
|
Changes the language to English. |
||
|
Alarm |
Displays detailed information about an alarm. |
|
|
User |
Displays the name and login time of the current user and the number of online users. To display information about all online users, click Details. To log out, click Logout. |
|
|
Refresh |
Refreshes the webpage. |
|
|
Online help |
Accesses the online help. |
System
View summary information
The Summary menu allows you to view information about the server, processors, memory, PCIe modules, sensors, and other components.
The supported configurations vary by server model.
|
|
NOTE: · HDM can display correct, complete processor, memory, and PCIe module information only after the server completes POST. · If the server is off, HDM displays the processor, memory, and PCIe module information obtained at the most recent POST. |
View device information
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
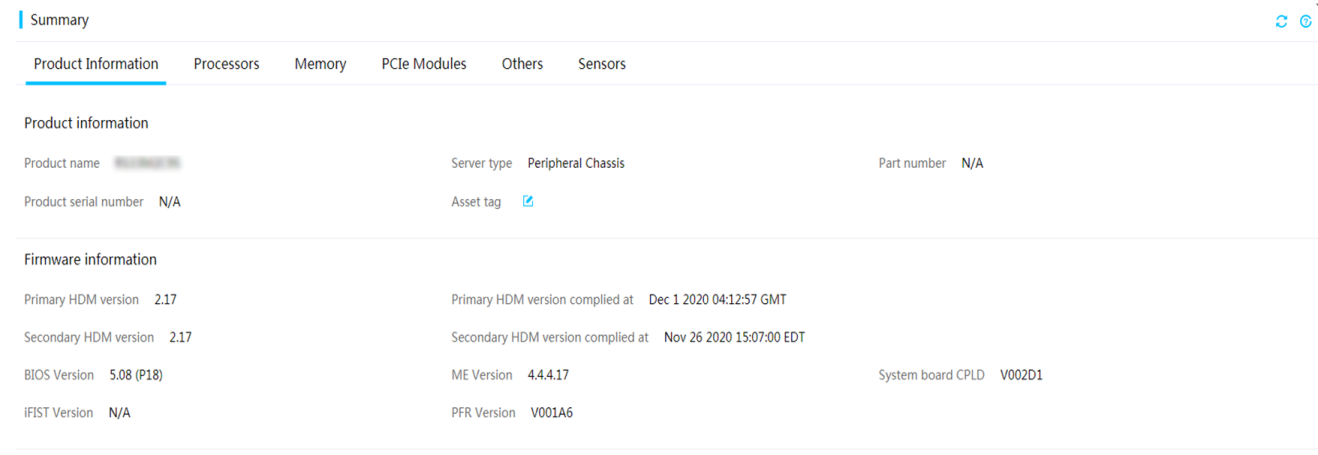
2. Click the Product Information tab to view device and firmware information.
Figure 14 Viewing device information
Parameters
· Product name: Server model.
· Server type: Server type.
· Part number: Part number of the server, which corresponds to the server model. This field displays N/A if the system fails to obtain the server part number.
· Product serial number: Serial number of the server.
· Asset tag: Asset tag of the server. This field is optional. The asset tag is a string of 1 to 48 characters and can contain only letters, digits, spaces, and the following special characters: ` ~ ! @ # $ % ^ & * ( ) _ + - = [ ] { } | ; ' : \ " , . / < > ?
· Primary HDM version: Firmware version of the primary HDM image.
· Primary HDM complied at: Most recent update time of the primary HDM image.
· Secondary HDM version: Firmware version of the backup HDM image.
· Secondary HDM complied at: Most recent update time of the backup HDM image.
· BIOS Version: Version of the Basic Input Output System (BIOS).
· ME Version: Version of the Intel Management Engine (ME). This field is available only for servers installed with an Intel processor.
· System board CPLD version: Version of the system board Complex Programmable Logical Device (CPLD).
· STBCPLD version: Version of the system board STBCPLD firmware. This field is available only for the R6700 G3 server.
· iFIST Version: Current version of the integrated Fast Intelligent Scalable Toolkit (iFIST). The system displays N/A if HDM fails to obtain the iFIST version.
· PFR Version: Version of the PFRCPLD firmware. This field is available only for G5 servers.
View processor information
Perform this task to view summary and detailed processor information and processor errors.
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
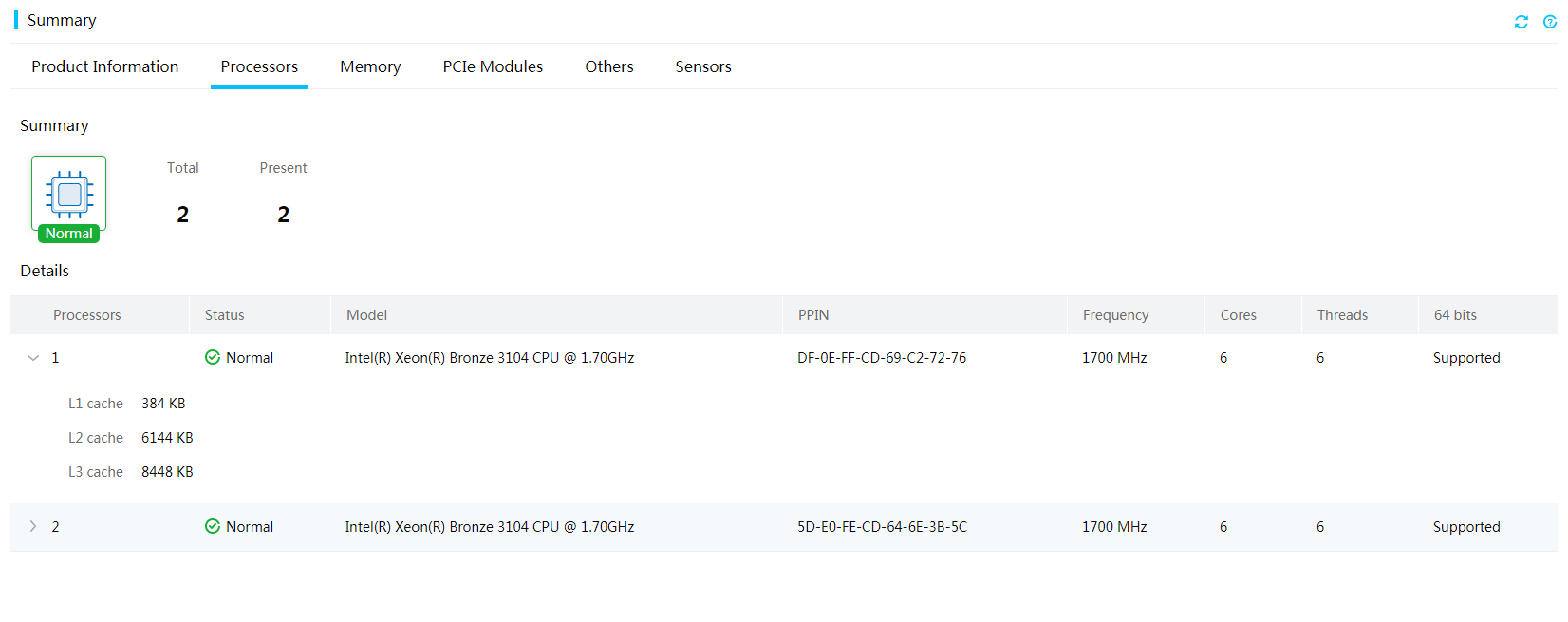
2. Click the Processors tab to view processor information.
Figure 15 Viewing processor information
Parameters
· Status: Operating status of the processor. If a processor is in abnormal state, view the fault description to locate the errors.
· Model: Model of the processor.
· PPIN: Unique product code assigned by the manufacturer. This field displays N/A if HDM fails to obtain the PPIN.
· Frequency: Base frequency of the processor.
· Cores: Cores of the processor.
· Threads: Number of the threads supported by the processor.
· 64 bits: Indicates whether the processor supports 64-bit computing.
· L1 cache: L1 cache of the processor.
· L2 cache: L2 cache of the processor.
· L3 cache: L3 cache of the processor.
· Fault description: Alarms generated for processor errors.
View memory information
Perform this task to view summary and detailed memory information and memory errors.
Restrictions and guidelines
If the Status field for a memory module displays that it is absent, all remaining fields display a tilde (~).
If a DIMM is disabled because of a memory training error, the other DIMM in the same channel will also be disabled.
The memory module slots are colored to indicate the state of the installed memory modules. Color options include:
· Green—The memory module is present and operating correctly.
· Grey—The memory module is absent.
· Grey and striped—The memory module is disabled.
· Yellow—A minor memory error is present.
· Orange—A major memory error is present.
· Red—A critical memory error is present.
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
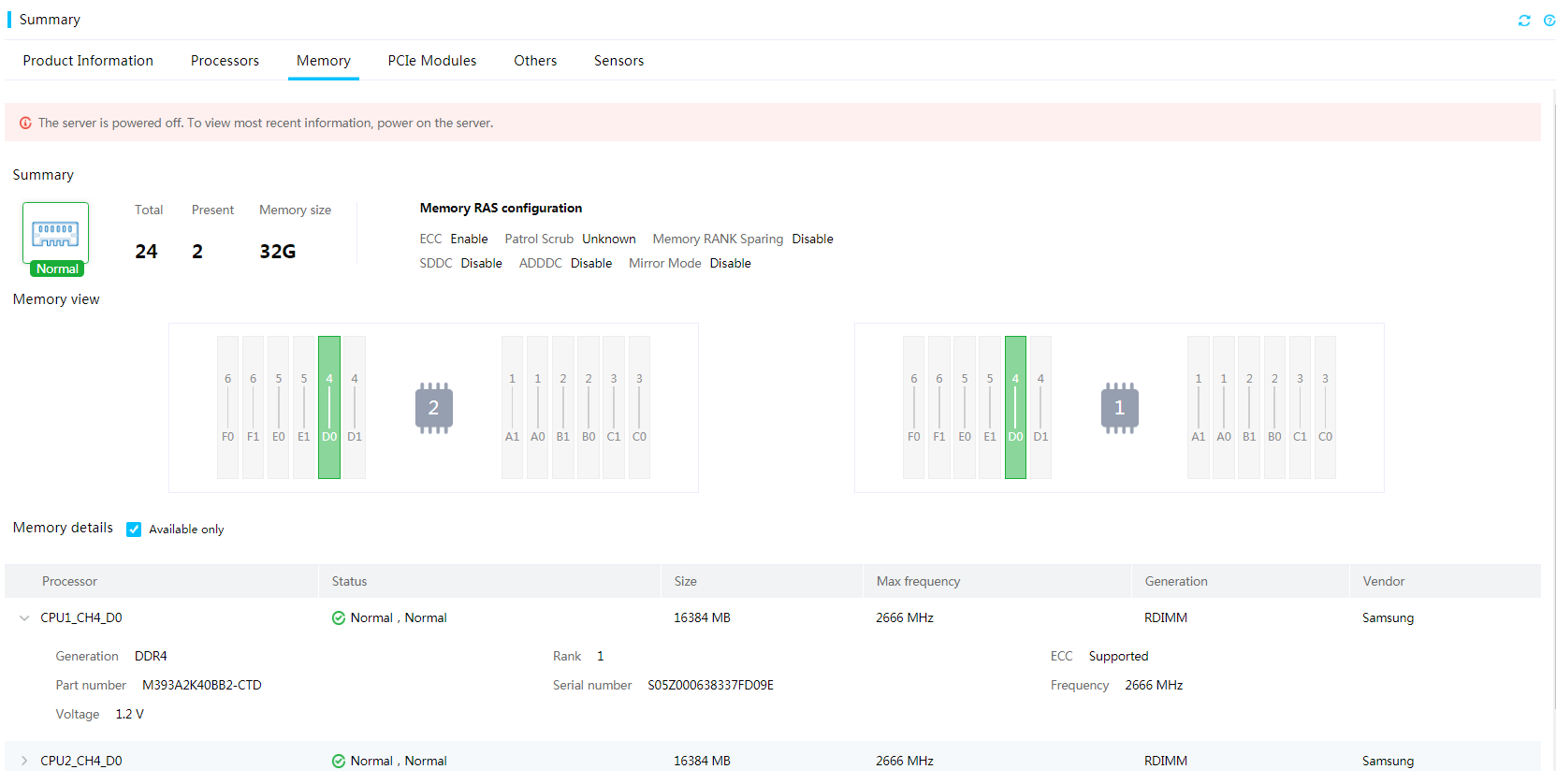
2. Click the Memory tab to view memory information.
3. (Optional.) Select the target compute module to view the corresponding memory information.
Figure 16 Viewing memory information
Parameters
· ECC: Support for error-correcting code (ECC).
· Patrol Scrub: Patrol scrubbing settings. Patrol scrubbing allows a processor to automatically search for and correct correctable memory errors at regular intervals.
· Memory RANK Sparing: Enablement status of Memory RANK Sparing, which reserves some memory in each channel as backup in case of DIMM failures.
· SDDC: Enablement status of DRAM Single Device Data Correction (SDDC), which can correct multiple bit errors in x4 or x8 chips.
· ADDDC: Enablement status of Adaptive Double Device Data Correction Sparing (ADDDC), which can correct two-bit memory errors.
· Mirror Mode: Mirror mode. Options includes:
¡ Disable—Disables memory mirroring.
¡ Full Mirror Mode—Sets the entire 1LM memory in the system to be mirrored.
¡ Partial Mirror Mode—Sets a part of the 1LM memory in the system to be mirrored.
Memory details (available for all DIMMs)
· Location: Processor ID, channel ID, and slot number of a DIMM.
· Status: Health status and authenticity status of a memory module. If a DIMM is in abnormal state, view the fault description to locate the errors. The authenticity status indicates whether the memory is vendor certified and available options include:
¡ Vendor certified—The module has been certified.
¡ Normal—The module has not been certified.
· Size: Capacity of the DIMM.
· Max frequency: Main frequency of the memory module.
· Generation: Generation of the DIMM.
· Vendor: DIMM manufacturer.
· Type: DIMM type.
· Rank: Rank type of the DIMM. Options include SR DIMM, DR DIMM, and QR DIMM.
· ECC: Support for error-correcting code (ECC).
· Serial number: Unique product code assigned by the manufacturer. This field displays N/A if HDM fails to obtain the serial number.
· Part number: Part number of the DIMM. This field displays N/A if HDM fails to obtain the part number.
· Frequency: Frequency at which the memory operates.
· Voltage: Voltage for the memory.
· Fault description: Alarms generated for DIMM errors.
View PCIe module information
Restrictions and guidelines
This feature is available only when a PCIe module is present and the present PCIe module supports information obtaining.
If the system cannot obtain the current power, verify that the GPU driver has been installed.
To enable the Management Component Transport Protocol (MCTP) feature, first update the system firmware to a version that supports MCTP. Then, access the BIOS setup utility, access the Advanced > Platform Configuration > Server ME Configuration menu, enable MCTP proxy, and then restart the server.
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
2. Click the PCIe Modules tab to view PCIe module information.
3. To view information about a type of PCIe modules, click the corresponding tab.
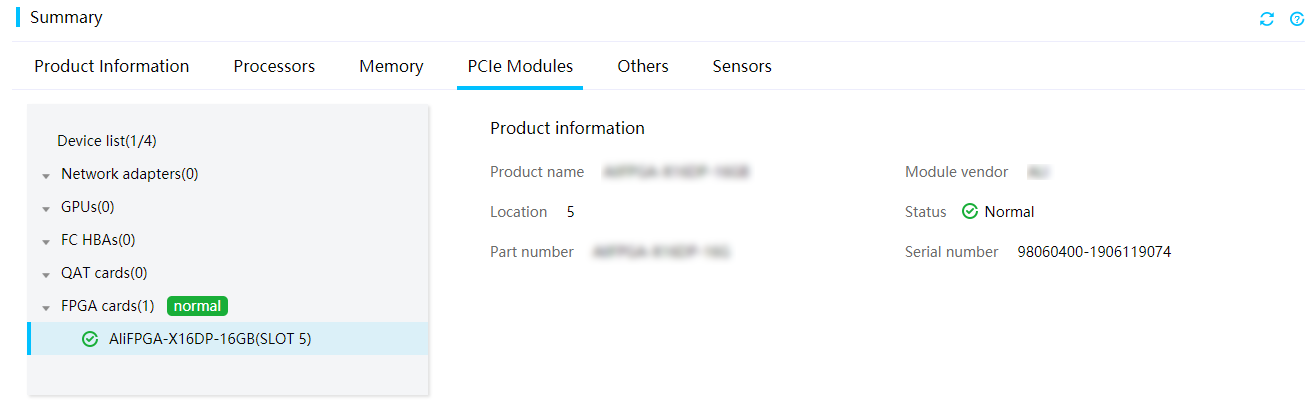
Figure 17 Viewing PCIe module information
Parameters
Device list
· Slot: Slot of the PCIe module. For more information about slot locations, see the user guide for the server.
· Status: PCIe module status, including Normal and Abnormal.
· Product name: Model of the PCIe module.
· Module vendor: Manufacturer of the PCIe module.
· Chip vendor: Chip manufacturer of the PCIe module.
· Serial number: Unique product code assigned by the manufacturer. This field displays N/A if HDM fails to obtain the serial number.
· Part number: Part number of the PCIe module, which corresponds to the model of the PCIe module. This field displays N/A if HDM fails to obtain the part number.
· Max speed: Maximum PCIe link rate.
· Negotiated speed: Auto-negotiated PCIe link rate.
· Max protocol: Supported latest generation of the PCIe standard.
· Negotiated protocol: Auto-negotiated generation of the PCIe standard.
· Max link width: Maximum link width supported by the PCIe slot.
· Device max link width: Maximum link width supported by the PCIe device.
· Negotiated link width: Auto-negotiated link width of the PCIe module.
· Mezzanine slot: Slot number of the mezzanine PCIe module. This field is displayed only for blade servers.
· Processor: Processor to which the PCIe module is subordinate to. Support for this field depends on the device model.
· Riser connector: Connector number of the riser card where the PCIe module is installed.
Network adapters
· Product name: Name of the network adapter.
· Port: Port type of the network adapter.
· Module vendor: Manufacturer of the network adapter.
· Chip vendor: Chip manufacturer of the network adapter.
· Mezzanine slot: Slot number of the mezzanine PCIe module. This field is displayed only for blade servers.
· Firmware: Firmware version of the network adapter.
· Status: Network adapter health status. If a network adapter is in abnormal state, review the event logs to locate the errors.
· Location: Physical location of the network adapter.
· Serial number: Unique product code assigned by the manufacturer. This field displays N/A if HDM fails to obtain the serial number.
· Part number: Part number of the PCIe module, which corresponds to the model of the PCIe module. This field displays N/A if HDM fails to obtain the part number.
· Network port: Network ports on the network adapter.
· MAC address: MAC address of the network port.
· PCIe Address: PCIe address of the network adapter, which contains the Bus:Device:Function (BDF) information:
¡ Bus: Bus number of the network adapter.
¡ Device: Device number of the network adapter.
¡ Function: Function number of the network adapter.
· Negotiated speed: Negotiated speed of the network port. This field displays N/A if HDM fails to obtain the negotiated speed.
· Port type: Network port type. Options include Fiber and Copper.
· Port connection: Displays whether a cable is connected to the network port. Options include Connected and Disconnected. This field displays N/A if HDM fails to obtain the connection status.
· Fault description: Event log information about an error on the PCIe module.
· LLDP: Enablement status of LLDP for the network port. You can enable or disable LLDP as needed. If the field is not configurable, the network port does not support LLDP. After enabling or disabling LLDP, you must restart the server for the change to take effect.
GPUs
· Product name: Model of the GPU.
· Vendor name: Manufacturer of the GPU.
· Firmware version: Firmware version of the GPU.
· Status: GPU health status. If a GPU is in abnormal state, review the event logs to locate the errors.
· Location: Number of the slot in which the GPU resides. For information about the slot location, see the user guide for the server.
· Part number: Part number of the GPU, which corresponds to the model of the GPU module. This field displays N/A if HDM fails to obtain the part number.
· Serial number: Unique product code assigned by the vendor. This field displays N/A if HDM fails to obtain the serial number.
· Power: Current power of the GPU.
· Fault description: Event log information about an error on the PCIe module.
FC HBAs
· Product name: Model of the FC HBA.
· Vendor name: Manufacturer of the FC HBA.
· Firmware version: Firmware version of the FC HBA.
· Status: FC HBA health status. If an FC HBA is in abnormal state, review the event logs to locate the errors.
· Location: Location of the FC HBA.
· WWPN: Worldwide port number (WWPN) for the network port.
· WWNN: Worldwide node name (WWNN) for the network port.
· Port connection: Displays whether a cable is connected to the network port. Options include Connected and Disconnected. This field displays N/A if HDM fails to obtain the connection state.
· Speed: Speed of the network port. This field displays N/A if HDM fails to obtain the speed.
· Fault description: Event log information about an error on the PCIe module.
QAT cards
· Product name: Model of the QAT card.
· Module vendor: Manufacturer of the QAT card.
· Chip vendor: Chip manufacturer of the QAT card.
· Status: QAT card health status. If a QAT card is in abnormal state, review the event logs to locate the errors.
· Location: Number of the slot in which the QAT card resides. For information about slot locations, see the user guide for the server.
· Part number: Part number of the QAT card, which corresponds to the model of the QAT card. This field displays N/A if HDM fails to obtain the part number.
· Serial number: Unique product code assigned by the vendor. This field displays N/A if HDM fails to obtain the serial number.
· Fault description: Event log information about an error on the PCIe module.
FPGA cards
· Product name: Model of the FPGA card.
· Module vendor: Manufacturer of the FPGA card.
· Status: FPGA card health status. If an FPGA card is in abnormal state, review the event logs to locate the errors.
· Location: Number of the slot in which the FPGA card resides. For information about the slot location, see the user guide for the server.
· Part number: Part number of the FPGA card, which corresponds to the model of the FPGA card. This field displays N/A if HDM fails to obtain the part number.
· Serial number: Unique product code assigned by the vendor. This field displays N/A if HDM fails to obtain the serial number.
· Fault description: Event log information about an error on the PCIe module.
View information about other components
Restrictions and guidelines
HDM displays component information only about present components.
The supported components vary by server model.
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
2. Click the Others tab.
3. Select the target component type to view the corresponding component information.
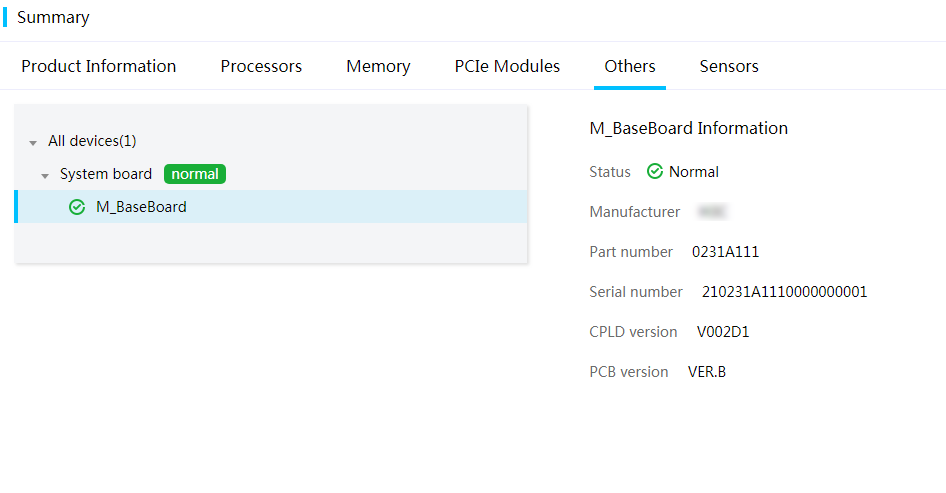
Figure 18 Viewing information about other components
Parameters
· Status: Component health status. If a component is in abnormal state, review the event logs to locate the errors.
· Manufacturer: Manufacturer of the component.
· Part number: Part number of the component, which corresponds to the component model. This field displays N/A if HDM fails to obtain the part number.
· Serial number: Unique product code assigned by the manufacturer. This field displays N/A if HDM fails to obtain the serial number.
· CPLD version: Version of the CPLD firmware.
· STBCPLD version: Version of the system board STBCPLD firmware. This field is available only for the R6700 G3 server.
· AUXCPLD version: Version of the AUXCPLD firmware. This field is available only for some blade servers.
· PCB version: Version of the Printed Circuit Board (PCB) firmware.
· Module model: Model of the drive backplane.
· Current firmware version: Firmware version of the drive backplane.
· Current configuration file version: Configuration file version of the drive backplane.
· Bootloader version: Bootloader version of the drive backplane.
· EEPROM version (for firmware): Electrically erasable programmable read only memory (EEPROM) version of the drive backplane.
· Fault description: Event log information about errors on the components.
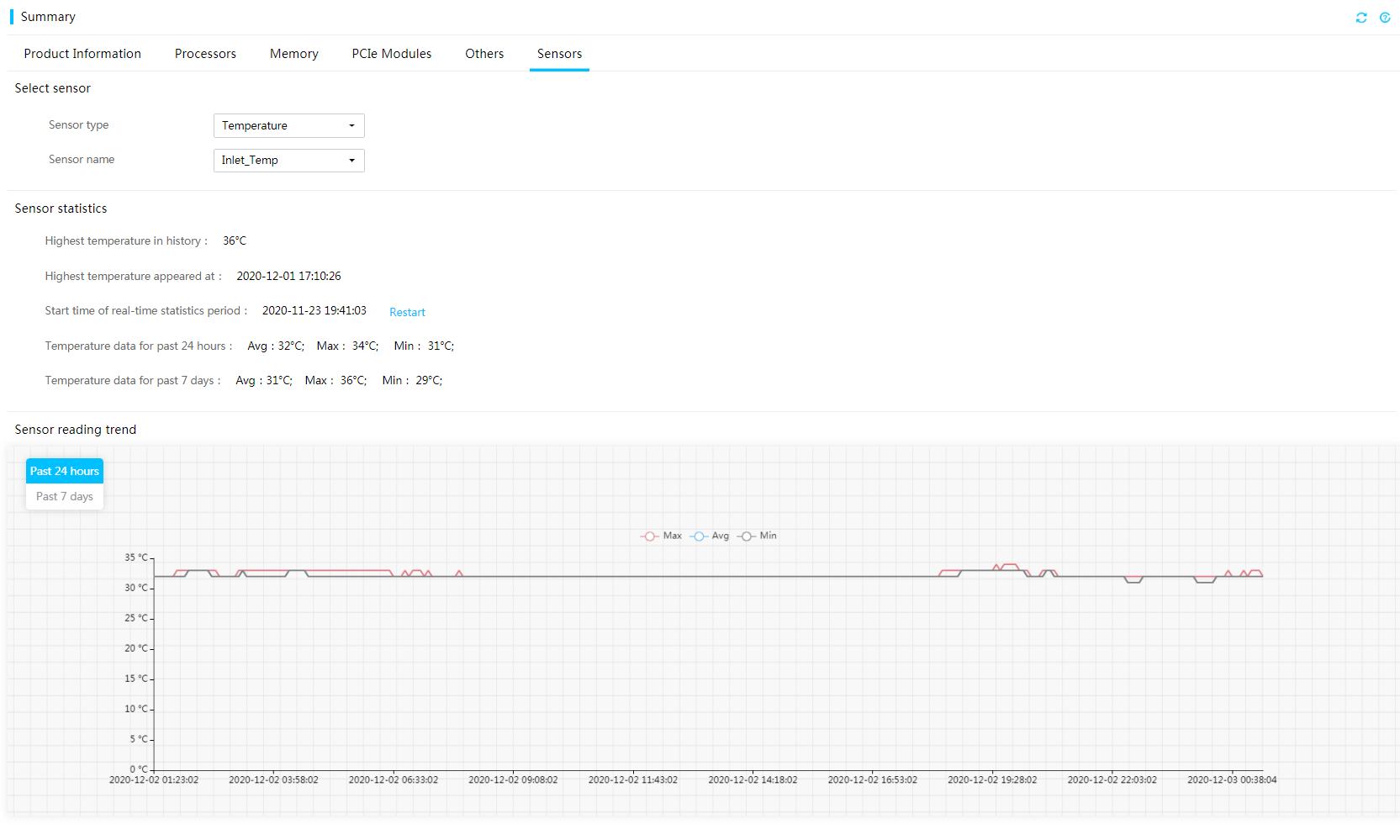
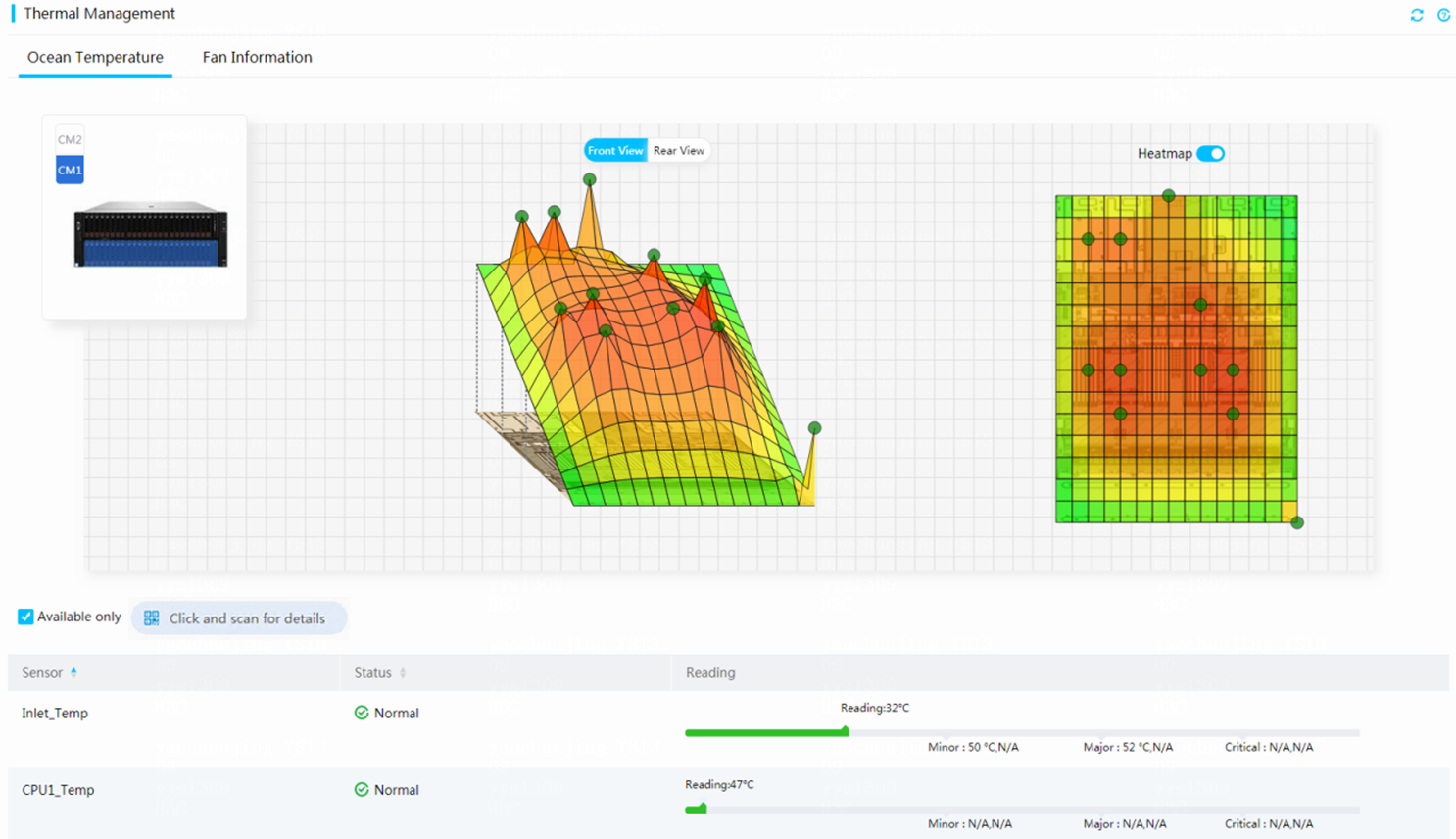
View the sensor reading chart
Perform this task to view the sensor readings in a line chart.
The system collects sensor readings at intervals of 5 minutes.
Restrictions and guidelines
R4950 G3 and R4950 G5 servers support displaying only the average sensor readings.
HDM cannot obtain the sensor readings during restart.
Restoring HDM settings clears the sensor reading statistics.
Only linear sensors support this feature.
Procedure
1. On the top navigation bar, click System.
You are placed on the Summary page.
2. Click the Sensors tab to view the corresponding information.
3. To view sensor readings on the Sensors tab, select a sensor type and name. You can perform the following tasks in the work pane:
¡ To clear the history readings and start a new statistics collection period, click Restart.
¡ To view sensor readings for the past 24 hours or past 7 days in the line chart, select Past 24 hours or Past 7 days. You can hover over the lines in the chart to view the minimum, average, and minimum readings during the statistics collection period.
¡ To
view only the maximum, average,
or minimum sensor readings,
click the ![]() Max,
Max, ![]() Avg, or
Avg, or ![]() Min icon, respectively.
Min icon, respectively.
Figure 19 Viewing the sensor reading chart
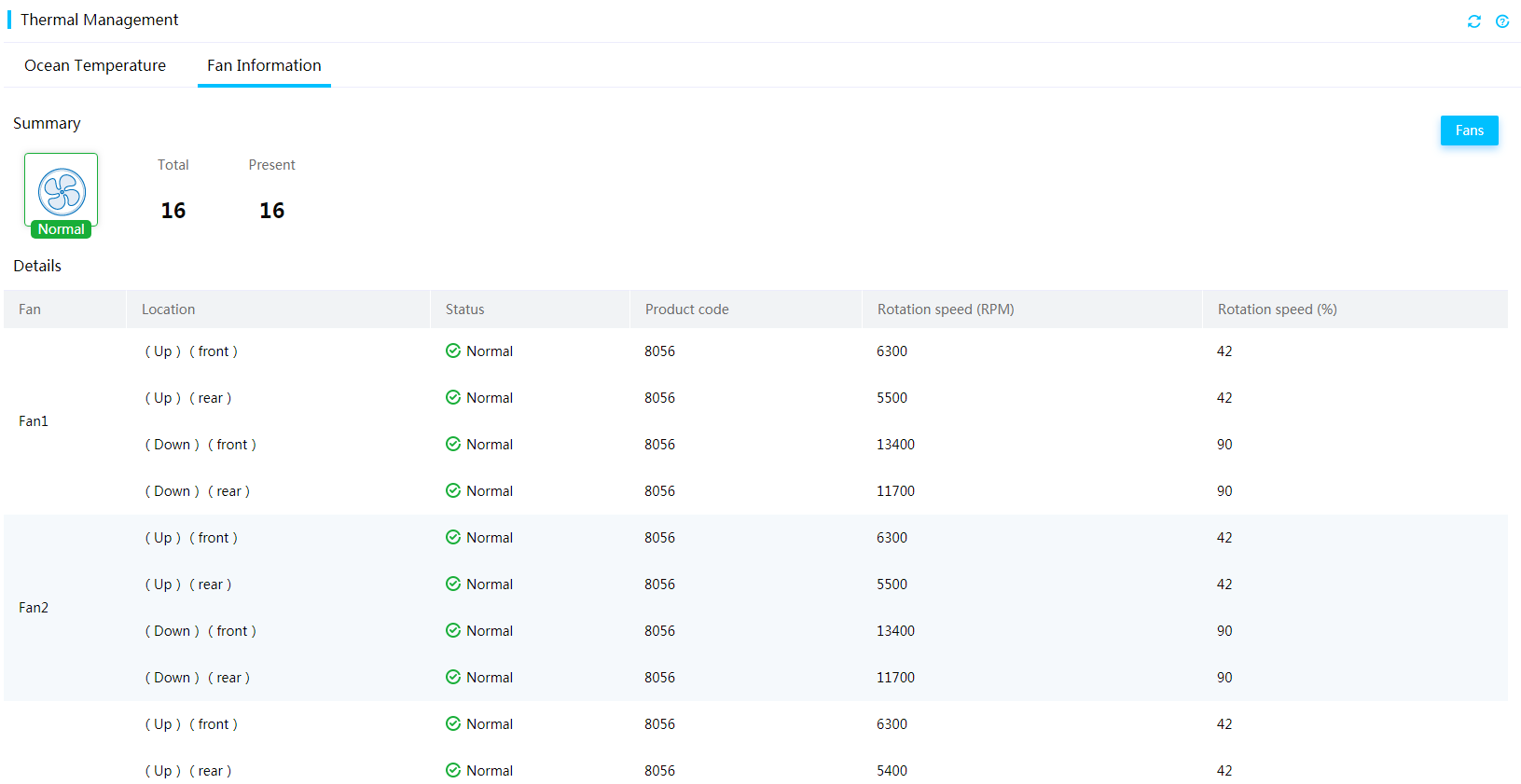
Storage
The Storage menu allows you to perform the following tasks:
· View information about storage controllers, logical drives, physical drives, and storage errors.
· Manage physical and logical drives controlled by the following storage controller in an out-of-band manner:
¡ RAID-LSI-9361-8i(1G)-A1-X
¡ RAID-LSI-9361-8i(2G)-1-X
¡ RAID-LSI-9361-8i(2G)
¡ RAID-LSI-9460-8i(2G)
¡ RAID-LSI-9460-8i(4G)
¡ RAID-LSI-9460-16i(4G)
¡ HBA-LSI-9440-8i
¡ RAID-L460-M4
¡ RAID-P5408-Mf-8i-4GB
¡ RAID-P5408-Ma-8i-4GB
¡ HBA-H5408-Mf-8i
¡ RAID-LSI-9560-LP-16i-8GB
¡ RAID-LSI-9560-LP-8i-4GB
For more compatibility information, visit the OS compatibility query tool at http://www.h3c.com/cn/Service/Document_Software/Document_Center/Server/.
|
|
NOTE: In HDM-2.96 and later versions, you can scan the QR code on the screen to view the function diagram or give feedback. |
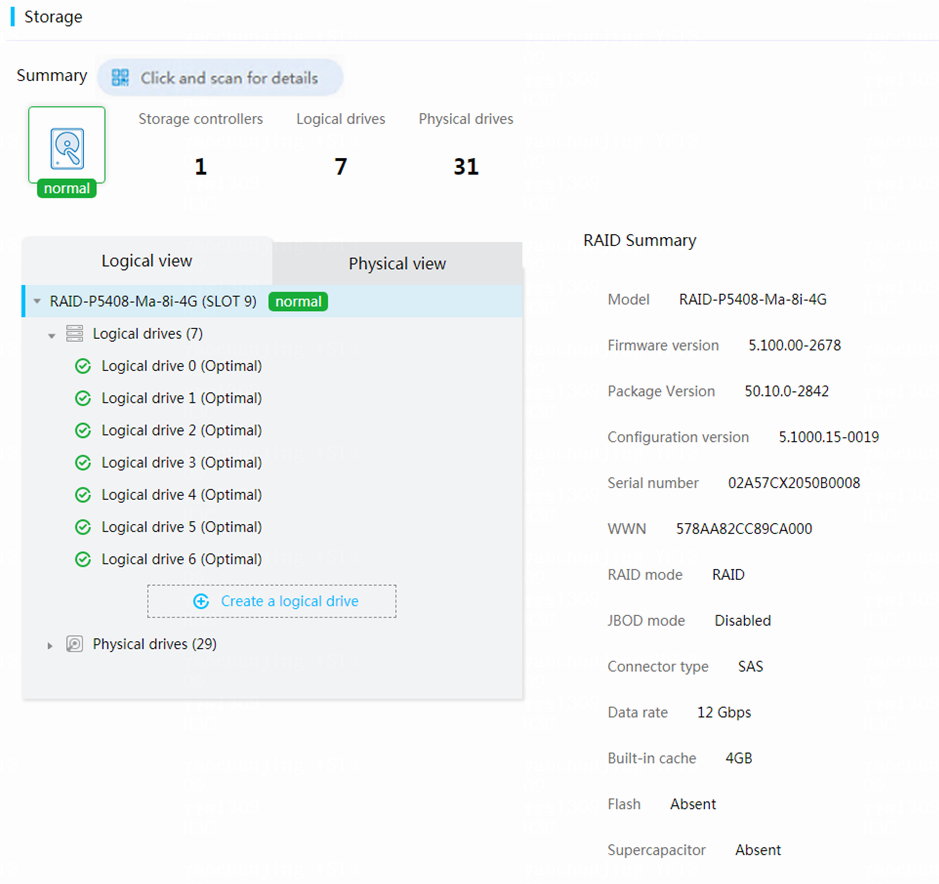
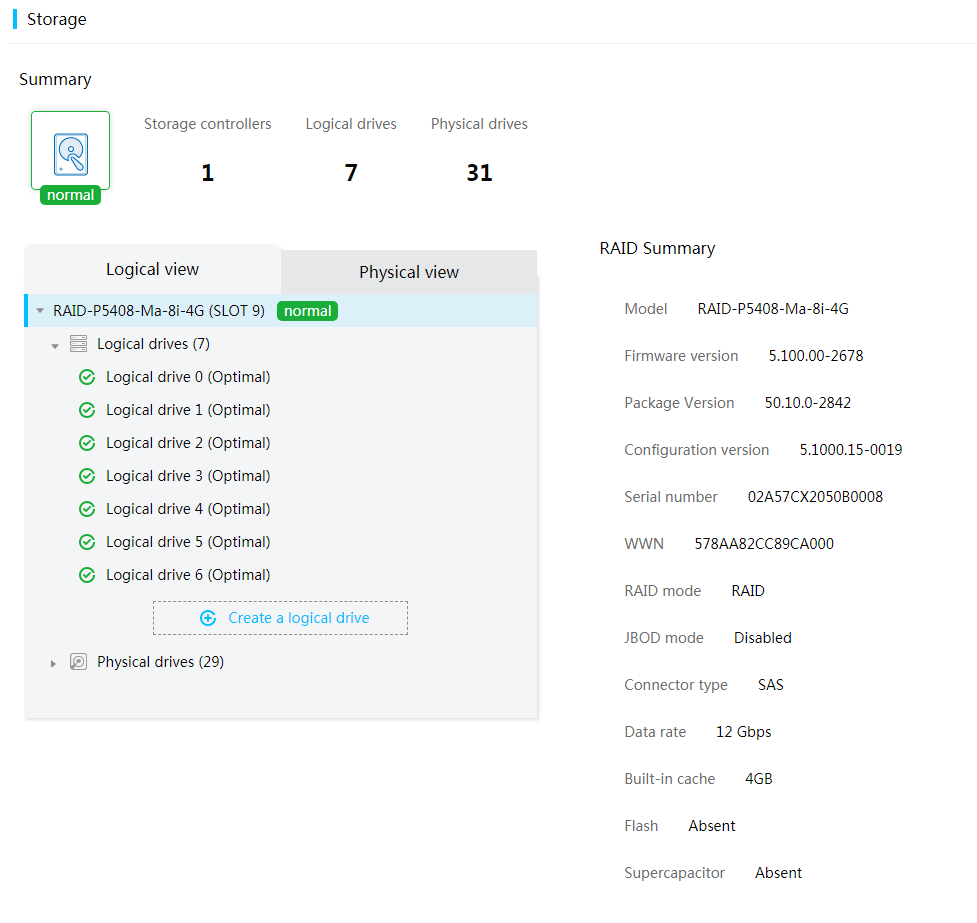
View storage summary information
1. On the top navigation bar, click System.
2. In the left navigation pane, select Storage.
3. View storage summary information, including the health status of the storage system, the numbers of storage controllers, logical drives, and physical drives, and fault descriptions.
If the health status is abnormal, check the fault descriptions and review the event logs to locate the errors.
Figure 20 Viewing storage summary information
View storage controller information
Perform this task to view information about storage controllers.
Restrictions and guidelines
Refresh the Storage page to obtain the update-to-date storage information after the server OS starts up successfully.
Storage controllers that do not support RAID do not have logical views.
HDM cannot obtain storage and temperature information about LSI HBAs that do not support out-of-band management.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Storage.
3. On the Logical view tab, select a storage controller.
Figure 21 Viewing storage controller information
Parameters
Storage controller
· Model: Model of the storage controller.
· Vendor: Vendor of the storage controller.
· Firmware version: Firmware version of the storage controller.
· Package version: Software package version of the storage controller. This field is available only for some LSI storage controllers.
· Configuration version: Configuration version of the storage controller.
· Serial number: Serial number of the storage controller.
· WWN: SAS address of the storage controller.
· Mode: Storage controller mode.
¡ For the LSI storage controller, supported options include RAID and JBOD.
¡ For the PMC storage controller, supported options include RAID, HBA, Mixed, Simple volume, and Auto volume.
· JBOD mode: Enablement status of JBOD mode in the BIOS.
· Connector type: Connector type supported by the storage controller.
· Data rate: Data rate supported by the connectors of the storage controller.
· Built-in cache: Capacity of the read/write cache embedded in the storage controller.
· Flash: Status of the flash card of the power fail safeguard module.
¡ For an LSI storage controller, status options include:
- Normal—The flash card is operating correctly.
- Abnormal—The flash card is operating incorrectly.
- Absent—The flash card is not connected to the supercapacitor, not installed securely, or not installed at all.
¡ For a PMC storage controller, status options include:
- Normal—The flash card is operating correctly.
- Absent—The flash card of the power fail module is not securely installed or is not installed at all.
- Abnormal_status code—The flash card is operating incorrectly. You can check the status code to identify the exceptions that cause the flash card to enter the abnormal state.
- Warning_status code—A warning is present on the flash card. You can check the status code to identify the exceptions that cause the flash card to enter the warning state.
A status code is a hexadecimal number. To identify the exceptions, convert the hexadecimal status code into a 16-digit binary number (bit 0 to bit 15 from the right to the left). A set bit means that the exception indicated by the bit is present. For information about a set bit and its corresponding exception, see Table 9.
For example, if the status code is 0x500 (binary format 0000 0101 0000 0000), exceptions indicated by bit 8 and bit 10 are present on the flash card.
Table 9 Flash card exceptions and their set bits
|
Bit# |
Bit state |
Description |
|
0 |
1 |
GB subsystem is currently initializing. |
|
1 |
1 |
GB subsystem is in ready state. |
|
2 |
1 |
GB subsystem is executing a learning cycle. Learning cycles do not disrupt normal operation or the ability to protect data. |
|
3 |
1 |
GB subsystem has failed. |
|
4 |
1 |
The supercapacitor pack has exceeded the maximum temperature threshold. |
|
5 |
1 |
The supercapacitor pack has exceeded the warning temperature threshold. |
|
6 |
1 |
The supercapacitor pack is over voltage. |
|
7 |
1 |
The supercapacitor pack has exceeded the maximum charging current. |
|
8 |
1 |
GB subsystem learning cycle has passed. |
|
9 |
1 |
GB subsystem learning cycle has failed. |
|
10 |
1 |
The supercapacitor pack has failed. |
|
11 |
1 |
The supercapacitor pack is nearing the end of its life. Replacement is recommended. |
|
12 |
1 |
The supercapacitor pack has reached the end of its life. Replacement is required. |
|
13 |
1 |
One of the capacitors in the supercapacitor pack seems to be missing. |
|
14 |
N/A |
Reserved. |
|
15 |
N/A |
Reserved. |
|
|
NOTE: The Green backup (GB) system reports several types of operation status progress and health information. |
· Supercapacitor: Presence status of the supercapacitor.
· Charging status: The remaining amount of power available with the supercapacitor.
· RAID levels: RAID levels supported by the storage controller. For PMC storage controllers, RAID1(Triple) and RAID10(Triple) are displayed as RAID1(ADM) and RAID10(ADM), respectively.
|
|
NOTE: The Flash and Charging status fields are available only if a power fail safeguard module is installed. A power fail safeguard module contains a flash card and a supercapacitor. When a system power failure occurs, this supercapacitor can provide power for a minimum of 20 seconds. During this interval, the storage controller transfers data from memory to the flash card, where the data remains indefinitely or until the controller retrieves the data. |
Manage logical drives
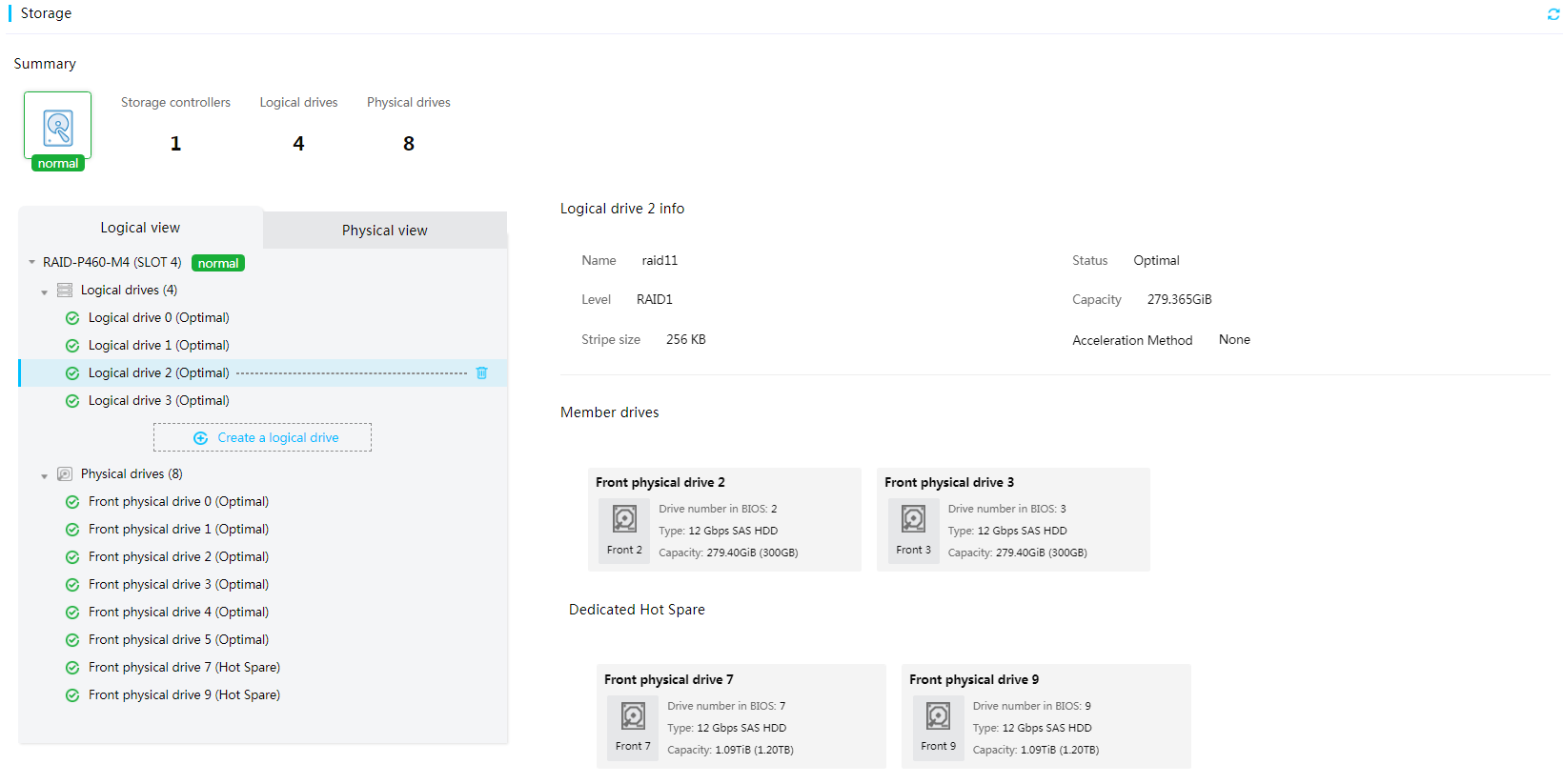
Perform this task to view logical drive information and create logical drives.
Restrictions and guidelines
After you create or delete a logical drive, wait a few moments for the system to complete the operation and then refresh the page to verify the operation result.
A physical drive can be used to create only one logical drive.
The default maximum capacity of a logical drive might be slightly different from the maximum capacity you can set. If you do not specify a drive capacity when creating a logical drive, the drive capacity is the default maximum capacity calculated by the system.
You can view and set the enablement status of JBOD mode from the BIOS only for some LSI storage controllers in RAID mode.
A storage controller can manage a maximum of 64 logical drives through HDM.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Storage.
3. On the Logical view tab, select a logical drive to view its information.
4. To delete a logical drive, select the
logical drive, and then click the ![]() icon.
icon.
5. To create a logical drive, click Create a logical drive, specify drive parameters, and then click Save.
Figure 22 Logical drive information
Parameters
· Name: Name of the logical drive, a string of 0 to 15 characters. As a best practice, use letters and digits, and do not use special characters, such as exclamation points (!), at signs (@), and pound signs (#). For a PMC storage controller, this field is required.
· Spans/Parity groups: Number of spans or parity groups for mixed-mode RAID (RAID 00, RAID 10, RAID 50, or RAID 60).
· Initialization type: Select an initialization type. Options include:
¡ No—Does not initialize the logical drive.
¡ Fast—Initializes the first and last 8 MB of the logical drive for data write upon drive creation, and then initializes the remaining space in background.
¡ Full—Initializes all space in the logical drive.
· Capacity: Enter the drive capacity. The minimum capacity of a logical drive is 100 MB. If you do not specify a capacity, the maximum capacity is used.
· Dedicated hot spare: Dedicated hot spare disks for redundancy-capable logical drives.
· Status: Status of the logical drive. Options include:
¡ Optimal—The logical drive is operating correctly.
¡ Degraded—Some RAID member drives have failed and require prompt replacement.
¡ Rebuilding—The RAID array is being rebuilt to reconstruct data and recover from the degraded state.
¡ Offline—The logical drive is corrupt and inaccessible.
¡ Zeroing—The logical drive is being formatted. All data will be deleted upon this action.
¡ Scrubbing—The member drives are being scanned to maintain data continuity in the logical drive. This field is available for logical drives with parity bits, such as RAID 5 and RAID 6 logical drives.
¡ Suboptimal—One member drive in the RAID 6 or RAID 60 logical drive has failed. If more than one member drive has failed, the logical drive is placed in Degraded state. This field is available for RAID 6 and RAID 60 logical drives.
¡ Morphing—Data is being migrated between drives or the RAID array is changing to a new RAID level.
¡ Copying—Data is being copied from the hot spare disk back to the replacement drive of a failed drive. When this operation is complete, the hot spare returns to the hot standby state.
· Level: RAID level.
· BootEnable: Indicates whether the logical drive is a boot drive. Support for this field depends on the storage controller model. Options include:
¡ True—The logical drive is a boot drive.
¡ False—The logical drive is not a boot drive.
· Stripe size: Stripe size of each physical drive. Support for this field depends on the storage controller model.
· Read policy: Read policy for the logical drive. Support for this field depends on the storage controller model. Options are:
¡ No read ahead—Disables read ahead capability.
¡ Read ahead—Enables read ahead capability. When this capability is enabled, the controller reads sequentially ahead of requested data and stores the additional data in cache memory.
· Write policy: Write policy for the logical drive. Support for this field depends on the storage controller model. Options are:
¡ Write through—Enables the controller to send a data transfer completion signal to the host when the drive subsystem has received all data in a transaction.
¡ Write back—Enables the controller to send a data transfer completion signal to the host when the controller cache receives all data in a transaction. If the storage controller is not installed with a supercapacitor or if the supercapacitor is faulty, the Write through policy is used.
¡ Always write back—Enables the controller to send a data transfer completion signal to the host when the controller cache receives all data in a transaction.
· I/O policy: I/O policy for the logical drive. Support for this field depends on the storage controller model. Options include:
¡ Direct—Enables the cache module to process all read and write operations of the storage controller.
¡ Cached—Disables the cache module from processing any read or write operations on the storage controller.
· Drive cache: Indicates whether drive cache is enabled for the logical drive. Support for this field depends on the storage controller model. Options include:
¡ Unchanged—The default drive cache policy is used.
¡ Enable—Drive cache is enabled.
¡ Disable—Drive cache is disabled.
· Access policy: Access policy for the logical drive. Support for this field depends on the storage controller model. Options include:
¡ Read/Write.
¡ Read only.
¡ Blocked.
· Acceleration method: Status of read/write cache. Support for this field depends on the storage controller model. Options include:
¡ Controller Cache—Enables read/write cache.
¡ None—Disables read/write cache.
¡ IO Bypass—Enables the storage controller to use I/O bypass paths to enhance read/write performance. This feature is available only on SSDs.
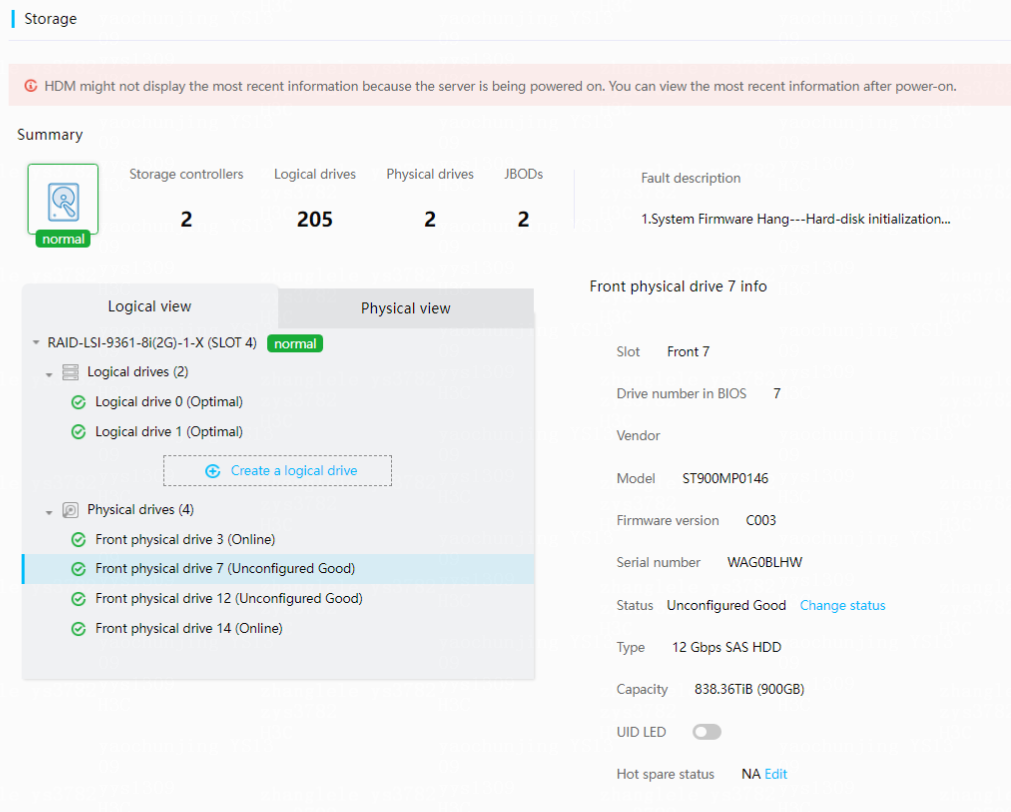
Manage physical drives
Perform this task to view information about physical drives, change drive status, create hot spare drives, and turn on the drive UID LED.
Restrictions and guidelines
If the storage controllers or drive backplanes are not installed as expected, the physical drive numbers might be incorrect.
If the drive status is Failed, the drive information (including the drive size, speed, and interface type) might be inaccurate and is provided only for reference.
You cannot change the state of physical drives in Unconfigured Good (Foreign), Unconfigured Bad (Foreign), or Online state.
When you create hot spare drives, follow these restrictions and guidelines:
· Only spare physical drives can be used as hot spare drives, and member drives of logical drive cannot be configured to provide the hot spare service.
· Make sure the physical drive to be used is an SATA or SAS drive and its capacity is not smaller than the minimum capacity of a member drive. The physical drive must have the same type (SATA/SAS) as the member drives of the logical drive.
· You can create hot spares for logical drives of any RAID level, except for RAID 0.
· If an LSI storage controller is used, make sure the physical drive to use is in Unconfigured Good state. If a PMC storage controller is used, make sure the physical drive to use is in Ready or Hot Spare state.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Storage.
3. To view information about a physical drive that has been used for creating logical drive:
a. On the Logical view tab, select a storage controller and a logical drive.
b. Select the physical drive.
c. If an LSI storage controller is installed, you can click Change status to change the physical drive state.
d. To set the hot spare state of a physical drive, click Edit.
- Physical drives managed by an LSI storage controller support global hot spare and dedicated hot spare. With an LSI controller used, you can select multiple logical drives when creating a dedicated hot spare.
- Physical drives managed by a PMC storage controller only support dedicated hot spare. With a PMC storage controller used, you can select only one logical drive and must repeat the creation task to specify multiple logical drives for a dedicated hot spare.
e. (Optional.) To locate the drive, enable the drive UID LED. This feature is available only for some physical drives.
Figure 23 View physical drive information (logical view)
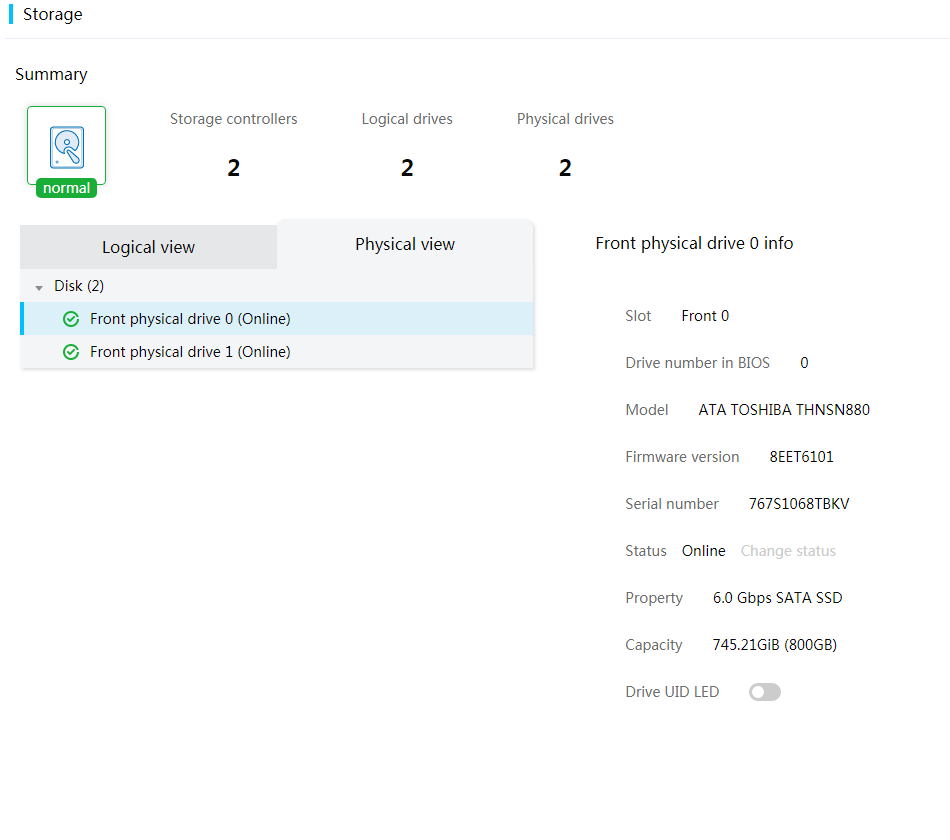
4. To view information about physical drives that are not used for creating logical drive:
a. Click the Physical view tab.
b. (Optional.) To change the physical drive state, click Change status. This feature is available only for some physical drives.
c. (Optional.) To locate the drive, enable the drive UID LED. This feature is available only for some physical drives.
Figure 24 View physical drive information (physical view)
Parameters
HDD and SSD drives
· Slot: Slot number of the physical drive.
· Drive number in BIOS: Drive number displayed in the BIOS.
· Vendor: Vendor of the physical drive.
· Model: Model of the physical drive.
· Firmware version: Firmware version of the physical drive.
· Serial number: Serial number of the physical drive.
· Status: Status of the physical drive. Options include:
If an LSI storage controller is installed, you can click Change status to change the physical drive state.
¡ Ready/Unconfigured Good—The physical drive has been initialized or has not been configured, and it is available for RAID configuration and hot spare setting. The status name depends on the storage controller model.
¡ Unconfigured Bad—The physical drive is in abnormal state. To use the physical drive, you must change the physical drive state to Unconfigured Good. If an error has occurred on the physical drive, you will fail to change the physical drive state. In this case, you need to replace the faulty drive.
¡ Unconfigured Good (Foreign)—The physical drive has residual RAID information. After you clear residual RAID information, the physical drive state changes to Unconfigured Good.
¡ Unconfigured Bad (Foreign)—The physical drive has residual RAID information. After you clear residual RAID information, the physical drive state changes to Unconfigured Bad.
¡ Optimal/Online—The physical drive is already used to create a RAID. The status name depends on the storage controller model.
¡ Offline—The physical drive is disabled.
¡ Rebuilding—The physical drive is being used in RAID rebuilding.
¡ Hot spare—The physical drive is already used as a hot spare.
¡ JBOD—The physical drive is a passthrough drive, which can be used directly in the OS without RAID building.
¡ Failed—The physical drive failed.
¡ Predict_Fail/PFA—The physical drive is analyzing possible failures. The status name depends on the storage controller model.
¡ Raw—A new physical drive or a physical drive in Unconfigured good state is uninitialized.
¡ Normal—The physical drive is used as a common hard disk for storage. It is not used for other purposes.
¡ Copyback—Data is being copied from the hot spare disk back to the replacement drive of a failed drive. When this operation is complete, the hot spare returns to the hot standby state. This field is available only for a physical drive attached to an LSI storage controller.
· Rebuilding progress: Rebuilding progress of the physical drive in RAID rebuilding. This field is displayed for a physical drive only when the drive is in Rebuilding state.
· Type: Interface speed, interface type, and drive type of the physical drive. This field displays the negotiated speed, instead of the interface speed, for some storage controllers.
· Capacity: Capacity of the physical drive.
· Remaining life: Remaining drive life in percent. This field is available only for the following drives when the drives are attached to an LSI storage controller that supports out-of-band RAID configuration:
¡ Intel SSD S4610 drives.
¡ Intel SSD S4600 drives.
¡ Intel SSD S4510 drives.
¡ Intel SSD S4500 drives.
¡ Intel SSD S3520 drives.
¡ Micron SSD 5200 drives.
¡ Samsung SSD drives.
· UID LED: Drive UID LED status. You can click this field to manage the drive UID LED. This field is available only when the drive is directly connected to the drive backplane.
· Hot spare status: Hot spare status of a physical drive. When a member of a logical drive fails, a hot spare can replace the faulty member to store data. The supported hot spare status varies by the storage controller type.
¡ Global hot spare—Acts as the spare for all qualified logical drives managed by an LSI storage controller. After the faulty drive recovers, data will be transmitted back to the drive from the hot spare, and the hot spare continues to operate in global hot spare state.
¡ Dedicated hot spare—Acts as the spare for the specified logical drives. After the faulty drive recovers, data will be transmitted back to the drive from the hot spare, and the hot spare continues to operate in dedicated spare state.
NVMe drives
· Product name: Product name of the NVMe drive.
· Vendor: Manufacturer of the NVMe drive.
· Status: NVMe drive status:
¡ Normal—The NVMe drive is operating correctly.
¡ Abnormal—A bus uncorrectable error, bus fatal error, or PCIe err error has occurred on the NVMe drive.
¡ Spare space below threshold—The available space in the NVMe drive has fallen below the threshold.
¡ Temperature anomaly—The NVMe drive temperature is above the upper threshold or below the lower threshold.
¡ Subsystem degraded—The NVMe subsystem reliability has been degraded because of storage media or internal errors.
¡ Read-only mode—The NVMe drive has been placed in read only mode.
¡ Cache failed—The volatile memory backup device has failed.
· Firmware version: Firmware version of the NVMe drive. This field displays N/A if HDM does not support displaying the firmware version of the NVMe drive.
· Serial number: Serial number of the NVMe drive.
· Model: Model of the NVMe drive.
· Interface type: Interface type of the NVMe drive.
· Capacity: Capacity of the NVMe drive.
· Physical location—NVMe drive slot number.
· Slot number—NVMe drive slot number or PCIe slot number assigned to the drive by the system.
· Max speed—Maximum speed supported by the NVMe drive.
· Percentage drive life used: Estimate of the percentage of NVMe subsystem life used. The value can be greater than 100.
· UID LED: Drive UID LED status. You can click this field to manage the drive UID LED. This field is available only when the drive is directly connected to the drive backplane.
Power management
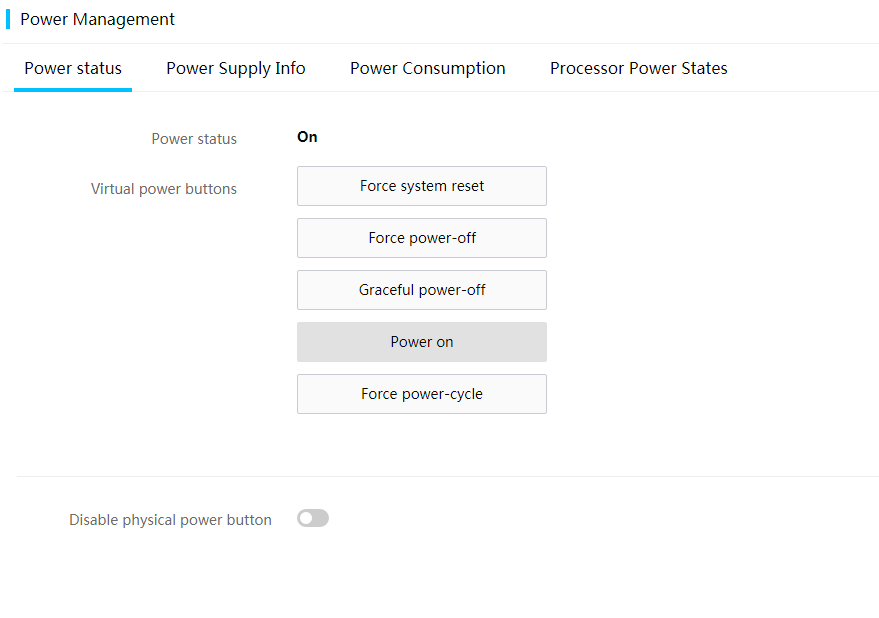
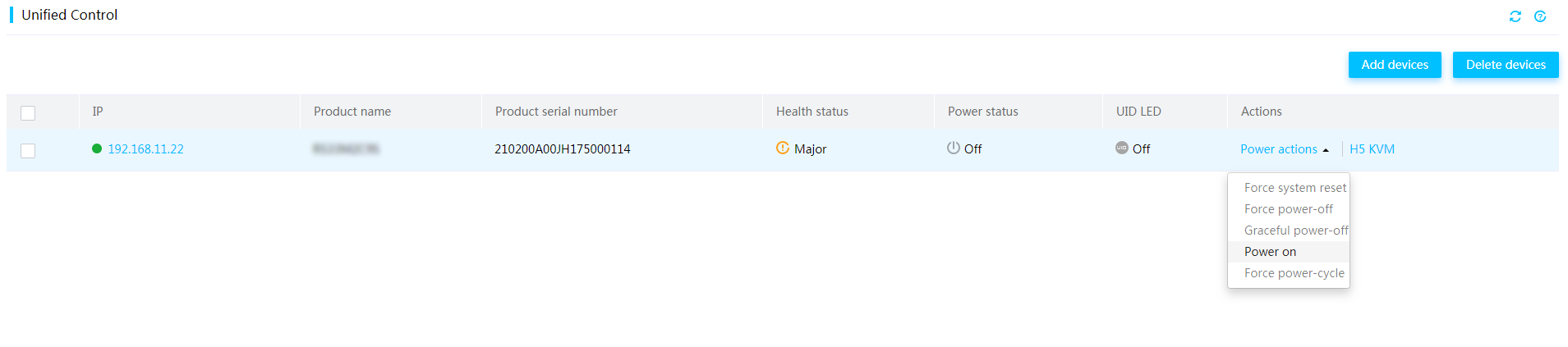
Power on or power off the server
|
CAUTION: The force power-off, force system reset, and force power-cycle actions might cause corruption or loss of data. When you perform these actions, make sure you fully understand their impact on the services. |
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. Click the Power status tab to view the current power status of the server.
4. To change the power status, click the desired action.
5. Select whether to enable or disable the physical power button as needed. This button is available only for G5 servers (blade servers excluded).
Figure 25 Powering on or powering off the server
Parameters
· Force system reset: Warm reboots the server without power cycling the server.
· Force power-off: Shuts down the server immediately by force. This action is equivalent to pressing the power button on the server for five seconds.
· Graceful power-off: Shuts down the operating system first, and then removes power from the server.
· Power on: Starts up the server.
· Force power-cycle: Powers off and then powers on the server.
· Disable physical power button: Controls the physical power button. With the power button disabled, users cannot use the physical power button to manage the power status of the server.
View power supply information
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
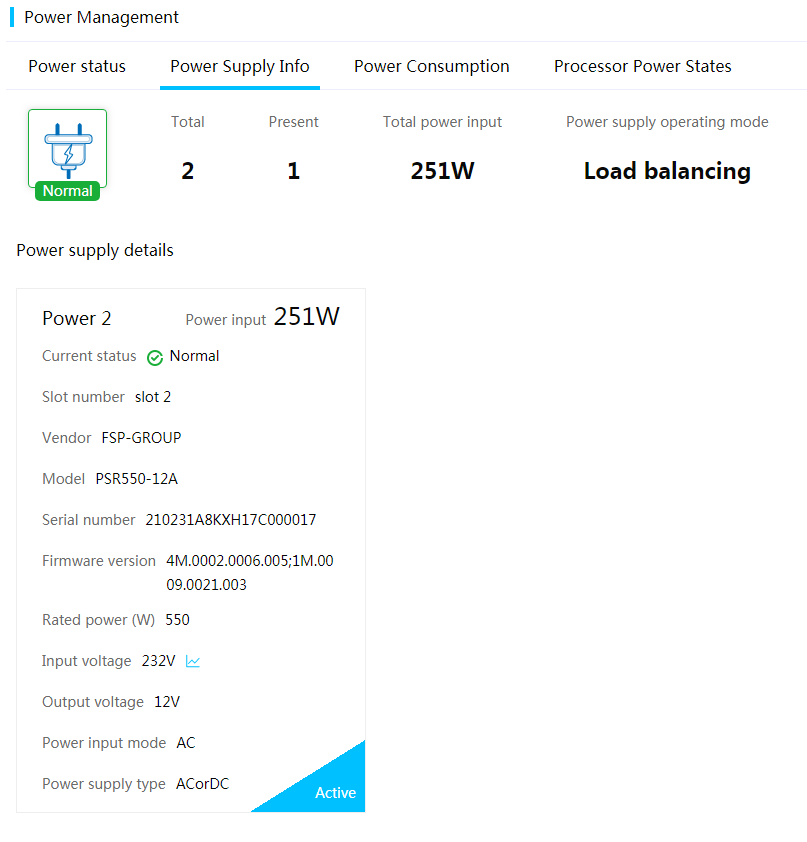
3. Click the Power Supply Info tab.
4. View power supply summary and detailed information.
Figure 26 View power supply information
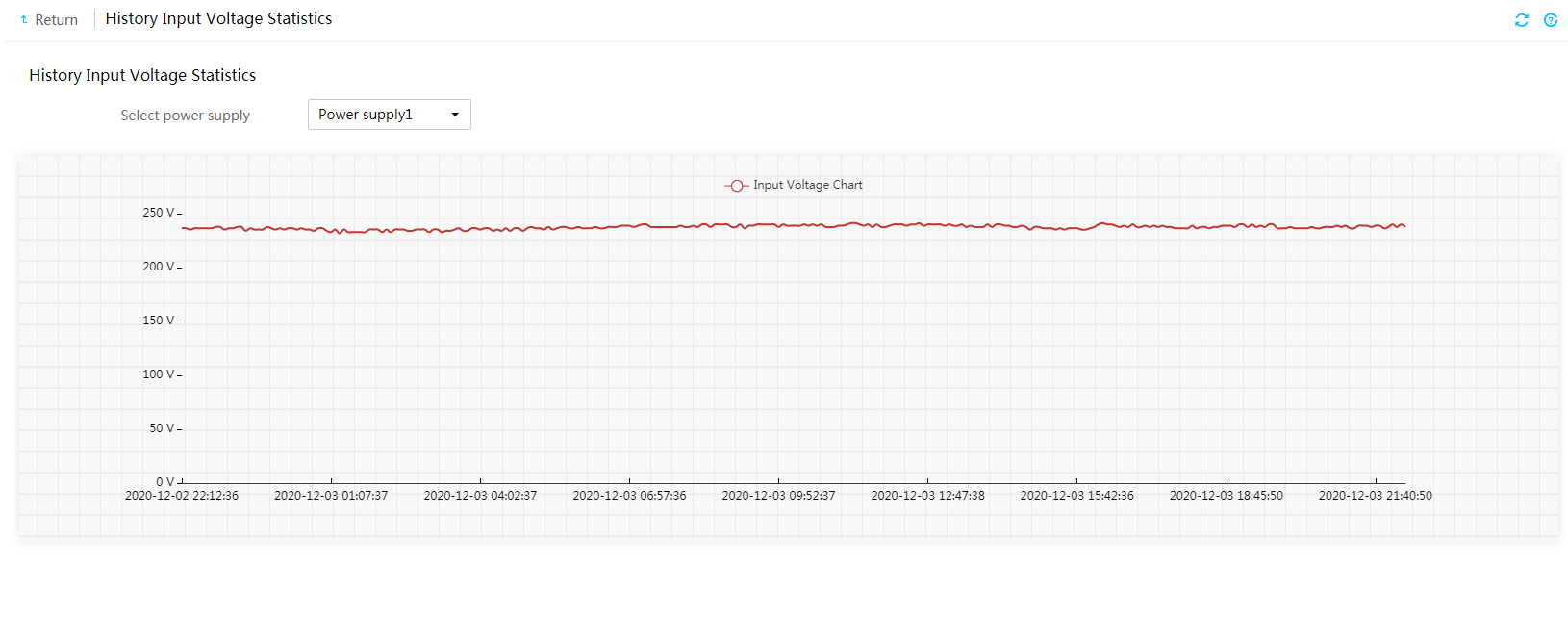
5. To view the input voltage history, click the
voltage icon ![]() .
.
Figure 27 View the input voltage history
Parameters
· Power mode: Role of the power supply. Options include Active and Standby. The active power supplies provide power normally and the standby power supplies provide low power output.
· Power input: Input power of the power supply
· Current status: Status of the power supply. If a power supply is in abnormal state, review the event logs to locate the errors.
· Slot number: Number of the slot in which the power supply resides.
· Vendor: Manufacturer of the power supply.
· Model: Model of the power supply.
· Serial number: Unique code assigned by the manufacturer.
· Firmware version: Firmware version of the power supply.
· Rated power: Rated power of the power supply.
· Input voltage: Input voltage of the power supply.
· Output voltage: Output voltage of the power supply.
· Power input mode: Power input mode. Options include:
¡ No input: The power supply is not connected to the power source.
¡ AC: The power supply is connected to an AC power source.
¡ HVDC: The power supply is connected to a high-voltage DC power source. The voltage is in the range of 192 V to 400 V.
¡ LVDC: The power supply is connected to a low-voltage DC power source. The voltage is in the range of 12 V to 72 V.
· Supported power input modes: Power input modes supported by the power supply. Options include:
¡ AC: The power supply supports only the AC input mode.
¡ AC or DC: The power supply supports both the AC and DC input modes.
¡ DC: The power supply supports only the DC input mode.
¡ Unknown: HDM has failed to obtain the power supply information.
· Fault description: Event log information about power supply errors.
Set the power supply operating mode
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
To avoid configuration failure, set the power supply operating mode after the server starts up.
If you fail to set the operating mode for multiple power supplies in bulk, HDM generates a log message only for the power supply with the lowest slot number.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. In the work pane, click the Power Supply Info tab.
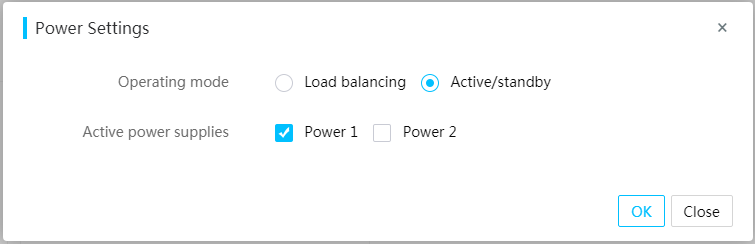
4. Click Power Settings.
5. Select the power supply operating mode. Options include:
¡ Load balancing—Allows all power supplies to provide power in a balanced way.
¡ Active/standby—Allows active power supplies to mainly provide power. In this mode, you must specify a minimum of one active power supply and a minimum of one standby power supply. If an active power supply fails, a standby power supply becomes active to supply power. If an actual power consumption of the active power supply exceeds 62% of its maximum rated power consumption, a standby power supply becomes active to supply power. The active/standby switchover will not be performed after the power consumption of the original active power supply drops.
6. Click OK.
Figure 28 Setting the power supply operating mode
Parameters
Fault description: Event log information about power supply errors.
Configure automatic power-on
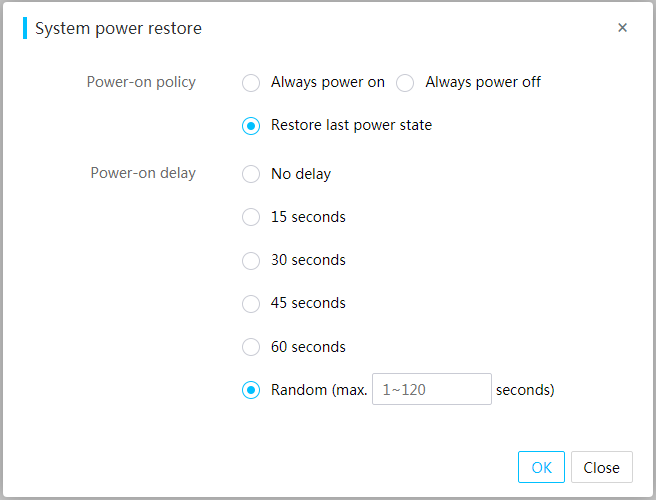
Perform this task to configure the power-on policy of the server when the server is connected to the power source.
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. In the work pane, click the Power Supply Info tab.
4. Click System Power Restore.
5. Select the power-on policy and set the power-on delay:
¡ Power-on policy—Select whether to start the server when the server is connected to the power source. Options are Always power on, Always power off, and Restore last power state.
- To have the server always automatically start up when it is connected to the power source, select Always power on.
- To have the server stay off when it is connected to the power source, select Always power off.
- To have the server return to the power state on the previous power-off, select Restore last power state.
¡ Power-on delay—Set the power-on delay time. If you select Random, you can customize the delay time range.
6. Click OK.
Figure 29 Configuring automatic power-on
Parameters
Fault description: Event log information about power supply errors.
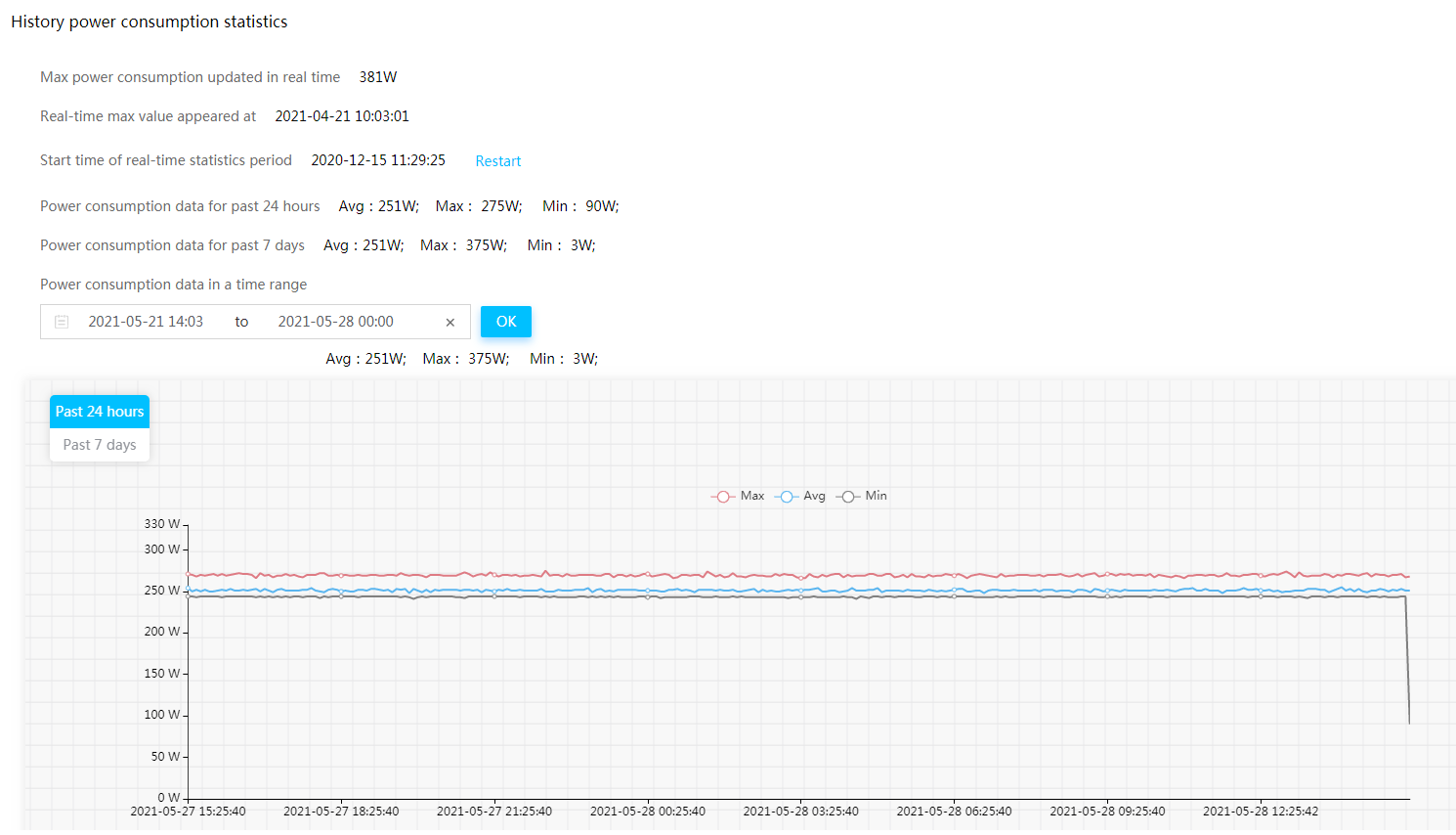
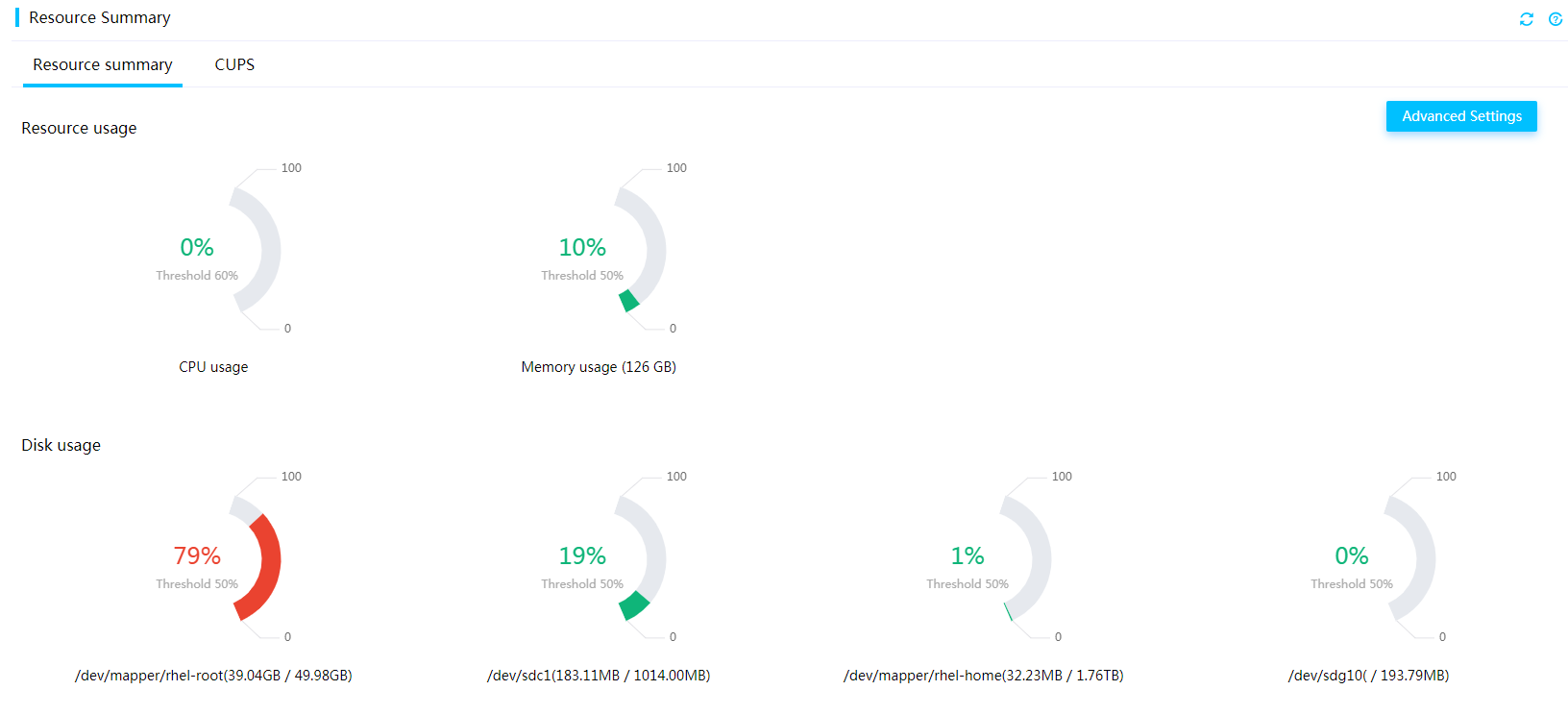
View power consumption information
Perform this task to view power consumption summary, power information, and power consumption history. You can view the 5-minute server power consumption statistics for the past 24 hours or seven days, including the maximum, average, and minimum power consumption.
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
The R4950 G3, R4330 G5, R4950 G5, and R5500 G5 servers support displaying only the average sensor readings.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. In the work pane, click the Power Consumption tab.
4. View the power consumption information, power alarming, system board power capping, GPU power capping, and history power information.
¡ To clear the history readings and start a new statistics collection period, click Restart.
¡ To view the power consumption statistics within a time range, select a time range and then click OK.
¡ To
view only the maximum, average, or minimum power consumption, click the ![]() Max,
Max, ![]() Avg, or
Avg, or ![]() Min icon, respectively.
Min icon, respectively.
Figure 30 Viewing power consumption information
Figure 31 Viewing the power consumption history
Configure power alarming
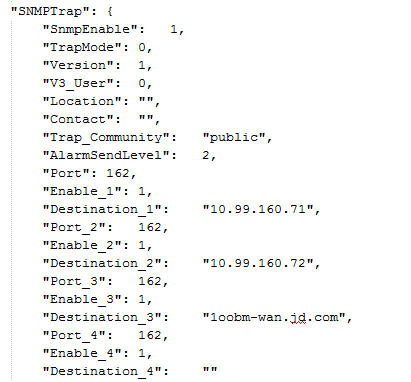
Power alarming allows the system to generate an alarm log when the total power consumption of the server exceeds the alarm threshold.
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. In the work pane, click the Power Consumption tab.
4. Click the ![]() icon
in the Power alarming section.
icon
in the Power alarming section.
5. In the dialog box that opens, enable power alarming and then specify the alarm threshold.
6. Click OK.
Figure 32 Configuring power alarming
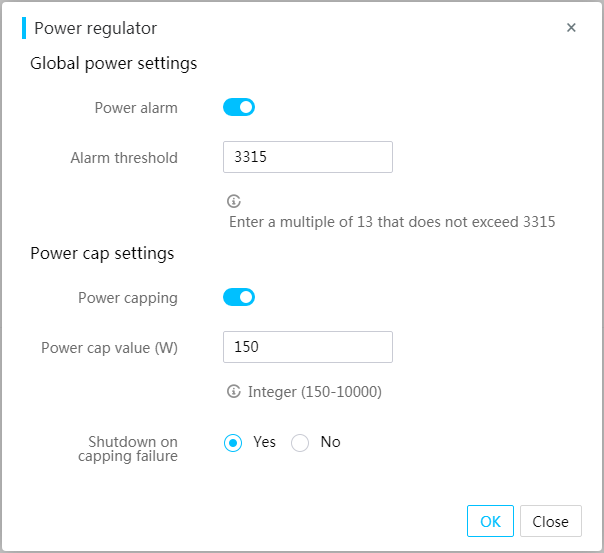
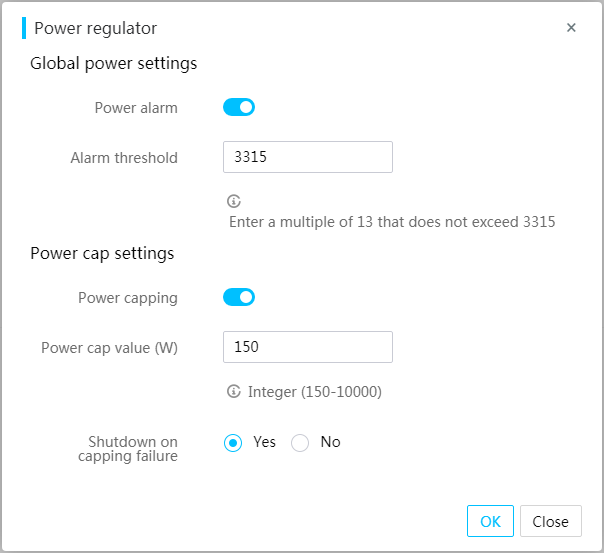
Configure power capping
Power capping limits the power consumption of the server to a power cap value that is lower or equal to the maximum rated power of the server.
When the power cap value is exceeded, the server attempts to decrease power consumption by automatically decreasing the operating frequency of system components such as processors. When the GPU power cap value is exceeded, the server attempts to decrease power consumption by automatically decreasing the operating frequency of GPUs. Power capping fails if the power consumption cannot drop below the power cap value in 30 seconds.
You can configure the server to shut down or continue to run on a power capping failure.
Restrictions and guidelines
|
CAUTION: Server shutdown upon a power capping failure causes service interruption. To use this function, make sure you understand the impact. |
The blade servers and AE modules do not support system board power capping configuration.
Only the R5500 G5 server supports GPU power capping configuration.
Power capping is at the expense of system performance. Select the power cap value carefully to avoid undesirable decrease in performance.
To avoid GPU power capping configuration invalidity, make sure the GPU driver is installed in the OS before configuring GPU power capping settings.
HDM cannot obtain the server power consumption statistics during restart.
Restoring the HDM settings clears the power consumption statistics.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. In the work pane, click the Power Consumption tab.
4. Click the ![]() icon
in the System board power capping or GPU power capping section.
icon
in the System board power capping or GPU power capping section.
5. In the dialog box that opens, enable power capping, set the power cap value, and then set the action to take upon a power capping failure.
6. Click OK.
Figure 33 Configuring power capping
Configure processor power states
Perform this task to configure the processor power states and the power supply operating mode.
You can adjust the power consumption of processors by changing the processor power states.
Restrictions and guidelines
This feature is not available for the R4950 G3, E3200 G3, B5700 G3, B5800 G3, B7800 G3, R4330 G5, B5700 G5, R4930 G5, R4950 G5, R5500 G5 AMD, or AE100.
Prerequisites
For the power states to take effect, configure the following tasks on the Socket Configuration > Advanced Power Management Configuration screen from the BIOS:
1. Set EIST (P-States) and Software Controlled T-States to Enabled.
2. Select the T-state throttle level.
3. Set Hardware P-States to Disable.
4. Set Power Performance Tuning to BIOS Controls EPB.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Power Management.
3. Click the Processor Power States tab.
4. Click Advanced Settings.
5. Adjust the preferred P-state or T-state value and then click OK.
The available state values vary by processor model.
6. Select the power supply performance mode, and then click Save. The performance mode options include:
¡ Performance—Indicates the performance first mode.
¡ Balanced—Indicates the balanced performance and power consumption mode.
¡ Power—Automatically adapts the speed and energy consumption of the processors to processor usage. This mode reduces the total consumption and has little or no impact on the performance.
7. Restart the server for the configuration to take effect.
Figure 34 Configuring power saving
Parameters
· P-state: Defines the operating frequency of processors. A smaller P-state value represents a higher operating frequency, which translates to higher performance and higher power consumption.
· T-state: Defines the duty cycle of processors. A smaller T-state value represents a higher duty cycle, which translates to higher performance and higher power consumption.
Thermal management
View status and readings of temperature sensors
HDM presents temperature data in both heatmap and table formats to help you monitor the cooling performance of the server.
· The temperature heatmaps use colors between green and red to show the temperature distribution inside the server chassis in 2D and 3D views and use circles to represent sensors. Green indicates 0°C (32°F). As the temperature gets higher, the color gets warmer until it changes to red. With the temperature heatmaps, you can quickly identify the component that is in a poor cooling condition.
· The temperature sensor table displays the temperature reading, status, and coordinates of each sensor.
Restrictions and guidelines
The temperature heatmaps do not display sensors whose reading is negative.
|
|
NOTE: In HDM-2.96 and later versions, you can scan the QR code on the screen to view the functional diagram or give feedback. |
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Thermal Management.
3. View the temperature heatmap and sensor list.
Figure 35 Viewing status and readings of temperature sensors
Parameters
· Status: Temperature status of a component:
¡ Normal—The temperature is normal, between the lower and upper minor thresholds (exclusive). No action is required.
¡ Minor—The temperature is between the lower major threshold (exclusive) and lower minor threshold (inclusive) or between the upper minor threshold (inclusive) and upper major threshold exclusive). Administrative attention is required.
¡ Major—The temperature is between the lower critical threshold (exclusive) and lower major threshold (inclusive) or between the upper major threshold (inclusive) and upper critical threshold (exclusive). Immediate action is required.
¡ Critical—The temperature is equal to or below the lower critical threshold, or it is equal to or above the upper critical threshold. Immediate action is required.
¡ N/A—The monitored component is not installed or the temperature sensor cannot be read.
· Reading: Current temperature. If HDM fails to read the sensor, this field displays N/A.
· Thresholds: Temperature thresholds:
¡ Critical—Lower and upper critical thresholds. When the temperature reaches either threshold, the server might automatically shut down to avoid damage to its components.
¡ Major—Lower and upper major thresholds. If the temperature reaches either threshold, server performance will significantly degrade.
¡ Minor—Lower and upper minor thresholds. If the temperature reaches either threshold, server performance will slightly degrade.
Manage fans
Perform this task to view fan information and fan errors and configure the fan speed mode.
You can adjust the fan speed mode to optimize the cooling, noise control, and energy efficiency performance.
Restrictions and guidelines
This feature is not available for blade servers or AE modules.
Set the preferred fan speed mode
1. On the top navigation bar, click System.
2. In the left navigation pane, select Thermal Management.
3. View fan information.
4. Click Fans.
5. Select a fan speed mode.
6. Click OK.
Figure 36 Viewing fan information
Figure 37 Managing fans
Parameters
· Status: Operation status of the fan.
· Model: Fan model.
· Rotation speed (RPM): Current actual rotational speed.
· Rotation speed (%): Current RPM as a percentage of the rated RPM.
· Fault description: Alarms generated for fan errors.
· Silent: Enables the fans to run at the lowest speed required by heat dissipation of the server. This mode is suitable for scenarios with high noise requirements.
· Balanced: Enables the fans to run at a higher speed to provide balanced noise control and cooling performance.
· Powerful: Enables the fans to run at the highest possible speed. This mode is suitable for scenarios where the server requires high cooling performance. For example, the server is busy and key components, such as processors, are heavily loaded, or the ambient temperature changes frequently.
· Custom: Specifies a customized fan speed level. A higher level represents a higher speed and larger noise.
Resource summary
Set resource usage alarm thresholds
Perform this task to set the alarm thresholds for processor, memory, and disk usage.
Restrictions and guidelines
To use this feature, you must install and run FIST SMS in the operating system of the server. For more information, see H3C Servers FIST SMS User Guide.
You cannot set the alarm threshold for the bandwidth usage from HDM. To set this alarm threshold, use IPMI commands. For more information, see H3C HDM IPMI Basics Command Reference.
The system generates a log entry when an alarm occurs or is cleared. You can view the alarms in the event logs.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Resource Summary.
3. Click the Resource summary tab to view the current processor usage, memory usage, disk usage, disk partition directory, used disk space, and total partition size.
Figure 38 Viewing resource summary
4. Click Advanced Settings.
5. Set the alarm thresholds for processor usage, memory usage, and disk usage and then click OK.
Figure 39 Setting resource usage alarm thresholds
Parameters
Drive usage threshold (%): Proportion of used disk space to the total size of the partition, disk partition directory, used space, and total partition space.
View CUPS information
The Compute Usage Per Second (CUPS) feature provides real-time monitoring of processor (CPU), memory, and I/O usage in the system. It uses the proportions of dynamic load factors for CPU, memory, and I/O usage to indicate the type of main services running on the system. The CUPS load factors are uncorrelated with resource usage calculated in the OS.
A higher CPU, memory, or I/O CUPS dynamic load factor indicates that main services running on the system are compute-intensive, memory-intensive, or I/O-intensive.
Restrictions and guidelines
This feature is not available for the R4950 G3, R4330 G5, R4930 G5, R4950 G5, or R5500 G5 AMD server.
The line chart displays the sum of the CPU, memory, and I/O CUPS load factors. To view the value of each load factor, hover over the line in the chart. The sum is 0% if all the three load factors are 0%.
The CPU, memory, and I/O CUPS dynamic load factors are all 0% when the server is powered off or no service runs in the operating system.
CUPS monitoring is an out-of-band function and does not consume processor resources.
Restoring HDM settings clears CUPS statistics.
The CPU and MEM CUPS dynamic load factors are uncorrelated with the CPU and MEM usage calculated in the OS.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select Resource Summary.
3. Click the CUPS tab to view CUPS information.
Figure 40 Viewing CUPS information
Parameters
· CPU CUPS dynamic load factor: Cumulative usage of CPU cores. A higher CPU CUPS dynamic load factor indicates that main services running on the system are compute-intensive.
· Memory CUPS dynamic load factor: Cumulative transfer rate of the memory bus, which does not relate to used memory. A high memory CUPS dynamic load factor indicates a high access frequency to the memory bus. The memory usage in the OS is the total memory capacity divided by the used memory capacity. For example, if 2GB of 8GB memory is used, the memory usage is 25%.
· I/O CUPS dynamic load factor: I/O bandwidth usage of the PCIe bus. A higher I/O CUPS dynamic load factor indicates that main services running on the system are I/O-intensive.
System settings
Configure boot options
You can configure the boot mode and boot device for the server to use at the next reboot in the Boot Options or System Boot Order section.
The system boot order defines the priorities of devices that the server attempts to boot from.
Restrictions and guidelines
· If you configure boot options at the BIOS startup phase, the configuration might fail to take effect.
· If the permanent boot options conflict with the system boot order settings, the permanent boot options take effect.
· If the one-time boot options conflict with the system boot order settings, the one-time boot options take effect at the next reboot.
· Only G5 servers support configuring boot options.
· You can set the system boot order only in HDM-2.11 and later.
Prerequisites
Verify that the hard disk drive supports the legacy mode if you are configuring the server to boot from a hard disk drive in legacy mode.
Configure boot options for the next reboot
1. On the top navigation bar, click System.
2. In the left navigation pane, select System Settings.
3. Click the Boot Options tab.
4. In the System Boot Options section, select a validity period for the next boot mode and option.
¡ To have the settings take effect only for the next reboot, select One time.
¡ To have the settings take effect for all subsequent reboots, select Permanent.
The Permanent option is not available for the B5700 G3, B5800 G3, B7800 G3, B5700 G5, or AE100.
5. Select a next boot mode.
¡ To boot to a UEFI compatible operating system, select UEFI.
¡ To boot to a traditional operating system in Legacy BIOS compatibility mode, select Legacy BIOS.
The AE100 does not support the legacy mode.
¡ To use the BIOS settings at the next reboot, select No override.
6. Select the boot device for the next reboot from the Boot option list. The BIOS option is not available if the validity period is Permanent.
To use the BIOS settings at the next reboot, select No override.
7. Click Save.
Figure 41 Configuring boot options for the next reboot
Set the system boot order
1. On the top navigation bar, click System.
2. In the left navigation pane, select System Settings.
3. Click the Boot Options tab.
4. In the System Boot Order section, select a boot mode.
¡ To boot to a UEFI compatible operating system, select UEFI.
¡ To boot to a traditional operating system in Legacy BIOS compatibility mode, select Legacy BIOS.
5. To change the boot order of a boot option, select the option, and then click Up or Down as needed.
The Other device option includes the following boot devices whose priorities are defined in the BIOS:
¡ Embedded UEFI shell. This option is displayed only when EFI Shell Boot is set to Enabled in the BIOS.
¡ Other boot devices whose type has not been identified.
6. To restore the default boot order, click Reset.
7. Click Save.
Figure 42 Setting the system boot order
Parameters
· Boot mode: Selects the boot mode for the next startup.
· Boot option: Selects the boot device for the next startup.
· Current boot mode: Displays the boot mode for the most recent startup.
· Current first boot option: Displays the first boot device for the most recent startup.
Switch the partitioning mode
Perform this task to set the partitioning mode of the server.
In single-system partitioning mode, the server operates as one system. Only management module 1 is running. You can manage the server through HDM, the BIOS, and OS of management module 1 .
In dual-system partitioning mode, the server operates as two separate systems. Both management modules 1 and 2 are running. You can manage each system through HDM, the BIOS, and OS of the corresponding management module. This mode provides higher server efficiency.
For more information about management modules, see the user guide of the server.
General restrictions and guidelines
This feature is available only for the R8900 G3 server.
This feature is available only in HDM-2.08.00, BIOS-2.00.47, CPLD-V006, PDBCPLD-V005, and later.
Make sure HDM, the BIOS, CPLD, and PDBCPLD versions of the server support this feature.
In dual-system mode, you can start or reboot the second system only after you start or reboot the first one successfully.
As a best practice, configure this feature under the guidance of the technical support.
Switch single-system mode to dual-system mode
Restrictions and guidelines
Before a partitioning mode switch, make sure the following requirements are met:
· The server is powered off, and HDM is not being updated.
· HDM, the BIOS, and all CPLD firmware of support partitioning mode configuration and are compatible with each other.
Prerequisites
If not all firmware of the server support partitioning mode configuration, perform the following steps to update the firmware:
1. Update HDM, the BIOS, and all CPLD firmware to versions that support partitioning mode configuration.
2. Power off the server, and switch the positions of management modules 1 and 2.
3. Power on the server, and update HDM, the BIOS, and all CPLD firmware again to versions that support partitioning mode configuration.
Procedure
1. On the top navigation bar, click System.
2. In the left navigation pane, select System Settings.
3. Click the Hard Partitioning tab.
4. Select the dual-system mode.
5. Enter the username and password of a user account.
Make sure the user account has the administrator or operator role or the remote control privilege.
6. Click Save.
To have the partitioning mode configuration take effect, restart the server with its power reconnected.
Figure 43 Switching single-system mode to dual-system mode
Sign in to HDM after the partitioning mode switch
After the switch from single-system mode to dual-system mode, both management modules 1 and 2 are running. The switch restores HDM and the BIOS of both systems on the server to the default settings.
To sign in to HDM of a system in the server after the partitioning mode switch:
1. Obtain the management IP address of HDM.
¡ If the HDM dedicated network port is connected, use the default management IP address of the HDM dedicated network port, 192.168.1.2/24.
¡ If the HDM shared network port is connected, the method for obtaining the management IP address of the HDM shared network port varies by system.
- For the system of the lower partition, the IP address is automatically assigned by the DHCP server. You can obtain the IP address from the POST screen of the BIOS.
- For the system of the upper partition, if the IP address was automatically assigned before the switch, the IP address remains the same after the switch. If the IP address was a static IP address before the switch, a new IP address is automatically assigned by the DHCP server. You can obtain the new IP address from the POST screen of the BIOS.
2. On the HDM sign-in page of each system, enter the default username (admin) and password (Password@_). The password is case-sensitive.
Switch dual-system mode to single-system mode
Restrictions and guidelines
Before a partitioning mode switch, make sure the following requirements are met:
· All systems are powered off, and HDM is not being updated.
· All systems have the same PDBCPLD firmware version and NDCPLD firmware version.
· HDM and the BIOS of all systems support partitioning mode configuration.
· You can perform a partitioning mode switch only from HDM of management module 1.
Procedure
1. Log in to HDM of management module 1.
2. On the top navigation bar, click System.
3. In the left navigation pane, select System Settings.
4. Click the Hard Partitioning tab.
5. Select the single-system mode.
6. Enter the username and password of a user account.
Make sure the user account has the administrator or operator role or the remote control privilege.
7. Click Save.
To have the partitioning mode configuration take effect, restart the server with its power reconnected.
Figure 44 Switching dual-system mode to single-system mode
Sign in to HDM after the partitioning mode switch
After the switch from dual-system mode to single-system mode, only management module 1 is running. The switch restores HDM and the BIOS to the default settings.
To sign in to HDM after the partitioning mode switch:
1. Obtain the management IP address of HDM of management module 1.
¡ If the HDM dedicated network port is connected, use the default management IP address of the HDM dedicated network port, 192.168.1.2/24.
¡ If the HDM shared network port is connected, the method for obtaining the management IP address of the HDM shared network port varies by IP address obtaining method before the switch.
- If the IP address was automatically assigned by the DHCP server before the switch, the IP address remains after the switch.
- If the IP address was a static IP address before the switch, a new IP address is automatically assigned by the DHCP server. You can obtain the new IP address from the POST screen of the BIOS.
2. On the HDM sign-in page, enter the default username (admin) and password (Password@_). The password is case-sensitive.
Configuration
Network
|
IMPORTANT: The HDM dedicated network port is not available for the AE100 or blade servers. |
You can log in to HDM from the HDM dedicated network port or the HDM shared network port.
The dedicated network port can process only HDM management traffic. By default, the dedicated network port uses IPv4 address 192.168.1.2/24 and obtains an IPv6 address from the DHCP server.
The shared network port transmits HDM management traffic and server data traffic simultaneously. By default, the shared network port automatically obtains its IP address through DHCP.
General restrictions and guidelines for network configuration
To ensure successful access to HDM, follow these restrictions and guidelines when you configure network settings:
· If the HDM dedicated network port and shared network port are in normal mode, make sure the dedicated port, shared port, and the WLAN use different IP addresses from different subnets. A violation might cause network failure.
· Do not disable the HDM dedicated network port and the shared network port at the same time. HDM Web interface will be inaccessible if both network ports are disabled.
· Any change to network settings can cause HDM user sessions to disconnect and take a few minutes to take effect. After you change network settings, reconnect to the HDM Web interface at prompt.
· If you need to power off the server after changing network settings, first wait for the changes to take effect.
If you cannot log in to HDM at its IPv6 address, disable proxy server in the browser and then try again.
An IP address assigned by the DHCP server or configured through stateless autoconfiguration supports only the 64-bit prefix.
View dedicated network port information
Perform this task to view information about the dedicated network port, including port name, MAC address, IP addresses, and VLAN settings.
Procedure
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. On the Dedicated Port tab, view information about the dedicated network port.
Figure 45 Viewing information about the dedicated network port
Parameters
· Port state: This field is available only when the network port mode is active/standby. Options include:
¡ Active—The port is connected and in active state.
¡ Disconnected—The port is disconnected.
· Port connection: Displays whether a cable is connected to the port. Options include:
¡ Disconnected—The port is disconnected.
¡ Active—The port is connected and is in active state.
Configure the dedicated network port
Restrictions and guidelines
See "General restrictions and guidelines for network configuration."
If the network port mode is active/standby, any IP configuration on the dedicated network port will be synchronized to the shared network ports.
Prerequisites
Verify that the dedicated network port is physically connected to the network.
Verify that the dedicated network port is in Active state if the network port mode is active/standby.
Configure IPv4 settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. On the Dedicated Port tab, click Configure.
3. Select Enable for IPv4 to enable IPv4 network service.
4. Configure IPv4 address settings for the port:
¡ To use the IP address automatically assigned by a DHCP server, select Automatic IP obtaining.
¡ To manually configure static IP address settings, clear Automatic IP obtaining, and then enter an IPv4 address, subnet mask, and default gateway address.
The default IP address of the HDM dedicated network port is 192.168.1.2/24. A gateway address of 0.0.0.0 indicates that no default gateway is specified.
5. Click Save.
Figure 46 Configuring IPv4 settings
Configure IPv6 settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. On the Dedicated Port tab, click Configure.
3. Select Enable for IPv6 to enable IPv6 network service.
4. Configure IPv6 address settings for the port:
¡ To use the IP address automatically assigned by a DHCP server, select Automatic IP obtaining.
¡ To manually configure static IP address settings, clear Automatic IP obtaining, and then enter an IPv6 address, the prefix length (in the range of 1 to 127), and default gateway address fe80::9628:2eff:fe9c:ffda.
5. Click Save.
Figure 47 Configuring IPv6 settings
Configure VLAN settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. On the Dedicated Port tab, click Configure.
3. Select Enable for VLAN to enable VLAN service.
4. Enter a VLAN ID in the range of 2 to 4094.
5. Enter an 802.1p priority in the range of 0 to 7.
The 802.1p priority determines the transmission priority of the traffic from the VLAN when congestion occurs. The higher the value, the higher the priority.
6. Click Save.
Figure 48 Configuring VLAN settings
View shared network port information
You can perform the following tasks:
· Enable or disable Network Controller Sideband Interface (NCSI).
· View information about the shared network port, including port name, MAC address, IP addresses, VLAN settings, and port connection state when NCSI is enabled.
Procedure
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Enable or disable NCSI as needed, and then click OK in the dialog box that opens.
HDM restarts for the configuration to take effect, and the current session is disconnected.
¡ If you enabled NCSI, you can re-log in to HDM to view information about the shared network port or configure the shared network port.
¡ If you disabled NCSI, the shared network port is inaccessible.
Figure 49 Viewing information about the shared network port
Parameters
· Port state: This field is available only when the network port mode is active/standby. Options include:
¡ Active—The port is connected and in active state.
¡ Disconnected—The port is disconnected.
¡ Standby—The port is connected and in standby state.
· Connection Information: Displays connection information about shared network ports, including automatic shared port selection state, network adapter type, and network port connection state. This field is not available when no network adapter is installed or the installed network adapters do not support NCSI. Options include:
¡ Disconnected—The port is disconnected.
¡ Connected—The port is connected but is not in active state.
¡ Active—The port is connected and is in active state.
Configure the shared network port
Perform this task to configure the IPv4 address, IPv6 address, and VLAN settings of the shared network port, change the shared network port, or enable automatic shared port selection when NCSI is enabled.
You can specify a port as the shared network port or enable automatic shared port selection for the system to select a port automatically.
The change of the shared network port does not require reconfiguring port network settings. All the network settings except for the IP address obtained through DHCP continue to take effect after the change. If the IP address of the HDM shared port is obtained through DHCP, the DHCP server re-assigns an IP address to the shared network port after you change it.
Restrictions and guidelines
See "General restrictions and guidelines for network configuration."
The AE module and blade servers do not support VLAN configuration or changing the shared network port.
If the network port mode is active/standby, any IP configuration on the shared network port will be synchronized to the other shared network ports and the dedicated network port.
If you disable automatic shared port selection and do not specify an interface as the shared port, the system uses the shared port specified before you enabled the feature. Make sure the port is in up state. If the port is in down state, HDM will be inaccessible.
To avoid network errors, do not enable both automatic shared port selection and the active/standby mode.
All sLOM, mLOM, FLOM, and OCP network adapters, and NCSI-capable PCIe network adapters support automatic shared port selection.
Before importing a configuration file to edit network port selection and network port mode, make sure the file content is intact and correct.
Prerequisites
Verify that the shared network port is physically connected to the network.
Verify that the shared network port is in Active state if the network port mode is active/standby.
Verify that the network interface to be used as the shared network port is in up state before manually changing the shared network port.
Enable the LAN function
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Click Configure.
4. Enable the LAN function, and then click Save.
Figure 50 Enabling the LAN function
Configure IPv4 settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Click Configure.
4. Select Enable for IPv4 to enable IPv4 network service.
5. Configure IPv4 address settings for the port:
¡ To use the IP address automatically assigned by a DHCP server, select Automatic IP obtaining. This is the default setting.
¡ To manually configure static IP address settings, clear Automatic IP obtaining, and then enter an IPv4 address, subnet mask, and default gateway address.
A gateway of 0.0.0.0 indicates that no default gateway is specified.
6. Click Save.
Figure 51 Configuring IPv4 settings
Configure IPv6 settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Click Configure.
4. Select Enable for IPv6 to enable IPv6 network service.
5. Configure IPv6 address settings for the port:
¡ To use the IP address automatically assigned by a DHCP server, select Automatic IP obtaining.
¡ To manually configure static IP address settings, clear Automatic IP obtaining, and then enter an IPv6 address, the prefix length (in the range of 1 to 127), and default gateway address fe80::9628:2eff:fe9c:ffda.
6. Click Save.
Figure 52 Configuring IPv6 settings
Configure VLAN settings
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Click Configure.
4. Select Enable for VLAN to enable VLAN service.
5. Enter a VLAN ID in the range of 2 to 4094.
6. Enter an 802.1p priority in the range of 0 to 7.
The 802.1p priority determines the transmission priority of the traffic from the VLAN when congestion occurs. The higher the value, the higher the priority.
7. Click Save.
Figure 53 Configuring VLAN settings
Enable automatic shared port selection
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab, as shown in Figure 49.
3. Click Configure.
4. Select Enable for Auto-selection.
5. Click Save.
Figure 54 Enabling automatic shared port selection
Manually specify a shared port
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Shared Port tab.
3. Click Configure.
4. Specify a port as the shared network port, as shown in Figure 54.
5. Click Save.
Configure DNS
To enable access to HDM by using a domain name instead of the management IP address of HDM, configure DNS.
Restrictions and guidelines
If all network ports use static IP addresses, specify the IP addresses of DNS servers manually.
If you are manually specifying IPv6 addresses of DNS servers, specify global IPv6 addresses.
Set a host name for HDM
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the DNS tab.
3. In the Set host name area, use either of the following methods to configure the host name of HDM:
¡ To manually configure the host name, select Manual and enter a host name in the Host name field.
The host name is a string of 1 to 48 characters. Hyphens (-) are allowed. However, the string cannot start or end with a hyphen (-).
¡ To enable HDM to automatically set the host name, select Auto.
The Host name field will be automatically populated with a host name, which is the combination of HDM and the serial number of the server.
4. Click Save.
Configure the DNS service
Perform this task to specify a domain suffix and specify the IP addresses of DNS servers. Use the domain suffix to specify the top-level and second-level domains. This domain suffix will be automatically combined with the HDM host name to form a fully qualified domain name for HDM access.
To configure the DNS service:
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the DNS tab.
3. In the Configure DNS service area, select Enable for DNS service, as shown in Figure 55.
4. Select Manual, IPv4 (Auto), or IPv6 (Auto) from the DNS server setup field.
¡ If you select Manual, enter a domain suffix in the Domain suffix field, and enter the IP addresses of DNS servers. The Domain suffix field is optional.
You can specify a maximum of three DNS servers. The priorities of DNS servers 1, 2, and 3 are in descending order.
¡ If you select IPv4 (Auto) or IPv6 (Auto), select Host name or DHCP Client FQDN from the Dynamic registration field and select the network port for registration info obtaining. The Domain suffix field will be automatically populated, and HDM will search for DNS servers automatically.
The Obtain registration info via field is available only when both the dedicated and shared network ports use an IP address assigned by the DHCP server.
5. Click Save.
Set the network port mode
|
IMPORTANT: The network port modes are not available on the AE module or blade servers. |
HDM supports the following network port modes:
· Normal mode—The HDM dedicated and shared network ports have separate IP addresses and operate in active/active mode. HDM is accessible at both ports. This is the default mode.
· Bonding mode—The HDM dedicated and shared network ports are aggregated into a logical bond port, which uses the IP address and MAC address of the dedicated port. HDM users can access HDM through the bond port as long as the dedicated or shared network port is up.
· Active/standby mode—The HDM dedicated and shared network ports have separate IP addresses and operate in active/standby mode. In this mode, the dedicated port is the primary port and the shared network is the secondary port. HDM is accessible at the dedicated port as long as the dedicated port is up and has network connectivity. After the dedicated port fails, HDM is accessible at the shared port. In standby mode, the shared port cannot forward management traffic, but it can still forward data traffic.
In bonding mode, VLAN setting is configurable only on the bond port. The dedicated and shared network ports do not have separate VLAN settings.
In normal and active/standby mode, you can assign the two ports to different VLANs.
Restrictions and guidelines
Make sure the bonding mode is disabled before you enable active/standby mode, or the active/standby mode is disabled before you enable network port bonding. The two modes cannot be enabled at the same time.
To avoid network errors, do not enable both automatic shared port selection and the active/standby mode.
Before importing a configuration file to edit network port selection and network port mode, make sure the file content is intact and correct.
Prerequisites
· Use one of the following methods to assign IP addresses to the HDM dedicated and shared network ports.
¡ Manually assign IP addresses to the network ports. As a best practice, use addresses in the same subnet. If IP addresses in different subnets are used, HDM might be inaccessible after the shared network port fails.
¡ Use DHCP to automatically assign IP addresses to the network ports.
· Verify that no VLAN settings are configured on the HDM dedicated or shared network ports if you are to enable the bonding mode.
Procedure
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Port Modes tab.
3. In the work pane, select a network port mode.
4. Click Save.
Figure 56 Setting the network port mode
Configure LLDP
The Link Layer Discovery Protocol (LLDP) is a standard link layer protocol that allows network devices from different vendors to discover neighbors and exchange system and configuration information.
Perform this task to enable the server to send LLDP frames. You can also view information about the received LLDP frames on the page.
Procedure
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the LLDP tab.
3. Select Enable, and then click Save.
4. View information about the received LLDP frames.
The list displays information about all connected devices of the server. If a device is unreachable or does not support sending LLDP frames, the corresponding fields display N/A.
Figure 57 Configuring LLDP
Parameters
· Network port: Network port of the server that receives LLDP frames.
· Switch MAC address: MAC address of the connected switch.
· Switch system name: System name of the connected switch.
· Port number: Number of the connected switch port.
· Port info: Information about the connected switch port, port name for example.
· VLAN ID: ID of the VLAN to which the server port belongs.
Configure Wi-Fi settings
Perform this task to configure Wi-Fi settings after you connect a USB Wi-Fi adapter to the server. This enables users to access the server through wireless connections and view information about online wireless clients.
Restrictions and guidelines
This feature is available only for G5 servers except the B5700 G5.
This feature is available only in HDM-2.14 and later.
To restore the network shut down by idle timeout, you can reconnect the USB Wi-Fi adapter or log in to HDM to enable the network.
Procedure
1. On the top navigation bar, click Configuration.
You are placed on the Network page.
2. Click the Wi-Fi Management tab.
The page that opens displays current Wi-Fi settings and information about online wireless clients.
3. Configure Wi-Fi settings as needed:
¡ Enter the Wi-Fi name.
¡ Select the encryption method. If you select Encrypted, you must also specify a Wi-Fi password.
¡ Specify the idle timeout.
¡ Enter the IPv4 address of the wireless network.
¡ Specify the IPv4 address range for IP address assignment to clients.
4. Click Save.
Figure 58 Configuring Wi-Fi settings
5. View client access information.
Figure 59 Viewing client access information
Parameters
· Wi-Fi Status: Enablement status of the Wi-Fi feature.
· Device status: Presence status of the USB Wi-Fi adapter.
· Wi-Fi name (SSID): Name of the wireless network, a case-sensitive string of 1 to 31 characters. Only letters, digits, dots (.), hyphens (-), and underscores (_) are allowed. This field is required. By default, the name is the product name_last 10 characters of the device SN format.
· Encryption mode: Whether to enable network encryption. By default, the network is not encrypted.
· Wi-Fi password: Password of the wireless network, a case-sensitive string of 8 to 63 characters. Only letters, digits, spaces, and special characters `~!@#$%^&*()_+-=[]\{}|;':,./<>? are allowed. This field is required if the encryption mode is Encrypted.
· Idle timeout: Maximum idle period before the network is shut down, in the range of 0 to 200 hours. 0 indicates that wireless network will not be shut down. By default, the value is 1. A network is considered idle if no online clients exist.
· Wi-Fi IP address: IP address of the wireless network. By default, the IP address is 192.168.199.1. The subnet mask is fixed to 255.255.255.0. The IP address cannot belong to the same subnet as the IP address of the HDM dedicated or shared network port.
· IP range: IPv4 address range for IP address assignment to online clients. Make sure the IP address range is in the same subnet as the Wi-Fi IP address. The subnet mask is fixed to 255.255.255.0.
· No.: Number of an online client. The system allows a maximum of two clients to come online at the same time.
· Client MAC address: MAC address of an online client.
· Client IP address: IPv4 address of an online client.
· Host name: Host name of an online client.
NTP
Network Time Protocol (NTP) is a protocol used to synchronize system clocks of devices on a network.
Use this feature to obtain the correct system date and time from an NTP server.
You can manually specify one primary NTP server, one secondary NTP server, and one tertiary NTP server. When synchronizing time with NTP, HDM first uses the primary NTP server. If the primary NTP server is not available, HDM uses the secondary NTP server. If neither the primary nor secondary server is available, HDM uses the tertiary NTP server.
With HDM, you can also choose to obtain NTP server settings from the DHCP server when all manually specified NTP servers are unavailable. If the DHCP server is not available, HDM uses the system date and time obtained in the most recent successful NTP time synchronization or uses the local system date and time.
Configure NTP settings
Restrictions and guidelines
If time synchronization with the NTP server fails because the NTP server is not reachable, the Web interface displays an error message about the failure to obtain date and time from the NTP server. To synchronize with the NTP server after it becomes reachable or to start new time synchronization, you must click Save again. HDM does not perform time synchronization without being triggered by the Save action.
Procedure
1. On the top navigation bar, click Configuration.
2. In the left navigation pane, select NTP.
3. In the work pane, select the time zone of the server.
4. Select Enable or Disable for Use manually specified, then DHCP advertised NTP servers.
¡ With this feature enabled, HDM synchronizes time settings with a manually specified NTP server. If the manually specified NTP servers fail, HDM synchronizes settings with the NTP server obtained from the DHCP server. This is the default setting.
¡ With this feature disabled, HDM synchronizes time settings with ME. After the BIOS reboots, HDM starts to synchronize time settings based on the time in the BIOS (UTC time) and the specified time zone. For example, if the specified time zone is UTC+8, HDM uses a time eight hours earlier than the time in the BIOS.
5. If you select Enable for Use manually specified, then DHCP advertised NTP servers, set the NTP synchronization interval, and enter the addresses of the primary, secondary, and tertiary NTP servers.
The server addresses can be IPv4 addresses, IPv6 addresses, or domain names. The secondary and tertiary servers are optional. The HDM server uses the secondary NTP server only when the primary NTP server fails, and uses the tertiary NTP server only when both the primary and secondary NTP servers fail.
By default, the primary NTP server address is 1.cn.pool.ntp.org, the secondary NTP server address is 2.cn.pool.ntp.org, and the tertiary server address is not specified.
6. Click Save.
HDM attempts to synchronize time.
Figure 60 Configuring NTP settings
Parameters
NTP sync interval: Set the interval at which HDM synchronizes time from the NTP server. By default, the interval is 3600 seconds. The value range is 600 to 2592000 seconds. This setting takes effect only when NTP is configured.
Configure remote services
Access services
View services and user sessions
Restrictions and guidelines
The available services vary by server model.
Procedure
1. In the navigation pane, select Remote Services > Services.
The service list page opens.
2. In the work pane, click View for an access service to view its detailed information, as shown in Figure 61.
Figure 61 Viewing access service entries
3. In the session list that opens, perform either of the following tasks, as shown in Figure 62:
¡ To close a session, click Delete for the session.
¡ To return to the previous page, click Close.
Figure 62 Viewing access services
Parameters
· Name: Name of the service.
HDM provides the following services:
¡ CD-Media—Access to the virtual CDs and DVDs.
¡ FD-Media—Access to the virtual floppy disk drives.
¡ HD-Media—Access to the virtual disk drives and USB.
¡ iHDT—Debugging through Hardware Debug Tool (HDT). This service is available only for the R4950 G5 and R5500 G5 AMD servers.
¡ IPMI—Remote Management Control Protocol (RMCP) or RMCP+ connections to HDM.
¡ KVM—Access to the server from a remote console.
¡ Remote_XDP—Remote debugging and diagnosis through XDP. This service is available only for the R2700 G3, R2900 G3, R4300 G3, R4400 G3, R4700 G3, R4900 G3, R5300 G3, R6700 G3, R4300 G5, R4700 G5, R4900 G5, R5300 G5, and B5700 G5 servers.
¡ SNMP—SNMP access to HDM.
¡ SSH—SSH access to HDM.
¡ Telnet—Telnet access to HDM.
¡ VNC—Access to the server from a Virtual Network Computing (VNC) client.
¡ Web—Access to the HDM Web interface.
· Status: Status of the service. Options include:
¡ Disabled.
¡ Enabled.
· Network ports: HDM network ports that can be used for the service.
¡ eth0—Shared port.
¡ eth1—HDM dedicated port.
¡ both—Both shared and HDM dedicated ports.
¡ Bond0—HDM Bond port.
· Insecure service port: Port used for unencrypted communication of the service.
· Secure service port: Port used for encrypted communication of the service.
· Idle timeout: Idle timeout time of the user session, in minutes. A user session automatically disconnects when it times out.
· Maximum sessions: Maximum number of sessions supported for the service.
· Session ID: ID that identifies the session among HDM user sessions. An asterisk (*) mark indicates that the session was established by using the IP address with which the client accesses the current Web interface.
· Session type: Protocol type or service type of the session.
· User ID: ID of the user account in the user list on the Users & Security > User Accounts page. 0 indicates that the user is neither a local user nor a domain user.
· Username: Username of the user account.
· IP address: IP address of the user using the service.
· User role: User role of the user account, which represents a set of access privileges.
Edit an access service
Restrictions and guidelines
The available services vary by server model.
If you change the default secure or insecure service port of a service, follow these guidelines when you use that service:
· If you change the default IPMI insecure service port number (623), you must use the -p parameter to explicitly specify the port number when you execute an IPMI command.
· If you change the default secure or insure Web service port number, you must explicitly specify the Web service port when you access HDM from a Web browser. The HDM URL address format is https://ip_address:secure-port.
· You can disable the insecure Web service port for users to access HDM only from the secure Web service port. When the insecure Web service port is disabled, you cannot access H5 KVM in unencrypted mode.
· If you change the default Remote_XDP service port number (6868), you must also update the port number change to the OpenIPC client in the installation directory\OpenIPC\Config\SKX\ SKX_ASD_JTAG.xml directory. The installation directory argument represents the installation directory of the OpenIPC client.
Changing the settings of a service restarts the service. During the restart, the service is unavailable.
Before enabling the iHDT service, make sure the server is powered on.
Procedure
1. In the navigation pane, select Remote Services > Services.
2. In the work pane, click Edit for the target service.
3. Edit service parameters, as shown in Figure 63.
Figure 63 Editing an access service
4. To restart the iHDT service, click Restart.
5. Click OK.
The service restarts automatically and all active sessions of the service disconnect.
Parameters
· Insecure service port: Set the service port number for unencrypted communication of the service. For access services except VNC, the value range is 1 to 65535. For VNC, the value range is 100 to 65535.
· Secure service port: Set the service port number for encrypted communication of the service. The value range is 1 to 65535.
Table 10 Default port numbers used by the supported access services
|
Service |
Default insecure port |
Default secure port |
|
CD-Media |
5120 |
5124 |
|
FD-Media |
5122 |
5126 |
|
HD-Media |
5123 |
5127 |
|
iHDT |
6123 |
N/A |
|
IPMI |
623 |
N/A |
|
KVM |
7578 |
7582 |
|
Remote_XDP |
6868 |
N/A |
|
SNMP |
161 |
N/A |
|
SSH |
N/A |
22 |
|
Telnet |
23 |
N/A |
|
VNC |
5900 |
N/A |
|
Web |
80 |
443 |
· Idle timeout: Set the session idle timeout time for the service. You can set the timeout for Web, KVM, SSH, Telnet, and VNC services. The SSH and Telnet services use the same idle timeout time. If you set an idle timeout for both SSH and Telnet, the most recent configuration takes effect.
Table 11 Timeout value ranges and default timeout settings of services
|
Service name |
Timeout value range (in minutes) |
Default timeout (in minutes) |
|
Web |
5 to 120 |
30 |
|
KVM |
5 to 30 |
30 |
|
SSH |
1 to 30 |
10 |
|
Telnet |
1 to 30 |
10 |
|
VNC |
5 to 30 |
10 |
Remote console
You can manage the server and install an operating system (OS) from a remote console.
HDM supports a maximum of four remote control sessions. If you establish the first session, you are the primary user. All subsequent remote console users are secondary users and must obtain access permissions from the primary user.
HDM supports KVM, H5 KVM, and VNC remote consoles. This section describes how to use KVM and H5 KVM remote consoles and configure the VNC login password.
Restrictions and guidelines
To use KVM, you must first set up the OS environment. The environment setup configuration varies by OS type.
To use the VNC remote console, you must first install the VNC client. H5 KVM requires no client.
If you use the virtual media function to install an OS through a remote console, do not restart HDM, update HDM, or perform any power actions during the process.
Launch a KVM or H5 KVM remote console
Restrictions and guidelines
Do not use KVM and H5 KVM at the same time or start the remote console in multiple browsers on one PC.
For security purposes, grant full permission to a trustworthy secondary user when you close the remote console session as the primary user.
Granting full permission to a secondary user removes the full permission from the primary user. Then, the primary user has only the read-only permission.
The primary user can grant full permission to any secondary user when closing the KVM window. If the primary user does not grant full permission in 10 seconds, the permissions of secondary users remain unchanged.
The UID LED of the server flashes if a remote console is active.
Prerequisites
Before you can launch a remote control console, you must perform the following tasks:
· Make sure your user account has the remote control privilege. If you do not have the remote control privilege, contact the administrator.
· To launch the KVM console, make sure your user account has the KVM extended privilege. To launch the H5 KVM console, make sure your account has the Web and KVM extended privileges. If you do not have the Web or KVM privilege, contact the administrator.
Procedure
1. In the navigation pane, select Remote Services > Remote Console, as shown in Figure 64.
Figure 64 Entering remote console page
2. (Optional.) Click Configure, select a launch mode for KVM and H5 KVM, and then click OK.
3. Launch a remote console:
¡ To launch the KVM remote console, click Start KVM.
¡ To launch the H5 KVM remote console, click Start H5 KVM.
Encrypted modes transmit encrypted data and provide better security performance. Unencrypted modes transmit unencrypted data and provide higher transmission speed.
The remote console sign-in page opens.
Figure 65 Remote console sign-in page
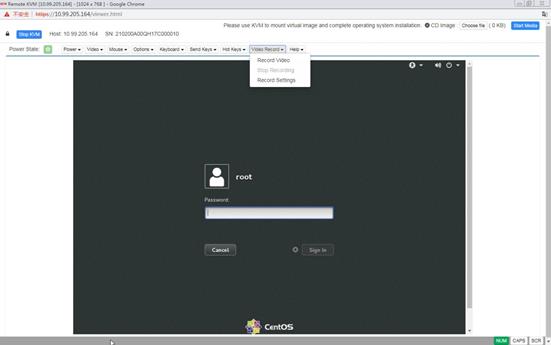
4. For a shared mode, wait for the access authorization from the primary user if you are not the first access user, as shown in Figure 4.
Figure 66 Waiting for remote console access authorization
If you are the primary user, you might need to grant access permissions to other users, as shown in Figure 5.
Figure 67 Authorizing remote console access
Parameters
· Dedicated mode: Includes Encrypted dedicated mode and Unencrypted dedicated mode. A dedicated mode allows for only one remote console session and grants the user with the full access permission. You can launch the remote console successfully in dedicated mode only if no other user is using the remote console.
· Shared mode: Includes Encrypted shared mode and Unencrypted shared mode. A shared mode allows for a primary session and multiple secondary sessions. If you are the first access user, the system assigns you with the full access permission. If you are a secondary user, the granted permission is decided by the primary user as follows:
¡ If you are granted full access permission, you can display information and configure the server.
¡ If you are granted read-only permission, you can only view videos and screenshots, and record videos. You cannot perform any configuration tasks.
¡ If your access is denied, the KVM window closes.
¡ If the primary user does not respond in 30 seconds, you are granted read-only permission.
Operate the server from KVM
Prerequisites
Launch a KVM remote console.
Start up or shut down the server
|
WARNING! The Force Power-Off and Graceful Power-Off options only put the server in standby mode by removing power from most circuits. To maintain the server with all power removed, you must remove all power cords from the server. |
1. Select the Power menu from the top menu bar.
2. Select a menu option as needed.
|
Power menu option |
Purpose |
|
Force System Reset |
Warm reboots the server without power cycling the server. |
|
Force Power-Off |
Shuts down the server immediately by force. This action is equivalent to pressing the power button on the server for five seconds to put the server in standby mode. |
|
Graceful Power-Off |
Shuts down the operating system first, and then removes power from the server to put it in standby mode. |
|
Power On |
Starts up the server. |
|
Force Power-Cycle |
Powers off and then powers on the server. |
3. Use the power icon in the lower right corner of the console to verify the power state of the server.
¡ If
the server is up, the icon is in green (![]() ).
).
¡ If
the server is down, the icon is in red (![]() ).
).
Capture the screen
1. Select Options > Capture Screen from the top menu bar.
2. In the dialog box that opens, select the screenshot file storage path, enter the file name, and then click Save, as shown in Figure 6.
Figure 68 Capturing the screen
Record a video
1. Select Video Record > Settings from the top menu bar.
2. Set the video recording parameters, as shown in Figure 7:
¡ Video Length.
¡ Video to be Saved.
¡ Normalized video resolution to 1024 × 768.
Figure 69 Setting video recording parameters
3. Select Video Record > Start Record to start video recording.
4. Select Video Record > Stop Record to stop video recording.
Mount virtual storage media
1. Select Media > Virtual Media Wizard from the top menu bar.
2. Mount a virtual storage medium, as shown in Figure 8:
¡ To mount a virtual CD/DVD, click the CD/DVD tab, click Browse next to a CD Image field to select a CD/DVD file or CD/DVD drive of the local PC, and then click Connect.
¡ To mount a virtual floppy disk, click the Floppy tab, click Browse next to the Floppy Image field, select a floppy disk file from the local PC, and then click Connect.
¡ To mount a virtual hard disk drive or USB, click the Hard disk/USB tab, and perform one of the following tasks:
- If the image already exists in the hard drive or USB, select HD/USB Image, click Browse next to the HD/USB Image field, select a disk file or USB device of the local PC, and then click Connect.
- If the image does not exist in the hard drive or USB but the files to be mounted exist in the local PC, select Folder Path, click Browse next to the Folder Path field to select the folder from the local PC. Then, click Browse next to the Image Path field to select a path from the hard drive or USB for saving the image generated by using the selected folder, and then click Connect.
Make sure the folder is not larger than 600 M, and the path for saving the image is different from the path for saving the folder.
Figure 70 Mounting a virtual storage medium
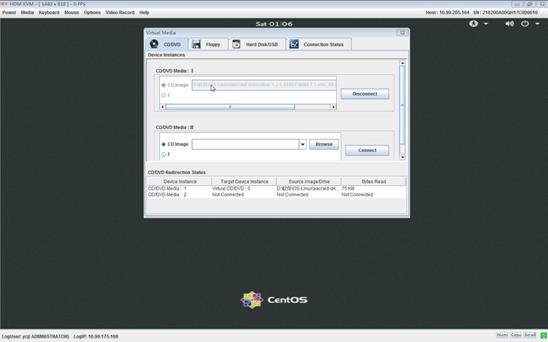
3. To unmount a virtual storage medium, access the medium tab, and click Disconnect.
Quit the remote console
To quit the remote console and disconnect from HDM, use one of the following methods:
· Click the close button ![]() of the
remote console window.
of the
remote console window.
· Click Logout on the HDM Web interface.
The KVM idle timeout does not take effect if a virtual medium is mounted through the remote console.
Configure the peripherals in the KVM console
· To configure keyboard settings, select the Keyboard menu from the top menu bar, and then select the desired menu option.
|
Keyboard menu option |
Task |
|
Ctrl+Alt+Del |
Perform an action equivalent to pressing the Ctrl, Alt, and Delete keys simultaneously on the keyboard. |
|
Hot Keys |
Define and use hot keys. You can define a maximum of 20 hot keys, each being a combination of up to six keys. |
|
SoftKeyboard |
Open the soft keyboard. Only American English soft keyboard is supported. |
· To configure the mouse settings, select the Mouse menu from the top menu bar, and then select the desired menu option.
|
Mouse menu option |
Task |
|
Show Cursor |
· Select this option to display mouse pointer trails. · Clear this option to hide mouse pointer trails. |
|
Mouse Calibration |
Calibrates the mouse location in relative mouse mode. |
|
Mouse Mode |
The mouse mode is used to calculate the current location of the mouse. Options include: · Absolute mouse mode—Calculates the mouse location according to the screen's absolute coordinates. · Relative mouse mode—Calculates the mouse location according to the offset of the mouse movement. · Other mouse mode—Calculates the mouse location according to the distance from the mouse to the screen center. Mouse mode recommendations for server operating systems: · Use absolute mouse mode in Windows 2008, Windows 2012, Redhat 6.5, Redhat 7.0, CentOS 6.5, CentOS 7.1, Ubuntu 12.04, Ubuntu 15.04, SLES 11, and SLES 13. · Use relative mouse mode for versions lower than Redhat 6, CentOS 6, or Fedora 14. · Use other mouse mode in SLES 11 installation interface. · Use absolute mouse mode in any operating systems that are not mentioned above. · As a best practice, do not change the mouse mode frequently. · The Show Cursor feature will be enabled automatically if you change the mouse mode from relative or other to absolute. |
Change the language in the KVM console
1. Select Options > GUI Languages from the top menu bar.
2. Change the language to Chinese or English.
Block full permission requests
If you are the primary user (the user that established the first console session), you might receive full permission requests from remote console users who have only read-permission.
To block full permission requests, select Options > Block Privilege Request from the top menu bar.
Accelerate OS installation
To accelerate OS installation, select Options > CD/DVD Acceleration from the top menu bar.
As a best practice, enable CD/DVD acceleration only when the following requirements are met:
· All switches and routers in the network operate at 1 Gbps or above.
· The user accesses HDM through a shared network port.
· A virtual CD/DVD image is mounted.
Support for this feature depends on server configuration.
Configure boot options for the next boot
To configure the boot option, boot mode, and boot order for the server to use at the next reboot, select Options > Boot Options from the top menu bar. For more information, see "Configure boot options."
Obtain version and copyright information
To obtain version and copyright right information, select Help > About HDM KVM from the top menu bar.
Use keyboard buttons
The remote console provides the following keyboard buttons at the bottom right:
· Num—Equivalent to pressing the Num key on the keyboard.
· Caps—Equivalent to pressing the Caps key on the keyboard.
· Scroll—Equivalent to pressing the Scroll key on the keyboard.
Operate the server from H5 KVM
Prerequisites
1. Launch an H5 KVM remote console.
2. To perform any server tasks except viewing videos and screenshots and recording videos, make sure you have full permission.
Block full permission requests
If you are the primary user (the user that established the first console session), you might receive full permission requests from remote console users who have only read-permission.
To block full permission requests, select Options > Block Privilege Request from the top menu bar.
Configure boot options for the next boot
To configure the boot option and boot mode for the server to use at the next reboot, select Options > Boot Options from the top menu bar. For more information, see "Configure boot options."
Configure the system boot order
To configure the system boot order, select Options > Configure Boot Order from the top menu bar. For more information, see "Configure boot options." This feature is available only for some servers.
Accelerate OS installation
To accelerate OS installation, select Options > CD/DVD Acceleration from the top menu bar.
The CD/DVD Acceleration option is available only when the following requirements are met:
· The user accesses HDM through a shared network port on a required Ethernet adapter.
· A virtual CD/DVD image is mounted.
As a best practice, use the CD/DVD acceleration feature only when all switches and routers in the network operate at 1Gbps or above.
Access the server
You can use the keyboard, mouse, and monitor of the local PC to access the server.
Start up or shut down the server
|
WARNING! The Force Power Off and Graceful Power Off options only put the server in standby mode by removing power from most circuits. To maintain the server with all power removed, you must remove all power cords from the server. |
1. Select the Power menu from the top menu bar.
2. Select a menu option as needed.
|
Power menu option |
Purpose |
|
Immediate Reset |
Warm reboots the server without power cycling the server. |
|
Force Power Off |
Shuts down the server immediately by force. This action is equivalent to pressing the power button on the server for five seconds to put the server in standby mode. |
|
Graceful Power Off |
Shuts down the operating system first, and then removes power from the server to put it in standby mode. |
|
Power On |
Starts up the server. |
|
Power Cycle |
Powers off and then powers on the server. |
3. Use the power icon in the upper left corner of the console to verify the power state of the server.
¡ If
the server is up, the icon is in green (![]() ).
).
¡ If
the server is down, the icon is in red (![]() ).
).
Record a video
1. Select Video Record > Record Settings from the top menu bar.
Figure 71 Selecting record settings
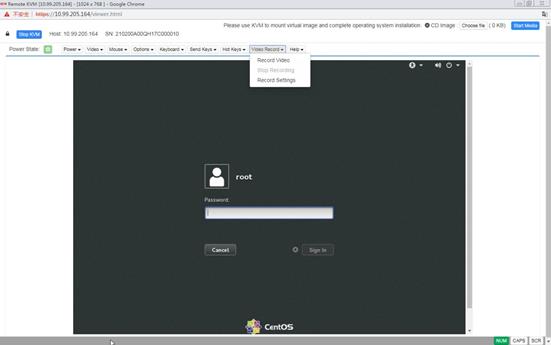
2. Set the video recording parameters:
¡ Video Length—Enters the maximum time length of the video. The value range is 1 to 1800 seconds.
¡ Video Compression—Sets the view compression ratio. The value range is 0.1 to 1.
¡ Normalized video resolution to 1024 × 768—To use the 1024 × 768 resolution, select this option. If you do not select this resolution, the screen resolution of the server monitor is used.
Figure 72 Setting video recording parameters
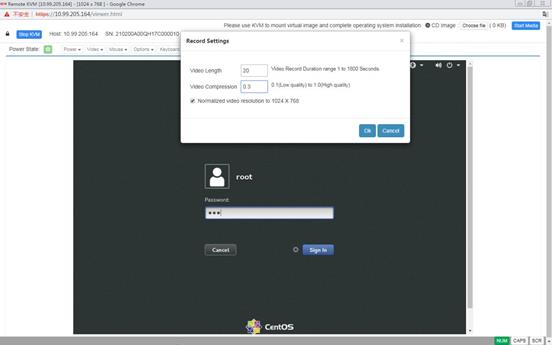
3. Select Video Record > Record Video to start video recording.
4. Select Video Record > Stop Record to stop video recording.
Play a video
1. Select the Video menu from the top menu bar.
2. Select a menu option as needed:
¡ To pause the video while it is playing, select Pause Video.
¡ To resume video playing, select Resume Redirection.
¡ To refresh the video displayed on the remote console, select Refresh Video.
Capture the screen
Select Video > Capture Screen from the top menu bar, as shown in Figure 11.
Figure 73 Capturing the screen
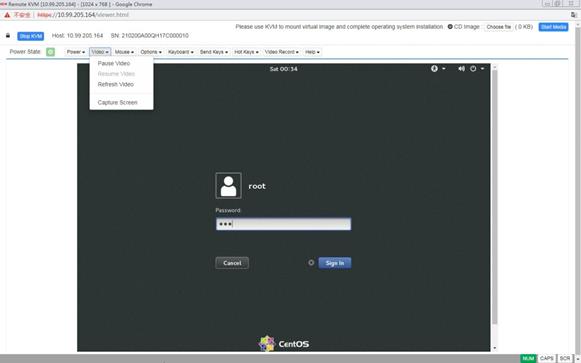
Configure the peripherals in the H5 KVM console
· To configure keyboard settings, select the Keyboard menu from the top menu bar, and then select the desired menu option.
|
Keyboard menu option |
Task |
|
Keyboard Layout |
Change the keyboard layout. |
|
English U.S |
Use the U.S. English keyboard layout. |
· To perform Send Keys operations, select the Send Keys menu from the top menu bar, and then select the desired menu option.
|
Send Keys menu option |
Description |
|
Hold Down section |
|
|
Right Ctrl Key |
Perform an action equivalent to pressing the right Ctrl key on the keyboard. |
|
Right Alt Key |
Perform an action equivalent to pressing the right Alt key on the keyboard. |
|
Right Windows Key |
Perform an action equivalent to pressing the right Windows key on the keyboard. |
|
Left Ctrl Key |
Perform an action equivalent to pressing the left Ctrl key on the keyboard. |
|
Left Alt Key |
Perform an action equivalent to pressing the left Alt key on the keyboard. |
|
Left Windows Key |
Perform an action equivalent to pressing the left Windows key on the keyboard. |
|
Press and Release section |
|
|
Ctrl+Alt+Del |
Perform an action equivalent to pressing and releasing the Ctrl, Alt, and Delete keys simultaneously on the keyboard. |
|
Left Windows Key |
Perform an action equivalent to pressing and releasing the left Windows key on the keyboard. |
|
Right Windows Key |
Perform an action equivalent to pressing and releasing the right Windows key on the keyboard. |
|
Context Menu Key |
Perform an action equivalent to pressing and releasing the context menu key on the keyboard. |
|
Print Screen Key |
Perform an action equivalent to pressing and releasing the PrScrn key on the keyboard. |
· To define and use hot keys, select the Hot Keys menu from the top menu bar, and then select Add Hot Keys.
· To configure the mouse settings, select the Mouse menu from the top menu bar, and then select the desired menu option.
|
Mouse menu option |
Task |
|
Show Client Cursor |
· Select this option to display mouse pointer trails. · Clear this option to hide mouse pointer trails. |
|
Mouse Mode |
The mouse mode is used to calculate the current location of the mouse. Options include: · Absolute Mouse Mode—Calculates the mouse location according to the screen's absolute coordinates. · Other Mouse Mode—Calculates the mouse location according to the distance from the mouse to the screen center. As a best practice, use KVM if you are using one of the following operating systems, with which the absolute mouse mode does not work well: · CentOS 6, Fedora 14, Redhat 6, or their lower versions. · SLES 11 installation interface. · As a best practice, do not change the mouse mode frequently. · The Show Client Cursor feature will be enabled automatically if you change the mouse mode from other to absolute. |
Obtain version and copyright information
To obtain version and copyright right information, select Help > About H5Viewer from the top menu bar.
Mount virtual media
H5 KVM only supports mounting an .iso image.
1. Click Browse File in the upper right corner of the remote console.
2. Select an .iso image file.
To unmount the virtual media, click Stop Media.
Use keyboard buttons
The remote console provides the following keyboard buttons at the bottom right:
· NUM—Performs an action equivalent to pressing the Num key on the keyboard.
· CAPS—Performs an action equivalent to pressing the Caps key on the keyboard.
· SCR—Performs an action equivalent to pressing the Scroll key on the keyboard.
Operate the server from VNC
About VNC
VNC is a technology for remote desktop sharing. In a VNC system, the client can connect to the server and control the remote desktop of the server by using the Remote Frame Buffer (RFB) protocol. RFB is a simple protocol used for remote access to graphical user interfaces. It works at the framebuffer level and is applicable to all windowing systems and applications such as Windows and Mac. VNC allows you to access and manage the server from a local PC without logging in to HDM.
HDM supports both IPv4 and IPv6 VNC sessions. The following session modes are available:
· Shared mode—Supports a maximum of two concurrent VNC sessions. Both of the sessions have access to the mouse and keyboard and have the control of the server's OS.
· Exclusive mode—Supports only one VNC session.
The session mode used in a VNC system is determined by the VNC client.
Prerequisites
Before you use VNC to operate the server, you must complete the following tasks:
· Sign in to HDM, and enable the VNC service on the Remote Services > Services page.
· Install a VNC client. This example uses TightVNC.
Procedure
1. Open the VNC client, enter the HDM management IP address in the address bar, and click Connect, as shown in Figure 12.
Figure 74 Entering the login page
2. In the window that opens, enter the VNC password (the default is root), and then click OK, as shown in Figure 13.
Figure 75 Authenticating to VNC server
A VNC session is established between the VNC client and VNC server. The VNC client displays the server screen.
You can view the established VNC session from the Remote Services > Services page of HDM. The IP address for the VNC session is the IP address of the VNC client.
Figure 76 VNC session information
3. Operate the server as needed.
Configure the VNC login password
Use this feature to configure the settings of passwords for VNC client login. By default, the password is root.
Procedure
1. In the navigation pane, select Remote Services > Remote Console.
2. In the work pane, click the VNC tab, as shown in Figure 15.
3. (Optional.) Select Enable for Complexity check.
4. Enter a new password and confirm the new password.
5. Click Save.
Parameters
Complexity check: Disable or enable password complexity check.
· If this feature is disabled, passwords must meet the following basic complexity requirements:
¡ 1 to 8 characters in length.
¡ Case sensitive. Valid characters are letters, digits, spaces, and special characters `~!@#$%^&*()_+-=[]\{}|;':",./<>?
· If this feature is enabled, passwords must meet the following enhanced complexity requirements:
¡ 8 characters in length.
¡ Case sensitive. Valid characters are letters, digits, spaces, and special characters `~!@#$%^&*()_+-=[]\{}|;':",./<>?
¡ Must contain characters from at least two of the following categories: uppercase letters, lowercase letters, and digits.
¡ Must contain at least one space or special character.
Remote media mounting
Image mounting mounts image files from a remote device to the operating system of the server. With this feature, you do not need to copy image files to the server before you can mount them.
You can mount virtual media by using the remote console (see "Remote console") or the image mounting feature. The following describes how to use image mounting to mount remote media images files.
Mount remote media
Perform this task to mount remote media to the server's operating system.
Prerequisites
Before you configure remote media image mounting, perform the following tasks:
1. Verify that the image files to be mounted are in correct format.
A CD/DVD image file must use the .iso extension, and a disk image file (for example, floppy disk, HDD or SSD) must use the .img or .ima extension.
A floppy disk image file cannot exceed 1.44 MB.
2. Make sure the number of CD/DVD image files, floppy image files, and disk image files each in the source directory on the NFS or CIFS server does not exceed 60.
3. Make sure your user account has the administrator or operator role or the remote media privilege. If the account is neither an administrator nor an operator, and does not have the remote media privilege, contact the administrator to obtain the privilege.
4. Make sure the desired virtual media services have been enabled for your user account. If they are not enabled, contact the administrator. You can use CD-Media and HD-Media to mount two image files and use FD-Media to mount only one media.
Procedure
1. Set up the image mounting environment. For more information, see "Configure virtual media."
2. In the navigation pane, select Remote Services > Virtual Media, as shown in Figure 16.
Figure 78 Accessing the remote media mounting page
3. In the work pane, click Settings.
4. In the dialog box that opens, enable remote media, select media types, and then click OK, as shown in Figure 17.
¡ If you select NFS as the shared file system, enter the server address and source path.
¡ If you select CIFS (Samba) as the shared file system, enter the server address, source path, username, password, and domain name. The domain name field is optional.
To avoid image mounting failure, do not enter unnecessary special characters, such as pound signs (#).
|
IMPORTANT: If remote media mounting has already been enabled, the media settings cannot be modified unless you stop all remote media mountings. |
Figure 79 Configuring media mounting settings
5. In the navigation pane, select Remote Services > Virtual Media.
6. Select an image file from the remote media list, and then click Start.
To unmount the image file, click Stop.
Figure 80 Starting or stopping remote media mounting
Parameters
· Media type: Type of the remote media, including CD/DVD, floppy, and disk (which includes both HDD and SSD).
· Status: Remote media mounting status, including Started and Not started. Common reasons for the Not started status include the following:
¡ Opening error—The image file is invalid.
¡ Connection in use—The maximum number of mounting sessions has reached.
¡ Connection lost—The virtual media service has failed.
¡ Access error—The virtual media service is not enabled.
¡ Session terminated—The virtual media session is terminated.
· Session index: Index of the remote media mounting session.
Disable remote media
1. In the navigation pane, select Remote Services > Virtual Media.
2. In the work pane, click Settings.
3. In the dialog box that opens, select Disable for the remote media, and then click OK, as shown in Figure 17.
SNMP
Simple Network Management Protocol (SNMP) is an Internet protocol used for remote management and operations. It allows users to manage devices of different vendors with different physical characteristics and interconnection technologies in the network through NMS. For example, monitor device status, collect statistics, and perform troubleshooting.
Perform this task to configure SNMP settings, including SNMP version, read-only community string, and read/write community string.
Restrictions and guidelines
The SNMP SET operation is not supported if the read/write community string is empty.
The read/write community string cannot be the same as the read-only community string.
The read/write community string and read-only community string are displayed in ciphertext format from the Web interface.
Procedure
1. In the navigation pane, select Remote Services > SNMP.
2. In the work pane, configure SNMP settings:
a. Select an SNMP version.
b. Select whether to enable the long community string feature.
c. Select Edit read-only community string or Edit read/write community string, and enter or delete the read-only or read/write community string.
3. Click Save.
Figure 81 Configuring SNMP settings
Parameters
· SNMP version: Select an SNMP version available for SNMP GET and SET operations. Options include v1 and v2c. SNMP v3 is supported by default.
· Long community string: Select whether to enable the long community string feature. This feature is disabled by default.
If you enable the long community string feature, the value range for the community strings is 16 to 32 characters. If you disable the long community string feature, the value range for the community strings is 1 to 32 characters. You can leave the read/write community string empty, regardless of whether the long community string feature is enabled.
· Read-only community string: Enter the read-only community string for security authentication. By default, this field is empty but the default read-only SNMP community string is rocommstr.
· Read/write community string: Enter the read/write community string for security authentication. By default, no read/write SNMP community string is specified.
Remarks
The Read-only community string and Read/write community string fields can contain only letters, digits, and special characters`~!@$%^&*()_+-=[]{}|:,./?
Remote O&M
Logs
Manage the event log
Perform this task to configure the event log policy, view, download, or clear event logs.
Restrictions and guidelines
When the event log reaches the maximum size (3639), logging action on new events depends on the event log policy.
After all event log entries are deleted, the system automatically generates a log entry that records the deletion.
Procedure
1. On the top navigation bar, click Remote O&M.
You are placed on the Logs page.
2. On the Event Log tab, select an event log policy from the Log policy field.
3. In the work pane, use one of the following methods to filter events:
¡ Select a severity level of the events.
¡ Select a sensor type.
¡ Select or customize a period when the events generated.
¡ Enter your keywords.
4. To filter events based on keywords, enter
the keywords, and then click the query icon ![]() .
.
5. To clear all specified filter criteria, click Reset.
6. To save event log entries to a .csv file, click Save.
7. To delete all event log entries, click Delete all.
The deleted event log entries cannot be restored.
Figure 82 Managing the event log
Parameters
· Stop logging at full storage: The system stops logging on new events when the event log fills up.
· Overwrite oldest entries at full storage: The system overwrites oldest entries with new log entries when the event log fills up.
· ID: Event number. Events are numbered in chronological order. By default, the events in the event list are sorted by event number in ascending order.
· Timestamp: Date and time when the event was logged.
· Alert status: Alarm status of the event. Cleared means that the event alarm has been cleared. Triggered means that the event is to be resolved.
· Severity: Severity level of the event.
¡ Info—The event does not adversely affect the system. No action is required. Examples of informational events include expected state change events and alarm removed events.
¡ Minor—The event has minor impacts on the system. Prompt action is required to avoid an escalation in severity.
¡ Major—The event might cause part of the system to fail and result in service interruption. Immediate action is required.
¡ Critical—The event might result in system outage or power failure. Immediate action is required.
· Event code: Event code that identifies a system event in HDM.
· Recommended action: Actions recommended for a system event.
Manage the operation log
The operation log includes audit log entries, firmware update log entries, hardware update log entries, and configuration log entries.
· Audit log entries record HDM administrative events, including access to HDM and remote console startup.
· Firmware update log entries record HDM firmware updates as well as their results.
· Hardware update log entries record hardware updates as well as their results.
· Configuration log entries record user configuration operations as well as their results.
Restrictions and guidelines
After all operation log entries are deleted, the system automatically generates a log entry that records the deletion.
Procedure
1. On the top navigation bar, click Remote O&M.
You are placed on the Logs page.
2. Click the Operation Log tab.
3. In the work pane, select a sensor type or a severity level to filter events as follows:
¡ To display the events generated by sensors of a particular type, select that sensor type from the All types list.
¡ To display the events of a particular level, select that severity from the All severities list.
4. To save operation log entries to a .csv file, click Save.
5. To delete all operation log entries, click Delete All.
The deleted log entries cannot be restored. Please use this feature with caution.
After the deletion, the system generates a log deletion log message.
Figure 83 Managing the operation log
Parameters
· ID: Event number. Events are numbered in chronological order. By default, the events in the event list are sorted by event number in ascending order. The system can display a maximum of 1000 event log entries.
· Timestamp: Date and time when the event was logged.
· Interface type: Type of the interface through which the operation was performed.
· IP address: User IP address.
· Host name: HDM host name.
· Description: Description of the log entry.
Download log
Perform this task to download Smart Diagnosis System (SDS) logs of the server. The SDS log includes BMC event log, BMC operation log, device information, operating parameters, and internal diagnostic information.
By decoding the collected SDS logs, users can comprehensively locate and analyze issues that occur to the server.
To decode SDS logs, contact Technical Support. As a best practice, add contact information at log downloading.
|
|
NOTE: In HDM-2.96 and later versions, you can scan the QR code on the screen to view the functional diagram or give feedback. |
Restrictions and guidelines
Simultaneous log downloading by multiple users is not supported.
An .sds file saves log entries in UTC, but HDM uses the date and time synchronized from an NTP server. If you download log entries for a specific period, HDM converts the specified start time and end time into UTC, which might introduce time differences.
The downloaded log entries are saved in an .sds file folder. For more information about files in the file folder, see "Appendix A Downloaded log files."
Procedure
1. On the top navigation bar, click Remote O&M.
You are placed on the Logs page.
2. Click the Log Download tab.
3. Display log entries to download:
¡ To download the log entries for a period, set a time range in days in the Download specified log area, and then click Download specified log.
¡ To download the entire log, click Download entire log.
The log entries will be displayed in the dialog box that opens.
Figure 84 Downloading log
4. (Optional.) Add contact information, including the name, phone number, and email address.
5. Click Download log to download the log. This page displays a progress bar.
Figure 85 Downloading the log
6. Save the displayed log entries to an .sds file on the local server.
SOL connection
Perform this task to select the serial port to connect to when the SOL feature is enabled.
Prerequisites
Before setting the SOL connection mode, make sure the SOL feature is disabled.
Procedure
1. On the top navigation bar, click Remote O&M .
2. In the left navigation pane, select SOL Connection.
3. In the work pane, select a serial port from the SOL connection mode field.
4. Click Save.
Figure 86 Setting the SOL connection
Parameters
· BIOS/OS: Connects to the BIOS or OS serial port.
· RAID: Connects to the serial port of the mezzanine storage controller.
· Smart Ethernet adapter: Connects to the serial port of the smart network adapter. Only some smart network adapters support serial port connection.
Screenshots & videos
Enable video recording
This feature records the server status upon occurrence of severe operating system events, including crash, restart, and shutdown. You can replay these videos to analyze or troubleshoot the recorded events.
Prerequisites
Make sure the KVM service has been enabled for your user account. If KVM is not enabled, contact the administrator.
If the remote console is open when an event triggers video recording, video recording will fail.
Procedure
1. On the top navigation bar, click Remote O&M
2. In the left navigation pane, select Screenshots & Videos.
3. In the work pane, click Configure.
4. In the dialog box that opens, enable video recording.
5. Set the video length. The value range is 15 to 255 seconds.
6. Select types of events to be recorded: crash, restart, or shutdown.
Crash event recording is available for Windows and Linux operating systems.
7. Click Save.
Figure 87 Configuring video recording
Play and manage videos
On the video replay page, you can play, download, and delete the recorded videos.
The system supports a maximum of three video files. If three video files already exist, a new video file overwrites the earliest one. The file creation time is recorded in the file properties.
Restrictions and guidelines
If the operating system was in sleep state when the event occurred, HDM displays a no signal message in place of the video.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Screenshots & Videos.
3. In the Video files section, click the video to be played.
4. To download a video, click Download after the video is loaded.
5. To close a video, click Cancel.
6. To delete a video, click the ![]() icon in the lower right corner of the
video and click Delete.
icon in the lower right corner of the
video and click Delete.
Figure 88 Playing videos
View BSoD screenshots
Prerequisites
Make sure the KVM service has been enabled for your user account. If KVM is not enabled, contact the administrator.
Restrictions and guidelines
If the server is installed with a non-Windows operating system, HDM also takes screenshots upon MCA triggers when the server detects an MCA error.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Screenshots & Videos.
3. View the BSoD screenshots listed on the page.
Figure 89 Viewing BSoD screenshots
Alarm settings
Use this feature to perform the following operations:
· Configure alert policies on the server when an error occurs, including NMI control and MCA policy.
· Send emails, SNMP traps, or syslog messages to notify the concerned server administrative staff members of server events for prompt action.
· Configure system diagnosis for the server.
|
|
NOTE: In HDM-2.96 and later versions, you can scan the QR code on the screen to view the function diagram or give feedback. |
Manage alert policies
Enable NMI debug
This feature enables the operating system debugger to help you debug software lock-up issues by generating non-maskable interrupts.
Restrictions and guidelines
The Non Maskable Interrupt (NMI) debug feature is intended for debugging only. Do not use this feature if the server is operating correctly.
Prerequisites
Verify that the operating system can handle NMIs. If the operating system cannot handle NMIs, using NMI debug might cause the operating system to crash.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. In the NMI debug section of the work pane, click Execute.
Figure 90 Enabling NMI debug
Set the MCA policy
Machine Check Architecture (MCA) is an Intel mechanism that enables error reporting and error recovery. IERRs include processor errors, memory errors, and PCIe errors. Perform this task to configure whether to restart the server automatically when an IERR occurs.
The R4950 G3, R4330 G5, R4930 G5, R4950 G5, and R5500 G5 AMD servers do not support MCA.
Restrictions and guidelines
The MCA policy does not affect the OS restart policy.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. In the MCA policy section of the work pane, select Yes or No from the Restart upon IERR occurrence field.
4. Click Save.
Figure 91 Setting the MCA policy
Manage alert emails
HDM sends alert emails through Simple Mail Transfer Protocol (SMTP). To send an alert email to a user, you must configure SMTP, specify that user as an email recipient, and configure the alert policy for that user.
Prerequisites
Make sure you have specified an email address in the user account for the email recipient. For information about adding an email address for a user account, see "User accounts."
Set up SMTP for alert emails
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the Email notification tab.
4. In the SMTP section, click Configure.
5. In the dialog box that opens, configure SMTP:
¡ Select Enable for SMTP.
¡ Enter the SMTP server address and port number.
¡ To send alert emails as anonymous emails, select Enable for Anonymous email. To send alert emails with sender identity information, clear Enable for Anonymous email and enter the username and password for connecting to the SMTP server. The username can contain only letters, digits, underscores (_), at signs (@), and dots (.).
¡ Enter the sender email address. Make sure the email service uses the SMTP mail server.
¡ Select severity levels. Options include Critical, Minor + Major + Critical, and All.
6. Click OK.
Figure 92 Setting up SMTP for alert emails
Add an alert email recipient
1. To have a user receive alert emails, you must specify an email address for that user when you set up the user account on the Users & Security > User Accounts page.
2. On the top navigation bar, click Remote O&M.
3. In the left navigation pane, select Alarm Settings.
4. Click the Email notification tab.
5. Click Add.
6. In the dialog box that opens, select the username of the recipient.
The email address of the user is automatically populated. To edit the email address, click the Here link.
7. Enter the email subject. Only letters, digits, and underscores (_) are supported for the email subject.
8. Click Test to send a test email, and then click Result to view the test result.
9. To edit the settings for a recipient, click Edit in the email recipient entry.
10. To delete a recipient, click Delete in email recipient entry.
Manage SNMP traps
You can send server events in SNMP traps to an SNMP management workstation.
Configure SNMP trap settings
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the SNMP trap tab.
4. In the SNMP trap settings section, click Configure.
5. In the dialog box that opens, configure SNMP trap settings.
a. Select Enable for SNMP trap.
b. Select an SNMP trap mode. Options include Node mode and Event mode (recommended).
c. Select an SNMP version. If SNMPv3 is selected, you must also specify an SNMPv3 user in the Choose trap v3 user field.
d. (Optional.) Enter the location of the server and contact information.
e. Enter a community name.
f. Select severity levels.
6. Click OK.
Figure 93 Configuring SNMP trap settings
Configure SNMP trap server settings
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the SNMP trap tab.
4. In the SNMP trap server settings section, click Edit in a server entry.
5. In the dialog box that opens, configure SNMP trap server parameters.
Figure 94 Configuring SNMP trap server settings
6. Click Save.
7. (Optional.) Click Test in a server entry to send a test email.
Parameters
· Node mode: Specifies the OID of an SNMP node as the ID of a trap event. This is the default mode.
· Event mode (recommended): Specifies the OID of the SNMP node that is in a mapping relationship with a trap event as the ID of the event. Information provided by this mode is more accurate.
· SNMP version: Select an SNMP version. Options include SNMPv1, SNMPv2c, and SNMPv3.
· Choose trap v3 user: Select the username used by the system to send SNMPv3 traps.
· System location: Enter the location of the server, a string of up to 31 characters.
· Contact: Enter contact information, a string of up to 31 characters.
· Trap community: Enter the trap community string for authentication on the manager. The value range is 1 to 31 characters. The default value is public.
· Severity levels: Select the severity levels. Options include Major + Critical, Minor + Major + Critical, and All.
· No.: Entry number. You can specify a maximum of eight servers, one server in each entry. This field cannot be edited.
· Status: Indicates whether trap notification is enabled for the specified server.
· Server address: IP or domain address of the destination host.
· Server port: Enter the port number at which the destination host receives SNMP traps. The value range is 1 to 65535. The default port number is 162.
Remarks
The System location, Contact, and Trap community fields can contain only letters, digits, and the following special characters:
` ~ ! @ $ % ^ & * ( ) _ + - = [ ] { } | : , . / ?
Manage syslog settings
Perform this task to use syslog messages to report the following information to destination hosts:
· Log information including operation, event, and security log messages.
· Sensor information including sensor name, reading, and state.
· Host serial port information including BIOS boot and OS serial port information.
Restrictions and guidelines
The alarm log server settings restore to the default after you change the alarm log notification settings.
Prerequisites
Before enabling syslog notification, make sure an alarm log server is available.
Configure syslog notification settings
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the Syslog Settings tab.
4. In the Alarm log notification section, click Configure, and then perform the following tasks:
a. Enable alarm log notification.
b. Select an alarm log server identifier.
c. Select a transmission protocol.
If you select TLS, you must select an authentication mode, and upload the CA certificate, local certificate, and private key file.
d. Click OK.
Figure 95 Configuring syslog notification settings
5. In the Alarm log server settings section, click Edit in a server entry, and then perform the following tasks:
a. Enable the server.
b. Edit the IP address and port number of the alarm log server as needed.
c. Select the types of logs to be reported.
d. Click OK.
Figure 96 Configuring alarm log server settings
Configure SDR information settings
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the Syslog Settings tab.
4. In the SDR Information Settings section, click Configure, and then perform the following tasks:
a. Enable SDR remote log.
b. Select a transmission protocol.
c. Enter the IP address and port number of an alarm log server, and specify a report interval.
d. Click OK.
Figure 97 Configuring SDR information settings
Configure host serial port settings
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the Syslog Settings tab.
4. In the Host Serial Port Settings section, click Configure, and then perform the following tasks:
a. Enable serial port log.
b. Select a transmission protocol.
c. Enter the IP address and port number of an alarm log server.
d. Click OK.
Figure 98 Configuring host serial port settings
Parameters
· Alarm log host ID: Select an alarm log server identifier. Options include Host name, System board serial number, Asset tag, and Product serial number.
· Transmission protocol: Select the transmission protocol used for syslog message transmission. Options include:
¡ TCP—A connection-oriented protocol that requires establishing connection between the sender and the receiver before data transmission.
¡ UDP—A message-oriented protocol that does not require establishing connection between the sender and the receiver before data transmission.
¡ TLS—A connection-oriented protocol and provides privacy and data integrity between the sender and the receiver.
· Authentication mode: Select an authentication mode. Options include:
¡ One-way authentication: Authenticates only the alarm log server.
¡ Two-way authentication: Authenticates both the alarm log server and the client used for HDM login.
· CA certificate: Upload a CA certificate in PEM format to authenticate packets sent by the alarm log server.
· Local certificate: Upload a local certificate in PEM format whose information will be carried in packets sent to the alarm log server by HDM for the server to authenticate the client used for HDM login.
· Private key: Upload a private key file in PEM format to decrypt the local certificate.
· No.: Entry number. You can specify a maximum of eight servers, one server in each entry. This field cannot be edited.
· Server address: Enter the IP address or domain name of the destination host. The default IP address is 127.0.0.1. A domain name cannot exceed 48 characters.
· Server port: Enter the port number at which the destination host receives syslog messages. The value range is 1 to 65535. The default port number is 514.
· Log type: Types of logs to be reported. Options include Operation log, Event log, and Security log.
· Interval: Specify the interval at which sensor information is reported, in the range of 10 to 2592000 seconds.
Configure system diagnosis
Perform this task to perform minimum configuration startup or diagnosis isolation if the server gets stuck in POST phase because of hardware replacement errors.
Minimum configuration startup enables the system to start the UEFI SHELL or OS installed on the SATA M.2 SSDs with one CPU, one core, and memory modules in one channel.
Diagnosis isolation enables the system to diagnose hardware components, isolate failed components, and then start up.
Restrictions and guidelines
This feature is available only in HDM-2.26 and later.
This feature is available only for the R4300 G5, R4700 G5, R4900 G5, and R5300 G5 servers.
Before performing this task, make sure the BIOS is not being updated.
If you enable both minimum configuration startup and diagnosis isolation, only diagnosis isolation takes effect.
Server restart in this section refers to power cycle triggered by clicking the Force power-cycle option on the Power Management page.
In minimum configuration startup or diagnosis isolation mode, USB connectors on the server are disabled and HDM is wirelessly inaccessible. Before enabling minimum configuration startup or the diagnosis isolation mode, prepare backup network access as needed.
The diagnosis process takes a long time. To interrupt the process, first disable diagnosis isolation from the Web interface, and then restart the server. To change the diagnosis isolation mode, disable diagnosis isolation from the Web interface, restart the server to exit the current mode, set the new mode, and then restart the server.
Before the diagnosis, the system performs a pre-check on the server. If the server starts up successfully or UEFI SHELL minimum startup fails during the pre-check, the system terminates the diagnosis process.
In minimum configuration startup, devices that do not start up will be isolated by the BIOS and cannot be identified by HDM.
In minimum configuration startup or diagnosis mode, the USB channels and PCIe channels between HDM and the server stay in normal communication state.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Alarm Settings.
3. Click the Diagnosis tab.
The page that opens displays the current minimum configuration startup and diagnosis isolation configurations.
Figure 99 Viewing system diagnosis
4. Click Configure.
5. In the dialog box that opens, enable minimum configuration startup or select the diagnosis isolation mode, as shown in Figure 38.
Figure 100 Configuring system diagnosis
6. Click OK.
7. Restart the server. The configured minimum configuration startup or diagnosis isolation mode will take effect immediately upon the restart.
Parameters
Diagnosis isolation: Select the diagnosis isolation mode. Options include:
· Disable—Disables diagnosis isolation.
· Diagnose only—Examines components for errors that cause the startup failure, and then displays the diagnosis result.
· Diagnose and isolate—Examines components for errors that cause the startup failure, displays the diagnosis result, and then isolates the failed components.
Configuration
Perform this task to import and export HDM, BIOS, or RAID configuration, and restore HDM settings.
Restrictions and guidelines
Export HDM, BIOS, or RAID configuration
Restrictions and guidelines
Make sure the storage controllers have been initialized before you export the RAID configuration.
PMC storage controllers do not support RAID configuration export.
Make sure the logical drives attached to the storage controllers are in normal state and no expansion, migration, rebuilding, or erasing task is being performed before you export the RAID configuration.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Manage Configuration.
3. In the Export configuration section, select the target configuration type from the Select type field.
4. Click Export.
Figure 101 Exporting HDM, BIOS, or RAID configuration
Import HDM, BIOS, or RAID configuration
General restrictions and guidelines
To avoid HDM and operating system anomalies, do not perform any power actions on the server during the import process.
If configuration import fails, troubleshoot the issue that leads to the failure as instructed and then import the configuration again.
To avoid import failure, make sure the other users are not operating the server from HDM before you import configuration.
To avoid import failure, when you modify the configuration file, make sure the configurations are valid.
Make sure you have deleted all the comment statements in the configuration file before the import.
If the password in the configuration to be imported is empty and the configuration is from a different server, you must add the password manually. The new password will take effect after the import.
PMC storage controllers do not support RAID configuration import.
Restrictions and guidelines for importing HDM configuration
Make sure the server model in the configuration file to import is consistent with the actual server model.
Make sure the bonding mode setting in the configuration file to import is consistent with the bonding mode setting on the target server.
The import operation does not affect HDM configurations that are not covered by the configuration file to import.
If the imported HDM configuration includes network settings, HDM restarts automatically after the import for the configuration to take effect. If the imported HDM configuration does not include network settings, the configuration takes effect immediately after the import.
If the configuration to be imported includes HDM management IP settings, you cannot access HDM by using the current management IP address after the import. If a static IP address is imported, the IP address becomes the management address. If a DHCP-assigned address is imported, the server obtains a new IP address from the DHCP server and uses the address as the management address, and the address obtaining method changes to DHCP.
Restrictions and guidelines for importing BIOS configuration
Make sure the server model and hardware configuration (for example, storage controller and drive configuration) in the configuration file is consistent with the actual configuration.
For the imported BIOS configuration to take effect, restart the server after the import.
Restrictions and guidelines for importing RAID configuration
Make sure the server is powered on and the storage controller is in RAID mode before you import RAID configuration.
Make sure the server model and hardware configuration (for example, storage controller and drive configuration) in the configuration file is consistent with the actual configuration.
To avoid import failure, clear existing RAID configuration from the BIOS before you import RAID configuration.
After a RAID configuration import, it takes about 40 seconds for the imported file to take effect.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Manage Configuration.
3. In the Import configuration section, select HDM from the Select type field.
4. Select the target configuration file, and then click Import.
5. In the confirmation dialog box that opens, click OK.
Figure 102 Importing HDM, BIOS, or RAID configuration
Restore HDM settings
|
CAUTION: · After the HDM settings are restored, you can access HDM only with the default username and password. Please use this function with caution. · Do not refresh the webpage when HDM settings are being restored. If you refresh the page, HDM might fail to be accessed. |
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Manage Configuration.
3. In the Restore HDM settings section, perform one of the following tasks:
¡ To restore HDM to the default settings, click Restore default settings.
¡ To restore HDM to the factory defaults (if any), click Restore factory defaults.
4. In the confirmation dialog box that opens, click OK.
HDM restarts after the settings are restored.
Figure 103 Restoring HDM settings
Update firmware
You can update the firmware of HDM, BIOS, CPLD, power supplies, LCD, REPO, GPUFPGA, FANMCU, or PMem 200. REPO firmware includes storage controller firmware, network adapter firmware, and drive firmware. Table 12 shows server models and the firmware types that they support.
Table 12 Server models and supported firmware types
|
Server model |
Firmware type |
|
· R2900 G3 · R4100 G3 · R4400 G3 · E3200 G3 · B5700 G3 · AE100 |
· HDM · BIOS · CPLD · REPO |
|
R4900 G3 |
· HDM · BIOS · CPLD · BPCPLD · PSU · REPO |
|
· R2700 G3 · R4300 G3 · R4700 G3 · R4950 G3 · B5800 G3 |
· HDM · BIOS · CPLD · BPCPLD · REPO |
|
R5300 G3 |
· HDM · BIOS · CPLD · PSU · GPUCPLD · BPCPLD · REPO |
|
R6700 G3 |
· HDM · BIOS · CPLD · DBCPLD · STBCPLD · LCD · BPCPLD · REPO |
|
R6900 G3 |
· HDM · BIOS · CPLD · PDBCPLD · NDCPLD · BPCPLD · LCD · REPO |
|
R8900 G3 |
· HDM · BIOS · CPLD · BPCPLD · PDBCPLD · NDCPLD · PDBSCPLD · LCD · REPO |
|
B7800 G3 |
· HDM · BIOS · CPLD · AUXCPLD · REPO |
|
R4330 G5 |
· HDM · BIOS · CPLD · BPCPLD · PSU · LCD · PFRCPLD · PMem 200 |
|
· R4700 G5 · R4900 G5 · R4930 G5 · R4950 G5 · R4300 G5 |
· HDM · BIOS · CPLD · BPCPLD · PSU · LCD · PFRCPLD · REPO · PMem 200 |
|
R5300 G5 |
· HDM · BIOS · CPLD · BPCPLD · PSU · PFRCPLD · OCPCPLD · GPUFPGA · REPO · PMem 200 |
|
R5500 G5 |
· HDM · BIOS · CPLD · BPCPLD · PFRCPLD · PSWCPLD · PSU · FANMCU · REPO · PMem 200 |
|
R6900 G5 |
· HDM · BIOS · CPLD · DBCPLD · BPCPLD · PSU · LCD · PFRCPLD · REPO · OCPCPLD · PMem 200 |
|
B5700 G5 |
· HDM · BIOS · CPLD · PFRCPLD · REPO · PMem 200 |
Firmware update restrictions and guidelines
To ensure a successful firmware update, follow these restrictions and guidelines during the update:
· To avoid HDM or operating system errors, do not power on or power off the server during the update.
· Do not refresh the HDM webpage during the update unless you are instructed to do so. Doing so will reset the update process.
Only one user can update firmware at a time. If multiple users attempt to update firmware, only the one who first started the update can perform this operation. When you successfully start a firmware update, HDM automatically disables all other webpages and signs out all the other users. The signed-out users can sign in again only after the update is finished.
Firmware update might fail if the update image file does not contain a vendor signature or is corrupt. In this situation, obtain the desired firmware image file and try again.
For the firmware to be updated successfully, do not perform the following tasks from the Web interface during the update process:
· Change network settings, including dedicated and shared network ports, VLAN, network port mode, network adapter, DNS, and Wi-Fi settings.
· Configure remote services.
· Configure NTP settings.
· Configure user and security settings, including access service, firewall, and SSL.
· Set the server power status or change power capping settings.
· Perform the following remote operation and maintenance tasks:
¡ Perform NMI control.
¡ Import or export configuration.
¡ Restore HDM settings.
¡ Restart HDM.
¡ Perform primary/backup switchover.
¡ Restart CPLD.
If CPLD update fails, the server will become unavailable. If the server cannot be accessed, contact Technical Support.
The following remote console menus are not available during the update:
· Keyboard menu in the KVM console.
· Send Keys and Hot Keys menus in the H5 KVM console.
|
|
NOTE: In HDM-2.96 and later versions, you can scan the QR code on the screen to view the function diagram or give feedback. |
Firmware update workflow
Figure 42 shows the firmware update workflow.
Figure 104 Firmware update workflow
Prerequisites for firmware update
Before a firmware update, perform the following tasks:
1. Obtain the up-to-date server firmware image. Make sure the image matches the firmware type.
2. To avoid configuration loss caused by inadvertent mistakes, back up the configuration. You can export the HDM configuration for backup.
3. Make sure no user is updating firmware. You cannot update firmware if there is an ongoing firmware update.
Update HDM firmware
HDM supports one primary firmware image and one backup firmware image, and it always runs the primary image.
To minimize the impact on HDM services, HDM uses the following procedure to update HDM firmware:
1. When you update HDM firmware, HDM replaces the backup firmware image with the uploaded update image.
2. When you restart HDM or perform a primary/backup switchover, HDM changes the roles of primary and backup HDM images. Then, HDM restarts with the update image, which is now the primary image.
Restrictions and guidelines
If the Restore factory defaults option is selected, you must use the default user account settings at the first sign-in to HDM after its firmware is updated.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
The page as shown in Figure 43 opens.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 44 opens.
Figure 106 Uploading firmware image file
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select HDM as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for file upload and enter the image name. Then, select HDM as the firmware type. The image name must include the suffix and cannot exceed 45 characters in length.
b. Select the HDM restart method after the update is complete. You can have HDM automatically restart when the update is complete or manually restart HDM later.
c. (Optional.) To remove all user-configured settings after you update HDM firmware, enable the Restore factory default option.
d. Click Next.
|
CAUTION: The Restore factory defaults option removes all user configured settings and restore factory defaults when HDM starts up with the new firmware. If the firmware does not have factory defaults, the system restores the default settings of the firmware. When you select this option, make sure you understand its impact on the services. |
5. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page. Verify that the current partition version of image in use, current partition version of image to update, and image file version are correct, and then click Next as shown in Figure 45.
The firmware update starts and the system displays the update progress.
Figure 107 Verifying firmware information
6. Follow the system instructions to complete the update.
7. If you selected manual restart, use one of the following methods to have the new firmware image take effect:.
¡ Restart HDM.
¡ Switch over between primary and backup HDM firmware images.
If you selected automatic restart, HDM restarts automatically.
8. (Optional.) Clear the browser cache, and then re-sign in to HDM.
Clearing the browser cache ensures the correct display of webpage contents after you re-sign in to HDM.
9. Verify the update:
a. On the top navigation bar, click Dashboard.
b. In the left navigation pane, select Summary.
c. In the Device information section of the work pane, verify that the HDM firmware is updated.
Update BIOS firmware
Restrictions and guidelines
To avoid update errors, make sure power supply redundancy is normal before the update.
If the Restore or Forcedly restore option is selected, the boot mode in the BIOS changes to the default (UEFI) after the update.
After an update, the server must restart for the new firmware to take effect. To avoid BIOS errors, do not perform BIOS update again or restart HDM during the restart.
For a server installed with Intel processors, do not perform graceful power-off from HDM to restart the server after you update the BIOS with the Forcedly restore option specified. If you perform graceful power-off, ME exceptions might occur.
To select the Retain or Restore option when updating the BIOS firmware of a server installed with Hygon processors through HDM, do not mount any CD/DVD image file to the server. If the server has been mounted with a CD/DVD image file, unmount the image file before the upgrade or do not unmount the image file during the upgrade. Unmounting the image file during the upgrade might interrupt the channel for transmitting the BIOS file, causing upgrade failure.
mLOM network adapter settings will get lost after a BIOS update because these settings are stored in the BIOS.
All user-configured BIOS settings will get lost if you downgrade the BIOS firmware.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 46 opens.
Figure 108 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select BIOS as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select BIOS as the firmware type. The image name must include the suffix.
b. If the server is up, select the method to reboot the server after the update is complete.
You can have the server automatically reboot immediately or at a scheduled time. Alternatively, you can choose Manual restart to manually reboot the server.
c. Select the firmware to update. Options include BIOS + ME, BIOS, and ME. The default is BIOS + ME. This step is available only for servers installed with Intel processors.
d. Select whether to restore default BIOS settings after the update. This step is unavailable if you specify only the ME as the firmware to update.
- To retain the user-configured BIOS settings, select Retain.
- To remove the user-configured BIOS settings and restore factory defaults, select Restore. If no factory defaults exist, the system restores the default settings.
- To remove the user-configured BIOS settings and restore default settings, select Forcedly restore. This option enables HDM to rewrite the BIOS flash and can be used when BIOS is operating incorrectly and cannot be updated in any other ways.
e. Click Next.
|
CAUTION: The Forcedly restore option restores the factory defaults (if any) or default settings of the BIOS. Before you select this option, make sure the server has entered the OS or has been powered off. Otherwise, BIOS exceptions might occur. When you select this option, make sure you understand its impact on the services. |
5. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page. Verify that the current image version and image file version are correct as shown in Figure 47, and then click Next.
The firmware update starts and the system displays the update progress.
Figure 109 Verifying firmware information
6. Follow the system instructions to complete the update.
7. Power cycle the server.
If the server is up and you selected an automatic restart option, the server will reboot automatically.
8. If the previous boot mode in the BIOS is legacy, access the BIOS menu during startup to change the boot mode to Legacy mode, and then continue with the server startup.
The boot mode in the BIOS automatically restores to the default (UEFI) after each firmware update. This step is required for a successful reboot of the operating system installed in Legacy mode.
9. After the POST phase finishes successfully, re-sign in to HDM to verify the update:
a. On the top navigation bar, click Dashboard
b. In the left navigation pane, select Summary.
c. In the Device information section of the work pane, verify that the BIOS firmware is updated.
Update CPLD firmware
Perform this task to update the following types of CPLD firmware: CPLD, DBCPLD, STBCPLD, AUXCPLD, PDBCPLD, NDCPLD, PDBSCPLD, PFRCPLD, and OCPCPLD.
Restrictions and guidelines
See "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 48 opens.
Figure 110 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select CPLD as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select CPLD as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Verify that the current image version and image file version are correct as shown in Figure 49, and then click Next.
The firmware update starts and the system displays the update progress.
Figure 111 Verifying firmware information
6. Perform the corresponding task based on the device model to have the new CPLD firmware version take effect. For more information, see the firmware update guide for the server.
Update drive backplane firmware
This task applies to R2700 G3, R4300 G3, R4700 G3, R4900 G3, R4950 G3, R5300 G3, R6700 G3, R6900 G3, R8900 G3, B5800 G3, and all G5 servers except the B5700 G5.
Restrictions and guidelines
An update operation updates only drive backplanes supported by the uploaded BPCPLD image file.
To update the firmware after a drive backplane replacement, first power on the server for the newly installed drive backplane to be identified.
If the update fails for a drive backplane, the system will try again. A maximum of three update attempts are allowed for each drive backplane.
You can try to start a new update after the current update fails. If multiple updates fail, contact the technical support to use a different method to update the firmware.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 50 opens.
Figure 112 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select BPCPLD as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select BPCPLD as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Select the drive backplanes to update, verify that the current image version and image file version are correct as shown in Figure 51, and then click Next.
Figure 113 Verifying firmware information
6. If the server is powered on, power off the server. The firmware update starts nine seconds after the server is powered off.
7. After the update finishes, restart HDM to make the new BPCPLD take effect.
Update PCIe switch board firmware
Perform this task to update the firmware of the PCIe switch board.
Restrictions and guidelines
This feature is available only for the R5500 G5 server.
This feature is available only in HDM-2.17 and later.
If the update fails, the system retries. The system allows a maximum of two retries.
You can try to start a new update after the current update fails. If multiple updates fail, contact the technical support to use a different method to update the firmware.
To update the firmware after a PCIe switch board replacement, first power on the server for the newly installed PCIe switch board to be identified.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 52 opens.
Figure 114 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select PSWCPLD as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select PSWCPLD as the firmware type. The image name must include the suffix.
b. Click Next.
5. Verify that the information of the PCIe switch board to update, the current image version, and image file version are correct as shown in Figure 53, and then click Next.
Figure 115 Verifying firmware information
6. If the server is powered on, power off the server. The firmware update starts nine seconds after the server is powered off.
7. After the update finishes, restart the server with the power cords reconnected to make the new firmware take effect.
Update power supply firmware
This task applies only to R4900 G3, R5300 G3, R4400 G3, R4330 G5, R4700 G5, R4900 G5, R4930 G5, R4950 G5, R5300 G5, R5500 G5, and R6900 G5.
Restrictions and guidelines
The system updates the firmware only for power supplies using the same model defined in the image file and updates the power supplies one by one. The power supply that is being updated cannot supply power to the server. Make sure a minimum of one power supply is present and the power supply can provide power to the system board during the update process.
Before the update, make sure the present power supplies are operating correctly.
For the R5500 G5, the system board and GPU modules use different sets of power supplies, which must be updated separately.
Power supply firmware supports the following update methods:
· Immediate update—Start immediately once the new firmware image version is verified.
To avoid power supply errors, do not power on or power off the server or disconnect any power supply during the update.
· Update after server power-off—Start nine seconds after the server is powered off.
To avoid power supply errors, do not power on the server or disconnect any power supply during the update.
The firmware update method is determined by the image file. Before the update, contact Technical Support to identify the update method.
The update process might take a long time.
If the update fails for a power supply, the power supply might fail to operate.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 54 opens.
Figure 116 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select PSU as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select PSU as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Verify that the current image version and image file version are correct as shown in Figure 55, and then click Next.
The Present field indicates whether a power supply is present.
Figure 117 Verifying firmware information
6. The server starts the update immediately or after the server is powered off depending on the update method of the new firmware image.
To view the update result for each power supply, access the Operation Log page.
The new firmware takes effect automatically after the update finishes.
Update LCD firmware
Only HDM-2.09 and later versions support updating LCD firmware. This task applies to R6700 G3, R6900 G3, R8900 G3, R4330 G5, R4700 G5, R4900 G5, R4930 G5, R4950 G5, and R6900 G5.
Restrictions and guidelines
If the update fails, the LCD might fail to operate. In this case, try to update LCD firmware again.
The update process might take a long time, and the LCD is not available during the update.
The LCD automatically restarts to have the new firmware take effect after the update finishes.
You can upload an LCD firmware image and update the LCD firmware only after an LCD is connected to the server.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 56 opens.
Figure 118 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select LCD as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select LCD as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Verify that the current image version and image file version are correct as shown in Figure 57, and then click Next.
The firmware update starts and the system displays the update progress.
Figure 119 Verifying firmware information
Update GPUCPLD firmware
Perform this task to update the CPLD firmware for GPUs.
Restrictions and guidelines
This feature is available only for the R5300 G3 server.
This feature is available only in HDM-2.16 and later.
This feature is available only for specific GPUs. If multiple GPUs are present, the operation updates only GPUs supported by the uploaded GPUCPLD image.
If the update fails for a GPU, the system retries. The system allows a maximum of two retries.
The BIOS will restart multiple times during the update process.
This feature is available only when the server is powered on. During the update process, do not power off or remove power from the server. If you do so, the update might fail or GPUs might fail to be identified.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 58 opens.
Figure 120 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select GPUCPLD as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select GPUCPLD as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Select the target GPUs, verify that the GPU information, current image version, and image file version are correct, and then click Next.
Figure 121 Verifying firmware information
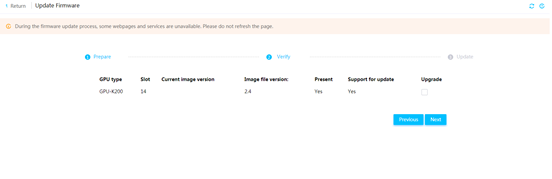
6. After the update, for the new firmware to take effect, power cycle the server with the power cords reconnected.
Update GPUFPGA firmware
Perform this task to update the Field Programmable Gate Array (FPGA) firmware for GPUs.
Restrictions and guidelines
This feature is available only in HDM-2.25 and later.
This feature is available only for the R5300 G5 servers installed with the Redstone GPU module.
This feature is available only for specific GPUs. If multiple GPUs are present, the operation updates only GPUs supported by the uploaded GPUFPGA image.
This feature is available only when the server is powered on. During the update process, do not power off or remove power from the server. If you do so, the update might fail or GPUs might fail to be identified.
If the update fails for a GPU, the system retries. The system allows a maximum of two retries.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 60 opens.
Figure 122 Uploading firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select GPUFPGA as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select GPUFPGA as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
5. Select the target GPUs, verify that the GPU information, current image version, and image file version are correct, and then click Next.
Figure 123 Verifying firmware information
6. After the update, for the new firmware to take effect, power cycle the server.
Update FANMCU firmware
Perform this task to update the micro control unit (MCU) firmware of fans.
Restrictions and guidelines
This task is supported only in HDM-2.42 and later.
This task is supported only by the R5500 G5 server.
An update operation updates only fans supported by the uploaded FANMCU image file.
You can update FANMCU firmware only when the server is powered on. To avoid update failure or fan identification failure, do not power off the server or disconnect power cords from the server during the update.
During the update, the fans rotate at the maximum speed. The fan speed can be adjusted during the update, but the adjustment takes effect only after the update.
If the update fails for a fan, the system retries. A maximum of two automatic retries are allowed for a user-triggered FANMCU firmware update.
If the update fails, the MCUs cannot operate correctly and the fans rotate at the maximum speed. You can try again for MCUs to operate correctly.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select FANMCU as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select FANMCU as the firmware type. The image name must include the suffix.
b. Click Next. HDM will verify the signature information of the firmware image file. If the signature information passes the verification, HDM will open the firmware information verification page.
Figure 124 Updating FANMCU firmware
5. Select the fans to update, verify that the current image version and image file version are correct, and then click Next.
Figure 125 Verifying the firmware update configuration
6. The firmware takes effect immediately after the firmware update is complete.
Update the REPO for firmware update
Perform this task to update the REPO for the firmware update of server components, including storage controllers, network adapters, and drives in an out-of-band manner.
Restrictions and guidelines
This task is supported only in HDM-2.52, iFIST-1.32, and later.
If the server does not support iFIST, you cannot upload the REPO for firmware update in the HDM.
For the new firmware to take effect after REPO update, iFIST of the server is required. Make sure the iFIST version is compatible with the current HDM version. For information about the compatibility between HDM and iFIST, see HDM release notes or iFIST release notes.
At the first restart after REPO update from HDM, the server will automatically enter iFIST to make the new firmware of server components take effect. During the process for the new firmware to take effect in iFIST, do not restart the server or reconnect its power cords. After the new firmware takes effect, the server automatically restarts again with boot options configured before the update.
Make sure the REPO image file to be uploaded does not exceed 300 MB, and the MD5 file does not exceed 1024 bytes.
When you download the REPO image file, the MD5 file and REPO image file will be downloaded in a package.
As a best practice, configure HDM to use the Local image upload method to upload the REPO firmware image.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
For information about how to download and use the REPO image file, see the REPO user guide for the server.
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select REPO as the firmware type. Browse to the update image file and select it. Then, browse to upload the MD5 file for the REPO as needed. HDM will use the MD5 file to check the integrity of the REPO.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name, which must include the suffix. Select REPO as the firmware type. Then, enter the name of the MD5 file for the REPO as needed, which must include the suffix. HDM will use the MD5 file to check the integrity of the REPO.
b. Select the method to reboot the server after the update is complete.
You can have the server automatically restart immediately. Alternatively, you can choose Restart the Server Manually to manually restart the server.
c. Select the components to update in the Update Options field.
- To update only the components of lower versions than the version to be updated, select Update Only Components of Lower Versions.
- To update all the components to the version to be updated, select Forcedly Update.
d. Click Next.
Figure 126 Updating the REPO for firmware update
5. Verify that the firmware update configuration is correct, and then click Next.
The firmware update starts and the system displays the update progress.
Figure 127 Verifying the firmware update configuration
6. If you selected automatic restart, the server automatically restarts and enters iFIST after the update to make the new firmware take effect.
If you selected manual restart, manually restart the server. The server automatically enters iFIST to make the new firmware take effect.
7. Access the Operation Log page from HDM to view the firmware update result.
Update PMem 200 firmware
Perform this task to update the firmware for PMem 200 DIMMs.
Restrictions and guidelines
This feature is available only in HDM-2.96 and later.
This feature is available only for G5 servers.
For the firmware to be updated successfully, if PMem 200 DIMMs are disabled, make sure the DIMMs are working correctly before performing the update operation in HDM.
This feature is available only when the BIOS boot mode is UEFI.
For more restrictions and guidelines, see "Firmware update restrictions and guidelines."
Prerequisites
See "Prerequisites for firmware update."
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
3. In the Update Firmware section, click Update Firmware.
The firmware image file upload page as shown in Figure 128 opens.
Figure 128 Updating firmware image
4. In the work pane, perform the following tasks:
a. Select an image upload method.
- If you select Local, select PMem 200 as the firmware type. Then, browse to the update image file and select it.
- If you select TFTP, enter the IP address of the interface used for image upload and enter the image name. Then, select PMem 200 as the firmware type. The image name must include the suffix.
b. Select the method to reboot the server after the update is complete.
You can have the server automatically restart immediately. Alternatively, you can choose Restart the Server Manually to manually restart the server.
5. Verify that the current firmware type and image file version are correct, and then click Next.
The system starts to update the firmware.
Figure 129 Verifying firmware information
6. If you selected manual restart, manually restart the server. The server automatically enters iFIST to make the new firmware take effect.
If you selected automatic restart, the server automatically restarts and enters iFIST after the update to make the new firmware take effect.
Restart HDM
You can restart HDM to have the new firmware image take effect after a firmware update or when HDM is malfunctioning.
When HDM restarts, all HDM user sessions are closed. These sessions will be automatically re-established after HDM starts up.
HDM restart does not remove the HDM configuration.
Restrictions and guidelines
Do not power on, power off, or power cycle the server during an HDM restart operation. Doing so might cause malfunctioning of some HDM features or operating system errors.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
The page as shown in Figure 43 opens.
3. In the Restart Firmware section, click Restart HDM, and then click OK to confirm the operation.
Restart CPLD
You can restart CPLD to have the new CPLD or PFRCPLD firmware image take effect after a firmware update.
Restarting CPLD is supported by R2700 G3, R2900 G3, R4400 G3, R4700 G3, R4900 G3, R5300 G3, and all G5 servers except the B5700 G5.
Restrictions and guidelines
You can restart CPLD only when the server is powered off.
Restarting CPLD will cause HDM to restart immediately.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
The page as shown in Figure 43 opens.
3. In the Restart Firmware section, click Restart CPLD and then click OK to confirm the operation.
Switch over between primary and backup HDM firmware images
HDM supports one primary firmware image and one backup firmware image, which are stored in different storage areas. When the primary firmware image is corrupt, you can perform an image switchover to have the backup firmware image take over the primary role.
Restrictions and guidelines
Do not power on, power off, or power cycle the server during an HDM restart operation. Doing so might cause malfunctioning of some HDM features or operating system errors.
After updating the primary HDM firmware image, perform a primary/backup switchover, and then update firmware again for version consistency between the primary and backup HDM firmware images.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Update Firmware.
The page as shown in Figure 43 opens.
3. In the Primary/backup switchover section, check the primary and backup firmware image versions, and then click Switchover.
HDM automatically restarts with the original backup image, which is now the primary image.
POST codes
The system generates power-on self-test (POST) codes to record its state in each phase of server startup. For more information about POST codes, contact Technical Support.
View POST codes
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select POST Codes.
3. In the work pane as show in Figure 68, view the system POST codes.
Parameters
· POST code of current phase—POST code for the current startup phase of the system.
· POST results—All POST codes generated during the current or the most recent startup of the system.
Manage the intelligent security bezel
Perform this task to identify the presence status of the intelligent security bezel and configure security bezel settings.
Restrictions and guidelines
This feature is available only for G5 servers except the R5300 G5, R5500 G5, and B5700 G5.
This feature is available only in HDM-2.13 and later.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Security Bezel Control.
The security bezel control settings page opens, as shown in Figure 69.
3. Identify whether the intelligent security bezel is present.
¡ If you set the decorative LED mode to Server status sync, the flashing mode and color of the decorative LEDs change as the server operation status changes.
¡ If you set the decorative LED mode to Custom, you can set the flashing mode and color of the decorative LEDs.
4. Click Save.
Figure 131 Security bezel control settings
Parameters
· Decorative LEDs: Includes the following options: Bright, Soft, and Off. If you enable the decorative LEDs, select Soft as a best practice to decrease power consumption.
· Health status sync: Enables the decorative LEDs to flash based on the server health status. To use this feature, make sure the Server status sync option is selected. For more information, see the user guide for the server.
Manage service USB devices
A service USB device is a USB device burned with the image file of the USB diagnostic tool. You can connect such a device to a server to download SDS logs automatically and manage the service USB device from HDM as needed.
Restrictions and guidelines
This feature is available only for G5 servers except the B5700 G5.
This feature is available only in HDM-2.25 and later.
If a user is downloading SDS logs at the time you connect a service USB device, the system ejects the service USB device. You can wait for the ongoing downloading process to end and then reconnect the service USB device.
Before connecting a service USB device, make sure the available space on the device is greater than 500 MB.
To avoid USB exceptions, do not forcibly remove an operating service USB device.
To avoid USB exceptions, do not connect or remove a service USB device frequently.
If you connect multiple service USB devices to a server, the server can identify only the first-connected one.
Procedure
1. On the top navigation bar, click Remote O&M.
2. In the left navigation pane, select Service USB Device.
The page that opens displays the status of the service USB device.
3. Select whether to enable the service USB device.
4. Select whether to enable auto SDS log downloading.
5. Click Save.
6. If the service USB device is operating, wait for the operation to end and then reconnect the service USB device for the settings to take effect.
Figure 132 Managing USB devices
Parameters
· Status: Status of the service USB device. Options include Present, Absent, and Operating.
· Auto SDS log downloading: With this feature enabled, the service USB device automatically downloads SDS logs to its Sds_And_SmartTest/ServiceUdisk directory when you connect the device to a server.
Users & Security
User accounts
Configure user accounts, including local users, LDAP users, and AD groups, to control access to HDM. You can also enable 2FA authentication to authenticate HDM users through static and dynamic passwords.
View local user information
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. In the work pane, view information about HDM users in the user list.
Figure 133 Viewing local user information
Parameters
· User ID: ID of the user.
· Username: Name of the user.
· Access to HDM: Whether the user can access the HDM Web interface.
· User role: Role of the user, which determines the network access privileges of the user.
¡ Administrator—The user has read and write permissions to all features.
¡ Operator—The user has read permission to all features and has write permission to some features.
¡ User—The user has read-only permission.
¡ CustomRoleN—The user has the privileges specified for the custom role by an administrator user. The system supports a maximum of five custom user roles.
¡ None—The user does not have network access permissions. This role is for special use. Do not assign the role to any users.
· Email: Email address at which the user is contacted.
Configure the password policy for local users
Perform this task to enhance HDM access security by setting rules that the passwords of user accounts must follow.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. In the work pane, click Advanced Settings.
4. In the dialog box that opens, configure the password policy, and then click OK.
Figure 134 Configuring the password policy
Parameters
· Complexity check: Disable or enable password complexity check.
¡ If this feature is disabled, passwords must meet the following basic complexity requirements:
- 2 to 20 characters in length.
- Case sensitive. Valid characters are letters, digits, spaces, and the following special characters: ` ~ ! @ # $ % ^ & * ( ) _ + - = [ ] \ { } | ; ' : " , . / < > ?
¡ If this feature is enabled, passwords must meet the following enhanced complexity requirements:
- 8 to 20 characters in length.
- Case sensitive. Valid characters are the same as those supported when complexity check is disabled.
- Must contain characters from at least two of the following categories: uppercase letters, lowercase letters, and digits.
- Must contain at least one space or special character.
- Must not be identical to the username or the reverse of the username.
- Must meet the old password reuse requirement.
· Maximum password age: Maximum number of days that a password can be used. When a password is about to expire, HDM prompts the user to change the password. The password of the default administrator will not expire.
· Password history count: Number of unique passwords that a user must create before an old password can be reused.
· Account lockout threshold: Number of consecutive login failures that will cause a user account to be locked.
· Account lockout duration: Amount of time before a locked account can be used again.
Configure privileges for custom users
Perform this task to configure privileges for custom users and change the names of custom user roles.
Hardware and software version compatibility
This task is supported only in HDM-2.03 and later.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. To edit the names of custom user roles,
click the ![]() icon in the User roles field of the table header.
icon in the User roles field of the table header.
4. In the Custom privileges section, select access privileges for custom users CustomRole1 to CustomRole5 as needed as shown in Figure 73.
5. Click Save.
Figure 135 Configuring privileges for custom users
Parameters
· User roles: User role that represents a set of network and service access privileges.
· CustomRoleN: Name of the custom user role. The system supports a maximum of five custom user roles. By default, a custom user role has only the information query privilege. You can edit a custom user role name as needed. A name is a case-sensitive string of 1 to 16 characters, and supports only letters, digits, dots (.), hyphens (-), underscores (_), and at signs (@).
· User accounts: Specify the privilege to manage local users, LDAP users, and AD groups, configure two-factor authentication, import and export configurations, and perform unified control.
· Basic configuration: Specify the privilege to manage asset tags, network configuration, NTP configuration, SNMP configuration, and alarm settings (SMTP settings, SNMP trap settings, syslog settings, and emergence diagnosis), event log, operation log, video replay, and intelligent security bezel.
· Security: Specify the privilege to configure access services, firewall, SSL certificate, PFR, and security tip for login settings.
· Remote control: Specify the privilege to manage storage configuration (RAID configuration and physical drive management), system resource monitoring, hard partitioning configuration, KVM, H5 KVM, password settings for VNC client login, system boot options, UID LED, SOL connection mode, and MCA policy. The privilege for power control and mounting media images are not included.
· Remote media: Specify the privilege to configure virtual media configuration, media mounting from the KVM console, and media mounting from the H5 KVM console.
· Power control: Specify the privilege to manage power configuration, physical power supply button control, NMI control, and fan settings.
· Maintenance: Specify the privilege to manage the drive UID LED, BSoD screenshots, video replay, firmware update, HDM settings restoration, HDM primary/backup switchover, HDM restart, CPLD restart, and service USB device settings.
· Information query: Specify the information viewing privilege for a user. For an administrator user, this privilege allows the user to view information about all users. For a non-administrator user, this privilege allows the user to view its own information.
· Password modification: Specify the privilege to modify the local user's own password and SSH key.
Manage local user accounts
Restrictions and guidelines
You cannot modify the username of a user in a session or delete such a user.
You cannot delete a user in a session.
Prerequisites
Make sure you signed in with the administrator role.
Add a user account
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click Add.
4. In the dialog box that opens, configure the user parameters.
Figure 136 Adding a user account
5. Click OK.
Edit a user account
You cannot edit the username of a user with sessions.
To edit a user account:
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click Edit in the user account entry.
4. In the dialog box that opens, configure the user parameters.
Figure 137 Editing a user account
5. Click OK.
Delete a user account
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click Delete in the user account entry.
4. In the dialog box that opens, click OK.
Parameters
· User ID: ID of the user.
· Username: Specify a username for the user account. The username is a case-sensitive string of 1 to 16 characters. Valid characters are letters, digits, dots (.), hyphens (-), underscores (_), and at signs (@).
· Password: Specify a password for the user account, which must comply with the password policy described in "Configure the password policy for local users."
· Confirm: Enter the password again for confirmation.
· Access to HDM: Select Enable to enable the user to access HDM through the Web or IPMI interface. If you do not enable user access, the user cannot access HDM through the Web or IPMI interface.
· User role: Select a user role, which represents a set of network and service access privileges. Available user roles include:
¡ Administrator—The user has read and write permissions to all features.
¡ Operator—The user has read permission to all features and has write permission to some features.
¡ User—The user has read-only permission.
¡ CustomRoleN—The user has the privileges specified for the custom role by an administrator user. The system supports a maximum of five custom user roles.
¡ None—The user does not have network access permissions. This role is for special use. Do not assign the role to any users.
· Available interfaces: Select the Web and IPMI access privileges for the user as needed.
Web and IPMI access are authorized to administrators and operators by default and cannot be revoked.
· SNMP extended privileges: Select whether to grant the user with SNMP extended privileges. To grant the privileges, you must enable user access to HDM and the user password must contain a minimum of eight characters. If you select SNMP extended privileges, select a privilege from the SNMP v3 R/W permission field. Options include:
¡ Read: The user has read-only permission. This enables the user to perform GET operations and receive traps.
¡ Read/Write: The user has read-and-write permission. This enables the user to perform GET and SET operations and receive traps.
· SNMP v3 authProtocol: Select the SNMP v3 authentication protocol. Options include SHA and MD5. The default protocol is SHA.
· SNMP v3 privProtocol: Select the SNMP v3 privacy protocol. Options include DES and AES. The default protocol is DES.
· Email address: Enter the email address at which the user is contacted. The address cannot exceed 63 characters. You can use the address to retrieve the password for the user account. To send alert emails to a user, you must specify an email address in the user account for that user. Alert emails are configurable from the Alarm Settings menu.
· SSH key: Upload an SSH key for the user to access the HDM CLI. At access attempts, the user must also enter the password for the key if a password was specified during key generation on the HDM CLI client. If no password was specified, the user can directly log in to the HDM CLI.
In the current software version, RSA, ECDSA, and ED25519 keys are supported. The length of an SSH key varies by key format.
¡ For RSA SSH keys, the length can be 1024, 2048, or 4096 bytes.
¡ For ECDSA SSH keys, the length can be 256, 384, or 521 bytes.
¡ For ED25519 SSH keys, the length can only be 256 bytes.
User roles and privileges matrix
The supported features or feature menus vary by server model.
The following information describes the privileges that a user role has. A feature or feature menu is inaccessible if your user role does not have the privileges to use that feature or feature menu.
|
Menu/Feature |
Administrator |
Operator |
User |
|
User accounts |
|||
|
Configure a local user account |
√ |
× |
× |
|
Configure LDAP settings |
√ |
× |
× |
|
Configure AD settings |
√ |
× |
× |
|
Configure two-factor authentication |
√ |
× |
× |
|
Import and export configurations |
√ |
× |
× |
|
Perform unified control |
√ |
× |
× |
|
Basic configuration |
|||
|
Set asset tags |
√ |
√ |
× |
|
Configure the HDM dedicated network port |
√ |
√ |
× |
|
Specify the HDM shared network port |
√ |
√ |
× |
|
Configure DNS settings |
√ |
√ |
× |
|
Configure network port mode settings |
√ |
√ |
× |
|
Configure LLDP |
√ |
√ |
× |
|
Configure Wi-Fi settings |
√ |
√ |
× |
|
Configure NTP servers |
√ |
√ |
× |
|
Configure SNMP settings |
√ |
√ |
× |
|
Manage alert emails |
√ |
√ |
× |
|
Configure SNMP trap settings |
√ |
√ |
× |
|
Configure syslog settings |
√ |
√ |
× |
|
Manage event log (configure the event log policy, save event log, and delete event log entries) |
√ |
√ |
× |
|
Save operation log in CSV format or delete operation log entries |
√ |
√ |
× |
|
Configure advanced settings for video replay (download and play videos) |
√ |
√ |
× |
|
Configure the intelligent security bezel |
√ |
√ |
× |
|
Security |
|||
|
Configure services |
√ |
√ |
× |
|
Configure the firewall |
√ |
√ |
× |
|
Configure SSL |
√ |
√ |
× |
|
PFR |
√ |
√ |
× |
|
Security tip for login |
√ |
√ |
× |
|
Remote console |
|||
|
Manage storage configuration (RAID configuration and physical drive management) |
√ |
√ |
× |
|
Configure the alarm thresholds for system resource monitoring |
√ |
√ |
× |
|
Hard partitioning configuration |
√ |
√ |
× |
|
Use KVM remote console (except power control and media mounting) |
√ |
√ |
× |
|
Use H5 KVM remote console (except power control and media mounting) |
√ |
√ |
× |
|
Configure password settings for VNC client login |
√ |
√ |
× |
|
Configure boot options |
√ |
√ |
× |
|
Switch SOL connection mode |
√ |
√ |
× |
|
Set the UID LED |
√ |
√ |
× |
|
Set the MCA policy |
√ |
√ |
× |
|
Remote media |
|||
|
Configure virtual media settings |
√ |
√ |
× |
|
Mount media images from KVM |
√ |
√ |
× |
|
Mount media images from H5 KVM |
√ |
√ |
× |
|
Power control |
|||
|
Power on or power off the server |
√ |
√ |
× |
|
NMI control |
√ |
√ |
× |
|
Meter power (operating mode and power-on policy) |
√ |
√ |
× |
|
Physical power button control |
√ |
√ |
× |
|
Configure global power settings (alarm threshold for the global power consumption and power capping) |
√ |
√ |
× |
|
Configure fan settings |
√ |
√ |
× |
|
Configure processor power states |
√ |
√ |
× |
|
Maintenance |
|||
|
Set the drive UID LED |
√ |
× |
× |
|
Restart collection of CUPS statistics |
√ |
× |
× |
|
Manage event log (configure the event log policy, save event log, and delete event log entries) |
√ |
× |
× |
|
Save operation log in CSV format |
√ |
× |
× |
|
Configure advanced settings for video replay (download and play videos) |
√ |
× |
× |
|
Update firmware |
√ |
× |
× |
|
Restore HDM settings |
√ |
× |
× |
|
Restart HDM |
√ |
× |
× |
|
Change between the primary and backup HDM images |
√ |
× |
× |
|
Restart CPLD |
√ |
× |
× |
|
Manage service USB device settings |
√ |
× |
× |
|
Information query |
|||
|
View basic server information |
√ |
√ |
√ |
|
View basic server status information |
√ |
√ |
√ |
|
View server health state |
√ |
√ |
√ |
|
View HDM user sessions |
√ |
√ |
√ |
|
View storage information |
√ |
√ |
√ |
|
View system information |
√ |
√ |
√ |
|
View temperature heatmaps |
√ |
√ |
√ |
|
View fan configuration |
√ |
√ |
√ |
|
Display system boot options |
√ |
√ |
√ |
|
View system resource monitoring statistics |
√ |
√ |
√ |
|
Download and view the log |
√ |
√ |
√ |
|
View event log |
√ |
√ |
√ |
|
View operation log |
√ |
√ |
√ |
|
View BSoD screenshots |
√ |
√ |
√ |
|
Play videos |
√ |
√ |
√ |
|
View information about the HDM dedicated network port |
√ |
√ |
√ |
|
View information about the HDM shared network port |
√ |
√ |
√ |
|
View DNS settings |
√ |
√ |
√ |
|
View network port mode settings |
√ |
√ |
√ |
|
View LLDP information |
√ |
√ |
√ |
|
View WLAN management information |
√ |
√ |
√ |
|
View information about the current local user |
√ |
√ |
√ |
|
View information about the other local users |
√ |
× |
× |
|
View NTP servers |
√ |
√ |
√ |
|
View LDAP settings |
√ |
√ |
√ |
|
View AD settings |
√ |
√ |
√ |
|
View SNMP settings |
√ |
√ |
√ |
|
View alarm settings |
√ |
√ |
√ |
|
View service information |
√ |
√ |
√ |
|
View firewall settings |
√ |
√ |
√ |
|
View PFR settings |
√ |
√ |
√ |
|
View the SSL certificate |
√ |
√ |
√ |
|
View UID LED status |
√ |
√ |
√ |
|
View system boot options |
√ |
√ |
√ |
|
View SOL connection mode information |
√ |
√ |
√ |
|
View virtual media information |
√ |
√ |
√ |
|
View intelligent security bezel settings |
√ |
√ |
√ |
|
View service USB device settings |
√ |
√ |
√ |
|
View the security tip for login |
√ |
√ |
√ |
|
Display power status |
√ |
√ |
√ |
|
View two-factor authentication settings |
√ |
√ |
√ |
|
View the security module status |
√ |
√ |
√ |
|
View power information |
√ |
√ |
√ |
|
Display power configuration (operating mode and power-on policy) |
√ |
√ |
√ |
|
Display global power settings (alarm threshold for the global power consumption and power capping) |
√ |
√ |
√ |
|
View history power consumption statistics |
√ |
√ |
√ |
|
View POST codes |
√ |
√ |
√ |
|
View fan configuration |
√ |
√ |
√ |
|
View processor power states |
√ |
√ |
√ |
|
View unified control information |
√ |
√ |
√ |
|
Toggle between languages |
√ |
√ |
√ |
|
Access online help |
√ |
√ |
√ |
|
Refresh a page |
√ |
√ |
√ |
|
View most recent event notifications |
√ |
√ |
√ |
|
Sign out HDM |
√ |
√ |
√ |
|
Password modification |
|||
|
Modify the current user's password and SSH key (for local users only) |
√ |
√ |
√ |
Configure LDAP settings
Lightweight Directory Access Protocol (LDAP) enables you to efficiently access and maintain distributed directory information services over an IP network.
You can enable LDAP authentication and access to HDM with the user accounts in LDAP role groups on the LDAP server.
Prerequisites
Before configuring LDAP settings, make sure an LDAP server is available. For more information, see "Set up an LDAP server."
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
Figure 138 Domain Users tab
4. In the LDAP Settings section, click Settings.
5. In the dialog box that opens, enable LDAP authentication, and then configure the LDAP parameters.
Figure 139 Configuring LDAP parameters
6. Click OK.
Parameters
· Encryption type: Select the encryption type.
¡ No encryption—Establishes an unencrypted connection with the LDAP server.
¡ SSL—Establishes an SSL encrypted connection with the LDAP server.
· Common name type: IP address or domain name.
· Server address: IPv4 address, IPv6 address, or domain name of the LDAP server.
· Port number: LDAP service port number, in the range of 1 to 65535. For an SSL connection, the port number is 636 by default. For the remaining types of connections, the port number is 389 by default. Make sure the port number is unique among all services.
· Bind DN: DN information of the LDAP user that is bound to the LDAP server and HDM. The maximum length is 255 bytes. The DN information includes the following comma-separated items:
¡ CN—User login name.
¡ UID—User ID.
¡ OU—Organizational units in ascending order of levels.
¡ DC—Name of the domain to which the user belongs.
· Password: Directory password of the LDAP user.
· Search base: Search base (directory) of the LDAP user in the bind DN on the LDAP server. The maximum length is 255 bytes.
· User identification method: User identification method used by the LDAP server. Supported methods are CN and UID. The user identification method must be consistent with LDAP user information in the bind DN.
Manage LDAP role groups
Add a role group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the LDAP Settings section, click Add role groups.
5. Configure the role group parameters.
Figure 140 Adding a role group
6. Click OK.
Edit a role group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the LDAP Settings section, click the Edit link in the role group entry that you want to modify.
5. Modify the parameters.
Figure 141 Editing a role group
6. Click OK.
Delete a role group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the LDAP Settings section, click Delete in the role group entry that you want to delete.
Parameters
· Role group ID: ID of the role group.
· Role group name: Name of an existing role group on the LDAP server.
· Role group domain: Search base (directory) of the role group on the LDAP server. The maximum length is 255 bytes.
· Role group privileges: Network privileges of the group.
Configure AD authentication
Perform this task to enable users to access HDM by using the username and password of user accounts in a valid Active Directory (AD) group configured on the AD server.
Prerequisites
Before configuring AD settings, make sure an AD server is available.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the Active Directory section, click Settings.
5. Select Enable or Disable for AD authentication. If you select Enable, configure AD authentication parameters as needed.
Figure 142 Configuring AD authentication parameters
6. Click OK.
Parameters
· Secret username: Enter the username used for logging in to the AD servers, a string of up to 64 characters. The username can contain only digits, letters, or both and must start with a letter. The username is optional.
· Secret password: Enter the password used for logging in to the AD servers, a string of 6 to 96 characters. The password is optional.
· User domain name: Enter the user domain name.
· Domain controller address: Enter the IP address or domain name of an AD server. Domain controller address 1 is required.
Manage AD groups
Perform this task to add, edit, or delete AD groups.
Add an AD group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the Active Directory section, click Add role groups.
5. In the dialog box that opens, configure AD group parameters.
Figure 143 Adding an AD group
6. Click OK.
Edit an AD group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the Active Directory section, click Edit for the target AD group from the AD group list.
5. In the dialog box that opens, edit AD group parameters.
Figure 144 Editing an AD group
6. Click OK.
Delete an AD group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the Active Directory section, click Delete for the target AD group from the AD group list.
Parameters
· Role group ID: ID of the AD group.
· Group name: Name of an existing group on the AD server, a string of 1 to 64 characters. Only digits, letters, underscores (_), and hyphens (-) are allowed.
· Group domain: Name of the domain to which the group belongs, a string of 1 to 255 characters. Only digits, letters, underscores (_), hyphens (-), and dots (.) are allowed.
· Group privileges: Network privileges of the group.
Configure two-factor authentication
Two-factor authentication requires a static password and a dynamic password for each login attempt to provide enhanced network security.
HDM supports DKEY token and can collaborate with a one-time password (OTP) server to provide two-factor authentication for user login. With this feature configured, a user must enter the correct username, static password, and dynamic password obtained from a mobile phone or hardware token to log in to HDM.
Restrictions and guidelines
|
CAUTION: Use this feature with caution. Enabling two-factor authentication might affect HDM login. |
This feature is not available for the blade servers or AE modules.
This feature is available only in HDM-2.25 and later.
Before enabling two-factor authentication, make sure an OTP server is available and the related settings have been configured on the OTP server. Required settings include HDM management IP address, HDM user accounts (local users and domain users), authentication policy, and tokens.
HDM does not lock a user if the number of user login failures caused by incorrect dynamic passwords reaches the account lockout threshold.
Enabling two-factor authentication affects server management as follows:
· You cannot manage the current server through the HDM management address by using management software or features that do not support two-factor authentication, for example, FIST, HDM Mobile, and HDM unified control of other servers.
· Existing sessions might be terminated and new sessions might fail to be established, as shown in Table 13. However, the configuration of these interfaces is not modified. After you disable two-factor authentication, these interfaces restore to the status before two-factor authentication was enabled.
Table 13 Session consistency and establishment
|
Interface |
Disconnect existing sessions or connections |
Block new sessions or connections |
|
Web |
No |
No |
|
SSH |
No |
Yes |
|
Telnet |
No |
No |
|
VNC |
Yes |
Yes |
|
Redfish |
No |
Yes |
|
IPMI |
Yes |
Yes |
|
SNMPv3 |
No |
Yes |
|
SOL |
Yes |
Yes |
Procedure
1. On the top navigation bar, click Users & Security.
2. In the navigation pane, select User Accounts.
3. Click the Two-Factor Authentication tab.
4. Configure two-factor authentication:
a. Enable Two-factor authentication.
b. Enter the OTP server address, service port, and shared key.
Figure 145 Configuring two-factor authentication
5. Click Save.
Parameters
· OTP server address: Enter the IPv4 or domain address of the OTP server.
· Service port: Enter the service port number of the OTP server. The default is 1812.
· Shared key: Enter the shared key configured when you add the HDM management IP address to the OTP server. The shared key is a case-sensitive string of 1 to 64 characters. Only letters, digits, and special characters `~!@$%^&*()_+-=[]\{}|;':",./? are allowed.
Security
Configure firewall
The firewall protects HDM from attacks based on firewall rules that identify accesses to be permitted or blocked.
If HDM cannot be accessed due to improper firewall settings, you can restore the HDM default settings from the BIOS to clear the firewall rules. For more information, see the BIOS user guide for the server.
Types of firewall rules and their priority order
You can create the following firewall rules:
· Blacklist rules—Block accesses to the HDM server from specific IP addresses or MAC addresses. You can configure a blacklist rule to take effect in the specified time range.
· Whitelist rules—Permit accesses to the HDM server from specific IP addresses of MAC addresses. You can configure a whitelist rule to take effect in the specified time range.
The blacklist rules take precedence over the whitelist rules.
Manage blacklist rules
Use blacklist rules to block accesses from the specified IP addresses and MAC addresses.
Restrictions and guidelines
· You must specify an IP address/IP range, a MAC address, or both for a blacklist rule.
· The time range settings take effect based on the system time in the HDM server and use the same time zone as HDM. To identify the current time in the HDM server, navigate to Dashboard > Summary.
· If you create multiple blacklist rules with the same content, the system displays only one of them.
Add a blacklist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Blacklist rules section, click Add New Rules.
Figure 146 Adding a blacklist rule
4. In the dialog box that opens, enter an IP address/IP range, a MAC address, or both, and set the time range during which the rule takes effect. By default, no validity period is set and the rule is valid permanently.
Figure 147 Configuring blacklist rule parameters
5. Click OK.
Delete a blacklist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Blacklist rules section, click Delete for the target rule.
4. In the dialog box that opens, click OK.
Edit a blacklist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Blacklist rules section, click Edit for the target rule.
4. In the dialog box that opens, edit the rule as needed.
Figure 148 Editing a blacklist rule
5. Click OK.
Manage whitelist rules
Use whitelist rules to permit accesses from the specified IP addresses and MAC addresses.
Restrictions and guidelines
· First add the IP address and MAC address of the local device to the whitelist before adding any other whitelist rules. If you do not do so, HDM cannot be accessed from the local device.
· If whitelist rules exist, only devices whose addresses have been added to the whitelist can access HDM.
· When you delete a whitelist rule, make sure you fully understand the impact of the operation.
· You must specify an IP address/IP range, a MAC address, or both for a whitelist rule.
· The time range settings take effect based on the system time in the HDM server and use the same time zone as HDM.
· If you create multiple whitelist rules with the same content, the system displays only one of them.
Add a whitelist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Whitelist rules section, click Add New Rules.
4. In the dialog box that opens, enter an IP address/IP range, a MAC address, or both, and set the time range during which the rule takes effect. By default, no validity period is set and the rule is valid permanently.
Figure 149 Adding a whitelist rule
5. Click OK.
Delete a whitelist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Whitelist rules section, click Delete for the target rule.
4. In the dialog box that opens, click OK.
Edit a whitelist rule
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. In the Whitelist rules section, click Edit for the target rule.
4. In the dialog box that opens, edit the rule as needed.
Figure 150 Editing a whitelist rule
5. Click OK.
Manage an SSL certificate
Secure Sockets Layer (SSL) is a protocol for securely transmitting private data over the Internet by using for TCP-based application layer protocols, such as HTTP. It uses keys to encrypt and decrypt data. Using SSL, the Web server and client can have secure data transmission, verify the identity of the data source, and ensure the integrity of the data.
SSL protects HDM accesses from eavesdropping and data tampering and enables HDM users to authenticate the HDM server through SSL certificate authentication.
View SSL certificate
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. Click the SSL Certificate tab.
4. View information about the current SSL certificate.
Figure 151 Viewing SSL certificate
Upload an SSL certificate and key to HDM
Prerequisites
Before you upload an SSL certificate, perform the following tasks:
· Make sure you signed in with the administrator or operator role, or a user account that has the privilege to configure security settings.
· Identify the date and time in HDM on the Dashboard > Summary page, and verify that the HDM system time is in the validity period of the certificate. If the HDM system time is not in the validity period of the certificate, SSL authentication will fail.
· Make sure the certificate file and the private key files are in PEM format.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. Click the SSL Certificate tab.
4. Click Upload SSL.
5. Examine information about the current certificate and private key to decide whether a new set of certificate and private key is needed:
¡ Current certificate uploaded at—Date and time when the current certificate was uploaded.
¡ Current private key uploaded at—Date and time when the current private key was uploaded.
6. Click Browse next to the New certificate field, and then select an SSL certificate file.
7. Click Browse next to the New private key field, and then select a private key file.
8. Click OK.
After the certificate is uploaded, your user session will be disconnected. The HDM server will use the new SSL certificate for authentication during subsequent sign ins.
Figure 152 Uploading an SSL certificate and key
9. If you uploaded an SSL certificate generated by yourself, verify that the corresponding root certificate already exists in the client browser. This section uses IE 11.0 to illustrate how to view and add the root certificate of the certification authority to the browser.
a. Open the IE browser.
b. From the toolbar, click Tools. Then, select Internet options.
c. In the dialog box that opens, click the Content tab and then click Certificates.
d. Click the Trusted Root Certification Authorities tab to view the trusted root certification authorities and root certificate expiration date.
e. If the certification authority is not in the list, click Import to import the root certificate.
Figure 153 Viewing and adding the root certificate
Generate an SSL certificate
Prerequisites
To generate an SSL certificate, you must have the administrator role.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select Security.
3. Click the SSL Certificate tab.
4. Click Generate SSL.
5. Configure the certificate parameters.
Figure 154 Configuring the certificate parameters.
6. Click OK.
7. In the confirmation dialog box that opens, click OK.
If the certificate is generated, you receive a success result message.
The HDM server will use the new SSL certificate for authentication during subsequent sign-ins.
Parameters
· Common name (CN): Full domain name of the HDM server, a string of 1 to 64 characters. Only letters, digits, spaces, underscores (_), hyphens (-), and dots (.) are allowed. The common name cannot be a digits-only string.
· Organization (O): Name of the organization that owns the HDM server, a string of 1 to 64 characters. Only letters, digits, spaces, underscores (_), hyphens (-), dots (.), and commas (,) are allowed. The organization name cannot be a digits-only string.
· Organizational Unit (OU): Name of the unit that owns the HDM server in the organization, a string of 1 to 64 characters. Only letters, digits, spaces, underscores (_), hyphens (-), and dots (.) are allowed. The organizational unit name cannot be a digits-only string.
· Locality (L): City or county where the HDM server resides, a string of 1 to 128 characters. Only letters, digits, spaces, underscores (_), hyphens (-), and dots (.) are allowed. The locality name cannot be a digits-only string.
· State or province (ST): State or province where the HDM server resides, a string of 1 to 128 characters. Only letters, digits, spaces, underscores (_), hyphens (-), and dots (.) are allowed. The state or province name cannot be a digits-only string.
· Country (C): Country or region where the HDM server resides. The country/region is represented as a two-letter code.
· Email address: Email address at which the HDM server owner can be contacted.
· Validity period: Validity period of the SSL certificate, in the range of 1 to 5475 days.
· Key length: Key length of the certificate.
· Basic information: Basic information about the current SSL certificate.
¡ Version—Version number of the certificate.
¡ Serial number—Serial number of the certificate. This number is assigned by the certificate authority (CA).
¡ Signature algorithm—Signature algorithm of the certificate.
¡ Public key—Public key information of the certificate.
· Issued by: Certificate authority that issued the certificate.
· Validity: Validity period of the certificate.
¡ Issued at—First valid day of the certificate.
¡ Expires at—Expiration day of the certificate.
· Issued to: Entity to whom the certificate is issued.
Configure PFR
Platform Firmware Resiliency (PFR) is a technology used to protect HDM from attacks. If PFR is enabled, PFR will verify the HDM firmware image when HDM starts.
· If the primary HDM firmware image passes the verification, HDM starts with the primary image.
· If the primary HDM firmware image is damaged, PFR verifies the backup HDM firmware image. If the backup image passes the verification, HDM starts with the backup image.
· If both the primary and backup HDM firmware images are damaged, but the damage to the primary image does not affect HDM start, HDM starts with the primary image.
Hardware and feature compatibility
Only the G5 series server supports this feature.
Software version and feature compatibility
This feature is supported only in HDM-2.13 and later.
Restrictions and guidelines
· You can update a damaged firmware image to correct it.
· Enabling PFR extends the startup time of HDM.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the navigation pane, select Security.
3. Click the PFR tab.
4. Select whether to enable HDM to start with the backup image upon primary image damage.
Figure 155 PFR tab
Parameters
· Enablement status: Enablement status of PFR.
· Current firmware status: Result of the verification on HDM firmware images during this startup.
· Start with the backup image upon primary image damage: Select whether HDM can start with the backup firmware image. This feature is disabled by default. With this feature enabled, HDM can start with the backup firmware image if the primary image fails the verification but the backup image passes the verification.
Configure the security tip for login
Perform this task to configure the security tip displayed on the login page.
Software version and feature compatibility
This feature is supported only in HDM-2.13 and later.
Restrictions and guidelines
The security tip can contain 1 to 1024 bytes. Valid characters include letters, digits, Chinese characters, and special characters except the left angle brackets (<) and right angle brackets (>).
Procedure
1. On the top navigation bar, click Users & Security.
2. In the navigation pane, select Security.
3. Click the Security Tip for Login tab.
4. Enable Display security tip at login.
5. (Optional.) Configure the security tip.
6. Click Save.
After a successful configuration, you can view the configured security tip on the login page.
Figure 156 Configuring the security tip for login
Figure 157 Security tip at login
Security modules
View TPM/TCM status
Trusted Platform Module (TPM) is a microchip embedded in the system board. It stores encryption information (such as encryption keys) for authenticating server hardware and software. Trusted Cryptography Module (TCM) is a trusted computing platform-based hardware module with protected storage space, which enables the platform to implement password calculation. For information about the TPM/TCM module, see the user guide for the server.
Restrictions and guidelines
This feature is available only in HDM-2.14 and later.
Procedure
1. On the top navigation bar, click Users & Security.
2. In the navigation pane, select Security Modules.
3. On the tab that opens, you can view TPM or TCM status. This field displays N/A if both the TPM and TCM are not supported.
Figure 158 Viewing TPM or TCM status
Unified control
Use unified control to manage a maximum of 10 devices in bulk. You can perform the following tasks:
· Launch an H5 KVM remote console
Add devices
Perform this task to add devices one by one or in bulk.
Restrictions and guidelines
The specified IP range can contain a maximum of 255 IP addresses.
If the specified IP range contains IP addresses of over 10 devices, the system adds the 10 devices whose information is obtained first.
If you change the HDM login username or password of a device after you add it for unified control, the device will become inaccessible from the unified control interface.
Only one user can add devices at a time.
Procedure
1. In the navigation pane, select Unified Control.
Figure 159 Unified control page
2. Click Add devices.
3. In the dialog box that opens, enter the start and end IP addresses, username, and password of the device, and then click OK.
Parameters
· Start IP: Enter the HDM management IP address or the start IP address of the HDM management IP range. Only IPv4 addresses are supported. This field is required.
· End IP: Enter the end HDM management IP address. Only IPv4 addresses are supported. This field is optional.
· Username: Enter a username for HDM login. As a best practice, enter the username of an administrator user. If you enter the username of a non-administrator user, some functions will be unavailable.
· Password: Enter the password for HDM login.
View device information
Perform this task to view information about devices that have been added, including IP addresses, product names, product serial numbers, health status, power status, and UID LED status.
Procedure
In the navigation pane, select Unified Control and view information about the added devices.
Figure 161 Viewing device information
Parameters
· IP: HDM management IP address of the server.
· Health status: Health status of the server.
¡ ![]() Normal—All server components are operating correctly.
Normal—All server components are operating correctly.
¡ ![]() Critical,
Critical, ![]() Major, or
Major, or ![]() Minor—A minimum
of one component is experiencing issues.
Minor—A minimum
of one component is experiencing issues.
· Power status: Power status of the server.
¡ ![]() On—The server is powered on.
On—The server is powered on.
¡ ![]() Off—The server is powered off.
Off—The server is powered off.
· UID LED: Status of the UID LED.
¡ ![]() On—The UID LED
of the server is steady blue.
On—The UID LED
of the server is steady blue.
¡ ![]() Off—The UID LED
of the server is off.
Off—The UID LED
of the server is off.
¡ ![]() Flashing—The UID
LED of the server is flashing blue. The server is
updating firmware or the remote console is launched.
Flashing—The UID
LED of the server is flashing blue. The server is
updating firmware or the remote console is launched.
Access HDM
Perform this task to access the HDM interface of a specific server.
Prerequisites
Make sure the specified user account for the device has the privilege to access HDM. The user privileges are determined by the user role.
Procedure
1. In the navigation pane, select Unified Control.
2. Click the IP address link of the target server.
The HDM interface for the server opens, as shown in Figure 100.
Figure 162 HDM interface for the specified server
Perform power actions
|
CAUTION: The force power-off, force system reset, and force power-cycle actions might cause corruption or loss of data. When you perform these actions, make sure you fully understand their impact on the services. |
Perform this task to manage power status of a server.
Prerequisites
Make sure the specified user account for the device has the administrator, operator, or power control role.
To avoid operation failure, make sure the other users are not performing any power actions.
Procedure
1. In the navigation pane, select Unified Control.
2. Identify the entry for the target server.
3. Select a power action for the server as shown in Figure 101.
¡ To warm reboot the server without power cycling the server, select Force system reset.
¡ To shut down the server immediately by force, select Force power-off. This action is equivalent to pressing the power button on the server for five seconds.
¡ To shut down the operating system first, and then remove power from the server, select Graceful power-off.
¡ To start up the server, select Power on.
¡ To power off and then power on the server, select Force power-cycle.
Figure 163 Performing power actions
Launch an H5 KVM remote console
Perform this task to operate a server from an H5 KVM remote console.
Prerequisites
Before you can launch an H5 KVM remote console, you must perform the following tasks:
· Make sure the specified user account for the device has the KVM extended privilege. If the user account does not have the privilege, edit the user account. For more information, see "Edit a user account."
· Make sure the user account specified for the device is enabled with the KVM service. If KVM is not enabled, enable the KVM service first. For more information, see "Edit an access service."
Procedure
1. In the navigation pane, select Unified Control.
2. Click H5 KVM in the target server entry.
For more information about the H5 KVM remote console, see "Remote console."
Figure 164 Remote console for a secondary user
Delete devices
To avoid operation failure, make sure the other users are not performing device deletion actions before you delete devices.
To delete devices:
1. In the navigation pane, select Unified Control.
2. Select one or multiple servers.
3. Click Delete devices.
4. In the dialog box that opens, click OK.
Figure 165 Deleting devices
Common operations
This section introduces common operations in HDM configuration.
Configure virtual media
Mount images through a Windows CIFS server
Common Internet File System (CIFS) allows HDM to access files on a remote server. Windows OSs are embedded with CIFS software and do not require CIFS installation.
This section uses Windows 7 as an example.
To mount images through a Windows CIFS server:
1. Copy the target image file to a local path. This section takes D:\IMAGE 2 as an example.
Figure 166 Copying an image file to a local path
2. Configure file sharing.
a. Right-click the IMAGE 2 file folder, select Share with > Specific people.
b. Add users as needed. This section uses UserA as an example.
Figure 167 Configuring file sharing settings
c. Select a Read/Write permission for each user from the Permission Level column.
Figure 168 Adding a user
3. Access HDM and configure media mounting settings.
a. On the top navigation bar, click Remote Services.
b. In the left navigation pane, select Virtual Media.
c. In the work pane, click Settings.
d. In the dialog box that opens, enable remote media.
e. Select CD/DVD as the media type.
f. Specify the IP address of the CIFS server and IMAGE2 as the source path. In this example, the server address is 192.168.32.48.
g. Select CIFS as the shared file system.
h. Enter the username and password for access to the shared image file.
Figure 169 Configuring media mounting settings
4. Click OK.
The Virtual Media page displays mounted images.
Mount images through a Linux CIFS server
Common Internet File System (CIFS) is an open version of Server Messages Block (SMB) and allows applications to access files on a remote server.
To set up a Linux CIFS server, you must install the Samba software on the device.
This section uses Red Hat Enterprise Linux 7.3 as an example.
Install and configure Samba
1. Execute the yum –y install samba samba-common samba-client command to install Samba.
The samba-common and samba-client keyword represent the Samba server and Samba client, respectively. As a best practice, specify both keywords to install both the server and the client.
2. Execute the yum list installed | grep samba command to verify that both the Samba server and Samba client have been installed successfully.
3. Execute the testparm command to verify that Samba is configured correctly as shown in Figure 109.
Figure 171 Verifying Samba parameters
4. Execute the systemctl start smb command to start the Samba service and execute the systemctl status smb command to verify that the service operates correctly.
5. Disable the firewall and disable SELinux.
systemctl stop firewalld
getenforce
setenforce 0
6. Execute the pdbedit –L command to verify that Samba users exist. If no user exists, execute the smbpasswd -a username command to add a user. In this example, the username is ldt.
Make sure the added user already exists in the server OS. To view existing users in the OS, execute the cat /etc/passwd command.
Figure 172 Adding a Samba user
7. Execute the smbclient -L //OS_IP_address command to access the Samba server. In this example, the address is 10.99.205.165.
Figure 173 Accessing the Samba server
8. Edit the /etc/samba/smb.conf configuration file to create a shared file path. In this example, the path is /test.
vi /etc/samba/smb.conf
[mnt]
comment = /mnt dir
path = /test
9. Execute the systemctl restart smb command to restart Samba.
10. Upload the file to share to the path. In this example, the file is named test.iso.
Mount an image to HDM
1. Access HDM.
2. On the top navigation bar, click Remote Services.
3. In the left navigation pane, select Virtual Media.
4. In the work pane, click Settings.
5. In the dialog box that opens, enable remote media.
a. Select CD/DVD as the media type.
b. Specify the IP address of the Samba server and /mnt as the source path. In this example, the server address is 10.99.205.165.
c. Select CIFS as the shared file system.
d. Enter the username and password of a Samba user.
e. (Optional.) Enter a domain name.
Figure 174 Configuring media mounting settings
6. Click OK.
The Virtual Media page displays mounted images.
Figure 175 Virtual Media page
Import HDM configuration
Import HDM user accounts
Restrictions and guidelines
Make sure the server model in the configuration file to import is consistent with the actual server model.
The password fields are empty in a configuration file exported from a server. To import the configuration file to its source server, you can leave the password fields empty or specify passwords as needed. To import the configuration file to another server of the same model, you must specify the passwords in the configuration file.
Procedure
1. Open the configuration file, and search for User Accounts.
Figure 176 Searching for user account information
2. To edit the password of an existing user, delete the comment statement for the user, and then set the new password.
To retain the password of an existing user, leave the password field for the user empty.
If the complexity check field displays 1 in Figure 114, make sure the password you enter meet the complexity requirements.
Figure 177 Configuring a new password
3. To add a new user account, delete the comment statement for the user, and then specify the username and password.
The username and password fields are required for a new user account.
If the complexity check field displays 1 in Figure 114, make sure the password you enter meet the complexity requirements.
Figure 178 Deleting the comment statement
Figure 179 Setting the username and password
4. To configure the role of a user and enable access to HDM, set the User role and Access to HDM fields, respectively. For supported options of the fields, see Table 14.
Figure 180 Configuring user privileges
5. Modify miscellaneous settings as needed.
For more information about the configurable fields, see Table 14.
Table 14 Configurable item description
|
Item |
Description |
|
role customrole 1 through 5 |
Privileges of custom user roles 1 through 5. Each role custom field displays the decimal number equivalent of an 9-bit binary number, where each bit represents a privilege as follows: · Bit 0—Remote control. · Bit 1—Remote media. · Bit 2—Security configuration. · Bit 3—User account configuration. · Bit 4—Basic configuration. · Bit 5—Power control. · Bit 6—Maintenance. · Bit 7—Information query. · Bit 8—Password modification. The bit value indicates the enablement status of a privilege as follows: · 1—Enabled. · 0—Disabled. |
|
User ID |
User ID, in the range of 2 to 16. A user ID must be unique. |
|
User role |
Specify the role of the user. · 2—User. · 3—Operator. · 4—Administrator. · 6—CustomRole 1. · 7—CustomRole 2. · 8—CustomRole 3. · 9—CustomRole 4. · 10—CustomRole 5. · 15—None. |
|
Access to HDM |
Enter 0 or 1 to disable or enable access to HDM. |
|
WEB |
Enter 0 or 1 to disable or enable the Web extended privilege. |
|
IPMI |
Enter 0 or 1 to disable or enable the IPMI extended privilege. |
6. Save and import the configuration file.
a. On the top navigation bar, click Remote O&M.
b. In the left navigation pane, select Manage Configuration.
c. Import the configuration file.
The configuration takes effect immediately.
Figure 181 Importing the configuration file
7. To verify the configuration, re-sign in to HDM after HDM restarts and access the Users & Security > User Accounts page to view HDM user accounts.
Figure 182 Re-signing in to HDM
Figure 183 Viewing user accounts
Import SNMP trap settings
1. Open the configuration file, and search for SNMPTrap.
Figure 184 Searching for SNMP trap settings
2. Modify SNMP trap server settings. For example:
¡ Set the Destination_2 address to 10.99.160.75 and the Port_2 field to 161.
¡ Set the Enable_3 field to 0 to disable the SNMP trap server.
¡ Set the Destination_4 address to 10.99.160.70.
Figure 185 Modifying SNMP trap server settings
3. Modify miscellaneous SNMP trap settings as needed.
For more information about configurable SNMP trap settings, see Table 15.
Table 15 Configurable item description
|
Item |
Description |
|
SnmpEnable |
Enter 0 or 1 to disable or enable SNMP trap notification. |
|
Trap Mode |
Enter an SNMP trap mode. Options include: · 0—Node mode. · 1—Event mode. |
|
Version |
Enter an SNMP version. Options include: · 0—v1. · 1—v2c. · 2—v3. |
|
V3_User |
Enter a username used by the system to send SNMPv3 traps. |
|
Location |
Enter the location of the server, a string of up to 31 bytes. |
|
Contact |
Enter contact information, a string of up to 31 bytes. |
|
Trap_Community |
Enter the trap community string for authentication on the manager. The value range is 1 to 31 characters. The default value is public. |
|
AlarmSendLevel |
Severity levels of SNMP traps. Options include: · 0—Minor + Major + Critical. · 1—Major + Critical. · 2—All. |
|
Port-Port_8 |
Enter the port number at which the destination host receives SNMP traps. The value range is 1 to 65535. The default port number is 162. |
|
Enable_1-Enable_8 |
Enter 0 or 1 to disable or enable an SNMP trap server. |
|
Destination_1-Destination_8 |
IP or domain address of a destination host that receives SNMP traps. |
4. Save and import the configuration file.
a. On the top navigation bar, click Remote O&M.
b. In the left navigation pane, select Manage Configuration.
c. Import the configuration file.
The configuration takes effect immediately.
5. To verify the configuration, open the SNMP trap packet settings page, and then view SNMP trap settings.
Figure 186 Viewing SNMP trap settings
Set up a syslog server
This section uses Red Hat Enterprise Linux 7.7 as an example.
You can set up a Linux syslog server based on UDP, TCP, or TLS.
Set up a Linux syslog server based on UDP or TCP
1. Open the /etc/rsyslog.conf configuration file.
Figure 187 Opening the configuration file
2. Enable UDP and TCP syslog reception.
a. Uncomment the line as shown in Figure 125.
b. Set the UDP server port, TCP server port, or both. If you specify both ports, make sure the specified ports are different. In this example, the UDP port is 514 and the TCP port is 518.
c. Specify the path to store remote logs as /var/log/hdm/messages.log.
Figure 188 Configuring UDP and TCP syslog reception settings
|
|
NOTE: · The $template RemoteLogs directive instructs rsyslog daemon to collect and write all remote messages to distinct files stored in the /var/log directory. · The *.* ?RemoteLogs directive indicates that the RemoteLogs template will be used to receive all log messages. · The & ~ directive instructs rsyslog daemon to stop writing messages to local files, and to write messages only to the messages.log directory. |
3. Execute commands to restart rsyslog and view its status.
Figure 189 Restarting rsyslog and viewing its status
4. Configure syslog settings on the HDM Web interface.
a. Sign in to the HDM Web interface.
b. On the top navigation bar, click Remote O&M.
c. In the left navigation pane, select Alarm Settings.
d. Click the Syslog Settings tab.
e. In the Syslog notification settings section, select Enable for Syslog notification, select host name as the syslog server identifier, select UDP as the transmission protocol, and then click OK.
Figure 190 Configuring syslog notification settings
e. In the Syslog server settings section, click Edit for a syslog server. Configure the syslog server parameters, and then click OK.
Make sure you specify the OS IP address of the server instead of the HDM management address.
Figure 191 Configuring syslog server parameters
Set up a Linux syslog server based on TLS
TLS is an encrypted transmission protocol and supports the following authentication modes.
· One-way authentication—Authenticates only the syslog server.
· Two-way authentication—Authenticates both the syslog server and the client used for HDM login.
Prerequisites
Install the OS on the server. Rsyslog is installed on the OS by default.
Procedure
1. Download the rsyslog-gnutls package for TLS transmission.
¡ If the server is connected to the network, use the sudo yum install -y rsyslog-gnutls or apt command to download the package.
¡ If the server is disconnected from the network, obtain the package from the OS image, as shown in Figure 130.
Figure 192 Obtaining the rsyslog-gnutls package from the OS image
2. Install the rsyslog-gnutls package.
Figure 193 Installing the rsyslog-gnutls package
3. Generate a self-signed CA certificate. Right-click on the desktop, select Open Terminal, and then perform the following tasks:
a. Generate a private key file in PEM format.
# cd /root/Desktop
# mkdir tls
# cd tls
# mkdir server
# mkdir client
# openssl genrsa -out cakey.pem 2048
b. Generate a root certificate signing request (CSR) file.
# openssl req -new -key cakey.pem -out ca.csr -subj "/C=CN/ST=myprovice/L=mycity/O=myorganization/OU=mygroup/CN=myCA"
c. Generate a self-signed root certificate.
# openssl x509 -req -days 365 -sha1 -extensions v3_ca -signkey cakey.pem -in ca.csr -out cacert.pem
4. Generate a private key and certificate for the server. Right-click on the desktop, select Open Terminal, and then perform the following tasks:
a. Generate a private key file.
# cd server
# openssl genrsa -out key.pem 2048
b. Generate a certificate request file. This section uses IP address 172.16.18.48 (OS IP address of the server) as an example.
# openssl req -new -key key.pem -out server.csr -subj "/C=CN/ST=myprovice/L=mycity/O=myorganization/OU=mygroup/CN=172.16.18.48"
c. Use the root certificate to issue the server certificate.
# openssl x509 -req -days 365 -sha1 -extensions v3_req -CA ../cacert.pem -CAkey ../cakey.pem -CAserial ca.srl -CAcreateserial -in server.csr -out cert.pem
d. Use the CA certificate to verify the server certificate.
# openssl verify -CAfile ../cacert.pem cert.pem
5. Generate a private key and certificate for the client. Right-click on the desktop, select Open Terminal, and then perform the following tasks:
a. Generate a private key file.
# cd ../client
# openssl genrsa -out key.pem 2048
b. Generate a certificate request file. This section uses IP address 172.16.20.168 as an example.
# openssl req -new -key key.pem -out client.csr -subj "/C=CN/ST=myprovice/L=mycity/O=myorganization/OU=mygroup/CN=172.16.20.168"
c. Use the root certificate to issue the client certificate.
# openssl x509 -req -days 365 -sha1 -extensions v3_req -CA ../cacert.pem -CAkey ../cakey.pem -CAserial ../server/ca.srl -CAcreateserial -in client.csr -out cert.pem
d. Use the CA certificate to verify the client certificate.
# openssl verify -CAfile ../cacert.pem cert.pem
6. Configure the rsyslog.conf configuration file.
a. Leave TCP and UDP settings unchanged, and modify the marked lines as shown in Figure 132.
Figure 194 Configuring the configuration file
b. Set the server port to 516.
c. For one-way authentication, add the following line to the file:
$InputTCPServerStreamDriverAuthMode anon
d. For two-way authentication, add the following line to the file:
$InputTCPServerStreamDriverAuthMode x509/certvalid
7. Turn off the firewall. Execute the following commands and set SELINUX to disabled:
# systemctl stop firewalld
# setenforce 0
# sed -i 's#SELINUX=enforcing#SELINUX=disabled#g' /etc/selinux/config
8. Restart rsyslog and view its status.
systemctl restart rsyslog
systemctl status rsyslog
9. Configure syslog settings on the HDM Web interface.
a. Copy the certificates generated in steps 3 through 5 to the host used for HDM access.
b. Sign in to HDM.
c. On the top navigation bar, click Remote O&M.
d. In the left navigation pane, select Alarm Settings.
e. Click the Syslog Settings tab.
f. In the Alarm log notification section, enable alarm log notification, select an alarm log host ID and TLS, as shown in Figure 128.
- If you select One-way authentication, upload the self-signed CA certificate generated in step 3.
- If you select Two-way authentication, upload the self-signed CA certificate, local certificate, and private key file generated in steps 3 and 5.
g. Click OK.
Figure 195 Configuring syslog notification settings
g. Configure the alarm log server parameters, and then click OK.
Figure 196 Configuring alarm log server parameters
View rsyslog log
1. Log in to the rsyslog server through SSH.
In this example, the IP address of the server is 172.16.18.48.
2. View log entries in the /var/log/hdm/messages.log path.
Figure 197 Viewing rsyslog log
Configure LDAP settings
Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an IP network. LDAP can quickly respond to user query requests, and can be used to implement unified user authentication management.
HDM supports both Windows Active Directory and Linux OpenLDAP. This section uses Windows Server 2012 R2 Datacenter as an example to describe LDAP configuration.
Install an OS
Install Windows Server 2012 R2 Datacenter. For more information, see H3C Servers Operating System Installation Guide.
Set up an LDAP server
Prerequisites
Install the OS and access the OS as administrator.
Install a DNS server
2. From the left navigation pane, select Local Server to enter the PROPERTIES page of the local server.
Figure 198 PROPERTIES page of the local server
3. Click Manage in the upper right corner and select Add Roles and Features.
4. In the window that opens, click Next.
Figure 199 Add Roles and Features wizard
5. Select Role-based or feature-based installation as the installation type, and then click Next.
Figure 200 Selecting an installation type
6. Select Select a server from the server pool, select the current server as the destination server, and then click Next.
Figure 201 Selecting the destination server
7. Select DNS server as the server role, and then click Next.
Figure 202 Selecting the server role
8. Select NET Framework 4.5 Features, and then click Next.
Figure 203 Selecting the features of the server
9. On the DNS Server tab, click Next.
10. Verify that the server configuration is correct, and then click Install.
Install Active Directory Domain Services on the server
1. Repeat steps 1 to 6 in DNS server installation.
2. On the Server Roles tab, select Active Directory Domain Services, and then click Next.
Figure 204 Selecting the server role
3. Select NET Framework 4.5 Features, and then click Next.
Figure 205 Selecting the features of the server
4. On the AD DS tab, click Next.
5. Verify that the service configuration is correct, and then click Install.
Configure Active Directory Domain Services
1. From the left navigation pane, select AD DS, and then click More....
Figure 206 AD DS menu
2. In the dialog box that opens, click Promote this server to a domain controller in the Action column to open the AD DS configuration wizard.
Figure 207 All Servers Task Details dialog box
3. Select Add a new forest, enter an Active Directory domain name in the Root domain name field, for example, hdmldap, and then click Next.
Figure 208 Active Directory Domain Services configuration wizard
4. On the Domain Controller Options tab, enter the password for the domain controller, and then click Next.
Figure 209 Domain Controller Options menu
5. Click Next as instructed until you enter the Paths tab. Specify the location of the AD DS database, log files, and SYSVOL, and then click Next.
Figure 210 Configuring Active Directory paths
6. Click Next as instructed until you enter the Prerequisites Check tab, and then click Install.
The OS automatically restarts after the installation is complete.
Figure 211 Prerequisites Check menu
Install Active Directory Certificate Services on the server
1. Access the OS as administrator.
To access the OS successfully, you must add the domain name to the front of the username.
2. Repeat steps 1 to 6 in DNS server installation.
3. On the Server Roles tab, select Active Directory Certificate Services, and then click Next.
Figure 212 Selecting the server role
4. Select NET Framework 4.5 Features, and then click Next.
Figure 213 Selecting the features of the server
5. On the AD CS tab, click Next.
6. On the Role Services tab, select Certification Authority and Certification Authority Web Enrollment, and then click Next.
Figure 214 Selecting role services for AD CS
7. On the Web Server Role (IIS) tab, click Next.
8. On the Role Services tab, select role services for the Web server, and then click Next.
As a best practice, use the default role services.
Figure 215 Selecting role services for the Web server
9. On the Confirmation tab, click Install.
Configure Active Directory Certificate Services
1. From the left navigation pane, select AD CS, and then click More....
Figure 216 AD CS menu
2. In the dialog box that opens, click Configure Active Directory Certificate Services on the server in the Action column to open the AD CS configuration wizard.
Figure 217 All Servers Task Details dialog box
3. On the Credentials tab, click Next.
Figure 218 AD CS configuration wizard
4. On the Role Services tab, select Certificate Authority and Certificate Authority Web Enrollment, and then click Next.
Figure 219 Selecting role services
5. On the Setup Type tab, select Enterprise CA, and then click Next.
6. On the CA Type tab, select Root CA, and then click Next.
7. On the Private Key tab, select Create a new private key, and then click Next.
8. Select RSA as the cryptographic provider, 2048 as the key length, and SHA1 as the hash algorithm, and then click Next.
Figure 220 Specifying the cryptographic options
9. Specify hdmldap-test02 as the CA name, and then click Next.
Figure 221 Specifying the CA name
10. Enter a validity period, and then click Next. The default validity period is 5 years.
11. On the Certificate Database tab, specify the database locations, and then click Next.
Figure 222 Specifying the database locations
12. Verify that the configuration is correct, and then click Configure.
After the configuration is complete, restart the server to make the configuration take effect.
Configure the LDAP server
Prerequisites
After the OS restarts, access the OS as administrator. To access the OS successfully, you must add the domain name to the front of the username.
Create organizational units
LDAP supports levels of organizational units. You can create an organizational unit of any level as needed. This section creates a first-level organizational unit and its second-level units as an example.
To create organizational units:
1. Open Server Manager.
2. Click the Tasks button in the upper right corner, and then select Active Directory Users and Computers.
Figure 223 Active Directory Users and Computers window
3. Right-click hdmldap.com in the left navigation pane, and select New > Organizational Unit.
Figure 224 Right-clicking a domain name
4. In the dialog box that opens, enter an organizational unit name, for example, company, and then click OK.
First-level organizational unit company is created successfully.
Figure 225 Creating a first-level organizational unit
5. To create a second-level organizational unit for the first-level organizational unit, right-click company, and select New > Organizational Unit.
6. In the dialog box that opens, enter an organizational unit name, for example, product, and then click OK.
Second-level organizational unit product is created successfully.
Figure 226 Creating a second-level organizational unit
Create a role group
You can create a role group for an organizational unit of any level.
To create a role group:
1. Right-click an organizational unit and select New > Group. This section takes second-level organizational unit product as an example.
2. In the dialog box that opens, enter a group name, for example, group1, select the group scope and group type, and then click OK.
As a best practice, specify the same group name in the Group name (A) and Group name (pre-Windows 2000) fields.
Figure 227 Creating a role group
Creating a user
You can create a user for an organizational unit of any level.
To create a user:
1. Right-click an organizational unit and select New > User. This section takes second-level organizational unit product as an example.
2. In the dialog box that opens, configure the user settings as required, and then click Next.
The usernames in the User logon name and User logon name (pre-Windows 2000) fields will be used for HDM login.
Figure 228 Creating a user
3. Set the password, cancel the User must change password at next logon option, and click Next.
The password will be used for HDM login.
Figure 229 Setting the password
4. Verify that the user configuration is correct, and click Finish.
Add a user to a role group
You can add a user to a role group by configuring the role group or configuring the user. This section configures the user as an example.
To add a user to a user group:
1. Right-click the target user, for example, user1, and select Add to a group.
2. In the dialog box that opens, enter a role group name, for example, group1, and then click OK.
Figure 230 Selecting a role group
Configure LDAP settings from HDM
Configure LDAP settings
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the LDAP Settings section, click Settings.
5. In the dialog box that opens, enable LDAP authentication, and then configure the following LDAP parameters, as shown in Figure 169:
a. Select No encryption as the encryption type.
b. Select IP as the common name type.
c. Enter the OS IP address of the LDAP server in the Server address field.
d. Use the default port number.
e. Enter the DN information of a user, for example, user1, including the common name, organizational units in ascending order of levels, and the domain names. Separate these parameters with commas.
In this example, enter cn=user1,ou=product,ou=company,dc=hdmldap,dc=com.
f. Enter the password of the user.
g. Enter the domain information of the user in the Search base field.
h. Select cn as the user identification method.
Figure 231 Configuring the LDAP parameters
6. Click OK.
Add a role group
1. On the top navigation bar, click Users & Security.
2. In the left navigation pane, select User Accounts.
3. Click the Domain Users tab.
4. In the LDAP Settings section, click Add role groups.
5. Configure the role group parameters, as shown in Figure 170.
6. Click OK.
Figure 232 Adding a role group
Verify the LDAP configuration
Perform this task to verify that the LDAP configuration is complete and has taken effect.
To verify the LDAP configuration:
1. Sign in to HDM with a username and password in role group group1. This section uses user user1 as an example.
Figure 233 Signing in to HDM
2. View the LDAP settings.
LDAP keywords
|
Keyword |
Full name |
Description |
|
dc |
Domain component |
Domain name. For example, domain name example.com can be translated into dc=example,dc=com. |
|
uid |
User ID |
ID of a user. |
|
ou |
Organizational unit |
Container of Active Directory that can manage Active Directory objects such as users and groups. |
|
cn |
Common name |
N/A |
|
sn |
Surname |
N/A |
|
dn |
Distinguished name |
Distinguished name that uniquely identifies an entry in a directory. |
|
c |
Country |
Country or region code, for example, CN. |
|
o |
Organization |
Organization name. |
Appendix A Downloaded log files
|
Level 1 |
Level 2 |
File name |
Description |
|
dump |
|
dump_end |
Dump end time |
|
HDM_SDS_DUMP_DUP_01 |
Dump encryption information |
||
|
HDM_SDS_DUMP_DUP_02 |
Dump encryption information |
||
|
HDM_SDS_DUMP_DUP_03 |
Dump encryption information |
||
|
HDM_SDS_DUMP_DUP_04 |
Dump encryption information |
||
|
event |
|
*.sbe |
Internal record for event log |
|
*.csv |
Internal record for event log |
||
|
hdm |
|
pack.info |
SDS log compression information |
|
sdmmc0p4 |
log |
auth |
HDM login authentication information |
|
operate |
Operation log |
||
|
update |
Update log |
||
|
visible |
Audit log |
||
|
static |
|
board_cfg |
System board or mainboard information |
|
hdm.json |
HDM configuration |
||
|
bios.json |
BIOS configuration |
||
|
raid.json |
RAID configuration |
||
|
firmware_version |
System firmware version information |
||
|
FruInfo |
FRU information |
||
|
dcpmm_info |
DCPMM information |
||
|
gpu_info |
GPU information |
||
|
hardware.info |
Hardware information |
||
|
hardware_info |
Hardware information |
||
|
net_cfg |
Net configuration |
||
|
PCIe_arguments_table |
PCIe device configuration information |
||
|
Pdb_Node_dump_info |
CPLD register values of node board and power supply board on R6900 G3 and R8900 G3 |
||
|
nvme_info |
NVMe drive information |
||
|
psu_cfg |
Power configuration |
||
|
sensor_info |
Sensor list |
||
|
test |
SDS log |