- Table of Contents
-
- 04-Layer 3-IP Services Configuration Guide
- 00-Preface
- 01-ARP configuration
- 02-IP addressing configuration
- 03-DHCP configuration
- 04-DNS configuration
- 05-IP forwarding basics configuration
- 06-IRDP configuration
- 07-IP performance optimization configuration
- 08-UDP Helper configuration
- 09-IPv6 basics configuration
- 10-DHCPv6 configuration
- 11-Tunnel configuration
- 12-GRE configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 12-GRE configuration | 134.03 KB |
Contents
GRE tunnel operating principle
Configuring a GRE over IPv4 tunnel
Displaying and maintaining GRE
GRE over IPv4 tunnel configuration example
Configuring GRE
Overview
GRE encapsulation format
Figure 1 GRE encapsulation format
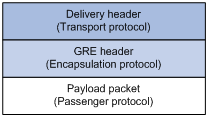
As shown in Figure 1, a GRE-tunneled packet includes the following parts:
· Payload packet—Original packet. The protocol type of the payload packet is called the passenger protocol. The passenger protocol can be any network layer protocol.
· GRE header—Header that is added to the payload packet to change the payload packet to a GRE packet. A GRE header includes the number of encapsulations, version, passenger protocol type, checksum, and key. GRE is called the encapsulation protocol.
· Delivery header—Header that is added to the GRE packet to deliver it to the tunnel end. The transport protocol (or deliver protocol) is the network layer protocol that transfers GRE packets. The device supports IPv4 and IPv6 as the transport protocols. When the transport protocol is IPv4, the GRE tunnel is called the "GRE over IPv4 tunnel." When the transport protocol is IPv6, the GRE tunnel is called the "GRE over IPv6 tunnel."
|
|
NOTE: The device only supports GRE over IPv4 tunnels. |
GRE tunnel operating principle
Figure 2 IPv6 networks interconnected through a GRE tunnel
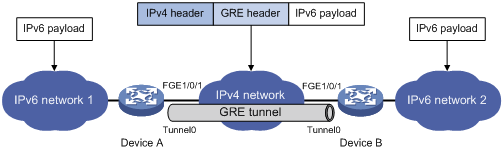
As shown in Figure 2, an IPv6 protocol packet traverses an IPv4 network through a GRE tunnel as follows:
1. After receiving an IPv6 packet from the interface connected to IPv6 network 1, Device A processes the packet as follows:
a. Looks up the routing table to identify the outgoing interface for the IPv6 packet.
b. Submits the IPv6 packet to the outgoing interface—the GRE tunnel interface Tunnel 0.
2. Upon receiving the packet, the tunnel interface encapsulates the packet with GRE and then with IPv4. In the IPv4 header:
? The source address is the tunnel's source address (the IP address of interface FortyGigE 1/0/1 of Device A).
? The destination address is the tunnel's destination address (the IP address of interface FortyGigE 1/0/1 of Device B).
3. Device A looks up the routing table according to the destination address in the IPv4 header, and forwards the IPv4 packet out of the physical interface (FortyGigE 1/0/1) of the GRE tunnel.
4. When the IPv4 arrives at the GRE tunnel destination Device B, Device B checks the destination address. Because the destination is Device B itself and the protocol number in the IP header is 47 (the protocol number for GRE), Device B submits the packet to GRE for de-encapsulation.
5. GRE first removes the IPv4 header, and then processes the packet. After GRE finishes processing, it removes the GRE header, and submits the payload to the IPv6 protocol for forwarding.
|
|
NOTE: GRE encapsulation and de-encapsulation can decrease the forwarding efficiency of tunnel-end devices. |
Protocols and standards
· RFC 1701, Generic Routing Encapsulation (GRE)
· RFC 1702, Generic Routing Encapsulation over IPv4 networks
· RFC 2784, Generic Routing Encapsulation (GRE)
· RFC 2890, Key and Sequence Number Extensions to GRE
Configuring a GRE over IPv4 tunnel
Follow these guidelines when you configure a GRE over IPv4 tunnel:
· Before you create a tunnel interface, you must reserve global resources of two VLAN interfaces. The device uses the reserved resources to create the tunnel interface. For more information about global VLAN interface resource reservation, see Layer 2—LAN Switching Configuration Guide.
· The device cannot directly route a tunneled packet based on its destination address. The packet is sent to a tunnel-type service loopback group, which then delivers the packet to the forwarding module for Layer 3 forwarding. For the tunnel interface to receive and forward packets, you must configure a tunnel-type service loopback group on the device. For information about service loopback group, see Layer 2—LAN Switching Configuration Guide.
· You must configure the tunnel source address and destination address at both ends of a tunnel. The tunnel source or destination address at one end must be the tunnel destination or source address at the other end.
· As a best practice, do not configure the same tunnel source and destination addresses for local tunnel interfaces that use the same tunnel mode.
· To ensure correct packet forwarding, identify whether the destination network of packets and the IP address of the local tunnel interface are on the same subnet. If they are not, configure a route reaching the destination network through the tunnel interface. You can configure the route by using one of the following methods:
? Configure a static route, using the local tunnel interface as the outgoing interface of the route.
? Enable BGP or OSPF on both the tunnel interface and the interface connecting the private network. This allows BGP or OSPF to establish a routing entry with the tunnel interface as the outgoing interface.
The route configuration is required on both ends of the tunnel. For more information about the route configuration, see static routing, BGP, or OSPF in Layer 3—IP Routing Configuration Guide.
· The IP address of the tunnel interface and the tunnel destination address configured on the tunnel interface must be in different subnets.
For information about tunnel interfaces, and the tunneling commands, see "Configuring tunneling."
To configure a GRE over IPv4 tunnel:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Reserve global VLAN interface resources. |
reserve-vlan-interface vlan-interface-id1 [ to vlan-interface-id2 ] global |
By default, no reserved VLAN interface resources exist. |
|
3. Create a service loopback group and specify its service type as tunnel. |
service-loopback group number type tunnel |
By default, no service loopback groups exist. |
|
4. Enter Layer 2 Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
5. Assign the port to the service loopback group. |
port service-loopback group number |
By default, a port does not belong to any service loopback group. |
|
6. Return to system view. |
quit |
N/A |
|
7. Create a GRE over IPv4 tunnel interface and enter its view. |
interface tunnel interface-number mode gre |
By default, the device has no tunnel interface. You must configure the same tunnel mode on both ends of a tunnel. Otherwise, packet delivery might fail. |
|
8. Configure an IPv4 or IPv6 address for the tunnel interface. |
For information about how to assign an IPv4 address to an interface, see "Configuring IP addressing." For information about how to assign an IPv6 address to an interface, see "Configuring basic IPv6 settings." |
By default, no IPv4 or IPv6 address is configured for a tunnel interface. When the passenger protocol is IPv4, configure an IPv4 address for the tunnel interface. When the passenger protocol is IPv6, configure an IPv6 address for the tunnel interface. |
|
9. Configure a source address or source interface for the tunnel interface. |
source { ip-address | interface-type interface-number } |
By default, no source address or interface is configured for a tunnel interface. If you configure a source address for a tunnel interface, the tunnel interface uses the source address as the source address of the encapsulated packets. If you configure a source interface for a tunnel interface, the tunnel interface uses the primary IP address of the source interface as the source address of the encapsulated packets. |
|
10. Configure a destination address for the tunnel interface. |
destination ip-address |
By default, no destination address is configured for a tunnel interface. The destination address is the address of the physical interface that the tunnel remote end uses to receive packets from the GRE tunnel. The tunnel local end uses this address as the destination address of the encapsulated packets. |
|
11. (Optional.) Enable GRE keepalive, and set the keepalive interval and keepalive number. |
keepalive [ interval [ times ] ] |
By default, GRE keepalive is disabled. |
|
12. Return to system view. |
quit |
N/A |
|
13. (Optional.) Configure the device to discard IPv6 packets with IPv4-compatible IPv6 addresses. |
tunnel discard ipv4-compatible-packet |
By default, the device does not discard such IPv6 packets. |
Displaying and maintaining GRE
Execute display commands in any view and the reset command in user view.
|
Task |
Command |
Remarks |
|
Display information about tunnel interfaces. |
display interface [ tunnel ] [ brief [ down ] ] display interface [ tunnel [ number ] ] [ brief [ description ] ] |
For more information about the commands, see Layer 3—IP Services Command Reference. |
|
Display IPv6 information about tunnel interface. |
display ipv6 interface [ tunnel [ number ] ] [ brief ] |
For more information about this command, see Layer 3—IP Services Command Reference. |
|
Clear tunnel interface statistics. |
reset counters interface [ tunnel [ number ] ] |
For more information about this command, see Layer 3—IP Services Command Reference. |
GRE over IPv4 tunnel configuration example
Network requirements
Group 1 and Group 2 are two private IPv4 networks. The two networks both use private network addresses and belong to the same VPN. Configure a GRE tunnel between Switch A and Switch B so the two private IPv4 networks can communicate with each other.
Figure 3 Network diagram
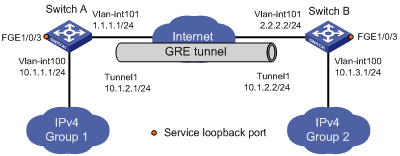
Configuration procedure
Before performing the following configuration, configure an IP address for each interface, and make sure Switch A and Switch B can reach each other.
1. Configure Switch A:
# Reserve global resources of VLAN-interface 3001 and VLAN-interface 3002.
<SwitchA> system-view
[SwitchA] reserve-vlan-interface 3001 to 3002 global
# Create service loopback group 1, and configure the service type as tunnel.
[SwitchA] service-loopback group 1 type tunnel
# Add port FortyGigE 1/0/3 to service loopback group 1.
[SwitchA] interface FortyGigE 1/0/3
[SwitchA-FortyGigE1/0/3] port service-loopback group 1
[SwitchA-FortyGigE1/0/3] quit
# Create a tunnel interface Tunnel 1, and specify the tunnel mode as GRE over IPv4.
[SwitchA] interface tunnel 1 mode gre
# Configure an IP address for the tunnel interface.
[SwitchA-Tunnel1] ip address 10.1.2.1 255.255.255.0
# Configure the source address of tunnel interface as the IP address of VLAN-interface 101 on Switch A.
[SwitchA-Tunnel1] source vlan-interface 101
# Configure the destination address of the tunnel interface as the IP address of VLAN-interface 101 on Switch B.
[SwitchA-Tunnel1] destination 2.2.2.2
[SwitchA-Tunnel1] quit
# Configure a static route from Switch A through the tunnel interface to Group 2.
[SwitchA] ip route-static 10.1.3.0 255.255.255.0 tunnel 1
2. Configure Switch B:
# Reserve global resources of VLAN-interface 3001 and VLAN-interface 3002.
<SwitchB> system-view
[SwitchB] reserve-vlan-interface 3001 to 3002 global
# Create service loopback group 1, and configure the service type as tunnel.
[SwitchB] service-loopback group 1 type tunnel
# Add port FortyGigE 1/0/3 to service loopback group 1.
[SwitchB] interface FortyGigE 1/0/3
[SwitchB-FortyGigE1/0/3] port service-loopback group 1
[SwitchB-FortyGigE1/0/3] quit
# Create a tunnel interface Tunnel 1, and specify the tunnel mode as GRE over IPv4.
[SwitchB] interface tunnel 1 mode gre
# Configure an IP address for the tunnel interface.
[SwitchB-Tunnel1] ip address 10.1.2.2 255.255.255.0
# Configure the source address of tunnel interface as the IP address of VLAN-interface 101 on Switch B.
[SwitchB-Tunnel1] source vlan-interface 101
# Configure the destination address of the tunnel interface as the IP address of VLAN-interface 101 on Switch A.
[SwitchB-Tunnel1] destination 1.1.1.1
[SwitchB-Tunnel1] quit
# Configure a static route from Switch B through the tunnel interface to Group 1.
[SwitchB] ip route-static 10.1.1.0 255.255.255.0 Tunnel 1
Verifying the configuration
# Display tunnel interface information on Switch A.
[SwitchA] display interface tunnel 1
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 1476
Internet Address is 10.1.2.1/24 Primary
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel keepalive disabled
Tunnel TTL 255
Tunnel protocol/transport GRE/IP
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Display tunnel interface information on Switch B.
[SwitchB] display interface tunnel 1
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64kbps
Maximum Transmit Unit: 1476
Internet Address is 10.1.2.2/24 Primary
Tunnel source 2.2.2.2, destination 1.1.1.1
Tunnel keepalive disabled
Tunnel TTL 255
Tunnel protocol/transport GRE/IP
GRE key disabled
Checksumming of GRE packets disabled
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# From Switch B, ping the IP address of VLAN-interface 100 on Switch A.
[SwitchB] ping -a 10.1.3.1 10.1.1.1
Ping 10.1.1.1 (10.1.1.1) from 10.1.3.1: 56 data bytes, press CTRL_C to break
56 bytes from 10.1.1.1: icmp_seq=0 ttl=255 time=11.000 ms
56 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=0.000 ms
56 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/2.400/11.000/4.317 ms
The output shows that Switch B can successfully ping Switch A.
Troubleshooting GRE
The key to configuring GRE is to keep the configurations consistent. Most faults can be located by using the debugging gre or debugging tunnel command. This section analyzes one type of fault for illustration, with the scenario shown in Figure 4.
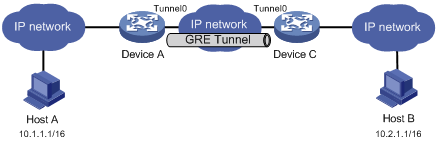
Symptom
The interfaces at both ends of the tunnel are configured correctly and can ping each other, but Host A and Host B cannot ping each other.
Analysis
It might be because that Device A or Device C has no route to reach the peer network.
Solution
1. Execute the display ip routing-table command on Device A and Device C to view whether Device A has a route over tunnel 0 to 10.2.0.0/16 and whether Device C has a route over tunnel 0 to 10.1.0.0/16.
2. If such a route does not exist, execute the ip route-static command in system view to add the route. Take Device A as an example:
[DeviceA] ip route-static 10.2.0.0 255.255.0.0 tunnel 0
