- Table of Contents
-
- 07-Security Configuration Guide
- 00-Preface
- 01-Security Overview
- 02-AAA Configuration
- 03-802.1X Configuration
- 04-MAC Authentication Configuration
- 05-Port Security Configuration
- 06-Public Key Configuration
- 07-PKI Configuration
- 08-SSH Configuration
- 09-SSL Configuration
- 10-User Isolation Configuration
- 11-Portal Configuration
- 12-IPsec Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 06-Public Key Configuration | 88.70 KB |
Creating a local asymmetric key pair
Displaying or exporting the local host public key
Displaying and recording the host public key information
Displaying the host public key in a specific format and saving it to a file
Exporting the host public key in a specific format to a file
Destroying a local asymmetric key pair
Specifying the peer public key on the local device
Public key configuration examples
To protect data confidentiality during transmission, the data sender uses an algorithm and a key to encrypt the plain text data before sending the data out. The receiver uses the same algorithm with the help of a key to decrypt the data, as shown in Figure 1.
Figure 1 Encryption and decryption
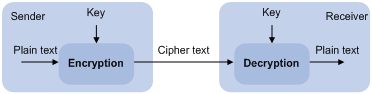
The keys that participate in the conversion between plain text and cipher text can be the same or different, dividing the encryption and decryption algorithms into the following types:
· Symmetric key algorithm—The keys for encryption and decryption are the same.
· Asymmetric key algorithm—The keys for encryption and decryption are different. One is the public key, and the other is the private key. The information encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. The private key is kept secret,and the public key may be distributed widely. The private key cannot be practically derived from the public key. Asymmetric key algorithms include RSAand ECDSA.
The asymmetric key algorithms can be used for the following purposes:
· To encrypt and decrypt data—Any public key receiver can use the public key to encrypt information, but only the private key owner can decrypt the information. This mechanism ensuresconfidentiality.Only RSA can be used for data encryption and decryption.
· To authenticate a sender—Also called "digital signature."The key owner uses the private key to "sign"information to be sent, and the receiver decrypts the information with the sender's public keyto verify information authenticity.RSA and ECDSAcan be used for digital signature.
Asymmetric key algorithms are widely used in variousapplications.For example, SSH, SSL, and PKI use the algorithms for digital signature. For information about SSH, SSL, and PKI, see "Configuring SSH,""Configuring SSL," and "Configuring PKI."
Configuration task list
Public keyconfiguration tasks enable you to manage the local asymmetric key pairs and configure the peer host public keys on the local device. By completing these tasks, the local device is ready to work with applications such as SSH and SSL to implement data encryption/decryption, or digital signature.
Complete these tasks to configure public keys:
|
Task |
Remarks |
|
|
Configuring a local asymmetric key pair on the local device |
Choose one or more tasks. |
|
Creating a local asymmetric key pair
When you create an asymmetric key pair on the local device, follow these guidelines:
· Create an asymmetric key pair of the proper type to work with a target application.
· After you enter the command, specify a proper modulus length for the key pair.The following table compares thesetypes of key pairs.
Table 1 A comparison between different types of asymmetric key pairs
|
Type |
Number of key pairs |
Modulus length |
Remarks |
|
RSA |
Two key pairs, one server key pair and one host key pair. Each key pair comprises a public key and a private key. |
512 to 2048 bits. 1024 by default. |
To achieve high security, specify at least 768 bits. |
|
ECDSA |
One key pair, the host key pair. |
192 bits. |
N/A |
|
|
IMPORTANT: Only SSH1.5 uses the RSA server key pair. |
To create a localasymmetric key pair:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a localasymmetric key pair. |
public-key local create { ecdsa | rsa } |
By default, no asymmetrickey pair is created. |
Displaying or exporting the local host public key
In some applications, such asSSH, to allow your local deviceto be authenticated by a peerdevicethrough digital signature, you must display or export the local host public key, which will then be specified on the peer device.
To display or export the local host public key, choose one of the following methods:
· Displaying and recording the host public key information
· Displaying the host public key in a specific format and saving it to a file
· Exporting the host public key in a specific format to a file
If your local device functions to authenticate the peer device, you must specify thepeer public key on the local device. For more information, see "Specifying the peer public key on the local device."
Displaying and recording the host public key information
|
Task |
Command |
Remarks |
|
Display the local RSA public keys. |
display public-key localrsapublic[ | { begin | exclude | include } regular-expression ] |
Available in any view. Use at least one command. |
|
Display the local ECDSA host public key. |
display public-key localecdsapublic[ | { begin | exclude | include } regular-expression ] |
The display public-key localrsapublic command displays both the RSA server and host public keys. Recording the RSA host public key is enough.
After you display the host public key, record the key information for manually configuration of the key on the peer device.
Displaying the host public key in a specific format and saving it to a file
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Display the local RSA host public key ina specific format. |
public-key local export rsa { openssh |ssh1 |ssh2 } |
After you display the host public key in a specific format, save the key to a file, and transfer the file to the peer device.
Exporting the host public key in a specific format to a file
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Export the local RSA host public key in a specific format to a file. |
public-key local export rsa { openssh |ssh1 |ssh2 } filename |
After you export the host public key in a specific format to a file, transfer the file to the peer device.
Destroying a local asymmetric key pair
You may haveto destroy a local asymmetric key pair and generate a new pair when an intrusion event has occurred, the storage media of the device is replaced, the asymmetric key has been used for a long time, or the local certificate expires. For more information about the local certificate, see "Configuring PKI."
To destroy a localasymmetric key pair:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Destroy a local asymmetric key pair. |
public-key local destroy { ecdsa|rsa } |
Specifying the peer public key on the local device
In SSH, toenablethe local device to authenticate a peer device, specify the peer public key on the local device. The device supports up to 20 peer public keys.
For information about displaying or exporting the host public key, see "Displaying or exporting the local host public key."
To specify the peer public key on the local device:
|
Method |
Prerequisites |
Remarks |
|
Import the public key from a public key file (recommended) |
1. Save the host public key of the intended asymmetric key pair in a file. 2. Transfer a copy of the file through FTP or TFTP in binary mode to the local device. |
During the import process, the system automatically converts the public key to a string in Public Key Cryptography Standards (PKCS) format. |
|
Manually configure the public key—input or copy the key data |
· Display and record the public key of the intended asymmetric key pair. · If the peer device is an H3C device, use the display public-key local public command to view and record its public key. A public key displayed by other methods for the H3C device may not be in a correct format. |
· The recorded public key must be in the correct format, or the manual configuration of a format-incompliant public key will fail. · Always use the first method if you are not sure about the format of the recorded public key. |
To import thehost public key from a public key filetothe local device:
|
Step |
Command |
|
1. Enter system view. |
system-view |
|
2. Import the host public key from the public key file. |
public-key peerkeynameimport sshkeyfilename |
Tomanually configure the peer public keyon the local device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specifya name for the public key and enter public key view. |
public-key peer keyname |
N/A |
|
3. Enter public key code view. |
public-key-code begin |
N/A |
|
4. Configure the peer public key. |
Type or copythe key |
Spaces and carriage returns are allowed between characters. |
|
5. Return to public key view. |
public-key-code end |
When you exit public key code view, the system automatically saves the public key. |
|
6. Return to system view. |
peer-public-key end |
N/A |
Displaying public keys
|
Task |
Command |
Remarks |
|
Display the local public keys |
display public-key local {ecdsa| rsa} public [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
|
Display the specified or all peer public keys on the local device. |
display public-key peer [brief | name publickey-name] [ | { begin | exclude | include } regular-expression ] |
Available in any view. |
Public key configuration examples
See "Configuring SSH" and Fundamentals Configuration Guide.
