- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 02-DPI engine configuration | 81.77 KB |
Contents
DPI engine configuration task list
Configure a DPI application profile
Activating policy and rule configurations for DPI service modules
Configuring action parameter profiles
Configuring a block source parameter profile
Configuring a capture parameter profile
Configuring a logging parameter profile
Configuring a redirect parameter profile
Configuring an email parameter profile
Specifying a proxy server for online DPI service signature update
Enabling inspection suspension upon excessive CPU usage
Configuring stream fixed length inspection
Displaying and maintaining DPI engine
Configuring DPI engine
Overview
DPI engine is an inspection module shared by DPI service modules, such as IPS. DPI engine uses inspection rules to identify the application layer information. DPI service modules process packets based on the inspection results. Packets are inspected by the DPI engine once and are processed by multiple DPI service modules. With DPI engine, the DPI service modules do not need to inspect packets separately, which prevents degrading device performance.
DPI engine provides the following functions:
· Protocol parsing—Identifies the application layer protocols and analyzes the application layer information. Information analysis includes recognizing, normalizing, and uncompressing application layer fields.
· AC pattern matching—Matches packet payloads by the Aho-Corasick (AC) patterns in inspection rules. AC pattern matching is fast and it is the core function of the DPI engine.
· Option matching—Matches packet payloads by the options in the inspection rules whose AC patterns have been matched. Option matching is slower than AC pattern matching.
DPI engine inspection rules
DPI engine uses inspection rules to match packets. Inspection rules are transformed from the rules or signatures of the DPI service modules. The match criteria in an inspection rule can contain the following types:
· AC pattern—Criteria that identify packet signatures. An AC pattern is a character string that is three or more bytes long.
· option—Criteria other than AC patterns. For example, an option can be the port number or protocol type.
An inspection rule must contain an option, but it does not necessarily contain an AC pattern. If an inspection rule contains both AC patterns and options, the rule is matched if both its AC patterns and options are matched.
DPI engine mechanism
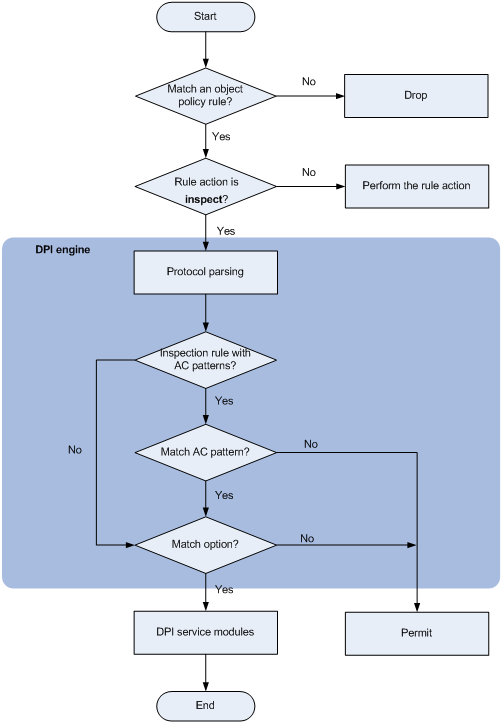
As shown in Figure 1, DPI engine works as follows:
1. Upon receiving a packet, the device compares the packet against the object policy rules.
¡ If a matching rule is found and the rule action is inspect, the device forwards the packet to the DPI engine.
¡ If a matching rule is found and the rule action is drop or pass, the device processes the packet according to the action.
¡ If no matching rule is found, the device drops the packet.
For more information about the object policy, see Security Configuration Guide.
2. The DPI engine performs protocol parsing for the packet and searches for applicable inspection rules according to the parsing results.
3. If an applicable inspection rule contains AC patterns, DPI engine performs AC pattern matching. If an applicable inspection rule does not contain AC patterns, DPI engine directly performs option matching. The packet matches the rule if it matches the options.
4. If the packet matches an AC pattern in an applicable inspection rule, the DPI engine further compares the packet against the options in the rule. The packet matches the rule if it matches the options.
5. If the packet matches an inspection rule, the DPI engine informs the corresponding DPI service modules to process the packet. If the packet does not match any rule, the DPI engine allows the packet to pass.
DPI engine configuration task list
|
Task at a glance |
|
(Required.) Configure a DPI application profile |
|
(Required.) Activating policy and rule configurations for DPI service modules |
|
(Optional.) Configuring action parameter profiles |
|
(Optional.) Optimizing the DPI engine |
|
(Optional.) Specifying a proxy server for online DPI service signature update |
|
(Optional.) Disabling the DPI engine |
|
(Optional.) Enabling inspection suspension upon excessive CPU usage |
|
(Optional.) Configuring stream fixed length inspection |
Configure a DPI application profile
The DPI application profile is a security service template that can include DPI service policies, such as IPS policy. A DPI application profile takes effect after an object policy rule uses it as the action. DPI engine inspects the packets matching the object policy rule. DPI service modules process the packets matching the DPI engine inspection rules.
To configure a DPI application profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a DPI application profile and enter its view. |
app-profile profile-name |
By default, no DPI application profiles exist. |
|
3. Specify an IPS policy. |
ips apply policy policy-name mode { protect | alert } |
For more information about this command, see DPI Command Reference. |
Activating policy and rule configurations for DPI service modules
This task validates the policy and rule configurations for DPI service modules without rebooting the device. The operation produces the same effect as saving the configurations and rebooting the device.
This task can cause temporary service disruptions. As a best practice, perform it after all DPI service policy and rule configurations are complete.
To activate policy and rule configurations for DPI service modules:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Activate policy and rule configurations for DPI service modules. |
inspect activate |
By default, the creation, modification, and deletion of DPI service policies and rules do not take effect. |
Configuring action parameter profiles
Configuring a block source parameter profile
A block source parameter profile defines the block period for the block source action in DPI service modules.
For the block period to take effect, make sure the blacklist feature is enabled.
The device drops the packet that matches an inspection rule and adds the packet's source IP address to the IP blacklist.
· If the blacklist feature is enabled, the device directly drops subsequent packets from the source IP address during the block period.
· If the blacklist feature is disabled, the block period does not take effect. The device inspects all packets and drops the matching ones.
To enable the blacklist feature, use the blacklist enable command or the blacklist global enable command. For more information about the blacklist feature, see attack detection and prevention in the Security Configuration Guide.
To configure a block source parameter profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a block source parameter profile and enter its view. |
inspect block-source parameter-profile parameter-name |
By default, no block source parameter profiles exist. |
|
3. Set the block period during which a source IP address is blocked. |
block-period period |
The default setting is 1800 seconds. |
Configuring a capture parameter profile
A capture parameter profile defines the following parameters for the packet capture action in DPI service modules:
· The maximum volume of captured packets that can be cached.
· The daily export time for cached captured packets.
· The URL to which cached captured packets are exported.
The device caches captured packets locally on the device. The device exports the cached captured packets to a URL and clears the cache at the daily export time or when the volume of cached captured packets reaches the maximum. After the export, the device starts to capture packets again.
To configure a capture parameter profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a capture parameter profile and enter its view. |
inspect capture parameter-profile parameter-name |
By default, no capture parameter profiles exist. |
|
3. Set the maximum volume of captured packets that can be cached. |
capture-limit kilobytes |
By default, the device can cache a maximum of 512 kilobytes of captured packets. |
|
4. Set the daily export time for cached captured packets. |
export repeating-at time |
By default, the cached captured packets are exported at 1:00 a.m. every day. |
|
5. Specify the URL to which cached captured packets are exported |
export url url-string |
By default, no URL is specified for exporting the cached captured packets. |
Configuring a logging parameter profile
A logging parameter profile defines the log output method for the logging action in DPI service modules.
To configure a logging parameter profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a logging parameter profile and enter its view. |
inspect logging parameter-profile parameter-name |
By default, no logging parameter profiles exist. |
|
3. Specify the log storage method. |
log { email | syslog } |
By default, the logs are exported to the information center. |
Configuring a redirect parameter profile
A redirect parameter profile defines the URL to which packets are redirected for the redirect action in DPI service modules.
To configure a redirect parameter profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a redirect parameter profile and enter its view. |
inspect logging parameter-profile parameter-name |
By default, no redirect parameter profiles exist. |
|
3. Specify the URL to which packets are redirected. |
redirect-url url-string |
By default, no URL is specified for packet redirecting. |
Configuring an email parameter profile
An email parameter profile defines the following parameters for the email action in DPI service modules:
· Email server.
· Email sender and receiver.
· Username and password for logging in to the email server.
To configure an email parameter profile:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an email parameter profile and enter its view. |
inspect email parameter-profile parameter-name |
By default, no email parameter profiles exist. |
|
3. Specify the email server. |
email-server addr-string |
By default, no email server is specified. |
|
4. Specify the DNS server address. |
dns-server ip-address |
By default, no DNS server address is specified. |
|
5. Specify the email sender address. |
sender addr-string |
By default, no email sender address is specified. |
|
6. Specify the email receiver address. |
receiver addr-string |
By default, no email receiver address is specified. |
|
7. Enable email client authentication. |
authentication enable |
By default, email client authentication is enabled. |
|
8. Enable the secure password authentication feature. |
secure-authentication enable |
By default, the secure password authentication feature is disabled. |
|
9. Specify the username for logging in to the email server. |
username name-string |
By default, no username is specified for logging in to the email server. |
|
10. Specify the password for logging in to the email server. |
password { cipher | simple } string |
By default, no password is specified for logging in to the email server. |
Optimizing the DPI engine
The DPI engine includes a series of optimization features. For example, you can enable the DPI engine to uncompress or decode the compressed or encoded packets to identify the application information of the packets. The optimization features improve inspection and accuracy of the DPI engine, but consume more system resources. You can adjust the optimization features for different scenarios to provide optimal inspection performance.
To optimize the DPI engine:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of payload-carrying packets to be inspected per data flow. |
inspect packet maximum max-number |
By default, the DPI engine can inspect a maximum of 32 payload-carrying packets per data flow. |
|
3. Set the maximum number of options to be cached per TCP/UDP data flow. |
inspect cache-option maximum max-number |
By default, the DPI engine can cache a maximum of 32 options per TCP/UDP data flow. |
|
4. Configure the TCP segment reassembly feature. |
· Enable TCP segment reassembly. · Set the maximum number of TCP segments
that can be cached for reassembly per TCP flow: |
By default: · The TCP segment reassembly feature is disabled. · A maximum of 10 TCP segments can be cached for reassembly per TCP flow. The inspect tcp-reassemble max-segment command takes effect only after the command is inspect tcp-reassemble enable configured. |
|
5. Disable a DPI engine optimization feature. |
inspect optimization [ chunk | no-acsignature | raw | uncompress | url-normalization ] disable |
All DPI engine optimization features are enabled by default. |
Specifying a proxy server for online DPI service signature update
The device must access the H3C website for online signature update of DPI services (such as IPS). If direct connectivity is not available, the device can access the H3C website through the specified proxy server. For more information about online signature update, see "Configuring IPS."
If you specify a proxy server by domain name instead of IP address, make sure the device can resolve the domain name into an IP address through DNS. For more information about DNS, see Layer 3—IP Services Configuration Guide.
To specify a proxy server for online DPI service signature update:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a proxy server for online DPI service signature update |
inspect signature auto-update proxy { domain domain-name | ip ip-address } [ port port-number ] [ user user-name password { cipher | simple } string ] |
By default, the proxy server used by DPI services for online signature update is not specified. |
Disabling the DPI engine
Packet inspection in the DPI engine is a complex and resource-consuming process. When the CPU usage is too high, you can disable the DPI engine to guarantee the device performance. After you disable the DPI engine, packets will not be processed by DPI.
To disable the DPI engine:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Disable the DPI engine. |
inspect bypass |
By default, the DPI engine is enabled. |
Enabling inspection suspension upon excessive CPU usage
Packet inspection in the DPI engine is a complex and resource-consuming process. When the device's CPU usage is below the CPU usage threshold, the DPI engine inspects the whole packet data in a stream. When the device's CPU usage reaches the threshold, inspection suspension upon excessive CPU usage is triggered and the DPI engine inspects packets as follows:
· If stream fixed length inspection is disabled, the DPI engine suspends packet inspection to guarantee the device performance.
· If stream fixed length inspection is enabled, the DPI engine inspects only a fixed length of data for a stream and ignores the remaining stream data.
If you disable this feature, the DPI engine continues to inspect the whole packet data in a stream even when the CPU usage threshold is reached. Disabling inspection suspension upon excessive CPU usage is not recommended if the device's CPU usage is high.
To enable inspection suspension upon excessive CPU usage:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable inspection suspension upon excessive CPU usage. |
undo inspect cpu-threshold disable |
By default, inspection suspension upon excessive CPU usage is enabled. |
Configuring stream fixed length inspection
The stream fixed length inspection feature enables the DPI engine to inspect only a fixed length of data for a stream when the CPU usage threshold is reached. When the device's CPU usage is below the threshold, the DPI engine inspects the whole packet data in a stream. For information about configuring the CPU usage threshold, see Fundamentals Configuration Guide.
This feature takes effect only when inspection suspension upon excessive CPU usage is enabled.
You can also disable this feature so the DPI engine can suspend packet inspection to guarantee the device performance when the CPU usage threshold is reached.
To configure the stream fixed length inspection feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable stream fixed length inspection. |
undo inspect stream-fixed-length disable |
By default, stream fixed length inspection is enabled. |
|
3. Set the fixed data inspection length for application protocols. |
inspect stream-fixed-length { email I ftp | http } * length |
The default length is 32 kilobytes for FTP, HTTP, and email protocols. The larger the inspection length value, the lower the device throughput, and the higher the packet inspection accuracy. |
Displaying and maintaining DPI engine
Execute display commands in any view.
|
Task |
Command |
|
Display the status of the DPI engine. |
display inspect status |

