- Table of Contents
-
- 06-Layer 3 - IP Services Configuration Guide
- 00-Preface
- 01-ARP configuration
- 02-IP addressing configuration
- 03-DHCP configuration
- 04-DNS configuration
- 05-NAT configuration
- 06-IP forwarding basics configuration
- 07-Fast forwarding configuration
- 08-Flow classification configuration
- 09-Adjacency table configuration
- 10-IRDP configuration
- 11-IP performance optimization configuration
- 12-UDP Helper configuration
- 13-IPv6 basics configuration
- 14-DHCPv6 configuration
- 15-IPv6 fast forwarding configuration
- 16-Tunneling configuration
- 17-GRE configuration
- 18-ADVPN configuration
- 19-AFT configuration
- 20-WAAS configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-ARP configuration | 270.73 KB |
Configuring a static ARP entry
Setting the maximum number of dynamic ARP entries for a device
Setting the maximum number of dynamic ARP entries for an interface
Setting the aging timer for dynamic ARP entries
Enabling dynamic ARP entry check
Displaying and maintaining ARP
Static ARP entry configuration example
Gratuitous ARP packet learning
Periodic sending of gratuitous ARP packets
Enabling IP conflict notification
Common proxy ARP configuration example
Displaying and maintaining ARP suppression
ARP suppression configuration example
Configuring ARP direct route advertisement
Configuring ARP
Overview
ARP resolves IP addresses into MAC addresses on Ethernet networks.
ARP message format
ARP uses two types of messages: ARP request and ARP reply. Figure 1 shows the format of ARP request/reply messages. Numbers in the figure refer to field lengths.
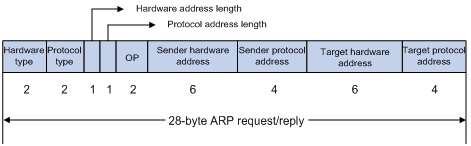
· Hardware type—Hardware address type. The value 1 represents Ethernet.
· Protocol type—Type of the protocol address to be mapped. The hexadecimal value 0x0800 represents IP.
· Hardware address length and protocol address length—Length, in bytes, of a hardware address and a protocol address. For an Ethernet address, the value of the hardware address length field is 6. For an IPv4 address, the value of the protocol address length field is 4.
· OP—Operation code, which describes the type of ARP message. The value 1 represents an ARP request, and the value 2 represents an ARP reply.
· Sender hardware address—Hardware address of the device sending the message.
· Sender protocol address—Protocol address of the device sending the message.
· Target hardware address—Hardware address of the device to which the message is being sent.
· Target protocol address—Protocol address of the device to which the message is being sent.
ARP operating mechanism
As shown in Figure 2, Host A and Host B are on the same subnet. Host A sends a packet to Host B as follows:
1. Host A looks through the ARP table for an ARP entry for Host B. If one entry is found, Host A uses the MAC address in the entry to encapsulate the IP packet into a data link layer frame. Then Host A sends the frame to Host B.
2. If Host A finds no entry for Host B, Host A buffers the packet and broadcasts an ARP request. The payload of the ARP request contains the following information:
¡ Sender IP address and sender MAC address—Host A's IP address and MAC address.
¡ Target IP address—Host B's IP address.
¡ Target MAC address—An all-zero MAC address.
All hosts on this subnet can receive the broadcast request, but only the requested host (Host B) processes the request.
3. Host B compares its own IP address with the target IP address in the ARP request. If they are the same, Host B operates as follows:
a. Adds the sender IP address and sender MAC address into its ARP table.
b. Encapsulates its MAC address into an ARP reply.
c. Unicasts the ARP reply to Host A.
4. After receiving the ARP reply, Host A operates as follows:
a. Adds the MAC address of Host B into its ARP table.
b. Encapsulates the MAC address into the packet and sends the packet to Host B.
Figure 2 ARP address resolution process

If Host A and Host B are on different subnets, Host A sends a packet to Host B as follows:
1. Host A broadcasts an ARP request where the target IP address is the IP address of the gateway.
2. The gateway responds with its MAC address in an ARP reply to Host A.
3. Host A uses the gateway's MAC address to encapsulate the packet, and then sends the packet to the gateway.
4. If the gateway has an ARP entry for Host B, it forwards the packet to Host B directly. If not, the gateway broadcasts an ARP request, in which the target IP address is the IP address of Host B.
5. After the gateway gets the MAC address of Host B, it sends the packet to Host B.
ARP table
An ARP table stores dynamic, static, OpenFlow, and Rule ARP entries.
Dynamic ARP entry
ARP automatically creates and updates dynamic entries. A dynamic ARP entry is removed when its aging timer expires or the output interface goes down. In addition, a dynamic ARP entry can be overwritten by a static ARP entry.
Static ARP entry
A static ARP entry is manually configured and maintained. It does not age out and cannot be overwritten by any dynamic ARP entry.
Static ARP entries protect communication between devices because attack packets cannot modify the IP-to-MAC mapping in a static ARP entry.
A static ARP entry contains only the IP address and MAC address.
· If the output interface is a Layer 3 Ethernet interface, the ARP entry can be directly used to forward packets.
· If the output interface is a VLAN interface, the device sends an ARP request whose target IP address is the IP address in the entry. If the sender IP and MAC addresses in the received ARP reply match the static ARP entry, the device performs the following operations:
¡ Adds the interface that received the ARP reply to the static ARP entry.
¡ Uses the resolved static ARP entry to forward IP packets.
To communicate with a host by using a fixed IP-to-MAC mapping, configure a static ARP entry on the device.
OpenFlow ARP entry
ARP creates OpenFlow ARP entries by learning from the OpenFlow module. An OpenFlow ARP entry does not age out, and it cannot be updated. It can be overwritten by a static ARP entry. An OpenFlow ARP entry can be used directly to forward packets. For more information about OpenFlow, see OpenFlow Configuration Guide.
Rule ARP entry
ARP creates Rule ARP entries by learning from the IPoE, portal, and VXLAN modules. A Rule ARP entry does not age out, and it cannot be updated. It can be overwritten by a static ARP entry. A Rule ARP entry can be used directly to forward packets.
For more information about IPoE, see Layer 2—WAN Access Configuration Guide. For more information about portal, see Security Configuration Guide. For more information about VXLAN, see VXLAN Configuration Guide.
Configuring a static ARP entry
Static ARP entries are effective when the device functions correctly.
To configure a static ARP entry:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static ARP entry. |
arp static ip-address mac-address [ vpn-instance vpn-instance-name ] |
By default, no static ARP entries exist. |
Setting the maximum number of dynamic ARP entries for a device
A device can dynamically learn ARP entries. To prevent a device from holding too many ARP entries, you can set the maximum number of dynamic ARP entries that the device can learn. When the maximum number is reached, the device stops learning ARP entries.
If you set a value lower than the number of existing dynamic ARP entries, the device does not remove the existing entries unless they are aged out.
To set the maximum number of dynamic ARP entries for a device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of dynamic ARP entries for the device. |
· In standalone mode: · In IRF mode: |
By default, the maximum number of dynamic ARP entries that a device can learn is the upper limit of the allowed value range. To disable the device from learning dynamic ARP entries, set the number to 0. |
Setting the maximum number of dynamic ARP entries for an interface
An interface can dynamically learn ARP entries. To prevent an interface from holding too many ARP entries, you can set the maximum number of dynamic ARP entries that the interface can learn. When the maximum number is reached, the interface stops learning ARP entries.
You can set limits for both a Layer 2 interface and the VLAN interface for a permitted VLAN on the Layer 2 interface. The Layer 2 interface learns an ARP entry only when neither limit is reached.
The total number of dynamic ARP entries that all interfaces learn will not be larger than the maximum number of dynamic ARP entries set for the device.
To set the maximum number of dynamic ARP entries for an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the maximum number of dynamic ARP entries for the interface. |
arp max-learning-num max-number |
By default, the maximum number of dynamic ARP entries that an interface can learn is the upper limit of the allowed value range. To disable the interface from learning dynamic ARP entries, set the number to 0. |
Setting the aging timer for dynamic ARP entries
Each dynamic ARP entry in the ARP table has a limited lifetime, called an aging timer. The aging timer of a dynamic ARP entry is reset each time the dynamic ARP entry is updated. A dynamic ARP entry that is not updated before its aging timer expires is deleted from the ARP table.
To set the aging timer for dynamic ARP entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the aging timer for dynamic ARP entries. |
arp timer aging aging-time |
The default setting is 20 minutes. |
Enabling dynamic ARP entry check
The dynamic ARP entry check feature disables the device from supporting dynamic ARP entries that contain multicast MAC addresses. The device cannot learn dynamic ARP entries containing multicast MAC addresses. You cannot manually add static ARP entries containing multicast MAC addresses.
When dynamic ARP entry check is disabled, ARP entries containing multicast MAC addresses are supported. The device can learn dynamic ARP entries containing multicast MAC addresses obtained from the ARP packets sourced from a unicast MAC address. You can also manually add static ARP entries containing multicast MAC addresses.
To enable dynamic ARP entry check:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable dynamic ARP entry check. |
arp check enable |
By default, dynamic ARP entry check is enabled. |
Enabling ARP logging
This feature enables a device to log ARP events when ARP cannot resolve IP addresses correctly. The device can log the following ARP events:
· On a proxy ARP-disabled interface, the target IP address of a received ARP packet is not one of the following IP addresses:
¡ The IP address of the receiving interface.
¡ The virtual IP address of the VRRP group.
¡ The public IP address after NAT.
· The sender IP address of a received ARP reply conflicts with one of the following IP addresses:
¡ The IP address of the receiving interface.
¡ The virtual IP address of the VRRP group.
¡ The public IP address after NAT.
The device sends ARP log messages to the information center. You can use the info-center source command to specify the log output rules for the information center. For more information about information center, see Network Management and Monitoring Configuration Guide.
To enable the ARP logging feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the ARP logging feature. |
arp check log enable |
By default, ARP logging is disabled. |
Displaying and maintaining ARP
|
|
IMPORTANT: Clearing ARP entries from the ARP table might cause communication failures. Make sure the entries to be cleared do not affect current communications. |
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display ARP entries (in standalone mode). |
display arp [ [ all | dynamic | static ] [ slot slot-number ] | vlan vlan-id | interface interface-type interface-number ] [ count | verbose ] |
|
Display ARP entries (in IRF mode). |
display arp [ [ all | dynamic | static ] [ chassis chassis-number slot slot-number ] | vlan vlan-id | interface interface-type interface-number ] [ count | verbose ] |
|
Display the ARP entry for an IP address (in standalone mode). |
display arp ip-address [ slot slot-number ] [ verbose ] |
|
Display the ARP entry for an IP address (in IRF mode). |
display arp ip-address [ chassis chassis-number slot slot-number ] [ verbose ] |
|
Display the ARP entries for a VPN instance. |
display arp vpn-instance vpn-instance-name [ count ] |
|
Display the aging timer of dynamic ARP entries. |
display arp timer aging |
|
Clear ARP entries from the ARP table (in standalone mode). |
reset arp { all | dynamic | interface interface-type interface-number | slot slot-number | static } |
|
Clear ARP entries from the ARP table (in IRF mode). |
reset arp { all | chassis chassis-number slot slot-number | dynamic | interface interface-type interface-number | static } |
Static ARP entry configuration example
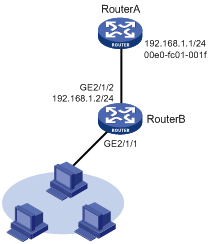
Network requirements
As shown in Figure 3, hosts are connected to Router B. Router B is connected to Router A through interface GigabitEthernet 2/1/2.
To ensure secure communications between Router B and Router A, configure a static ARP entry for Router A on Router B.
Configuration procedure
# Configure an IP address for GigabitEthernet 2/1/2.
<RouterB> system-view
[RouterB] interface gigabitethernet 2/1/2
[RouterB-GigabitEthernet2/1/2] ip address 192.168.1.2 24
[RouterB-GigabitEthernet2/1/2] quit
# Configure a static ARP entry that has IP address 192.168.1.1 and MAC address 00e0-fc01-001f.
[RouterB] arp static 192.168.1.1 00e0-fc01-001f
Verifying the configuration
# Verify that Router B has a static ARP entry for Router A.
[RouterB] display arp static
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address SVID Interface Aging Type
192.168.1.1 00e0-fc01-001f -- -- -- S
Configuring gratuitous ARP
Overview
In a gratuitous ARP packet, the sender IP address and the target IP address are the IP address of the sending device.
A device sends a gratuitous ARP packet for either of the following purposes:
· Determine whether its IP address is already used by another device. If the IP address is already used, the device is informed of the conflict by an ARP reply.
· Inform other devices of a MAC address change.
Gratuitous ARP packet learning
This feature enables a device to create or update ARP entries by using the sender IP and MAC addresses in received gratuitous ARP packets.
When this feature is disabled, the device uses received gratuitous ARP packets to update existing ARP entries only. ARP entries are not created based on the received gratuitous ARP packets, which saves ARP table space.
Periodic sending of gratuitous ARP packets
Enabling periodic sending of gratuitous ARP packets helps downstream devices update ARP entries or MAC entries in a timely manner.
This feature can implement the following functions:
· Prevent gateway spoofing.
Gateway spoofing occurs when an attacker uses the gateway address to send gratuitous ARP packets to the hosts on a network. The traffic destined for the gateway from the hosts is sent to the attacker instead. As a result, the hosts cannot access the external network.
To prevent such gateway spoofing attacks, you can enable the gateway to send gratuitous ARP packets at intervals. Gratuitous ARP packets contain the primary IP address and manually configured secondary IP addresses of the gateway, so hosts can learn correct gateway information.
· Prevent ARP entries from aging out.
If network traffic is heavy or if the host CPU usage is high, received ARP packets can be discarded or are not promptly processed. Eventually, the dynamic ARP entries on the receiving host age out. The traffic between the host and the corresponding devices is interrupted until the host re-creates the ARP entries.
To prevent this problem, you can enable the gateway to send gratuitous ARP packets periodically. Gratuitous ARP packets contain the primary IP address and manually configured secondary IP addresses of the gateway, so the receiving hosts can update ARP entries in a timely manner.
· Prevent the virtual IP address of a VRRP group from being used by a host.
The master router of a VRRP group can periodically send gratuitous ARP packets to the hosts on the local network. The hosts can then update local ARP entries and avoid using the virtual IP address of the VRRP group. The sender MAC address in the gratuitous ARP packet is the virtual MAC address of the virtual router. For more information about VRRP, see High Availability Configuration Guide.
· Update MAC entries of devices in the VLANs having ambiguous Dot1q or QinQ termination configured.
In VRRP configuration, if ambiguous Dot1q or QinQ termination is configured for multiple VLANs and VRRP groups, interfaces configured with VLAN termination must be disabled from transmitting broadcast/multicast packets. Also, a VRRP control VLAN must be configured so that VRRP advertisements can be transmitted within the control VLAN only. In such cases, you can enable periodic sending of gratuitous ARP packets containing the following addresses:
¡ The VRRP virtual IP address.
¡ The primary IP address or a manually configured secondary IP address of the sending interface on the subinterfaces.
When a VRRP failover occurs, devices in the VLANs can use the gratuitous ARP packets to update their corresponding MAC entries in a timely manner. For more information about ambiguous Dot1q or QinQ termination, see Layer 2—LAN Switching Configuration Guide.
Configuration procedure
When you configure gratuitous ARP, follow these restrictions and guidelines:
· You can enable periodic sending of gratuitous ARP packets on a maximum of 1024 interfaces.
· Periodic sending of gratuitous ARP packets takes effect on an interface only when the following conditions are met:
¡ The data link layer state of the interface is up.
¡ The interface has an IP address.
· If you change the sending interval for gratuitous ARP packets, the configuration takes effect at the next sending interval.
· The sending interval for gratuitous ARP packets might be much longer than the specified sending interval in any of the following circumstances:
¡ This feature is enabled on multiple interfaces.
¡ Each interface is configured with multiple secondary IP addresses.
¡ A small sending interval is configured when the previous two conditions exist.
To configure gratuitous ARP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable learning of gratuitous ARP packets. |
gratuitous-arp-learning enable |
By default, learning of gratuitous ARP packets is enabled. |
|
3. Enable the device to send gratuitous ARP packets upon receiving ARP requests whose sender IP address belongs to a different subnet. |
gratuitous-arp-sending enable |
By default, a device does not send gratuitous ARP packets upon receiving ARP requests whose sender IP address belongs to a different subnet. |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable periodic sending of gratuitous ARP packets. |
arp send-gratuitous-arp [ interval interval ] |
By default, periodic sending of gratuitous ARP packets is disabled. |
Enabling IP conflict notification
By default, if the sender IP address of an incoming ARP packet is the same as that of the device, the device sends a gratuitous ARP request. The device displays an error message only after it receives an ARP reply about the conflict.
You can use this command to enable the device to display error messages before sending a gratuitous ARP reply or request for conflict confirmation.
To enable IP conflict notification:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP conflict notification. |
arp ip-conflict log prompt |
By default, IP conflict notification is disabled. |
Configuring proxy ARP
Proxy ARP enables a device on one network to answer ARP requests for an IP address on another network. With proxy ARP, hosts on different broadcast domains can communicate with each other as they would on the same broadcast domain.
Proxy ARP includes common proxy ARP and local proxy ARP.
· Common proxy ARP—Allows communication between hosts that connect to different Layer 3 interfaces and reside in different broadcast domains.
· Local proxy ARP—Allows communication between hosts that connect to the same Layer 3 interface and reside in different broadcast domains.
Enabling common proxy ARP
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
The following interface types are supported: · Layer 3 Ethernet interface. · Layer 3 Ethernet subinterface. · Layer 3 aggregate interface. · Layer 3 aggregate subinterface. |
|
3. Enable common proxy ARP. |
proxy-arp enable |
By default, common proxy ARP is disabled. |
Enabling local proxy ARP
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
The following interface types are supported: · Layer 3 Ethernet interface. · Layer 3 Ethernet subinterface. · Layer 3 aggregate interface. · Layer 3 aggregate subinterface. |
|
3. Enable local proxy ARP. |
local-proxy-arp enable [ ip-range start-ip-address to end-ip-address ] |
By default, local proxy ARP is disabled. |
Displaying proxy ARP
Execute display commands in any view.
|
Task |
Command |
|
Display common proxy ARP status. |
display proxy-arp [ interface interface-type interface-number ] |
|
Display local proxy ARP status. |
display local-proxy-arp [ interface interface-type interface-number ] |
Common proxy ARP configuration example
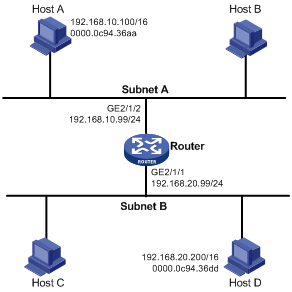
Network requirements
As shown in Figure 4, Host A and Host D have the same prefix and mask, but they are located on different subnets. No default gateway is configured on Host A and Host D.
Configure common proxy ARP on the router to enable communication between Host A and Host D.
Configuration procedure
# Configure the IP address of interface GigabitEthernet 2/1/2.
<Router> system-view
[Router] interface gigabitethernet 2/1/2
[Router-GigabitEthernet2/1/2] ip address 192.168.10.99 255.255.255.0
# Enable common proxy ARP on interface GigabitEthernet 2/1/2.
[Router-GigabitEthernet2/1/2] proxy-arp enable
[Router-GigabitEthernet2/1/2] quit
# Configure the IP address of interface GigabitEthernet 2/1/1.
[Router] interface gigabitethernet 2/1/1
[Router-GigabitEthernet2/1/1] ip address 192.168.20.99 255.255.255.0
# Enable common proxy ARP on interface GigabitEthernet 2/1/1.
[Router-GigabitEthernet2/1/1] proxy-arp enable
[Router-GigabitEthernet2/1/1] quit
Verifying the configuration
# Verify that Host A and Host D can ping each other.
Configuring ARP suppression
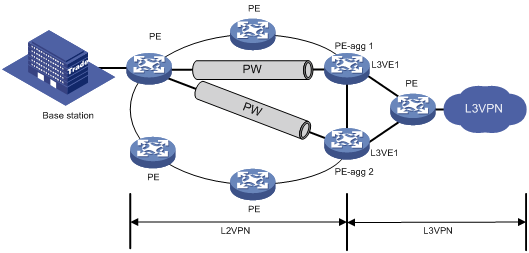
Overview
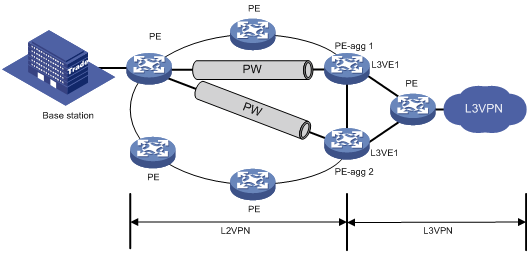
The ARP suppression feature enables a device to directly answer ARP requests by using ARP suppression entries. The device generates ARP suppression entries based on dynamic ARP entries that it learns. This feature is typically configured on the PEs connected to base stations in an MPLS L2VPN that provides access to an L3VPN network.
You can also configure the ARP suppression push feature to push ARP suppression entries by broadcasting gratuitous ARP packets.
Figure 5 shows a typical application scenario. ARP suppression is enabled on the PE that connects to the base station. The PE generates ARP suppression entries for the base station, PE-agg 1, and PE-agg 2, and it directly replies subsequent ARP requests for these devices.
Configuration procedure
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a cross-connect group and enter its view. |
xconnect-group group-name |
By default, no cross-connect groups exist. For more information about this command, see MPLS Command Reference. |
|
3. Create a cross-connect and enter its view. |
connection connection-name |
By default, no cross-connects exist. For more information about this command, see MPLS Command Reference. |
|
4. Enable ARP suppression. |
arp suppression enable |
By default, ARP suppression is disabled. |
|
5. Return to cross-connect group view. |
quit |
N/A |
|
6. Return to system view. |
quit |
N/A |
|
7. (Optional.) Enable the ARP suppression push feature and set a push interval. |
arp suppression push interval interval |
By default, the ARP suppression push feature is disabled. |
Displaying and maintaining ARP suppression
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display ARP suppression entries (in standalone mode). |
display arp suppression xconnect-group [ name group-name ] [ slot slot-number ] [ count ] |
|
Display ARP suppression entries (in IRF mode). |
display arp suppression xconnect-group [ name group-name ] [ chassis chassis-number slot slot-number ] [ count ] |
|
Clear dynamic ARP suppression entries (in standalone mode). |
reset arp suppression xconnect-group [ name group-name ] [ slot slot-number ] |
|
Clear dynamic ARP suppression entries (in IRF mode). |
reset arp suppression xconnect-group [ name group-name ] [ chassis chassis-number slot slot-number ] |
ARP suppression configuration example
Network requirements
As shown in Figure 6, the base station, Router A, and Router B are in an MPLS L2VPN.
Enable ARP suppression on Router A to directly reply to ARP requests for Router B.
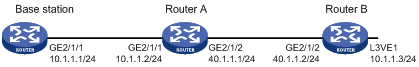
Configuration procedure
1. Configure IP addresses for the interfaces, and make sure the base station can reach the L3VE interface VE-L3VPN 1 of Router B. (Details not shown.)
2. Configure ARP suppression on Router A:
# Create a cross-connect group named vpna and create a cross-connect named svc in the group.
<RouterA> system-view
[RouterA] xconnect-group vpna
[RouterA-xcg-vpna] connection svc
# Enable ARP suppression for the cross-connect svc in cross-connect group vpna.
[RouterA-xcg-vpna-svc] arp suppression enable
Verifying the configuration
1. On the base station, clear ARP entries, and ping the L3VE interface VE-L3VPN 1 of Router B. (Details not shown.)
2. Verify that Router A has ARP suppression entries for the base station and Router B.
[RouterA-xcg-vpna-svc] display arp suppression xconnect-group
IP address MAC address Xconnect-group Connection Aging
10.1.1.1 00e0-fc04-582c vpna svc 25
10.1.1.3 0023-89b7-0861 vpna svc 25
3. Enable ARP debugging on Router B to verify that Router B does not receive an ARP request from the base station under the following conditions (details not shown):
a. Clear ARP entries on the base station.
b. Ping the L3VE interface VE-L3VPN 1 of Router B from the base station.
Configuring ARP direct route advertisement
Overview
The ARP direct route advertisement feature advertises host routes instead of advertising the network route. This feature is typically configured on PE-aggs to advertise host routes to the connected PEs in the L3VPN.
Figure 7 shows a typical application scenario where the PE in the L3VPN has ECMP routes destined to a base station in the L2VPN. Traffic from the PE in the L3VPN to the base station can be load shared by PE-agg 1 and PE-agg 2. If PE-agg 1 fails, the PE uses the host route through PE-agg 2 to forward traffic.
Configuration procedure
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an L3VE interface and enter its view. |
interface ve-l3vpn interface-number |
By default, no L3VE interface exists. For more information about this command, see MPLS Command Reference. |
|
3. Enable the ARP direct route advertisement feature. |
arp route-direct advertise |
By default, the ARP direct route advertisement feature is disabled. |

