- Table of Contents
-
- 09 Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Portal configuration
- 05-Port security configuration
- 06-Password control configuration
- 07-Public key management
- 08-PKI configuration
- 09-IPsec configuration
- 10-SSH configuration
- 11-SSL configuration
- 12-IP source guard configuration
- 13-ARP attack protection configuration
- 14-MFF configuration
- 15-uRPF configuration
- 16-Crypto engine configuration
- 17-FIPS configuration
- 18-Attack detection and prevention configuration
- 19-ND attack defense configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-AAA configuration | 652.99 KB |
AAA implementation on the device
AAA configuration considerations and task list
Configuring AAA methods for ISP domains
Configuring authentication methods for an ISP domain
Configuring authorization methods for an ISP domain
Configuring accounting methods for an ISP domain
Enabling the session-control feature
Setting the maximum number of concurrent login users
Displaying and maintaining AAA
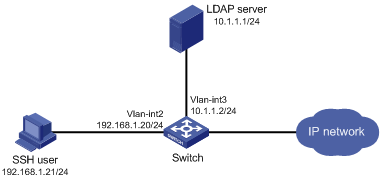
AAA for SSH users by an HWTACACS server
Local authentication, HWTACACS authorization, and RADIUS accounting for SSH users
Authentication and authorization for SSH users by a RADIUS server
Authentication for SSH users by an LDAP server
RADIUS packet delivery failure
Overview
Authentication, Authorization, and Accounting (AAA) provides a uniform framework for implementing network access management. This feature specifies the following security functions:
· Authentication—Identifies users and verifies their validity.
· Authorization—Grants different users different rights, and controls the users' access to resources and services. For example, you can permit office users to read and print files and prevent guests from accessing files on the device.
· Accounting—Records network usage details of users, including the service type, start time, and traffic. This function enables time-based and traffic-based charging and user behavior auditing.
AAA uses a client/server model. The client runs on the access device, or the network access server (NAS), which authenticates user identities and controls user access. The server maintains user information centrally. See Figure 1.
Figure 1 AAA network diagram
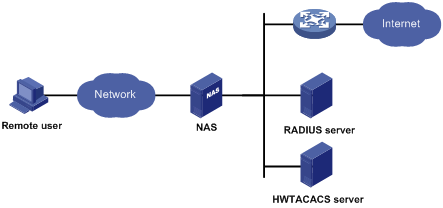
To access networks or resources beyond the NAS, a user sends its identity information to the NAS. The NAS transparently passes the user information to AAA servers and waits for the authentication, authorization, and accounting result. Based on the result, the NAS determines whether to permit or deny the access request.
AAA has various implementations, including RADIUS, HWTACACS, and LDAP. RADIUS is most often used.
The network in Figure 1 has one RADIUS server and one HWTACACS server. You can use different servers to implement different security functions. For example, you can use the HWTACACS server for authentication and authorization, and use the RADIUS server for accounting.
You can choose the security functions provided by AAA as needed. For example, if your company wants employees to be authenticated before they access specific resources, you would deploy an authentication server. If network usage information is needed, you would also configure an accounting server.
The device performs dynamic password authentication.
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a distributed information interaction protocol that uses a client/server model. The protocol can protect networks against unauthorized access and is often used in network environments that require both high security and remote user access.
The RADIUS authorization process is combined with the RADIUS authentication process, and user authorization information is piggybacked in authentication responses. RADIUS uses UDP port 1812 for authentication and UDP port 1813 for accounting.
RADIUS was originally designed for dial-in user access, and has been extended to support additional access methods, such as Ethernet and ADSL.
Client/server model
The RADIUS client runs on the NASs located throughout the network. It passes user information to RADIUS servers and acts on the responses to, for example, reject or accept user access requests.
The RADIUS server runs on the computer or workstation at the network center and maintains information related to user authentication and network service access.
The RADIUS server operates using the following process:
1. Receives authentication, authorization, and accounting requests from RADIUS clients.
2. Performs user authentication, authorization, or accounting.
3. Returns user access control information (for example, rejecting or accepting the user access request) to the clients.
The RADIUS server can also act as the client of another RADIUS server to provide authentication proxy services.
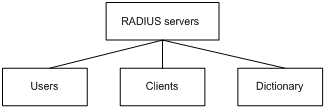
The RADIUS server maintains the following databases:
· Users—Stores user information, such as the usernames, passwords, applied protocols, and IP addresses.
· Clients—Stores information about RADIUS clients, such as shared keys and IP addresses.
· Dictionary—Stores RADIUS protocol attributes and their values.
Figure 2 RADIUS server databases
Information exchange security mechanism
The RADIUS client and server exchange information between them with the help of shared keys, which are preconfigured on the client and server. A RADIUS packet has a 16-byte field called Authenticator. This field includes a signature generated by using the MD5 algorithm, the shared key, and some other information. The receiver of the packet verifies the signature and accepts the packet only when the signature is correct. This mechanism ensures the security of information exchanged between the RADIUS client and server.
The shared keys are also used to encrypt user passwords that are included in RADIUS packets.
User authentication methods
The RADIUS server supports multiple user authentication methods, such as PAP, CHAP, and EAP.
Basic RADIUS packet exchange process
Figure 3 illustrates the interactions between a user host, the RADIUS client, and the RADIUS server.
Figure 3 Basic RADIUS packet exchange process
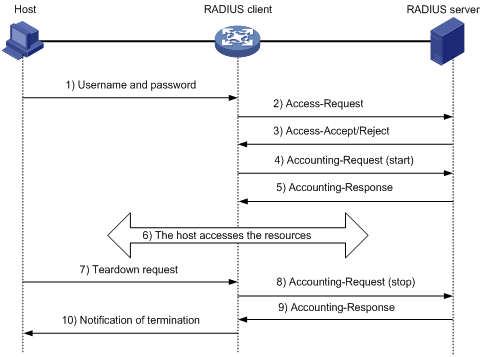
RADIUS uses the following workflow:
1. The host sends a connection request that includes the user's username and password to the RADIUS client.
2. The RADIUS client sends an authentication request (Access-Request) to the RADIUS server. The request includes the user's password, which has been processed by the MD5 algorithm and shared key.
3. The RADIUS server authenticates the username and password. If the authentication succeeds, the server sends back an Access-Accept packet that contains the user's authorization information. If the authentication fails, the server returns an Access-Reject packet.
4. The RADIUS client permits or denies the user according to the authentication result. If the result permits the user, the RADIUS client sends a start-accounting request (Accounting-Request) packet to the RADIUS server.
5. The RADIUS server returns an acknowledgment (Accounting-Response) packet and starts accounting.
6. The user accesses the network resources.
7. The host requests the RADIUS client to tear down the connection.
8. The RADIUS client sends a stop-accounting request (Accounting-Request) packet to the RADIUS server.
9. The RADIUS server returns an acknowledgment (Accounting-Response) and stops accounting for the user.
10. The RADIUS client notifies the user of the termination.
RADIUS packet format
RADIUS uses UDP to transmit packets. The protocol also uses a series of mechanisms to ensure smooth packet exchange between the RADIUS server and the client. These mechanisms include the timer mechanism, the retransmission mechanism, and the backup server mechanism.
Figure 4 RADIUS packet format
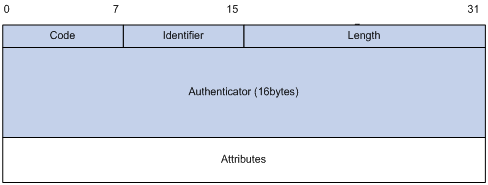
Descriptions of the fields are as follows:
· The Code field (1 byte long) indicates the type of the RADIUS packet. Table 1 gives the main values and their meanings.
Table 1 Main values of the Code field
|
Code |
Packet type |
Description |
|
1 |
Access-Request |
From the client to the server. A packet of this type includes user information for the server to authenticate the user. It must contain the User-Name attribute and can optionally contain the attributes of NAS-IP-Address, User-Password, and NAS-Port. |
|
2 |
Access-Accept |
From the server to the client. If all attribute values included in the Access-Request are acceptable, the authentication succeeds, and the server sends an Access-Accept response. |
|
3 |
Access-Reject |
From the server to the client. If any attribute value included in the Access-Request is unacceptable, the authentication fails, and the server sends an Access-Reject response. |
|
4 |
Accounting-Request |
From the client to the server. A packet of this type includes user information for the server to start or stop accounting for the user. The Acct-Status-Type attribute in the packet indicates whether to start or stop accounting. |
|
5 |
Accounting-Response |
From the server to the client. The server sends a packet of this type to notify the client that it has received the Accounting-Request and has successfully recorded the accounting information. |
· The Identifier field (1 byte long) is used to match response packets with request packets and to detect duplicate request packets. The request and response packets of the same exchange process for the same purpose (such as authentication or accounting) have the same identifier.
· The Length field (2 bytes long) indicates the length of the entire packet (in bytes), including the Code, Identifier, Length, Authenticator, and Attributes fields. Bytes beyond this length are considered padding and are ignored by the receiver. If the length of a received packet is less than this length, the packet is dropped.
· The Authenticator field (16 bytes long) is used to authenticate responses from the RADIUS server and to encrypt user passwords. There are two types of authenticators: request authenticator and response authenticator.
· The Attributes field (variable in length) includes authentication, authorization, and accounting information. This field can contain multiple attributes, each with the following subfields:
¡ Type—Type of the attribute.
¡ Length—Length of the attribute in bytes, including the Type, Length, and Value subfields.
¡ Value—Value of the attribute. Its format and content depend on the Type subfield.
Commonly used RADIUS attributes are defined in RFC 2865, RFC 2866, RFC 2867, and RFC 2868. For more information, see "Commonly used standard RADIUS attributes."
Table 2 Commonly used RADIUS attributes
|
No. |
Attribute |
No. |
Attribute |
|
1 |
User-Name |
45 |
Acct-Authentic |
|
2 |
User-Password |
46 |
Acct-Session-Time |
|
3 |
CHAP-Password |
47 |
Acct-Input-Packets |
|
4 |
NAS-IP-Address |
48 |
Acct-Output-Packets |
|
5 |
NAS-Port |
49 |
Acct-Terminate-Cause |
|
6 |
Service-Type |
50 |
Acct-Multi-Session-Id |
|
7 |
Framed-Protocol |
51 |
Acct-Link-Count |
|
8 |
Framed-IP-Address |
52 |
Acct-Input-Gigawords |
|
9 |
Framed-IP-Netmask |
53 |
Acct-Output-Gigawords |
|
10 |
Framed-Routing |
54 |
(unassigned) |
|
11 |
Filter-ID |
55 |
Event-Timestamp |
|
12 |
Framed-MTU |
56-59 |
(unassigned) |
|
13 |
Framed-Compression |
60 |
CHAP-Challenge |
|
14 |
Login-IP-Host |
61 |
NAS-Port-Type |
|
15 |
Login-Service |
62 |
Port-Limit |
|
16 |
Login-TCP-Port |
63 |
Login-LAT-Port |
|
17 |
(unassigned) |
64 |
Tunnel-Type |
|
18 |
Reply-Message |
65 |
Tunnel-Medium-Type |
|
19 |
Callback-Number |
66 |
Tunnel-Client-Endpoint |
|
20 |
Callback-ID |
67 |
Tunnel-Server-Endpoint |
|
21 |
(unassigned) |
68 |
Acct-Tunnel-Connection |
|
22 |
Framed-Route |
69 |
Tunnel-Password |
|
23 |
Framed-IPX-Network |
70 |
ARAP-Password |
|
24 |
State |
71 |
ARAP-Features |
|
25 |
Class |
72 |
ARAP-Zone-Access |
|
26 |
Vendor-Specific |
73 |
ARAP-Security |
|
27 |
Session-Timeout |
74 |
ARAP-Security-Data |
|
28 |
Idle-Timeout |
75 |
Password-Retry |
|
29 |
Termination-Action |
76 |
Prompt |
|
30 |
Called-Station-Id |
77 |
Connect-Info |
|
31 |
Calling-Station-Id |
78 |
Configuration-Token |
|
32 |
NAS-Identifier |
79 |
EAP-Message |
|
33 |
Proxy-State |
80 |
Message-Authenticator |
|
34 |
Login-LAT-Service |
81 |
Tunnel-Private-Group-id |
|
35 |
Login-LAT-Node |
82 |
Tunnel-Assignment-id |
|
36 |
Login-LAT-Group |
83 |
Tunnel-Preference |
|
37 |
Framed-AppleTalk-Link |
84 |
ARAP-Challenge-Response |
|
38 |
Framed-AppleTalk-Network |
85 |
Acct-Interim-Interval |
|
39 |
Framed-AppleTalk-Zone |
86 |
Acct-Tunnel-Packets-Lost |
|
40 |
Acct-Status-Type |
87 |
NAS-Port-Id |
|
41 |
Acct-Delay-Time |
88 |
Framed-Pool |
|
42 |
Acct-Input-Octets |
89 |
(unassigned) |
|
43 |
Acct-Output-Octets |
90 |
Tunnel-Client-Auth-id |
|
44 |
Acct-Session-Id |
91 |
Tunnel-Server-Auth-id |
Extended RADIUS attributes
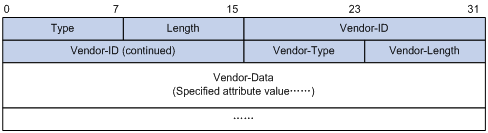
The RADIUS protocol features excellent extensibility. The Vendor-Specific attribute (attribute 26) allows a vendor to define extended attributes. The extended attributes implement functions that the standard RADIUS protocol does not provide.
A vendor can encapsulate multiple sub-attributes in the TLV format in attribute 26 to provide extended functions. As shown in Figure 5, a sub-attribute encapsulated in attribute 26 consists of the following parts:
· Vendor-ID—ID of the vendor. The most significant byte is 0. The other three bytes contains a code compliant to RFC 1700. The vendor ID of H3C is 25506.
· Vendor-Type—Type of the sub-attribute.
· Vendor-Length—Length of the sub-attribute.
· Vendor-Data—Contents of the sub-attribute.
For more information about the proprietary RADIUS sub-attributes of H3C, see "H3C proprietary RADIUS sub-attributes."
Figure 5 Format of attribute 26
HWTACACS
HWTACACS typically provides AAA services for PPP, VPDN, and terminal users. In a typical HWTACACS scenario, terminal users need to log in to the NAS. Working as the HWTACACS client, the NAS sends users' usernames and passwords to the HWTACACS server for authentication. After passing authentication and obtaining authorized rights, a user logs in to the device and performs operations. The HWTACACS server records the operations that each user performs.
Differences between HWTACACS and RADIUS
HWTACACS and RADIUS have many features in common, such as using a client/server model, using shared keys for data encryption, and providing flexibility and scalability. Table 3 lists the primary differences between HWTACACS and RADIUS.
Table 3 Primary differences between HWTACACS and RADIUS
|
HWTACACS |
RADIUS |
|
Uses TCP, which provides reliable network transmission. |
Uses UDP, which provides high transport efficiency. |
|
Encrypts the entire packet except for the HWTACACS header. |
Encrypts only the user password field in an authentication packet. |
|
Protocol packets are complicated and authorization is independent of authentication. Authentication and authorization can be deployed on different HWTACACS servers. |
Protocol packets are simple and the authorization process is combined with the authentication process. |
|
Supports authorization of configuration commands. Access to commands depends on both the user's roles and authorization. A user can use only commands that are permitted by the user roles and authorized by the HWTACACS server. |
Does not support authorization of configuration commands. Access to commands solely depends on the user's roles. For more information about user roles, see Fundamentals Configuration Guide. |
Basic HWTACACS packet exchange process
Figure 6 describes how HWTACACS performs user authentication, authorization, and accounting for a Telnet user.
Figure 6 Basic HWTACACS packet exchange process for a Telnet user
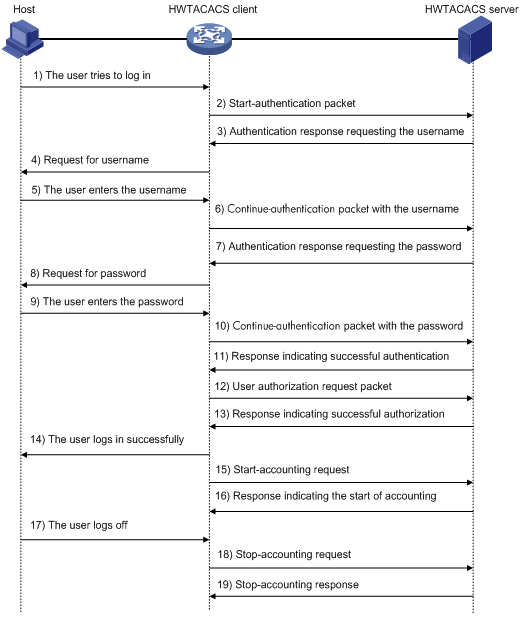
HWTACACS operates using the following workflow:
1. A Telnet user sends an access request to the HWTACACS client.
2. The HWTACACS client sends a start-authentication packet to the HWTACACS server when it receives the request.
3. The HWTACACS server sends back an authentication response to request the username.
4. Upon receiving the response, the HWTACACS client asks the user for the username.
5. The user enters the username.
6. After receiving the username from the user, the HWTACACS client sends the server a continue-authentication packet that includes the username.
7. The HWTACACS server sends back an authentication response to request the login password.
8. Upon receipt of the response, the HWTACACS client prompts the user for the login password.
9. The user enters the password.
10. After receiving the login password, the HWTACACS client sends the HWTACACS server a continue-authentication packet that includes the login password.
11. If the authentication succeeds, the HWTACACS server sends back an authentication response to indicate that the user has passed authentication.
12. The HWTACACS client sends a user authorization request packet to the HWTACACS server.
13. If the authorization succeeds, the HWTACACS server sends back an authorization response, indicating that the user is now authorized.
14. Knowing that the user is now authorized, the HWTACACS client pushes its CLI to the user and permits the user to log in.
15. The HWTACACS client sends a start-accounting request to the HWTACACS server.
16. The HWTACACS server sends back an accounting response, indicating that it has received the start-accounting request.
17. The user logs off.
18. The HWTACACS client sends a stop-accounting request to the HWTACACS server.
19. The HWTACACS server sends back a stop-accounting response, indicating that the stop-accounting request has been received.
LDAP
The Lightweight Directory Access Protocol (LDAP) provides standard multiplatform directory service. LDAP was developed on the basis of the X.500 protocol. It improves the following functions of X.500:
· Read/write interactive access.
· Browse.
· Search.
LDAP is suitable for storing data that does not often change. The protocol is used to store user information. For example, LDAP server software Active Directory Server is used in Microsoft Windows operating systems. The software stores the user information and user group information for user login authentication and authorization.
LDAP directory service
LDAP uses directories to maintain the organization information, personnel information, and resource information. The directories are organized in a tree structure and include entries. An entry is a set of attributes with distinguished names (DNs). The attributes are used to store information such as usernames, passwords, emails, computer names, and phone numbers.
LDAP uses a client/server model, and all directory information is stored in the LDAP server. Commonly used LDAP server products include Microsoft Active Directory Server, IBM Tivoli Directory Server, and Sun ONE Directory Server.
LDAP authentication and authorization
AAA can use LDAP to provide authentication and authorization services for users. LDAP defines a set of operations to implement its functions. The main operations for authentication and authorization are the bind operation and search operation.
· The bind operation allows an LDAP client to perform the following tasks:
¡ Establish a connection with the LDAP server.
¡ Obtain the access rights to the LDAP server.
¡ Check the validity of user information.
· The search operation constructs search conditions and obtains the directory resource information of the LDAP server.
In LDAP authentication, the client completes the following tasks:
1. Uses the LDAP server administrator DN to bind with the LDAP server. After the binding is created, the client establishes a connection to the server and obtains the right to search.
2. Constructs search conditions by using the username in the authentication information of a user. The specified root directory of the server is searched and a user DN list is generated.
3. Binds with the LDAP server by using each user DN and password. If a binding is created, the user is considered legal.
In LDAP authorization, the client performs the same tasks as in LDAP authentication. When the client constructs search conditions, it obtains both authorization information and the user DN list.
· If the authorization information meets the authorization requirements, the authorization process ends.
· If the authorization information does not meet the authorization requirements, the client sends an administrator bind request to the LDAP server. This operation obtains the right to search for authorization information about users on the user DN list.
Basic LDAP packet exchange process
The following example illustrates the basic packet exchange process during LDAP authentication and authorization for a Telnet user.
Figure 7 Basic packet exchange process for LDAP authentication of a Telnet user
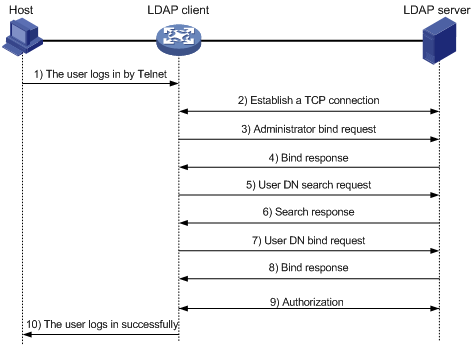
The basic packet exchange process is as follows:
1. A Telnet user initiates a connection request and sends the username and password to the LDAP client.
2. After receiving the request, the LDAP client establishes a TCP connection with the LDAP server.
3. To obtain the right to search, the LDAP client uses the administrator DN and password to send an administrator bind request to the LDAP server.
4. The LDAP server processes the request. If the bind operation is successful, the LDAP server sends an acknowledgment to the LDAP client.
5. The LDAP client sends a user DN search request with the username of the Telnet user to the LDAP server.
6. After receiving the request, the LDAP server searches for the user DN by the base DN, search scope, and filtering conditions. If a match is found, the LDAP server sends a response to notify the LDAP client of the successful search. There might be one or more user DNs found.
7. The LDAP client uses the obtained user DN and the entered user password as parameters to send a user DN bind request to the LDAP server. The server will check whether the user password is correct.
8. The LDAP server processes the request, and sends a response to notify the LDAP client of the bind operation result. If the bind operation fails, the LDAP client uses another obtained user DN as the parameter to send a user DN bind request to the LDAP server. This process continues until a DN is bound successfully or all DNs fail to be bound. If all user DNs fail to be bound, the LDAP client notifies the user of the login failure and denies the user's access request.
9. The LDAP client and server perform authorization exchanges. If another scheme (for example, an HWTACACS scheme) is expected for authorization, the LDAP client exchanges authorization packets with the HWTACACS authorization server instead.
10. After successful authorization, the LDAP client notifies the user of the successful login.
AAA implementation on the device
This section describes AAA user management and methods.
User management based on ISP domains and user access types
AAA manages users based on the users' ISP domains and access types.
On a NAS, each user belongs to one ISP domain. The NAS determines the ISP domain to which a user belongs based on the username entered by the user at login.
Figure 8 Determining the ISP domain for a user by username
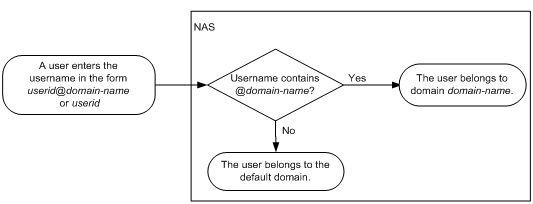
AAA manages users in the same ISP domain based on the users' access types. The device supports the following user access types:
· LAN—LAN users must pass 802.1X or MAC authentication to come online.
· Login—Login users include SSH, Telnet, FTP, and terminal users who log in to the device. Terminal users can access through console ports.
· Portal—Portal users must pass portal authentication to access the network.
· Web—Web users log in to the Web interface of the device through HTTP or HTTPS.
|
|
NOTE: The device also provides authentication modules (such as 802.1X) for implementation of user authentication management policies. If you configure these authentication modules, the ISP domains for users of the access types depend on the configuration of the authentication modules. |
AAA methods
AAA supports configuring different authentication, authorization, and accounting methods for different types of users in an ISP domain. The NAS determines the ISP domain and access type of a user. The NAS also uses the methods configured for the access type in the domain to control the user's access.
AAA also supports configuring a set of default methods for an ISP domain. These default methods are applied to users for whom no AAA methods are configured.
The device supports the following authentication methods:
· No authentication—This method trusts all users and does not perform authentication. For security purposes, do not use this method.
· Local authentication—The NAS authenticates users by itself, based on the locally configured user information including the usernames, passwords, and attributes. Local authentication allows high speed and low cost, but the amount of information that can be stored is limited by the size of the storage space.
· Remote authentication—The NAS works with a RADIUS, HWTACACS, or LDAP server to authenticate users. The server manages user information in a centralized manner. Remote authentication provides high capacity, reliable, and centralized authentication services for multiple NASs. You can configure backup methods to be used when the remote server is not available.
The device supports the following authorization methods:
· No authorization—The NAS performs no authorization exchange. The following default authorization information applies after users pass authentication:
¡ Non-login users can access the network.
¡ Login users are assigned the default user role. For more information about the default user role feature, see Fundamentals Configuration Guide.
¡ FTP, SFTP, and SCP login users also have the root directory of the NAS set as the working directory. However, the users do not have permission to access the root directory.
· Local authorization—The NAS performs authorization according to the user attributes locally configured for users.
· Remote authorization—The NAS works with a RADIUS, HWTACACS, or LDAP server to authorize users. RADIUS authorization is bound with RADIUS authentication. RADIUS authorization can work only after RADIUS authentication is successful, and the authorization information is included in the Access-Accept packet. HWTACACS authorization is separate from HWTACACS authentication, and the authorization information is included in the authorization response after successful authentication. You can configure backup methods to be used when the remote server is not available.
The device supports the following accounting methods:
· No accounting—The NAS does not perform accounting for the users.
· Local accounting—Local accounting is implemented on the NAS. It counts and controls the number of concurrent users who use the same local user account, but does not provide statistics for charging.
· Remote accounting—The NAS works with a RADIUS server or HWTACACS server for accounting. You can configure backup methods to be used when the remote server is not available.
In addition, the device provides the following login services to enhance device security:
· Command authorization—Enables the NAS to let the authorization server determine whether a command entered by a login user is permitted. Login users can execute only commands permitted by the authorization server. For more information about command authorization, see Fundamentals Configuration Guide.
· Command accounting—When command authorization is disabled, command accounting enables the accounting server to record all valid commands executed on the device. When command authorization is enabled, command accounting enables the accounting server to record all authorized commands. For more information about command accounting, see Fundamentals Configuration Guide.
· User role authentication—Authenticates each user who wants to obtain another user role without logging out or getting disconnected. For more information about user role authentication, see Fundamentals Configuration Guide.
AAA for MPLS L3VPNs
You can deploy AAA across VPNs in an MPLS L3VPN scenario where clients in different VPNs are centrally authenticated. The deployment enables forwarding of RADIUS and HWTACACS packets across MPLS VPNs. For example, as shown in Figure 9, you can deploy AAA across the VPNs. The PE at the left side of the MPLS backbone acts as a NAS. The NAS transparently delivers the AAA packets of private users in VPN 1 and VPN 2 to the AAA servers in VPN 3 for centralized authentication. Authentication packets of private users in different VPNs do not affect each other.
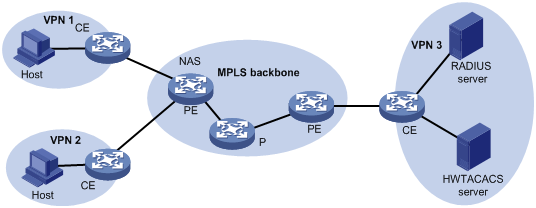
This feature can also help an MCE to implement portal authentication for VPNs. For more information about MCE, see MPLS Configuration Guide. For more information about portal authentication, see "Configuring portal authentication."
Protocols and standards
· RFC 2865, Remote Authentication Dial In User Service (RADIUS)
· RFC 2866, RADIUS Accounting
· RFC 2867, RADIUS Accounting Modifications for Tunnel Protocol Support
· RFC 2868, RADIUS Attributes for Tunnel Protocol Support
· RFC 2869, RADIUS Extensions
· RFC 1492, An Access Control Protocol, Sometimes Called TACACS
· RFC 1777, Lightweight Directory Access Protocol
· RFC 2251, Lightweight Directory Access Protocol (v3)
RADIUS attributes
Commonly used standard RADIUS attributes
|
No. |
Attribute |
Description |
|
1 |
User-Name |
Name of the user to be authenticated. |
|
2 |
User-Password |
User password for PAP authentication, only present in Access-Request packets when PAP authentication is used. |
|
3 |
CHAP-Password |
Digest of the user password for CHAP authentication, only present in Access-Request packets when CHAP authentication is used. |
|
4 |
NAS-IP-Address |
IP address for the server to use to identify the client. Typically, a client is identified by the IP address of its access interface. This attribute is only present in Access-Request packets. |
|
5 |
NAS-Port |
Physical port of the NAS that the user accesses. |
|
6 |
Service-Type |
Type of service that the user has requested or type of service to be provided. |
|
7 |
Framed-Protocol |
Encapsulation protocol for framed access. |
|
8 |
Framed-IP-Address |
IP address assigned to the user. |
|
11 |
Filter-ID |
Name of the filter list. |
|
12 |
Framed-MTU |
MTU for the data link between the user and NAS. For example, with 802.1X EAP authentication, NAS uses this attribute to notify the server of the MTU for EAP packets to avoid oversized EAP packets. |
|
14 |
Login-IP-Host |
IP address of the NAS interface that the user accesses. |
|
15 |
Login-Service |
Type of the service that the user uses for login. |
|
18 |
Reply-Message |
Text to be displayed to the user, which can be used by the server to communicate information, for example, the reason of the authentication failure. |
|
26 |
Vendor-Specific |
Vendor-specific proprietary attribute. A packet can contain one or more proprietary attributes, each of which can contain one or more sub-attributes. |
|
27 |
Session-Timeout |
Maximum service duration for the user before termination of the session. |
|
28 |
Idle-Timeout |
Maximum idle time permitted for the user before termination of the session. |
|
31 |
Calling-Station-Id |
User identification that the NAS sends to the server. For the LAN access service provided by an H3C device, this attribute includes the MAC address of the user in the format HHHH-HHHH-HHHH. |
|
32 |
NAS-Identifier |
Identification that the NAS uses to identify itself to the RADIUS server. |
|
40 |
Acct-Status-Type |
Type of the Accounting-Request packet. Possible values include: · 1—Start. · 2—Stop. · 3—Interim-Update. · 4—Reset-Charge. · 7—Accounting-On. (Defined in the 3rd Generation Partnership Project.) · 8—Accounting-Off. (Defined in the 3rd Generation Partnership Project.) · 9 to 14—Reserved for tunnel accounting. · 15—Reserved for failed. |
|
45 |
Acct-Authentic |
Authentication method used by the user. Possible values include: · 1—RADIUS. · 2—Local. · 3—Remote. |
|
60 |
CHAP-Challenge |
CHAP challenge generated by the NAS for MD5 calculation during CHAP authentication. |
|
61 |
NAS-Port-Type |
Type of the physical port of the NAS that is authenticating the user. Possible values include: · 15—Ethernet. · 16—Any type of ADSL. · 17—Cable. (With cable for cable TV.) · 19—WLAN-IEEE 802.11. · 201—VLAN. · 202—ATM. If the port is an ATM or Ethernet one and VLANs are implemented on it, the value of this attribute is 201. |
|
79 |
EAP-Message |
Used to encapsulate EAP packets to allow RADIUS to support EAP authentication. |
|
80 |
Message-Authenticator |
Used for authentication and verification of authentication packets to prevent spoofing Access-Requests. This attribute is present when EAP authentication is used. |
|
87 |
NAS-Port-Id |
String for describing the port of the NAS that is authenticating the user. |
H3C proprietary RADIUS sub-attributes
|
No. |
Sub-attribute |
Description |
|
1 |
Input-Peak-Rate |
Peak rate in the direction from the user to the NAS, in bps. |
|
2 |
Input-Average-Rate |
Average rate in the direction from the user to the NAS, in bps. |
|
3 |
Input-Basic-Rate |
Basic rate in the direction from the user to the NAS, in bps. |
|
4 |
Output-Peak-Rate |
Peak rate in the direction from the NAS to the user, in bps. |
|
5 |
Output-Average-Rate |
Average rate in the direction from the NAS to the user, in bps. |
|
6 |
Output-Basic-Rate |
Basic rate in the direction from the NAS to the user, in bps. |
|
15 |
Remanent_Volume |
Total remaining available traffic for the connection, in different units for different server types. |
|
20 |
Command |
Operation for the session, used for session control. Possible values include: · 1—Trigger-Request. · 2—Terminate-Request. · 3—SetPolicy. · 4—Result. · 5—PortalClear. |
|
24 |
Control_Identifier |
Identification for retransmitted packets. For retransmitted packets from the same session, this attribute must be the same value. For retransmitted packets from different sessions, this attribute does not have to be the same value. The client response of a retransmitted packet must also include this attribute and the value of this attribute must be the same. For Accounting-Request packets of the start, stop, and interim update types, the Control_Identifier attribute does not take effect. |
|
25 |
Result_Code |
Result of the Trigger-Request or SetPolicy operation, zero for success and any other value for failure. |
|
26 |
Connect_ID |
Index of the user connection. |
|
28 |
Ftp_Directory |
FTP, SFTP, or SCP user working directory. When the RADIUS client acts as the FTP, SFTP, or SCP server, this attribute is used to set the working directory for an FTP, SFTP, or SCP user on the RADIUS client. |
|
29 |
Exec_Privilege |
EXEC user priority. |
|
59 |
NAS_Startup_Timestamp |
Startup time of the NAS in seconds, which is represented by the time elapsed after 00:00:00 on Jan. 1, 1970 (UTC). |
|
60 |
Ip_Host_Addr |
User IP address and MAC address included in authentication and accounting requests, in the format A.B.C.D hh:hh:hh:hh:hh:hh. A space is required between the IP address and the MAC address. |
|
61 |
User_Notify |
Information that must be sent from the server to the client transparently. |
|
62 |
User_HeartBeat |
Hash value assigned after an 802.1X user passes authentication, which is a 32-byte string. This attribute is stored in the user list on the NAS and verifies the handshake packets from the 802.1X user. This attribute only exists in Access-Accept and Accounting-Request packets. |
|
140 |
User_Group |
User groups assigned after the SSL VPN user passes authentication. A user can belong to multiple user groups that are separated by semicolons. This attribute is used to work with the SSL VPN device. |
|
141 |
Security_Level |
Security level assigned after the SSL VPN user passes security authentication. |
|
201 |
Input-Interval-Octets |
Number of bytes input within a real-time accounting interval. |
|
202 |
Output-Interval-Octets |
Number of bytes output within a real-time accounting interval. |
|
203 |
Input-Interval-Packets |
Number of packets input within an accounting interval in the unit set on the NAS. |
|
204 |
Output-Interval-Packets |
Number of packets output within an accounting interval in the unit set on the NAS. |
|
205 |
Input-Interval-Gigawords |
Amount of bytes input within an accounting interval, in units of 4G bytes. |
|
206 |
Output-Interval-Gigawords |
Amount of bytes output within an accounting interval, in units of 4G bytes. |
|
207 |
Backup-NAS-IP |
Backup source IP address for sending RADIUS packets. |
|
255 |
Product_ID |
Product name. |
FIPS compliance
The device supports the FIPS mode that complies with NIST FIPS 140-2 requirements. Support for features, commands, and parameters might differ in FIPS mode (see "Configuring FIPS") and non-FIPS mode.
AAA configuration considerations and task list
To configure AAA, complete the following tasks on the NAS:
1. Configure the required AAA schemes.
¡ Local authentication—Configure local users and the related attributes, including the usernames and passwords, for the users to be authenticated.
¡ Remote authentication—Configure the required RADIUS, HWTACACS, and LDAP schemes.
2. Configure AAA methods for the users' ISP domains. To use remote AAA methods, you must specify the configured RADIUS, HWTACACS, or LDAP schemes in ISP domain view.
Figure 10 AAA configuration procedure
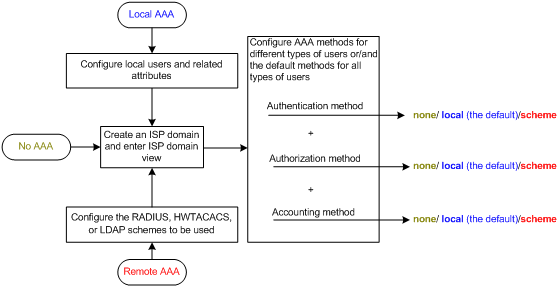
To configure AAA, perform the following tasks:
|
Tasks at a glance |
|
(Required.) Perform at least one of the following tasks to configure local users or AAA schemes: |
|
(Required.) Configure AAA methods for ISP domains: 1. (Required.) Creating an ISP domain 2. (Optional.) Setting ISP domain status 3. (Required.) Perform at least one of the following tasks to configure AAA authentication, authorization, and accounting methods for the ISP domain: ¡ Configuring authentication methods for an ISP domain |
|
(Optional.) Enabling the session-control feature |
|
(Optional.) Setting the maximum number of concurrent login users |
|
(Optional.) Configuring a NAS-ID profile |
Configuring AAA schemes
This section includes information on configuring local users, RADIUS schemes, HWTACACS schemes, and LDAP schemes.
Configuring local users
To implement local authentication, authorization, and accounting, create local users and configure user attributes on the device. The local users and attributes are stored in the local user database on the device. A local user is uniquely identified by the combination of a username and a user type. Local users are classified into the following types:
· Device management user—User who logs in to the device for device management.
· Network access user—User who accesses network resources through the device.
The following shows the configurable local user attributes:
· Service type—Services that the user can use. Local authentication checks the service types of a local user. If none of the service types is available, the user cannot pass authentication.
Service types include FTP, HTTP, HTTPS, LAN access, portal, SSH, Telnet, and terminal.
· User state—There are two user states: active and blocked. A user in active state can request network services. A user in blocked state cannot request authentication, authorization, and accounting services, but it can request to stop the accounting service in use.
· Upper limit of concurrent logins using the same user name—Maximum number of users who can concurrently access the device by using the same user name. When the number reaches the upper limit, no more local users can access the device by using the user name.
· User group—Each local user belongs to a local user group and has all attributes of the group. The attributes include the password control attributes and authorization attributes. For more information about local user group, see "Configuring user group attributes."
· Binding attributes—Binding attributes control the scope of users, and are checked during local authentication of a user. If the attributes of a user do not match the binding attributes configured for the local user account, the user cannot pass authentication. Binding attributes include the IP address, access port, MAC address, and native VLAN. For support and usage information about binding attributes, see "Configuring local user attributes."
· Authorization attributes—Authorization attributes indicate the user's rights after it passes local authentication. Authorization attributes include the ACL, idle cut function, user role, VLAN, and FTP/SFTP/SCP working directory. For support information about authorization attributes, see "Configuring local user attributes."
Configure the authorization attributes based on the service type of local users.
You can configure an authorization attribute in user group view or local user view. The setting of an authorization attribute in local user view takes precedence over the attribute setting in user group view.
¡ The attribute configured in user group view takes effect on all local users in the user group.
¡ The attribute configured in local user view takes effect only on the local user.
· Password control attributes—Password control attributes help control password security for device management users. Password control attributes include password aging time, minimum password length, password composition checking, password complexity checking, and login attempt limit.
You can configure a password control attribute in system view, user group view, or local user view. A password control attribute with a smaller effective range has a higher priority. For more information about password management and global password configuration, see "Configuring password control."
Local user configuration task list
|
Tasks at a glance |
|
(Required.) Configuring local user attributes |
|
(Optional.) Configuring user group attributes |
|
(Optional.) Displaying and maintaining local users and local user groups |
Configuring local user attributes
When you configure local user attributes, follow these guidelines:
· When you use the password-control enable command to globally enable the password control feature, local user passwords are not displayed.
· You can configure authorization attributes and password control attributes in local user view or user group view. The setting in local user view takes precedence over the setting in user group view.
· Configure authorization attributes according to the application environments and purposes. Support for authorization attributes depends on the service types of users.
¡ For LAN and portal users, only the authorization attributes acl and vlan are effective.
¡ For Telnet and terminal users, only the authorization attribute idle-cut and user-role is effective.
¡ For HTTP and HTTPS users, only the authorization attribute user-role is effective.
¡ For SSH users, only the authorization attributes idle-cut, user-role and work-directory are effective.
¡ For FTP users, only the following authorization attributes are effective: user-role and work-directory.
¡ For other types of local users, no authorization attribute is effective.
· Configure the location binding attribute based on the service types of users.
¡ For 802.1X users, specify the 802.1X-enabled Layer 2 Ethernet interfaces through which the users access the device.
¡ For MAC authentication users, specify the MAC authentication-enabled Layer 2 Ethernet interfaces through which the users access the device.
¡ For portal users, specify the portal-enabled interfaces through which the users access the device. Specify the Layer 2 Ethernet interfaces if portal is enabled on VLAN interfaces and the portal roaming enable command is not configured.
To configure local user attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Add a local user and enter local user view. |
local-user user-name [ class { manage | network } ] |
By default, no local user exists. |
|
3. (Optional.) Configure a password for the local user. |
· For a network access user: · For a device management user: ¡ In non-FIPS mode: ¡ In FIPS mode: |
Network access user passwords are encrypted with the encryption algorithm and saved in ciphertext. Device management user passwords are encrypted with the hash algorithm and saved in ciphertext. In non-FIPS mode, a non-password-protected user passes authentication if the user provides the correct username and passes attribute checks. To enhance security, configure a password for each local user. In FIPS mode, only password-protected users can pass authentication. |
|
4. Assign services to the local user. |
· For a network access user: · For a device management user: ¡ In non-FIPS mode: ¡ In FIPS mode: |
By default, no service is authorized to a local user. |
|
5. (Optional.) Place the local user to the active or blocked state. |
state { active | block } |
By default, a created local user is in active state and can request network services. |
|
6. (Optional.) Set the upper limit of concurrent logins using the local user name. |
access-limit max-user-number |
By default, the number of concurrent logins is not limited for the local user. This command takes effect only when local accounting is configured for the local user. It does not apply to FTP, SFTP, or SCP users, who do not support accounting. |
|
7. (Optional.) Configure binding attributes for the local user. |
bind-attribute { ip ip-address | location interface interface-type interface-number | mac mac-address | vlan vlan-id } * |
By default, no binding attribute is configured for a local user. Binding attribute ip applies only to LAN users using 802.1X. Binding attributes location, mac, and vlan apply only to LAN and portal users. |
|
8. (Optional.) Configure authorization attributes for the local user. |
authorization-attribute { acl acl-number | idle-cut minute | user-profile profile-name | user-role role-name | vlan vlan-id | work-directory directory-name } * |
The following default settings apply: · FTP, SFTP, and SCP users have the root directory of the NAS set as the working directory. However, the users do not have permission to access the root directory. · The network-operator user role is assigned to local users that are created by a network-admin or level-15 user. The user-profile profile-name option is not supported in the current release. |
|
9. (Optional.) Configure password control attributes for the local user. |
· Set the password aging time: · Set the minimum password length: · Configure the password composition policy: · Configure the password complexity checking policy: · Configure the maximum login attempts and the action to take if there is a login failure: |
Optional. By default, the local user uses password control attributes of the user group to which the local user belongs. Only device management users support the password control feature. |
|
10. (Optional.) Assign the local user to a user group. |
group group-name |
By default, a local user belongs to the default user group system. |
Configuring user group attributes
User groups simplify local user configuration and management. A user group contains a group of local users and has a set of local user attributes. You can configure local user attributes for a user group to implement centralized user attributes management for the local users in the group. Local user attributes that are manageable include authorization attributes.
By default, every new local user belongs to the default user group system and has all attributes of the group. To assign a local user to a different user group, use the group command in local user view.
To configure user group attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a user group and enter user group view. |
user-group group-name |
By default, there is a system-defined user group named system, which is the default user group. |
|
3. Configure authorization attributes for the user group. |
authorization-attribute { acl acl-number | idle-cut minute | user-profile profile-name | vlan vlan-id | work-directory directory-name } * |
By default, no authorization attribute is configured for a user group. The user-profile profile-name option is not supported in the current release. |
|
4. (Optional.) Configure password control attributes for the user group. |
· Set the password aging time: · Set the minimum password length: · Configure the password composition policy: · Configure the password complexity checking policy: · Configure the maximum login attempts and the action to take for
login failures: |
Optional. By default, the user group uses the global password control settings. For more information, see "Configuring password control." |
Displaying and maintaining local users and local user groups
Execute display commands in any view.
|
Task |
Command |
|
Display the local user configuration and online user statistics. |
display local-user [ class { manage | network } | idle-cut { disable | enable } | service-type { ftp | http | https | lan-access | portal | ssh | telnet | terminal } | state { active | block } | user-name user-name class { manage | network } | vlan vlan-id ] |
|
Display the user group configuration. |
display user-group [ group-name ] |
Configuring RADIUS schemes
A RADIUS scheme specifies the RADIUS servers that the device can work with and defines a set of parameters. The device uses the parameters to exchange information with the RADIUS servers, including the server IP addresses, UDP port numbers, shared keys, and server types.
Configuration task list
|
Tasks at a glance |
|
(Required.) Creating a RADIUS scheme |
|
(Required.) Specifying the RADIUS authentication servers |
|
(Optional.) Specifying the RADIUS accounting servers and the relevant parameters |
|
(Optional.) Specifying the shared keys for secure RADIUS communication |
|
(Optional.) Specifying a VPN for the scheme |
|
(Optional.) Setting the username format and traffic statistics units |
|
(Optional.) Setting the maximum number of RADIUS request transmission attempts |
|
(Optional.) Setting the status of RADIUS servers |
|
(Optional.) Specifying the source IP address for outgoing RADIUS packets |
|
(Optional.) Setting RADIUS timers |
|
(Optional.) Configuring the accounting-on feature |
|
(Optional.) Configuring the IP addresses of the security policy servers |
|
(Optional.) Configuring the Login-Service attribute check method for SSH, FTP, and terminal users |
|
(Optional.) Enabling SNMP notifications for RADIUS |
|
(Optional.) Displaying and maintaining RADIUS |
Creating a RADIUS scheme
Create a RADIUS scheme before performing any other RADIUS configurations. You can configure a maximum of 16 RADIUS schemes. A RADIUS scheme can be used by multiple ISP domains.
To create a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create a RADIUS scheme and enter RADIUS scheme view. |
radius scheme radius-scheme-name |
The default setting depends on the type of the startup configuration: · If the device starts up with initial settings, no RADIUS scheme is defined. · If the device starts up with the default configuration file, a RADIUS scheme named system is defined. For more information about the startup configuration, see Fundamentals Configuration Guide. |
Specifying the RADIUS authentication servers
A RADIUS authentication server completes authentication and authorization together, because authorization information is piggybacked in authentication responses sent to RADIUS clients.
You can specify one primary authentication server and a maximum of 16 secondary authentication servers for a RADIUS scheme. When the primary server is not available, the device searches for the secondary servers in the order they are configured. The first secondary server in active state is used for communication.
If redundancy is not required, specify only the primary server. A RADIUS authentication server can function as the primary authentication server for one scheme and a secondary authentication server for another scheme at the same time.
To specify a RADIUS server by hostname in an MPLS VPN network, first complete one of the following tasks on the device:
· Configure hostname-to-IP address mappings for the VPN by using the ip host or ipv6 host command.
· Configure a DNS server for the VPN by using the dns server or ipv6 dns server command.
For more information about these commands, see Layer 3—IP Services Command Reference.
To specify RADIUS authentication servers for a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify RADIUS authentication servers. |
· Specify the primary RADIUS authentication
server: · Specify a secondary RADIUS authentication server: |
By default, no authentication server is specified. Two authentication servers in a scheme, primary or secondary, cannot have the same combination of hostname, IP address, port number, and VPN. |
Specifying the RADIUS accounting servers and the relevant parameters
You can specify one primary accounting server and a maximum of 16 secondary accounting servers for a RADIUS scheme. When the primary server is not available, the device searches for the secondary servers in the order they are configured. The first secondary server in active state is used for communication.
If redundancy is not required, specify only the primary server. A RADIUS accounting server can function as the primary accounting server for one scheme and a secondary accounting server for another scheme at the same time.
The device sends a stop-accounting request to the accounting server in the following situations:
· The device receives a connection teardown request from a host.
· The device receives a connection teardown command from an administrator.
When the maximum number of real-time accounting attempts is reached, the device disconnects users who have no accounting responses.
RADIUS does not support accounting for FTP, SFTP, and SCP users.
To specify a RADIUS server by hostname in an MPLS VPN network, first complete one of the following tasks on the device:
· Configure hostname-to-IP address mappings for the VPN by using the ip host or ipv6 host command.
· Configure a DNS server for the VPN by using the dns server or ipv6 dns server command.
For more information about these commands, see Layer 3—IP Services Command Reference.
To specify RADIUS accounting servers and the relevant parameters for a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify RADIUS accounting servers. |
· Specify the primary RADIUS accounting server: · Specify a secondary RADIUS accounting server: |
By default, no accounting server is specified. Two accounting servers in a scheme, primary or secondary, cannot have the same combination of hostname, IP address, port number, and VPN. |
|
4. (Optional.) Set the maximum number of real-time accounting attempts. |
retry realtime-accounting retry-times |
The default setting is 5. |
Specifying the shared keys for secure RADIUS communication
The RADIUS client and server use the MD5 algorithm and shared keys to generate the Authenticator value for packet authentication and user password encryption. The client and server must use the same key for each type of communication.
A key configured in this task is for all servers of the same type (accounting or authentication) in the scheme. The key has a lower priority than a key configured individually for a RADIUS server.
To specify a shared key for secure RADIUS communication:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify a shared key for secure RADIUS communication. |
key { accounting | authentication } { cipher | simple } string |
By default, no shared key is specified. The shared key configured on the device must be the same as the shared key configured on the RADIUS server. |
Specifying a VPN for the scheme
The VPN specified for a RADIUS scheme applies to all authentication and accounting servers in that scheme. If a VPN is also configured for an individual RADIUS server, the VPN specified for the RADIUS scheme does not take effect on that server.
To specify a VPN for a scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify a VPN for the RADIUS scheme. |
vpn-instance vpn-instance-name |
By default, a RADIUS scheme belongs to the public network. |
Setting the username format and traffic statistics units
A username is in the userid@isp-name format, where the isp-name argument represents the user's ISP domain name. By default, the ISP domain name is included in a username. However, older RADIUS servers might not recognize usernames that contain the ISP domain names. In this case, you can configure the device to remove the domain name of each username to be sent.
If two or more ISP domains use the same RADIUS scheme, configure the RADIUS scheme to keep the ISP domain name in usernames for domain identification.
The device reports online user traffic statistics in accounting packets. The traffic measurement units are configurable, but they must be the same as the traffic measurement units configured on the RADIUS accounting servers.
To set the username format and the traffic statistics units for a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Set the format for usernames sent to the RADIUS servers. |
user-name-format { keep-original | with-domain | without-domain } |
The default setting depends on the type of the startup configuration: · If the device starts up with initial settings, the ISP domain name is included in a username. · If the device starts up with the default configuration file, the ISP domain name is included in a username except for the predefined RADIUS scheme named system. When the username is sent to a RADIUS server in the system scheme, the ISP domain name is removed. For more information about the startup configuration, see Fundamentals Configuration Guide. |
|
4. (Optional.) Set the data flow and packet measurement units for traffic statistics. |
data-flow-format { data { byte | giga-byte | kilo-byte | mega-byte } | packet { giga-packet | kilo-packet | mega-packet | one-packet } }* |
By default, traffic is counted in bytes and packets. |
Setting the maximum number of RADIUS request transmission attempts
RADIUS uses UDP packets to transfer data. Because UDP communication is not reliable, RADIUS uses a retransmission mechanism to improve reliability. A RADIUS request is retransmitted if the NAS does not receive a server response for the request within the response timeout timer. For more information about the RADIUS server response timeout timer, see "Setting RADIUS timers."
You can set the maximum number for the NAS to retransmit a RADIUS request to the same server. When the maximum number is reached, the NAS tries to communicate with other RADIUS servers in active state. If no other servers are in active state at the time, the NAS considers the authentication or accounting attempt a failure.
To set the maximum number of RADIUS request transmission attempts:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Set the maximum number of RADIUS request transmission attempts. |
retry retry-times |
The default setting is 3. |
Setting the status of RADIUS servers
To control the RADIUS servers with which the device communicates when the current servers are no longer available, set the status of RADIUS servers to blocked or active. You can specify one primary RADIUS server and multiple secondary RADIUS servers. The secondary servers function as the backup of the primary server. The device chooses servers based on the following rules:
· When the primary server is in active state, the device communicates with the primary server.
· If the primary server fails, the device performs the following tasks:
¡ Changes the server status to blocked.
¡ Starts a quiet timer for the server.
¡ Tries to communicate with a secondary server in active state that has the highest priority.
· If the secondary server is unreachable, the device performs the following tasks:
¡ Changes the server status to blocked.
¡ Starts a quiet timer for the server.
¡ Tries to communicate with the next secondary server in active state that has the highest priority.
· The search process continues until the device finds an available secondary server or has checked all secondary servers in active state. If no server is available, the device considers the authentication or accounting attempt a failure.
· When the quiet timer of a server expires or you manually set the server to the active state, the status of the server changes back to active. The device does not check the server again during the authentication or accounting process.
· When you remove a server in use, communication with the server times out. The device looks for a server in active state by first checking the primary server, and then checking secondary servers in the order they are configured.
· When the primary server and secondary servers are all in blocked state, the device tries to communicate with the primary server.
· When one or more servers are in active state, the device tries to communicate with these active servers only, even if the servers are unavailable.
· When a RADIUS server's status changes automatically, the device changes this server's status accordingly in all RADIUS schemes in which this server is specified.
By default, the device sets the status of all RADIUS servers to active. However, in some situations, you must change the status of a server. For example, if a server fails, you can change the status of the server to blocked to avoid communication attempts to the server.
To set the status of RADIUS servers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Set the RADIUS server status. |
· Set the status of the primary RADIUS
authentication server: · Set the status of the primary RADIUS
accounting server: · Set the status of a secondary RADIUS authentication server: · Set the status of a secondary RADIUS accounting server: |
By default, every server specified in a RADIUS scheme is in active state. The configured server status cannot be saved to any configuration file, and can only be viewed by using the display radius scheme command. After the device restarts, all servers are restored to the active state. |
Specifying the source IP address for outgoing RADIUS packets
The source IP address of RADIUS packets that a NAS sends must match the IP address of the NAS configured on the RADIUS server. A RADIUS server identifies a NAS by its IP address. Upon receiving a RADIUS packet, a RADIUS server checks whether the source IP address of the packet is the IP address of a managed NAS.
· If the source IP address of the packet is the IP address of a managed NAS, the server processes the packet.
· If the source IP address of the packet is not the IP address of a managed NAS, the server drops the packet.
The source address of outgoing RADIUS packets is typically the IP address of an egress interface on the NAS to communicate with the RADIUS server. However, in some situations, you must change the source IP address. For example, when VRRP is configured for stateful failover, configure the virtual IP address of the uplink VRRP group as the source IP address.
You can specify a source IP address for outgoing RADIUS packets in RADIUS scheme view or in system view.
· The IP address specified in RADIUS scheme view applies only to one RADIUS scheme.
· The IP address specified in system view applies to all RADIUS schemes whose servers are in a VPN or the public network.
Before sending a RADIUS packet, the NAS selects a source IP address in the following order:
1. The source IP address specified for the RADIUS scheme.
2. The source IP address specified in system view for the VPN or public network, depending on where the RADIUS server resides.
3. The IP address of the outbound interface specified by the route.
To specify a source IP address for all RADIUS schemes in a VPN or the public network:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a source IP address for outgoing RADIUS packets. |
radius nas-ip { ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] |
By default, the IP address of the RADIUS packet outbound interface is used as the source IP address. |
To specify a source IP address for a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify a source IP address for outgoing RADIUS packets. |
nas-ip { ipv4-address | ipv6 ipv6-address } |
By default, the source IP address specified by the radius nas-ip command in system view is used. If the source IP address is not specified, the IP address of the outbound interface is used. |
Setting RADIUS timers
The device uses the following types of timers to control communication with a RADIUS server:
· Server response timeout timer (response-timeout)—Defines the RADIUS request retransmission interval. The timer starts immediately after a RADIUS request is sent. If the device does not receive a response from the RADIUS server before the timer expires, it resends the request.
· Server quiet timer (quiet)—Defines the duration to keep an unreachable server in blocked state. If one server is not reachable, the device changes the server status to blocked, starts this timer for the server, and tries to communicate with another server in active state. After the server quiet timer expires, the device changes the status of the server back to active.
· Real-time accounting timer (realtime-accounting)—Defines the interval at which the device sends real-time accounting packets to the RADIUS accounting server for online users.
When you set RADIUS timers, follow these guidelines:
· When you configure the maximum number of RADIUS packet transmission attempts and the RADIUS server response timeout timer, consider the number of secondary servers. If the retransmission process takes too much time, the client connection in the access module (for example, Telnet) might time out during the process.
· When a number of secondary servers are configured, the client connections of access modules that have a short client connection timeout period might still be timed out during initial authentication or accounting, even if the packet transmission attempt limit and server response timeout period are configured with small values. However, the next authentication or accounting attempt can succeed, because the device has set the unreachable servers to blocked, which shortens the amount of time for finding a reachable server.
· Make sure the server quiet timer is set correctly. A timer that is too short might result in frequent authentication or accounting failures. This is because the device will continue to attempt to communicate with an unreachable server that is in active state. A timer that is too long might temporarily block a reachable server that has recovered from a failure. This is because the server will remain in blocked state until the timer expires.
· A short real-time accounting interval helps improve accounting precision but requires many system resources. When there are 1000 or more users, set the interval to 15 minutes or longer.
To set RADIUS timers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Set the RADIUS server response timeout timer. |
timer response-timeout seconds |
The default setting is 3 seconds. |
|
4. Set the quiet timer for the servers. |
timer quiet minutes |
The default setting is 5 minutes. |
|
5. Set the real-time accounting timer. |
timer realtime-accounting minutes |
The default setting is 12 minutes. |
Configuring the accounting-on feature
When the accounting-on feature is enabled, the device automatically sends an accounting-on packet to the RADIUS server after a reboot. Upon receiving the accounting-on packet, the RADIUS server logs out all online users so they can log in again through the device. Without this feature, users cannot log in again after the reboot, because the RADIUS server considers them to come online.
You can configure the interval for which the device waits to resend the accounting-on packet and the maximum number of retries.
To configure the accounting-on feature for a RADIUS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Enable accounting-on. |
accounting-on enable [ interval seconds | send send-times ] * |
By default, the accounting-on feature is disabled. |
Configuring the IP addresses of the security policy servers
The NAS verifies the validity of received control packets and accepts only control packets from known servers. To use a security policy server that is independent of the AAA servers, configure the IP address of the security policy server on the NAS.
The security policy server is the management and control center of the H3C EAD solution. To implement all EAD functions, configure both the IP address of the security policy server and that of the IMC Platform on the NAS.
To configure the IP address of a security policy server for a scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Specify a security policy server. |
security-policy-server { ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] |
By default, no security policy server is specified for a scheme. You can specify a maximum of eight security policy servers for a RADIUS scheme. |
Configuring the Login-Service attribute check method for SSH, FTP, and terminal users
· Strict—Matches Login-Service attribute values 50, 51, and 52 for SSH, FTP, and terminal services, respectively.
· Loose—Matches the standard Login-Service attribute value 0 for SSH, FTP, and terminal services.
An Access-Accept packet received for a user must contain the matching attribute value. Otherwise, the user cannot log in to the device.
Use the loose check method only when the server does not issue Login-Service attribute values 50, 51, and 52 for SSH, FTP, and terminal users.
To configure the Login-Service attribute check method for SSH, FTP, and terminal users:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter RADIUS scheme view. |
radius scheme radius-scheme-name |
N/A |
|
3. Configure the Login-Service attribute check method for SSH, FTP, and terminal users. |
attribute 15 check-mode { loose | strict } |
The default check method is strict. |
Enabling SNMP notifications for RADIUS
When SNMP notifications are enabled for RADIUS, the SNMP agent supports the following notifications generated by RADIUS:
· RADIUS server unreachable notification—The RADIUS server cannot be reached. RADIUS generates this notification if it cannot receive any response to an accounting or authentication request within the specified RADIUS request transmission attempts.
· RADIUS server reachable notification—The RADIUS server can be reached. RADIUS generates this notification for a previously blocked RADIUS server after the quiet timer expires.
· Excessive authentication failures notification—The number of authentication failures to the total number of authentication attempts exceeds the specified threshold.
You can configure SNMP parameters to control the output of these SNMP notifications. For more information, see Network Management and Monitoring Configuration Guide.
To enable SNMP notifications for RADIUS:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for RADIUS. |
snmp-agent trap enable radius [ accounting-server-down | authentication-error-threshold | authentication-server-down | accounting-server-up | authentication-server-up ] * |
By default, all types of SNMP notifications are enabled for RADIUS. |
Displaying and maintaining RADIUS
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the RADIUS scheme configuration. |
display radius scheme [ radius-scheme-name ] |
|
Display RADIUS packet statistics. |
display radius statistics |
|
Clear RADIUS statistics. |
reset radius statistics |
Configuring HWTACACS schemes
Configuration task list
|
Tasks at a glance |
|
(Required.) Creating an HWTACACS scheme |
|
(Required.) Specifying the HWTACACS authentication servers |
|
(Optional.) Specifying the HWTACACS authorization servers |
|
(Optional.) Specifying the HWTACACS accounting servers |
|
(Required.) Specifying the shared keys for secure HWTACACS communication |
|
(Optional.) Specifying a VPN for the scheme |
|
(Optional.) Setting the username format and traffic statistics units |
|
(Optional.) Specifying the source IP address for outgoing HWTACACS packets |
|
(Optional.) Setting HWTACACS timers |
|
(Optional.) Displaying and maintaining HWTACACS |
Creating an HWTACACS scheme
Create an HWTACACS scheme before performing any other HWTACACS configurations. You can configure a maximum of 16 HWTACACS schemes. An HWTACACS scheme can be used by multiple ISP domains.
To create an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an HWTACACS scheme and enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
By default, no HWTACACS scheme is defined. |
Specifying the HWTACACS authentication servers
You can specify one primary authentication server and a maximum of 16 secondary authentication servers for an HWTACACS scheme. When the primary server is not available, the device searches for the secondary servers in the order they are configured. The first secondary server in active state is used for communication.
If redundancy is not required, specify only the primary server. An HWTACACS server can function as the primary authentication server in one scheme and as the secondary authentication server in another scheme at the same time.
To specify an HWTACACS server by hostname in an MPLS VPN network, first complete one of the following tasks on the device:
· Configure hostname-to-IP address mappings for the VPN by using the ip host or ipv6 host command.
· Configure a DNS server for the VPN by using the dns server or ipv6 dns server command.
For more information about these commands, see Layer 3—IP Services Command Reference.
To specify HWTACACS authentication servers for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify HWTACACS authentication servers. |
· Specify the primary HWTACACS authentication
server: · Specify a secondary HWTACACS authentication server: |
By default, no authentication server is specified. Two HWTACACS authentication servers in a scheme, primary or secondary, cannot have the same combination of hostname, IP address, port number, and VPN. |
Specifying the HWTACACS authorization servers
You can specify one primary authorization server and a maximum of 16 secondary authorization servers for an HWTACACS scheme. When the primary server is not available, the device searches for the secondary servers in the order they are configured. The first secondary server in active state is used for communication.
If redundancy is not required, specify only the primary server. An HWTACACS server can function as the primary authorization server of one scheme and as the secondary authorization server of another scheme at the same time.
To specify an HWTACACS server by hostname in an MPLS VPN network, first complete one of the following tasks on the device:
· Configure hostname-to-IP address mappings for the VPN by using the ip host or ipv6 host command.
· Configure a DNS server for the VPN by using the dns server or ipv6 dns server command.
For more information about these commands, see Layer 3—IP Services Command Reference.
To specify HWTACACS authorization servers for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify HWTACACS authorization servers. |
· Specify the primary HWTACACS authorization
server: · Specify a secondary HWTACACS authorization server: |
By default, no authorization server is specified. Two HWTACACS authorization servers in a scheme, primary or secondary, cannot have the same combination of hostname, IP address, port number, and VPN. |
Specifying the HWTACACS accounting servers
You can specify one primary accounting server and a maximum of 16 secondary accounting servers for an HWTACACS scheme. When the primary server is not available, the device searches for the secondary servers in the order they are configured. The first secondary server in active state is used for communication.
If redundancy is not required, specify only the primary server. An HWTACACS server can function as the primary accounting server of one scheme and as the secondary accounting server of another scheme at the same time.
HWTACACS does not support accounting for FTP, SFTP, and SCP users.
To specify an HWTACACS server by hostname in an MPLS VPN network, first complete one of the following tasks on the device:
· Configure hostname-to-IP address mappings for the VPN by using the ip host or ipv6 host command.
· Configure a DNS server for the VPN by using the dns server or ipv6 dns server command.
For more information about these commands, see Layer 3—IP Services Command Reference.
To specify HWTACACS accounting servers for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify HWTACACS accounting servers. |
· Specify the primary HWTACACS accounting server: · Specify a secondary HWTACACS accounting server: |
By default, no accounting server is specified. Two HWTACACS accounting servers in a scheme, primary or secondary, cannot have the same combination of hostname, IP address, port number, and VPN. |
Specifying the shared keys for secure HWTACACS communication
The HWTACACS client and server use the MD5 algorithm and shared keys to generate the Authenticator value for packet authentication and user password encryption. The client and server must use the same key for each type of communication.
Perform this task to configure shared keys for servers in an HWTACACS scheme. The keys take effect on all servers for which a shared key is not individually configured.
To specify a shared key for secure HWTACACS communication:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify a shared key for secure HWTACACS authentication, authorization, or accounting communication. |
key { accounting | authentication | authorization } { cipher | simple } string |
By default, no shared key is specified. The shared key configured on the device must be the same as the shared key configured on the HWTACACS server. |
Specifying a VPN for the scheme
The VPN specified for an HWTACACS scheme applies to all servers in that scheme. If a VPN is also configured for an individual HWTACACS server, the VPN specified for the HWTACACS scheme does not take effect on that server.
To specify a VPN for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify a VPN for the HWTACACS scheme. |
vpn-instance vpn-instance-name |
By default, an HWTACACS scheme belongs to the public network. |
Setting the username format and traffic statistics units
A username is in the userid@isp-name format, where the isp-name argument represents the user's ISP domain name. By default, the ISP domain name is included in a username. If HWTACACS servers do not recognize usernames that contain ISP domain names, you can configure the device to send usernames without domain names to the servers.
If two or more ISP domains use the same HWTACACS scheme, configure the HWTACACS scheme to keep the ISP domain name in usernames for domain identification.
The device reports online user traffic statistics in accounting packets. The traffic measurement units are configurable, but they must be the same as the traffic measurement units configured on the HWTACACS accounting servers.
To set the username format and traffic statistics units for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Set the format of usernames sent to the HWTACACS servers. |
user-name-format { keep-original | with-domain | without-domain } |
By default, the ISP domain name is included in a username. |
|
4. (Optional.) Set the data flow and packet measurement units for traffic statistics. |
data-flow-format { data { byte | giga-byte | kilo-byte | mega-byte } | packet { giga-packet | kilo-packet | mega-packet | one-packet } }* |
By default, traffic is counted in bytes and packets. |
Specifying the source IP address for outgoing HWTACACS packets
The source IP address of HWTACACS packets that a NAS sends must match the IP address of the NAS configured on the HWTACACS server. An HWTACACS server identifies a NAS by IP address. When the HWTACACS server receives a packet, it checks whether the source IP address of the packet is the IP address of a managed NAS.
· If the source IP address of the packet is the IP address of a managed NAS, the server processes the packet.
· If the source IP address of the packet is not the IP address of a managed NAS, the server drops the packet.
To communicate with the HWTACACS server, the source address of outgoing HWTACACS packets is typically the IP address of an egress interface on the NAS. However, in some situations, you must change the source IP address. For example, when VRRP is configured for stateful failover, configure the virtual IP address of the uplink VRRP group as the source IP address.
You can specify the source IP address for outgoing HWTACACS packets in HWTACACS scheme view or in system view.
· The IP address specified in HWTACACS scheme view applies to one HWTACACS scheme.
· The IP address specified in system view applies to all HWTACACS schemes whose servers are in a VPN or the public network.
Before sending an HWTACACS packet, the NAS selects a source IP address in the following order:
1. The source IP address specified for the HWTACACS scheme.
2. The source IP address specified in system view for the VPN or public network, depending on where the HWTACACS server resides.
3. The IP address of the outbound interface specified by the route.
To specify a source IP address for all HWTACACS schemes of a VPN or the public network:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Specify a source IP address for outgoing HWTACACS packets. |
hwtacacs nas-ip { ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] |
By default, the IP address of the HWTACACS packet outbound interface is used as the source IP address. |
To specify a source IP address for an HWTACACS scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Specify the source IP address of outgoing HWTACACS packets. |
nas-ip { ipv4-address | ipv6 ipv6-address } |
By default, the source IP address specified by the hwtacacs nas-ip command in system view is used. If the source IP address is not specified, the IP address of the outbound interface is used. |
Setting HWTACACS timers
The device uses the following timers to control communication with an HWTACACS server:
· Server response timeout timer (response-timeout)—Defines the HWTACACS server response timeout timer. The device starts this timer immediately after an HWTACACS authentication, authorization, or accounting request is sent. If the device does not receive a response from the server within the timer, it sets the server to blocked. Then, the device sends the request to another HWTACACS server.
· Real-time accounting timer (realtime-accounting)—Defines the interval at which the device sends real-time accounting packets to the HWTACACS accounting server for online users.
· Server quiet timer (quiet)—Defines the duration to keep an unreachable server in blocked state. If a server is not reachable, the device changes the server status to blocked, starts this timer for the server, and tries to communicate with another server in active state. After the server quiet timer expires, the device changes the status of the server back to active.
The server quiet timer setting affects the status of HWTACACS servers. If the scheme includes one primary HWTACACS server and multiple secondary HWTACACS servers, the device communicates with the HWTACACS servers based on the following rules:
· When the primary server is in active state, the device communicates with the primary server.
· If the primary server fails, the device performs the following tasks:
¡ Changes the server status to blocked.
¡ Starts a quiet timer for the server.
¡ Tries to communicate with a secondary server in active state that has the highest priority.
· If the secondary server is unreachable, the device performs the following tasks:
¡ Changes the server status to blocked.
¡ Starts a quiet timer for the server.
¡ Tries to communicate with the next secondary server in active state that has the highest priority.
· The search process continues until the device finds an available secondary server or has checked all secondary servers in active state. If no server is available, the device considers the authentication, authorization, or accounting attempt a failure.
· When the quiet timer of a server expires, the status of the server changes back to active. The device does not check the server again during the authentication, authorization, or accounting process.
· When you remove a server in use, communication with the server times out. The device looks for a server in active state by first checking the primary server, and then checking secondary servers in the order they are configured.
· When the primary server and secondary servers are all in blocked state, the device tries to communicate with the primary server.
· When one or more servers are in active state, the device tries to communicate with these active servers only, even if they are unavailable.
· When an HWTACACS server's status changes automatically, the device changes this server's status accordingly in all HWTACACS schemes in which this server is specified.
To set HWTACACS timers:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter HWTACACS scheme view. |
hwtacacs scheme hwtacacs-scheme-name |
N/A |
|
3. Set the HWTACACS server response timeout timer. |
timer response-timeout seconds |
By default, the HWTACACS server response timeout timer is 5 seconds. |
|
4. Set the real-time accounting interval. |
timer realtime-accounting minutes |
By default, the real-time accounting interval is 12 minutes. A short interval helps improve accounting precision but requires many system resources. When there are 1000 or more users, set a longer interval. |
|
5. Set the server quiet timer. |
timer quiet minutes |
By default, the server quiet timer is 5 minutes. |
Displaying and maintaining HWTACACS
Execute the display command in any view and the reset command in user view.
|
Task |
Command |
|
Display the configuration or server statistics of HWTACACS schemes. |
display hwtacacs scheme [ hwtacacs-server-name [ statistics ] |
|
Clear HWTACACS statistics. |
reset hwtacacs statistics { accounting | all | authentication | authorization } |
Configuring LDAP schemes
Configuration task list
|
Tasks at a glance |
|
Configuring an LDAP server: · (Required.) Creating an LDAP server · (Required.) Configuring the IP address of the LDAP server · (Optional.) Specifying the LDAP version · (Optional.) Setting the LDAP server timeout period · (Required.) Configuring administrator attributes · (Required.) Configuring LDAP user attributes |
|
(Required.) Creating an LDAP scheme |
|
(Required.) Specifying the LDAP authentication server |
|
(Optional.) Displaying and maintaining LDAP |
Creating an LDAP server
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an LDAP server and enter LDAP server view. |
ldap server server-name |
By default, no LDAP server exists. |
Configuring the IP address of the LDAP server
|
Step |
Command |
Remarks |
|
1. Enter system view. |
System-view |
N/A |
|
2. Enter LDAP server view. |
ldap server server-name |
N/A |
|
3. Configure the IP address of the LDAP server. |
{ ip ip-address | ipv6 ipv6-address } [ port port-number ] [ vpn-instance vpn-instance-name ] |
By default, an LDAP server has no IP address. You can configure either an IPv4 address or an IPv6 address for an LDAP server. The most recent configuration takes effect. |
Specifying the LDAP version
Specify the LDAP version on the NAS. The device supports LDAPv2 and LDAPv3. The LDAP version specified on the device must be consistent with the version specified on the LDAP server.
To specify the LDAP version:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDAP server view. |
ldap server server-name |
N/A |
|
3. Specify the LDAP version. |
protocol-version { v2 | v3 } |
By default, LDAPv3 is used. A Microsoft LDAP server supports only LDAPv3. |
Setting the LDAP server timeout period
If the device sends a bind or search request to an LDAP server without receiving the server's response within the server timeout period, the authentication or authorization request times out. Then, the device tries the backup authentication or authorization method. If no backup method is configured in the ISP domain, the device considers the authentication or authorization attempt a failure.
To set the LDAP server timeout period:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDAP server view. |
ldap server server-name |
N/A |
|
3. Set the LDAP server timeout period. |
server-timeout time-interval |
By default, the LDAP server timeout period is 10 seconds. |
Configuring administrator attributes
To configure the administrator DN and password for binding with the LDAP server during LDAP authentication:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDAP server view. |
ldap server server-name |
N/A |
|
3. Specify the administrator DN. |
login-dn dn-string |
By default, no administrator DN is specified. The administrator DN specified on the device must be the same as configured on the LDAP server. |
|
4. Configure the administrator password. |
login-password { cipher | simple } password |
By default, no administrator password is specified. |
Configuring LDAP user attributes
To authenticate a user, an LDAP client must complete the following operations:
1. Establish a connection to the LDAP server.
2. Obtain the user DN from the LDAP server.
3. Use the user DN and the user password to bind with the LDAP server.
LDAP provides a DN search mechanism for obtaining the user DN. According to the mechanism, an LDAP client sends search requests to the server based on the search policy determined by the LDAP user attributes of the LDAP client.
The LDAP user attributes include:
· Search base DN.
· Search scope.
· Username attribute.
· Username format.
· User object class.
If the LDAP server contains many directory levels, a user DN search starting from the root directory can take a long time. To improve efficiency, you can change the start point by specifying the search base DN.
To configure LDAP user attributes:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDAP server view. |
ldap server server-name |
N/A |
|
3. Specify the user search base DN. |
search-base-dn base-dn |
By default, no user search base DN is specified. |
|
4. (Optional.) Specify the user search scope. |
search-scope { all-level | single-level } |
By default, the user search scope is all-level. |
|
5. (Optional.) Specify the username attribute. |
user-parameters user-name-attribute { name-attribute | cn | uid } |
By default, the username attribute is cn. |
|
6. (Optional.) Specify the username format. |
user-parameters user-name-format { with-domain | without-domain } |
By default, the username format is without-domain. |
|
7. (Optional.) Specify the user object class. |
user-parameters user-object-class object-class-name |
By default, no user object is specified, and the default user object class on the LDAP server is used. The default user object class for this command varies by device model. |
Creating an LDAP scheme
You can configure a maximum of 16 LDAP schemes. An LDAP scheme can be used by multiple ISP domains.
To create an LDAP scheme:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an LDAP scheme and enter LDAP scheme view. |
ldap scheme ldap-scheme-name |
By default, no LDAP scheme is defined. |
Specifying the LDAP authentication server
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter LDAP scheme view. |
ldap scheme ldap-scheme-name |
N/A |
|
3. Specify the LDAP authentication server. |
authentication-server server-name |
By default, no LDAP authentication server is specified. |
Displaying and maintaining LDAP
Execute the display command in any view.
|
Task |
Command |
|
Display the configuration of LDAP schemes. |
display ldap scheme [ scheme-name ] |
Configuring AAA methods for ISP domains
You configure AAA methods for an ISP domain by specifying configured AAA schemes in ISP domain view. Each ISP domain has a set of system-defined AAA methods, which are local authentication, local authorization, and local accounting. If you do not configure any AAA methods for an ISP domain, the device uses the system-defined AAA methods for users in the domain.
Configuration prerequisites
To use local authentication for users in an ISP domain, configure local user accounts on the device first. See "Configuring local user attributes."
To use remote authentication, authorization, and accounting, create the required RADIUS, HWTACACS, or LDAP schemes. For more information about the scheme configuration, see "Configuring RADIUS schemes," "Configuring HWTACACS schemes," and "Configuring LDAP schemes."
Creating an ISP domain
In a networking scenario with multiple ISPs, the device can connect to users of different ISPs. These users can have different user attributes, such as different username and password structures, different service types, and different rights. To manage users of different ISPs, configure ISP domains, and configure AAA methods and domain attributes for each ISP domain as needed.
The device supports a maximum of 16 ISP domains, including the system-defined ISP domain system. You can specify one of the ISP domains as the default domain. You can modify the settings of the ISP domain system, but you cannot delete the domain.
On the device, each user belongs to an ISP domain. If a user does not provide an ISP domain name at login, the device considers the user belongs to the default ISP domain.
An ISP domain cannot be deleted when it is the default ISP domain. Before you use the undo domain command, change the domain to a non-default ISP domain by using the undo domain default enable command.
To create an ISP domain:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an ISP domain and enter ISP domain view. |
domain isp-name |
N/A |
|
3. Return to system view. |
quit |
N/A |
|
4. (Optional.) Specify the default ISP domain. |
domain default enable isp-name |
By default, the default ISP domain is the system-defined ISP domain system. |
Setting ISP domain status
By placing the ISP domain in active or blocked state, you allow or deny network service requests from users in the domain.
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter ISP domain view. |
domain isp-name |
N/A |
|
3. Place the ISP domain in active or blocked state. |
state { active | block } |
By default, an ISP domain is in active state, and users in the domain can request network services. |
Configuring authentication methods for an ISP domain
Configuration prerequisites
Before configuring authentication methods, complete the following tasks:
1. Determine the access type or service type to be configured. With AAA, you can configure an authentication method for each access type and service type.
2. Determine whether to configure the default authentication method for all access types or service types. The default authentication method applies to all access users. However, the method has a lower priority than the authentication method that is specified for an access type or service type.
Configuration guidelines
When configuring authentication methods, follow these guidelines:
· If a RADIUS scheme is used for authentication but not for authorization in the ISP domain, AAA accepts only the authentication result from the RADIUS server. The Access-Accept message from the RADIUS server also includes the authorization information, but the device ignores the information.
· If an HWTACACS scheme is specified, the device uses the entered username for role authentication. If a RADIUS scheme is specified, the device uses the username $enabn$ on the RADIUS server for role authentication. The variable n represents a user role level. For more information about user role authentication, see Fundamentals Configuration Guide.
Configuration procedure
To configure authentication methods for an ISP domain:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter ISP domain view. |
domain isp-name |
N/A |
|
3. Specify the default authentication method for all types of users. |
authentication default { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | ldap-scheme ldap-scheme-name [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the default authentication method is local. The none keyword is not supported in FIPS mode. |
|
4. Specify the authentication method for LAN users. |
authentication lan-access { ldap-scheme ldap-scheme-name [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default authentication method is used for LAN users. The none keyword is not supported in FIPS mode. |
|
5. Specify the authentication method for login users. |
authentication login { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | ldap-scheme ldap-scheme-name [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the default authentication method is used for login users. The none keyword is not supported in FIPS mode. |
|
6. Specify the authentication method for portal users. |
authentication portal { ldap-scheme ldap-scheme-name [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default authentication method is used for portal users. The none keyword is not supported in FIPS mode. |
|
7. Specify the authentication method for obtaining a temporary user role. |
authentication super { hwtacacs-scheme hwtacacs-scheme-name | radius-scheme radius-scheme-name } * |
By default, the default authentication method is used for obtaining a temporary user role. |
Configuring authorization methods for an ISP domain
Configuration prerequisites
Before configuring authorization methods, complete the following tasks:
1. Determine the access type or service type to be configured. With AAA, you can configure an authorization scheme for each access type and service type.
2. Determine whether to configure the default authorization method for all access types or service types. The default authorization method applies to all access users. However, the method has a lower priority than the authorization method that is specified for an access type or service type.
Configuration guidelines
When configuring authorization methods, follow these guidelines:
· The device supports HWTACACS authorization but not LDAP authorization.
· To use a RADIUS scheme as the authorization method, specify the same RADIUS scheme that is configured as the authentication method for the ISP domain. If an invalid RADIUS scheme is specified as the authorization method, RADIUS authentication and authorization fail.
Configuration procedure
To configure authorization methods for an ISP domain:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter ISP domain view. |
domain isp-name |
N/A |
|
3. Specify the default authorization method for all types of users. |
authorization default { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the authorization method is local. The none keyword is not supported in FIPS mode. |
|
4. Specify the command authorization method. |
authorization command { hwtacacs-scheme hwtacacs-scheme-name [ local [ none ] | local [ none ] | none } |
By default, the default authorization method is used for command authorization. The none keyword is not supported in FIPS mode. |
|
5. Specify the authorization method for LAN users. |
authorization lan-access { local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default authorization method is used for LAN users. The none keyword is not supported in FIPS mode. |
|
6. Specify the authorization method for login users. |
authorization login { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the default authorization method is used for login users. The none keyword is not supported in FIPS mode. |
|
7. Specify the authorization method for portal users. |
authorization portal { local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default authorization method is used for portal users. The none keyword is not supported in FIPS mode. |
Configuring accounting methods for an ISP domain
Configuration prerequisites
Before configuring accounting methods, complete the following tasks:
1. Determine the access type or service type to be configured. With AAA, you can configure an accounting method for each access type and service type.
2. Determine whether to configure the default accounting method for all access types or service types. The default accounting method applies to all access users. However, the method has a lower priority than the accounting method that is specified for an access type or service type.
Configuration guidelines
When configuring accounting methods, follow these guidelines:
· FTP, SFTP, and SCP users do not support accounting.
· Local accounting does not provide statistics for charging. It only counts and controls the number of concurrent users who use the same local user account. The threshold is configured by using the access-limit command.
Configuration procedure
To configure accounting methods for an ISP domain:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter ISP domain view. |
domain isp-name |
N/A |
|
3. Specify the default accounting method for all types of users. |
accounting default { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the accounting method is local. The none keyword is not supported in FIPS mode. |
|
4. Specify the command accounting method. |
accounting command hwtacacs-scheme hwtacacs-scheme-name |
By default, the default accounting method is used for command accounting. |
|
5. Specify the accounting method for LAN users. |
accounting lan-access { local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default accounting method is used for LAN users. The none keyword is not supported in FIPS mode. |
|
6. Specify the accounting method for login users. |
accounting login { hwtacacs-scheme hwtacacs-scheme-name [ radius-scheme radius-scheme-name ] [ local ] [ none ] | local [ none ] | none | radius-scheme radius-scheme-name [ hwtacacs-scheme hwtacacs-scheme-name ] [ local ] [ none ] } |
By default, the default accounting method is used for login users. The none keyword is not supported in FIPS mode. |
|
7. Specify the accounting method for portal users. |
accounting portal { local [ none ] | none | radius-scheme radius-scheme-name [ local ] [ none ] } |
By default, the default accounting method is used for portal users. The none keyword is not supported in FIPS mode. |
Enabling the session-control feature
A RADIUS server running on IMC can use session-control packets to inform disconnect or dynamic authorization change requests. This task enables the device to receive RADIUS session-control packets on UDP port 1812.
To enable the session-control feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the session-control feature. |
radius session-control enable |
By default, the session-control feature is disabled. |
Setting the maximum number of concurrent login users
Perform this task to set the maximum number of concurrent users who can log on to the device through a specific protocol, regardless of their authentication methods. The authentication methods include no authentication, local authentication, and remote authentication.
To set the maximum number of concurrent login users:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of concurrent login users. |
· In non-FIPS mode: · In FIPS mode: |
By default, the maximum number of concurrent login users is 32 for each user type. |
Configuring a NAS-ID profile
By default, the device sends its device name in the NAS-Identifier attribute of any RADIUS requests.
A NAS-ID profile enables you to send different NAS-Identifier attribute strings in RADIUS requests from different VLANs. The strings can be organization names, service names, or any user categorization criteria, depending on the administrative requirements.
For example, map the NAS-ID companyA to all VLANs of company A. The device will send companyA in the NAS-Identifier attribute for the RADIUS server to identify requests from any Company A users.
You can apply a NAS-ID profile to portal- or port security-enabled interfaces. For more information, see "Configuring portal" and "Configuring port security."
A NAS-ID can be bound with more than one VLAN, but a VLAN can be bound with only one NAS-ID.
To configure a NAS-ID profile:
|
Command |
Remarks |
|
|
1. Enter system view. |
N/A |
|
|
2. Create a NAS-ID profile and enter NAS-ID profile view. |
N/A |
|
|
3. Configure a NAS-ID and VLAN binding in the profile. |
nas-id nas-identifier bind vlan vlan-id |
By default, no NAS-ID and VLAN binding exists. |
Displaying and maintaining AAA
Execute the display command in any view.
|
Task |
Command |
|
Display the configuration of ISP domains. |
display domain [ isp-name ] |
AAA configuration examples
AAA for SSH users by an HWTACACS server
Network requirements
As shown in Figure 11, configure the switch to meet the following requirements:
· Use the HWTACACS server for SSH user authentication, authorization, and accounting.
· Assign the default user role network-operator to SSH users after they pass authentication.
· Exclude domain names from the usernames sent to the HWTACACS server.
· Use expert as the shared keys for secure HWTACACS communication.

Configuration procedure
1. Configure the HWTACACS server:
# Set the shared keys for secure communication with the switch to expert. (Details not shown.)
# Add user account hello for the SSH user and specify the password. (Details not shown.)
2. Configure the switch:
# Configure IP addresses for interfaces. (Details not shown.)
# Create an HWTACACS scheme.
<Switch> system-view
[Switch] hwtacacs scheme hwtac
# Specify the primary authentication server.
[Switch-hwtacacs-hwtac] primary authentication 10.1.1.1 49
# Specify the primary authorization server.
[Switch-hwtacacs-hwtac] primary authorization 10.1.1.1 49
# Specify the primary accounting server.
[Switch-hwtacacs-hwtac] primary accounting 10.1.1.1 49
# Set the shared keys for secure HWTACACS communication to expert in plain text.
[Switch-hwtacacs-hwtac] key authentication simple expert
[Switch-hwtacacs-hwtac] key authorization simple expert
[Switch-hwtacacs-hwtac] key accounting simple expert
# Exclude domain names from the usernames sent to the HWTACACS server.
[Switch-hwtacacs-hwtac] user-name-format without-domain
[Switch-hwtacacs-hwtac] quit
# Create ISP domain bbb and configure the domain to use the HWTACACS scheme for authentication, authorization, and accounting of login users.
[Switch-isp-bbb] authentication login hwtacacs-scheme hwtac
[Switch-isp-bbb] authorization login hwtacacs-scheme hwtac
[Switch-isp-bbb] accounting login hwtacacs-scheme hwtac
[Switch-isp-bbb] quit
# Create local RSA and DSA key pairs.
[Switch] public-key local create rsa
[Switch] public-key local create dsa
# Enable the SSH service.
[Switch] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Switch] line vty 0 63
[Switch-line-vty0-63] authentication-mode scheme
[Switch-line-vty0-63] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Switch] role default-role enable
Verifying the configuration
# Initiate an SSH connection to the switch, and enter the username hello@bbb and the password. The user logs in to the switch. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)
Local authentication, HWTACACS authorization, and RADIUS accounting for SSH users
Network requirements
As shown in Figure 12, configure the switch to meet the following requirements:
· Perform local authentication for SSH servers.
· Use the HWTACACS server and RADIUS server for SSH user authorization and accounting, respectively.
· Exclude domain names from the usernames sent to the servers.
· Assign the default user role network-operator to SSH users after they pass authentication.
Configure an account with the username hello for the SSH user. Configure the shared keys for secure communication with the HWTACACS server and RADIUS server to expert.
Configuration procedure
1. Configure the HWTACACS server. (Details not shown.)
2. Configure the RADIUS server. (Details not shown.)
3. Configure the switch:
# Configure IP addresses for interfaces. (Details not shown.)
# Create local RSA and DSA key pairs.
<Switch> system-view
[Switch] public-key local create rsa
[Switch] public-key local create dsa
# Enable the SSH service.
[Switch] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Switch] line vty 0 63
[Switch-line-vty0-63] authentication-mode scheme
[Switch-line-vty0-63] quit
# Configure an HWTACACS scheme.
[Switch] hwtacacs scheme hwtac
[Switch-hwtacacs-hwtac] primary authorization 10.1.1.2 49
[Switch-hwtacacs-hwtac] key authorization simple expert
[Switch-hwtacacs-hwtac] user-name-format without-domain
[Switch-hwtacacs-hwtac] quit
# Configure a RADIUS scheme.
[Switch] radius scheme rd
[Switch-radius-rd] primary accounting 10.1.1.1 1813
[Switch-radius-rd] key accounting simple expert
[Switch-radius-rd] user-name-format without-domain
[Switch-radius-rd] quit
# Create a device management user.
[Switch] local-user hello class manage
# Assign the SSH service for the local user.
[Switch-luser-manage-hello] service-type ssh
# Set a password for the local user to 123456TESTplat&! in plain text. In FIPS mode, you must set the password in interactive mode.
[Switch-luser-manage-hello] password simple 123456TESTplat&!
[Switch-luser-manage-hello] quit
# Create ISP domain bbb and configure the login users to use local authentication, HWTACACS authorization, and RADIUS accounting.
[Switch] domain bbb
[Switch-isp-bbb] authentication login local
[Switch-isp-bbb] authorization login hwtacacs-scheme hwtac
[Switch-isp-bbb] accounting login radius-scheme rd
[Switch-isp-bbb] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Switch] role default-role enable
Verifying the configuration
# Initiate an SSH connection to the switch, and enter the username hello@bbb and the correct password. The user logs in to the switch. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)
Authentication and authorization for SSH users by a RADIUS server
Network requirements
As shown in Figure 13, configure the switch to meet the following requirements:
· Use the RADIUS server for SSH user authentication and authorization.
· Include domain names in the usernames sent to the RADIUS server.
· Assign the default user role network-operator to SSH users after they pass authentication.
The RADIUS server runs on IMC. Add an account with the username hello@bbb on the RADIUS server.
The RADIUS server and the switch use expert as the shared key for secure RADIUS communication. The ports for authentication and accounting are 1812 and 1813, respectively.

Configuration procedure
1. Configure the RADIUS server on IMC 5.0:
|
|
NOTE: This example assumes that the RADIUS server runs on IMC PLAT 5.0 (E0101) and IMC UAM 5.0 (E0101). |
# Add the switch to the IMC Platform as an access device.
Log in to IMC, click the Service tab, and select User Access Manager > Access Device Management > Access Device from the navigation tree. Then, click Add to configure an access device as follows:
a. Set the shared key for secure RADIUS communication to expert.
b. Set the ports for authentication and accounting to 1812 and 1813, respectively.
c. Select the service type Device Management Service.
d. Select the access device type H3C.
e. Select the access device from the device list or manually add the access device (with the IP address 10.1.1.2).
f. Leave the default settings for other parameters and click OK.
The IP address of the access device specified here must be the same as the source IP address of the RADIUS packets sent from the switch. The source IP address is chosen in the following order on the switch:
¡ IP address specified by the nas-ip command.
¡ IP address specified by the radius nas-ip command.
¡ IP address of the outbound interface (the default).
Figure 14 Adding the switch as an access device
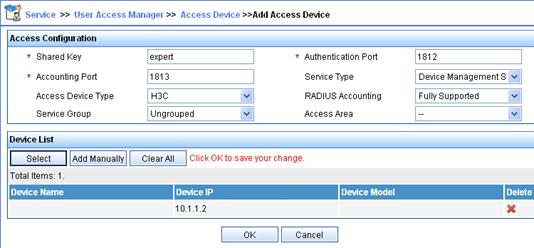
# Add an account for device management.
Click the User tab, and select Access User View > Device Mgmt User from the navigation tree. Then, click Add to configure a device management account as follows:
a. Enter the account name hello@bbb and specify the password.
b. Select the service type SSH.
c. Specify 10.1.1.0 to 10.1.1.255 as the IP address range of the hosts to be managed.
d. Click OK.
|
|
NOTE: The IP address range must contain the IP address of the switch. |
Figure 15 Adding an account for device management
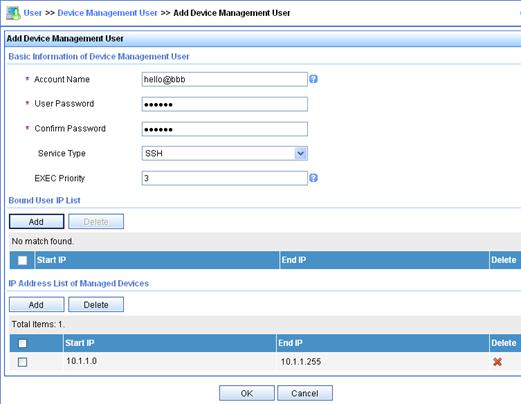
2. Configure the switch:
# Configure the IP address of VLAN-interface 2, through which the SSH user accesses the switch.
<Switch> system-view
[Switch] interface vlan-interface 2
[Switch-Vlan-interface2] ip address 192.168.1.70 255.255.255.0
[Switch-Vlan-interface2] quit
# Configure the IP address of VLAN-interface 3, through which the switch communicates with the server.
[Switch] interface vlan-interface 3
[Switch-Vlan-interface3] ip address 10.1.1.2 255.255.255.0
[Switch-Vlan-interface3] quit
# Create local RSA and DSA key pairs.
[Switch] public-key local create rsa
[Switch] public-key local create dsa
# Enable the SSH service.
[Switch] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Switch] line vty 0 63
[Switch-line-vty0-63] authentication-mode scheme
[Switch-line-vty0-63] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Switch] role default-role enable
# Create a RADIUS scheme.
[Switch] radius scheme rad
# Specify the primary authentication server.
[Switch-radius-rad] primary authentication 10.1.1.1 1812
# Set the shared key for secure communication with the server to expert in plain text.
[Switch-radius-rad] key authentication simple expert
# Include domain names in the usernames sent to the RADIUS server.
[Switch-radius-rad] user-name-format with-domain
[Switch-radius-rad] quit
# Create ISP domain bbb and configure authentication, authorization, and accounting methods for login users.
[Switch] domain bbb
[Switch-isp-bbb] authentication login radius-scheme rad
[Switch-isp-bbb] authorization login radius-scheme rad
[Switch-isp-bbb] accounting login none
[Switch-isp-bbb] quit
Verifying the configuration
# Initiate an SSH connection to the switch, and enter the username hello@bbb and the correct password. The user logs in to the switch. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)
Authentication for SSH users by an LDAP server
Network requirements
As shown in Figure 16, an LDAP server is located at 10.1.1.1/24 and uses the domain name ldap.com.
Configure the switch to meet the following requirements:
· Use the LDAP server to authenticate SSH users.
· Assign the default user role network-operator to SSH users after they pass authentication.
On the LDAP server, set the administrator password to admin!123456, add user aaa, and set the user password to ldap!123456.
Configuration procedure
1. Configure the LDAP server:
|
|
NOTE: This example assumes that the LDAP server runs Microsoft Windows 2003 Server Active Directory. |
# Add a user named aaa and set the password to ldap!123456.
a. On the LDAP server, select Start > Control Panel > Administrative Tools.
b. Double-click Active Directory Users and Computers.
The Active Directory Users and Computers window is displayed.
c. From the navigation tree, click Users under the ldap.com node.
d. Select Action > New > User from the menu to display the dialog box for adding a user.
e. Enter the logon name aaa and click Next.
Figure 17 Adding user aaa
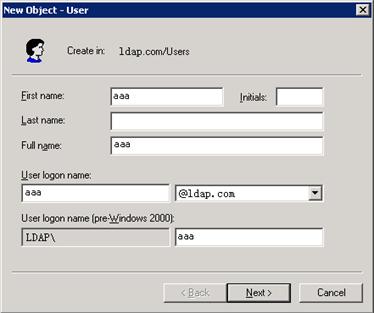
f. In the dialog box, enter the password ldap!123456, select options as needed, and click Next.
Figure 18 Setting the user password
g. Click OK.
# Add user aaa to group Users.
a. From the navigation tree, click Users under the ldap.com node.
b. In the right pane, right-click the user aaa and select Properties.
c. In the dialog box, click the Member Of tab and click Add.
Figure 19 Modifying user properties
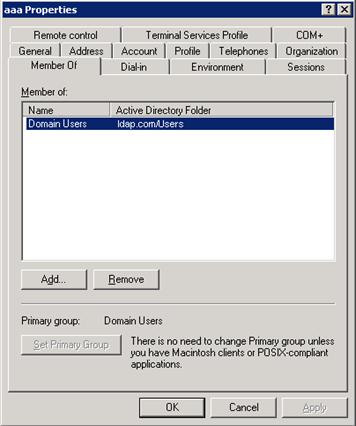
d. In the Select Groups dialog box, enter Users in the Enter the object names to select field, and click OK.
User aaa is added to group Users.
Figure 20 Adding user aaa to group Users
# Set the administrator password to admin!123456.
a. In the right pane, right-click the user Administrator and select Set Password.
b. In the dialog box, enter the administrator password. (Details not shown.)
2. Configure the switch:
# Configure the IP address of VLAN-interface 2, through which the SSH user accesses the switch.
<Switch> system-view
[Switch] interface vlan-interface 2
[Switch-Vlan-interface2] ip address 192.168.1.70 24
[Switch-Vlan-interface2] quit
# Configure the IP address of VLAN-interface 3, through which the switch communicates with the server.
[Switch] interface vlan-interface 3
[Switch-Vlan-interface3] ip address 10.1.1.2 24
[Switch-Vlan-interface3] quit
# Create local RSA and DSA key pairs.
[Switch] public-key local create rsa
[Switch] public-key local create dsa
# Enable the SSH service.
[Switch] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Switch] line vty 0 63
[Switch-line-vty0-63] authentication-mode scheme
[Switch-line-vty0-63] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Switch] role default-role enable
# Configure an LDAP server.
[Switch] ldap server ldap1
# Specify the IP address of the LDAP authentication server.
[Switch-ldap-server-ldap1] ip 10.1.1.1
# Specify the administrator DN.
[Switch-ldap-server-ldap1] login-dn cn=administrator,cn=users,dc=ldap,dc=com
# Specify the administrator password.
[Switch-ldap-server-ldap1] login-password simple admin!123456
# Configure the base DN for user search.
[Switch-ldap-server-ldap1] search-base-dn dc=ldap,dc=com
[Switch-ldap-server-ldap1] quit
# Create an LDAP scheme.
[Switch] ldap scheme ldap-shm1
# Specify the LDAP authentication server.
[Switch-ldap-ldap-shm1] authentication-server ldap1
[Switch-ldap-ldap-shm1] quit
# Create ISP domain bbb and configure authentication, authorization, and accounting methods for login users.
[Switch] domain bbb
[Switch-isp-bbb] authentication login ldap-scheme ldap-shm1
[Switch-isp-bbb] authorization login none
[Switch-isp-bbb] accounting login none
[Switch-isp-bbb] quit
Verifying the configuration
# Initiate an SSH connection to the switch, and enter the username aaa@bbb and password ldap!123456. The user logs in to the switch. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)
Troubleshooting RADIUS
RADIUS authentication failure
Symptom
User authentication always fails.
Analysis
Possible reasons include:
· A communication failure exists between the NAS and the RADIUS server.
· The username is not in the userid@isp-name format, or the ISP domain is not correctly configured on the NAS.
· The user is not configured on the RADIUS server.
· The password entered by the user is incorrect.
· The RADIUS server and the NAS are configured with different shared keys.
Solution
To resolve the problem:
1. Check that the following items:
¡ The NAS and the RADIUS server can ping each other.
¡ The username is in the userid@isp-name format and the ISP domain is correctly configured on the NAS.
¡ The user is configured on the RADIUS server.
¡ The correct password is entered.
¡ The same shared key is configured on both the RADIUS server and the NAS.
2. If the problem persists, contact H3C Support.
RADIUS packet delivery failure
Symptom
RADIUS packets cannot reach the RADIUS server.
Analysis
Possible reasons include:
· A communication failure exists between the NAS and the RADIUS server.
· The NAS is not configured with the IP address of the RADIUS server.
· The authentication and accounting UDP ports configured on the NAS are incorrect.
· The RADIUS server's authentication and accounting port numbers are being used by other applications.
Solution
To resolve the problem:
1. Check the following items:
¡ The link between the NAS and the RADIUS server work well at both the physical and data link layers.
¡ The IP address of the RADIUS server is correctly configured on the NAS.
¡ The authentication and accounting UDP port numbers configured on the NAS are the same as those of the RADIUS server.
¡ The RADIUS server's authentication and accounting port numbers are available.
2. If the problem persists, contact H3C Support.
RADIUS accounting error
Symptom
A user is authenticated and authorized, but accounting for the user is not normal.
Analysis
The accounting server configuration on the NAS is not correct. Possible reasons include:
· The accounting port number configured on the NAS is incorrect.
· The accounting server IP address configured on the NAS is incorrect. For example, the NAS is configured to use a single server to provide authentication, authorization, and accounting services, but in fact the services are provided by different servers.
Solution
To resolve the problem:
1. Check the following items:
¡ The accounting port number is correctly configured.
¡ The accounting server IP address is correctly configured on the NAS.
2. If the problem persists, contact H3C Support.
Troubleshooting HWTACACS
Similar to RADIUS troubleshooting. See "Troubleshooting RADIUS."
Troubleshooting LDAP
Symptom
User authentication fails.
Analysis
Possible reasons include:
· A communication failure exists between the NAS and the LDAP server.
· The LDAP server IP address or port number configured on the NAS is not correct.
· The username is not in the userid@isp-name format, or the ISP domain is not correctly configured on the NAS.
· The user is not configured on the LDAP server.
· The password entered by the user is incorrect.
· The administrator DN or password is not configured.
· Some user attributes (for example, the username attribute) configured on the NAS are not consistent with those configured on the server.
· No user search base DN is specified for the LDAP scheme.
Solution
To resolve the problem:
1. Check the following items:
¡ The NAS and the LDAP server can ping each other.
¡ The IP address and port number of the LDAP server configured on the NAS match those of the server.
¡ The username is in the correct format and the ISP domain for the user authentication is correctly configured on the NAS.
¡ The user is configured on the LDAP server.
¡ The correct password is entered.
¡ The administrator DN and the administrator password are correctly configured.
¡ The user attributes (for example, the username attribute) configured on the NAS are consistent with those configured on the LDAP server.
¡ The user search base DN for authentication is specified.
2. If the problem persists, contact H3C Support.