- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-SNMP Configuration | 139.54 KB |
Configuring SNMPv1 and SNMPv2c
Displaying and Maintaining SNMP
SNMPv1/SNMPv2c Configuration Example
SNMP Logging Configuration Example
Displaying and Maintaining MIB
l The models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region.
l Support of the H3C WA series WLAN access points for features may vary by AP model. For more information, see Feature Matrix.
l The interface types and the number of interfaces vary by AP model.
l The term AP in this document refers to common APs, wireless bridges, and mesh APs.
This chapter includes these sections:
l Displaying and Maintaining SNMP
l SNMPv1/SNMPv2c Configuration Example
l SNMPv3 Configuration Example
l SNMP Logging Configuration Example
SNMP Overview
The Simple Network Management Protocol (SNMP) offers the communication rules between a management device and the managed devices on the network. It defines a set of messages, methods and syntax to implement the access and management from the management device to the managed devices. SNMP has the following characteristics:
l Automatic network management: SNMP enables network administrators to search and modify information, find and diagnose network problems, plan for network growth, and generate reports on network nodes.
l SNMP shields the physical differences between various devices and thus realizes automatic management of products from different manufacturers. Offering only the basic set of functions, SNMP makes the management tasks independent of both the physical features of the managed devices and the underlying networking technology. Thus, SNMP achieves effective management of devices from different manufacturers, especially in small, high-speed and low cost network environments.
SNMP Mechanism
An SNMP managed network comprises primarily network management stations (NMSs) and an agent.
l An NMS is a station that runs SNMP client software. It offers a user-friendly interface, facilitating network administrators to perform most network management tasks.
l An agent is a program resides in the device. It receives and handles requests sent from the NMS. Only under certain circumstances, such as interface state change, will the agent inform the NMS.
An NMS is a manager in an SNMP enabled network, whereas agents are managed by the NMS. The NMS and agents exchange management information through the SNMP protocol.
SNMP provides the following four basic operations:
l Get operation: The NMS gets the value of one or more objects of the agent.
l Set operation: The NMS can reconfigure the value of one or more object in the agent MIB (Management Information Base) by means of this operation.
l Trap operation: The agent sends traps to the NMS through this operation.
l Inform operation: The NMS sends traps to other NMSs through this operation.
SNMP Protocol Versions
Currently, the SNMP agents on the AP support SNMPv3 and are compatible with SNMPv1 and SNMPv2c.
l SNMPv1 uses community name for authentication, which defines the relationship between an SNMP NMS and an SNMP agent. SNMP packets with community names that did not pass the authentication on the device will simply be discarded. A community name performs a similar role as a key word and can be used to regulate access from NMS to agent.
l SNMPv2c uses community name for authentication. Compatible with SNMPv1, it extends the functions of SNMPv1. SNMPv2c provides more operation modes such as GetBulk and InformRequest; it supports more data types such as Counter64; and it provides various error codes, thus being able to distinguish errors in more detail.
l SNMPv3 offers an authentication mechanism that is implemented based on the User-based Security Model (USM). You can set the authentication and privacy functions. The former is used to authenticate the validity of the sending end of the authentication packets, preventing access of unauthorized users; the latter is used to encrypt packets between the NMS and agents, preventing the packets from being intercepted. USM ensures a more secure communication between SNMP NMS and SNMP agent by authentication with privacy, authentication without privacy, or no authentication no privacy.
Successful interaction between an NMS and the agents requires consistency of SNMP versions configured on them.
MIB Overview
Any managed resource can be identified as an object, which is known as the managed object. Management Information Base (MIB) is a collection of all the managed objects. It defines the hierarchy of the objects and a set of characteristics associated with the managed objects, such as the object identifier (OID), access right and data type. Each agent has its own MIB. An NMS can read or write the managed objects in the MIB. The relationship between an NMS, agent and MIB is shown in Figure 1-1.
Figure 1-1 Relationship between NMS, agent and MIB
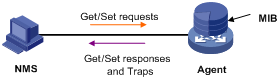
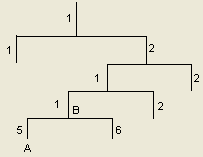
A MIB stores data using a tree structure. Each node of the tree represents a managed object that can be uniquely identified by a path starting from the root node. As illustrated in the following figure, the managed object A can be uniquely identified by a string of numbers {1.2.1.1.5}. This string of numbers is the OID of the managed object B.
Figure 1-2 MIB tree
Configuring SNMP
SNMPv3 differs from SNMPv1 and SNMPv2c in many aspects. Their configuration procedures are described in separate sections.
Configuring SNMPv3
Follow these steps to configure SNMPv3:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable SNMP agent |
snmp-agent |
Optional Disabled by default You can enable SNMP agent through this command or any commands that begin with snmp-agent. |
|
Configure SNMP agent system information |
snmp-agent sys-info { contact sys-contact | location sys-location | version { all | { v1 | v2c | v3 }* } } |
Optional The defaults are as follows: Hangzhou H3C Technologies Co., Ltd. for contact, Hangzhou China for location, and SNMP v3 for the version. |
|
Configure a local engine ID for an SNMP entity |
snmp-agent local-engineid engineid |
Optional Company ID and device ID by default. |
|
Create or update the MIB view content for an SNMP agent |
snmp-agent mib-view { excluded | included } view-name oid-tree [ mask mask-value ] |
Optional The MIB view name is ViewDefault and OID is 1 by default. |
|
Configure an SNMPv3 agent group |
snmp-agent group v3 group-name [ authentication | privacy ] [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number ] |
Required |
|
Convert a plain text key to an encrypted key |
snmp-agent calculate-password plain-password mode { 3desmd5 | 3dessha | md5 | sha } { local-engineid | specified-engineid engineid } |
Optional |
|
Add an SNMPv3 user to an SNMP agent group |
snmp-agent usm-user v3 user-name group-name [ [ cipher ] authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl acl-number ] |
Required If the cipher keyword is specified, the arguments auth-password and priv-password are considered as encrypted keys. |
|
Configure the maximum size of an SNMP packet that can be received or sent by an SNMP agent |
snmp-agent packet max-size byte-count |
Optional 1,500 bytes by default |
Configuring SNMPv1 and SNMPv2c
Follow these steps to configure SNMPv1 and SNMPv2c:
|
To do… |
Use the command… |
Remarks |
||
|
Enter system view |
system-view |
— |
||
|
Enable SNMP agent |
snmp-agent |
Optional Disabled by default You can also enable SNMP agent by using any commands that begin with snmp-agent. |
||
|
Configure SNMP agent system information |
snmp-agent sys-info { contact sys-contact | location sys-location | version { { v1 | v2c | v3 }* | all } } |
Required The defaults are as follows: Hangzhou H3C Technologies Co., Ltd. for contact, Hangzhou China for location and SNMP v3 for the version. |
||
|
Configure a local engine ID for an SNMP entity |
snmp-agent local-engineid engineid |
Optional Company ID and device ID by default. |
||
|
Create or update MIB view content for an SNMP agent |
snmp-agent mib-view { excluded | included } view-name oid-tree [ mask mask-value ] |
Optional ViewDefault by default |
||
|
Configure SNMP NMS access right |
Configure directly |
Create an SNMP community |
snmp-agent community { read | write } community-name [ acl acl-number | mib-view view-name ]* |
Use either approach. To be compatible with SNMPv3, use the snmp-agent group command. Ensure that the username is the same as the community name configured on the NMS. |
|
Configure indirectly |
Configure an SNMP group |
snmp-agent group { v1 | v2c } group-name [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number ] |
||
|
Add a new user to an SNMP group |
snmp-agent usm-user { v1 | v2c } user-name group-name [ acl acl-number ] |
|||
|
Configure the maximum size of an SNMP packet that can be received or sent by an SNMP agent |
snmp-agent packet max-size byte-count |
Optional 1500 bytes by default |
||
![]()
l The validity of a USM user depends on the engine ID of the SNMP agent. If the engine ID generated when the USM user is created is not identical to the current engine ID, the USM user is invalid.
l A MIB view is a subset of MIB and is uniquely identified by its view name and the MIB subtree together. MIB views with the same view name but containing different subtrees are considered different views. Except default MIB views, you can create at most 16 MIB views.
Configuring SNMP Logging
Introduction to SNMP Logging
The SNMP logging function logs the GET and SET operations that the NMS has performed on the SNMP agent.
l For a GET operation, the agent logs the IP address of the NMS, name of the accessed node, and OID of the node.
l For a SET operation, the agent logs the IP address of the NMS, name of the accessed node, OID of the node, the assigned value and the error code and error index of the SET response.
SNMP logs Get requests, Set requests and Set responses, but does not log Get responses.
The SNMP module sends these logs to the information center as informational messages. You may output these messages to certain destinations, for example, the console and the log buffer by configuring the information center to output informational messages to these destinations. For more information about the information center, see Information Center in the Network Management and Monitoring Configuration Guide.
Enabling SNMP Logging
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable SNMP logging |
snmp-agent log { all | get-operation | set-operation } |
Required Disabled by default. |
|
Configure SNMP log output rules |
info-center source { module-name | default } channel { channel-number | channel-name } [ debug { level severity | state state } * | log { level severity | state state } * | trap { level severity | state state } * ] * |
Optional By default, SNMP logs are output to loghost and logfile only. To output SNMP logs to other destinations such as console or monitor terminal, you need to set the output destinations with this command. |
![]()
l Disable SNMP logging in normal cases to prevent a large amount of SNMP logs from decreasing device performance.
l The total output size for the node and value fields in each log entry is 1024 bytes. If this limit is exceeded, the information center truncates the data in the fields.
Configuring SNMP Traps
Introduction to SNMP Traps
The SNMP agent sends traps to the NMS to inform the NMS of critical and important events (such as reboot of a managed device).
Two types of traps are available: generic traps and self-defined traps. Generic traps supported on the device include: authentication, coldstart, warmstart, linkdown, and linkup. The others are self-defined traps, which are generated by different modules.
SNMP traps generated by a module will be sent to the information center. The information center has seven information output destinations. By default:
l The information center outputs traps of all modules to the console, monitor terminal (monitor), loghost, and logfile; traps of all modules and with level equal to or higher than warnings are allowed to output to the trapbuffer and SNMP module (snmpagent)
l Traps cannot be sent to the logbuffer. You can set parameters for the information center based on the levels of the traps generated by each module, and thus decide the output rules of traps (that is, whether traps are allowed to be output and the output destinations). For more information about the information center, see Information Center in the Network Management and Monitoring Configuration Guide.
Enabling SNMP Traps
Enable SNMP traps only when necessary. SNMP traps are memory demanding and may affect device performance.
Follow these steps to enable the trap function:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the trap function globally |
snmp-agent trap enable [ configuration | flash | standard [ authentication | coldstart | linkdown | linkup | warmstart ] * | system | wlan ] |
Optional Enabled by default. |
|
Enter interface view |
interface interface-type interface-number |
Required |
|
Enable the trap function of interface state change |
enable snmp trap updown |
Optional Enabled by default. |
![]()
To enable an interface to send linkUp/linkDown traps when its state changes, enable the trap function of interface state changes on an interface and globally. To enable the trap function on an interface, use the enable snmp trap updown command. To enable this function globally, use the snmp-agent trap enable [ standard [ linkdown | linkup ] * ] command.
Configuring Trap Parameters
Configuration prerequisites
To send traps to the NMS, make the following preparations:
l Basic SNMP configurations have been completed. These configurations include version configuration: community name is needed when SNMPv1 and v2c are adopted; username and MIB view are needed if SNMPv3 is adopted.
l A connection has bee established between the device and the NMS, and they can operate each other.
Configuration procedure
When traps are sent to the SNMP module, the SNMP module saves the traps in the trap queue. You can set the size of the queue and the holding time of the traps in the queue, and you can also send the traps to the specified destination host (usually the NMS).
Follow these steps to configure trap parameters:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure target host attribute for traps |
snmp-agent target-host trap address udp-domain { ip-address | ipv6 ipv6-address } [ udp-port port-number ] params securityname security-string [ v1 | v2c | v3 [ authentication | privacy ] ] |
Optional To send the traps to the NMS, this command is required, and you must specify ip-address as the IP address of the NMS. |
|
Configure the source address for traps |
snmp-agent trap source interface-type interface-number |
Optional |
|
Extend the standard linkUp/linkDown traps defined in RFC |
snmp-agent trap if-mib link extended |
Optional Standard linkUp/linkDown traps defined in RFC are used by default. |
|
Configure the queue size for sending traps |
snmp-agent trap queue-size size |
Optional 100 by default |
|
Configure the holding time of the traps in the queue |
snmp-agent trap life seconds |
Optional 120 seconds by default |
![]()
l An extended linkUp/linkDown trap is the standard linkUp/linkDown trap (defined in RFC) appended with interface description and interface type information. If the extended messages are not supported on the NMS, disable this function to let the device send standard linkUp/linkDown traps.
l If the sending queue of traps is full, the system will automatically delete some oldest traps to receive new traps.
l The system automatically deletes the traps whose lifetime expires.
Displaying and Maintaining SNMP
|
To do… |
Use the command… |
Remarks |
|
Display SNMP-agent system information, including the contact, location, and version of the SNMP |
display snmp-agent sys-info [ contact | location | version ]* |
Available in any view |
|
Display SNMP agent statistics |
display snmp-agent statistics |
|
|
Display the SNMP agent engine ID |
display snmp-agent local-engineid |
|
|
Display SNMP agent group information |
display snmp-agent group [ group-name ] |
|
|
Display basic information of the trap queue |
display snmp-agent trap queue |
|
|
Display the modules that can send traps and whether their trap sending is enabled or not |
display snmp-agent trap-list |
|
|
Display SNMP v3 agent user information |
display snmp-agent usm-user [ engineid engineid | username user-name | group group-name ] * |
|
|
Display SNMP v1 or v2c agent community information |
display snmp-agent community [ read | write ] |
|
|
Display MIB view information for an SNMP agent |
display snmp-agent mib-view [ exclude | include | viewname view-name ] |
SNMPv1/SNMPv2c Configuration Example
Network requirements
l As shown in Figure 1-3, the NMS connects to AP through an Ethernet.
l The IP address of the NMS is 1.1.1.2/24.
l The IP address of the AP is 1.1.1.1/24.
l The NMS monitors and manages the AP using SNMPv1 or SNMPv2c. The AP reports errors or faults to the NMS.
Figure 1-3 Network diagram for SNMPv1/v2c

Configuration procedure
1) Configuring AP
# Configure the IP address of the AP as 1.1.1.1/24 and make sure that the AP and the NMS can reach other. (The configuration procedure is omitted here)
# Configure the SNMP basic information, including version and community name.
<Sysname> system-view
[Sysname] snmp-agent sys-info version v1 v2c
[Sysname] snmp-agent community read public
[Sysname] snmp-agent community write private
# Configure the contact person and physical location information of the AP.
[Sysname] snmp-agent sys-info contact Mr.Wang-Tel:3306
[Sysname] snmp-agent sys-info location telephone-closet,3rd-floor
# Enable the SNMP traps, set the NMS at IP address 1.1.1.2/24 as an SNMP trap destination, and use public as the community name. (To ensure that the NMS can receive traps, specify the same SNMP version in the snmp-agent target-host command as on the NMS.)
[Sysname] snmp-agent trap enable
[Sysname] snmp-agent target-host trap address udp-domain 1.1.1.2 udp-port 5000 params securityname public
2) Configuring the SNMP NMS
With SNMPv1/v2c, specify the read only community, the read and write community, the timeout time, and the number of retries. The user can inquire and configure the device through the NMS.
![]()
The configurations on the AP and the NMS must match.
3) Verify the configuration
l After the above configuration, an SNMP connection is established between the NMS and the AP. The NMS can get and configure the values of some parameters on the AP through MIB nodes.
l Execute the shutdown or undo shutdown command to an idle interface on the AP, and the NMS receives the corresponding trap.
SNMPv3 Configuration Example
Network requirements
l As shown in Figure 1-4, the NMS connects to the AP through an Ethernet.
l The IP address of the NMS is 1.1.1.2/24.
l The IP address of the AP is 1.1.1.1/24.
l The NMS monitors and manages the interface status of the AP using SNMPv3. The AP reports errors or faults to the NMS. The inbound port for traps on the NMS is 5000.
l When establishing the SNMP connection between the NMS and the agent, an authentication is required: the authentication algorithm is MD5 and the authentication key is authkey. In addition, packets transmitted between the agent and the NMS need to be encrypted: the privacy algorithm is DES56 and the privacy key is prikey.
Figure 1-4 Network diagram for SNMPv3

Configuration procedure
1) Configuring AP
# Configure the IP address of AP as 1.1.1.1/24 and make sure that the AP and the NMS can reach each other. (The configuration procedure is omitted here)
# Configure the access right: the user can read and write the objects under the interface node with the OID of 1.3.6.1.2.1.2, and cannot access other MIB objects. Set the user name to managev3user, authentication algorithm to MD5, authentication key to authkey, the encryption algorithm to DES56, and the privacy key to prikey.
<Sysname> system-view
[Sysname] undo snmp-agent mib-view ViewDefault
[Sysname] snmp-agent mib-view included test interfaces
[Sysname] snmp-agent group v3 managev3group read-view test write-view test
[Sysname] snmp-agent usm-user v3 managev3user managev3group authentication-mode md5 authkey privacy-mode des56 prikey
# Configure the contact person and physical location information of the device.
[Sysname] snmp-agent sys-info contact Mr.Wang-Tel:3306
[Sysname] snmp-agent sys-info location telephone-closet,3rd-floor
# Enable sending of traps to the NMS at IP address of 1.1.1.2/24, using public as the community name.
[Sysname] snmp-agent trap enable
[Sysname] snmp-agent target-host trap address udp-domain 1.1.1.2 udp-port 5000 params securityname public v3
2) Configuring the SNMP NMS
SNMPv3 uses an authentication and privacy security model. On the NMS, the user needs to specify the username and security level, and based on that level, configure the authentication mode, authentication key, privacy mode, and privacy key. In addition, the timeout time and number of retries should also be configured. The user can inquire and configure the device through the NMS.
![]()
The configurations on the AP and the NMS must match.
3) Verify the configuration
l After the above configuration, an SNMP connection is established between the NMS and the AP. The NMS can get and configure the values of some parameters on the agent through MIB nodes.
l Execute the shutdown or undo shutdown command to an idle interface on the AP, and the NMS receives the corresponding trap.
SNMP Logging Configuration Example
Network requirements
l As shown in Figure 1-5, the NMS and the AP are connected through an Ethernet
l The IP address of the NMS is 1.1.1.2/24
l The IP address of the AP is 1.1.1.1/24
l Configure SNMP logging on the agent to record the operations performed by the NMS to the agent
Figure 1-5 Network diagram for SNMP logging

Configuration procedure
![]()
For the configurations for the NMS and the AP, see SNMPv1/SNMPv2c Configuration Example and SNMPv3 Configuration Example.
# Enable log display on the console terminal (This function is enabled by default, so that you can omit this configuration).
<Sysname> terminal monitor
<Sysname> terminal logging
# Enable the information center to output the system information with the severity level equal to or higher than informational to the console port.
<Sysname> system-view
[Sysname] info-center source snmp channel console log level informational
# Enable SNMP logging on the AP to log the GET and SET operations of the NMS.
[Sysname] snmp-agent log get-operation
[Sysname] snmp-agent log set-operation
l The following log information is displayed on the terminal when NMS performs the GET operation on the AP.
%Jan 1 02:49:40:566 2006 Sysname SNMP/6/GET:
seqNO = <10> srcIP = <1.1.1.2> op = <get> node = <sysName(1.3.6.1.2.1.1.5.0)> value=<>
l The following log information is displayed on the console terminal when NMS performs the SET operation on the AP.
%Jan 1 02:59:42:576 2006 Sysname SNMP/6/SET:
seqNO = <11> srcIP = <1.1.1.2> op = <set> errorIndex = <0> errorStatus =<noError> node = <sysName(1.3.6.1.2.1.1.5.0)> value = <Sysname>
Table 1-1 Description on the output field of SNMP log
|
Field |
Description |
|
Jan 1 02:49:40:566 2006 |
The time when SNMP log is generated |
|
seqNO |
Sequence number of the SNMP log () |
|
srcIP |
IP address of NMS |
|
op |
SNMP operation type (GET or SET) |
|
node |
Node name of the SNMP operations and OID of the instance |
|
erroIndex |
Error index, with 0 meaning no error |
|
errorstatus |
Error status, with noError meaning no error |
|
value |
Value set when the SET operation is performed (This field is null, meaning the value obtained with the GET operation is not logged.) When the value is a string of characters and the string contains characters not in the range of ASCII 0 to 127 or invisible characters, the string is displayed in hexadecimal. For example, value = <81-43>[hex] |
![]()
The system information of the information center can be output to the console or to the log buffer. In this example, SNMP log is output to the console terminal. For information about the configuration of SNMP log output to other destinations, see Information Center in the Network Management and Monitoring Configuration Guide.
This chapter includes these sections:
l Overview
l Displaying and Maintaining MIB
Overview
The H3C private MIB has two styles: the H3C compatible MIB style and the H3C new MIB style. In the H3C compatible MIB style, the device sysOID is under the H3C’s enterprise ID 25506, and the private MIB is under the enterprise ID 2011. In the H3C new MIB style, both the device sysOID and the private MIB are under the H3C’s enterprise ID 25506. These two styles of MIBs implement the same management function except for their root nodes. A device is shipped with MIB loaded and the MIB style may vary depending on the device. To implement NMS’s flexible management of the device, the device allows you to configure MIB style, that is, you can switch between the two styles of MIBs. However, you need to ensure that the MIB style of the device is the same as that of the NMS.
Setting the MIB Style
Follow these steps to set the MIB style:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the MIB style |
mib-style [ new | compatible ] |
Optional new by default |
![]()
After changing the MIB style, reboot the device to validate the change.
Displaying and Maintaining MIB
|
To do… |
Use the command… |
Remarks |
|
Display the MIB style |
display mib-style |
Available in any view |
