- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 07-Public Key Configuration | 60 KB |
Asymmetric Key Algorithm Overview
Asymmetric Key Algorithm Applications
Configuring the Local Asymmetric Key Pair
Creating an Asymmetric Key Pair
Displaying or Exporting the Local RSA Host Public Key
Destroying an Asymmetric Key Pair
Configuring the Public Key of a Peer
Displaying and Maintaining Public Keys
Public Key Configuration Examples
l The models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region.
l Support of the H3C WA series WLAN access points (APs) for features may vary by AP model. For more information, see Feature Matrix.
l The interface types and the number of interfaces vary by AP model.
l The term AP in this document refers to common APs, wireless bridges, and mesh APs.
This chapter includes these sections:
l Asymmetric Key Algorithm Overview
l Configuring the Local Asymmetric Key Pair
l Configuring the Public Key of a Peer
l Displaying and Maintaining Public Keys
l Public Key Configuration Examples
Asymmetric Key Algorithm Overview
Basic Concepts
l Algorithm: A set of transformation rules for encryption and decryption.
l Plain text: Information without being encrypted.
l Cipher text: Encrypted information.
l Key: A string of characters that controls the transformation between plain text and cipher text. It participates in both the encryption and decryption.
Key Algorithm Types
As shown in Figure 1-1, the information in plain text is encrypted by an algorithm with the help of a key before being sent. The resulting cipher text is transmitted across the network to the receiver, where it is decrypted by the same algorithm also with the help of a key to obtain the original plain text.
Figure 1-1 Encryption and decryption
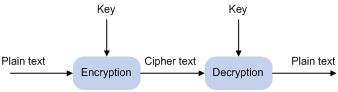
There are two types of key algorithms, based on whether the keys for encryption and decryption are the same:
l Symmetric key algorithm – The keys for encryption and decryption are the same. Commonly used symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
l Asymmetric key algorithm – The keys for encryption and decryption are different, one is the public key, and the other is the private key. The information encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. The private key is kept secret while the public key may be distributed widely, and the private key cannot be practically derived from the public key.
Asymmetric Key Algorithm Applications
Asymmetric key algorithms can be used for encryption/decryption and digital signature:
l Encryption/decryption – The sender uses the public key of the intended receiver to encrypt the information to be sent. Only the intended receiver, the holder of the paired private key, can decrypt the information. This mechanism ensures the confidentiality.
l Digital signature – The sender "signs" the information to be sent by encrypting the information with its own private key. A receiver decrypts the information with the sender's public key and, based on whether the information can be decrypted, determines the authenticity of the information.
Revest-Shamir-Adleman Algorithm (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA) are both asymmetric key algorithms. RSA can be used for data encryption/decryption and signature, whereas ECDSA is used for signature only.
![]()
Symmetric key algorithms are often used to encrypt/decrypt data for security. Asymmetric key algorithms are usually used in digital signature applications for peer identity authentication because they involve complex calculations and are time-consuming. In digital signature applications, only the digests, which are relatively short, are encrypted.
Configuring the Local Asymmetric Key Pair
You can create and destroy a local asymmetric key pair, and export the host public key of a local asymmetric key pair.
Creating an Asymmetric Key Pair
Follow these steps to create an asymmetric key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a local ECDSA key pair or RSA key pairs |
public-key local create { ecdsa | rsa } |
Required By default, there is no such key pair. |
l The public-key local create rsa command generates two key pairs: one server key pair and one host key pair. Each key pair consists of a public key and a private key.
l The length of an RSA key modulus is in the range 512 to 2048 bits. After entering the public-key local create rsa command, you are required to specify the modulus length. To achieve higher security, specify a modulus at least at least 768 bits.
l The length of an ECDSA host key modulus cannot exceed 192 bits.
![]()
Key pairs created with the public-key local create command are saved automatically and can survive system reboots.
Displaying or Exporting the Local RSA Host Public Key
Display the local RSA host public key on the screen or export it to a specified file. Then, you can configure the local RSA host public key on the remote end so that the remote end can use the host public key to authenticate the local end through digital signature.
Follow these steps to display or export the local RSA host public key:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Display the local RSA host public key on the screen in a specified format, or export it to a specified file |
public-key local export rsa { openssh | ssh1 | ssh2 } [ filename ] |
Required |
Destroying an Asymmetric Key Pair
An asymmetric key pair may expire or leak. In this case, destroy it and generate a new pair.
Follow these steps to destroy an asymmetric key pair:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Destroy an asymmetric key pair |
public-key local destroy { ecdsa | rsa } |
Required |
Configuring the Public Key of a Peer
To enable your local host to authenticate a remote host, configure the RSA public key of that peer on the local host by following either of the methods:
l Configure it manually: View the peer's host public key by the display command or other means on the remote host and record the public key. On the local host, input or copy the key data in public key code view.
l Import it from the public key file: The system automatically converts the public key to a string coded using the PKCS (Public Key Cryptography Standards). Before importing the public key, you must upload the peer's public key file (in binary) to the local host through FTP or TFTP.
![]()
l If you choose to input the public key, the public key must be in a correct format. The key data displayed by the display public-key local public command meets the format requirements. The public key displayed in other methods may not meet the format requirements. A format-incompliant key cannot be saved. Thus, you are recommended to configure the public key of the peer by importing it from a public key file.
l The AP supports up to 20 host pubic keys of peers.
Follow these steps to configure the public key of a peer manually:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter public key view |
public-key peer keyname |
— |
|
Enter public key code view |
public-key-code begin |
— |
|
Configure a public key of the peer |
Type or copy the key |
Required Spaces and carriage returns are allowed between characters. |
|
Return to public key view |
public-key-code end |
— When you exit public key code view, the system automatically saves the public key. |
|
Return to system view |
peer-public-key end |
— |
Follow these steps to import the host public key of a peer from the public key file:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Import the host public key of a peer from the public key file |
public-key peer keyname import sshkey filename |
Required |
Displaying and Maintaining Public Keys
|
To do… |
Use the command… |
Remarks |
|
Display the public keys of the local key pairs |
display public-key local { ecdsa | rsa } public |
Available in any view |
|
Display the public keys of the peers |
display public-key peer [ brief | name publickey-name ] |
Public Key Configuration Examples
For public key configuration examples, see the following configuration guides:
l SSH2.0 in the Security Configuration Guide
l HTTP in the Fundamentals Configuration Guide
