- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-AAA Configuration | 362.8 KB |
Security Authentication Mechanism
Basic Message Exchange Process of RADIUS
Configuring ISP Domain Attributes
Configuring AAA Authentication Methods for an ISP Domain
Configuring AAA Authorization Methods for an ISP Domain
Configuring AAA Accounting Methods for an ISP Domain
Configuring Local User Attributes
Tearing down User Connections Forcibly
Configuring a NAS ID-VLAN Binding
Displaying and Maintaining AAA
Specifying the RADIUS Authentication/Authorization Servers
Specifying the RADIUS Accounting Servers and Relevant Parameters
Setting the Shared Key for RADIUS Packets
Setting the Upper Limit of RADIUS Request Retransmission Attempts
Setting the Supported RADIUS Server Type
Setting the Status of RADIUS Servers
Configuring Attributes Related to the Data Sent to the RADIUS Server
Enabling the RADIUS Trap Function
Specifying the Source IP Address for RADIUS Packets to Be Sent
Setting Timers Regarding RADIUS Servers
Configuring RADIUS Accounting-on
Specifying Security Policy Servers
Enabling the Listening Port of the RADIUS Client
Configuring Interpretation of RADIUS Class Attribute as CAR Parameters
Displaying and Maintaining RADIUS
AAA for Telnet Users by a RADIUS Server
AAA for Telnet Users by Separate APs
Troubleshooting RADIUS Authentication/Authorization Failure
Troubleshooting RADIUS Packet Transmission Failure
Troubleshooting RADIUS Accounting Failure
Commonly Used Standard RADIUS Attributes
Proprietary RADIUS Sub-Attributes of H3C
l Support of the H3C WA series WLAN access points (APs) for features may vary by AP model. For more information, see Feature Matrix.
l The interface types and the number of interfaces vary by AP model.
l The term AP in this document refers to common APs, wireless bridges, or mesh APs.
l The models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region.
This chapter includes these sections:
l Domain-Based User Management
Introduction to AAA
Authentication, Authorization, and Accounting (AAA) provides a uniform framework for configuring these three security functions to implement network security management.
AAA usually uses a client/server model, where the client runs on the network access server (NAS) and the server maintains user information centrally. In an AAA network, a NAS is a server for users but a client for the AAA servers, as shown in Figure 1-1.
Figure 1-1 AAA networking diagram
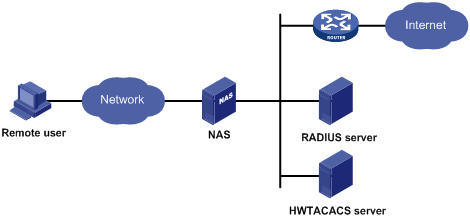
When a user tries to establish a connection to the NAS and obtain the rights to access other networks or some network resources, the NAS authenticates the user or the corresponding connection. The NAS can also transparently pass the user authentication, authorization and accounting information to the server (RADIUS server or HWTACACS server). The RADIUS/HWTACACS protocol defines how to exchange user information between a NAS and a server.
In the AAA network shown in Figure 1-1, there is a RADIUS server and a HWTACACS server. You can determine the authentication, authorization and accounting method according to the actual requirements. For example, you can use the HWTACACS server for authentication and authorization, and the RADIUS server for accounting.
The three security functions are described as follows:
l Authentication: Identifies remote users and judges whether a user is legal.
l Authorization: Grants different users different rights. For example, a user logging into the server can be granted the permission to access and print the files in the server.
l Accounting: Records all network service usage information of users, including the service type, start and end time, and traffic. In this way, accounting can be used for not only accounting itself, but also network security surveillance.
You can use AAA to provide only one or two security functions, if desired. For example, if your company only wants employees to be authenticated before they access specific resources, you can configure only an authentication server. If the network usage information is expected to be recorded, you also need to configure an accounting server.
As mentioned above, AAA provides a uniform framework to implement network security management. It is a security mechanism that enables authenticated and authorized entities to access specific resources and records operations by the entities. The AAA framework thus allows for excellent scalability and centralized user information management.
AAA can be implemented through multiple protocols. Currently, the AP supports using only RADIUS for AAA.
Introduction to RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a distributed information interaction protocol in the client/server model. RADIUS can protect networks against unauthorized access and is often used in network environments where both high security and remote user access are required. Based on UDP, RADIUS defines the RADIUS packet format and the message transfer mechanism, and uses UDP port 1812 as the authentication port and 1813 as the accounting port.
RADIUS was originally designed for dial-in user access. With the diversification of access methods, RADIUS has been extended to support more access methods, for example, Ethernet access and ADSL access. It uses authentication and authorization to provide access service and uses accounting to collect and record usage of network resources by users.
Client/Server Model
Client: The RADIUS client runs on the NASs located throughout the network. It passes user information to designated RADIUS servers and acts on the response (for example, rejects or accepts user access requests).
Server: The RADIUS server runs on the computer or workstation at the network center and maintains information related to user authentication and network service access. It authenticates a user after receiving a connection request and returns the processing result (for example, rejecting or accepting user access requests) to the client.
In general, the RADIUS server maintains three databases, namely, Users, Clients, and Dictionary, as shown in Figure 1-2:
Figure 1-2 RADIUS server components
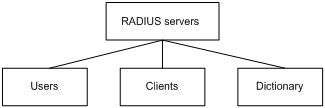
l Users: Stores user information such as the username, password, applied protocols, and IP address.
l Clients: Stores information about RADIUS clients such as the shared keys and IP addresses.
l Dictionary: Stores the information for interpreting RADIUS protocol attributes and their values.
Security Authentication Mechanism
Information exchanged between the RADIUS client and the RADIUS server is authenticated with a shared key, which is never transmitted over the network, thus enhancing the security of information exchange. To prevent user passwords from being intercepted in non-secure networks, the passwords are encrypted during transmission.
A RADIUS server supports multiple user authentication methods, such as the Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) of Point-to-Point Protocol (PPP). In addition, a RADIUS server can act as the client of another AAA server to provide proxy authentication or accounting service.
Basic Message Exchange Process of RADIUS
For the interaction among the host, the RADIUS client, and the RADIUS server, see Figure 1-3.
Figure 1-3 Basic message exchange process of RADIUS
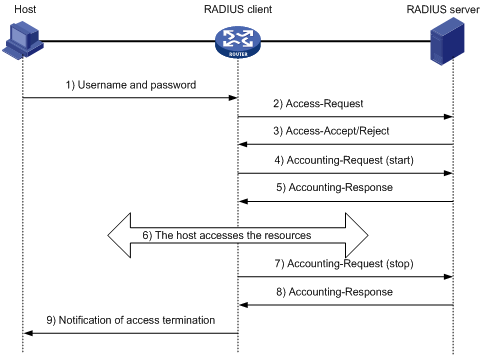
The following is how RADIUS operates:
1) The host initiates a connection request carrying the username and password to the RADIUS client.
2) Having received the username and password, the RADIUS client sends an authentication request (Access-Request) to the RADIUS server, where the user password is encrypted by the Message-Digest 5 (MD5) algorithm with the shared key.
3) The RADIUS server authenticates the username and password. If the authentication succeeds, it sends back an Access-Accept message containing the information of user’s right. If the authentication fails, it returns an Access-Reject message.
4) The RADIUS client accepts or denies the user according to the returned authentication result. If it accepts the user, it sends a start-accounting request (Accounting-Request) to the RADIUS server.
5) The RADIUS server returns a start-accounting response (Accounting-Response) and starts accounting.
6) The subscriber accesses the network resources.
7) The host requests the RADIUS client to tear down the connection and the RADIUS client sends a stop-accounting request (Accounting-Request) to the RADIUS server.
8) The RADIUS server returns a stop-accounting response (Accounting-Response) and stops accounting.
9) The subscriber stops network resource accessing.
RADIUS Packet Structure
RADIUS uses UDP to transmit messages. It ensures the smooth message exchange between the RADIUS server and the client through a series of mechanisms, including the timer management mechanism, retransmission mechanism, and slave server mechanism. Figure 1-4 shows the RADIUS packet structure.
Figure 1-4 RADIUS packet structure
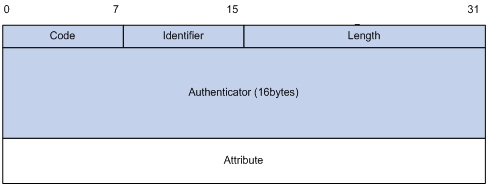
Descriptions of fields are as follows:
1) The Code field (1-byte long) is for indicating the type of the RADIUS packet. Table 1-1 gives the possible values and their meanings.
Table 1-1 Main values of the Code field
|
Code |
Packet type |
Description |
|
1 |
Access-Request |
From the client to the server. A packet of this type carries user information for the server to authenticate the user. It must contain the User-Name attribute and can optionally contain the attributes of NAS-IP-Address, User-Password, and NAS-Port. |
|
2 |
Access-Accept |
From the server to the client. If all the attribute values carried in the Access-Request are acceptable, that is, the authentication succeeds, the server sends an Access-Accept response. |
|
3 |
Access-Reject |
From the server to the client. If any attribute value carried in the Access-Request is unacceptable, the server rejects the user and sends an Access-Reject response. |
|
4 |
Accounting-Request |
From the client to the server. A packet of this type carries user information for the server to start/stop accounting on the user. It contains the Acct-Status-Type attribute, which indicates whether the server is requested to start the accounting or to end the accounting. |
|
5 |
Accounting-Response |
From the server to the client. The server sends to the client a packet of this type to notify that it has received the Accounting-Request and has correctly recorded the accounting information. |
2) The Identifier field (1-byte long) is for matching request packets and response packets and detecting retransmitted request packets. A request packet and its response packet have the same identifier.
3) The Length field (2-byte long) indicates the length of the entire packet, including the Code, Identifier, Length, Authenticator, and Attribute fields. The value of the field is in the range 20 to 4096. Bytes beyond the length are considered the padding and are neglected after being received. If the length of a received packet is less than that indicated by the Length field, the packet is dropped.
4) The Authenticator field (16-byte long) is used to authenticate the reply from the RADIUS server, and is also used in the password hiding algorithm. There are two kinds of authenticators: Request authenticator and Response authenticator.
5) The Attribute field carries information about the configuration details of a request or response. This field is represented in triplets of Type, Length, and Value.
l Type: One byte, in the range 1 to 255. It indicates the type of the attribute. Commonly used attributes for RADIUS authentication, authorization, and accounting are listed in Table 1-2.
l Length: One byte for indicating the length of the attribute in bytes, including the Type, Length, and Value fields.
l Value: Value of the attribute, up to 253 bytes. Its format and content depend on the Type and Length fields.
|
No. |
Attribute type |
No. |
Attribute type |
|
1 |
User-Name |
45 |
Acct-Authentic |
|
2 |
User-Password |
46 |
Acct-Session-Time |
|
3 |
CHAP-Password |
47 |
Acct-Input-Packets |
|
4 |
NAS-IP-Address |
48 |
Acct-Output-Packets |
|
5 |
NAS-Port |
49 |
Acct-Terminate-Cause |
|
6 |
Service-Type |
50 |
Acct-Multi-Session-Id |
|
7 |
Framed-Protocol |
51 |
Acct-Link-Count |
|
8 |
Framed-IP-Address |
52 |
Acct-Input-Gigawords |
|
9 |
Framed-IP-Netmask |
53 |
Acct-Output-Gigawords |
|
10 |
Framed-Routing |
54 |
(unassigned) |
|
11 |
Filter-ID |
55 |
Event-Timestamp |
|
12 |
Framed-MTU |
56-59 |
(unassigned) |
|
13 |
Framed-Compression |
60 |
CHAP-Challenge |
|
14 |
Login-IP-Host |
61 |
NAS-Port-Type |
|
15 |
Login-Service |
62 |
Port-Limit |
|
16 |
Login-TCP-Port |
63 |
Login-LAT-Port |
|
17 |
(unassigned) |
64 |
Tunnel-Type |
|
18 |
Reply Message |
65 |
Tunnel-Medium-Type |
|
19 |
Callback-Number |
66 |
Tunnel-Client-Endpoint |
|
20 |
Callback-ID |
67 |
Tunnel-Server-Endpoint |
|
21 |
(unassigned) |
68 |
Acct-Tunnel-Connection |
|
22 |
Framed-Route |
69 |
Tunnel-Password |
|
23 |
Framed-IPX-Network |
70 |
ARAP-Password |
|
24 |
State |
71 |
ARAP-Features |
|
25 |
Class |
72 |
ARAP-Zone-Access |
|
26 |
Vendor-Specific |
73 |
ARAP-Security |
|
27 |
Session-Timeout |
74 |
ARAP-Security-Data |
|
28 |
Idle-Timeout |
75 |
Password-Retry |
|
29 |
Termination-Action |
76 |
Prompt |
|
30 |
Called-Station-Id |
77 |
Connect-Info |
|
31 |
Calling-Station-Id |
78 |
Configuration-Token |
|
32 |
NAS-Identifier |
79 |
EAP-Message |
|
33 |
Proxy-State |
80 |
Message-Authenticator |
|
34 |
Login-LAT-Service |
81 |
Tunnel-Private-Group-id |
|
35 |
Login-LAT-Node |
82 |
Tunnel-Assignment-id |
|
36 |
Login-LAT-Group |
83 |
Tunnel-Preference |
|
37 |
Framed-AppleTalk-Link |
84 |
ARAP-Challenge-Response |
|
38 |
Framed-AppleTalk-Network |
85 |
Acct-Interim-Interval |
|
39 |
Framed-AppleTalk-Zone |
86 |
Acct-Tunnel-Packets-Lost |
|
40 |
Acct-Status-Type |
87 |
NAS-Port-Id |
|
41 |
Acct-Delay-Time |
88 |
Framed-Pool |
|
42 |
Acct-Input-Octets |
89 |
(unassigned) |
|
43 |
Acct-Output-Octets |
90 |
Tunnel-Client-Auth-id |
|
44 |
Acct-Session-Id |
91 |
Tunnel-Server-Auth-id |
![]()
l The attribute types listed in Table 1-2 are defined by RFC 2865, RFC 2866, RFC 2867, and RFC 2568.
l For information about commonly used standard RADIUS attributes, see Commonly Used Standard RADIUS Attributes.
RADIUS Extended Attributes
The RADIUS protocol features excellent extensibility. Attribute 26 (Vender-Specific) defined by RFC 2865 allows a vender to define extended attributes to implement functions that the standard RADIUS protocol does not provide.
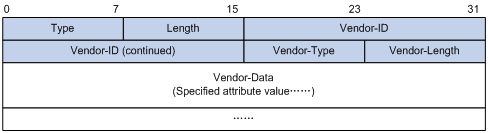
A vendor can encapsulate multiple type-length-value (TLV) sub-attributes in RADIUS packets for extension in applications. As shown in Figure 1-5, a sub-attribute that can be encapsulated in Attribute 26 consists of the following four parts:
l Vendor-ID (four bytes): Indicates the ID of the vendor. Its most significant byte is 0 and the other three bytes contain a code complying with RFC 1700. The vendor ID of H3C is 2011. For information about the proprietary RADIUS sub-attributes of H3C, see Proprietary RADIUS Sub-Attributes of H3C.
l Vendor-Type: Indicates the type of the sub-attribute.
l Vendor-Length: Indicates the length of the sub-attribute.
l Vendor-Data: Indicates the contents of the sub-attribute.
Figure 1-5 Segment of a RADIUS packet containing an extended attribute
Domain-Based User Management
An Internet service provider (ISP) domain accommodates a collection of users. NAS devices manage users based on ISP domains. Each user belongs to an ISP domain. The ISP domain of a user is determined by the username used for login, as shown in Figure 1-6.
Figure 1-6 Determine the ISP domain of a user by the username

AAA for a user depends on the AAA methods configured for the domain that the user belongs to. If no specific AAA methods are configured for the domain, the default ones are used. By default, a domain uses local authentication, local authorization, and local accounting.
The AAA feature allows you to manage users based on their access types:
l LAN users: Users on a LAN who access through, for example, 802.1X authentication or MAC address authentication.
l Login users: Users who wants to log in to the AP, including SSH users, Telnet users, Web users, FTP users, and terminal service users.
l PPP users: Users who access through PPP.
l Command line users: Users who can use only the commands authorized by the server.
l Privilege level switching users: Users who can switch to a higher level privilege without logging out the current system or disconnecting the current connections.
You can configure different authentication, authorization, and accounting methods for different users in a domain. For more configuration information, see Configuring AAA.
For command line users, you can configure only authorization and accounting methods, which will be used for authorizing configuration commands and tracking commands used by users respectively.
Protocols and Standards
The protocols and standards related to AAA and RADIUS include:
l RFC 2865: Remote Authentication Dial In User Service (RADIUS)
l RFC 2866: RADIUS Accounting
l RFC 2867: RADIUS Accounting Modifications for Tunnel Protocol Support
l RFC 2868: RADIUS Attributes for Tunnel Protocol Support
l RFC 2869: RADIUS Extensions
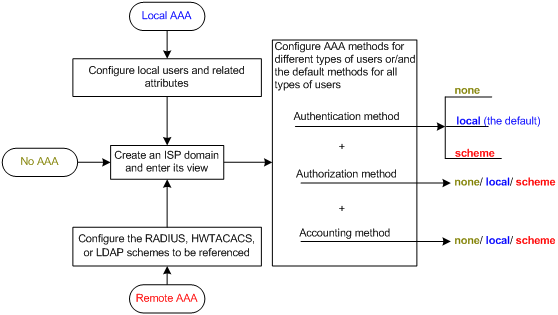
AAA Configuration Task List
The basic procedure to configure AAA is as follows:
1) Configure the required AAA schemes.
l Local authentication: Configure local users and related attributes, including usernames and passwords of the users to be authenticated.
l Remote authentication: Configure the required RADIUS schemes, and configure user attributes on the servers accordingly.
2) Configure the AAA methods: Reference the configured AAA schemes in the users’ ISP domains.
l Authentication method: No authentication (none), local authentication (local), or remote authentication (scheme)
l Authorization method: No authorization (none), local authorization (local), or remote authorization (scheme)
l Accounting method: No accounting (none), local accounting (local), or remote accounting (scheme)
Figure 1-7 illustrates the configuration procedure.
Figure 1-7 AAA configuration procedure
![]()
For login users, it is necessary to configure the authentication mode for logging into the user interface to scheme. For more information, see Logging In to the AP in the Fundamentals Configuration Guide.
AAA configuration task list
|
Task |
Remarks |
|
Required |
|
|
Optional |
|
|
Required |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
RADIUS configuration task list
|
Task |
Remarks |
|
Required |
|
|
Required |
|
|
Specifying the RADIUS Accounting Servers and Relevant Parameters |
Optional |
|
Required |
|
|
Setting the Upper Limit of RADIUS Request Retransmission Attempts |
Optional |
|
Optional |
|
|
Optional |
|
|
Configuring Attributes Related to the Data Sent to the RADIUS Server |
Optional |
|
Optional |
|
|
Specifying the Source IP Address for RADIUS Packets to Be Sent |
Optional |
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Optional |
|
|
Configuring Interpretation of RADIUS Class Attribute as CAR Parameters |
Optional |
|
Optional |
Configuring AAA
By configuring AAA, you can provide network access service for legal users, protect the networking devices, and avoid unauthorized access and bilking. In addition, you can configure ISP domains to perform AAA on accessing users.
Configuration Prerequisites
For remote authentication, authorization, or accounting, you must create the RADIUS scheme first, and then reference the RADIUS scheme to implement authentication/authorization and accounting. For RADIUS scheme configuration, see Configuring RADIUS.
Creating an ISP Domain
In a networking scenario with multiple ISPs, an access device may connect users of different ISPs. Because users of different ISPs may have different user attributes (such as username and password structure, service type, and rights), you need to configure multiple ISP domains for them and to configure different attribute sets including the AAA methods (such as the RADIUS schemes) for the ISP domains.
For the NAS, each accessing user belongs to an ISP domain. Up to 16 ISP domains can be configured on a NAS. If a user does not provide the ISP domain name, the system considers that the user belongs to the default ISP domain.
Follow these steps to create an ISP domain:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create an ISP domain and enter ISP domain view |
domain isp-name |
Required |
|
Return to system view |
quit |
— |
|
Specify the default ISP domain |
domain default enable isp-name |
Optional The system-default ISP domain named system by default |
![]()
l You cannot delete the default ISP domain unless you change it to a non-default ISP domain (with the domain default disable command) first.
l If a user enters a username without an ISP domain name, the AP uses the authentication method for the default ISP domain to authenticate the user.
Configuring ISP Domain Attributes
Follow these steps to configure ISP domain attributes:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter ISP domain view |
domain isp-name |
— |
|
Place the ISP domain to the state of active or blocked |
state { active | block } |
Optional When created, an ISP is in the state of active by default, and users in the domain can request network services. |
|
Specify the maximum number of users in the ISP domain |
access-limit enable max-user-number |
Optional No limit by default |
|
Configure the idle cut function |
idle-cut enable minute flow |
Optional Disabled by default |
|
Enable the self-service server localization function and specify the URL of the self-service server for changing user password |
self-service-url enable url-string |
Optional Disabled by default Currently, this command is effective only for LAN users and PPP users. |
|
Define an IP address pool for allocating addresses to PPP users |
ip pool pool-number low-ip-address [ high-ip-address ] |
Optional No IP address pool is configured for PPP users by default. |
![]()
Configuring AAA Authentication Methods for an ISP Domain
In AAA, authentication, authorization, and accounting are three separate processes. Authentication refers to the interactive authentication process of username/password/user information during access or service request. The authentication process neither sends authorization information to a supplicant nor triggers any accounting.
AAA supports the following authentication methods:
l No authentication (none): All users are trusted and no authentication is performed. Generally, this method is not recommended.
l Local authentication (local): Authentication is performed by the NAS. User information (including username, password, and attributes) is configured on the AP. Local authentication features high speed and low cost, but the amount of information that can be stored is limited by the hardware.
l Remote authentication (scheme): The AP cooperates with a RADIUS server to authenticate users. The AP can use the standard RADIUS protocol or extended RADIUS protocol in collaboration with systems like CAMS and iMC to implement user authentication. Remote authentication features centralized information management, high capacity, high reliability, and support for centralized authentication for multiple access devices. You can configure local authentication as the backup method to be used when the remote server is not available.
You can configure AAA to use only authentication. If you do not perform any authentication configuration, an ISP domain uses the local authentication method.
Before configuring an authentication method, complete these three tasks:
l For RADIUS authentication, configure the RADIUS scheme to be referenced first. The local and none authentication methods do not require any scheme.
l Determine the access mode or service type to be configured. With AAA, you can configure an authentication method specifically for each access mode and service type, limiting the authentication protocols that can be used for access.
l Determine whether to configure an authentication method for all access modes or service types.
Follow these steps to configure AAA authentication methods for an ISP domain:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter ISP domain view |
domain isp-name |
— |
|
Specify the default authentication method for all types of users |
authentication default { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional local by default |
|
Specify the authentication method for LAN users |
authentication lan-access { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authentication method is used by default. |
|
Specify the authentication method for login users |
authentication login { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authentication method is used by default. |
|
Specify the authentication method for PPP users |
authentication ppp { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authentication method is used by default. |
|
Specify the authentication method for privilege level switching |
authentication super radius-scheme radius-scheme-name |
Optional The default authentication method is used by default. |
![]()
l The authentication method specified with the authentication default command is for all types of users and has a priority lower than that for a specific access mode.
l With a RADIUS authentication method configured, AAA accepts only the authentication result from the RADIUS server. The response from the RADIUS server does include the authorization information when the authentication is successful, but the authentication process ignores the information.
l With the radius-scheme radius-scheme-name local keyword and argument combination configured, the local method is the backup method and is used only when the remote server is not available.
l If the primary authentication method is local or none, the system performs local authentication or does not perform any authentication, rather than uses the RADIUS method.
l If the method for level switching authentication references a RADIUS scheme, the system uses the username configured for the corresponding privilege level on the RADIUS server for level switching authentication. A username configured on the RADIUS server is in the format of $enab+level, where level specifies the privilege level to which the user wants to switch. For example, if user user1 wants to switch the privilege level to 3, the system uses $enab3@domain_name for authentication when the domain name is required and uses $enab3 for authentication when the domain name is not required.
l For more information about user privilege level switching, see Basic System in the Fundamentals Configuration Guide.
Configuring AAA Authorization Methods for an ISP Domain
In AAA, authorization is a separate process at the same level as authentication and accounting. Its responsibility is to send authorization requests to the specified authorization server and to send authorization information to users authorized. Authorization method configuration is optional in AAA configuration.
AAA supports the following authorization methods:
l Direct authorization (none): All users are trusted and authorized. A user gets the default rights of the system.
l Local authorization (local): Users are authorized by the AP according to the attributes configured for them.
l Remote authorization (scheme): The AP cooperates with a RADIUS server to authorize users. RADIUS authorization is bound with RADIUS authentication. RADIUS authorization can work only after RADIUS authentication is successful, and the authorization information is carried in the RADIUS authentication response. You can configure local authorization or no authorization as the backup method to be used when the remote server is not available.
If you do not perform any authorization configuration, an ISP domain uses the local authorization method. With the authorization method of none, the users are not required to be authorized, in which case an authenticated user has the default right. The default right is visiting (the lowest one) for EXEC users (that is, console users who use the console, or Telnet to connect to the AP, such as Telnet or SSH users. Each connection of these types is called an EXEC user). The default right for FTP users is to use the root directory of the AP.
Before configuring an authorization method, complete these three tasks:
1) For RADIUS authorization, the RADIUS authorization scheme must be the same as the RADIUS authentication scheme; otherwise, it does not take effect.
2) Determine the access mode or service type to be configured. With AAA, you can configure an authorization method specifically for each access mode and service type, limiting the authorization protocols that can be used for access.
3) Determine whether to configure an authorization method for all access modes or service types.
Follow these steps to configure AAA authorization methods for an ISP domain:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter ISP domain view |
domain isp-name |
— |
|
Specify the default authorization method for all types of users |
authorization default { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional local by default |
|
Specify the authorization method for command line users |
authorization command { local | none } |
Optional The default authorization method is used by default. |
|
Specify the authorization method for LAN users |
authorization lan-access { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authorization method is used by default. |
|
Specify the authorization method for login users |
authorization login { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authorization method is used by default. |
|
Specify the authorization method for PPP users |
authorization ppp { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default authorization method is used by default. |
![]()
l The authorization method specified with the authorization default command is for all types of users and has a priority lower than that for a specific access mode.
l RADIUS authorization is special in that it takes effect only when the RADIUS authorization scheme is the same as the RADIUS authentication scheme. In addition, if a RADIUS authorization fails, the error message returned to the NAS says that the server is not responding.
l With the radius-scheme radius-scheme-name local keyword and argument combination configured, the local method is the backup method and is used only when the RADIUS server is not available.
l If the primary authentication method is local or none, the system performs local authorization or does not perform any authorization, rather than uses the RADIUS method.
l Authorization information of the RADIUS server is sent to the RADIUS client along with the authorization response message; therefore, you cannot specify a separate RADIUS server. If you use RADIUS for authorization and authentication, you must use the same scheme setting for authorization and authentication; otherwise, the system will prompt you with an error message.
Configuring AAA Accounting Methods for an ISP Domain
In AAA, accounting is a separate process at the same level as authentication and authorization. Its responsibility is to send accounting start/update/end requests to the specified accounting server. Accounting is not required, and therefore accounting method configuration is optional. If you do not perform any accounting configuration, an ISP domain uses the local accounting method.
AAA supports the following accounting methods:
l No accounting (none): The system does not perform accounting on the users.
l Local accounting (local): Local accounting is implemented on the AP. It is for controlling the number of local user connections and collecting statistics on the number of users; it does not provide statistics on the charges of users.
l Remote accounting (scheme): Accounting is implemented by a RADIUS server remotely. You can configure local accounting as the backup method to be used when the remote server is not available.
Before configuring an accounting method, complete these three tasks:
1) For RADIUS accounting, configure the RADIUS scheme to be referenced first. The local and none authentication methods do not require any scheme.
2) Determine the access mode or service type to be configured. With AAA, you can configure an accounting method specifically for each access mode and service type, limiting the accounting protocols that can be used for access.
3) Determine whether to configure an accounting method for all access modes or service types.
Follow these steps to configure AAA accounting methods for an ISP domain:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter ISP domain view |
domain isp-name |
— |
|
Enable the accounting optional feature |
accounting optional |
Optional Disabled by default |
|
Specify the default accounting method for all types of users |
accounting default { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional local by default |
|
Specify the accounting method for LAN users |
accounting lan-access { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default accounting method is used by default. |
|
Specify the accounting method for login users |
accounting login { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default accounting method is used by default. |
|
Specify the accounting method for PPP users |
accounting ppp { local | none | radius-scheme radius-scheme-name [ local ] } |
Optional The default accounting method is used by default. |
![]()
l With the accounting optional command configured, a user that will be disconnected otherwise can use network resources even when there is no available accounting server or communication with the current accounting server fails.
l Local accounting is not used to implement accounting, but to work together with the access-limit command, which is configured in local user view, to limit the number of local user connections. However, with the accounting optional command configured, the limit on the number of local user connections is not effective.
l The accounting method specified with the accounting default command is for all types of users and has a priority lower than that for a specific access mode.
l With the radius-scheme radius-scheme-name local keyword and argument combination configured, local accounting is the backup method and is used only when the RADIUS server is not available.
l If the primary accounting method is local or none, the system performs local accounting or does not perform any accounting, rather than uses the RADIUS method.
l In login access mode, accounting is not supported for FTP services.
Configuring Local User Attributes
For local authentication, you must create a local user and configure the attributes.
A local user represents a set of users configured on the AP, which are uniquely identified by the username. For a user requesting network service to pass local authentication, you must add an entry for the user in the local user database of the AP.
Follow these steps to configure the attributes for a local user:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Set the password display mode for all local users |
local-user password-display-mode { auto | cipher-force } |
Optional auto by default, indicating to display the password of a local user in the way indicated by the password command. |
|
Add a local user and enter local user view |
local-user user-name |
Required No local user is configured by default |
|
Configure a password for the local user |
password { cipher | simple } password |
Optional |
|
Place the local user to the state of active or blocked |
state { active | block } |
Optional When created, a local user is in the state of active by default, and the user can request network services. |
|
Set the maximum number of user connections using the local user account |
access-limit max-user-number |
Optional By default, there is no limit on the maximum number of user connections using the same local user account. |
|
Specify the service types for the user |
service-type { ftp | lan-access | { ssh | telnet | terminal } * telnet | ppp } |
Optional No service is authorized to a user by default. |
|
Configure the binding attributes for the local user |
bind-attribute { call-number call-number [ : subcall-number ] | ip ip-address | location port slot-number subslot-number port-number | mac mac-address | vlan vlan-id } * |
Optional By default, no binding attribute is configured for a local user. |
|
Configure the authorization attributes for the local user |
authorization-attribute { acl acl-number | callback-number callback-number | idle-cut minute | level level | vlan vlan-id | work-directory directory-name } * |
Optional By default, no authorization attribute is configured for a local user. |
|
Set the expiration time of the local user |
expiration-date time |
Optional Not set by default. If some users need to access the network temporarily, you can create a guest account and specify an expiration time for the account. |
![]()
l With the local-user password-display-mode cipher-force command configured, a local user password is always displayed in cipher text, regardless of the configuration of the password command. In this case, if you use the save command to save the configuration, all existing local user passwords will still be displayed in cipher text after the AP restarts, even if you restore the display mode to auto.
l The access-limit command configured for a local user takes effect only when local accounting is used.
l Local authentication checks the service types of a local user. If the service types are not available, the user cannot pass authentication.
l In the authentication method that requires the username and password, including local authentication and RADIUS authentication, the level of the commands that a user can use after logging in depends on the priority of the user. In other authentication methods, the level of commands depends on the priority of user interface level. For more information about authentication method and command level, see Logging In to the AP in the Fundamentals Configuration Guide.
l Binding attributes are checked upon authentication of a local user. If the checking fails, the user fails the authentication. Therefore, be cautious when deciding which binding attributes should be configured for a local user.
l Every configurable authorization attribute has its definite application environments and purposes. Therefore, when configuring authorization attributes for a local user, consider what attributes are needed. For example, for PPP users, you do not need to configure the work directory attribute.
Tearing down User Connections Forcibly
Follow these steps to tear down user connections forcibly:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Tear down AAA user connections forcibly |
cut connection { all | domain isp-name | ucibindex ucib-index | user-name user-name | vlan vlan-id } |
Required Applies to only LAN access, and PPP user connections at present |
Configuring a NAS ID-VLAN Binding
In some application scenarios, it is required to identify the access locations of users. To meet the requirement, you must configure NAS ID-VLAN bindings on the AP, so that when a user gets online, the AP can obtain the NAS ID by the access VLAN of the user and then send the NAS ID to the RADIUS server through the NAS-identifier attribute.
Follow these steps to configure a NAS ID-VLAN binding:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a NAS ID profile and enter NAS ID profile view |
aaa nas-id profile profile-name |
Required |
|
Configure a NAS ID-VLAN binding |
nas-id nas-identifier bind vlan vlan-id |
Required By default, no NAS ID-VLAN binding exists. |
Displaying and Maintaining AAA
|
To do… |
Use the command… |
Remarks |
|
Display the configuration information of a specified ISP domain or all ISP domains |
display domain [ isp-name ] |
Available in any view |
|
Display information about specified or all user connections |
display connection [ domain isp-name | ucibindex ucib-index | user-name user-name ] |
Available in any view |
|
Display information about specified or all local users |
display local-user [ idle-cut { disable | enable } | service-type { ftp | lan-access | ppp | ssh | telnet | terminal } | state { active | block } | user-name user-name | | vlan vlan-id ] |
Available in any view |
Configuring RADIUS
The RADIUS protocol is configured scheme by scheme. After creating a RADIUS scheme, you need to configure the IP addresses and UDP ports of the RADIUS servers for the scheme. The servers include authentication/authorization servers and accounting servers, or from another point of view, primary servers and secondary servers. In other words, the attributes of a RADIUS scheme mainly include IP addresses of primary and secondary servers, shared key, and RADIUS server type.
Actually, the RADIUS protocol configurations only set the parameters necessary for the information interaction between a NAS and a RADIUS server. For these settings to take effect, you must reference the RADIUS scheme containing those settings in ISP domain view. For information about the commands for referencing a scheme, see Configuring AAA.
![]()
When there are users online, you cannot modify RADIUS parameters other than the number of retransmission attempts and the timers.
Creating a RADIUS Scheme
Before performing other RADIUS configurations, follow these steps to create a RADIUS scheme and enter RADIUS scheme view:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a RADIUS scheme and enter RADIUS scheme view |
radius scheme radius-scheme-name |
Required Not defined by default |
![]()
A RADIUS scheme can be referenced by more than one ISP domain at the same time.
Specifying the RADIUS Authentication/Authorization Servers
Follow these steps to specify the RADIUS authentication/authorization servers:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify the primary RADIUS authentication/authorization server |
primary authentication { ip-address | ipv6 ipv6-address } [ port-number ] |
Required Use either approach By default, neither the primary nor the secondary authentication/authorization server is specified. |
|
Specify the secondary RADIUS authentication/authorization server |
secondary authentication { ip-address | ipv6 ipv6-address } [ port-number ] |
![]()
l It is recommended to specify only the primary RADIUS authentication/authorization server if backup is not required.
l If both the primary and secondary authentication/authorization servers are specified, the secondary one is used when the primary one is unreachable.
l In practice, you may specify two RADIUS servers as the primary and secondary authentication/authorization servers respectively. At one time, a server can be the primary authentication/authorization server for a scheme and the secondary authentication/authorization servers for another scheme.
l The IP addresses of the primary and secondary authentication/authorization servers for a scheme cannot be the same. Otherwise, the configuration fails.
l All servers for authentication/authorization and accounting, primary or secondary, must use IP addresses of the same IP version.
Specifying the RADIUS Accounting Servers and Relevant Parameters
Follow these steps to specify the RADIUS accounting servers and perform related configurations:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Create a RADIUS scheme and enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify the primary RADIUS accounting server |
primary accounting {ip-address | ipv6 ipv6-address } [ port-number ] |
Required Use either approach By default, neither the primary nor the secondary accounting server is specified |
|
Specify the secondary RADIUS accounting server |
secondary accounting { ip-address ipv6 ipv6-address } [ port-number ] |
|
|
Enable the AP to buffer stop-accounting requests getting no responses |
stop-accounting-buffer enable |
Optional Enabled by default |
|
Set the maximum number of stop-accounting request transmission attempts |
retry stop-accounting retry-times |
Optional 500 by default |
|
Set the maximum number of accounting request transmission attempts |
retry realtime-accounting retry-times |
Optional 5 by default |
![]()
l It is recommended to specify only the primary RADIUS accounting server if backup is not required.
l If both the primary and secondary accounting servers are specified, the secondary one is used when the primary one is not reachable.
l In practice, you can specify two RADIUS servers as the primary and secondary accounting servers respectively; or specify one server to function as the primary accounting server in a scheme and the secondary accounting server in another scheme.. Besides, because RADIUS uses different UDP ports to receive authentication/authorization and accounting packets, the port for authentication/authorization must be different from that for accounting.
l You can set the maximum number of stop-accounting request transmission buffer, allowing the AP to buffer and resend a stop-accounting request until it receives a response or the number of transmission retries reaches the configured limit. In the latter case, the AP discards the packet.
l You can set the maximum number of accounting request transmission attempts on the AP, allowing the AP to disconnect a user when the number of accounting request transmission attempts for the user reaches the limit but it still receives no response to the accounting request.
l The IP addresses of the primary and secondary accounting servers cannot be the same. Otherwise, the configuration fails.
l Currently, RADIUS does not support keeping accounts on FTP users.
l All servers for authentication/authorization and accounting, primary or secondary, must use IP addresses of the same IP version.
Setting the Shared Key for RADIUS Packets
The RADIUS client and RADIUS server use the MD5 algorithm to encrypt packets exchanged between them and a shared key to verify the packets. Only when the same key is used can they properly receive the packets and make responses.
Follow these steps to set the shared key for RADIUS packets:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Set the shared key for RADIUS authentication/authorization or accounting packets |
key { accounting | authentication } string |
Required No key by default |
![]()
The shared key configured on the AP must be the same as that configured on the RADIUS server.
Setting the Upper Limit of RADIUS Request Retransmission Attempts
Because RADIUS uses UDP packets to carry data, the communication process is not reliable. If a NAS receives no response from the RADIUS server before the response timeout timer expires, it is required to retransmit the RADIUS request. If the number of transmission attempts exceeds the specified limit but it still receives no response, it considers that the authentication has failed.
Follow these steps to set the upper limit of RADIUS request retransmission attempts:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Set the number of retransmission attempts of RADIUS packets |
retry retry-times |
Optional 3 by default |
![]()
l The maximum number of retransmission attempts of RADIUS packets multiplied by the RADIUS server response timeout period cannot be greater than 75.
l For how to configure the RADIUS server response timeout period, see the timer response-timeout command in the command reference.
Setting the Supported RADIUS Server Type
Follow these steps to set the supported RADIUS server type:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify the RADIUS server type supported by the AP |
server-type { extended | standard } |
Optional By default, the supported RADIUS server type is standard. |
![]()
l If you change the type of RADIUS server, the data stream destined to the original RADIUS server will be restored to the default unit.
l When a CAMS or iMC server is used, you must configure the RADIUS server type to extended. When a third-party RADIUS server is used, you can configure the RADIUS server type to either standard or extended.
Setting the Status of RADIUS Servers
When a primary server fails, the AP automatically turns to the secondary server.
When both the primary and secondary servers are available, the AP sends request packets to the primary server.
Once the primary server fails, the primary server turns into the state of block, and the AP turns to the secondary server. In this case:
l If the secondary server is available, the AP triggers the primary server quiet timer. After the quiet timer times out, the status of the primary server is active again and the status of the secondary server remains the same.
l If the secondary server fails, the AP restores the status of the primary server to active immediately.
If the primary server has resumed, the AP turns to use the primary server and stops communicating with the secondary server. After accounting starts, the communication between the client and the secondary server remains unchanged.
Follow these steps to set the status of RADIUS servers:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Set the status of the primary RADIUS authentication/authorization server |
state primary authentication { active | block } |
Optional active for every server configured with IP address in the RADIUS scheme |
|
Set the status of the primary RADIUS accounting server |
state primary accounting { active | block } |
|
|
Set the status of the secondary RADIUS authentication/authorization server |
state secondary authentication { active | block } |
|
|
Set the status of the secondary RADIUS accounting server |
state secondary accounting { active | block } |
![]()
l If both the primary server and the secondary server are in the blocked state, it is necessary to manually turn the secondary server to the active state so that the secondary server can perform authentication. If the secondary server is still in the blocked state, the primary/secondary switchover cannot take place.
l If one server is in the active state while the other is blocked, the primary/secondary switchover will not take place even if the active server is not reachable.
l The server status set by the state command cannot be saved in the configuration file and will be restored to active every time the server restarts.
Configuring Attributes Related to the Data Sent to the RADIUS Server
Follow these steps to configure the attributes related to the data sent to the RADIUS server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify the format of the username to be sent to a RADIUS server |
user-name-format { keep-original | with-domain | without-domain } |
Optional By default, the ISP domain name is included in the username. |
|
Specify the unit for data flows or packets to be sent to a RADIUS server |
data-flow-format { data { byte | giga-byte | kilo-byte | mega-byte } | packet { giga-packet | kilo-packet | mega-packet | one-packet } }* |
Optional The defaults are as follows: byte for data flows, and one-packet for data packets. |
![]()
l Some earlier RADIUS servers cannot recognize usernames that contain an ISP domain name. In this case, the AP must remove the domain name before sending a username including a domain name. You can configure the user-name-format without-domain command on the AP for this purpose.
l If a RADIUS scheme defines that the username is sent without the ISP domain name, do not apply the RADIUS scheme to more than one ISP domain, thus avoiding the confused situation where the RADIUS server regards two users in different ISP domains but with the same userid as one.
l For level switching authentication, the user-name-format keep-original and user-name-format without-domain commands produce the same results, that is, usernames sent to the RADIUS server carry no ISP domain name.
l The unit of data flows sent to the RADIUS server must be consistent with the traffic statistics unit of the RADIUS server. Otherwise, accounting cannot be performed correctly.
Enabling the RADIUS Trap Function
If a NAS sends an accounting or authentication request to the RADIUS server but gets no response, the NAS retransmits the request. With the RADIUS trap function enabled, when the NAS transmits the request for half of the specified maximum number of transmission attempts, it sends a trap message; when the NAS transmits the request for the specified maximum number of transmission attempts, it sends another trap message.
Follow these steps to enable the RADIUS trap function:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the RADIUS trap function |
radius trap { accounting-server-down | authentication-server-down } |
Required Disabled by default |
Specifying the Source IP Address for RADIUS Packets to Be Sent
After you specify the source IP address for RADIUS packets to be sent on a NAS, if the physical port for sending the RADIUS packets fails, response packets from the RADIUS server will be able to arrive at the NAS.
Follow these steps to specify the source IP address for RADIUS packets to be sent:
|
To do… |
Use the command… |
Remarks |
|
|
Enter system view |
system-view |
— |
|
|
Specify the source IP address for RADIUS packets to be sent |
System view |
radius nas-ip { ip-address | ipv6 ipv6-address } |
Required Use either approach By default, there is no source IP address specified for RADIUS packets and the IP address of the interface for sending the RADIUS packets will be used as the source IP address of the RADIUS packets. |
|
RADIUS scheme view |
radius scheme radius-scheme-name |
||
|
nas-ip { ip-address | ipv6 ipv6-address } |
|||
![]()
The setting made with the nas-ip command in RADIUS scheme view is only applied to the RADIUS scheme, while that made with the radius nas-ip command in system view is applied to all RADIUS schemes. However, the setting made in RADIUS scheme view takes precedence over that made in system view.
Setting Timers Regarding RADIUS Servers
When communicating with the RADIUS server, an AP can enable the following three timers:
l RADIUS server response timeout (response-timeout): If a NAS receives no response from the RADIUS server in a period of time after sending a RADIUS request (authentication/authorization or accounting request), it has to resend the request so that the user has more opportunity to obtain the RADIUS service. The NAS uses the RADIUS server response timeout timer to control the transmission interval.
l Primary server quiet timer (timer quiet): If the primary server is not reachable, its state changes to blocked, and the AP will turn to the specified secondary server. If the secondary server is reachable, the AP starts this timer and communicates with the secondary server. After this timer expires, the AP turns the state of the primary server to active and tries to communicate with the primary server while keeping the state of the secondary server unchanged. If the primary server has come back into operation, the AP interacts with the primary server and terminates its communication with the secondary server.
l Real-time accounting interval (realtime-accounting): This timer defines the interval for performing real-time accounting of users. After this timer is set, the access point (AP) will send accounting information of online users to the RADIUS server at the specified interval.
Follow these steps to set timers regarding RADIUS servers:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Set the RADIUS server response timeout timer |
timer response-timeout seconds |
Optional 3 seconds by default |
|
Set the quiet timer for the primary server |
timer quiet minutes |
Optional 5 minutes by default |
|
Set the real-time accounting interval |
timer realtime-accounting minutes |
Optional 12 minutes by default |
![]()
l The maximum number of retransmission attempts of RADIUS packets multiplied by the RADIUS server response timeout period cannot be greater than 75. This product is also the upper limit of the timeout time of different access modules.
l For an access module, the maximum number of retransmission attempts multiplied by the RADIUS server response timeout period must be smaller than the timeout time. Otherwise, stop-accounting messages cannot be buffered, and the primary/secondary server switchover cannot take place. For example, as the timeout time of voice access is 10 seconds, the product of the two parameters cannot exceed 10 seconds; as the timeout time of Telnet access is 30 seconds, the product of the two parameters cannot exceed 30 seconds. For more information about timeout time of a specific access module, see the corresponding configuration guide.
l To configure the maximum number of retransmission attempts of RADIUS packets, see the command retry in the command reference.
Configuring RADIUS Accounting-on
With the accounting-on function enabled, an AP sends, whenever it reboots, accounting-on packets to the RADIUS server, requesting the server to force its users to log out. This solves the problem that users online before the reboot cannot re-log in after the reboot.
Once configured, the accounting-on function is executed as soon as the AP restarts and completes its configuration. In case that the majority of the RADIUS servers specified on an AP fail to respond to the accounting-on packets, the number of accounting-on packet retransmission attempts is too big, or the accounting-on packet retransmission interval is too long, the AP will not handle AAA services until all these packets are retransmitted and all RADIUS servers have responded to accounting-on packets.
Follow these steps to configure accounting-on function of a RADIUS server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Enable accounting-on |
accounting-on enable |
Required Disabled by default |
|
Set the number of accounting-on packet retransmission attempts |
accounting-on enable send send-times |
Optional 5 times by default |
|
Set the retransmission interval of accounting-on packets |
accounting-on enable interval seconds |
Optional 3 seconds by default |
![]()
The accounting-on feature needs to cooperate with the H3C CAMS or iMC network management system.
Specifying Security Policy Servers
The core of the EAD solution is integration and cooperation, and the security policy server system is the management and control center. As a collection of software, the security policy server system can run on Windows and Linux to provide functions such as user management, security policy management, security status assessment, security cooperation control, and security event audit.
Follow these steps to specify a security policy server:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify a security policy server |
security-policy-server ip-address |
Optional Not specified by default |
![]()
l If more than one interface of the AP is configured with access authentication functions, the interfaces may use different security policy servers. You can specify up to eight security policy servers for a RADIUS scheme.
l If the RADIUS server and the security policy server reside on the same physical AP, you do not need to specify the IP address of the security policy server.
l The specified security policy server must be a security policy server or RADIUS server that is correctly configured and working normally. Otherwise, the AP will regard it as an illegal server.
Enabling the Listening Port of the RADIUS Client
Follow these steps to enable the listening port of the RADIUS client:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the listening port of the RADIUS client |
radius client enable |
Optional Enabled by default |
Configuring Interpretation of RADIUS Class Attribute as CAR Parameters
According to RFC 2865, a RADIUS server assigns the RADIUS class attribute (25) to a RADIUS client. However, the RFC only requires the RADIUS client to send the attribute to the accounting server; it does not require the RADIUS client to resolve the attribute. Currently, some RADIUS servers use the class attribute to deliver the assigned committed access rate (CAR) parameters. To support such applications, you need to configure the RADIUS client to interpret the class attribute as the CAR parameters.
Follow these steps to configure the RADIUS client to interpret the class attribute as the CAR parameters:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter RADIUS scheme view |
radius scheme radius-scheme-name |
— |
|
Specify the scheme to interpret the class attribute as the CAR parameters |
attribute 25 car |
Required Be default, RADIUS attribute 25 is not interpreted as CAR parameters. |
![]()
Whether to configure this feature depends on the implementation of the AP and RADIUS server.
Displaying and Maintaining RADIUS
|
To do… |
Use the command… |
Remarks |
|
Display the configuration information of a specified RADIUS scheme or all RADIUS schemes on a centralized AP |
display radius scheme [ radius-scheme-name ] |
Available in any view |
|
Display statistics about RADIUS packets |
display radius statistics |
Available in any view |
|
Display information about buffered stop-accounting requests that get no responses |
display stop-accounting-buffer { radius-scheme radius-server-name | session-id session-id | time-range start-time stop-time | user-name user-name } |
Available in any view |
|
Clear RADIUS statistics |
reset radius statistics |
Available in user view |
|
Clear buffered stop-accounting requests that get no responses |
reset stop-accounting-buffer { radius-scheme radius-server-name | session-id session-id | time-range start-time stop-time | user-name user-name } |
Available in user view |
AAA Configuration Examples
AAA for Telnet Users by a RADIUS Server
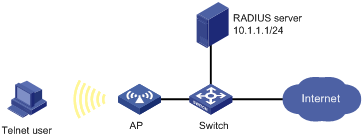
Network requirements
As shown in Figure 1-8, configure the AP to use the RADIUS server to provide authentication, authorization, and accounting services to login users.
l The RADIUS server is used for authentication, authentication, and accounting. Its IP address is 10.1.1.1/24.
l On the AP, set the shared keys for authentication, authorization, and accounting packets to expert. Configure the AP to remove the domain name from a username before sending the username to the RADIUS server.
l On the RADIUS server, set the shared keys for packets exchanged with the AP to expert.
Figure 1-8 Configure AAA for Telnet users by a RADIUS server
Configuration procedure
# Configure the IP addresses of various interfaces (omitted).
# Enable the Telnet server on the AP.
<AP> system-view
[AP] telnet server enable
# Configure the AP to use AAA for Telnet users.
[AP] user-interface vty 0 4
[AP-ui-vty0-4] authentication-mode scheme
[AP-ui-vty0-4] quit
# Configure the RADIUS scheme.
[AP] radius scheme radius1
[AP-radius-radius1] primary authentication 10.1.1.1 1812
[AP-radius-radius1] primary accounting 10.1.1.1 1813
[AP-radius-radius1] key authentication expert
[AP-radius-radius1] key accounting expert
[AP-radius-radius1] user-name-format without-domain
[AP-radius-radius1] quit
# Apply the AAA schemes to the domain.
[AP] domain bbb
[AP-isp-bbb] authentication login radius-scheme radius1
[AP-isp-bbb] accounting login radius-scheme radius1
[AP-isp-bbb] authorization login radius-scheme radius1
[AP-isp-bbb] quit
# You can achieve the same purpose by setting AAA schemes for all types of users.
[AP] domain bbb
[AP-isp-bbb] authentication default radius-scheme radius1
[AP-isp-bbb] accounting default radius-scheme radius1
[AP-isp-bbb] authorization default radius-scheme radius1
[AP-isp-bbb] quit
# Specify the default ISP domain.
[AP] domain default enable bbb
When telneting into the AP, a user enters username userid for authentication using domain bbb.
AAA for Telnet Users by Separate APs
Network requirements
As shown in Figure 1-9, configure the AP to provide local authentication, local authorization, and RADIUS accounting services to Telnet users. The username and the password for Telnet users are both hello.
The RADIUS server is used for accounting. Its IP address is 10.1.1.1/24. On the AP, set the shared keys for packets exchanged with the RADIUS server to expert. Configure the AP to remove the domain name from a username before sending the username to the RADIUS server.
![]()
Configuration of separate AAA for other types of users is similar to that given in this example. The only difference lies in the access type.
Figure 1-9 Configure AAA by separate APs for Telnet users

Configuration procedure
# Configure the IP addresses of various interfaces (omitted).
# Enable the Telnet server on the AP.
<AP> system-view
[AP] telnet server enable
# Configure the AP to use AAA for Telnet users.
[AP] user-interface vty 0 4
[AP-ui-vty0-4] authentication-mode scheme
[AP-ui-vty0-4] quit
# Configure the RADIUS scheme.
[AP] radius scheme rd
[AP-radius-rd] primary accounting 10.1.1.1 1813
[AP-radius-rd] key accounting expert
[AP]-radius-rd] server-type extended
[AP-radius-rd] user-name-format without-domain
[AP-radius-rd] quit
# Create a local user named hello.
[AP] local-user hello
[AP]-luser-hello] service-type telnet
[AP-luser-hello] password simple hello
[AP-luser-hello] quit
# Configure the AAA schemes of the ISP domain.
[AP] domain bbb
[AP-isp-bbb] authentication login local
[AP-isp-bbb] authorization login local
[AP-isp-bbb] accounting login radius-scheme rd
[AP-isp-bbb] quit
# Configure the default AAA schemes for all types of users.
[AP] domain bbb
[AP-isp-bbb] authentication default local
[AP-isp-bbb] authorization default local
[AP-isp-bbb] accounting default radius-scheme rd
[AP-isp-bbb] quit
# Specify the default ISP domain.
[AP] domain default enable bbb
When telneting into the AP, a user enters username hello@bbb for authentication using domain bbb.
Troubleshooting AAA
Troubleshooting RADIUS Authentication/Authorization Failure
Symptom: User authentication/authorization always fails.
Analysis:
1) A communication failure exists between the NAS and the RADIUS server.
2) The username is not in the format of userid@isp-name or no default ISP domain is specified for the NAS.
3) The user is not configured on the RADIUS server.
4) The password of the user is incorrect.
5) The RADIUS server and the NAS are configured with different shared key.
Solution:
Check that:
1) The NAS and the RADIUS server can ping each other.
2) The username is in the userid@isp-name format and a default ISP domain is specified on the NAS.
3) The user is configured on the RADIUS server.
4) The password entered by the user is correct.
5) The same shared key is configured on both the RADIUS server and the NAS.
Troubleshooting RADIUS Packet Transmission Failure
Symptom: RADIUS packets cannot reach the RADIUS server.
Analysis:
1) The communication link between the NAS and the RADIUS server is down (at the physical layer and data link layer).
2) The NAS is not configured with the IP address of the RADIUS server.
3) The UDP ports for authentication/authorization and accounting are not correct.
Solution:
Check that:
1) The communication links between the NAS and the RADIUS server work well at both physical and link layers.
2) The IP address of the RADIUS server is correctly configured on the NAS.
3) UDP ports for authentication/authorization/accounting configured on the NAS are the same as those configured on the RADIUS server.
Troubleshooting RADIUS Accounting Failure
Symptom: A user is authenticated and authorized, but accounting for the user is not normal.
Analysis:
1) The accounting port number is not correct.
2) Configuration of the authentication/authorization server and the accounting server are not correct on the NAS. For example, one server is configured on the NAS to provide all the services of authentication/authorization and accounting, but in fact the services are provided by different servers.
Solution:
Check that:
1) The accounting port number is correctly set.
2) The authentication/authorization server and the accounting server are correctly configured on the NAS.
Commonly Used Standard RADIUS Attributes
Table 2-1 Commonly used standard RADIUS attributes
|
No. |
Attribute |
Description |
|
1 |
User-Name |
Name of the user to be authenticated |
|
2 |
User-Password |
User password for PAP authentication, present only in Access-Request packets in PAP authentication mode. |
|
3 |
CHAP-Password |
Digest of the user password for CHAP authentication, present only in Access-Request packets in CHAP authentication mode. |
|
4 |
NAS-IP-Address |
IP address for the server to identify a client. Usually, a client is identified by the IP address of the access interface of the NAS, namely the NAS IP address. This attribute is present in only Access-Request packets. |
|
5 |
NAS-Port |
Physical port of the NAS that the user accesses |
|
6 |
Service-Type |
Type of the service that the user has requested or type of the service to be provided |
|
7 |
Framed-Protocol |
Encapsulation protocol |
|
8 |
Framed-IP-Address |
IP address to be configured for the user |
|
11 |
Filter-ID |
Name of the filter list |
|
12 |
Framed-MTU |
Maximum transmission unit (MTU) for the data link between the user and NAS. For example, with 802.1X EAP authentication, NAS uses this attribute to notify the server of the MTU to avoid oversized EAP packets. |
|
14 |
Login-IP-Host |
IP address of the NAS interface that the user accesses |
|
15 |
Login-Service |
Type of the service that the user uses for login |
|
18 |
Reply-Message |
Text to be displayed to the user, which can be used by the server to indicate, for example, the reason of the authentication failure. |
|
26 |
Vendor-Specific |
Vendor specific attribute. A packet can contain one or more such proprietary attributes, each of which can contain one or more sub-attributes. |
|
27 |
Session-Timeout |
Maximum duration of service to be provided to the user before termination of the session |
|
28 |
Idle-Timeout |
Maximum idle time permitted for the user before termination of the session |
|
31 |
Calling-Station-Id |
ID of the user that the NAS sends to the server. With the LAN access service provided by an H3C AP, this attribute carries the MAC address of the user in the format HHHH-HHHH-HHHH. |
|
32 |
NAS-Identifier |
ID that the NAS uses for indicating itself |
|
40 |
Acct-Status-Type |
Type of the Accounting-Request packet, which can be: l 1: Start l 2: Stop l 3: Interium-Update l 4: Reset-Charge l 7: Accounting-On (Defined in 3GPP, the 3rd Generation Partnership Project) l 8: Accounting-Off (Defined in 3GPP) l 9-14: Reserved for tunnel accounting l 15: Reserved for failed |
|
45 |
Acct-Authentic |
Authentication method used by the user, which can be: l 1: RADIUS l 2: Local l 3: Remote |
|
60 |
CHAP-Challenge |
CHAP challenge generated by the NAS for MD5 calculation during CHAP authentication |
|
61 |
NAS-Port-Type |
Type of the physical port of the NAS that is authenticating the user, which can be: l 15: Ethernet l 16: Any type of ADSL l 17: Cable (with cable for cable TV) l 201: VLAN l 202: ATM If the port is an ATM or Ethernet one and VLANs are implemented on it, the value of this attribute is 201. |
|
79 |
EAP-Message |
Used for encapsulating EAP packets to allow the NAS to authenticate dial-in users via EAP without having to understand the EAP protocol |
|
80 |
Message-Authenticator |
Used for authentication and checking of authentication packets to prevent spoofed Access-Requests. This attribute is used when RADIUS supports EAP authentication. |
|
87 |
NAS-Port-Id |
String for describing the port of the NAS that is authenticating the user |
Proprietary RADIUS Sub-Attributes of H3C
Table 2-2 Proprietary RADIUS sub-attributes of H3C
|
No. |
Sub-attribute |
Description |
|
1 |
Input-Peak-Rate |
Peak rate in the direction from the user to the NAS, in bps. |
|
2 |
Input-Average-Rate |
Average rate in the direction from the user to the NAS, in bps. |
|
3 |
Input-Basic-Rate |
Basic rate in the direction from the user to the NAS, in bps. |
|
4 |
Output-Peak-Rate |
Peak rate in the direction from the NAS to the user, in bps. |
|
5 |
Output-Average-Rate |
Average rate in the direction from the NAS to the user, in bps. |
|
6 |
Output-Basic-Rate |
Basic rate in the direction from the NAS to the user, in bps. |
|
15 |
Remanent_Volume |
Remaining traffic of the connection, in different units for different server types. |
|
20 |
Command |
Operation for the session, used for session control. It can be: l 1: Trigger-Request l 2: Terminate-Request l 3: SetPolicy l 4: Result l 5: PortalClear |
|
24 |
Control_Identifier |
Identifier for retransmitted packets. For retransmitted packets of the same session, this attribute must take the same value; while for retransmitted packets of different sessions, this attribute may take the same value. The response of a retransmitted packet must also carry the same attribute. For Accounting-Request packets of the start, stop, and interim update types, the Control-Identifier attribute, if present, makes no sense. |
|
25 |
Result_Code |
Result of the Trigger-Request or SetPolicy operation, which can be: l 0: Succeeded l Any other value: Failed |
|
26 |
Connect_ID |
Index of the user connection |
|
28 |
Ftp_Directory |
Working directory of the FTP user. For an FTP user, when the RADIUS client acts as the FTP server, this attribute is used to set the FTP directory on the RADIUS client. |
|
29 |
Exec_Privilege |
Priority of the EXEC user |
|
59 |
NAS_Startup_Timestamp |
Startup time of the NAS in seconds, which is represented by the time elapsed after 00:00:00 on Jan. 1, 1970 (UTC). |
|
60 |
Ip_Host_Addr |
IP address and MAC address of the user carried in authentication and accounting requests, in the format A.B.C.D hh:hh:hh:hh:hh:hh. A space is required between the IP address and the MAC address. |
|
61 |
User_Notify |
Information that needs to be sent from the server to the client transparently |
|
62 |
User_HeartBeat |
Hash value assigned after an 802.1X user passes authentication, which is a 32-byte string. This attribute is stored in the user list on the AP and is used for verifying the handshake messages from the 802.1X user. This attribute exists in only Access-Accept and Accounting-Request packets. |
|
141 |
Security_Level |
Security level assigned after the SSL VPN user passes security authentication |
|
255 |
Product_ID |
Product name |
