- Released At: 16-10-2023
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
|
|
|
SSL VPN Technology White Paper |
|
|
|
|
|
|
Copyright © 2022 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Customizing SSL VPN webpage elements
Multi-dimensional and refined information display
Unified access control by SSO login
Bandwidth limit based on SSL VPN connections
Global bandwidth limit based on contexts
URL masking for internal resources
CRL checking for certificate authentication
Quick access to internal resources
Brute-force cracking prevention
Highly-converged virtualization technologies
Dual-system hot backup for high availability
Overview
Technical background
The Internet popularity allows users to access the Internet from anywhere at any time. For enterprises, it is an urgent need for branches and employees on business trips to quickly and conveniently realize remote office through the VPN technology for remote access.
SSL VPN enables enterprises to manage users and control access for specific resources due to diversification of network resources. The traditional VPN features, such as IPsec and L2TP cannot meet the requirements although they can implement remote access. SSL VPN is available for any clients that are installed with browsers. It has rich resource access control functions, supports user-based management, and satisfies users with different types of resource access requirements.
SSL VPN is a VPN feature that provides Secure Sockets Layer (SSL) based secure remote access services through an SSL VPN gateway.
Benefits
SSL VPN provides the following benefits compared with other VPN features such as IPsec and L2TP:
· Simple operation—Users do not need to install any client software, and can directly use a Web browser to access internal resources safely and conveniently.
· Access control—SSL VPN controls user access to resources on a per-user basis. Different users and user groups have different access privileges to internal resources. User-based access control is more simple and convenient.
· SSL VPN access modes—SSL VPN supports IP access mode, TCP access mode, and Web access mode. This provides highly fine-grained control of user access to resources by assigning resources in different ways.
· Multiple user authentication methods—SSL VPN supports multiple user authentication methods for secure access to SSL VPN, including username/password authentication, certificate authentication, and WeChat Work authentication. You can also use the combination of authentication methods.
· Support for application protocols—SSL is between the transport layer and application layer, which allows SSL VPN to provide security for any applications.
· Support for multiple operating systems—SSL is integrated into most browsers including IE, Chrome, and Firefox. This indicates that any PC installed with an available browser supports SSL connection. Any operation system that supports the SSL protocol can run on SSL VPN clients.
· No influence on the existing network topology—The SSL VPN deployment does not affect the existing network topology. SSL operates over the transport layer, which does not change the IP header or TCP header. SSL packets are transparent to NAT. The port number used by SSL IS fixed at 443. You only need to open port 443 on the device and do not have to configure settings based on different applications. This reduces workload and improves network security.
SSL VPN implementation
Concepts
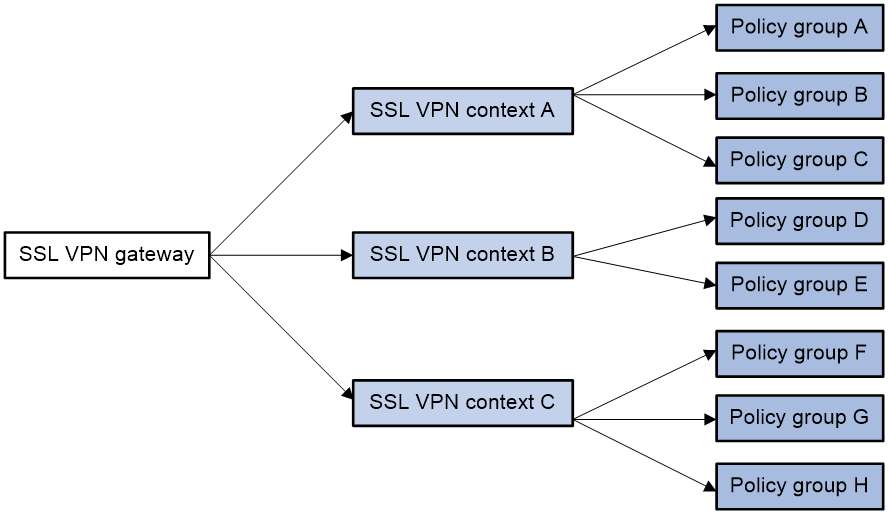
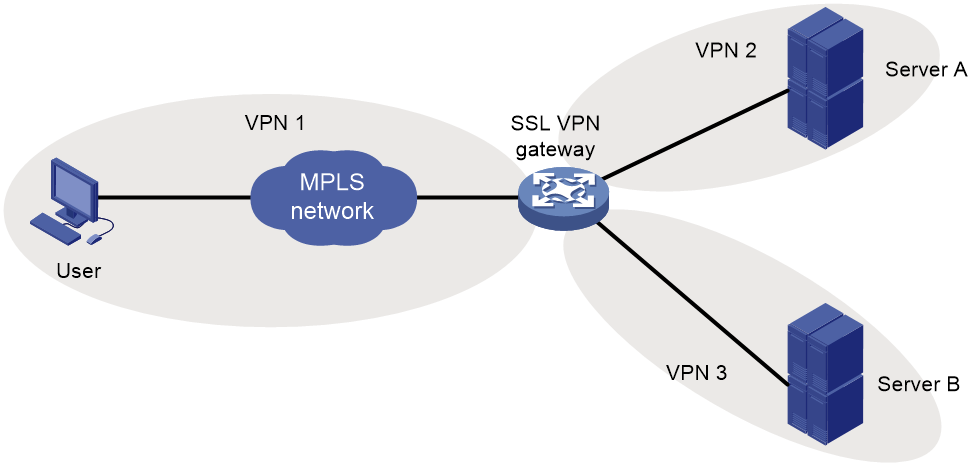
· SSL VPN gateway—A network device that provides SSL VPN services between the client and the internal server. The SSL VPN gateway forwards user access requests and provide users with accessible internal server resources.
· SSL VPN context—Manages user sessions, user authentication methods, and resources that users can access.
· SSL VPN policy group—A policy group is a collection of internal resources to associate internal resources for user access. After a user is authorized to use a policy group, the user can access resources allowed by the policy group.
As shown in Figure 1, an SSL VPN gateway can be associated with multiple SSL VPN contexts. An SSL VPN context contains multiple policy groups. A policy group is associated with internal resources. If the SSL VPN gateway authorizes a user to use a policy group, the user can access resources allowed by the policy group.
Figure 1 Basic SSL VPN concepts
SSL protocol mechanism
SSL VPN is based on the SSL protocol. The SSL protocol is between the transport layer and application layer. It can provide security for all application protocols based on TCP connections, for example HTTP. The HTTP protocol encrypted by the SSL protocol is called HTTPS that is the most commonly used application layer security protocol. In actual application, HTTPS can provide reliable security for Web browsing, email, instant messaging and other data interactions.
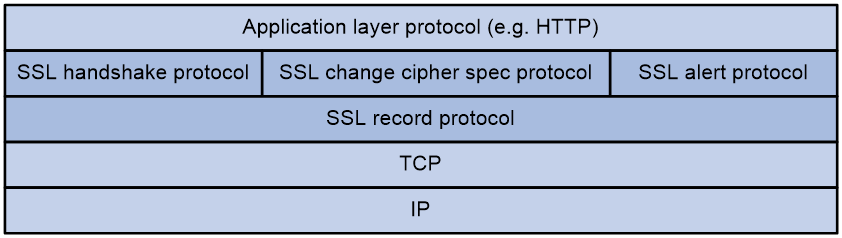
The SSL protocol stack includes the following protocols:
· SSL record protocol at the lower layer.
· SSL handshake protocol, SSL change cipher spec protocol, and SSL alert protocol at the upper layer.
The SSL protocol stack consists of two layers of protocols: the SSL record protocol at the lower layer and the SSL handshake protocol, change cipher spec protocol, and alert protocol at the upper layer.
The following describes the major functions of SSL protocols:
· SSL record protocol—Fragments data received from the upper layer, computes and adds MAC to the data, and encrypts the data.
· SSL handshake protocol—Negotiates the cipher suite used for secure communication, authenticates the server and client, and securely exchanges the keys between the server and client. The cipher suite that needs to be negotiated includes the symmetric encryption algorithm, key exchange algorithm, and MAC algorithm.
· SSL change cipher spec protocol—Notifies the receiver that subsequent packets are to be protected based on the negotiated cipher suite and key.
· SSL alert protocol—Sends alert messages to the receiving party. An alert message contains the alert severity level and a description.
SSL protocol versions include SSL 2.0, SSL 3.0, TLS 1.0 (or SSL 3.1), TLS 1.1, and TLS 1.2.
SSL provides the following security services for VPN access security:
· Privacy—SSL uses a symmetric encryption algorithm to encrypt data. It uses the asymmetric key algorithm of RSA to encrypt the key used by the symmetric encryption algorithm.
· Authentication—SSL uses certificate-based digital signatures to authenticate the SSL server and client.
· Integrity—SSL uses the message authentication code (MAC) to verify message integrity. It uses a MAC algorithm and a key to transform a message of any length to a fixed-length message. Any change to the original message will result in a change to the calculated fixed-length message.
SSL VPN mechanism
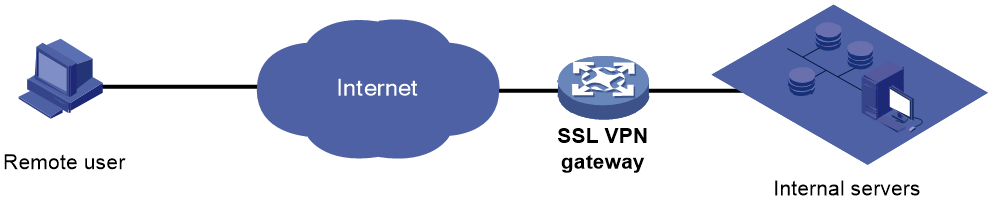
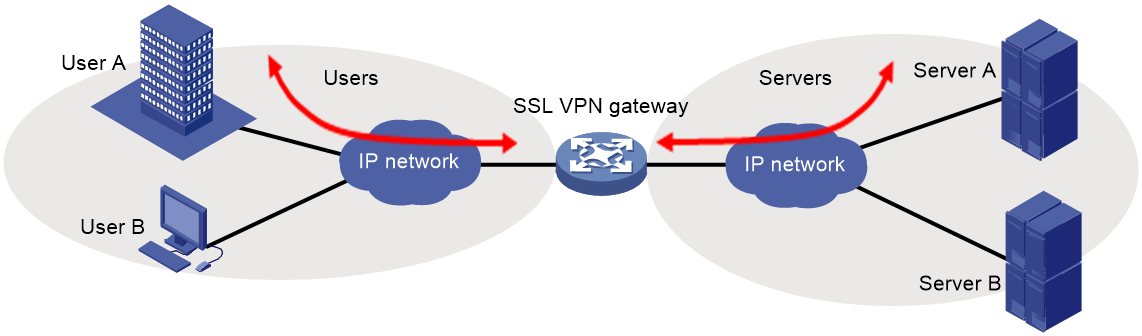
SSL VPN services are provided through an SSL VPN gateway. To allow remote user access to protected resources behind an SSL VPN gateway, you must configure these resources on the gateway.
Figure 3 SSL VPN network diagram
As shown in Figure 3, SSL VPN operates as follows:
1. The remote user establishes an HTTPS connection to the SSL VPN gateway.
In this process, the remote user and the SSL VPN gateway perform SSL certificate authentication.
2. The remote user enters the username and password.
3. The SSL VPN gateway authenticates the credentials that the user entered, and authorizes the user to access a range of resources.
4. The user selects a resource to access.
An access request for that resource is sent to the SSL VPN gateway through the SSL connection.
5. The SSL VPN gateway resolves the request and forwards the request to the corresponding internal server.
6. The SSL VPN gateway forwards the server's reply to the user through the SSL connection.
SSL VPN access modes
SSL VPN supports Web access mode, TCP access mode, and IP access mode. These access modes provide different granularity of resource access control and have different application compatibility. Web access has the finest granularity of access control, providing fine control of user access to resources. This mode requires only a browser to be installed on clients, and has the highest application compatibility. IP access implements access control to resources based on the network layer, which is simple and easy to manage, but provides low application compatibility. In IP access mode, you must install an IP access client software.
Web access
Web access process
In Web access mode, remote users use browsers to access Web resources allowed by an SSL VPN gateway through HTTPS. After login and authentication, a user can access any resources listed on the webpage. In Web access mode, all operations are performed on webpages. Web access is widely used because it does not require specific software installation.
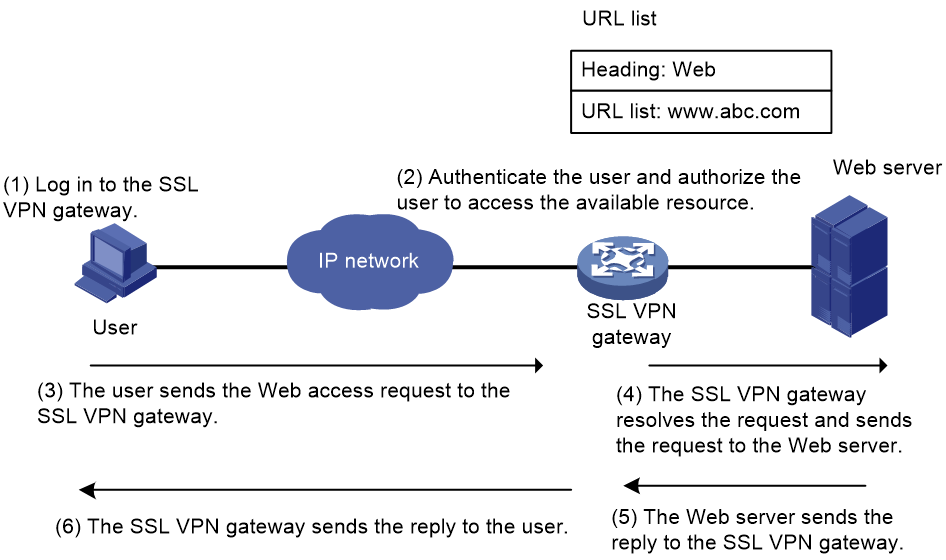
As shown in Figure 4, the Web access procedure is as follows:
1. A user uses a browser to log in to an SSL VPN gateway through HTTPS.
2. The SSL VPN gateway authenticates the user and authorizes the user to access the available URLs.
The authorized URLs are displayed on the SSL VPN gateway webpage as URL links.
3. The user selects a URL to access on the SSL VPN gateway webpage. The browser sends the access request to the SSL VPN gateway through the SSL connection for HTTPS.
4. The SSL VPN gateway resolves the request and sends the request to the Web server through HTTP or HTTPS.
5. The Web server sends the reply to the SSL VPN gateway.
6. After receiving the reply from the Web server, the SSL VPN gateway forwards the reply to the user through the SSL connection for HTTPS.
Figure 4 Network diagram for Web access
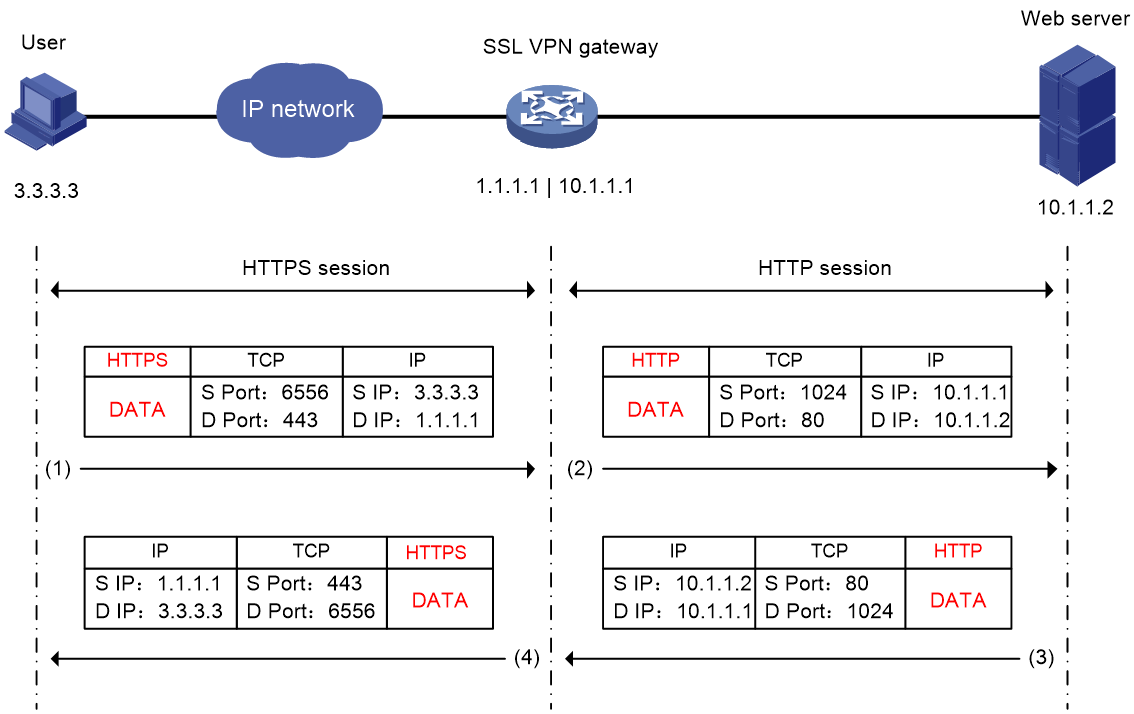
Packet encapsulation for Web access
As shown in Figure 5, the packet encapsulation process contains an HTTPS session and an HTTP session or another HTTPS session. A user sends an access request to the SSL VPN gateway through an HTTPS session, and then the SSL VPN gateway sends the access request to the Web server through an HTTP session. Then, after receiving the reply from the Web server, the SSL VPN gateway forwards the reply to the user through an HTTPS session.
Figure 5 Packet encapsulation process for Web access
TCP access
TCP access process
In TCP access mode, users access TCP applications on internal servers by accessing the applications' open ports. Supported applications include remote access services (such as Telnet), desktop sharing services, mail services, and other TCP services that use fixed ports.
In TCP access mode, a user installs the TCP access client software on the SSL VPN client (the terminal device that the user uses). The client software uses an SSL connection to transmit the application layer data for data security.
To implement TCP access, you must configure port forwarding instances on the SSL VPN gateway. A port forwarding instance maps a TCP service (identified by an IP address/domain name and port number) to an SSL VPN client's local IP address (or host name) and port number.
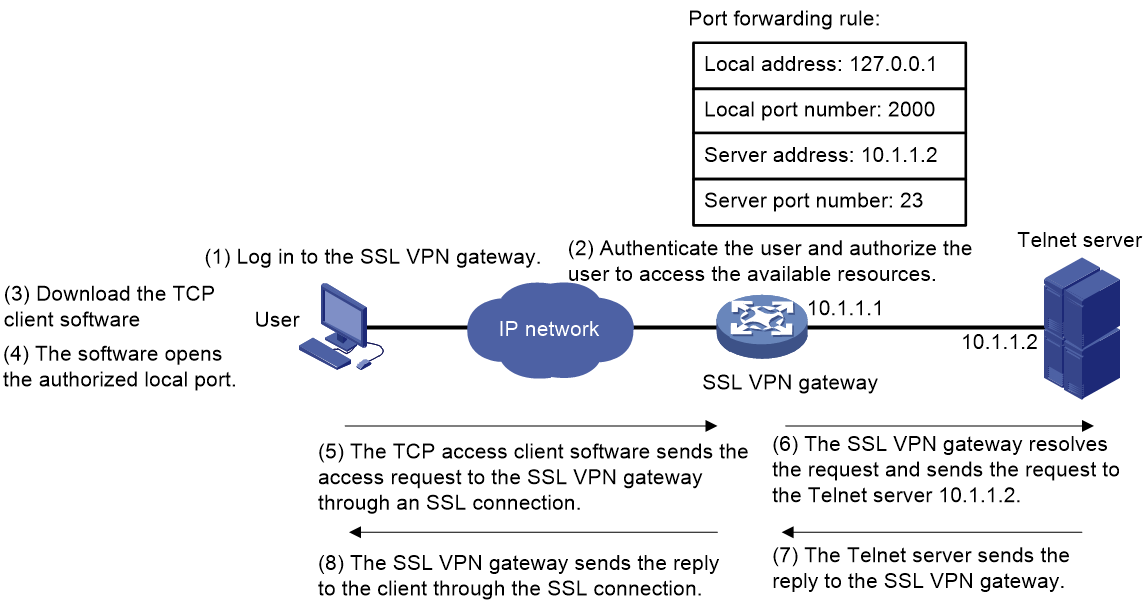
As shown in Figure 6, the TCP access procedure is as follows:
1. A user uses a browser to log in to an SSL VPN gateway through HTTPS.
2. The SSL VPN gateway authenticates the user and authorizes the user to access the Telnet service (port forwarding instance).
3. The user downloads the TCP access client software from the webpage of the SSL VPN gateway, and launches the software. The software opens the authorized local port in the port forwarding instance.
4. The user tries to access the local IP address and port number. The TCP access client software sends the access request to the SSL VPN gateway through an SSL connection.
5. The SSL VPN gateway resolves the request and sends the request to the Telnet server according to the port forwarding instance.
6. The Telnet sends the reply to the SSL VPN gateway.
7. After receiving the reply from the Telnet server, the SSL VPN gateway forwards the reply to the user through the SSL connection.
Figure 6 Network diagram for TCP access
Packet encapsulation for TCP access
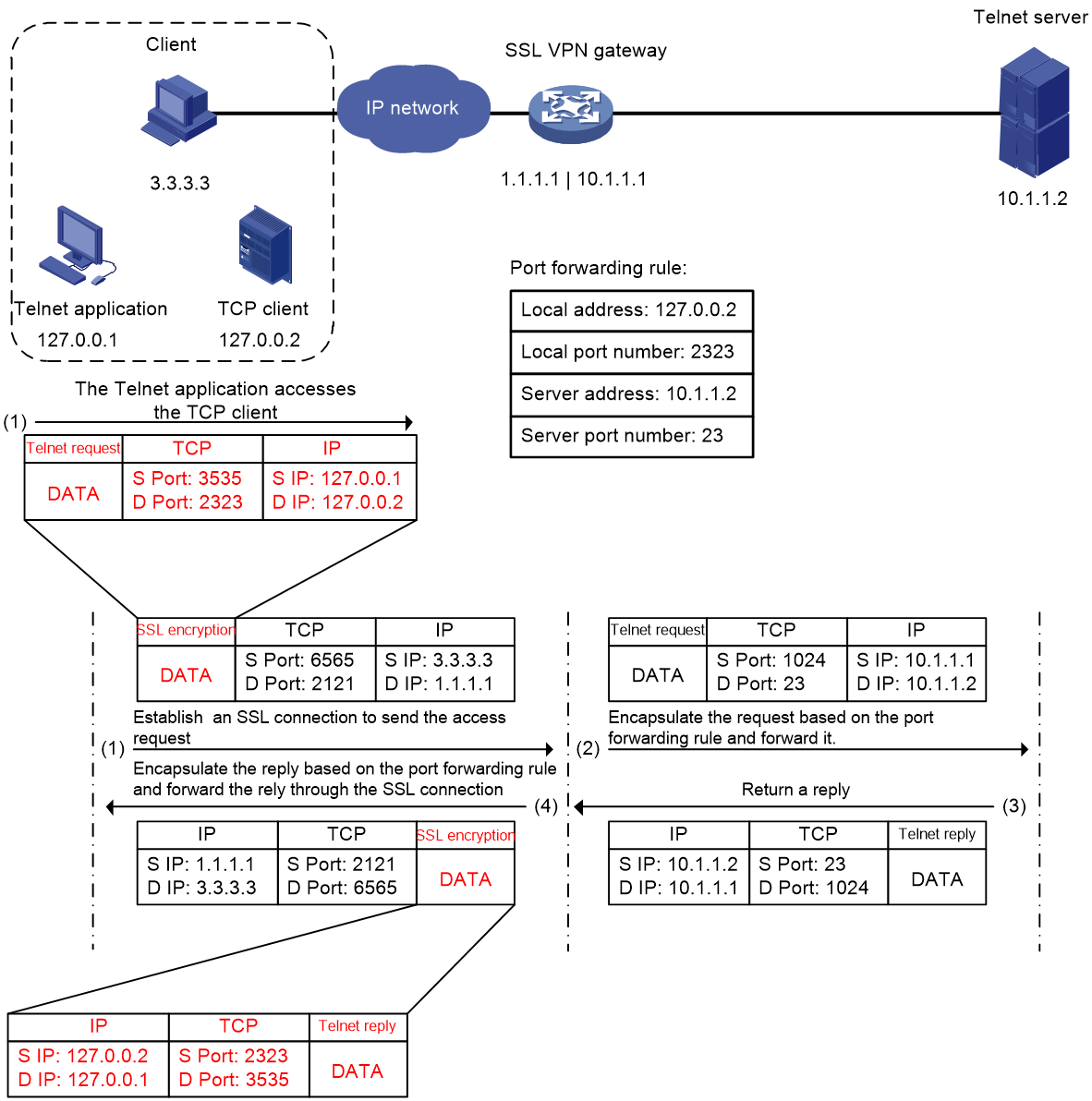
As shown in Figure 7, this example describes a client access to an internal Telnet server. The packet encapsulation for TCP access operates as follows:
1. The TCP client software listens to an access request sent by the Telnet application and sends the request to the SSL VPN gateway through an SSL connection.
2. The SSL VPN gateway performs SSL decryption, re-encapsulates the packet according to the port forwarding rule, and then sends the access request to the internal Telnet server.
3. After receiving the reply from the Telnet server, the SSL VPN gateway re-encapsulates the packet according to the port forwarding rule, and sends the reply to the TCP client through the SSL connection.
4. The TCP client sends the reply to the Telnet application through the loopback address.
Figure 7 Packet encapsulation process for TCP access
IP access
IP access process
IP access implements secured IP communication between remote users and internal servers.
To access an internal server in IP access mode, a user must install dedicated IP access client software. The client software will install a virtual network interface card (VNIC) on the SSL VPN client. H3C uses the iMC iNode client as the client software.
To implement IP access, you must configure the following on the SSL VPN gateway:
· An SSL VPN AC interface.
· Routes to accessible IP resources. The routes will be issued to SSL VPN clients to instruct packet forwarding.
As shown in Figure 8, the IP access process is as follows:
1. The user installs the IP access client software and launches the client software to log in to the SSL VPN gateway.
2. The SSL VPN gateway performs the following operations:
a. Authenticates and authorizes the user.
b. Allocates an IP address to the VNIC of the user.
c. Issues the authorized IP access resources to the client.
In this example, a route to server 10.1.1.2/24 is issued.
3. The client specifies the allocated IP address as the VNIC's address and adds the route to the local routing table, using the VNIC as output interface.
4. The client uses SSL to encapsulate the request packet, and then sends the packet to the SSL VPN AC interface through the VNIC.
5. The SSL VPN gateway de-encapsulates the SSL packet into the IP packet and forwards the IP packet to the corresponding internal server.
6. The internal server sends a reply to the SSL VPN gateway.
7. The SSL VPN gateway uses SSL to encapsulate the reply packet and then sends the packet to the client through the SSL VPN AC interface.
Figure 8 Network diagram for IP access
Packet encapsulation for IP access
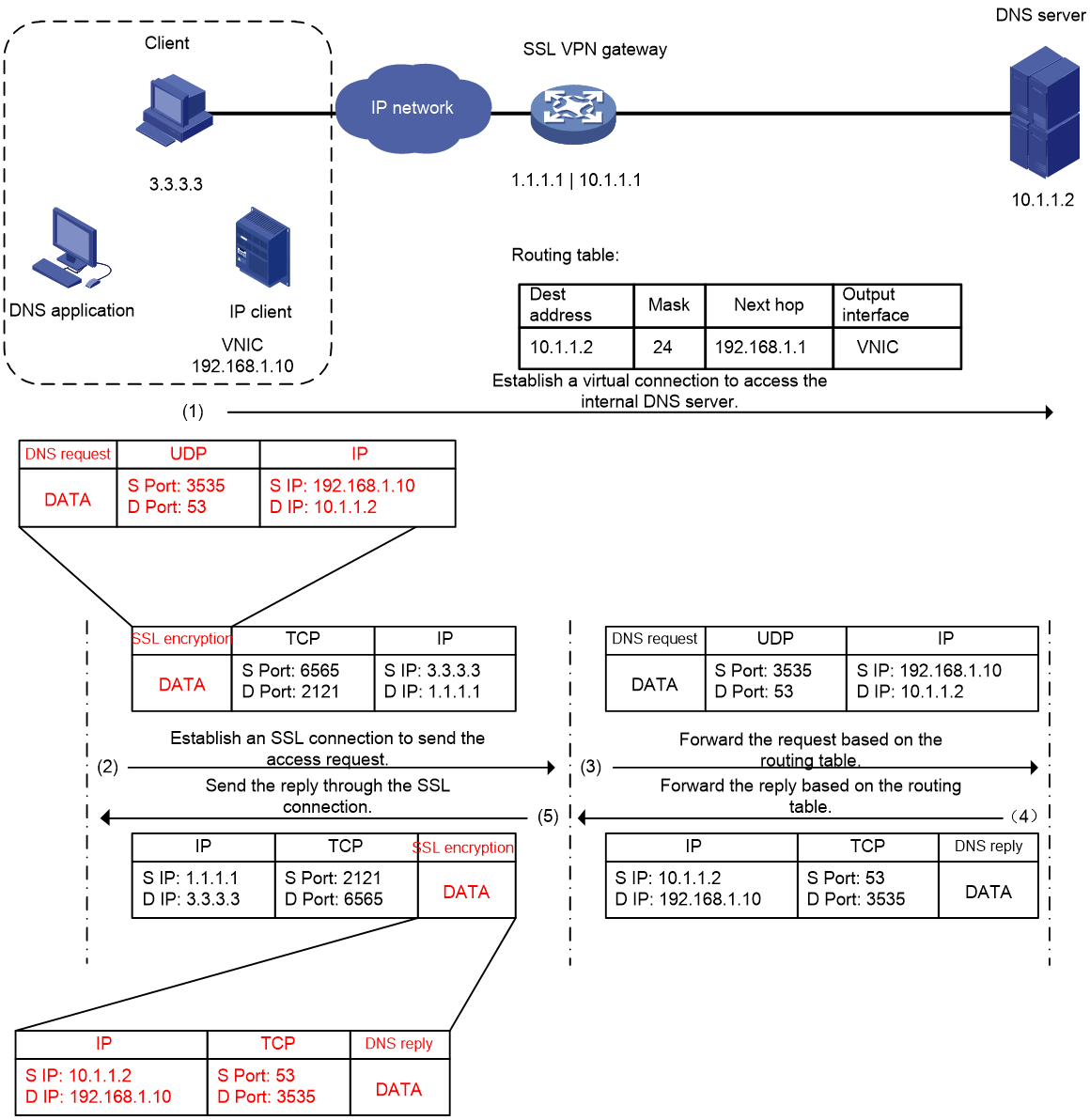
As shown in Figure 9, this example describes a client access to an internal DNS server. In IP access mode, the source IP address for the DNS application to access the internal DNS server is the IP address of VNIC assigned by the SSL VPN gateway. When a user accesses the internal DNS server, the packet encapsulation process for IP access is as follows:
1. The client encapsulates the DNS access request by looking up the routing table. The request packet is encrypted with SSL and is sent to the SSL VPN gateway.
2. The SSL VPN gateway de-encapsulates the request packet and sends it to the DNS server.
3. The DNS server returns a reply to the SSL VPN gateway.
4. The SSL VPN gateway sends the reply to the IP access client through the SSL connection.
Figure 9 Packet encapsulation process for IP access
SSL VPN user authentication
To access internal resources behind an SSL VPN gateway, a user must first pass identity authentication to log in to the SSL VPN gateway. SSL VPN supports multiple user authentication methods to satisfy different requirements in different scenarios. The combination of authentication methods is also supported. If multiple authentication methods are enabled, users must pass all authentication methods before SSL VPN login.
SSL VPN supports the following user authentication methods:
· Username/password authentication
After a user enters the login username and password, the SSL VPN gateway sends the username and password to the authentication module. Both remote authentication and local authentication are available. For local authentication, the username and password are configured on the SSL VPN gateway and the SSL VPN performs authentication. For remote authentication, the username and password are sent to a specific authentication server. The available servers include RADIUS server and LDAP server.
· Certificate authentication
A user certificate is sent to the SSL VPN gateway for authentication. The SSL VPN gateway verifies the validity of the user certificate. If the certificate is verified as valid, the authentication process continues. The SSL VPN gateway supports soft certificates and reading certificates from USB keys. The SSL VPN gateway can use the CN field in a certificate as the username for authentication, and also supports using a specific field of a certificate as the username.
· SMS authentication
After you enable SMS authentication, the device uses SMS verification codes to authenticate SSL VPN users. A user is allowed to log in to the SSL VPN gateway only when the user passes the SMS authentication. SSL VPN supports SMS authentication by using an IMC authentication server or a third-party SMS gateway.
· Custom authentication
Custom authentication allows you to set up and configure a custom authentication server as needed. The device can use the custom authentication server for user authentication and authorization. With support for customizing authentication message formats, the SSL VPN gateway is applicable to various non-standard authentication systems, thus greatly expanding SSL VPN application scenarios.
· WeChat Work authentication
WeChat Work (or WeCom) authentication allows the device to obtain user information in a company from WeChat Work and uses the user information for user authentication and authorization. After authentication and authorization, users can access internal resources through WeChat Work. WeChat Work can provide mobile office services with powerful terminal functions.
H3C implementation of SSL VPN
Customizing SSL VPN webpage elements
You can customize the following elements on the SSL VPN webpage:
· Login message.
· Password input box displaying.
· Title.
· Logo.
· Notification message on the SSL VPN gateway login page and resource page.
· Files for users to download on the SSL VPN resource page.
· Password complexity description.
· Server reply message rewriting.
The following further describes some elements to be customized:
· Notification message on the webpage
You can configure a notification message displayed on the SSL VPN login page or resource page, which is applicable to various scenarios.
· File upload and download
You can upload local files to the SSL VPN gateway and download uploaded files from the SSL gateway to implement file distribution and sharing.
· Password complexity description
The password complexity description will be displayed on the SSL VPN password modification page to notify users of password complexity requirements.
· Server reply message rewriting
A reply message might be returned from the authentication server during user access to the SSL VPN gateway. If the server reply message is hard to understand, you can rewrite the server reply message as needed. The reply message will be displayed on an access client, for example iNode client.
Multi-dimensional and refined information display
SSL VPN supports user access monitoring and query by providing multi-dimensional and refined information.
SSL VPN provides the following information:
· User access logs
When an SSL VPN user logs in or logs out, the SSL VPN gateway outputs a log message. The log information includes login or logout time, username, login IP address, SSL VPN context, login or logout operation, login or logout result, and reason for failure. You can view the logs for detailed user login or logout information to help with device management and maintenance.
· Resource access logs
When an SSL VPN user accesses internal resources, the SSL VPN gateway outputs corresponding log messages. The log information includes login time, username, login IP address, SSL VPN context, resource type, access resource, resource port number, and access result. You can view the logs to get detailed resource access information to help with resource access control and management.
· Server traffic statistics
The statistics provide traffic information about SSL VPN user access to internal servers. The administrator can adjust internal server deployment according to the statistics.
· Online users trend
The online SSL VPN users trend feature allows you to perform statistics about the number of concurrent online SSL VPN users. An online SSL VPN users trend graph and history statistics about SSL VPN users are also displayed. The administrator can view the online SSL VPN users trend and the historical maximum number of online users to expand capacity as needed.
Unified access control by SSO login
Single sign-on (SSO) allows a user to use one set of login credentials (such as username and password) to access multiple trusted systems. With SSO, SSL VPN users can gain access to internal servers without entering the login credentials for the internal servers, which improves resource access efficiency and user experience.
Bandwidth limit based on SSL VPN connections
The bandwidth limit feature based on SSL VPN connections limits traffic of a single SSL VPN connection. This prevents a single SSL VPN connection from using too much bandwidth and affecting other SSL VPN connections, which provides proper and effective bandwidth management.
Global bandwidth limit based on contexts
In IP access mode, SSL VPN supports global bandwidth rate limit based on contexts. A rate limit can be set on all users in a context. This feature also supports statistics on packet loss caused by rate limit and packet loss logs are generated.
URL masking for internal resources
The URL masking feature hides the real Web access resource URLs converting the URLs into coded strings to provide internal resources. You can enable or disable URL masking for a single URL or enable URL masking for all the Web resources in a context. For example, a real resource URL http://www.baidu.fin.com/cn/ can be converted into http://d3id3dsmgzeYy5jb20=r/cn/.
CRL checking for certificate authentication
For certificate authentication, the SSL VPN gateway will check for certificate revocation if CRL checking is enabled. If the certificate is verified as revoked, users cannot log in to the SSL VPN gateway. This feature ensures the reliability of user certificates and enhances the security of certificate authentication.
Quick access to internal resources
By default, after SSL VPN login, users need to enter the SSL VPN webpage and click a resource link to access the resource. The quick access feature allows users to directly access resources after logging in to the SSL VPN gateway without clicking the resource link on the SSL VPN webpage. This feature allows users to quickly access frequently used resources.
Support for GM algorithms
SSL VPN supports mainstream GM algorithms, including SM1, SM2, SM3, and SM4.
Brute-force cracking prevention
A brute-force cracking refers to consecutive login requests from the same IP address in an attempt to log in to an SSL VPN gateway by guessing passwords. If the brute-force cracking succeeds, internal resources will be leaked and user information security is seriously threatened.
The cracking prevention feature reduces the risk of brute-force cracking of user login information by limiting the number of login attempts from the same IP address. SSL VPN performs cracking prevention through the following methods:
· If the number of consecutive login failures of an IP address exceeds the specified number, code verification is enabled to prevent cracking. Code verification will be automatically disabled after a successful login.
· If the number of consecutive login failures of the same IP address reaches the specified number, the IP address will be frozen for the specified period of time. During the freeze period, the IP address is prohibited from logging in to the SSL VPN gateway
VRF-aware SSL VPN
VRF-aware SSL VPN provides the following functionalities:
· VRF-aware SSL VPN context—You associate different SSL VPN contexts with different VRF instances (VPN instances) on the SSL VPN gateway. Users in an SSL VPN context can access only the resources in the VPN instance associated with the SSL VPN context. VRF-aware SSL VPN contexts also allow server addresses to overlap.
· VRF-aware SSL VPN gateway—You specify the VPN instance to which the SSL VPN gateway belongs. Only users in the same VPN can access the SSL VPN gateway. The VRF-aware SSL VPN gateway prevents the internal server resources from leaking into the public network or other VPNs.
Figure 10 VRF-aware SSL VPN
Highly-converged virtualization technologies
SSL VPN supports the following levels of virtualization technologies for different application scenarios:
· Virtualization at the operating system level
A physical device can be virtualized into multiple logical devices called contexts. Each context is assigned separate hardware and software resources, and operates independently of other contexts.
Through virtualization at the operating system level, SSL VPN can implement isolation in management and forwarding, and completely appear as an independent SSL VPN gateway from users' perspective. This is suitable for to multi-tenant scenarios and can provide independent management interface for different administrators. Although different tenants share hardware resources, the default administrator can assign independent security capabilities to the device (context) corresponding to each tenant.
· Virtualization within SSL VPN
For scenarios that only need external access and service isolation, you can configure SSL VPN contexts within SSL VPN. SSL VPN contexts allows SSL VPN services to operate on a context basis to achieve independent configuration management between SSL VPN context domains. Users can access different SSL VPN contexts by using their domain names. In the forwarding layer, forwarding isolation between different SSL VPN contexts can be achieved through multiple VPN instances.
You can create SSL VPN contexts based on virtual devices (contexts) to implement two-level visualization. The administrator can specify the maximum number of online users for each context and SSL VPN context, and manage the number of access users in a unified manner.
Dual-system hot backup for high availability
SSL VPN supports dual-system hot backup to improve the reliability of SSL VPN user access. For dual-system hot backup, if the master SSL VPN gateway device fails, the other gateway device will take over the services. The new master has the authentication and authorization information and the online user can remain online after the master and backup switchover.
Application scenarios
SSL VPN networking modes typically include gateway mode and single-arm mode.
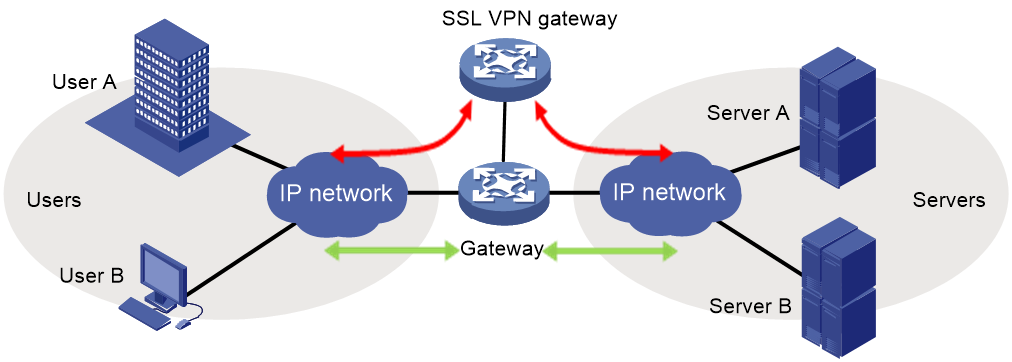
Gateway mode
In gateway mode, an SSL VPN gateway acts as a gateway that connects remote users and the internal servers network. All traffic is forwarded through the SSL VPN gateway
The gateway mode has the following characteristics:
· The SSL VPN gateway is deployed in the key path between the internal and the external, it can provide full protection for all traffic.
· This mode has high requirements on the processing capability, anti-attack capability, and stability for the SSL VPN gateway.
Single-arm mode
In single-arm mode, an SSL VPN gateway is attached to a network gateway. The network gateway forwards traffic to the SSL VPN gateway. The single-arm mode has the following characteristics:
· The SSL VPN gateway does not affect network communication even when it fails because it is not deployed on the key path.
· The network gateway forwards the traffic to be protected to the SSL VPN gateway. The SSL VPN gateway processes the traffic and sends the processed traffic back to the network gateway. The gateway forwards the traffic to the internal servers. Traffic that does need protection is forwarded directly to internal servers by the network gateway.
Figure 12 Single-arm mode